File encryption method combined with access deflection
A file encryption and file technology, which is applied in the field of file encryption combined with access deflection, can solve the problem of complex policy configuration, achieve the effect of simple policy configuration and ensure information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
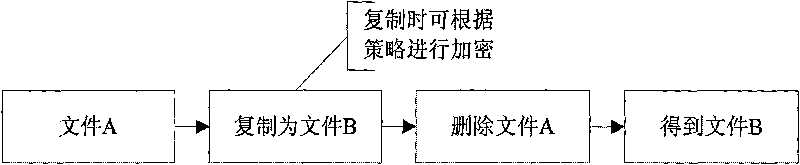
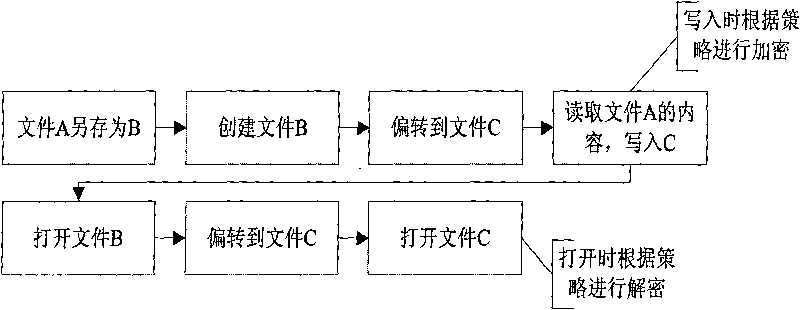
[0035] The access deflection module described in the present invention is a file microfilter driver under Windows, which needs to be used in combination with a transparent encryption module. The system framework is as follows: Figure 5 shown.
[0036] The access deflection module intercepts and processes various file operations at the bottom layer, mainly including the following file operations: open and create (IRP_MJ_CREATE), directory query (IRP_MJ_DIRECTORY_CONTROL), and delete and rename (IRP_MJ_SET_INFORMATION).
[0037] 1 Open and create processing (IRP_MJ_CREATE)
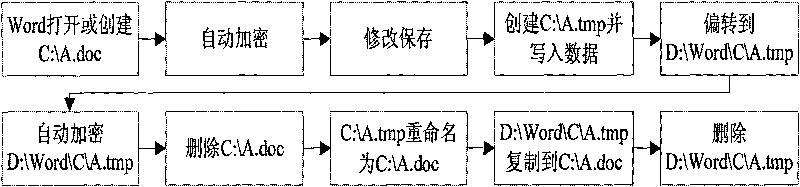
[0038] In the process of file opening and creation, deflection processing is mainly performed, and the logic is relatively simple, such as Image 6 shown. First obtain the file name and judge whether deflection is needed according to the file name; for the file that needs to be deflected, further judge whether to perform a modification operation; if it is a modification operation, perform copying or direc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com