Method for generating RTL hardware Trojan test vectors
A technology of test vectors and hardware Trojan horses, applied in the direction of measuring electricity, measuring devices, measuring electrical variables, etc., can solve problems such as difficulty in achieving consistency, achieve the effects of improving overall efficiency, speeding up speed and effectiveness, and improving branch coverage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0065] Select RS232-T400 on Trust-Hub as the analysis object, which contains three verilog files: uart.v, u_xmit.v, u_rec.v. The three verilog files are shown below. The Trojan trigger in the top-level file uart.v compares the sent and received data, and when both are equal to 8’h4c, the Trojan is activated. The payload part of the Trojan will replace 4 bits in the received data.
[0066] 1.uart.v program source code:
[0067]
[0068]
[0069]
[0070] 2.u_xmit.v program source code:
[0071]
[0072]
[0073]
[0074] 3.u_rec.v program source code:
[0075]
[0076]
[0077]
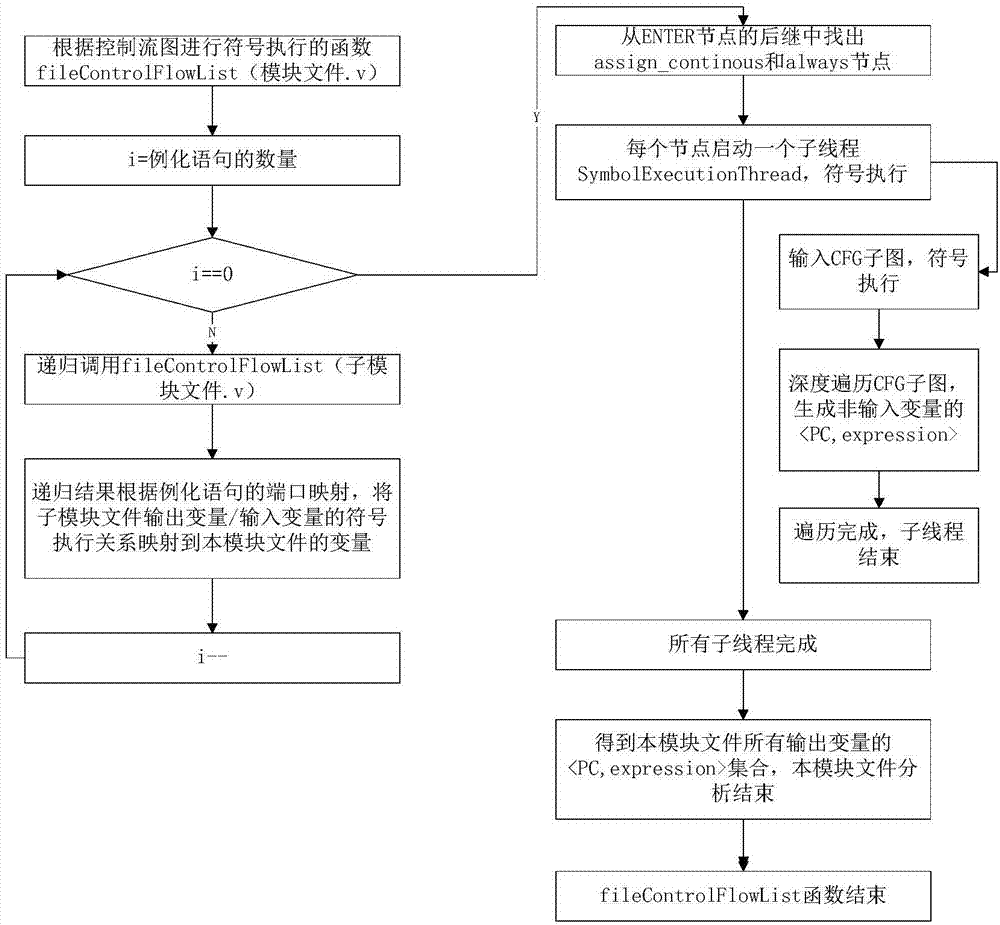
[0078] This embodiment takes uart.v as an example, which contains 2 instantiated statements, and u_xmit.v and u_rec.v will be analyzed in sequence.
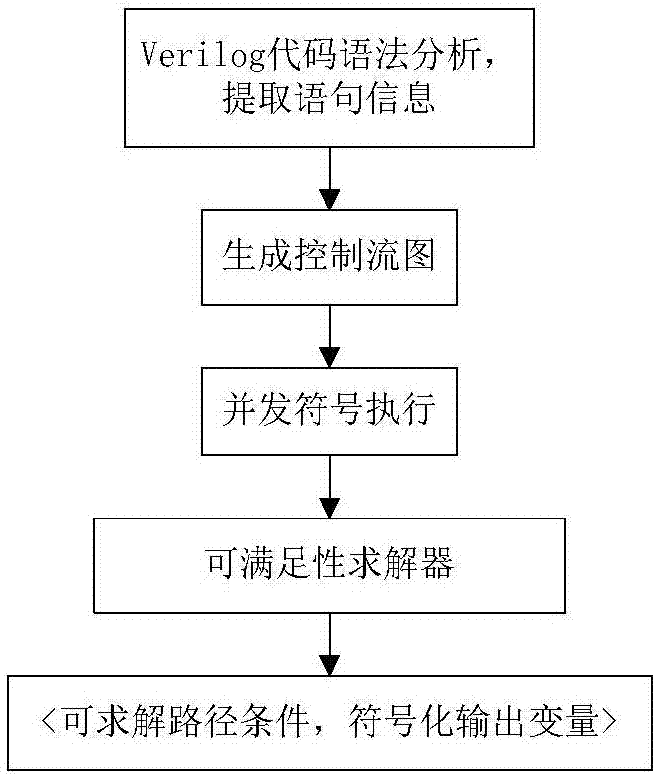
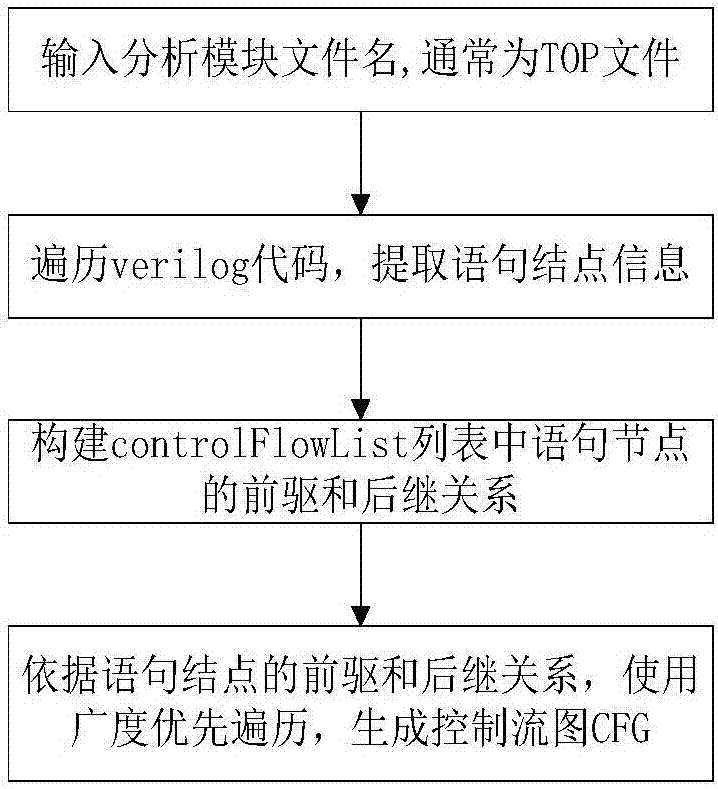
[0079] Step 1: Generation of control flow graph
[0080] 1) Deeply traverse the syntax parse tree (parseTree) of the uart.v file to obtain the information of the statement nodes. For example: the first node of the entire fil...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com