Data file security privacy storage and sharing method based on a block chain
A data file and blockchain technology, applied in the computer field, can solve problems such as undecryptable data, achieve the effects of improving security and privacy, ensuring availability and integrity, and improving control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
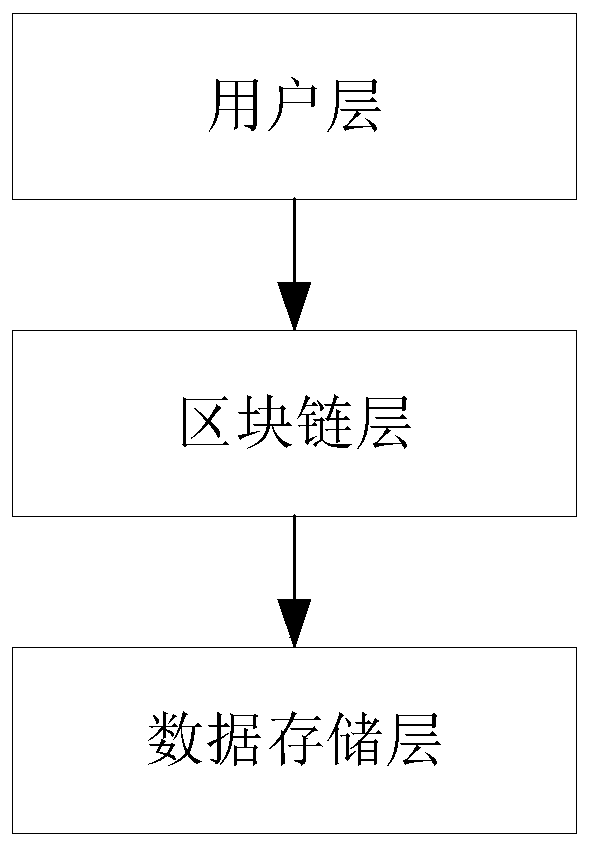
[0043] Such as figure 1 As shown, in this embodiment, the user layer mainly uses the symmetric encryption algorithm to encrypt its own data and uploads it to the storage server of the data storage layer, and then the data storage layer returns the data storage Location information, the data owner then encrypts the location information with an encryption algorithm according to the usage of the data, and then uses an encryption algorithm to encrypt the encrypted location information and encryption key according to the data sharing situation, and formulates related access strategies to The form of ciphertext is stored in the blockchain layer. When the blockchain layer completes the authentication of the new block, it returns the transaction id to the user layer.
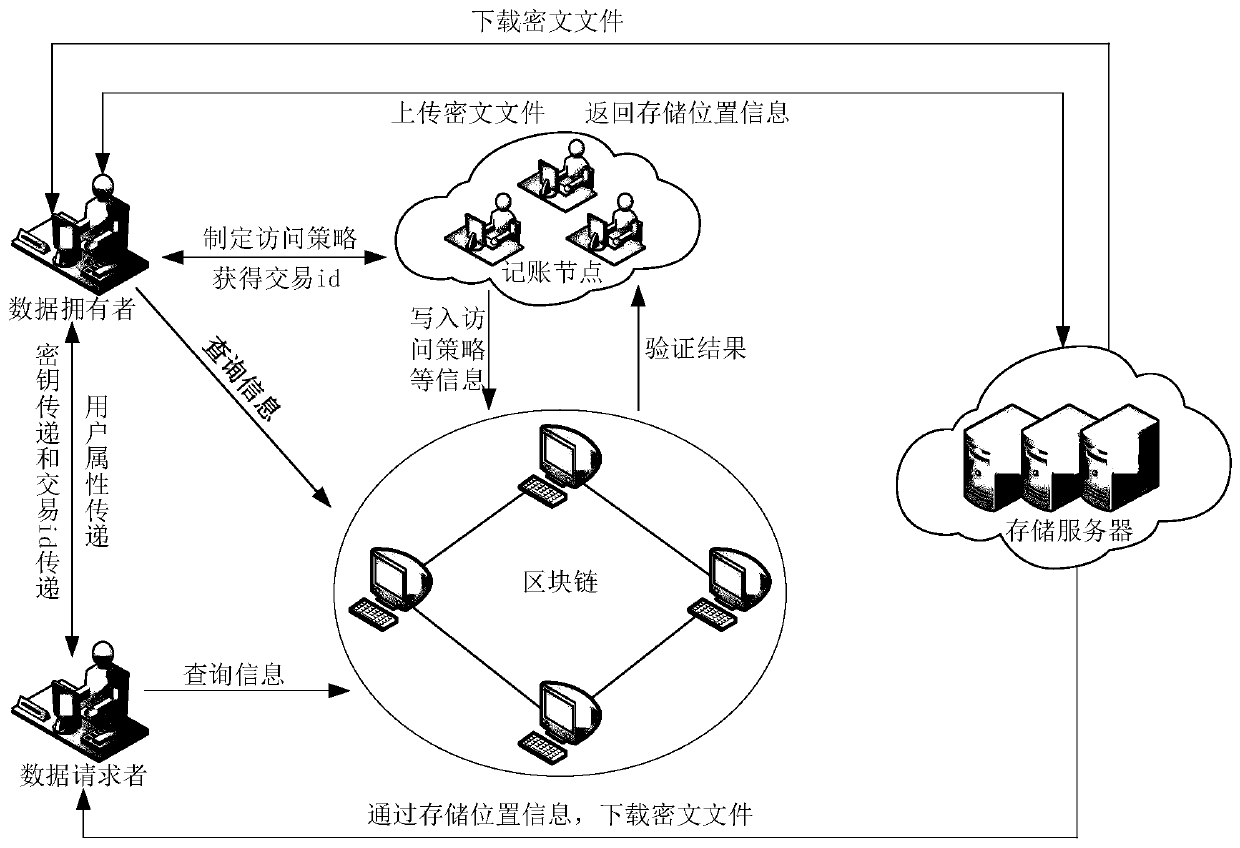
[0044] Such as figure 2 As shown, before the user joins the system, the system first performs an initialization. At this stage, the system verifies the identity attributes of the user, issues an identity certificate, ...
Embodiment 2
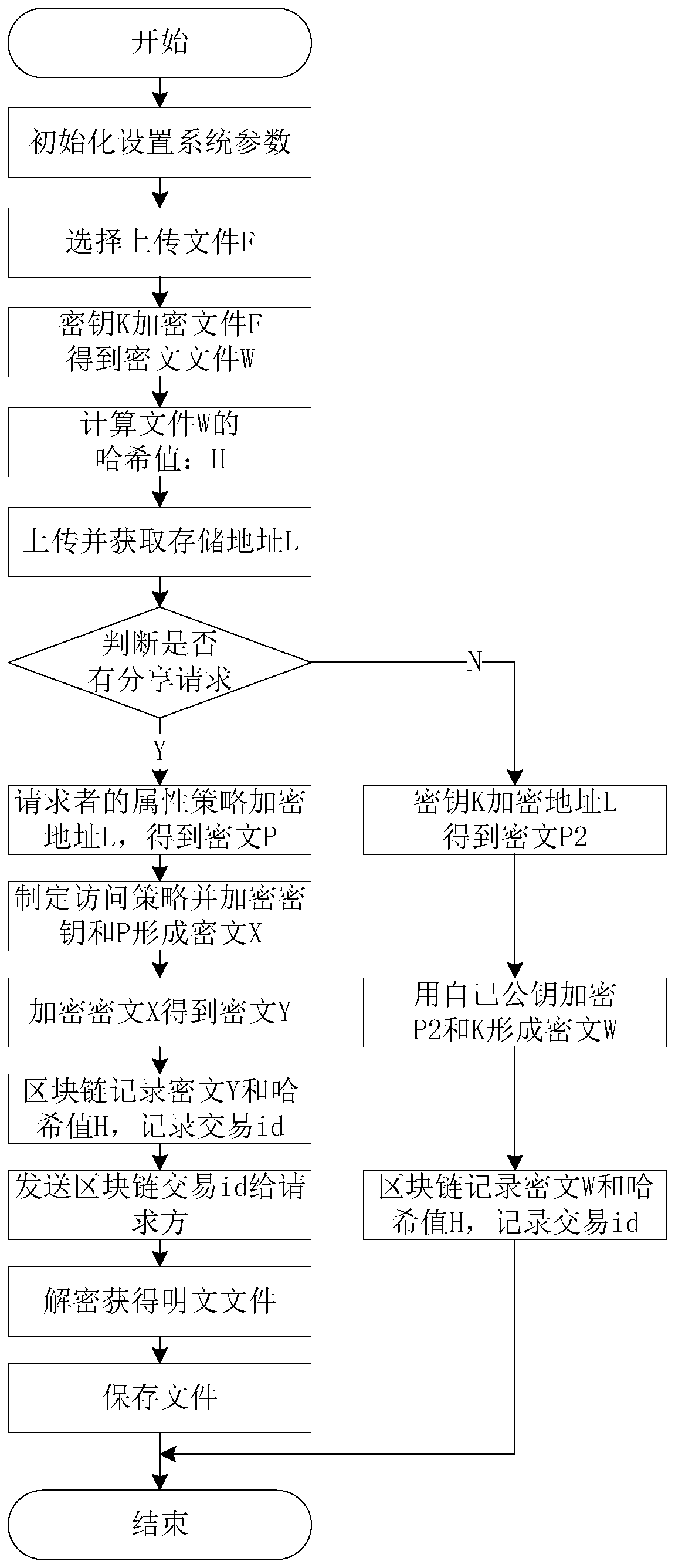
[0049] This embodiment provides a process for the data owner to share the data with the data requester, such as Figure 4 As shown, at this time, it is necessary to judge whether the number of people requesting sharing is greater than 1, or to determine whether the number of people is greater than this threshold according to a threshold n set by the system's computing power and other resources. If it is greater than this value, the system will automatically randomly select from the key space A key K2 uses symmetric encryption to encrypt the ciphertext X to obtain the ciphertext Y. At this time, the data owner stores the key K2 and combines the ciphertext Y with the previously calculated hash value of the uploaded ciphertext file. H is publicly stored in the blockchain account book together. After the consensus of the blockchain bookkeeping nodes, the returned transaction id is obtained, and the returned transaction id and K2 are distributed to the requester for data sharing. Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com