Patents
Literature
54 results about "Code clone" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
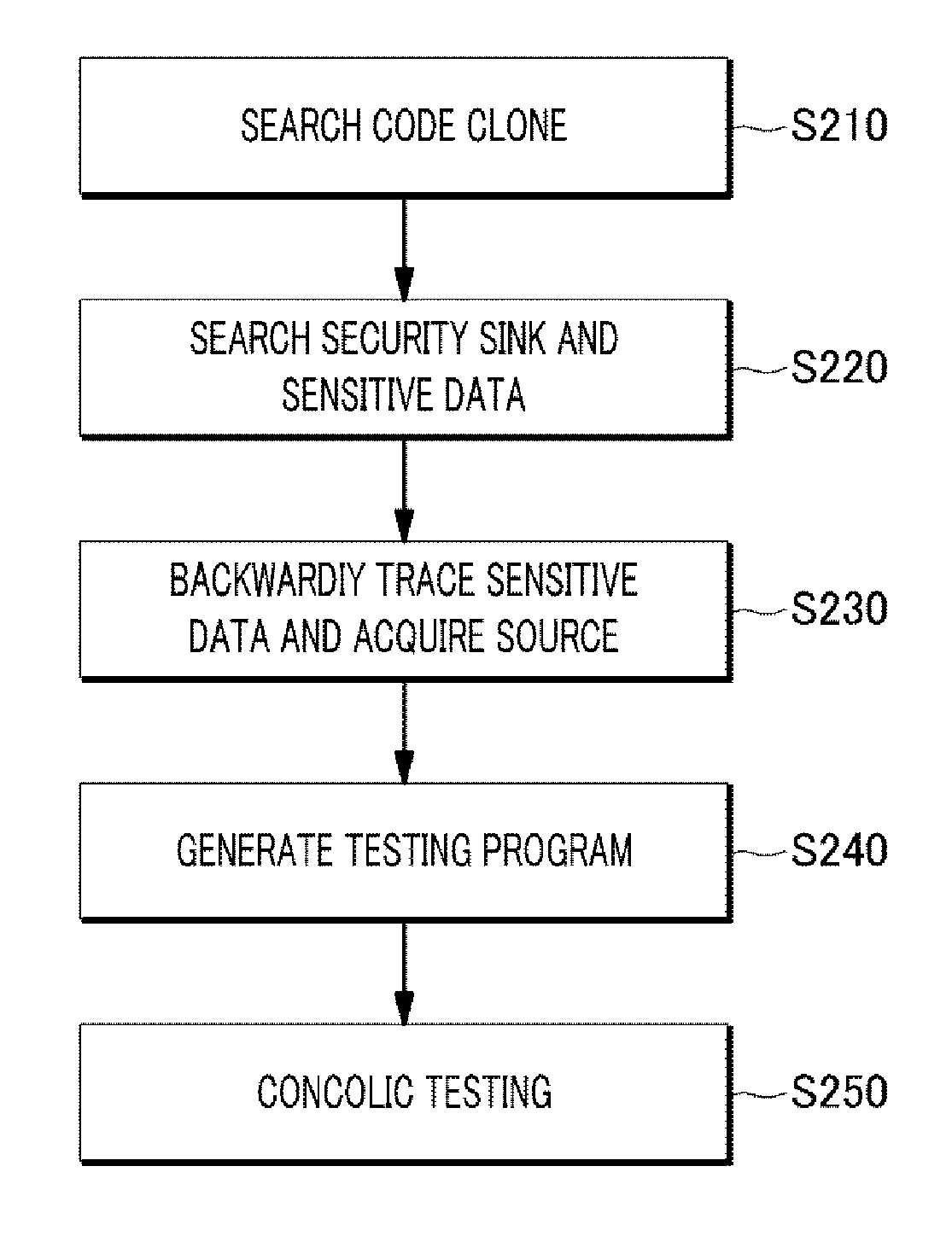
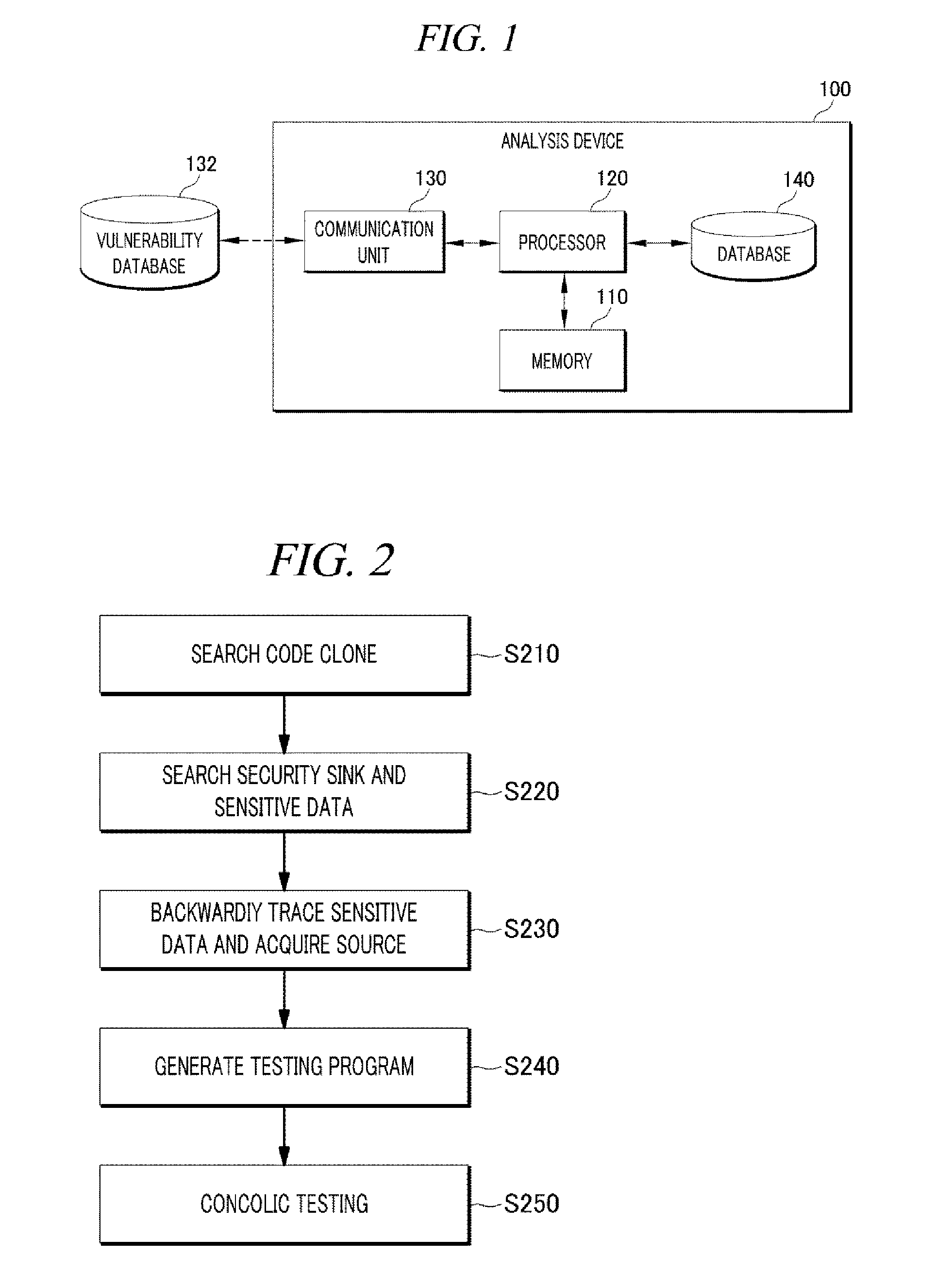
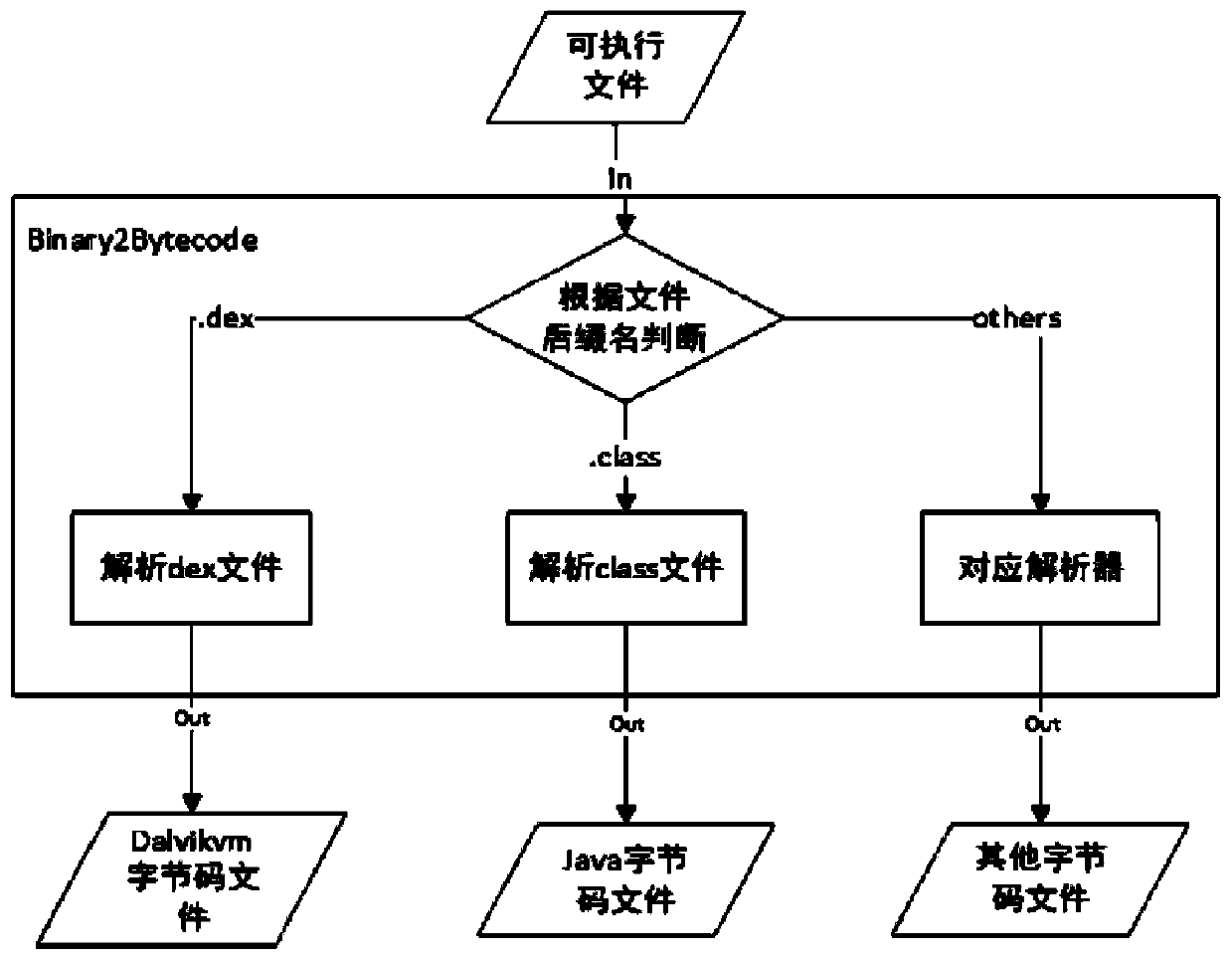
Software vulnerability analysis method and device
ActiveUS20160188885A1Improve efficiencyAchieve rapidityMemory loss protectionError detection/correctionConcolic testingUser input
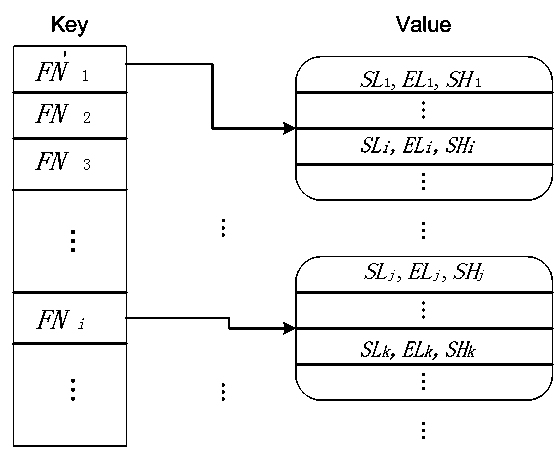
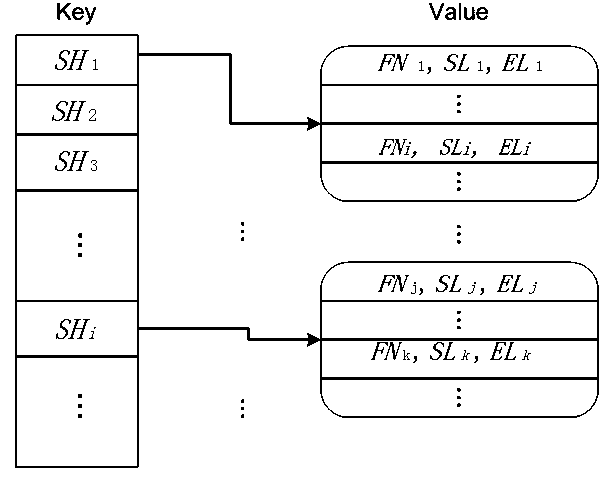
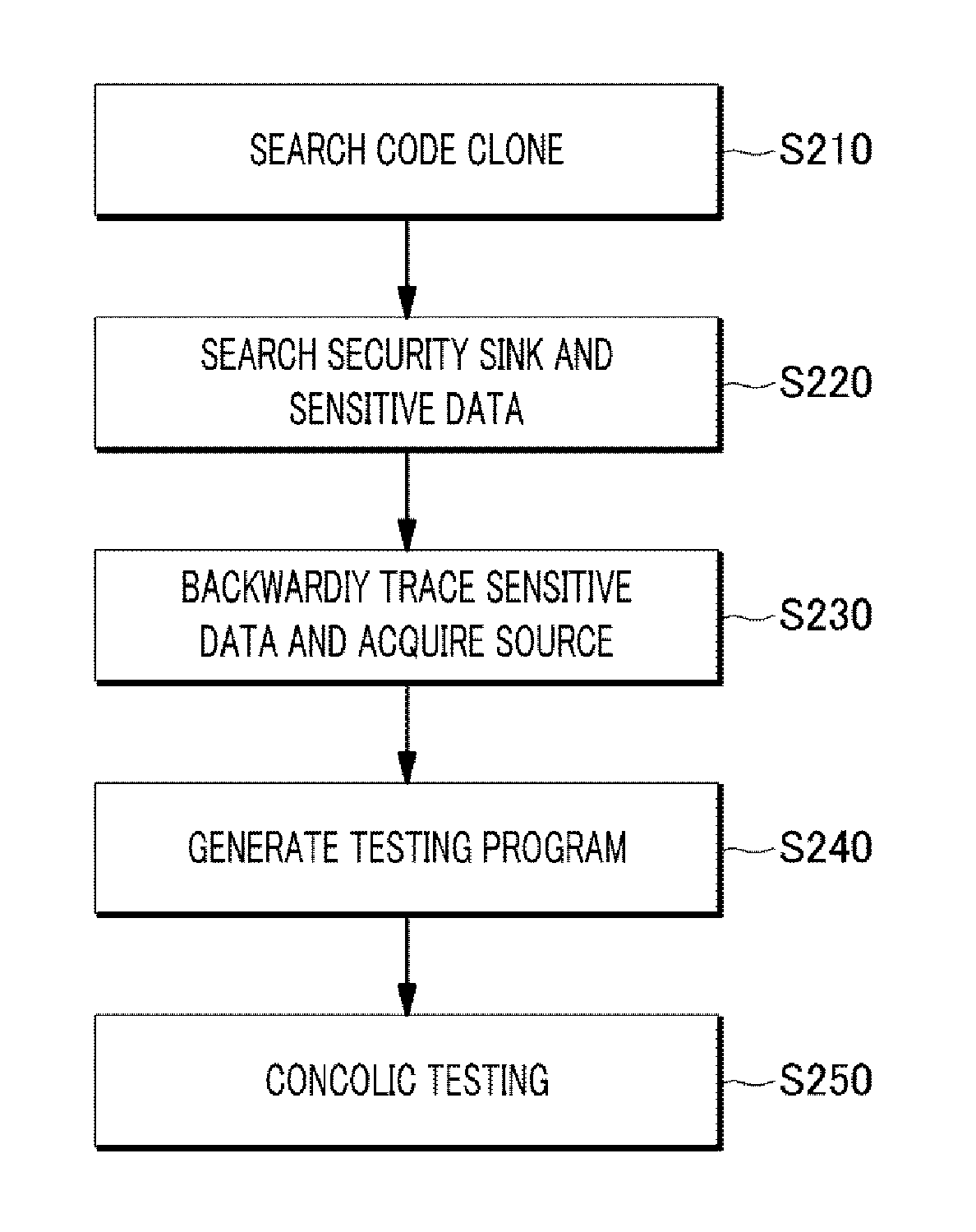
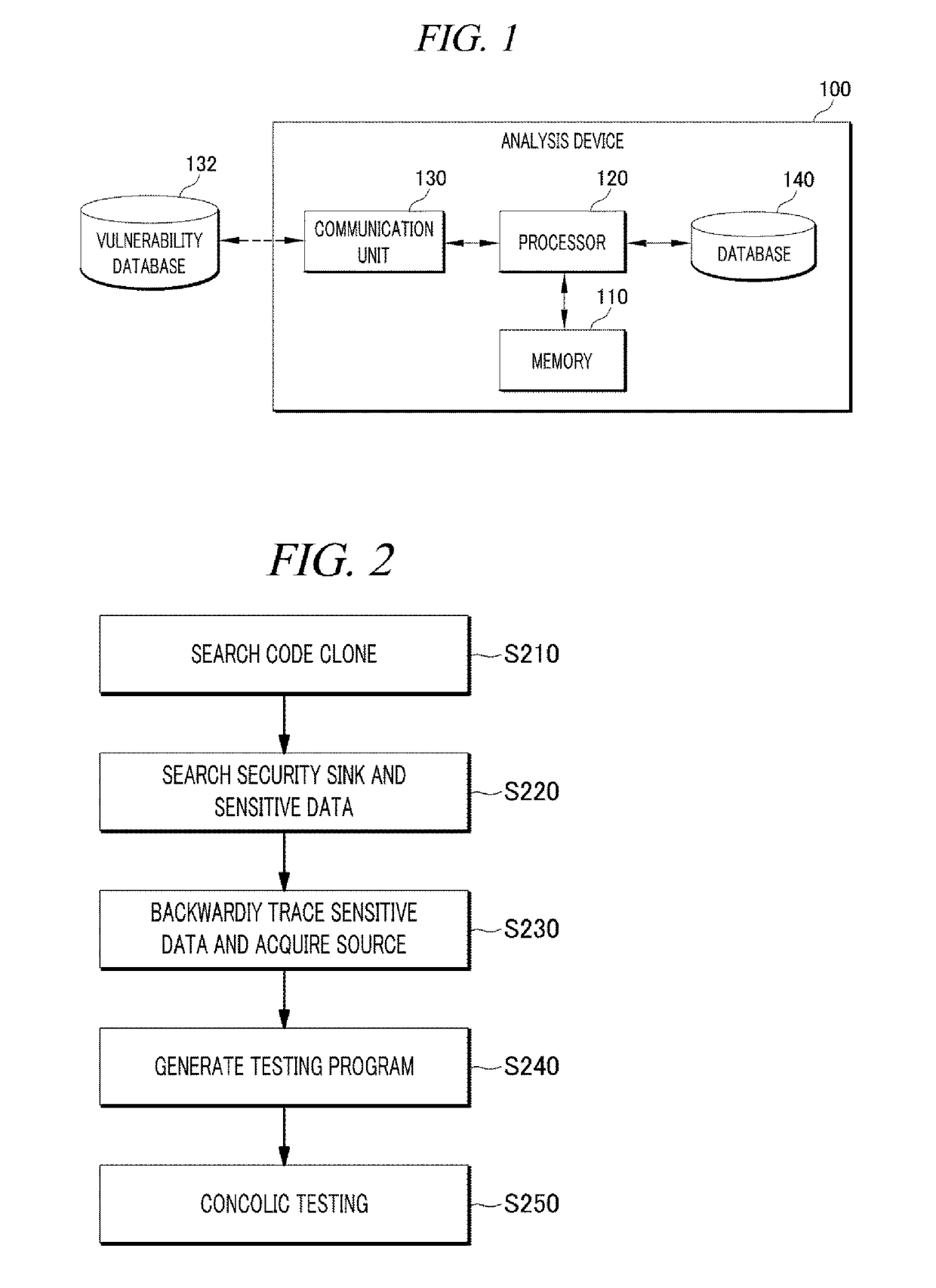
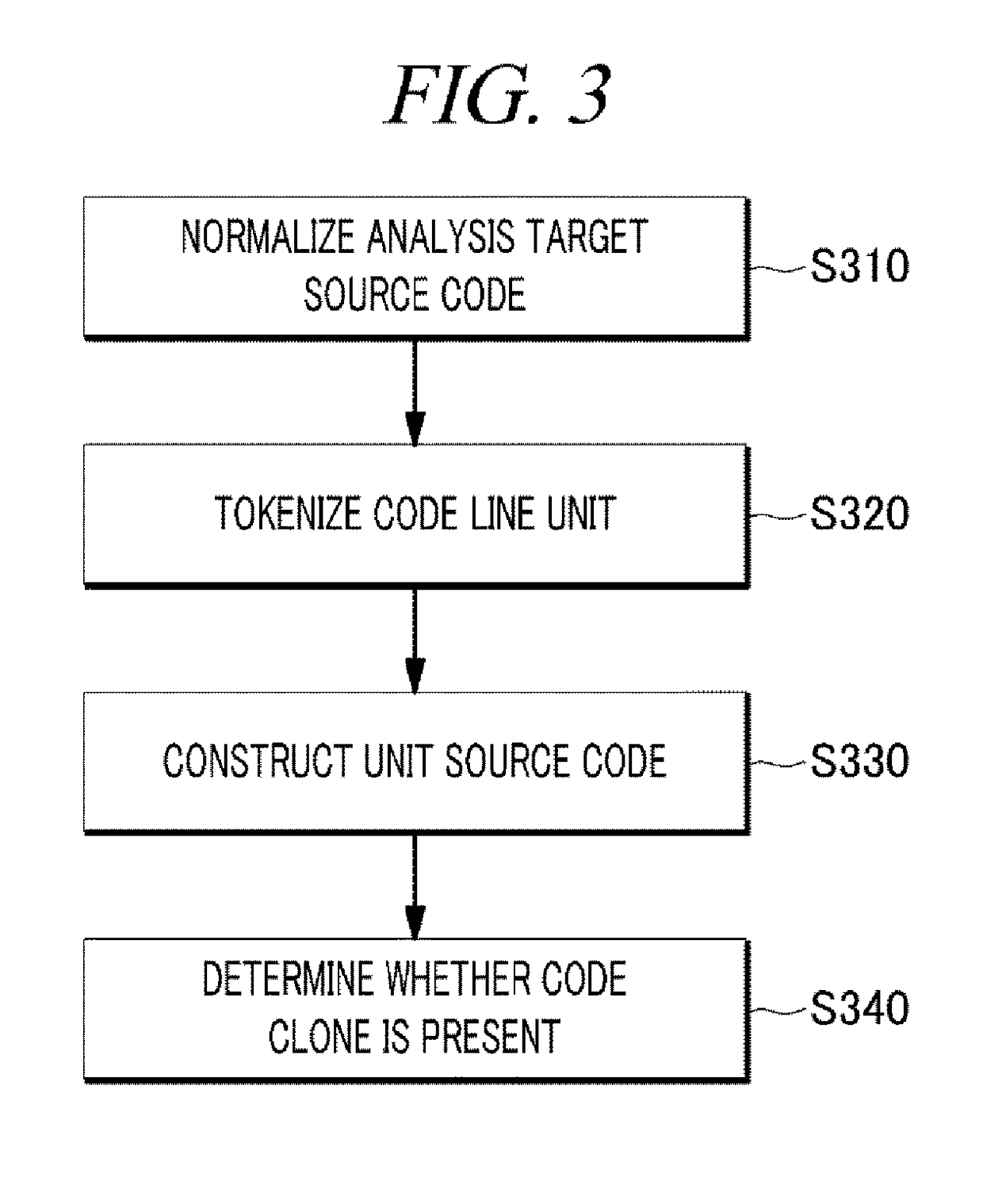
The present disclosure includes: searching a code clone corresponding to a used source code from any analysis target source code; detecting a security sink and sensitive data of the security sink on the basis of patch information in the searched code clone; acquiring a source code which is from the user input point the a security sink by backwardly tracing the sensitive data detected in the analysis target source code; and verifying whether the searched code clone is a vulnerability in the analysis target source code by performing a concolic testing on the basis of a path from the input point to the security sink.
Owner:KOREA UNIV RES & BUSINESS FOUND
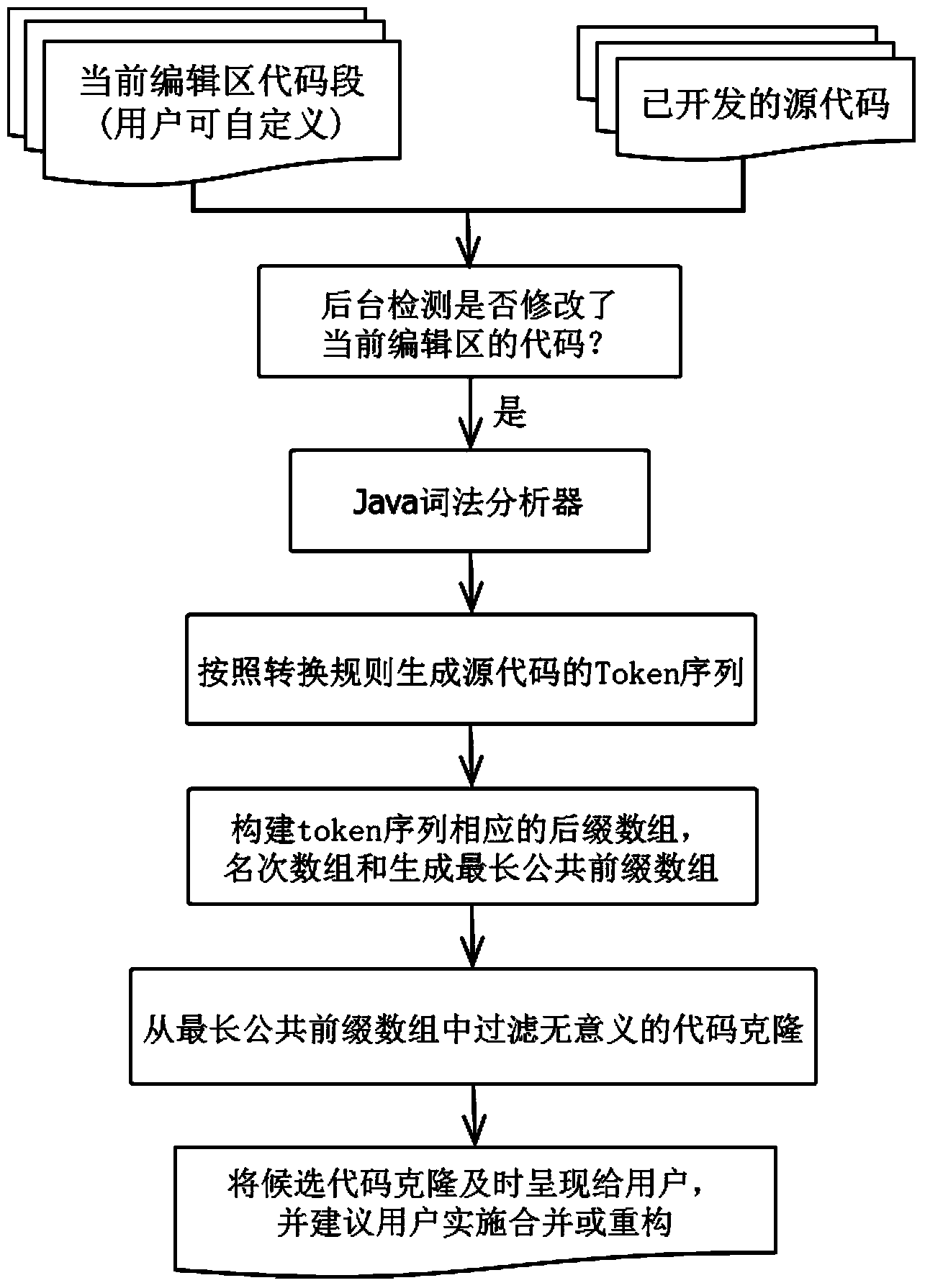
Software reusing method based on code clone automatic detection and timely prompting
InactiveCN104077147AEasy to detectRealize timely reminderSpecific program execution arrangementsArray data structureSource code file
The invention discloses a software reusing method based on code clone automatic detection and timely prompting. The method includes the steps that firstly, a Java lexical analyzer is generated through a lexical generator; secondly, if a background monitor monitors that a code in the current editing area is modified, the code in the current editing area and a developed code are input into the Java lexical generator, token values corresponding to source code files are generated according to a conversion rule, tokens are connected to form a Token sequence, and the Token sequence is stored in a one-dimensional array; thirdly, according to the multiplication algorithm or a DC3 algorithm, a suffix array and a rank array are constructed, and the longest public prefix array is generated; fourthly, meaningless code fragments are filtered out from the longest public prefix array, and if code clones still exist, a user is prompted to reuse or reconstruct the code clones. By means of the method, the user can conduct development while the background monitor detects the source code.
Owner:SOUTHEAST UNIV
Loophole fingerprint based vulnerability code clone detecting method and device
ActiveCN107688748AEfficient detectionEffective multiplexingPlatform integrity maintainanceCoding blockHash function
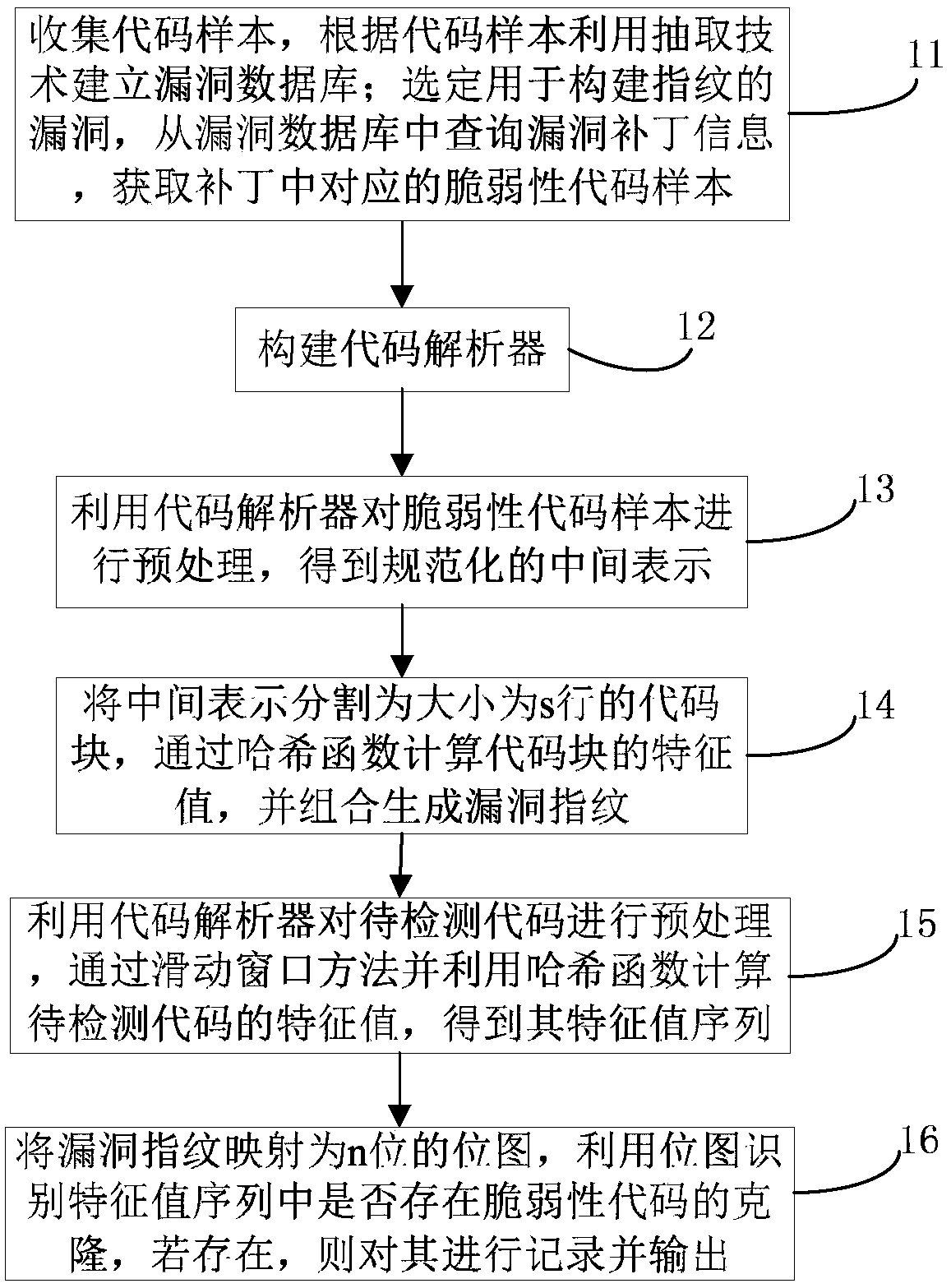
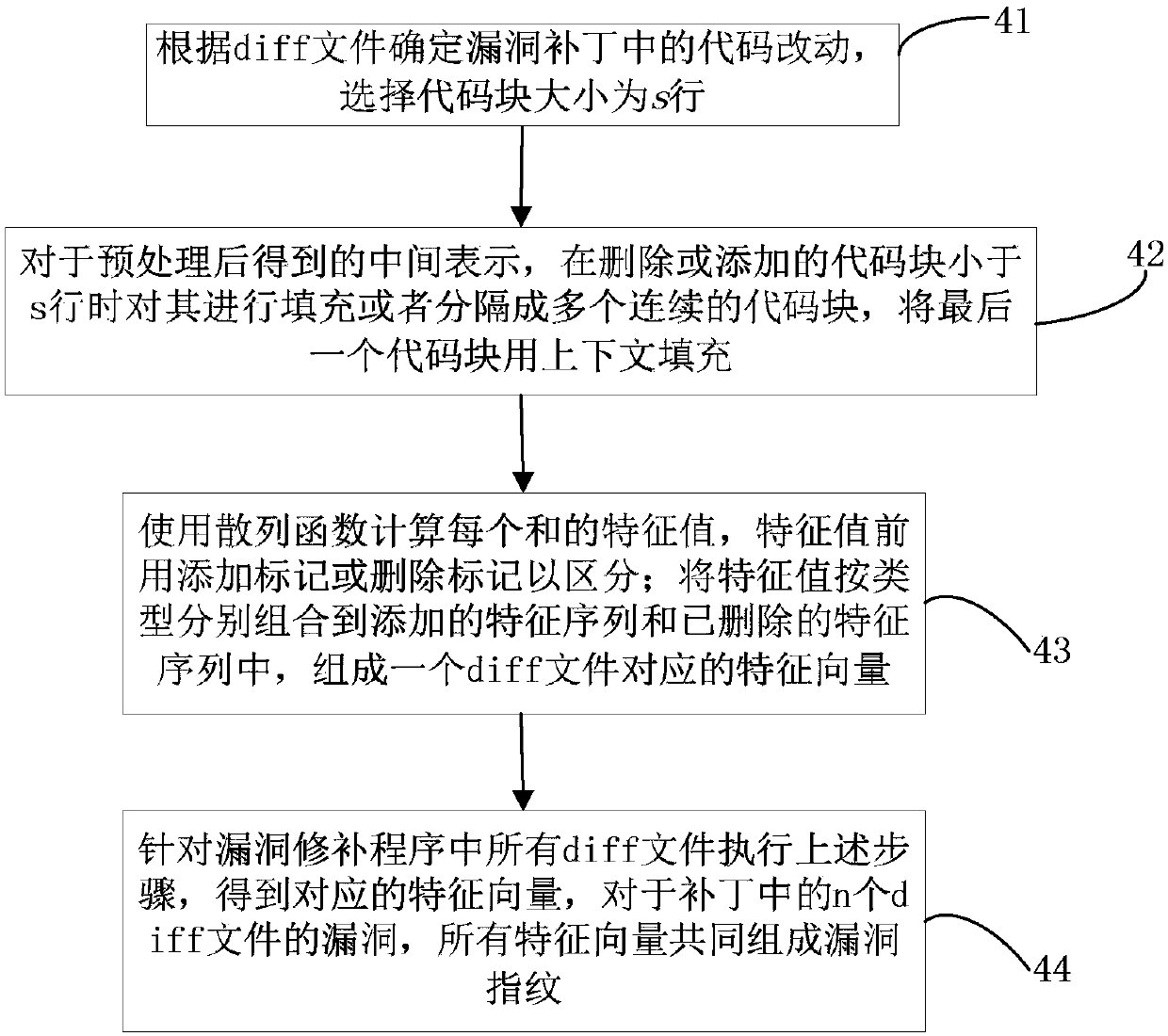
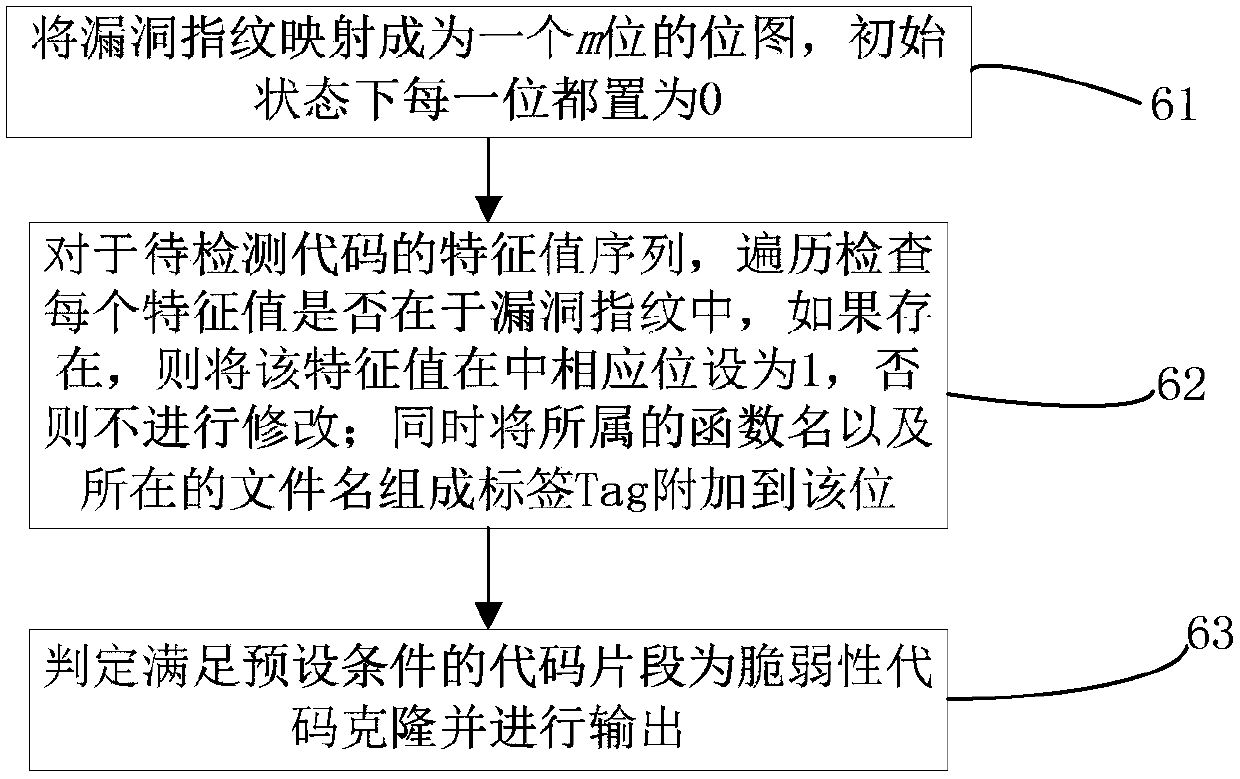
The invention relates to a loophole fingerprint based vulnerability code clone detecting method and device. The method includes steps of collecting a code sample, and building a loophole database; selecting the loophole and searching the loophole patch information, and acquiring a vulnerability code sample; structuring a code analyzer; pretreating the vulnerability code sample by means of the codeanalyzer to obtain a standard middle expression; dividing the middle expression to be a code block with size of s line; calculating a characteristic value of the code block through a hash function, and combining to generate the loophole fingerprint; pretreating the code to be detected by means of the code analyzer and acquiring a characteristic value sequence of the code to be detected; mapping the loophole fingerprint to n bit of bit drawing; identifying if the characteristic value sequence is existed with vulnerability code clone by means of the bit drawing and outputting it. The method anddevice can effectively deal with the common code modifying method in the code cloning, well balance the relationship between the detecting efficiency and the detecting accuracy, and effectively detect the large-scale objects while keeping good accuracy.
Owner:THE PLA INFORMATION ENG UNIV
Code clone detection method
ActiveCN104407872AImprove anti-aliasingImprove accuracySpecific program execution arrangementsApplication programming interfaceApplication software
The invention discloses a code clone detection method. The code clone detection method comprises respectively extracting respective invoking API (Application Programming Interface) sets of two groups of to-be-detected program codes; determining an invoking frequency of every API in every group of API set of the program codes; for every group of program codes k, generating a n-dimensional marking vector of the group of program codes according to the invoking frequency of the corresponding API, wherein the dimension values vk and i of the n-dimension marking vector is corresponding to the APIs one to one, a set N is a union set of the API sets of the two groups of program codes, the vk and i are obtained according to the invoking frequency pk and i of the APIi which is corresponding to the k group of program code; calculating the similarity of the two groups of program codes according to the n-dimension marking vector of every group of program codes; determining whether two groups of program codes have a clone relationship or not according to the similarity and the preset similar threshold value. The code clone detection method can improve the detection mix resistance and is high in accuracy and easy to achieve.
Owner:BEIJING UNIV OF POSTS & TELECOMM
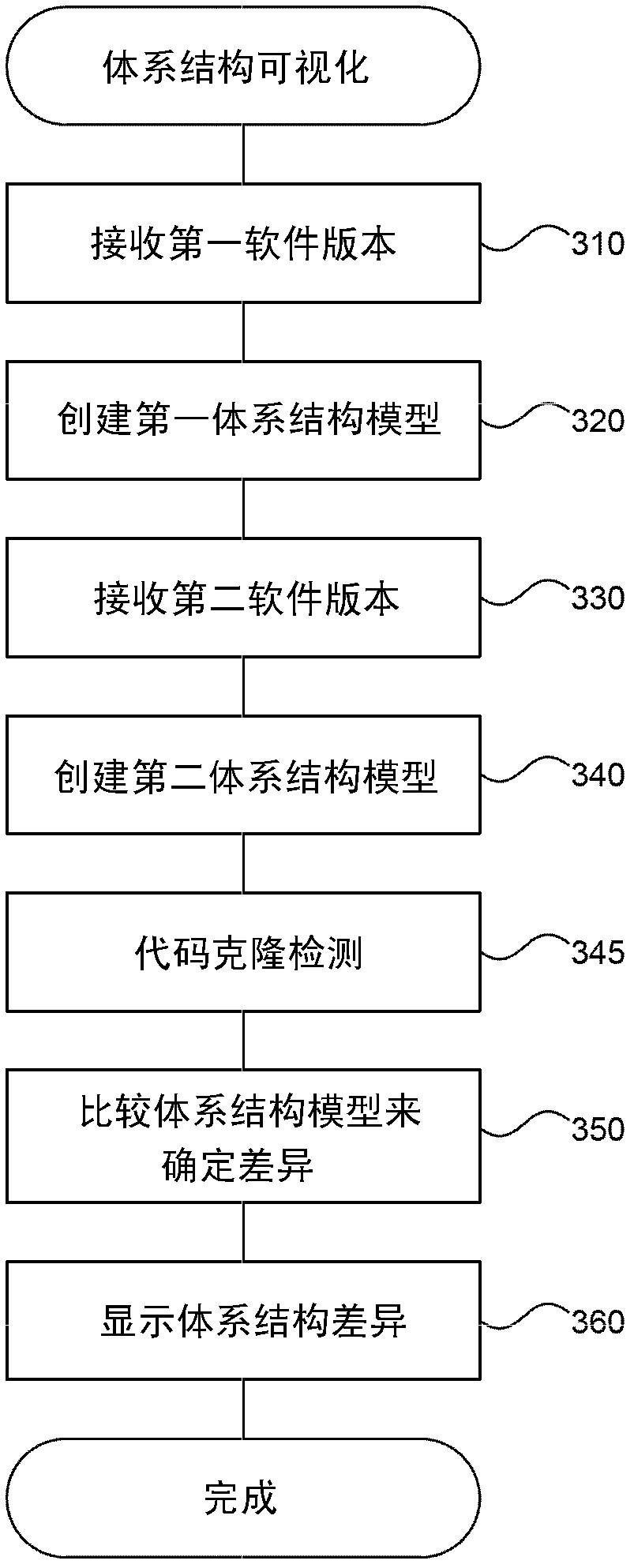
Code clone notification and architectural change visualization
InactiveCN102681835ASoftware testing/debuggingSoftware reuseSoftware development processTemporal change
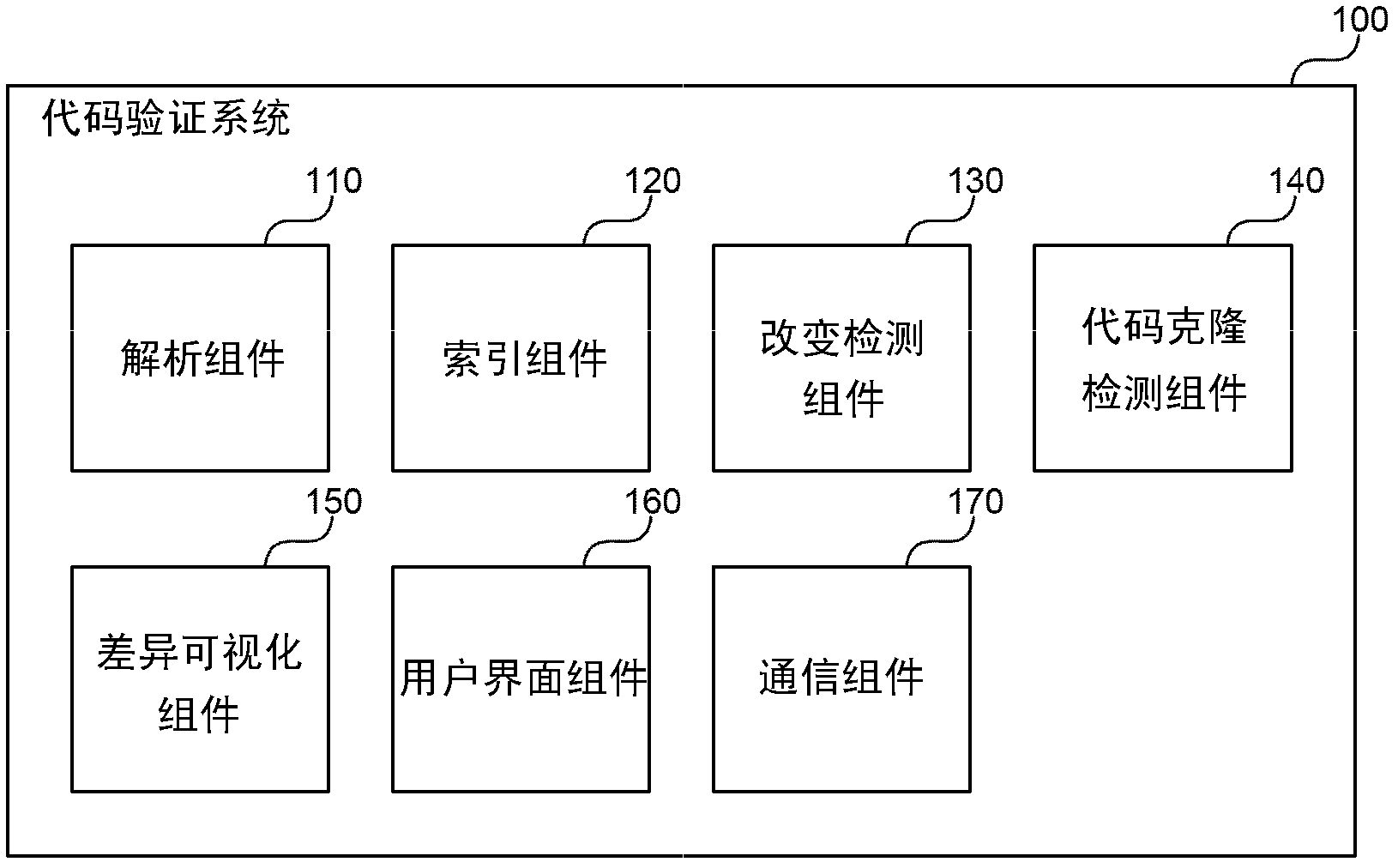
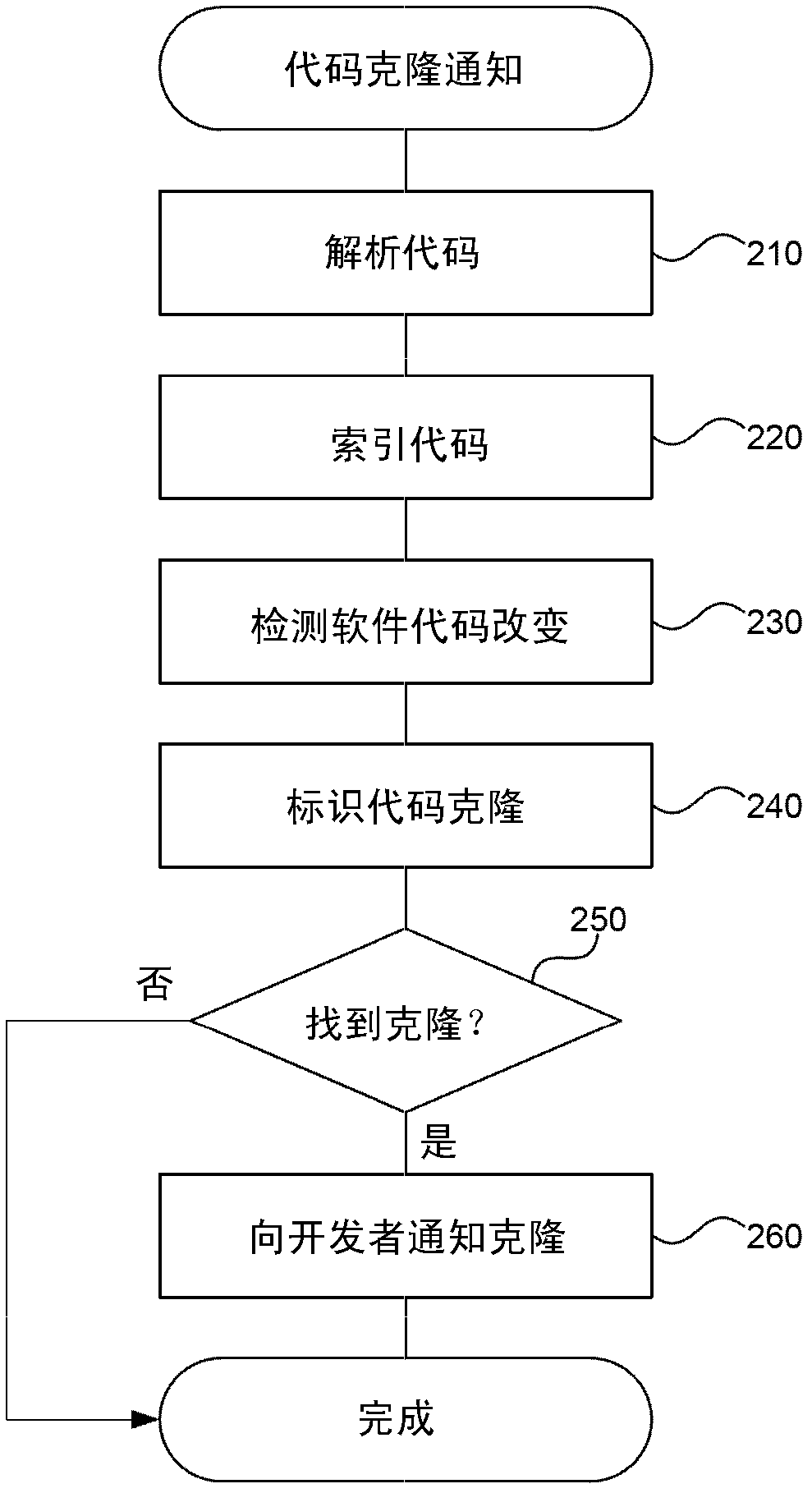
The invention relates to code clone notification and architectural change visualization. A code verification system is described herein that provides augmented code review with code clone analysis and visualization to help software developers automatically identify similar instances of the same code and to visualize differences in versions of software code over time. The system uses code clone search technology to identify code clones and to present the user with information about similar code as the developer makes changes. The system may provide automated notification to the developer or to other teams as changes are made to code segments with one or more related clones. The code verification system also helps the developer to understand architectural evolution of a body of software code. The code verification system provides an analysis component for determining architectural differences based on the code clone detection result between the two versions of the software code base. The code verification system also provides a user interface component for displaying identified differences to developers and others involved with the software development process in intuitive and useful ways.
Owner:MICROSOFT TECH LICENSING LLC
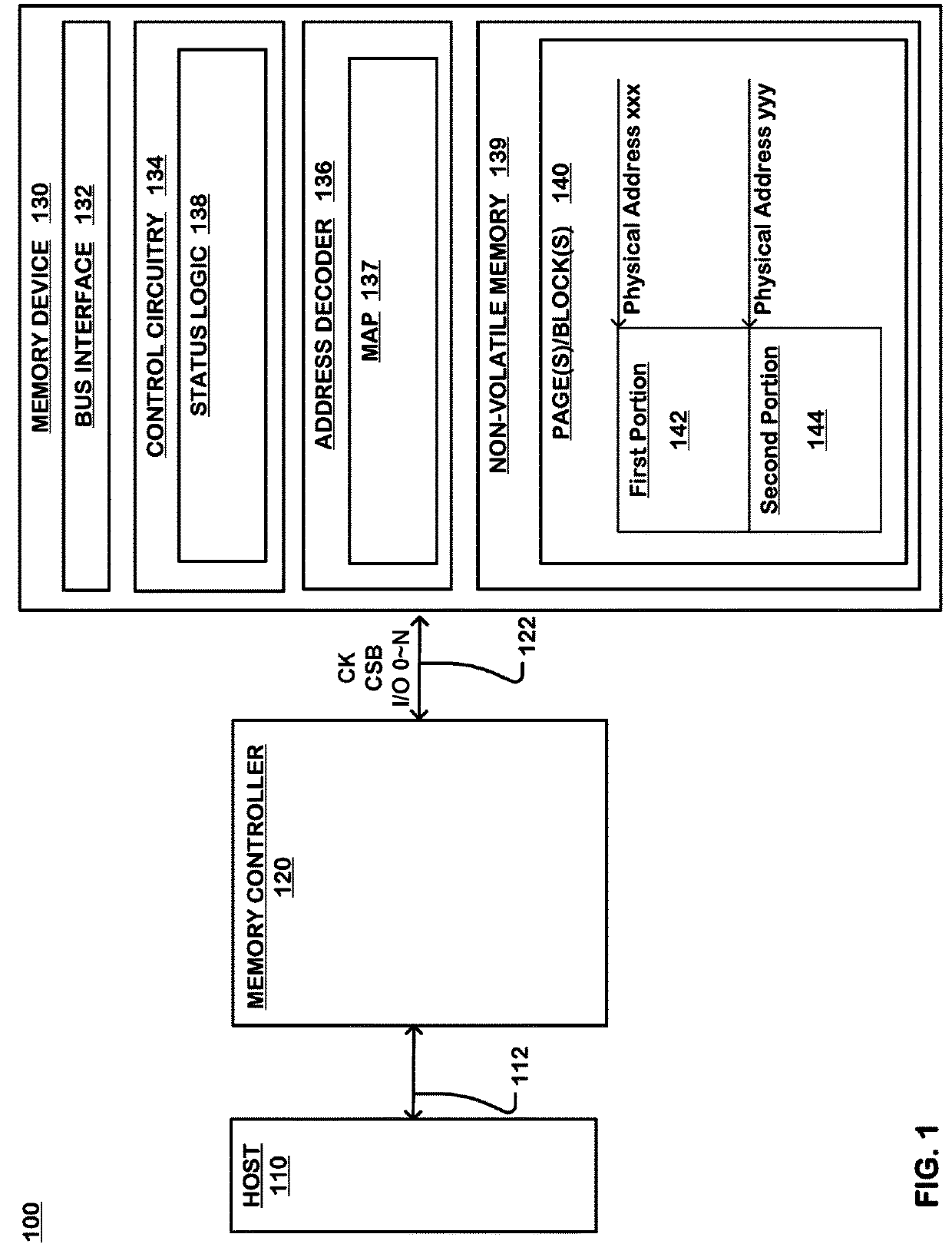
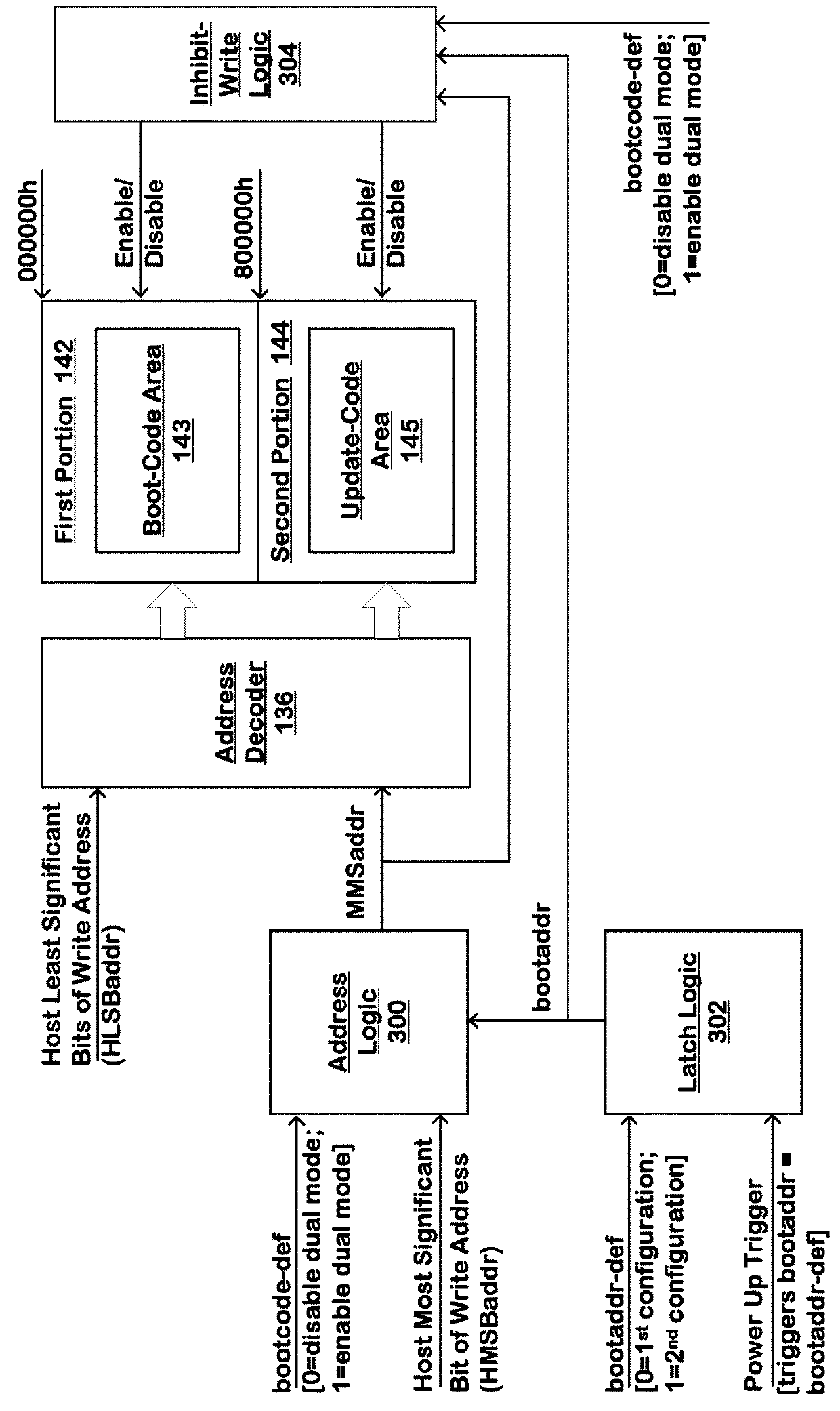
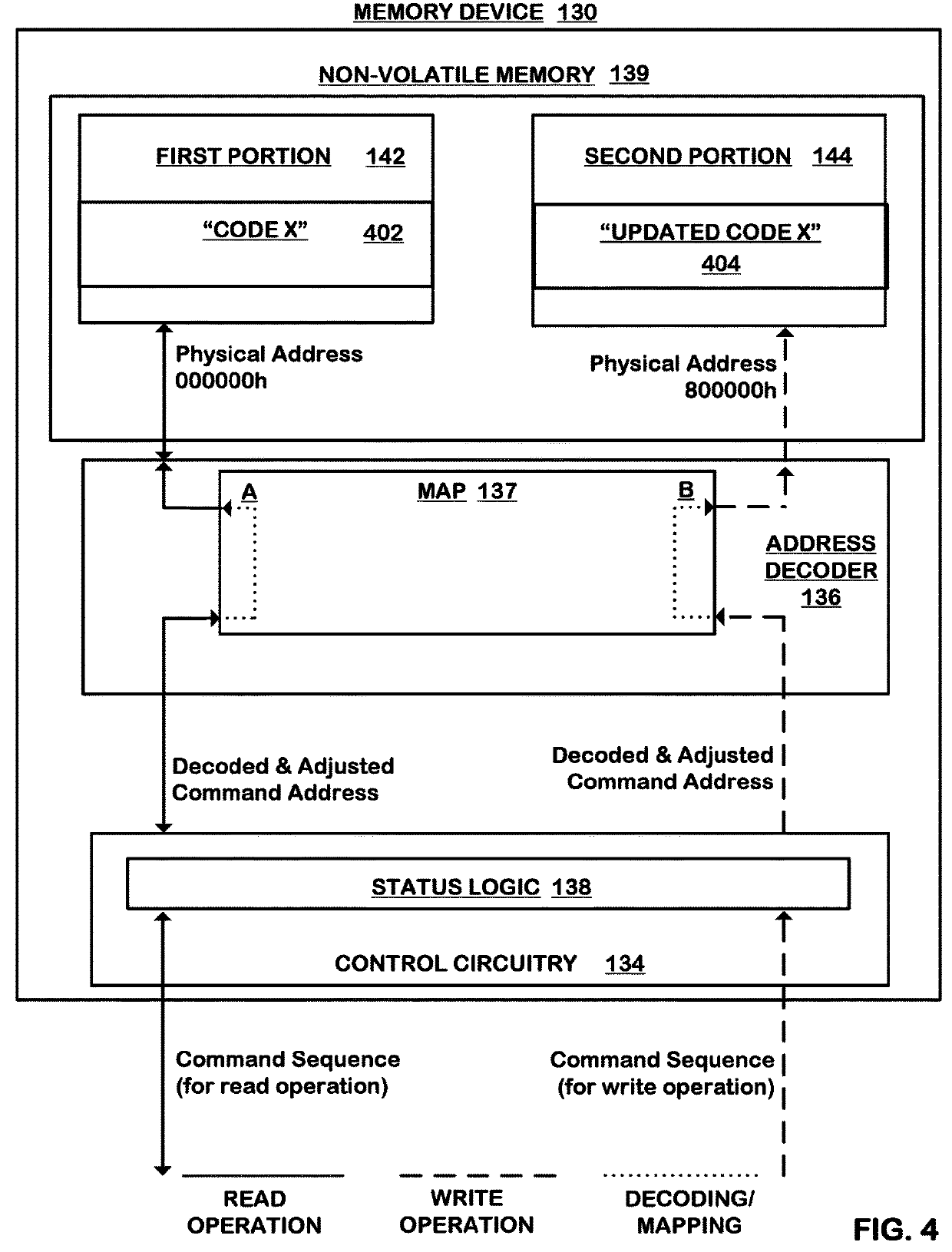
System boot code clone
ActiveUS20190212999A1Easy to produceInput/output to record carriersSoftware engineeringAddress decoderPhysical address
A memory device includes a non-volatile memory configured with a block including first and second portions and an address decoder mapping received command addresses to physical addresses of the non-volatile memory. The memory device includes control circuitry maintaining a current status of the first portion and the second portion and implementing an update operation, including responsive to receiving a write command sequence to the block, causing the address decoder to (i) map the write command address to one of the first portion and the second portion, selected in response to the current status and (ii) update the selected one of the first portion and the second portion with the updated information, and upon completion of the updating, changing the current status to indicate that the selected one of the first and second portion is the current area.
Owner:MACRONIX INT CO LTD
Binary vulnerability code cloning detection method and system
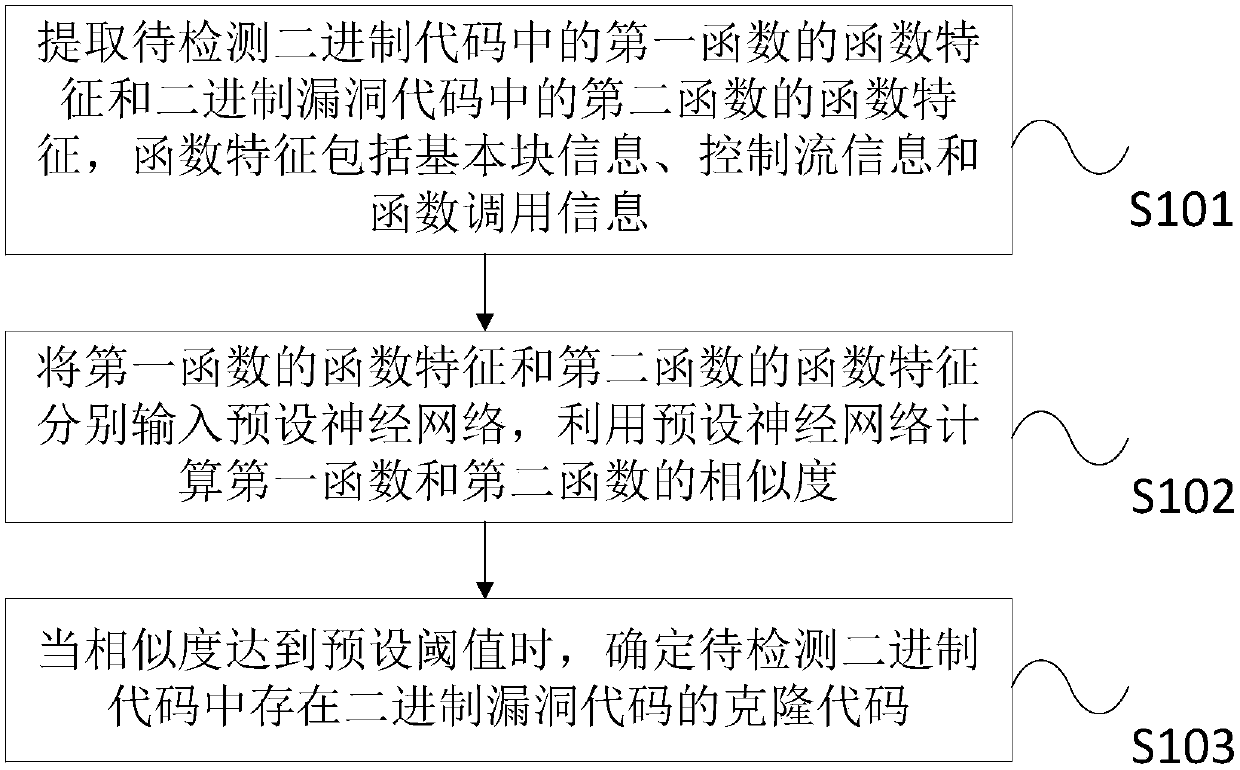
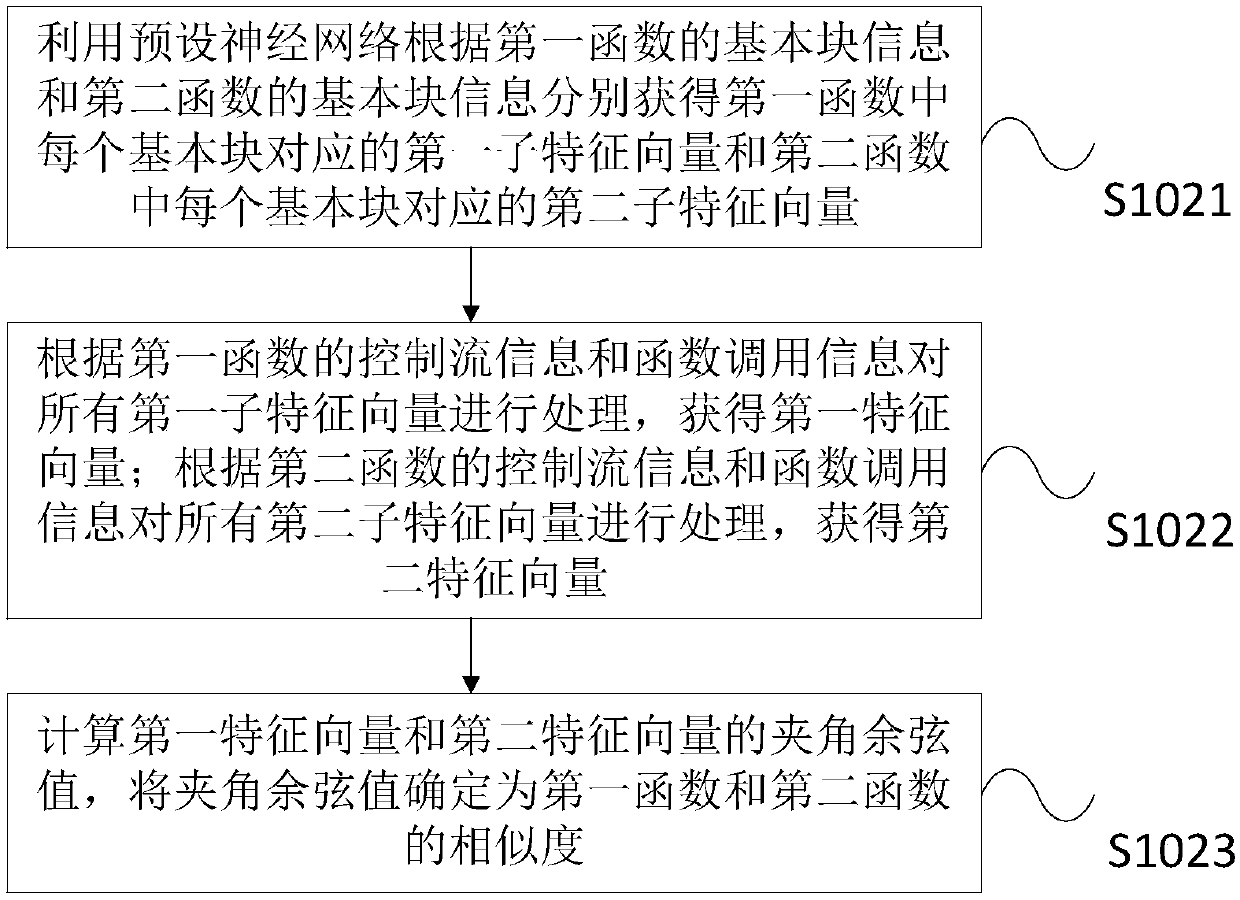
ActiveCN108491228AClone Detection Accurately AchievedClone Detection ImplementationReverse engineeringControl flowAlgorithm
The invention provides a binary vulnerability code cloning detection method and system. The method comprises the steps of extracting a function characteristic of a first function in a to-be-detected binary code and a function characteristic of a second function in a binary vulnerability code, wherein the function characteristic comprises basic block information, control flow information and function call information; inputting the function characteristic of the first function and the function characteristic of the second function to a preset neural network, and calculating the similarity between the first function and the second function by utilizing the preset neural network; and when the similarity reaches a preset threshold, determining that a cloned code of the binary vulnerability code exists in the to-be-detected binary code. According to the method and the system, the problems of incomprehensive clone type detection, low accuracy, high complexity, difficult realization and the like in an existing code cloning detection method are solved; the comprehensiveness of clone type detection and the accuracy of a detection result are ensured; and the detection efficiency is effectively improved.
Owner:TSINGHUA UNIV
Index-based Java software code clone detection method
ActiveCN104572471ASolving inefficienciesSolve the problem of large time consumptionSoftware testing/debuggingProgram/content distribution protectionParallel computingTime complexity
The invention discloses an index-based Java software code clone detection method. The index-based Java software code clone detection method employs the strategy that code segment information caching and memory index comparison are integrated and includes pre-saving code segment information of each source file in the memory index in the beginning; adopting the index searching method with time complexity to perform memory comparison. According to the arrangement, by caching the code segment information, the problem of the traditional method of low efficiency caused by rebuilding of a data structure in the case of every clone detection is solved; in the memory index comparison way, the problem of the traditional method of long period caused by pair comparison is solved.
Owner:HANGZHOU DIANZI UNIV
Software vulnerability analysis method and device
ActiveUS9946880B2Improve efficiencyAchieve rapidityPlatform integrity maintainanceConcolic testingUser input
The present disclosure includes: searching a code clone corresponding to a used source code from any analysis target source code; detecting a security sink and sensitive data of the security sink on the basis of patch information in the searched code clone; acquiring a source code which is from the user input point the a security sink by backwardly tracing the sensitive data detected in the analysis target source code; and verifying whether the searched code clone is a vulnerability in the analysis target source code by performing a concolic testing on the basis of a path from the input point to the security sink.
Owner:KOREA UNIV RES & BUSINESS FOUND
Code clone detection method based on hash value, electronic device and storage medium
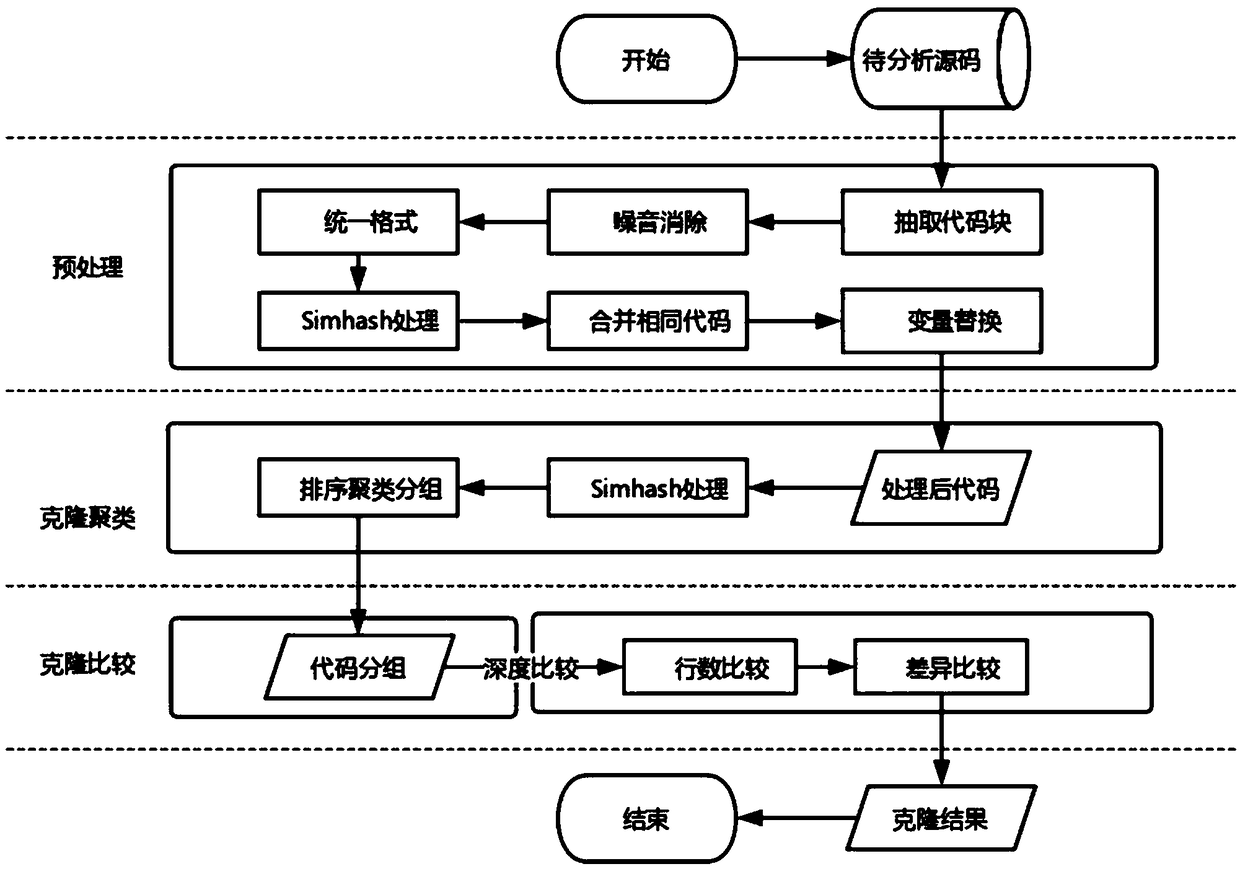
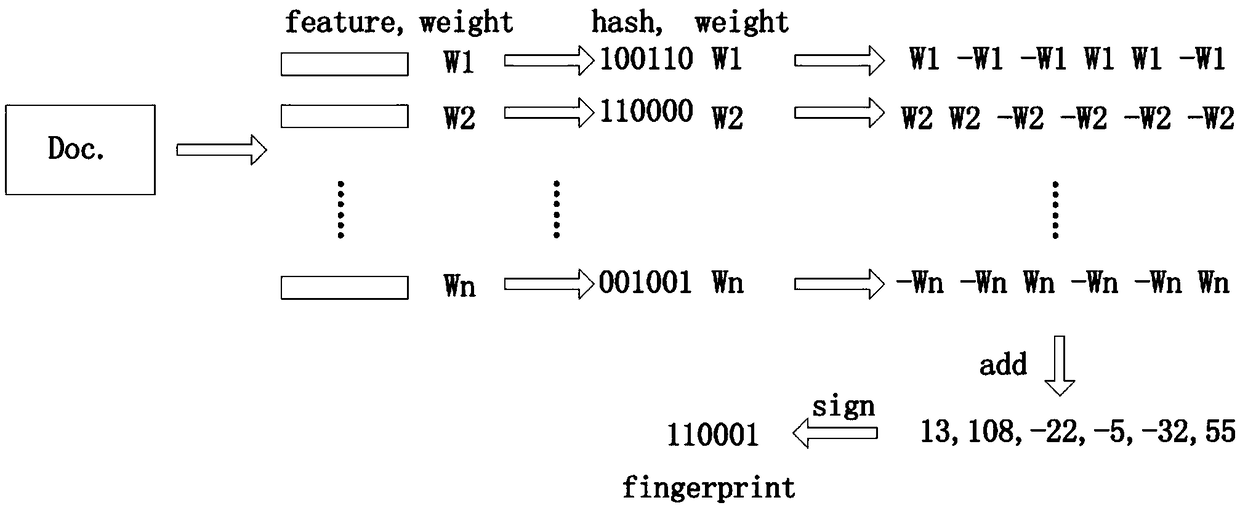
The invention provides a code cloning detection method based on a hash value, comprising the steps of reading a source code, extracting a code base in the source code through an analyzer, and obtaining a cloning detection object; obtaining the anonymous hash value of the clone detection object by processing the clone detection object with the hash algorithm, and obtaining some code clone groupingby clustering the anonymous hash value; comparing the code in the code cloning grouping in pairs within the group to determine whether the respective lines of the two pieces of code or the number of different code lines are less than a threshold value, and if yes, judging the code cloning to be similar, otherwise not judging the code cloning to be code cloning. The present invention relates to anelectronic device and a readable storage medium for performing the method described above. The invention can detect code cloning with identifier difference and code cloning with line number difference, can detect code cloning according to COBOL source code, has no limitation of platform and specific version language, has good portability, and reduces overall complexity by clustering hash value.
Owner:浙江网新恒天软件有限公司
Code clone detection method based on GAT graph neural network model
PendingCN113961241AImprove training effectGranularityCharacter and pattern recognitionReverse engineeringData setAlgorithm
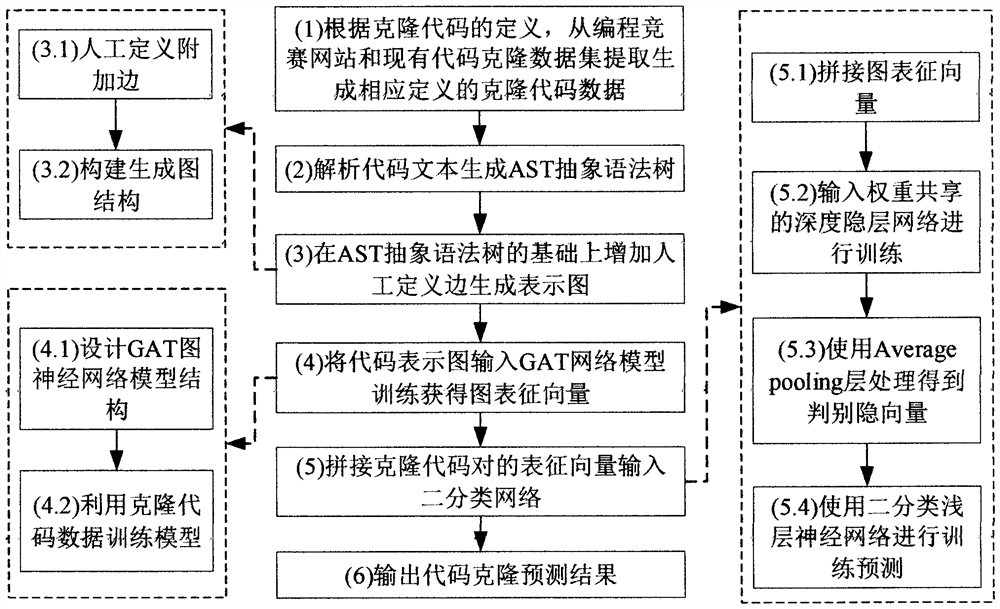
The invention discloses a code clone detection method based on a GAT graph neural network model, and the method comprises the following steps: extracting and generating clone code data of a corresponding definition from a programming competition website and an existing code clone data set according to the definition of a clone code; analyzing the code text to generate an AST abstract syntax tree; adding an artificially defined additional edge on the basis of the AST abstract syntax tree to generate a representation graph; inputting the code representation graph into a GAT network model for training to obtain a graph representation vector; splicing representation vectors of the cloning code pairs and inputting the representation vectors into a binary classification network; and judging an output code cloning prediction result. According to the method, the problem that the code semantic clone detection capability is insufficient in the code clone detection field is solved, the code text is converted into the graph structure representation, clone code information is represented from the semantic and structural level, the internal relation of learning clone codes can be accurately obtained, clone code judgment and prediction are carried out, and the code clone detection accuracy is improved.
Owner:NANJING UNIV
Code cloning detection method and device and electronic equipment
ActiveCN111124487AAccurate clone detectionReduce feature lossReverse engineeringFeature vectorAlgorithm
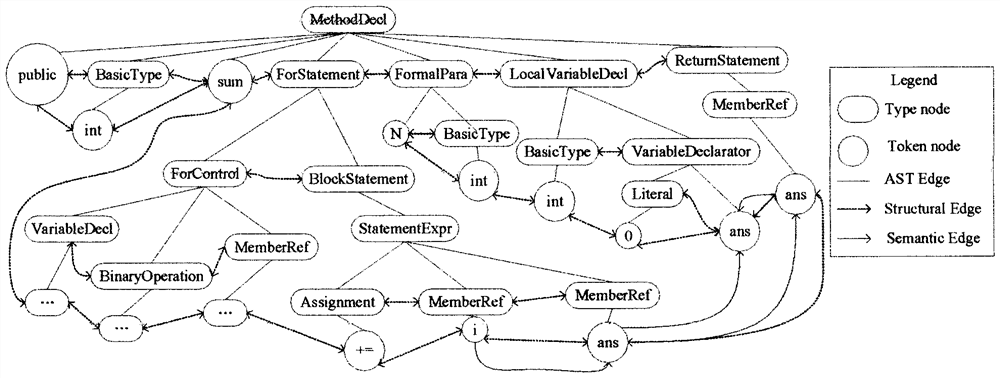
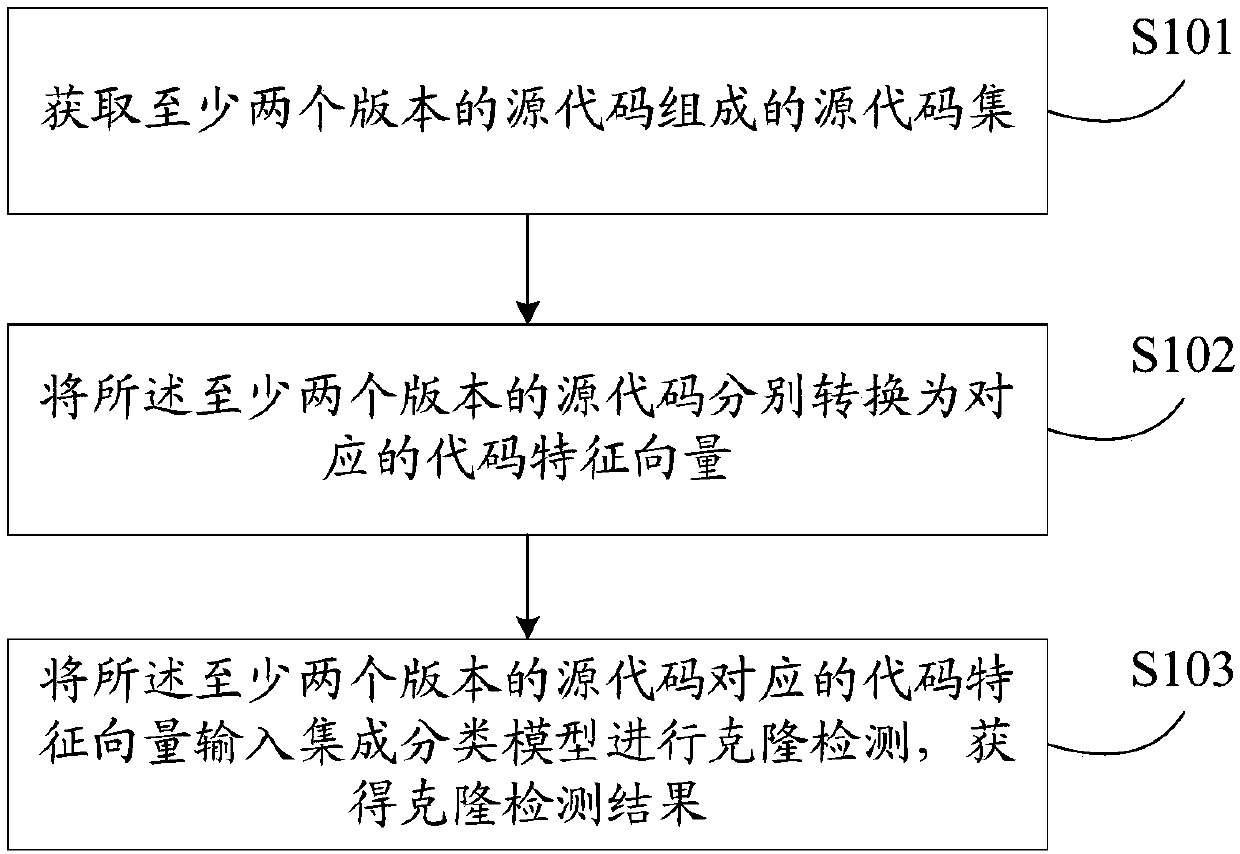
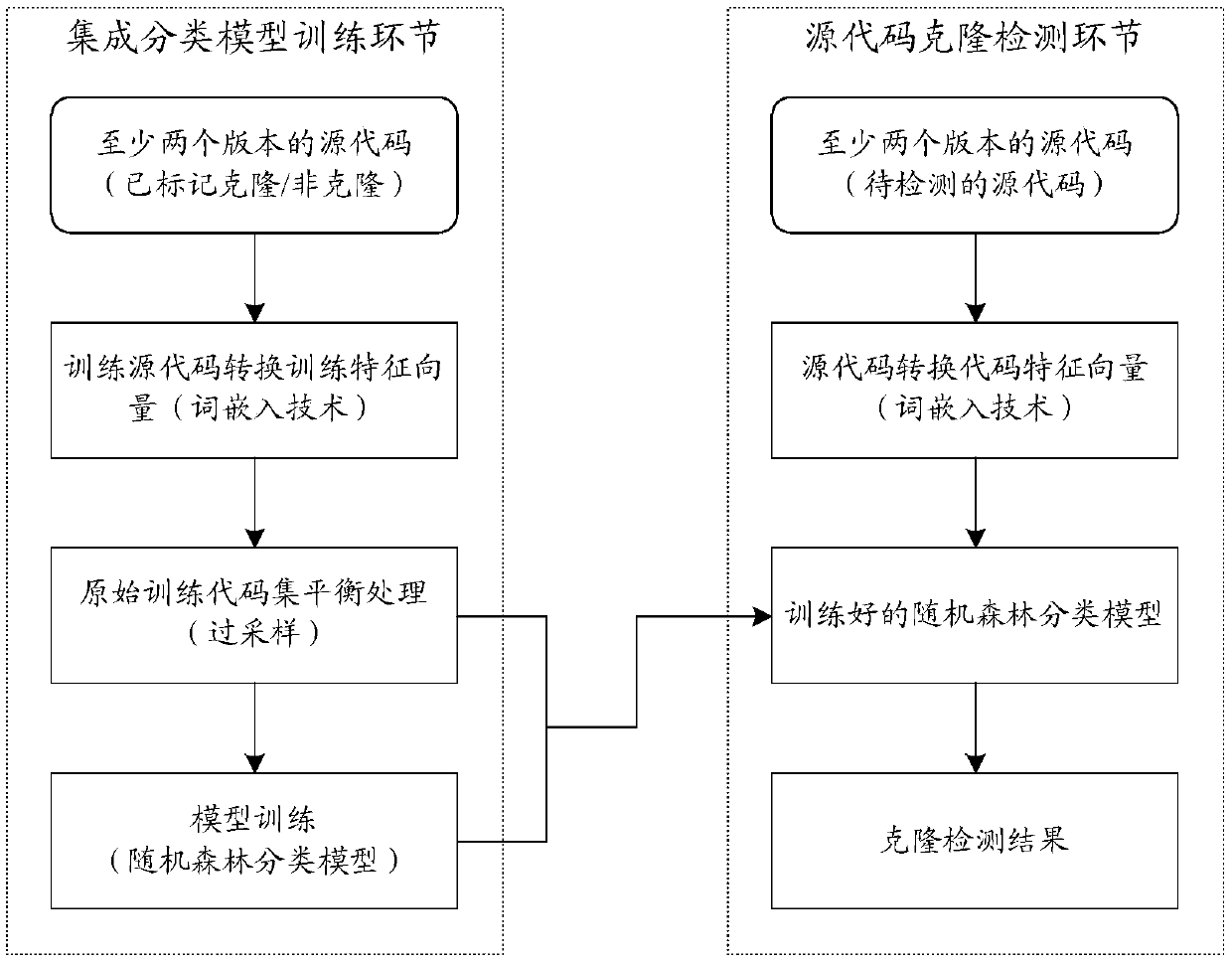
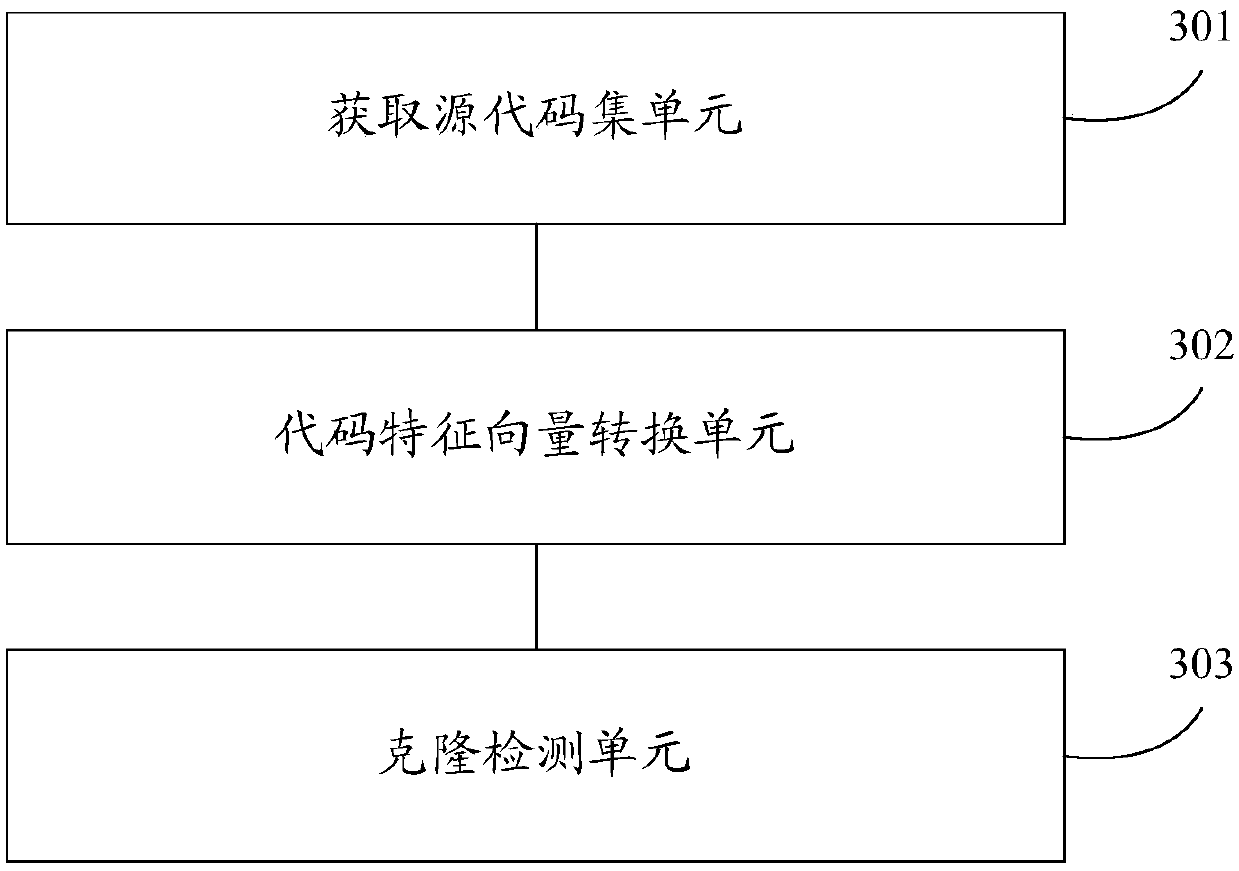
The invention discloses a code clone detection method. The method comprises the steps of obtaining a source code set composed of source codes of at least two versions; converting the source codes of the at least two versions into corresponding code feature vectors respectively; and inputting the code feature vectors corresponding to the source codes of the at least two versions into an integratedclassification model for clone detection to obtain a clone detection result. According to the code clone detection method, the respective feature information of the source codes is extracted and converted into the code feature vectors, clone detection is achieved through the integrated classification model on the basis of the code feature vectors, and therefore the feature loss of the source codesis reduced, and code clone detection achieved on the basis is more accurate and more effective.
Owner:ZHEJIANG UNIV
Code clone detection method and system based on isomorphic network
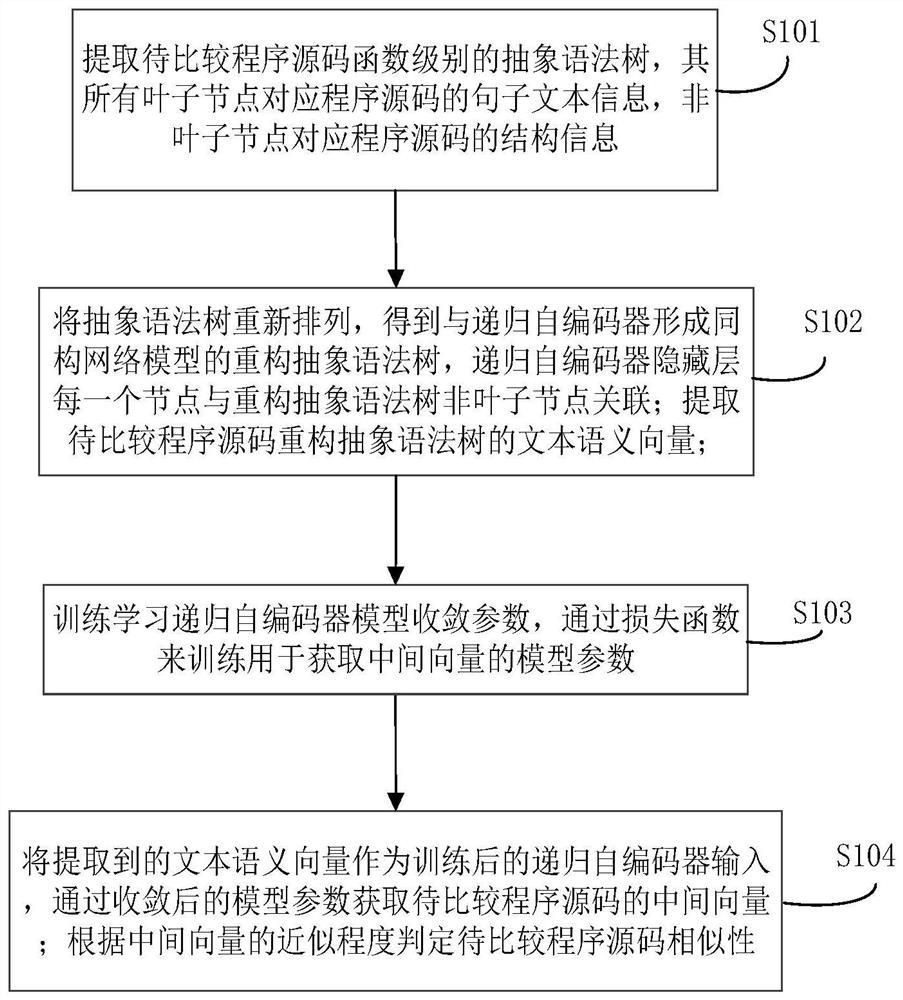
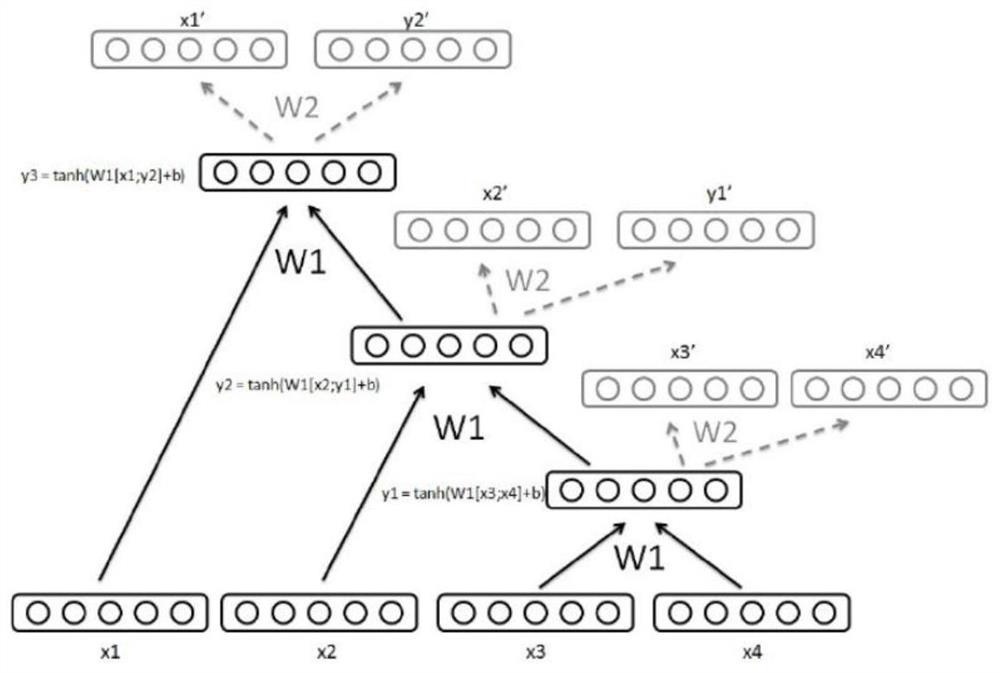
ActiveCN112035165ARealize detectionImprove efficiencySemantic analysisReverse engineeringSemantic vectorHidden layer
The invention belongs to the technical field of code detection, and relates to a code clone detection method and system based on an isomorphic network. The method comprises the steps that: an abstractsyntax tree of the function level of to-be-compared program source codes is extracted, all leaf nodes of the abstract syntax tree are corresponding to sentence text information of the program sourcecodes, and the non-leaf nodes of the abstract syntax tree are corresponding to the structure information of the program source codes; the abstract syntax tree is rearranged, so that a reconstructed abstract syntax tree which forms an isomorphic network model with a recursive auto-encoder can be obtained, and each node of a hidden layer of the recursive auto-encoder is associated with the non-leafnode of the reconstructed abstract syntax tree; recursive auto-encoder model convergence parameters are trained and learned, and model parameters used for obtaining an intermediate vector are trainedthrough a loss function; a text semantic vector of the syntax tree is extracted as input, and intermediate vectors of the to-be-compared program source codes are obtained through the converged model parameters; and the similarity of the to-be-compared program source codes is judged according to theapproximation degree of the intermediate vectors. The code clone detection efficiency and accuracy are improved by automatically learning code hiding features.
Owner:HENAN VALLEY INNOVATION NETWORK TECH
Clone code detection method capable of automatically constructing and utilizing pseudo-clone corpus
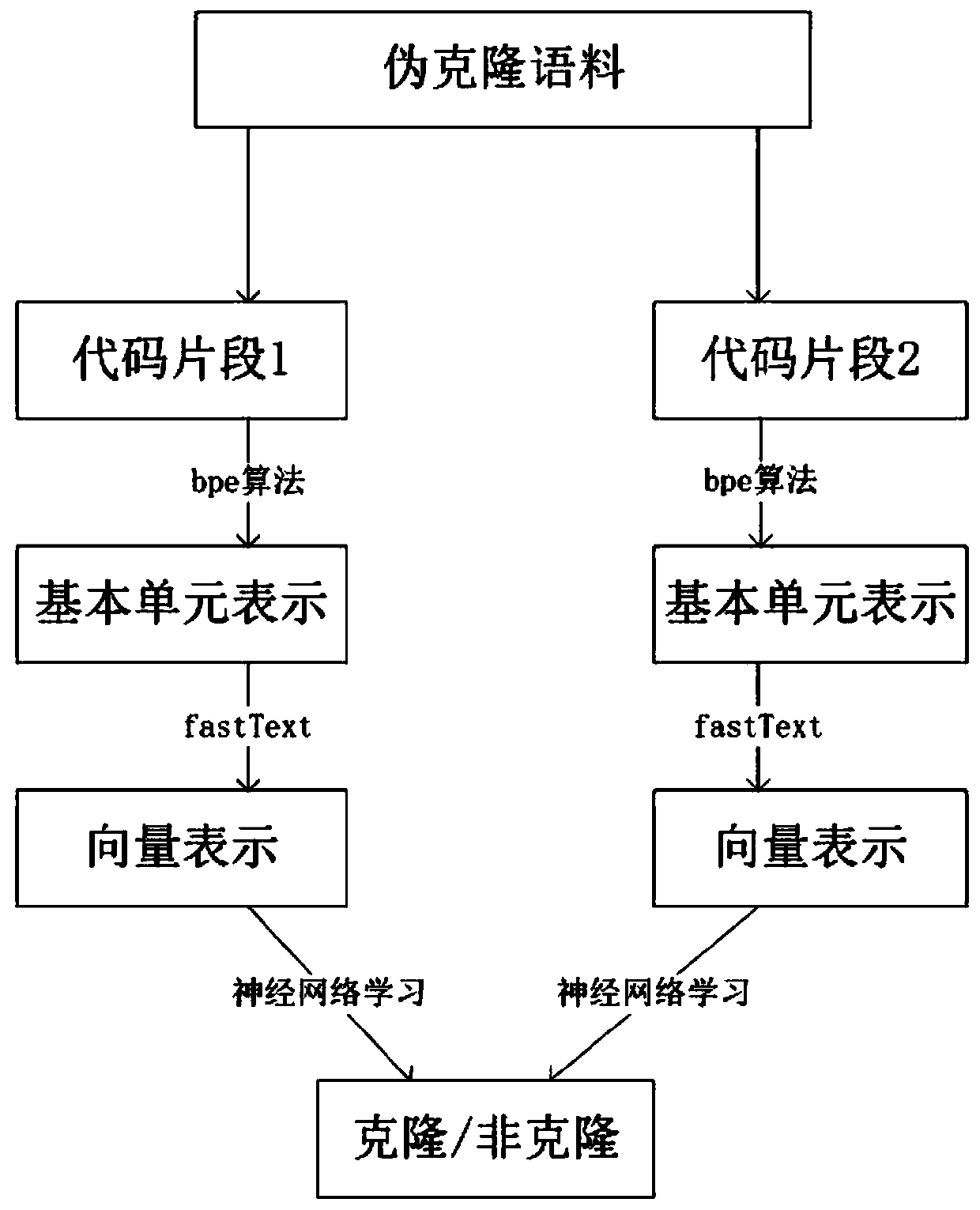
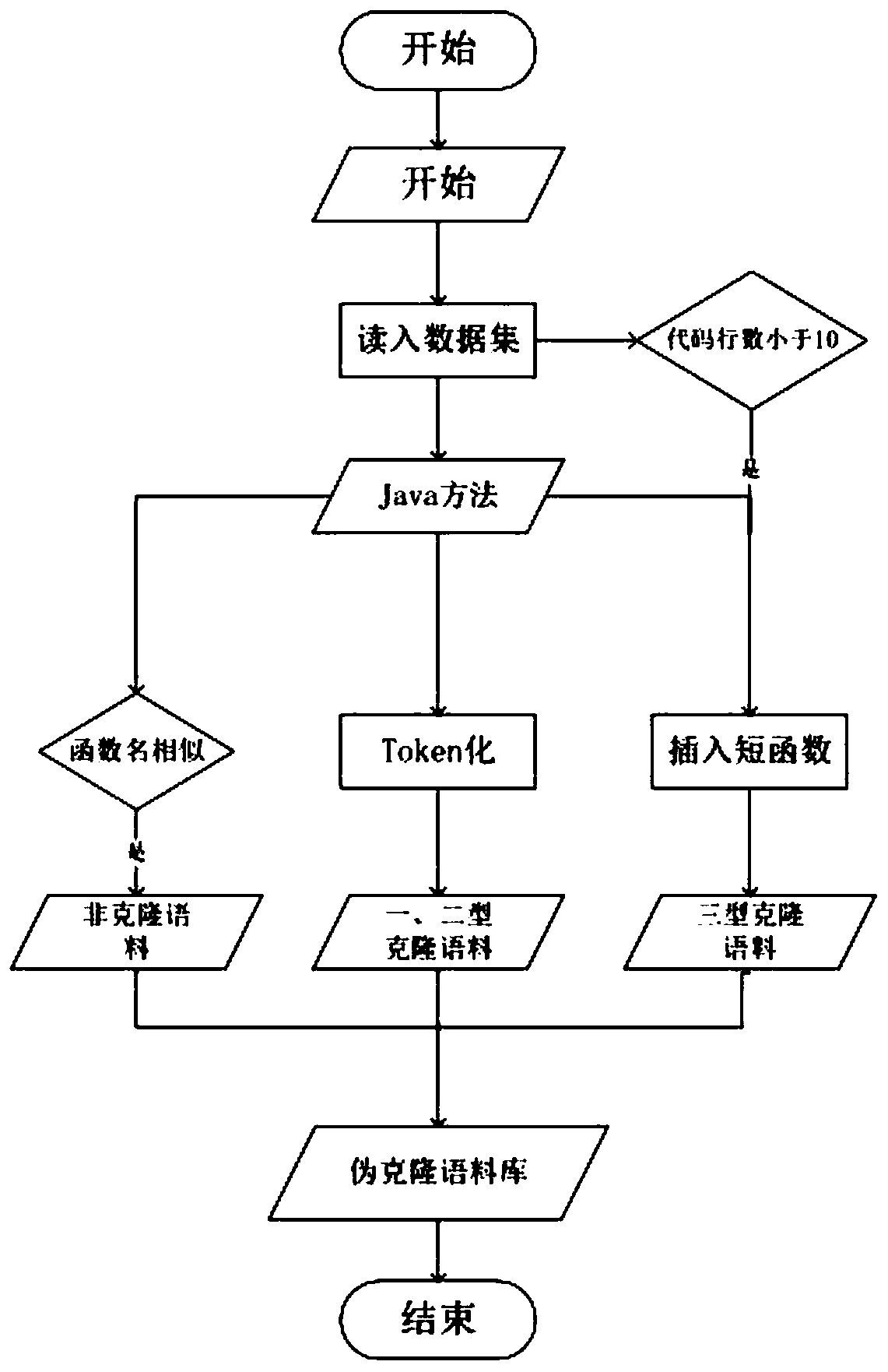
ActiveCN110851176AThe process is simple and fastCutting costsReverse engineeringEnergy efficient computingAlgorithmTheoretical computer science
The invention discloses a clone code detection method capable of automatically constructing and utilizing a pseudo-clone corpus. The clone code detection method comprises the following steps: step 1,automatically constructing a pseudo-training corpus; step 2, determining the most effective code unit in the clone code detection task, namely, segmenting a code basic unit required by clone detectionby using a BPE method; step 3, splicing tokens according to the most basic and most effective code units BPE determined in the step 2, performing word embedding, training a word embedding model for all methods in a corpus by using a statement sequence displayed by token characters, and generating a {code unit-vector} corresponding dictionary; step 4, establishing a simple and effective BiLSTM classification model for code clone detection, and performing training; and classifying the two methods by utilizing an L2-Norm algorithm, and judging whether the two methods are clone pairs or not. According to the invention, a clone code detection tool is realized, and a better detection effect on 1, 2 and 3 type clones is achieved.
Owner:TIANJIN UNIV
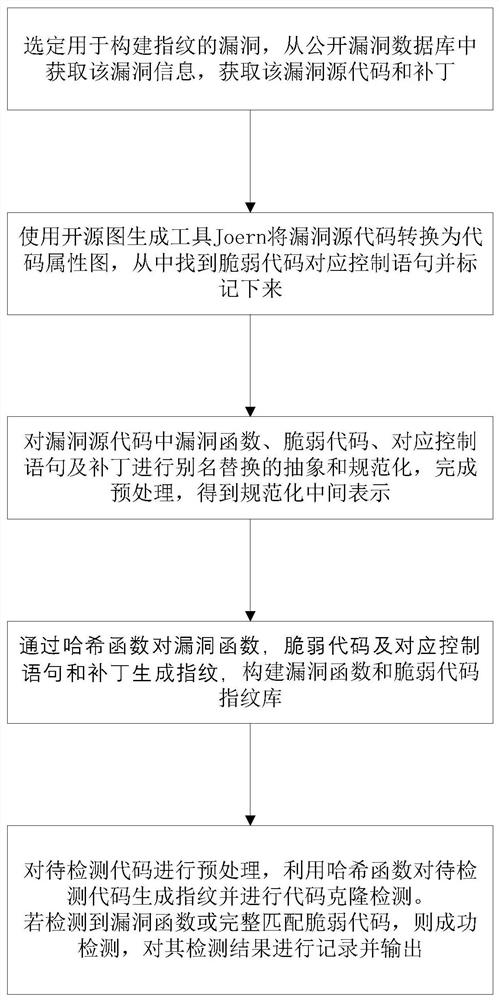
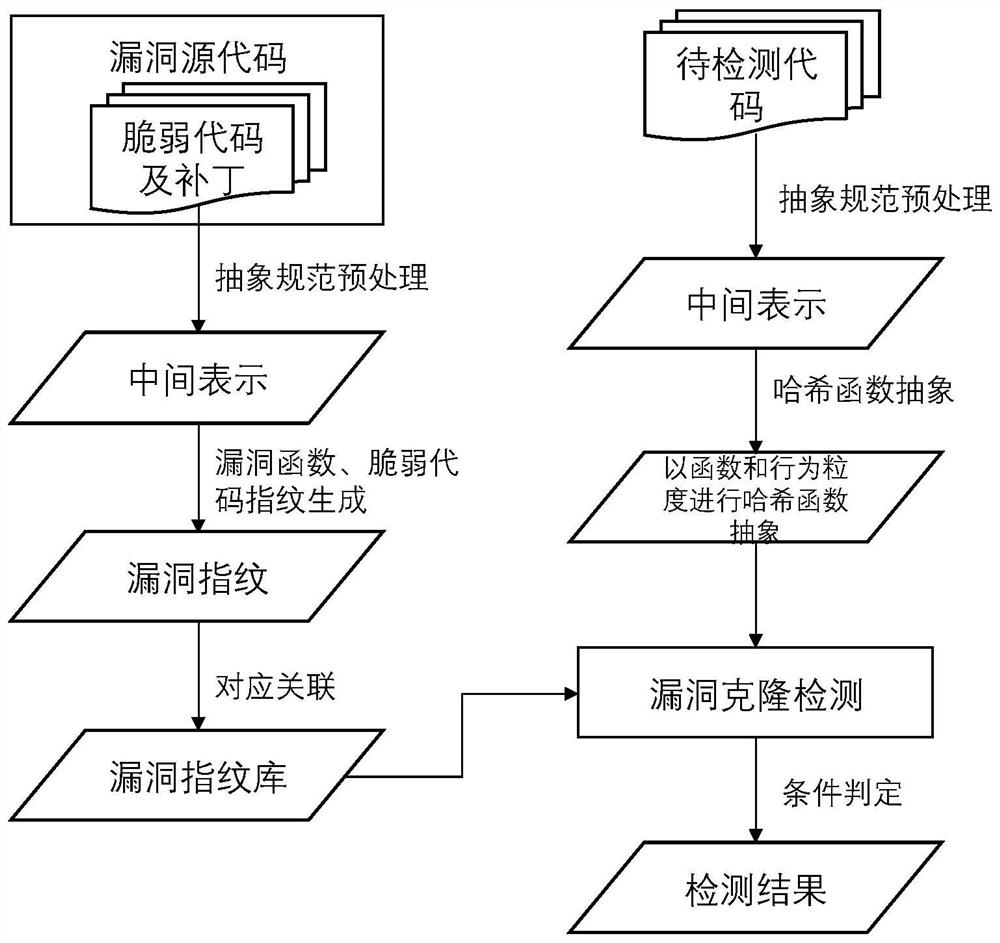
Vulnerability code clone detection method based on context semantics and patch verification
ActiveCN112651028AImprove detection efficiencyEasy to detectPlatform integrity maintainanceCode compilationAlgorithmRename
The invention discloses a vulnerability code clone detection method based on context semantics and patch verification, and solves the problem that an existing vulnerability code clone detection method cannot obtain vulnerability context and patch repair. The method comprises the steps of obtaining vulnerability data; marking vulnerability code control statements; performing abstract normalization preprocessing on vulnerability source codes and patches; constructing a vulnerability function and a vulnerability vulnerability code fingerprint library; cloning and detecting a to-be-detected code; and judging a detection result and outputting the detection result to finish vulnerability clone detection of the software. Based on the code fingerprint, the problem of low accuracy of a high-level abstract technology is avoided; according to the method, the influence of renaming on the detection accuracy is eliminated for the code abstract preprocessing operation; the context relationship and the patch are verified, so that the false alarm rate is reduced; besides, fragile code, control statement and patch detection is carried out on the to-be-detected code, so that the application scene is expanded and the missing report rate is reduced. The method is used for detecting bugs caused by code cloning in software.
Owner:陕西阡陌通达科技有限公司
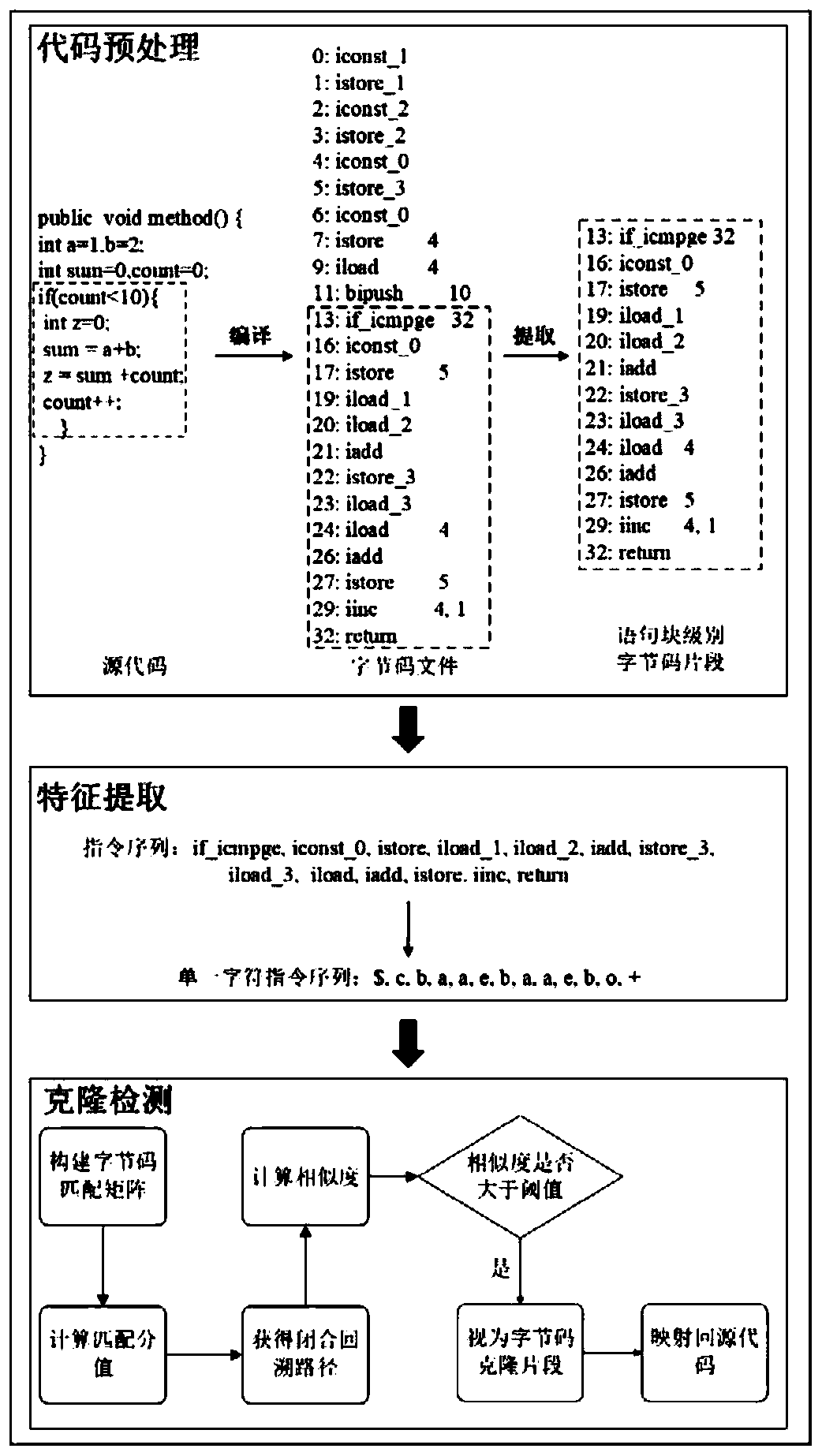
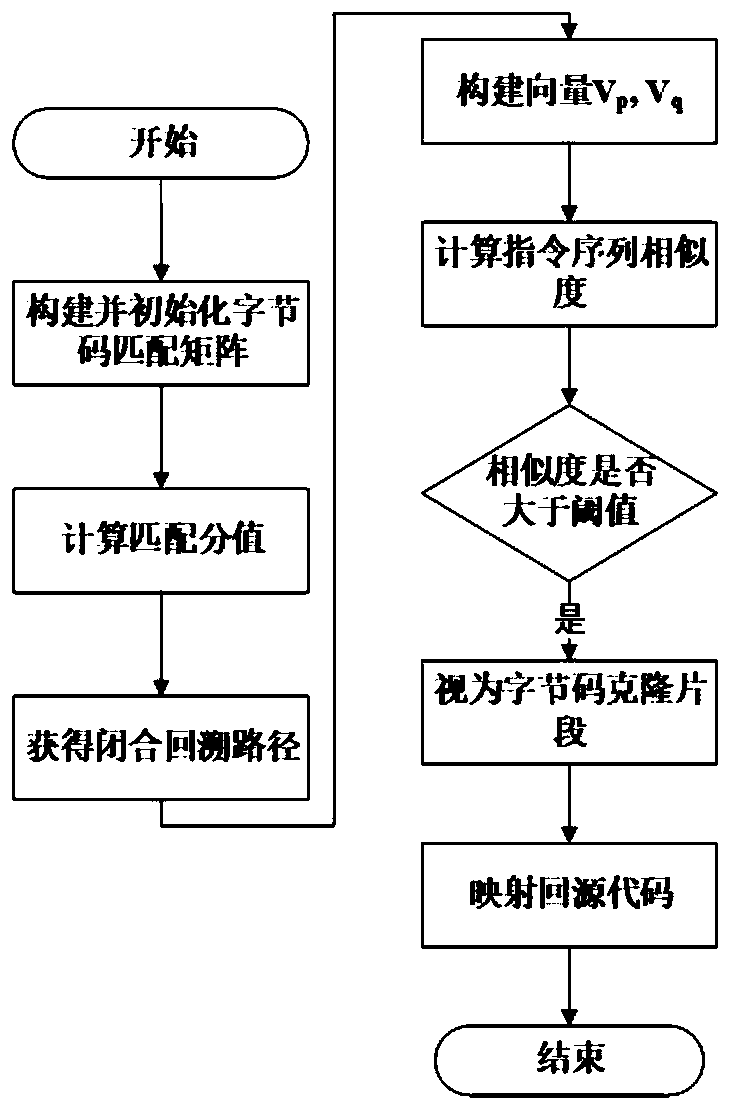
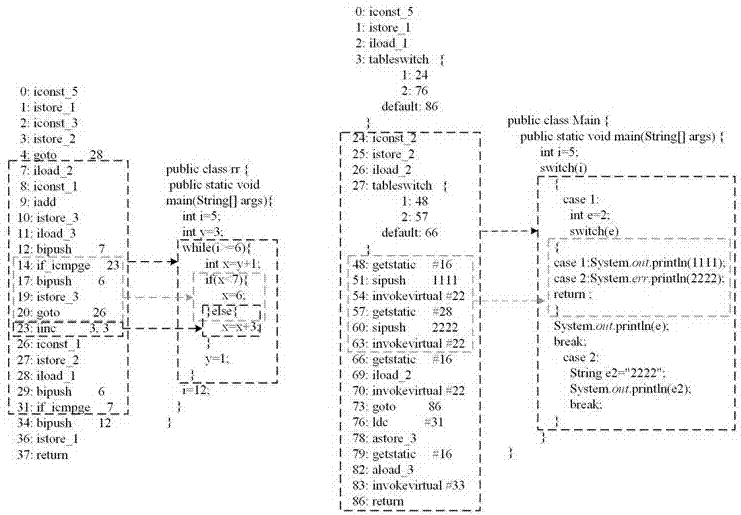
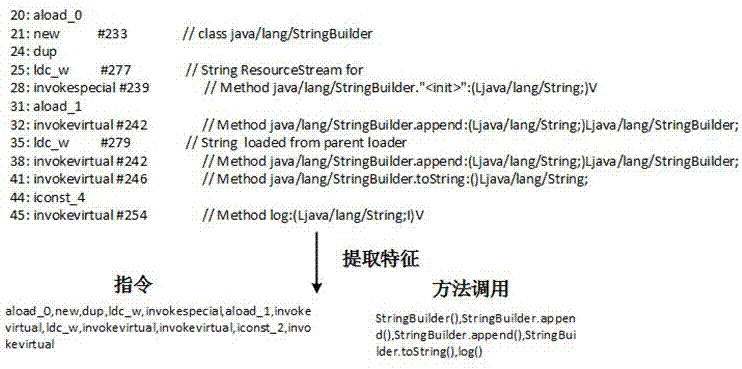
Java statement block cloning detection method based on bytecode sequence matching
ActiveCN109976806AImprove detection efficiencyGood detection and recognition effectReverse engineeringOther databases queryingParallel computingByte
The invention discloses a Java statement block cloning detection method based on bytecode sequence matching. The method provided by the invention comprises the following steps of: extracting a bytecode segment of a statement block level through execution of an instruction and analysis of skip, then extracting the instruction from the bytecode segment, and representing the instruction by adopting aunique character according to different functions realized by the instruction; and finally similar code segments are obtained by adopting a sequence matching and similarity calculation mode. According to the method, byte code fragments of a statement block level are accurately extracted through execution of an instruction and analysis of skip, the byte code fragments are expressed through uniquecharacters according to the function achieved by the instruction, and therefore the code cloning detection efficiency is improved. In the specific cloning code detection process, the sequence matchingmethod is applied to a single character instruction sequence, and compared with other traditional methods, the method has a better detection and recognition effect.
Owner:HANGZHOU DIANZI UNIV
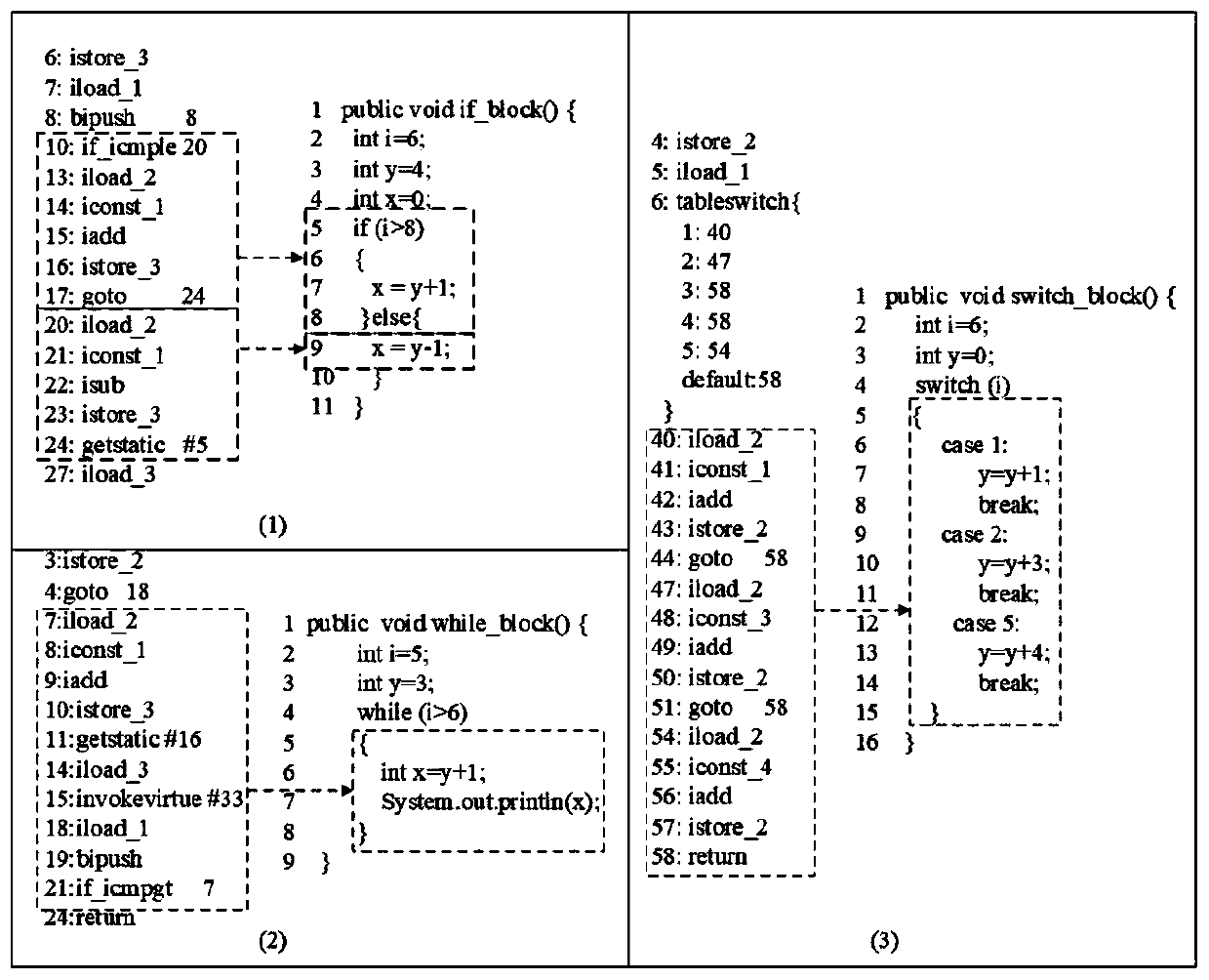
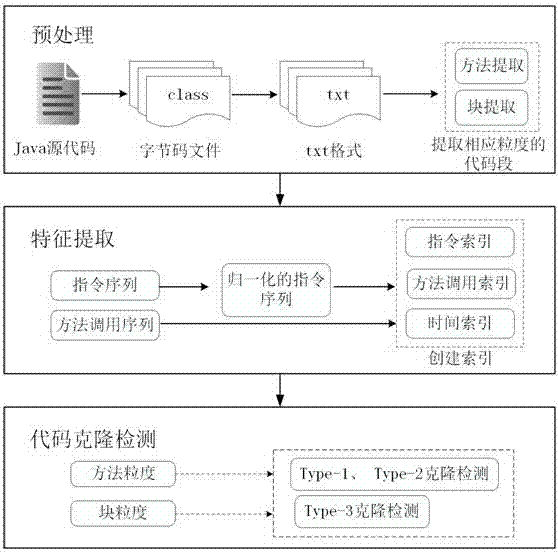
Multi-granularity code clone detection method based on Java byte codes under cloud environment
ActiveCN106919403ACloning detection results are accurateSoftware engineeringSpecific program execution arrangementsPattern recognitionGranularity
The invention discloses a multi-granularity code clone detection method based on Java byte codes under the cloud environment. The method extracts the codes of block granularity through analyzing the Java byte code instructions so as to simultaneously detect the clone of the method granularity and the clone of block granularity. During the calculation of similarity of codes, not only the similarity among instructions are taken into consideration, but also the similarity among method calling is introduced so that semantic clone is better detected. Compared with traditional methods for detecting code clone based on Java byte codes, the method of the invention can simultaneously detects the code clone of method granularity and block granularity; in addition, the similarity comparison of method calling is added so that the clone detection results are more accurate.
Owner:杭州鹿径科技有限公司
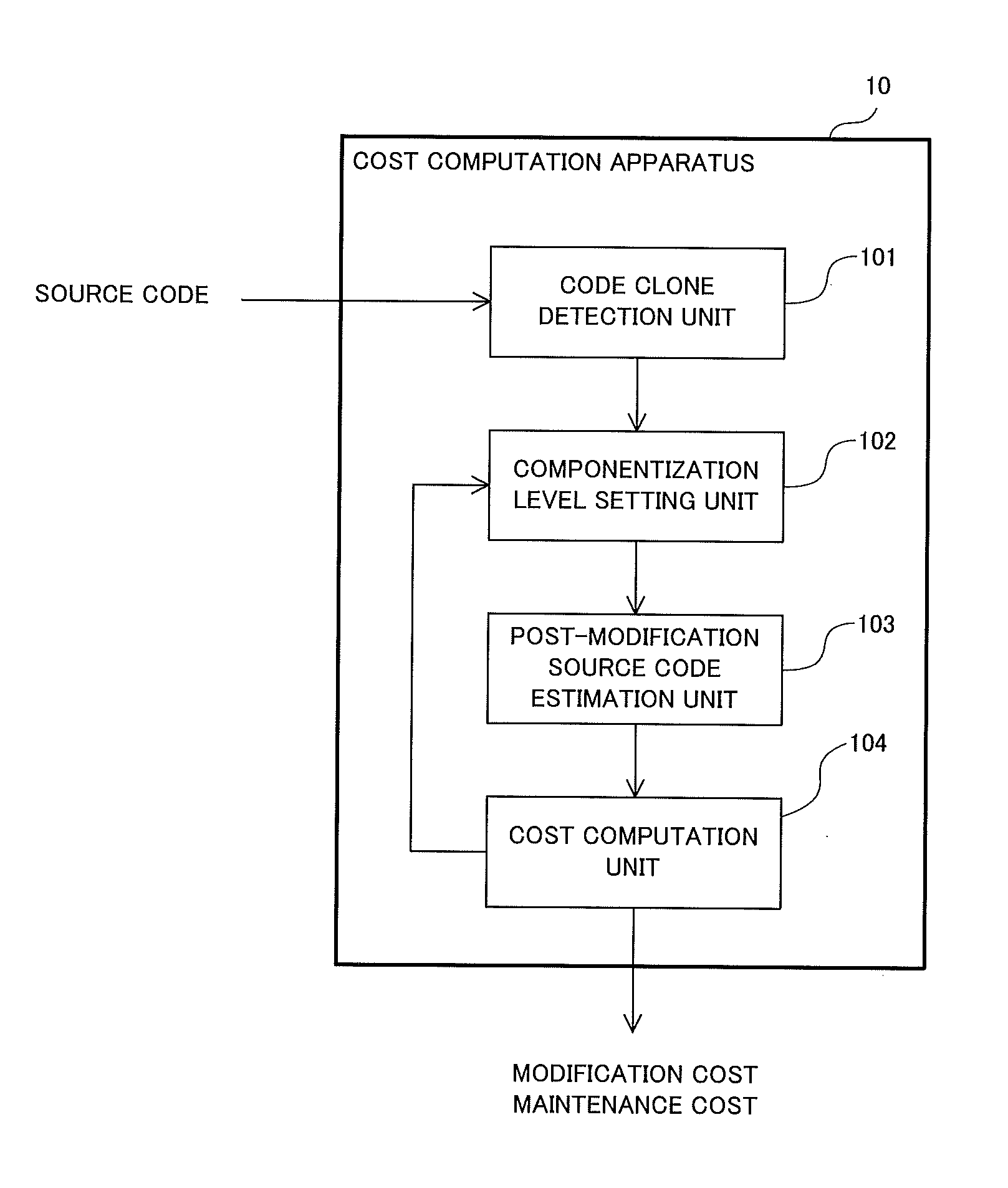
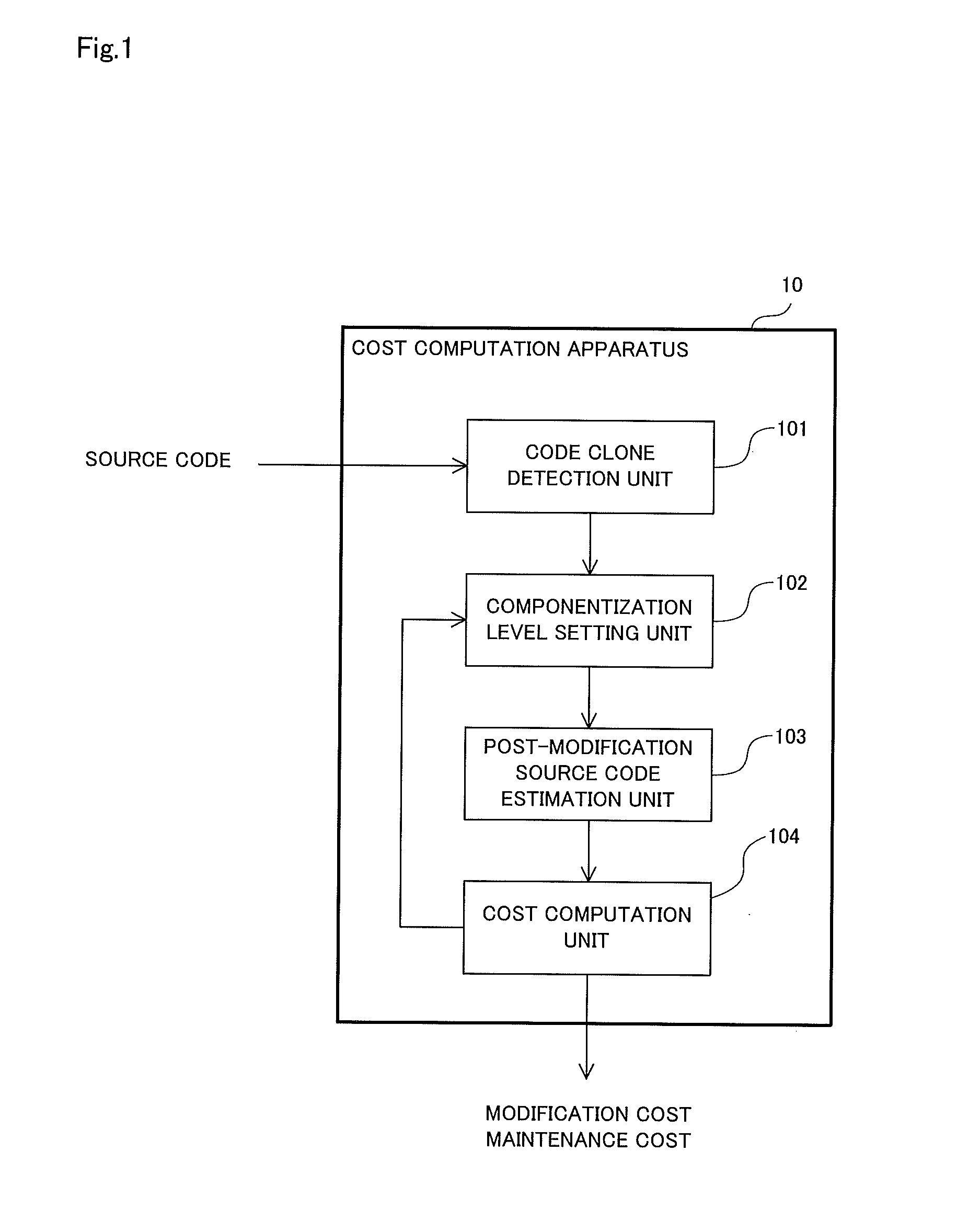
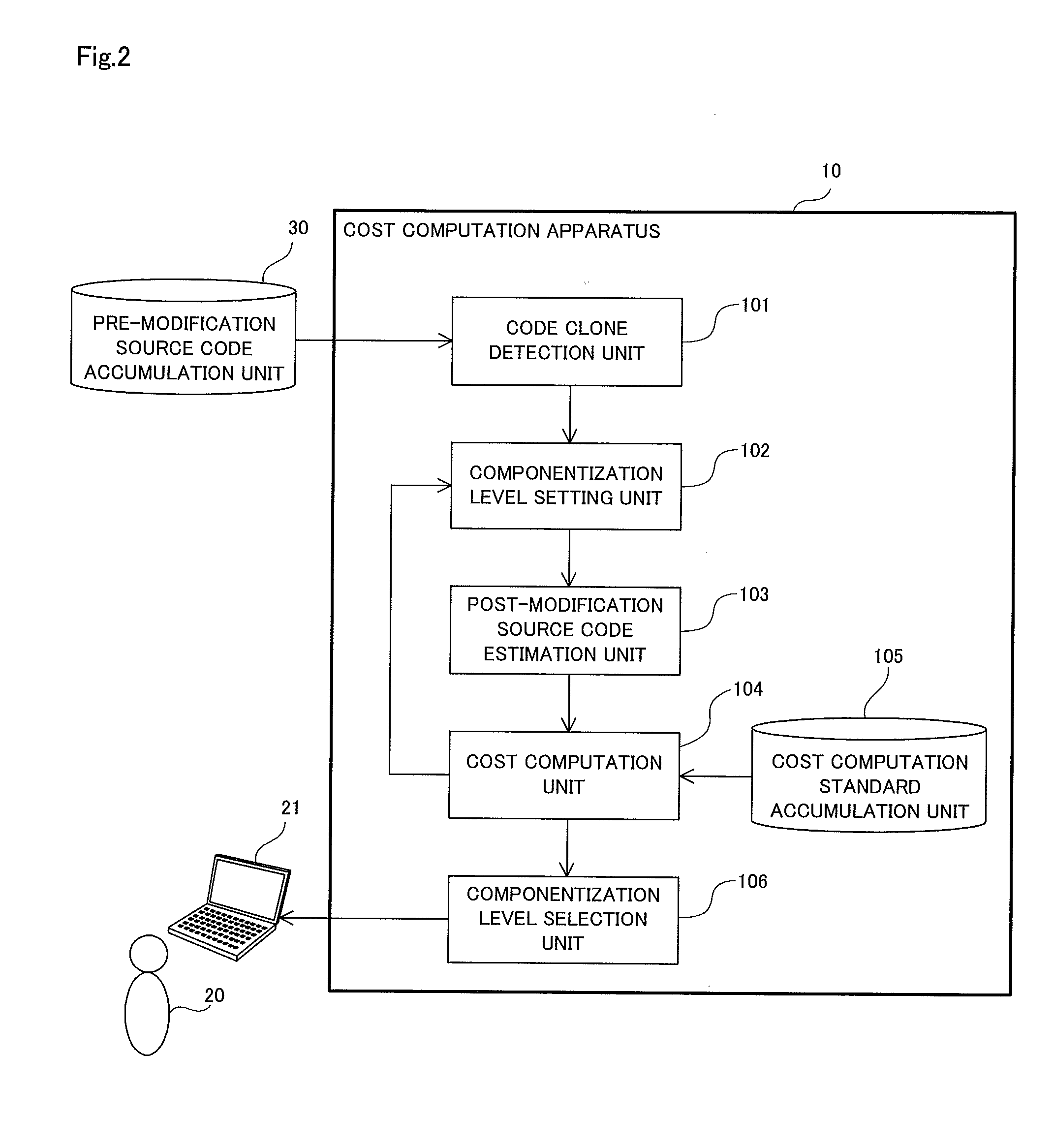
Cost computation device, cost computation method, and computer-readable recording medium
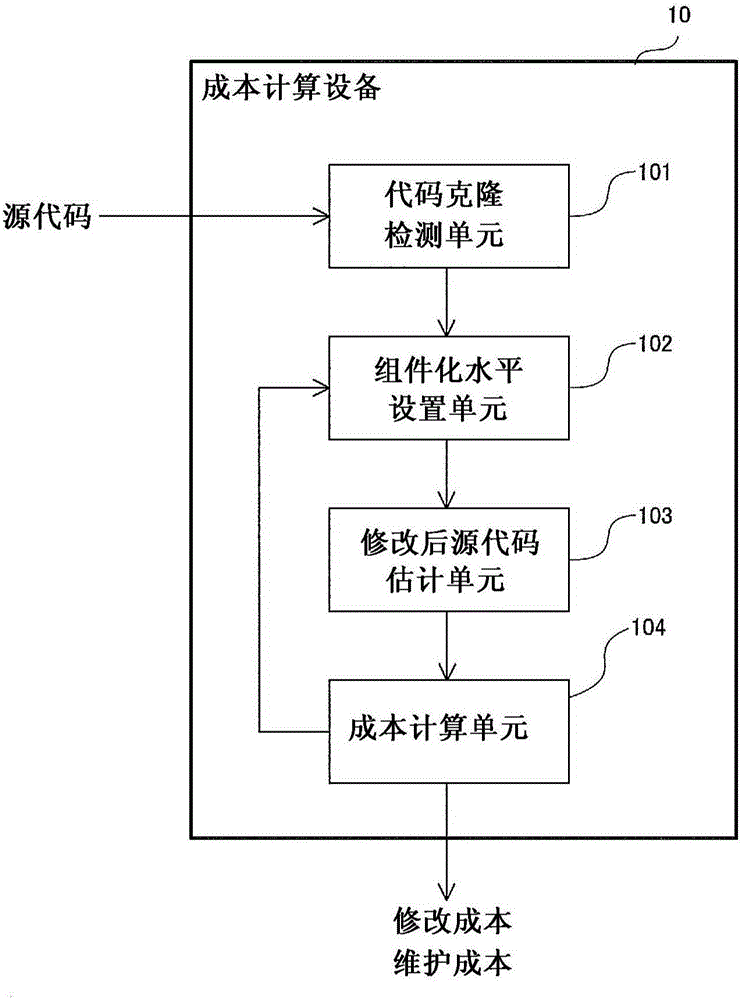
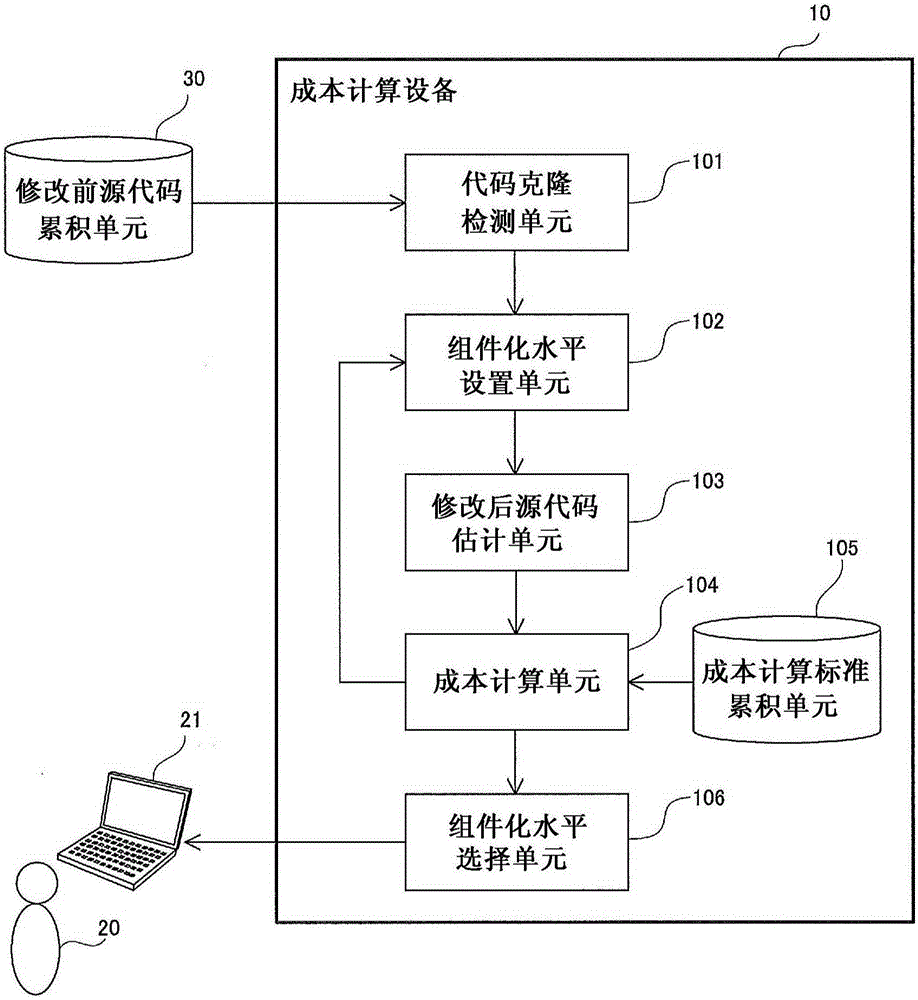
A cost computation apparatus (10) includes: a code clone detection unit (101) that detects, as a code clone, a set of identical or similar segments of pre-modification source code of a system; a componentization level setting unit (102) that sets a level at which the detected segments are integrated as a component; a post-modification source code estimation unit (103) that estimates post-modification source code obtained by applying componentization to the pre-modification source code at the set level; and a cost computation unit (104) that computes a modification cost required to update the system and a maintenance cost on the basis of the estimated post-modification source code in accordance with a computation standard that specifies a method of computing the modification cost and the maintenance cost.
Owner:NEC SOLUTION INNOVATORS LTD
Code clone detection method and system based on byte code and neural network
PendingCN114064117AEasy to detectDetection time is shortCharacter and pattern recognitionReverse engineeringAlgorithmTheoretical computer science
The invention belongs to the technical field of code clone detection, and particularly relates to a code clone detection method and system based on byte codes and a neural network. The method comprises the steps: obtaining to-be-detected code data, inputting the to-be-detected code data into a trained code clone detection model, and obtaining a detection result, marking and storing the detection result; according to the method, source codes are replaced with byte codes, compared with an existing detection method based on texts and lexical methods, the method has the advantages that code semantic information is fully considered, and the detection effect on type 3 clone and type 4 clone can be improved from the aspects of accuracy, the recall rate, the F1 metric value and the like.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
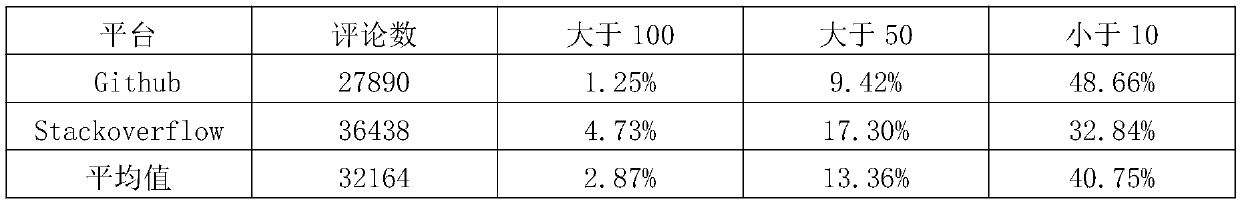
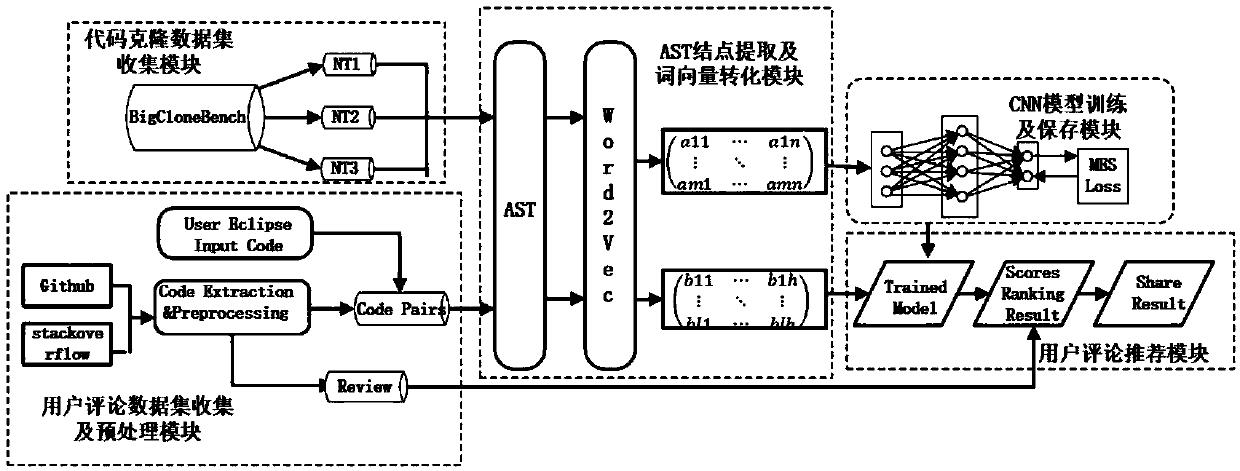
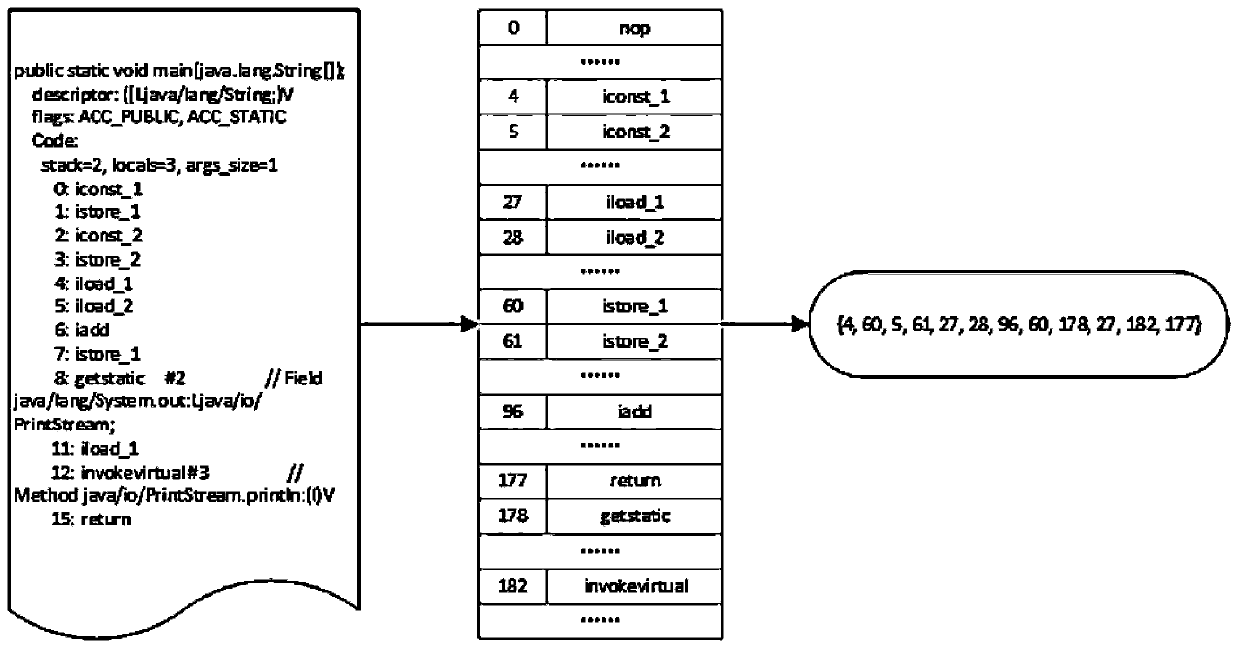
A user comment recommendation method based on a code cloning technology
ActiveCN109683946ASolve the problem of not having enough valid user reviewsImprove product qualitySemantic analysisVersion controlData setUser input
The invention discloses a user comment recommendation method based on a code cloning technology. The method is combined with the code cloning technology and a user comment recommendation algorithm toprovide reasonable and effective comments for newly developed software or software lacking user comments. The main process comprises the following steps: firstly, collecting a large amount of code cloning data, processing code pairs in a data set by using AST and Word2Vec, representing the code pairs as vectors, and carrying out CNN model training and storage based on the vectors; Secondly, user comment stage data is collected and preprocessed, codes input by a user based on a plug-in and codes used for comment recommendation form code pairs, and the code pairs are expressed as vectors by adopting a processing method with the same code cloning stage; And finally predicting the similarity value based on the vector and the stored CNN model, and finally providing reasonable and effective usercomments for the code segment input by the user. The problem that application software does not have enough effective user comments is solved, and more effective information is provided for further improvement and improvement of the software.
Owner:NANKAI UNIV
Method for detecting byte code similarity of N-Gram
InactiveCN110362343AEasy to operateFast executionCharacter and pattern recognitionReverse engineeringTheoretical computer scienceEngineering
The invention provides a method for detecting the byte code similarity of N-Gram. According to the method, the method comprises the following steps: converting an executable binary file to be comparedinto a byte code by using an N-element grammar model, and adopting N-element grammar model; analyzing the byte code by a Gram hash algorithm to obtain a corresponding hash value; and finally, extracting features from the byte code by a winning algorithm, and calculating to obtain the similarity. According to the method, similarity judgment on the byte code level can be carried out on the Java executable file. The hash algorithm is used for analysis. The execution efficiency of the method is improved, and therefore the method can be widely applied to Java byte code confusion degree evaluation,code clone detection and other aspects.
Owner:SHANGHAI JIAO TONG UNIV
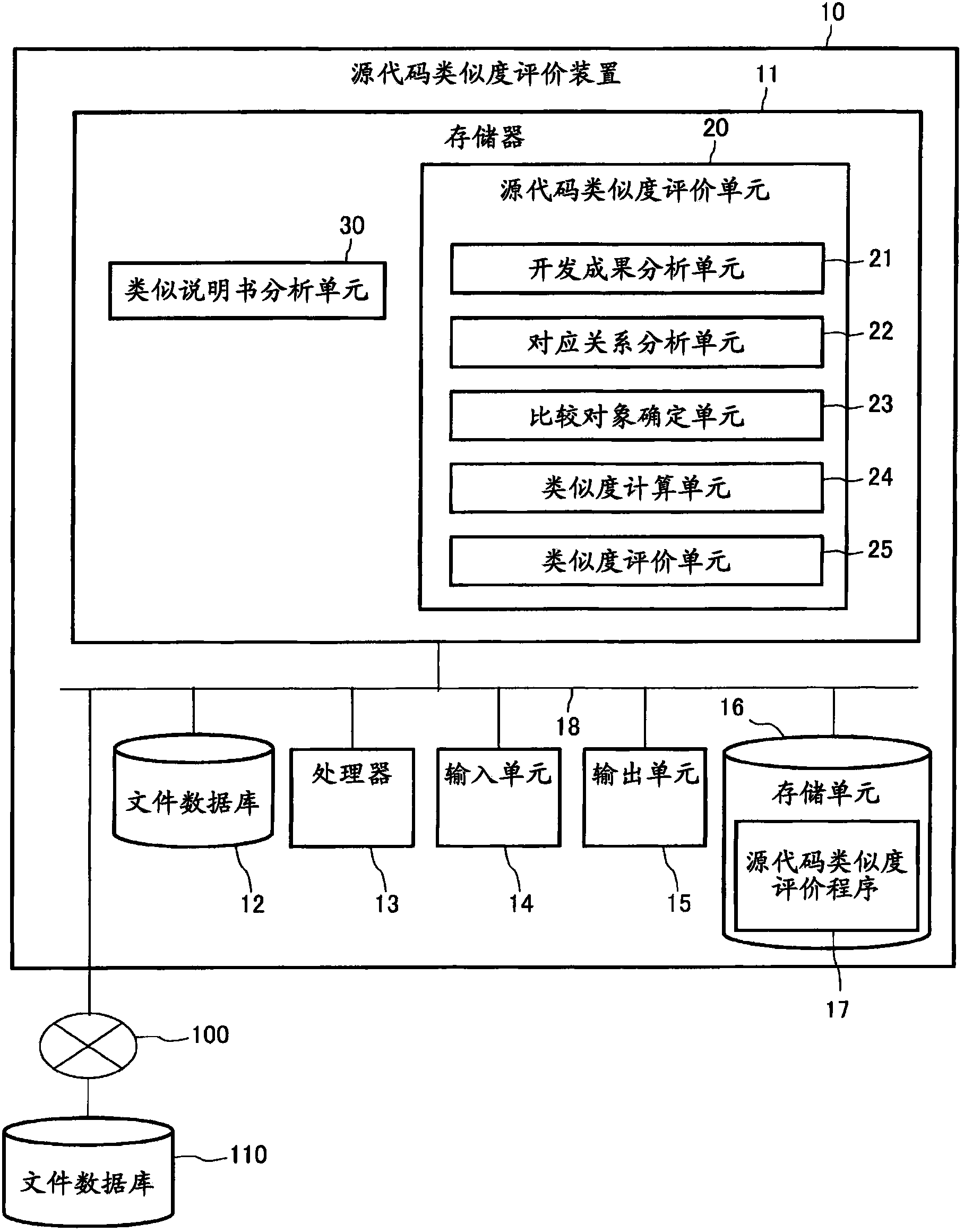
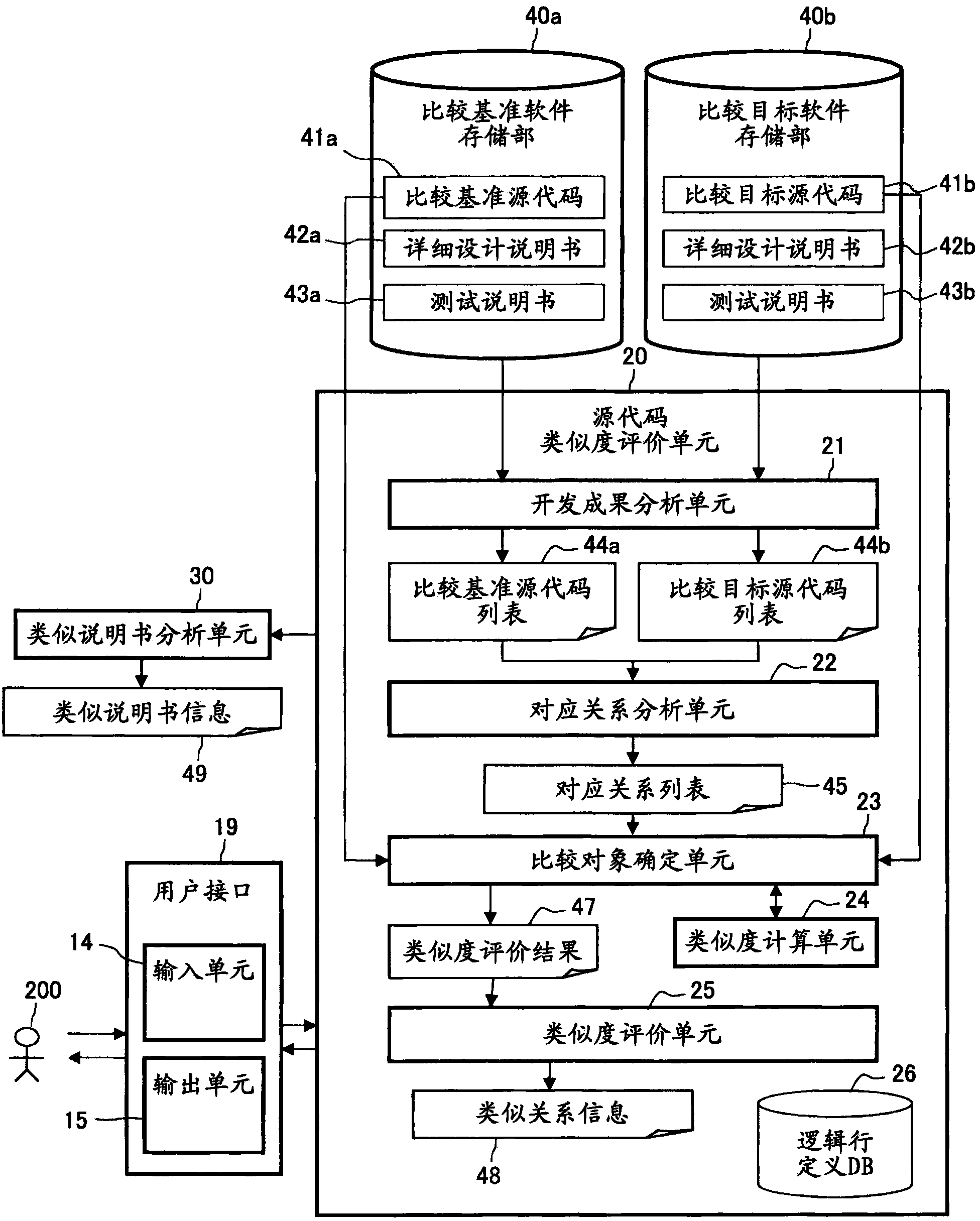
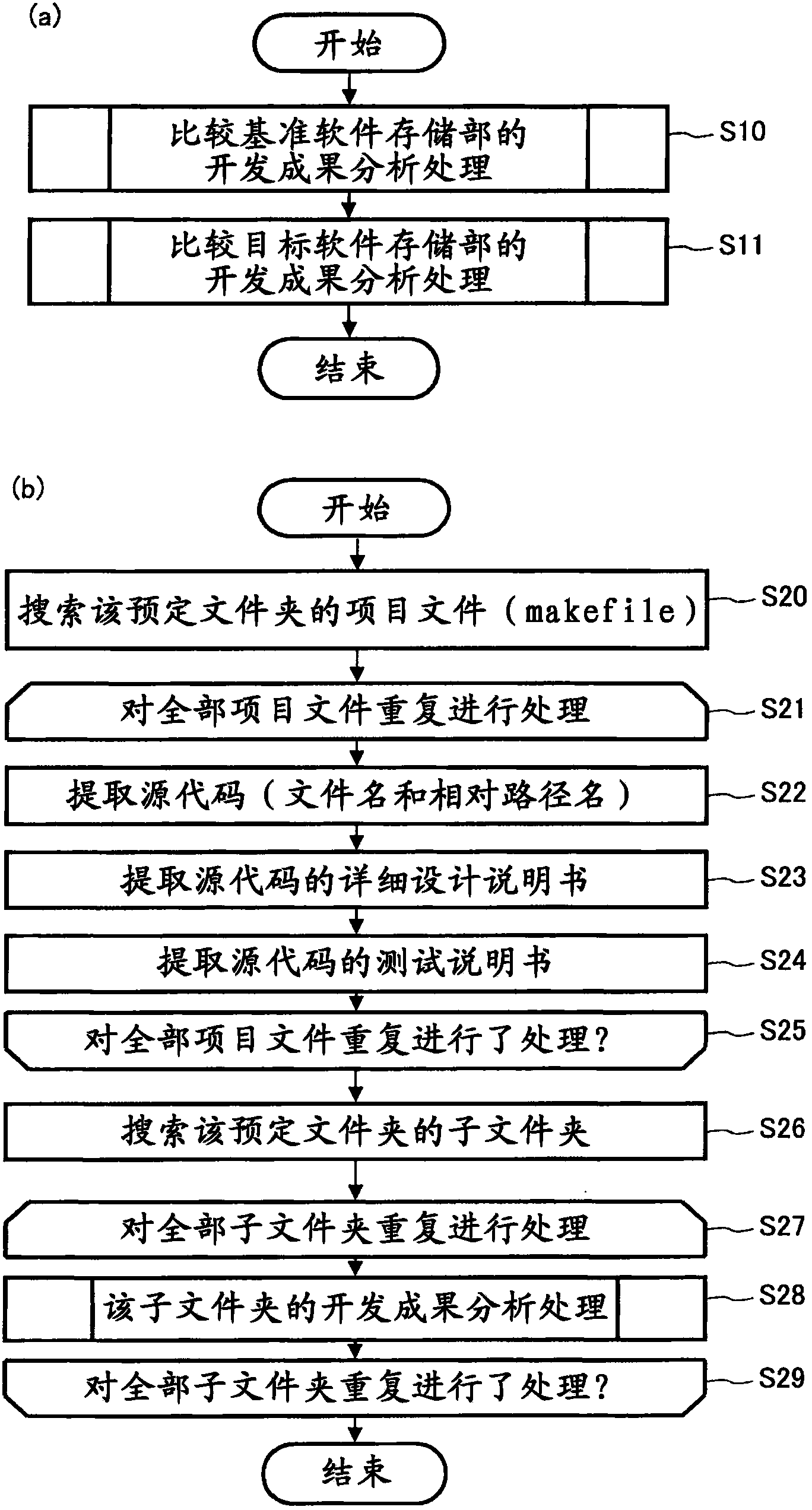
Evaluation method and evaluation device for similarity of source codes
The invention relates to an evaluation method and an evaluation device for similarity of source codes. Calculation amount for analysis of code clone increases with large-scale software. The evaluation device for similarity of the source codes comprises a development achievements analysis unit (21) for extracting source code list constituting the software, a corresponding relationship analysis unit (22) for comparing a comparison reference source code list (44a) and a comparison target source code list (44b) and analyzing corresponding relationships of the both, a comparison object determining unit (23) for determining a comparison object of a comparison target source code (44b) contained in a comparison reference of the comparison reference source code list (44a) from the comparison target source codes (44b) according to the corresponding relationship, a similarity calculation unit for calculating the similarity between a comparison reference source code (44a) and a source code determined by the comparison object determining unit (23), and an output unit (15) for outputting combination of the comparison reference source code (44a) and the similarity.
Owner:HITACHI LTD
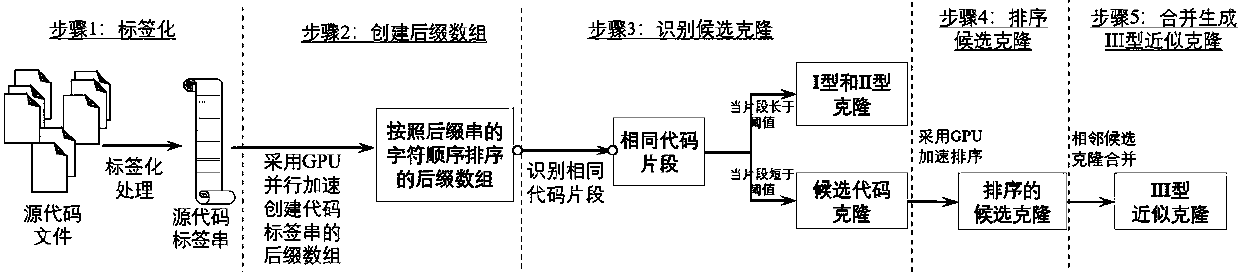
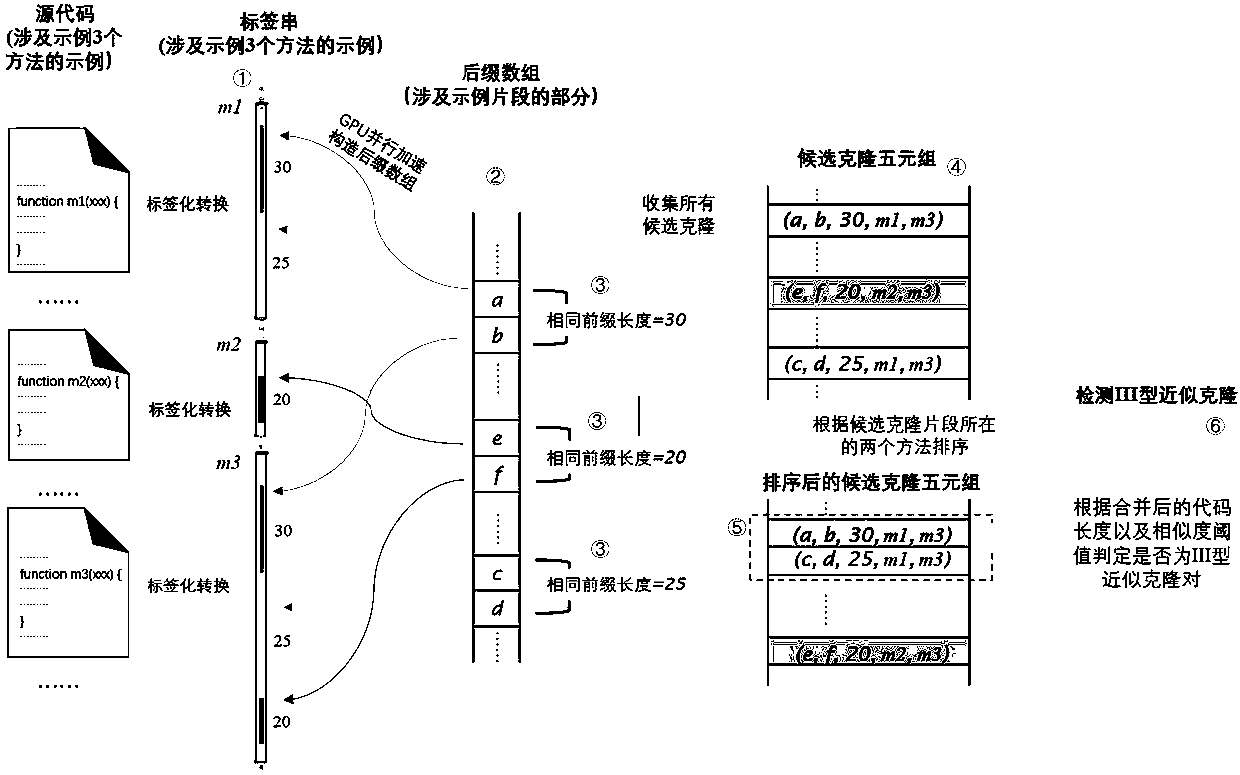
approximate code cloning detection method adopting GPU acceleration
The invention belongs to the technical field of software code analysis, and particularly relates to an approximate code cloning detection method accelerated by a GPU. According to the invention, source codes of a plurality of software projects are labeled; converting into a string consisting of a tag sequence; constructing the string into a suffix array sorted according to suffix character stringsby adopting a GPU (Graphics Processing Unit) parallel method; and finally, the code cloning fragments which are smaller than the code cloning length threshold but not smaller than the candidate cloning length threshold are sequenced through a GPU parallel acceleration method according to the position in the code file, and whether the cloned fragments can meet the similarity threshold requirementof approximate cloning or not after being merged is calculated. And if the code similarity meets the threshold requirement, recording the code similarity as approximate code cloning. According to themethod, the approximate code clone can be rapidly detected on the code fragment granularity in mass codes.
Owner:FUDAN UNIV
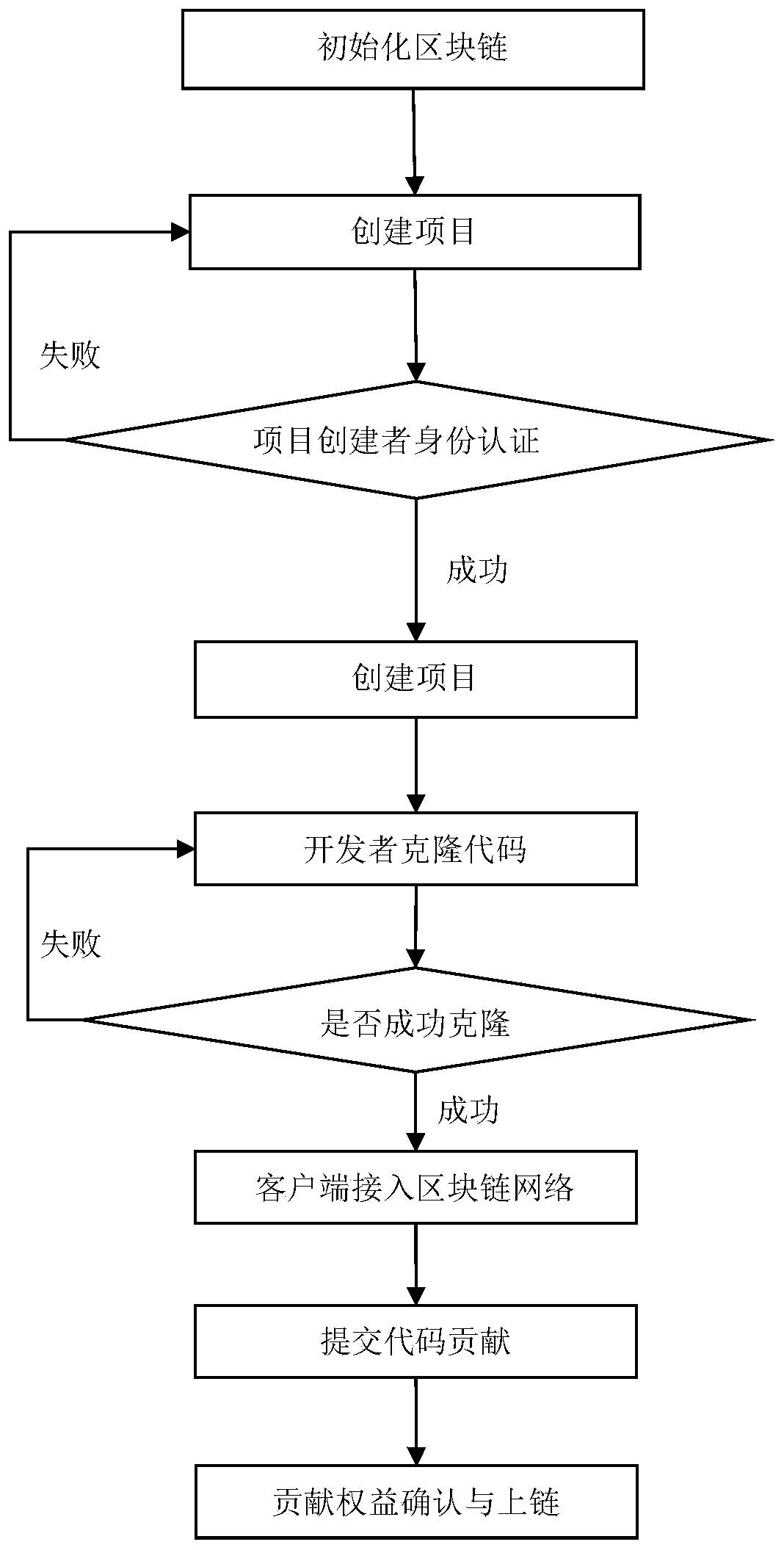
Open source software right confirmation method and system based on block chain
ActiveCN110750762AEffective protectionProgram/content distribution protectionSoftware engineeringOpen source
The invention discloses an open source software right confirmation method and system based on a block chain, and the method comprises the steps: a block chain service is intilaized on an open source software block chain service platform, and an intelligent contract is deployed for each node in a block chain network to transmit contribution information; and the open source software block chain service platform completes project creation according to the request and generates a corresponding software warehouse; each project developer client performs code cloning, copies the code information in the software warehouse to each project developer client, and completes network access; the project developer completes code submission, and the open source software block chain service platform completes right and interest allocation according to the contribution code quantity of the project developer so as to realize right and interest confirmation of contribution information corresponding to theproject developer.The code contribution condition of each project developer in the open source software project development process can be recorded into the blockchain network in a non-tamperable form, so that the conversion from the code contribution amount of each project developer to rights and interests is realized, and effective protection is formed.
Owner:NAT UNIV OF DEFENSE TECH
Code clone detection optimization method and device based on knowledge graph and electronic equipment
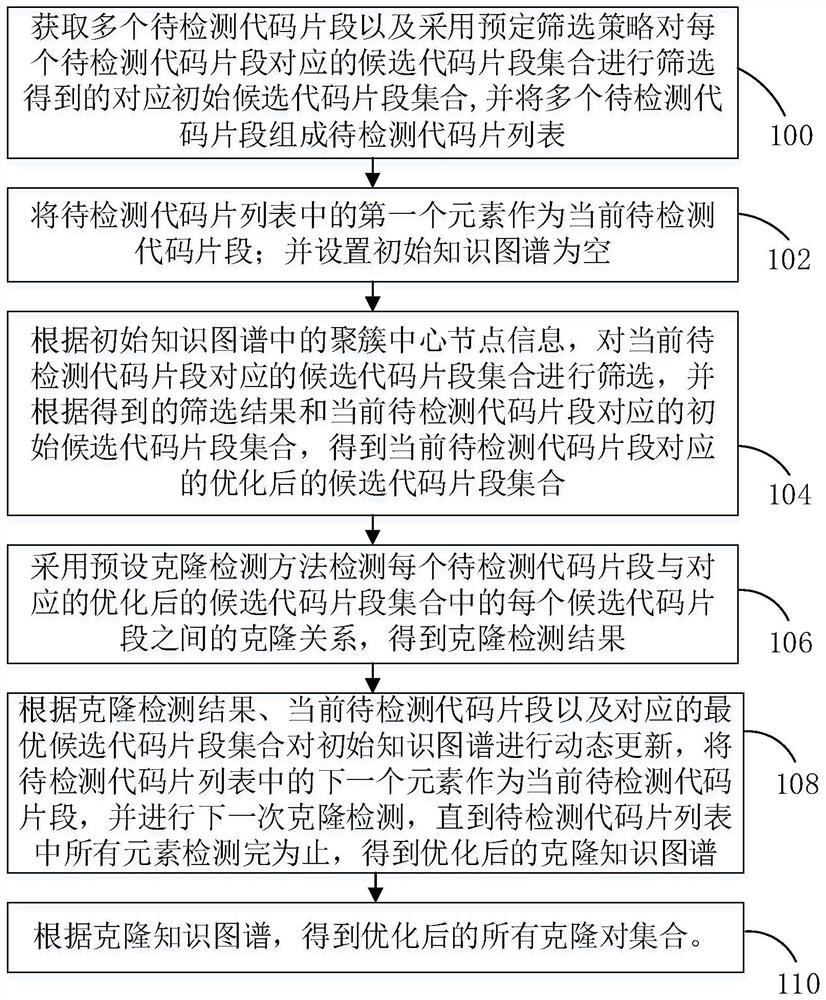
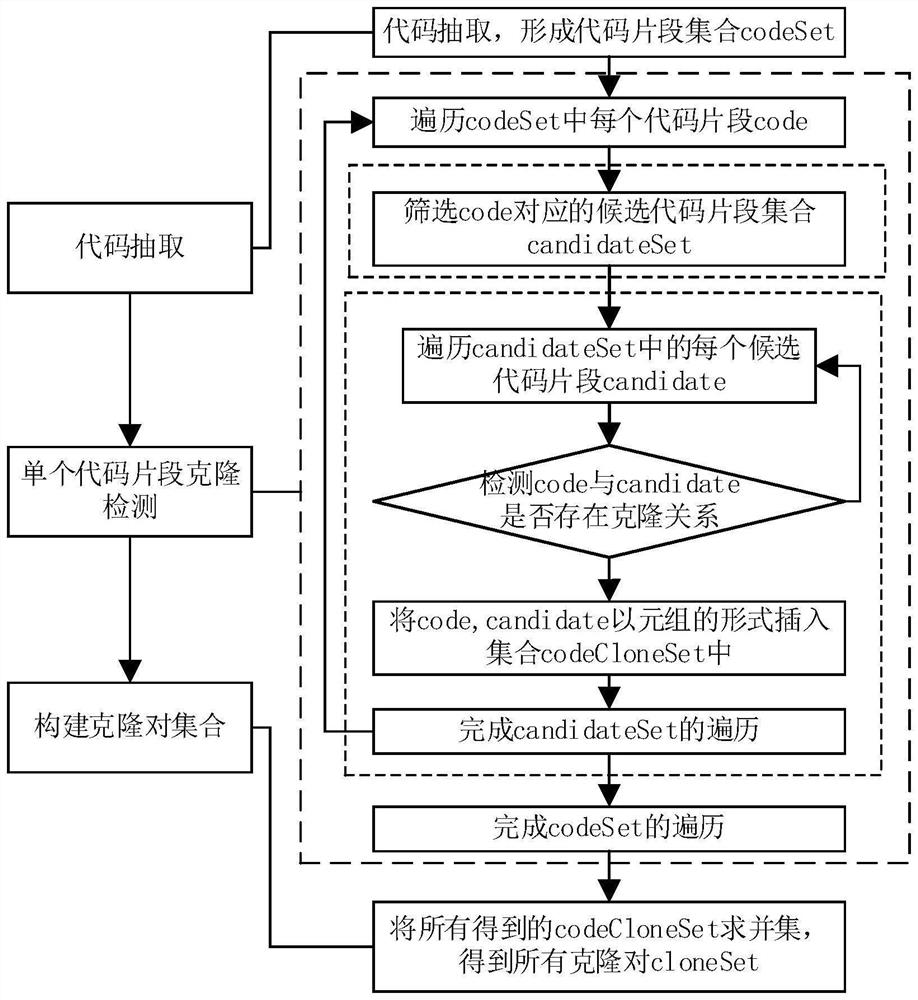
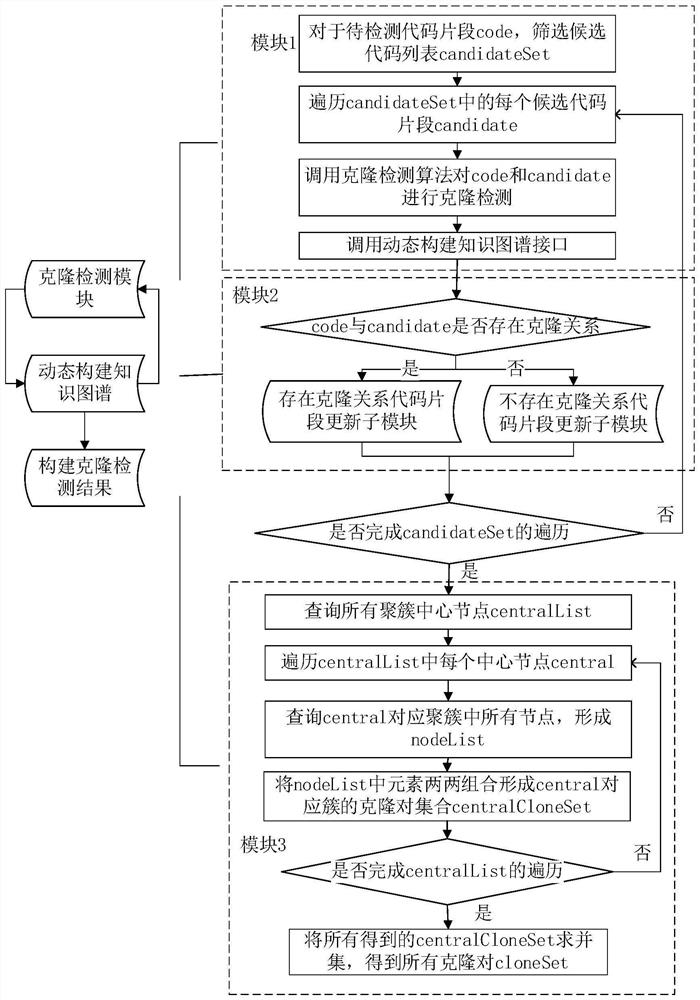
PendingCN114138330ANo dependencyReverse engineeringSpecial data processing applicationsCode snippetAlgorithm
The invention relates to a code clone detection optimization method and device based on a knowledge graph and electronic equipment. The method comprises the following steps: obtaining a plurality of to-be-detected code snippets, and screening corresponding candidate code snippet sets by adopting a predetermined screening strategy to obtain corresponding initial candidate code snippet sets; screening the initially selected code snippets by utilizing knowledge of the knowledge graph to obtain an optimized candidate code snippet set; detecting a clone relationship between each to-be-detected code snippet and each candidate code snippet in the corresponding optimized candidate code snippet set by adopting a preset clone detection method, and constructing an optimized clone knowledge graph according to an obtained clone detection result; and obtaining all optimized clone pair sets according to the clone knowledge graph. According to the method, an existing clone detection method is not modified, the accuracy of the original clone detection method is not changed, meanwhile, the method does not depend on development languages, and the method can be suitable for all existing clone detection methods.
Owner:NAT UNIV OF DEFENSE TECH
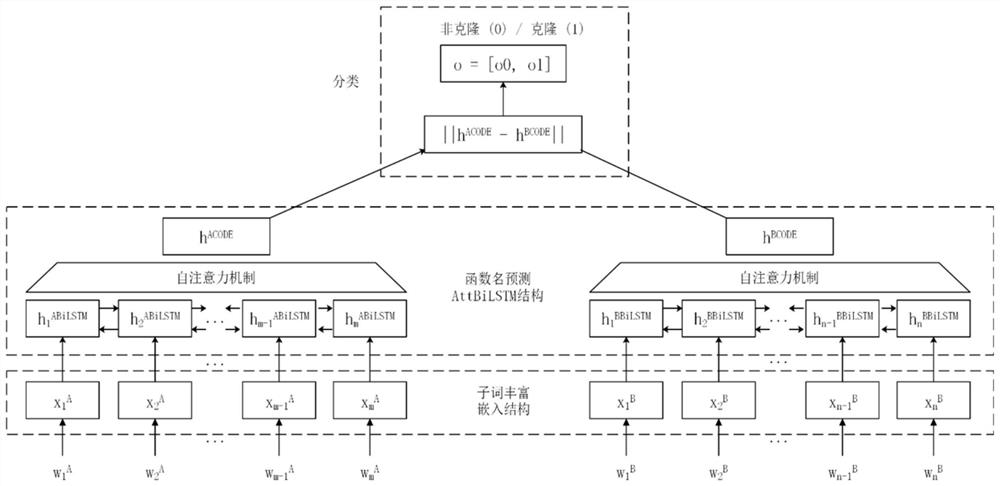
Pre-training enhanced code clone detection method
PendingCN113986345AImprove accuracySolve the OOV problemCharacter and pattern recognitionReverse engineeringData setCode snippet
The invention discloses a pre-training enhanced code clone detection method, which comprises the following steps of: (1) performing word vector training on words by using a sub-word enriching method, and better representing words outside a word list at the same time; (2) acquiring semantic information of a function fragment by predicting a pre-training task by using a function name, so that the dependence on a labeled data set is reduced; (3) performing fine adjustment on the clone detection model by using a small amount of labeled data so as to achieve a better effect. (4) Through learning the semantics of the code snippets, a better classification effect is achieved.
Owner:TIANJIN UNIV
Code clone detection method and application based on abstract syntax tree and token
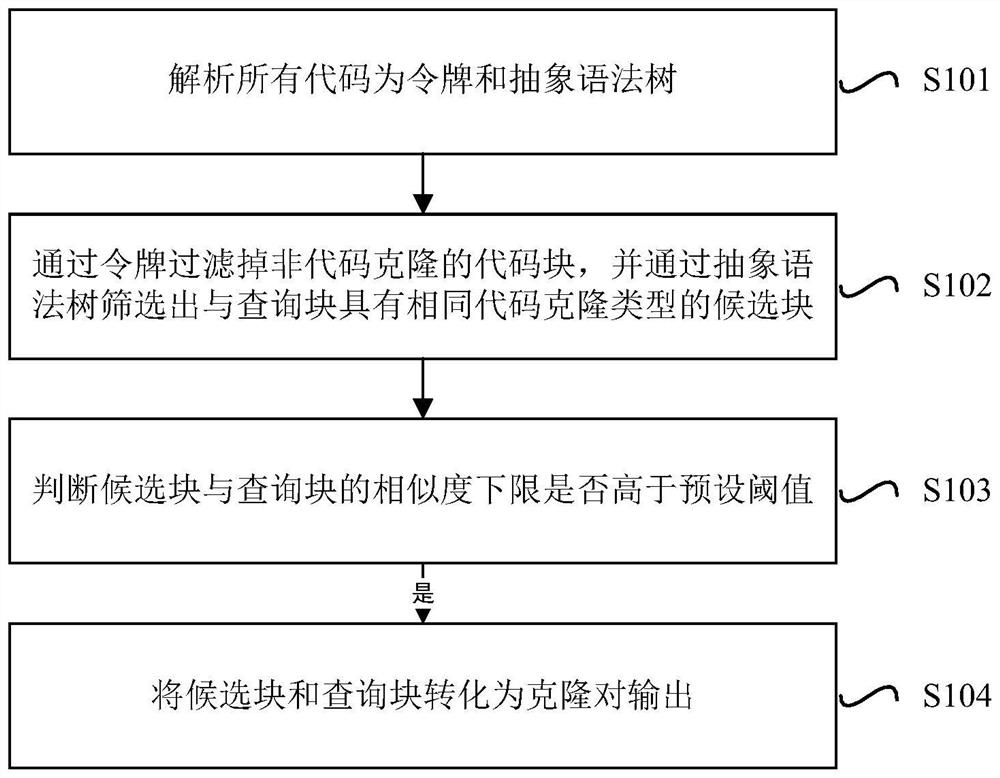
PendingCN114816519ANarrow down the candidatesImprove judgment efficiencyReverse engineeringText database indexingCoding blockLower limit
The invention discloses a code clone detection method and application based on an abstract syntax tree and a token. The method comprises the following steps: analyzing all codes into the token and the abstract syntax tree; non-code cloning code blocks are filtered out through the token, and candidate blocks with the same code cloning type as the query block are screened out through the abstract syntax tree; judging whether the similarity lower limit of the candidate block and the query block is higher than a preset threshold value or not; and if yes, converting the candidate block and the query block into a clone pair and outputting the clone pair. According to the method, the non-code cloned code blocks can be filtered through the tokens of the code blocks and the abstract syntax tree, the candidate range can be narrowed, the judgment efficiency of the similarity between the code snippets when different cloning types are judged is improved, and then the judgment accuracy is improved.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
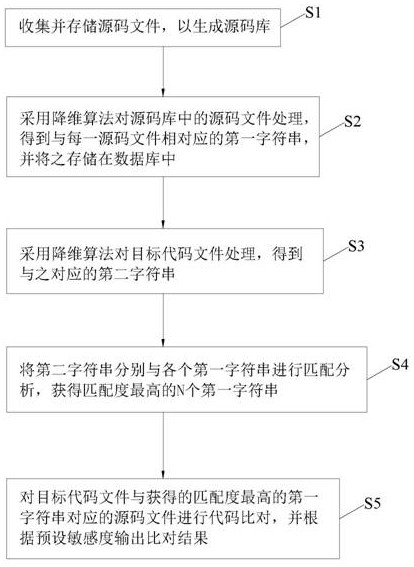
Source code clone identification method and system
InactiveCN112698861AImprove recognition accuracyImprove detection efficiencySoftware maintainance/managementSource code fileObject code
The invention discloses a source code clone identification method and system, and the method comprises the following steps: firstly collecting a source code file, and generating a source code library; secondly, respectively processing each source code file in the source code library by adopting a dimension reduction algorithm to generate a plurality of first character strings; then, processing the target code file by adopting a dimension reduction algorithm to generate a second character string; then, respectively performing matching analysis on the second character string and the plurality of first character strings to obtain N first character strings with the highest matching degree; and finally, comparing the target code file with the codes in the source code files corresponding to the previous N first character strings. By means of the source code cloning recognition method, the N open source code files with high similarity can be rapidly screened out from the massive source code library, then code comparison only needs to be conducted on the N open source code files one by one, and therefore cloning codes can be recognized and detected from the code level, the recognition accuracy is high, and the detection efficiency is effectively improved.
Owner:SECZONE TECH CO LTD
Code clone detection method and device based on event embedding tree and GAT network
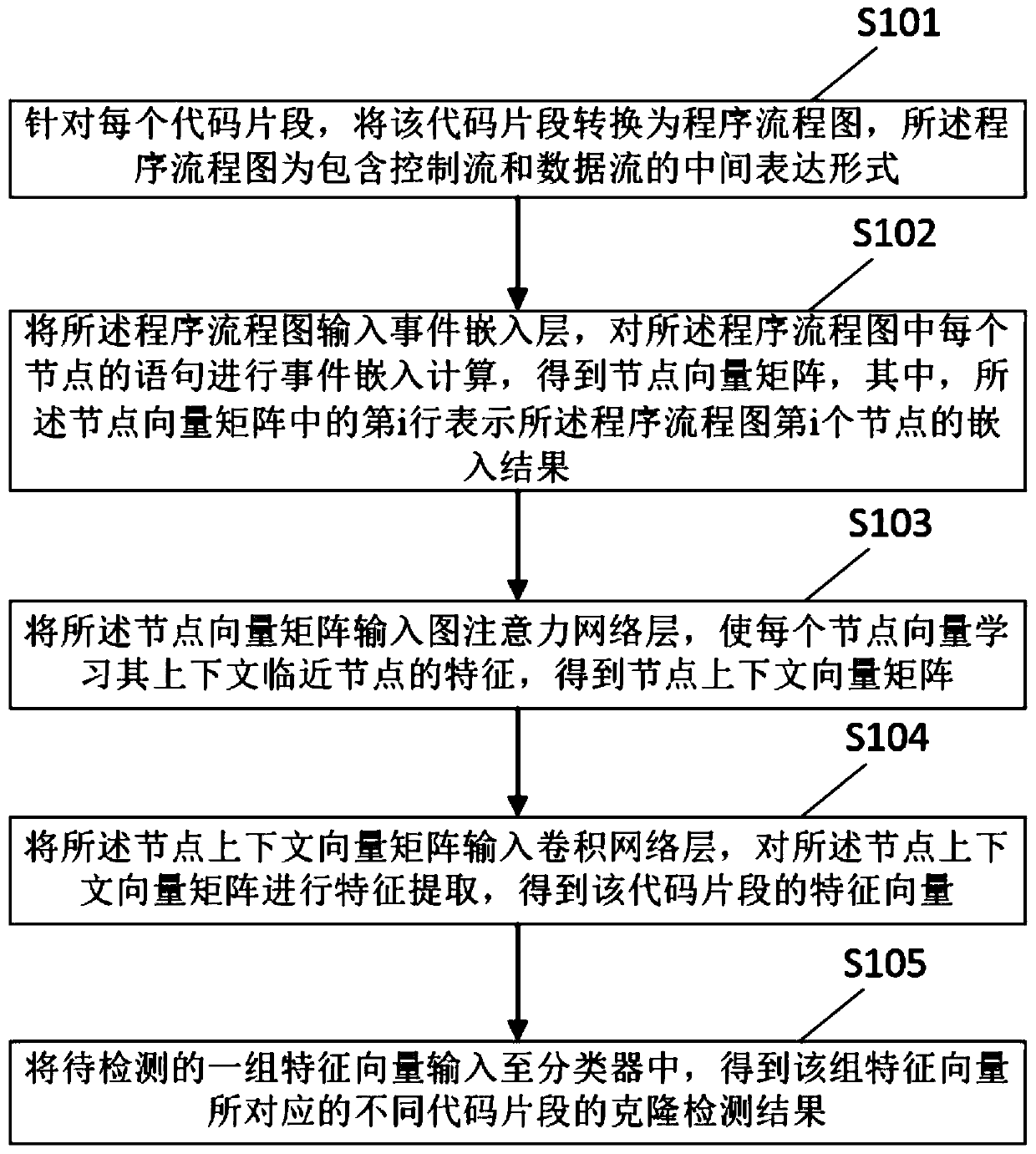
ActiveCN111562943AJudgment results are comprehensive and accurateReverse engineeringNeural architecturesCode snippetAlgorithm
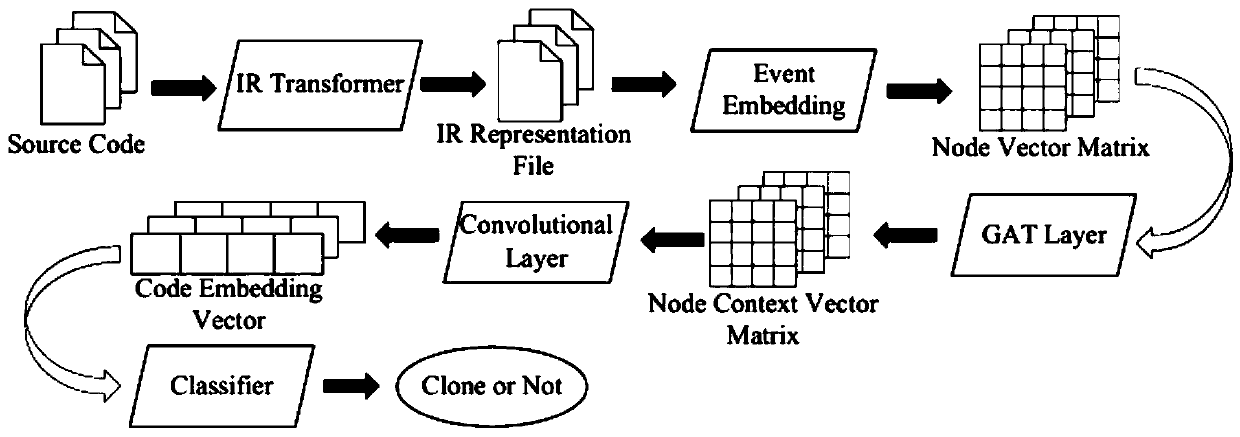
The invention relates to a code cloning detection method and device based on an event embedding tree and a GAT network. The code cloning detection method based on the event embedding tree and the GATnetwork includes: converting a source code into a flow chart corresponding to the source code, and describing the flow chart by using a self-defined IR intermediate representation text; carrying out event embedding calculation on the statement of each node in the IR through an event embedding layer (Event Embeddinhg) to obtain a node vector matrix (Node Vector Matrix); adjusting and fusing an event embedding vector of each node of the node vector matrix through a GAT attention network, so as to enabling the event embedding vector to sense event embedding semantics of context nodes, and obtaining a node context matrix (Node Context Vector Matrix); performing convolution calculation on each node in the node context matrix by using a convolution layer so as to extract final vector representation of the program flow chart; using the vector representation to determine whether the two code snippets are a cloned code pair by a classifier (classifier).
Owner:HAINAN UNIVERSITY
Cost computation device, cost computation method, and computer-readable recording medium
Owner:NEC SOLUTION INNOVATORS LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com