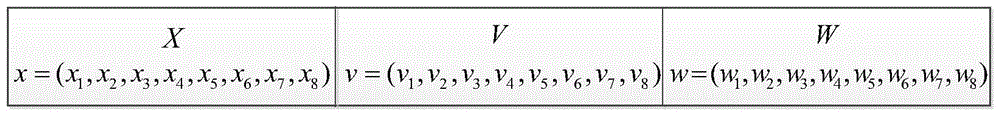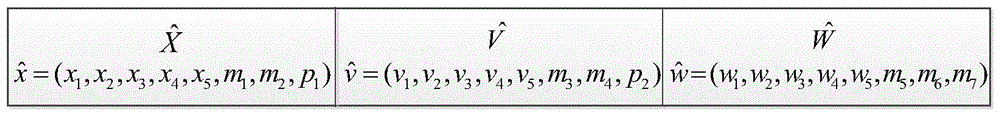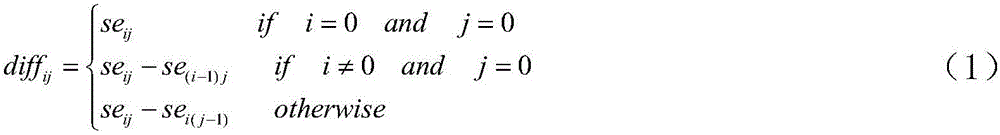A Method of Image Hiding and Authentication Based on Secret Sharing
A technology of secret sharing and authentication method, which is applied in the field of secret image sharing, and can solve problems such as potential safety hazards, differences in statistical characteristics, and reduced security of secret information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0069] We choose Matlab7.0 as the software platform, and program to realize the design of the scheme of the present invention. During the implementation process, the standard test image "Jet" of 256×256 was selected as the secret image, and four standard test images of 512×512 "Lena", "Peppers", "Baboon" and "Elaine" were selected as the carrier images, and parameters were selected in the sharing scheme k=3, n=4.
[0070] The present invention is characterized in that it is composed of two parts: secret sharing and information hiding, image authentication and secret information recovery. The specific operation steps are:
[0071] Ⅰ. Secret sharing and information hiding, including the following steps:
[0072] The first step is to read in a 256×256 standard test image “Jet” as the secret image SE;
[0073] In the second step, use the formula (1) to convert the secret image SE into a differential image DIFF={diff ij};
[0074] diff i ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com