Resilient secret sharing cloud based architecture for data vault
a data vault and cloud technology, applied in the direction of digital transmission, key distribution for secure communication, multiple keys/algorithms, etc., can solve the problems of data security and reliability issues, weak methodology, and cloud computing also presents a number
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033]A portion of the disclosure of this patent document contains material which is subject to copyright protection. The copyright owner has no objection to the facsimile reproduction by anyone of the patent document or the patent disclosure, as it appears in the Patent and Trademark Office patent file or records, but otherwise reserves all copyright rights whatsoever.
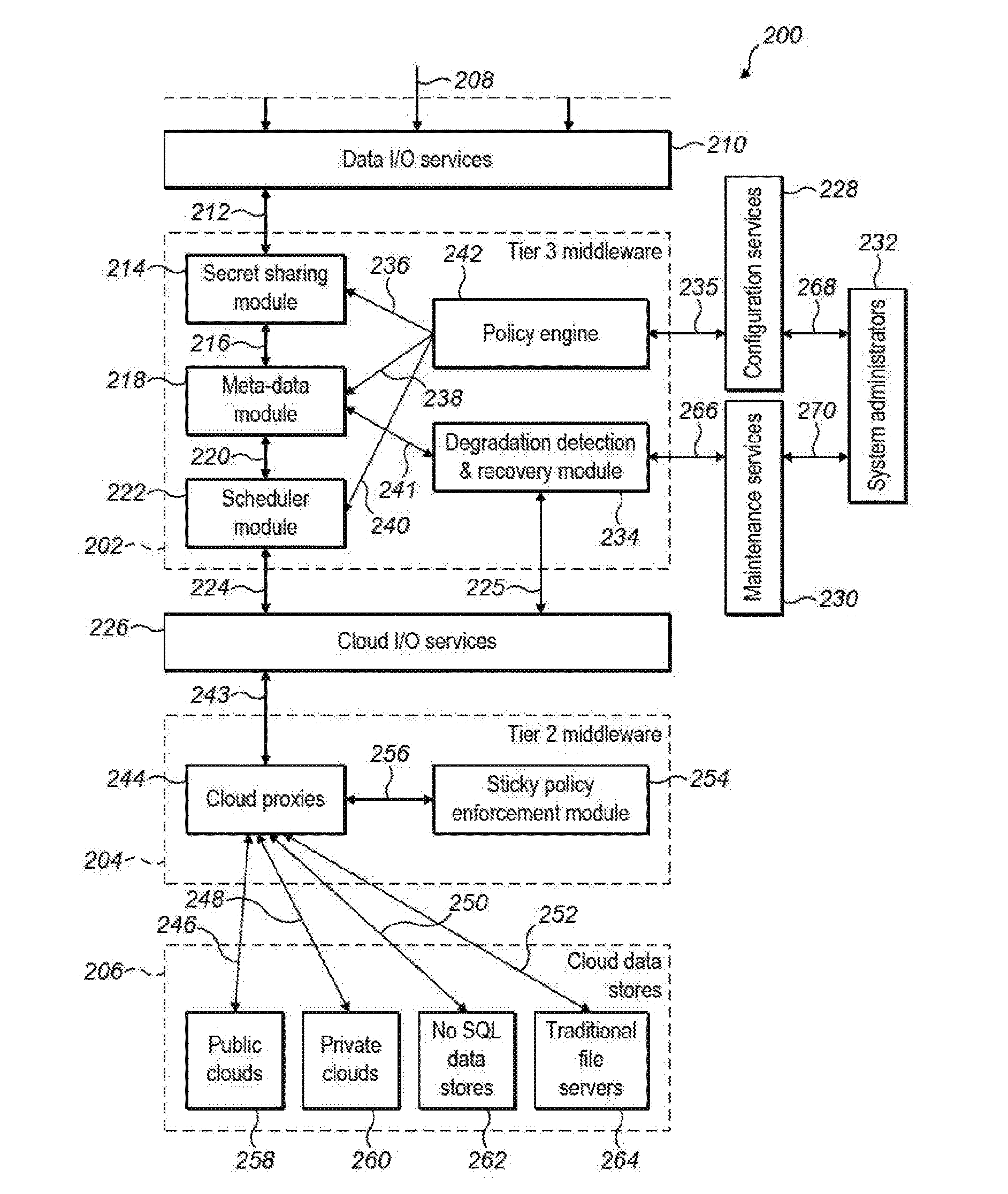
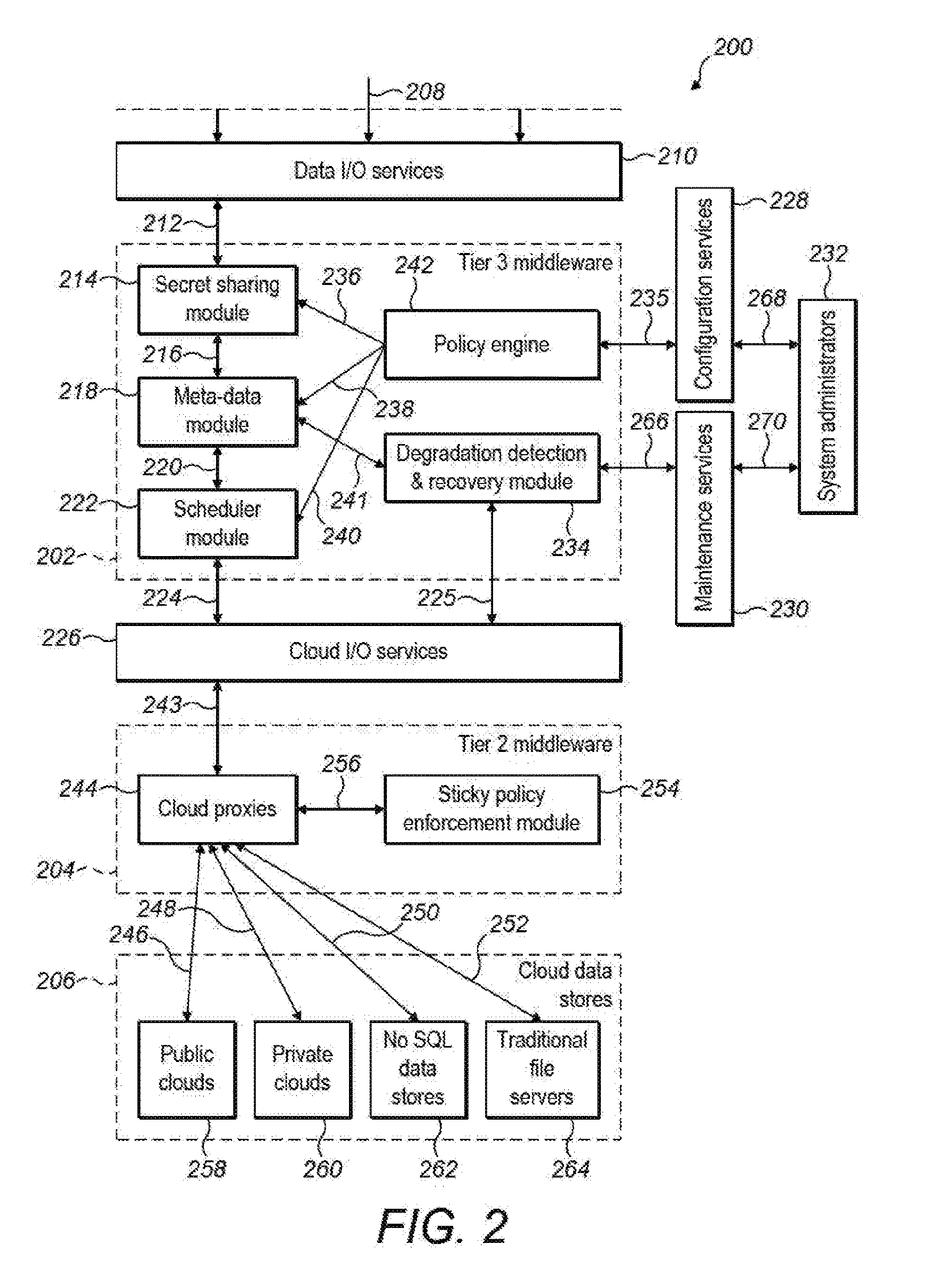
[0034]FIG. 1 shows an architecture which supports a secret sharing scheme in a multi-cloud environment 100 can be viewed as having an application platform 102 (having a secret sharing module that will be described), a main multi-cloud proxy server (with router) 104 and a metadata server 106. The metadata server 106 is illustrated as being connected between the application platform 102 and the main multi-cloud proxy server 104 illustrating that metadata can be associated with data passing between the application platform 102 and the main multi-cloud proxy server 104 in each direction.
[0035]The function of the applicati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com