Security management method of virtual machine based on trust root
A security management and virtual machine technology, applied in the field of virtual machine security management based on the root of trust, can solve the problems of concurrent sharing of virtual computing domains, no description or report found, and no data collected.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
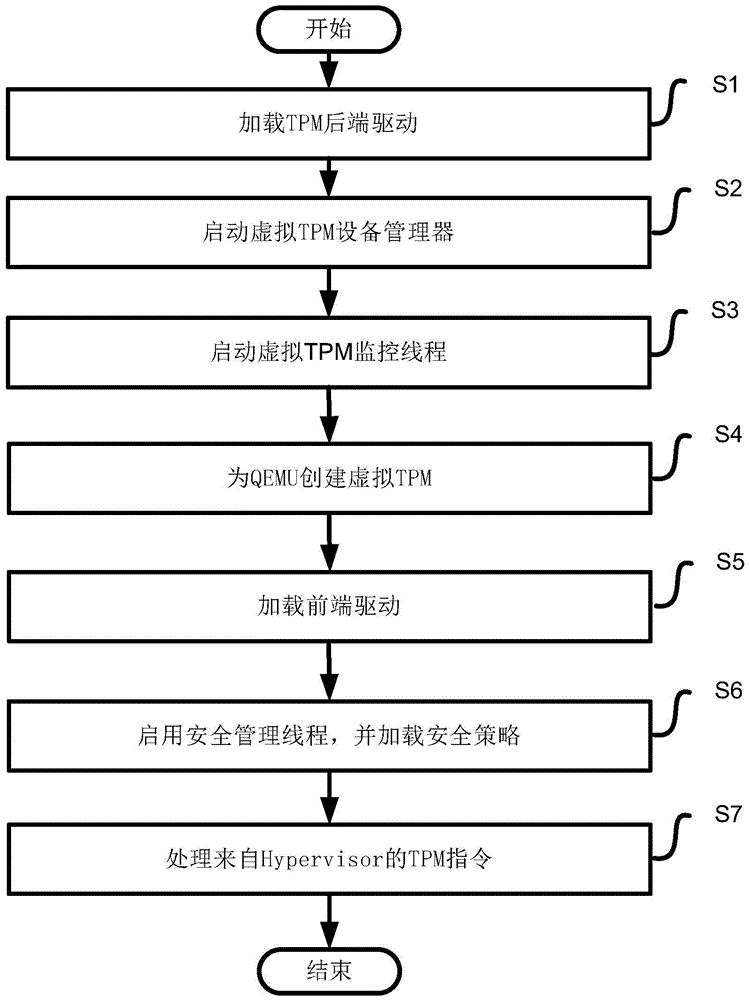
[0033] This embodiment provides a virtual machine security management method based on root of trust, including the following steps:
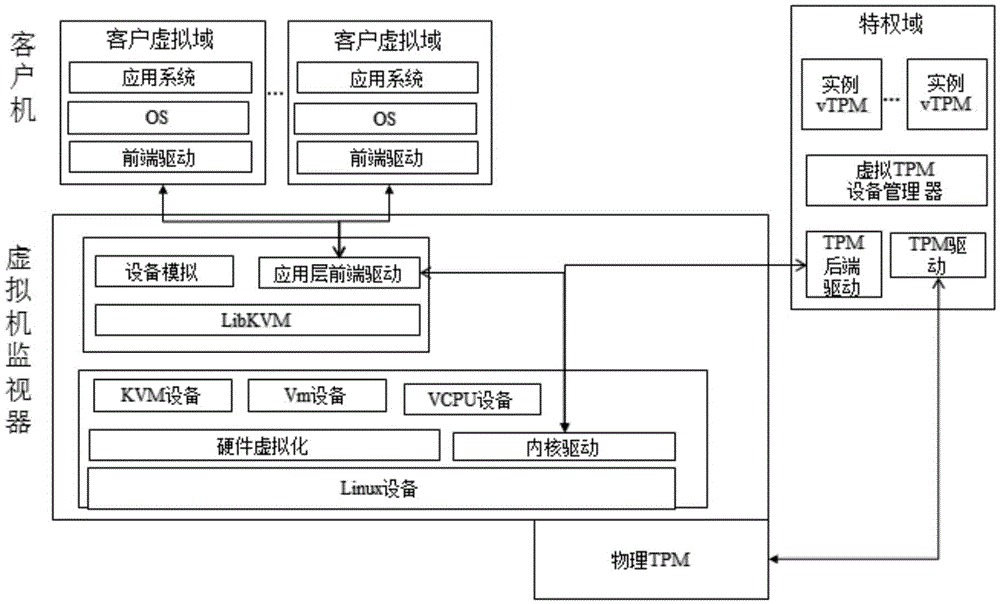
[0034] Step S1: Load the TPM back-end driver: load the TPM back-end driver in the privileged domain, and generate a simulated device vTPM (virtual TPM device); the virtual TPM device is mainly used for:
[0035] - The ability to interact with the physical TPM driver to realize the virtualization of the physical TPM;
[0036] - Receive instructions from the front-end TPM driver and hand them over to the simulated device vTPM for processing;
[0037] Step S2: Start the virtual TPM device manager: initialize the global configuration of the virtualization monitor of the virtual TPM device manager to store virtual TPM related information, and create a root virtual TPM based on the physical TPM, which has the highest authority TPM instance, denoted as Ring-0;
[0038] Step S3: start the monitoring thread of the virtual TPM device manager; the monito...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com