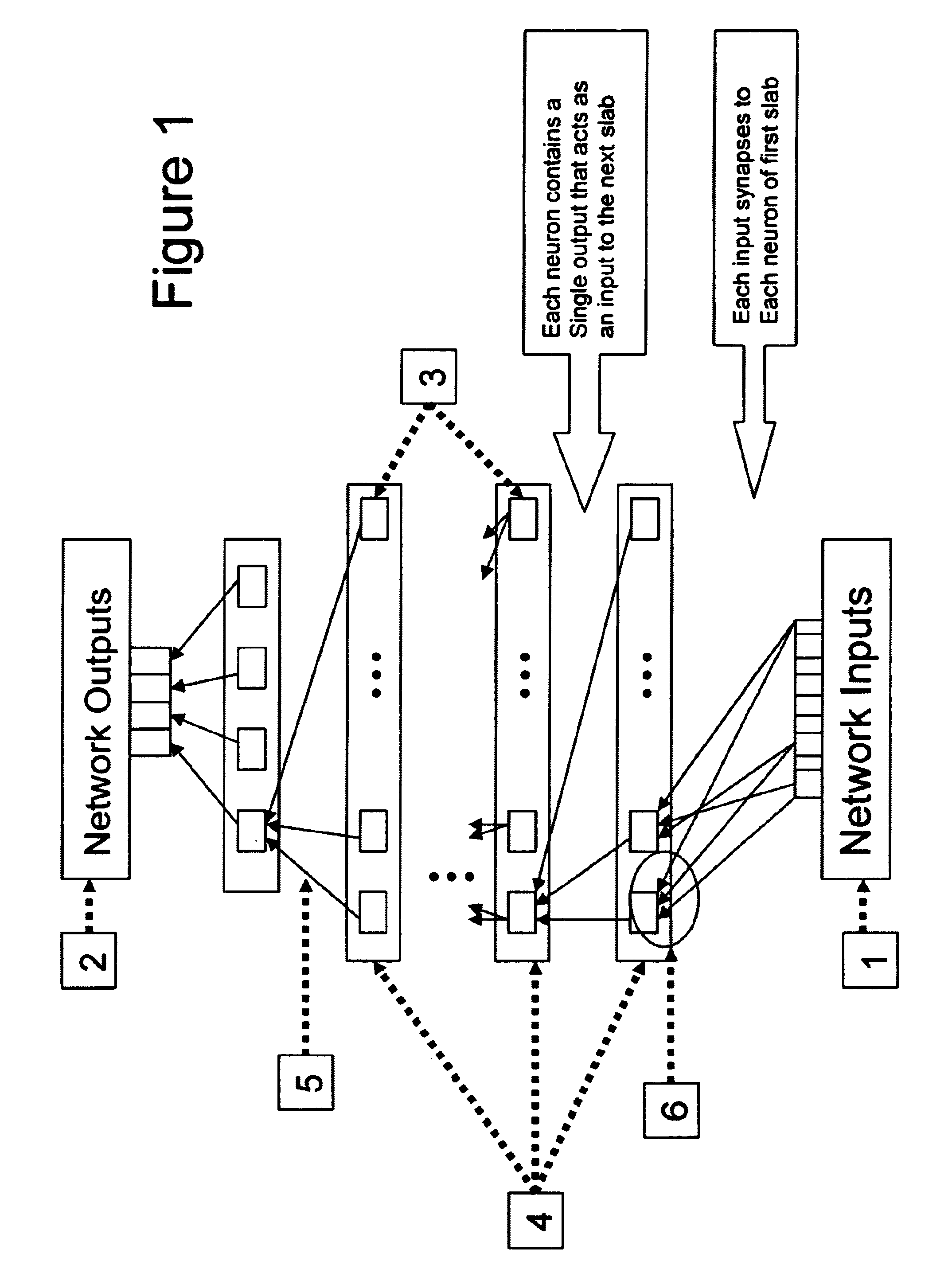
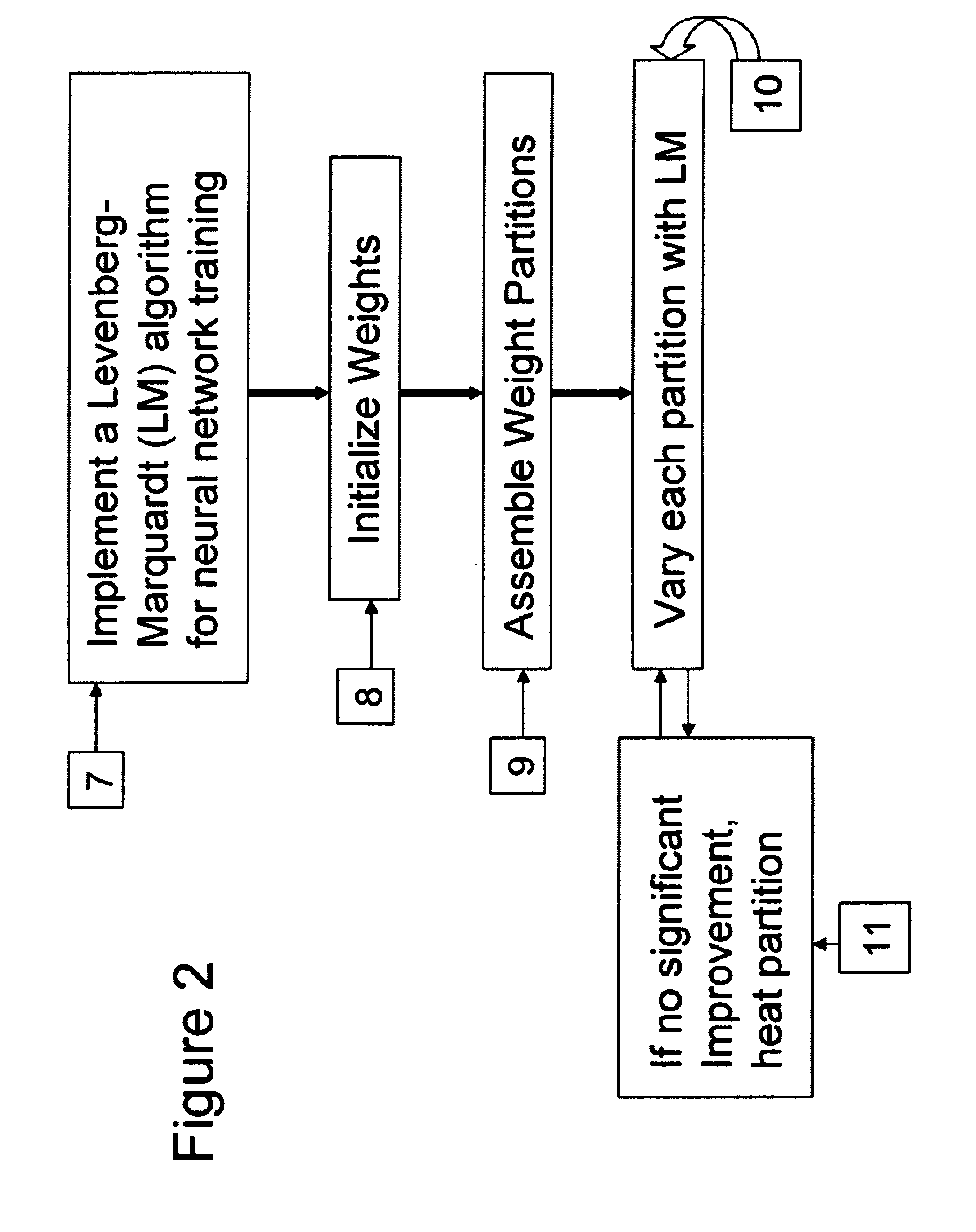
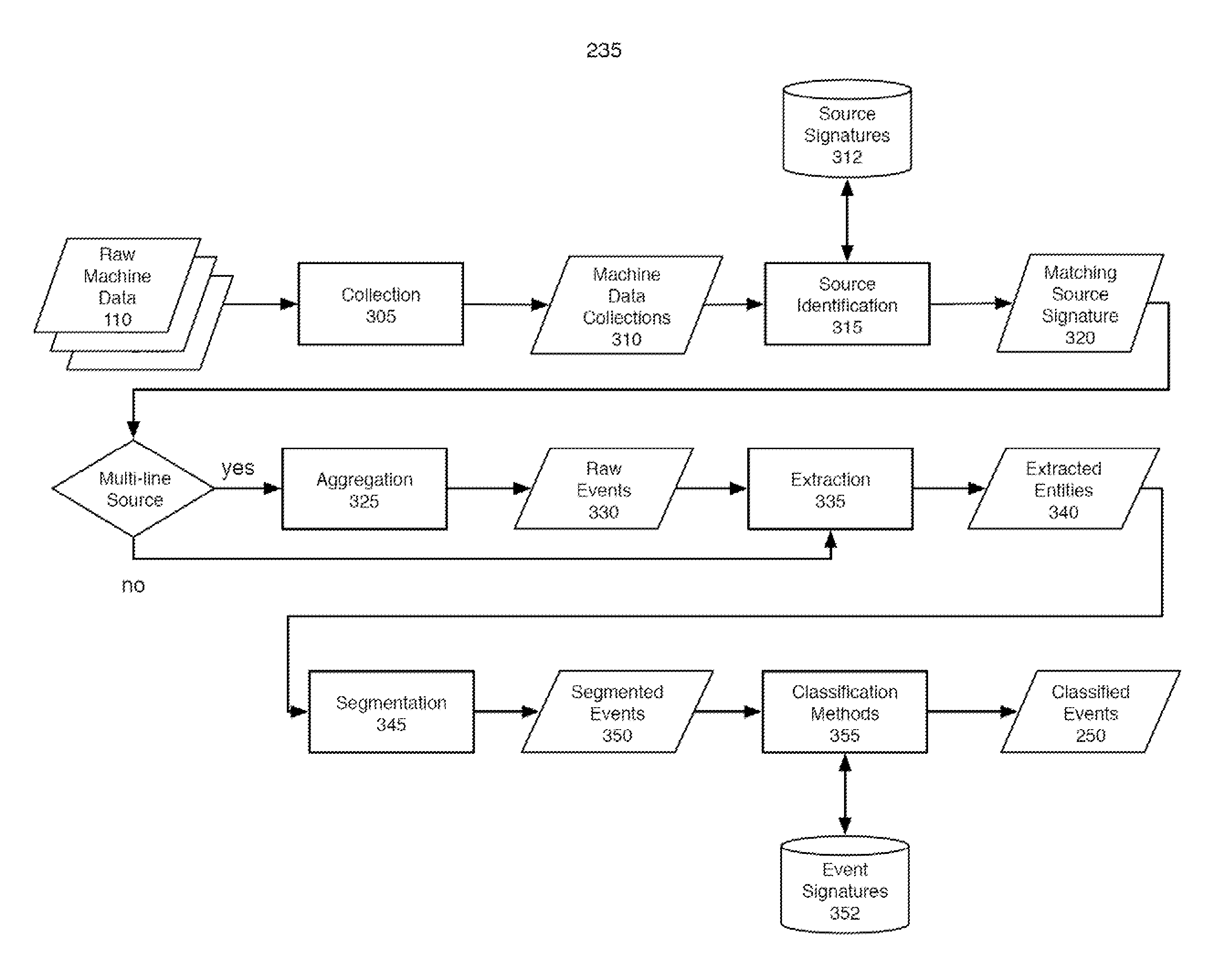
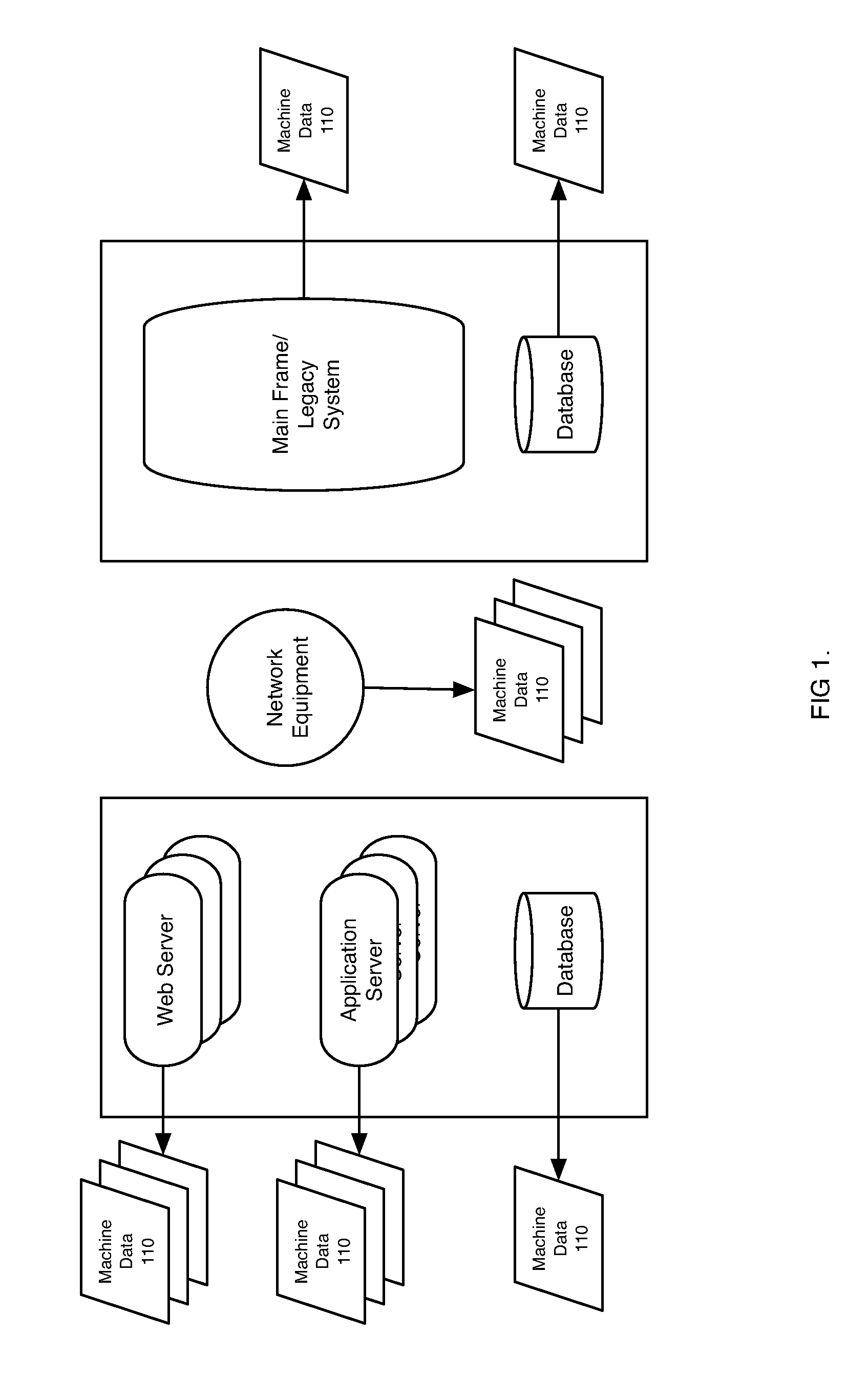
Patents
Literature
4041results about "Electric/magnetic computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
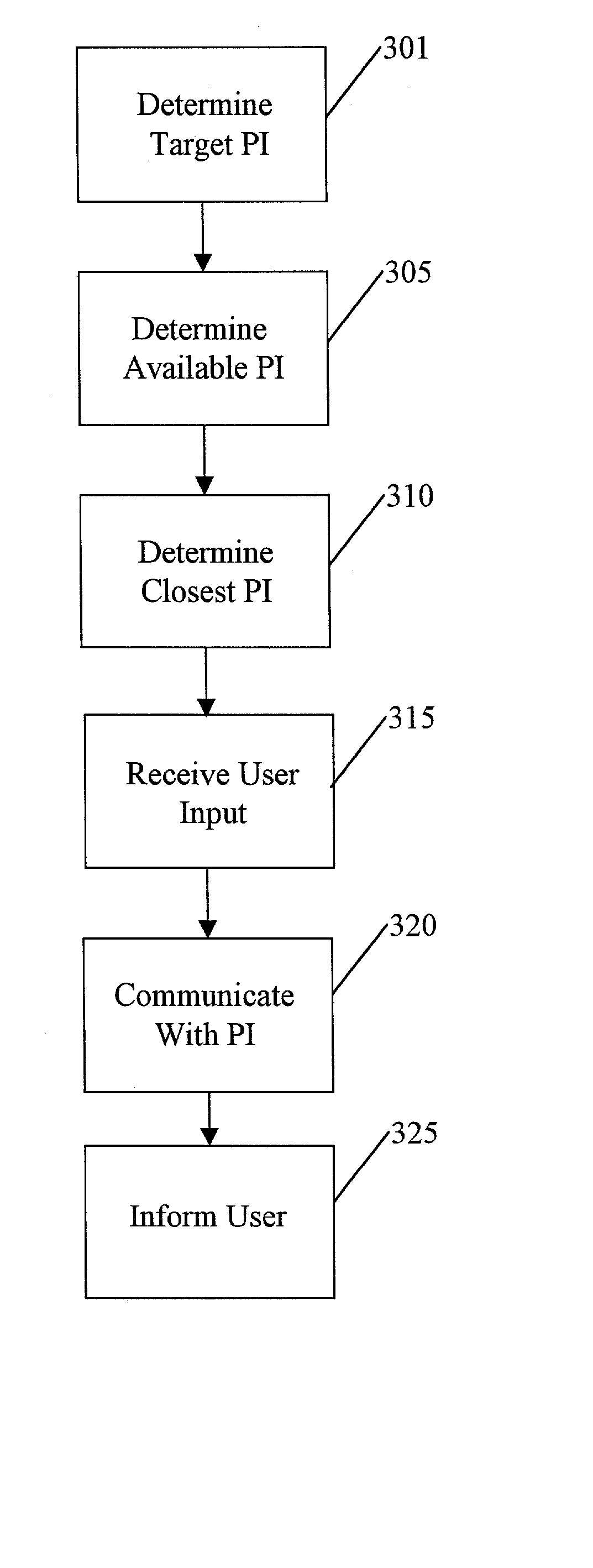
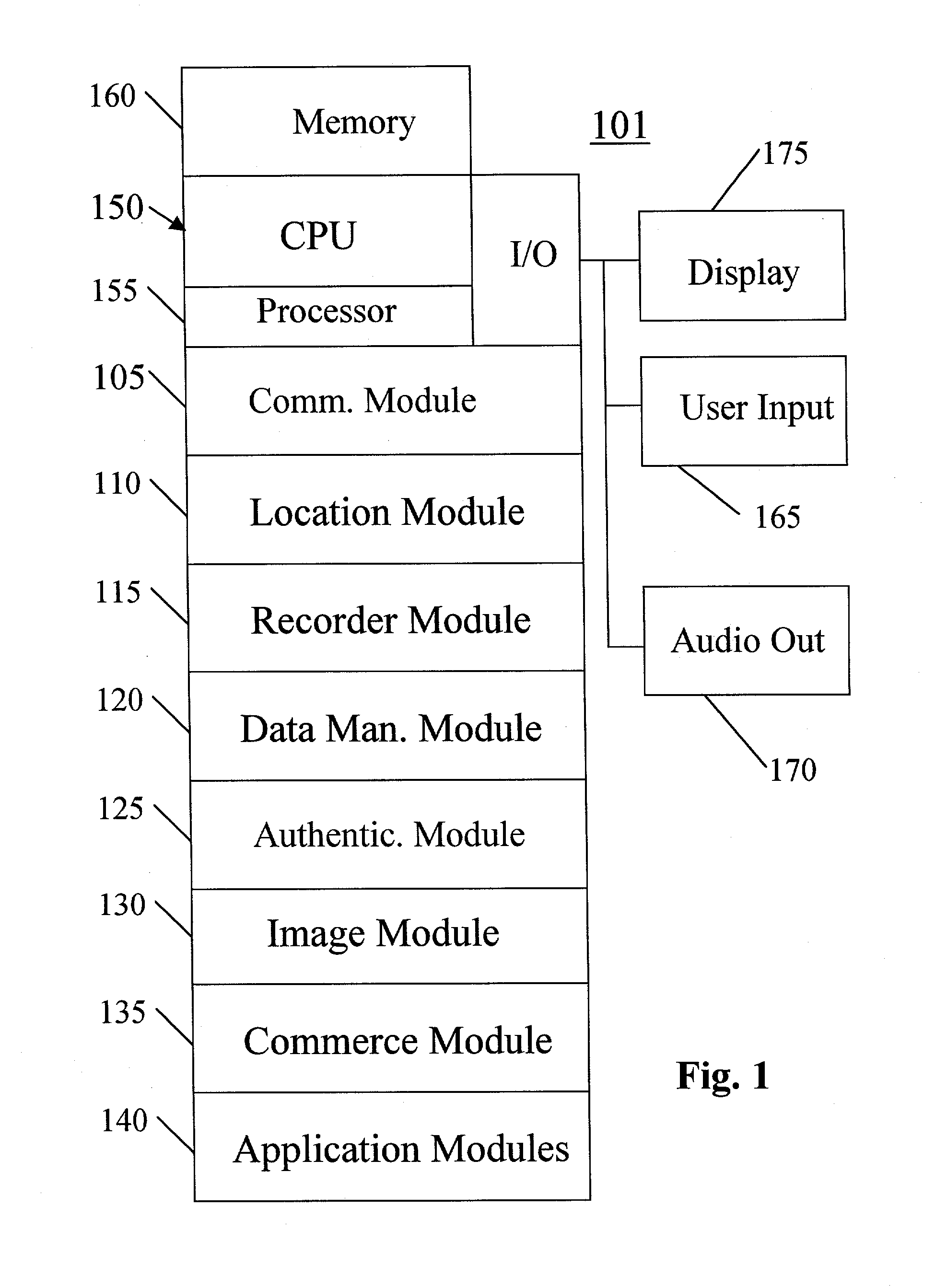
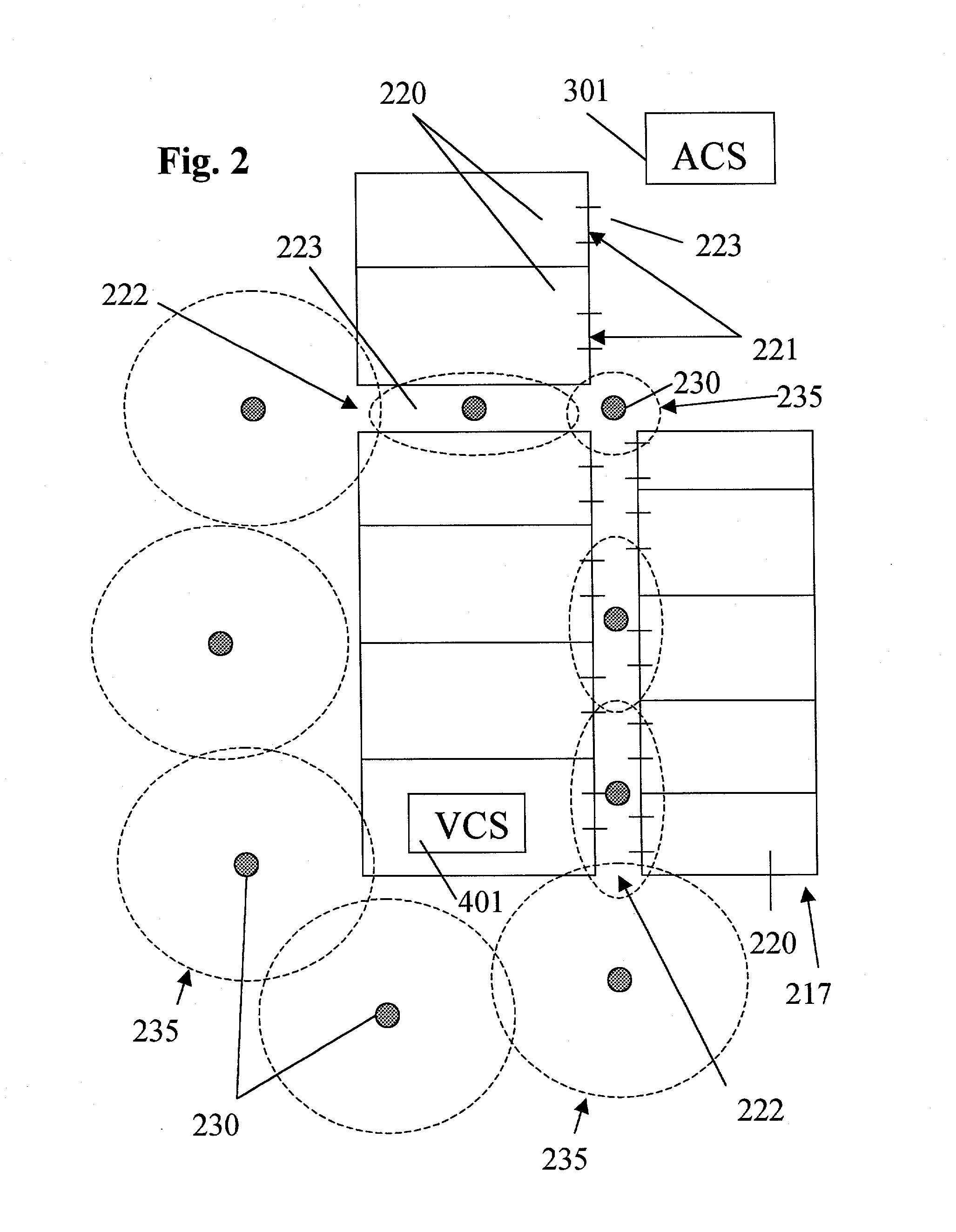
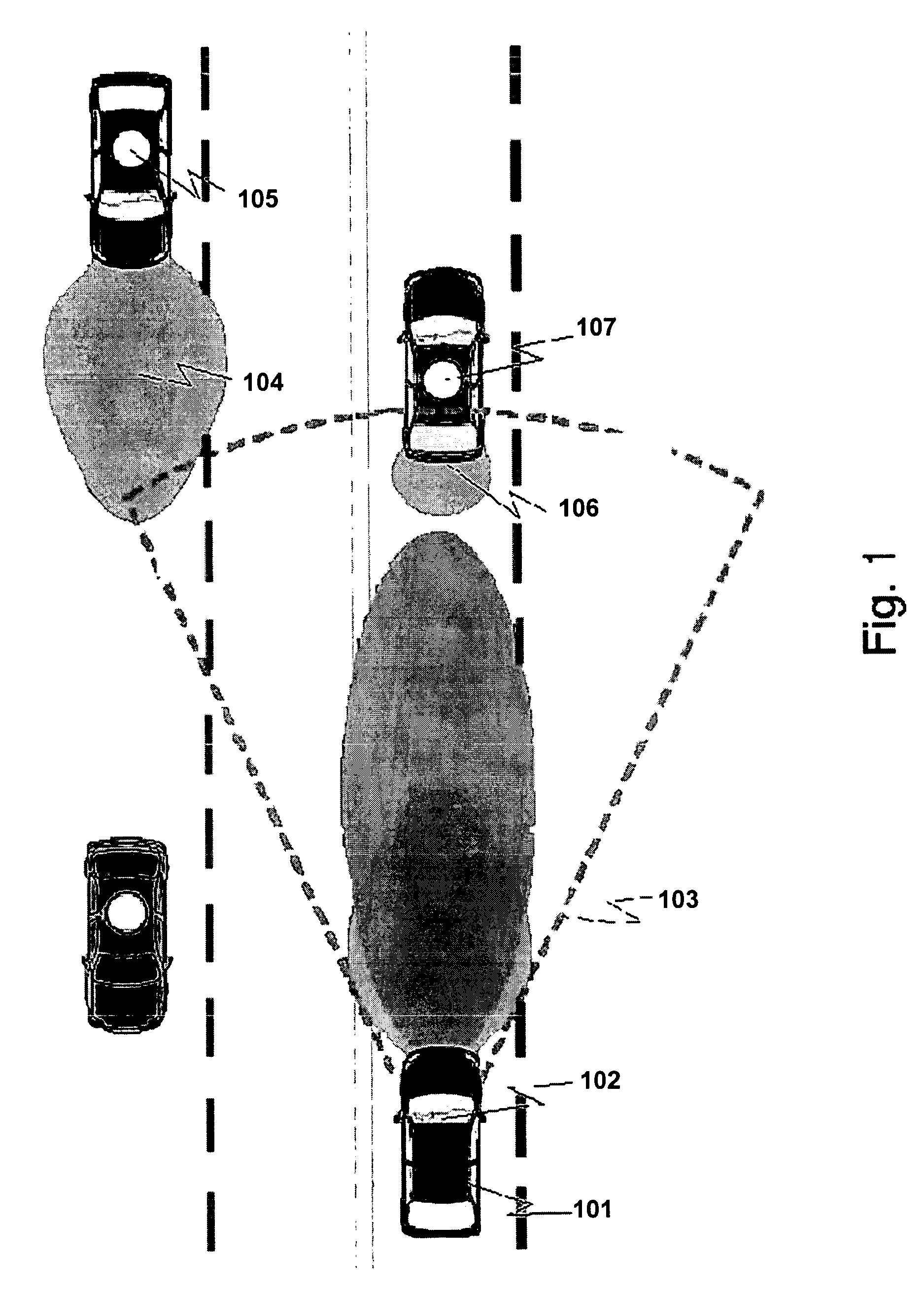
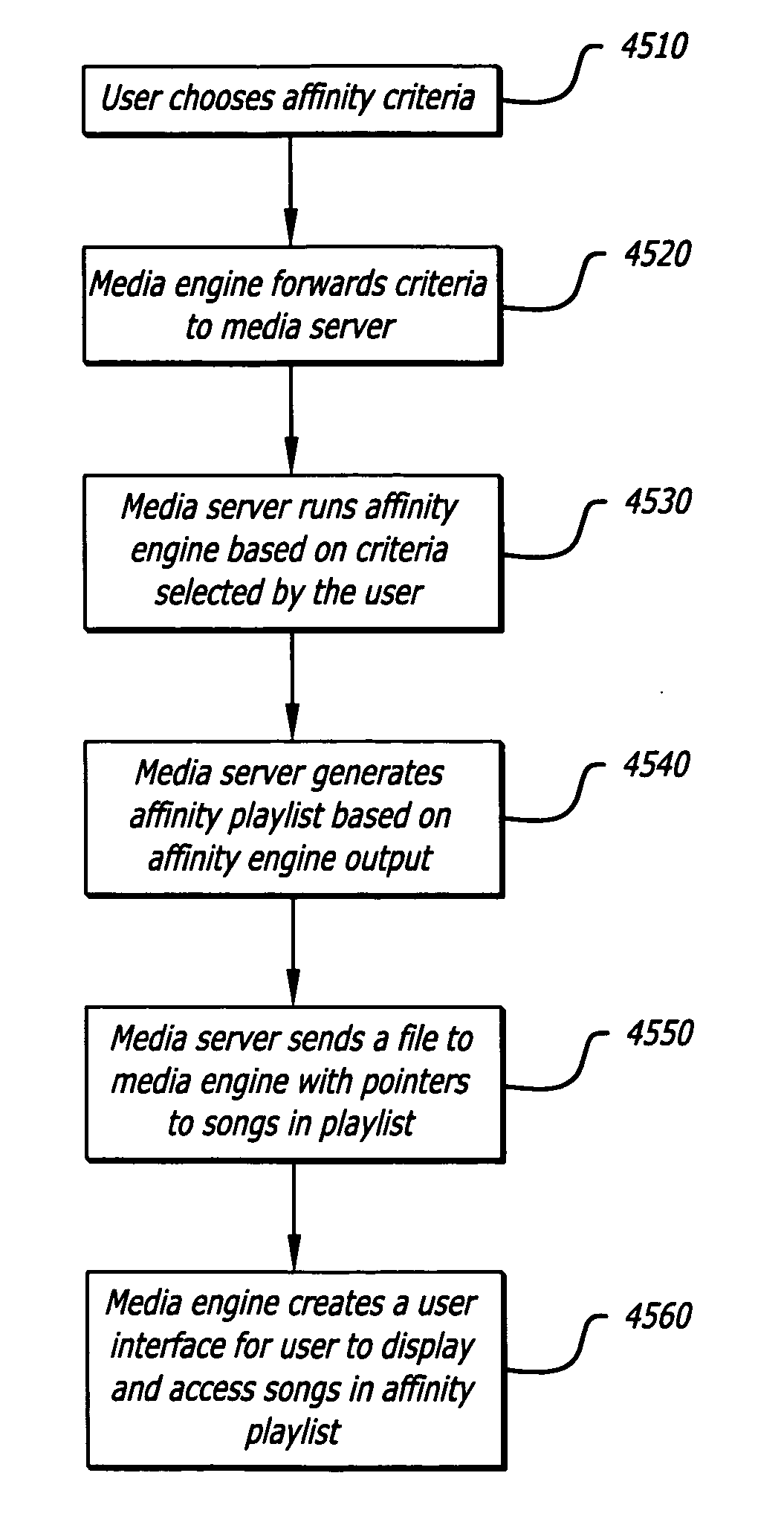
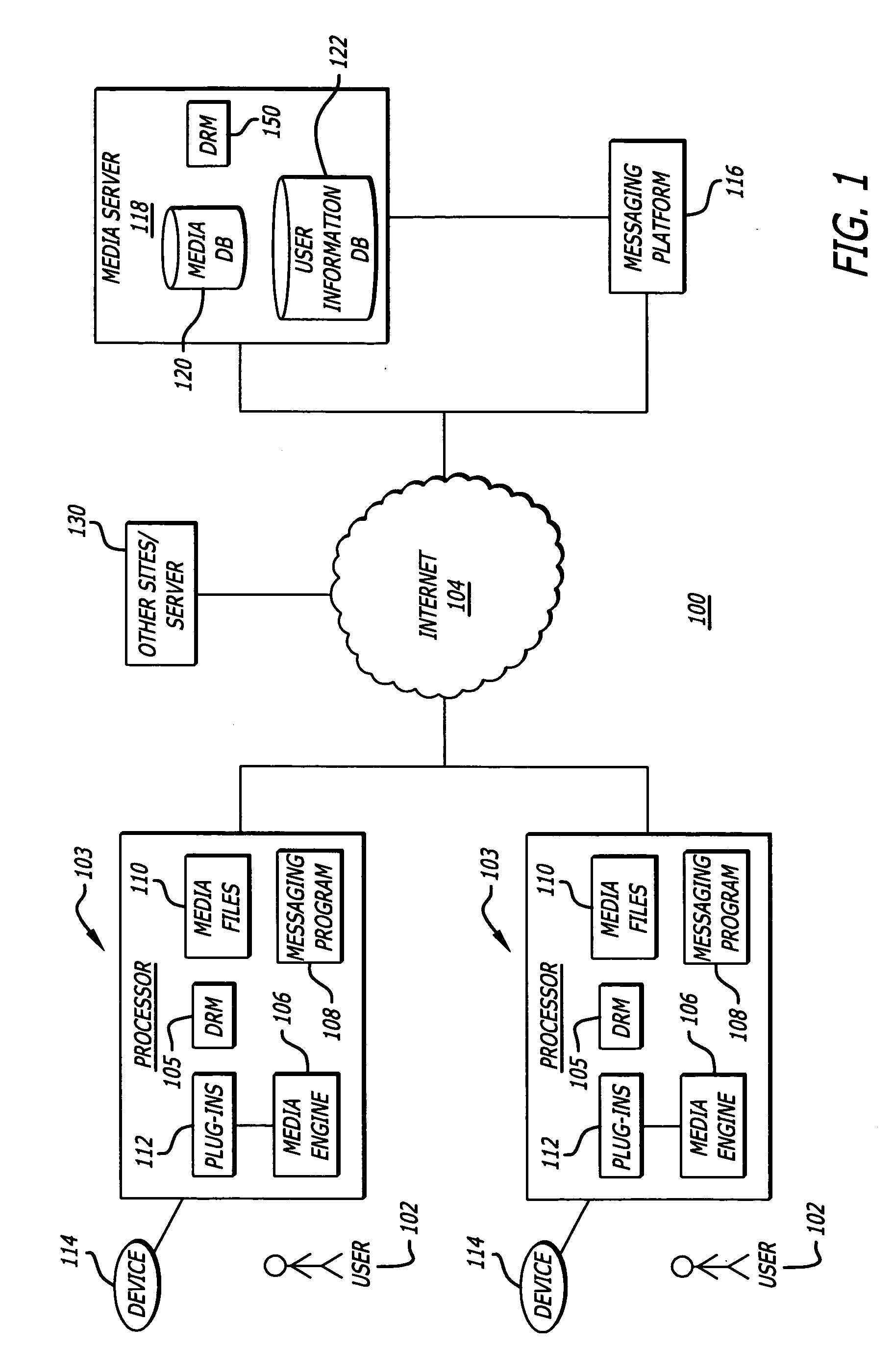
System, method, and computer program product for providing location based services and mobile e-commerce
ActiveUS20030065805A1Facilitating localized e-commerceFacilitate communicationTelevision system detailsColor television detailsDisplay deviceData file
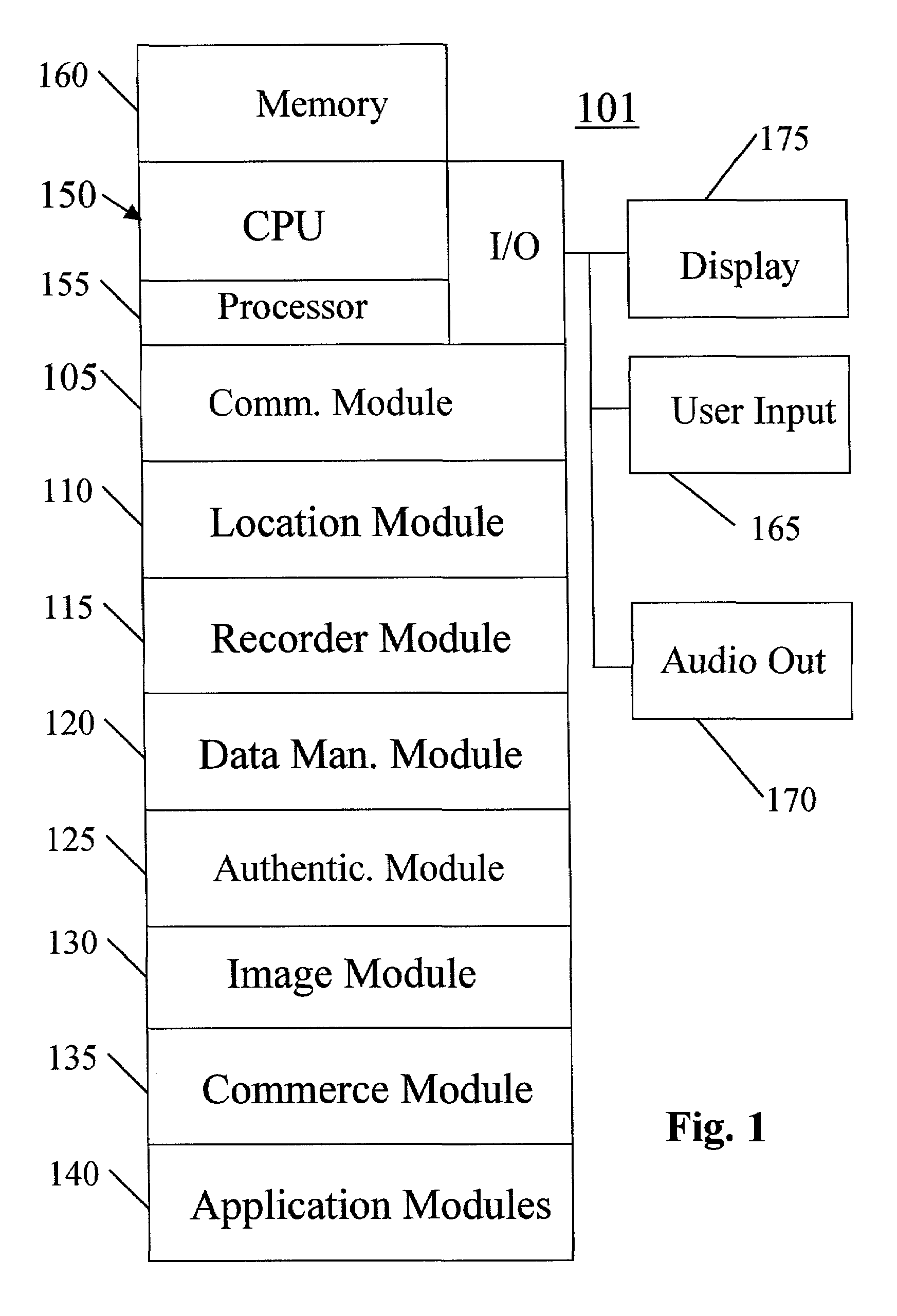
A system, method, apparatus and computer program product for providing location based functions and mobile e-commerce comprising a central processing unit including a processor, a storage device, and programming stored in the storage device, a display device, an audio input device, an audio output device, a communications module, a commerce module, an image module, and a location module. The programming controls the operation of the present invention to provide functions based on location data, to facilitate commercial exchanges by wirelessly exchanging payment and product information with venders, to identify services such as venders meeting selection criteria, to wirelessly exchange select information with other users and systems, to restrict and / or monitor the use of the device based on authorized user parameters, selecting one of a plurality networks through which to communicate, detecting a trigger for performing an action based on a change in location and sensed data, storing a voice annotation with a computer data file, determining service providers and associated communication parameters, contemporaneously maintaining a wireless voice and data link, providing a system for selecting and delivering mobile advertisements, and many other functions and services that are described herein.
Owner:GULA CONSULTING LLC
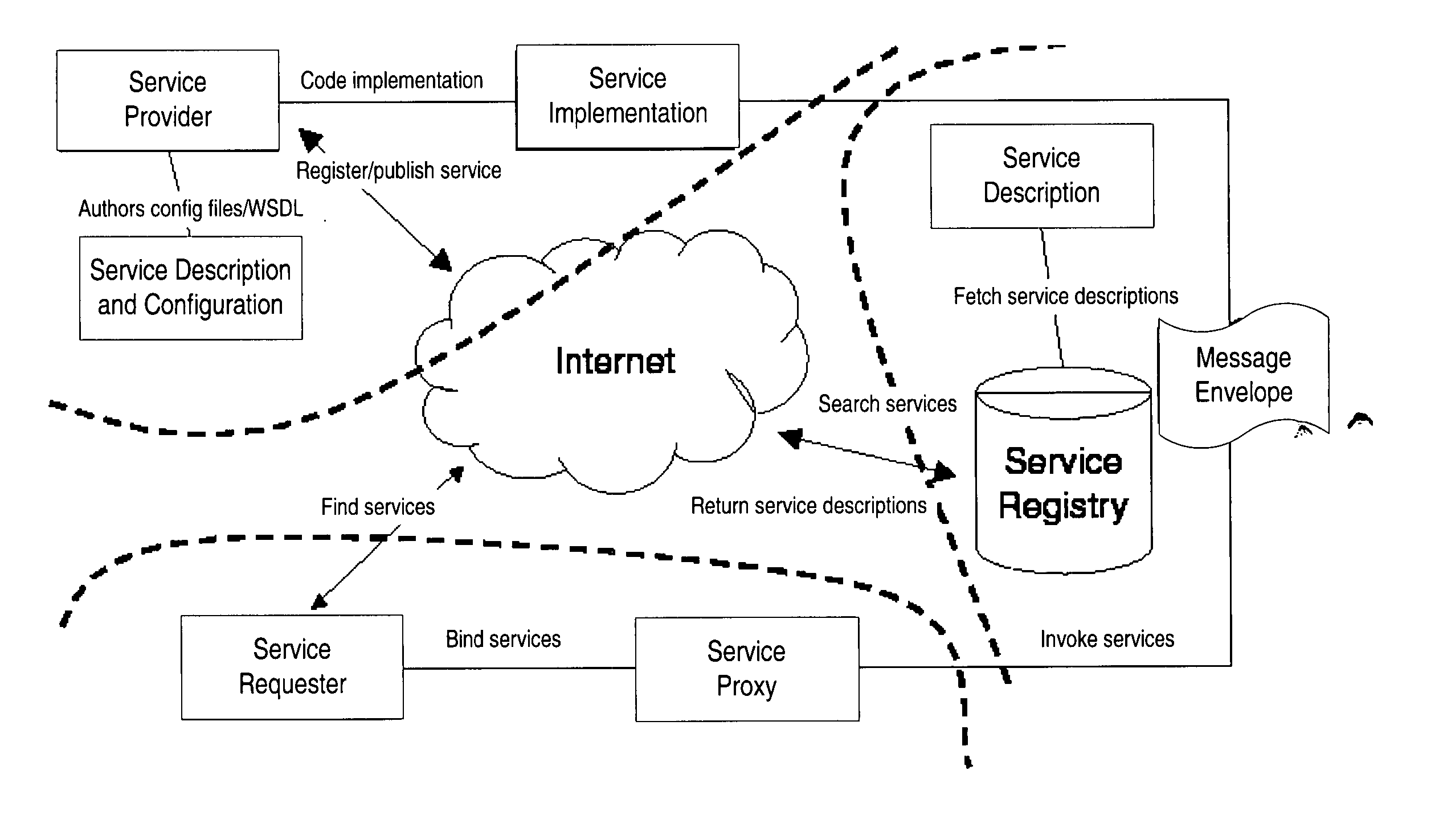
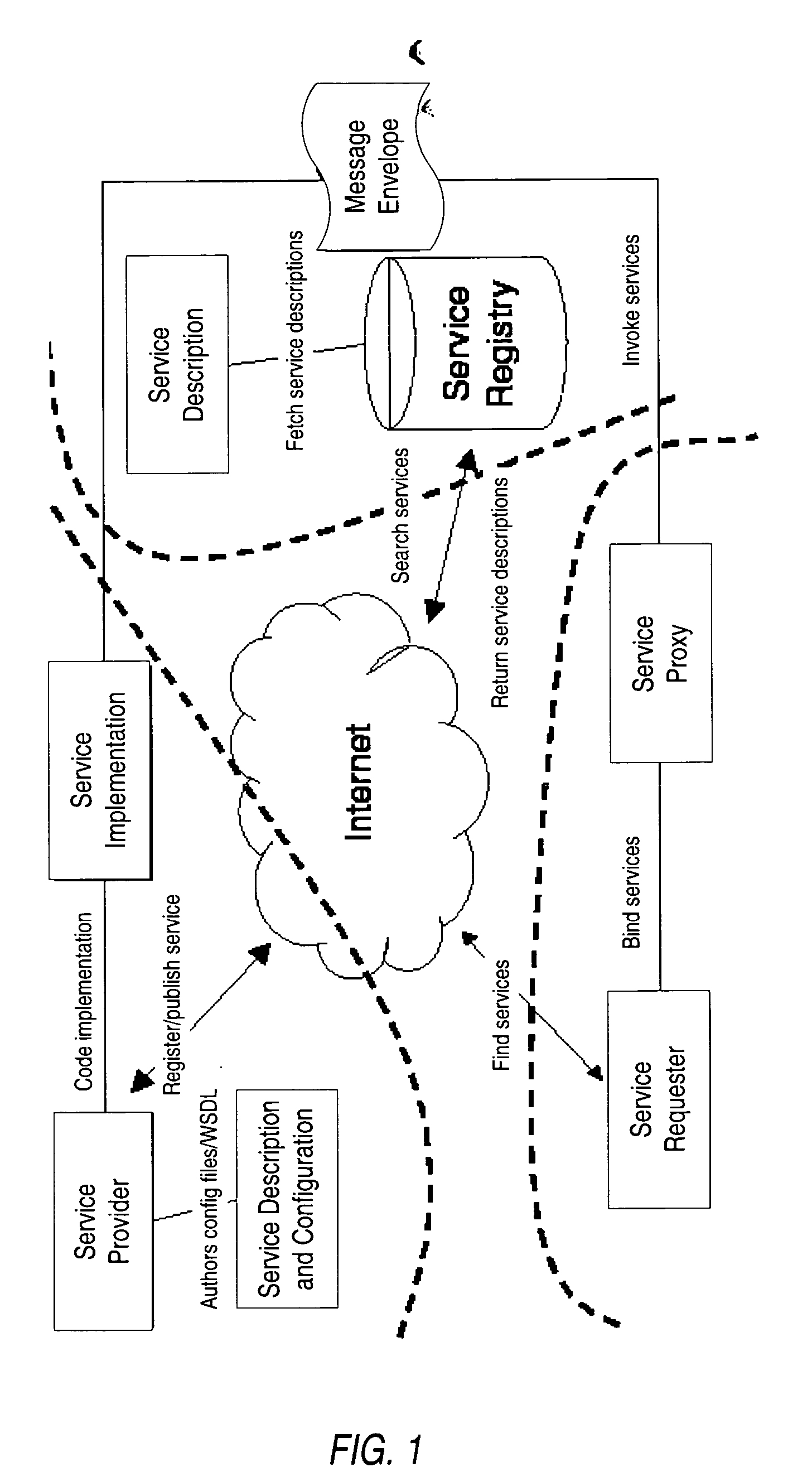
Structured methodology and design patterns for web services
ActiveUS20050044197A1Multiple digital computer combinationsDigital dataQuality of serviceBusiness-to-business
System and method for designing and implementing Web Services according to a structured methodology and design patterns. Embodiments may incorporate a structured methodology, best practices and design patterns that address reliability, availability and scalability of Web Services architecture. Embodiments may provide mechanisms for integrating heterogeneous technology components into Web Services. Embodiments may provide a vendor-independent Web Services architecture framework and reusable Web Services design patterns, which may be used in creating end-to-end solutions based on past experience and best practices. Embodiments may include design patterns and best practices for delivering Web Services solutions with Quality of Services. One embodiment may provide a Business-to-Business Integration (B2Bi) integration framework for Web Services. Embodiments may provide a Web Security framework and design patterns for designing end-to-end Web Services security.
Owner:ORACLE INT CORP
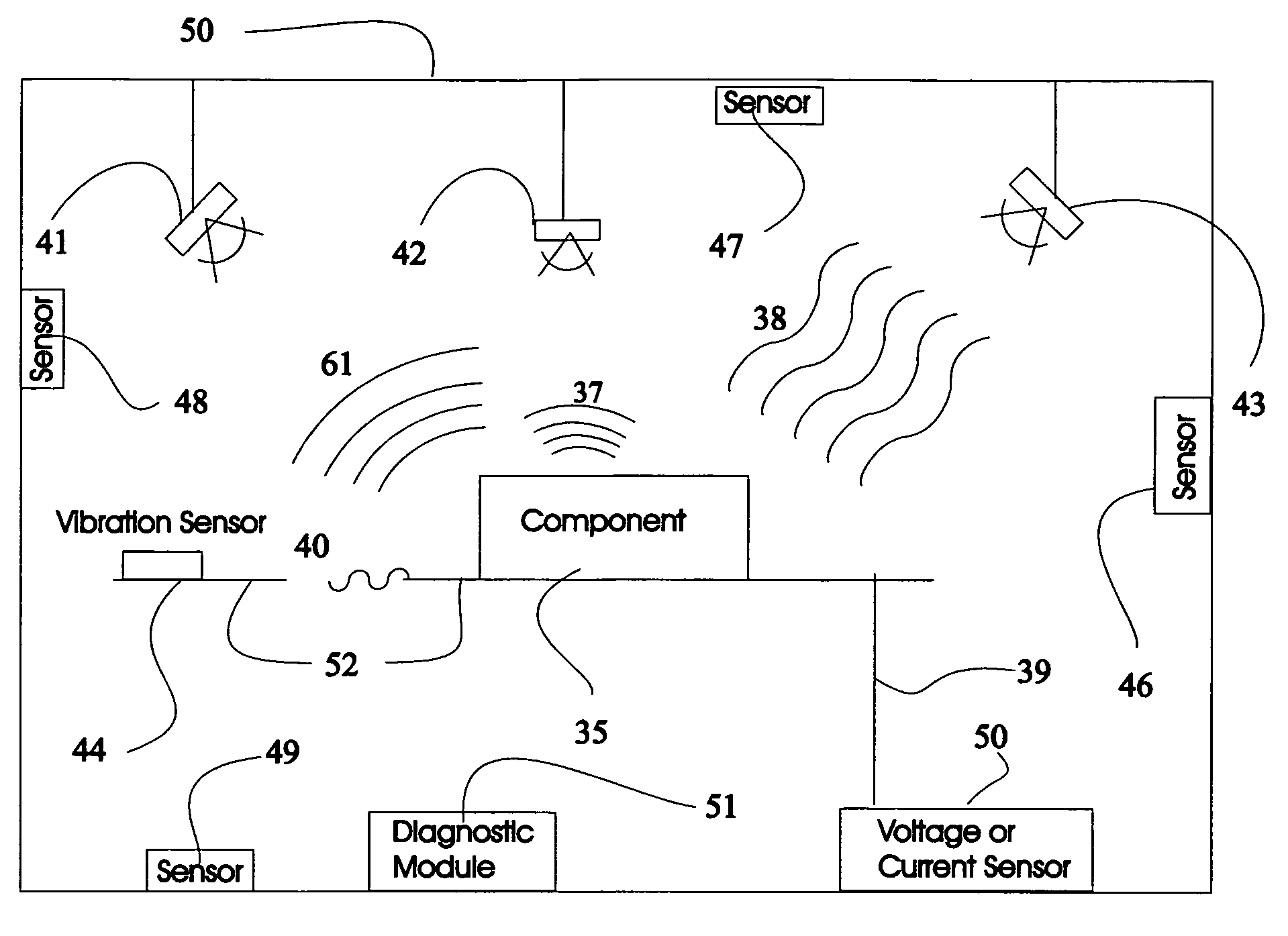
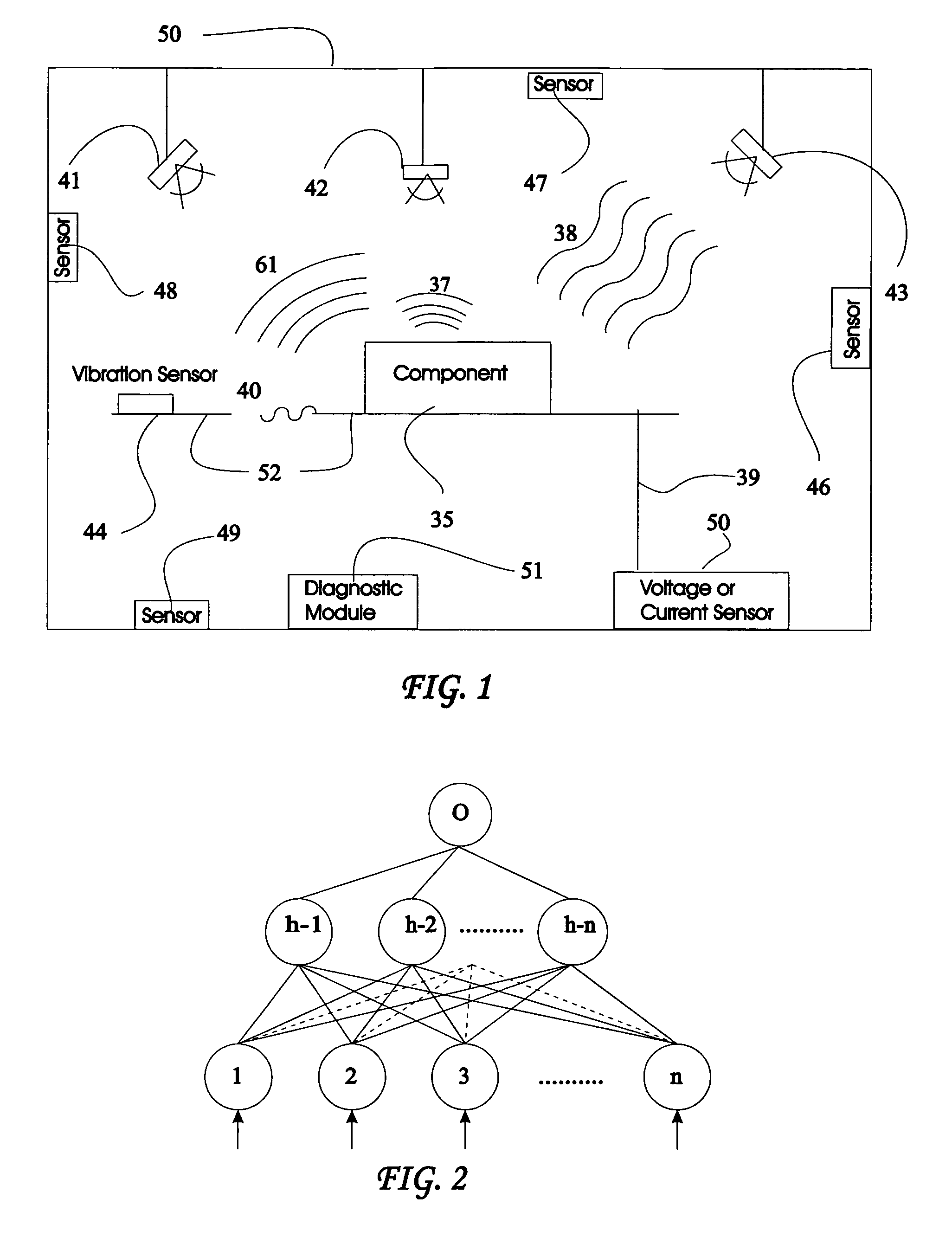
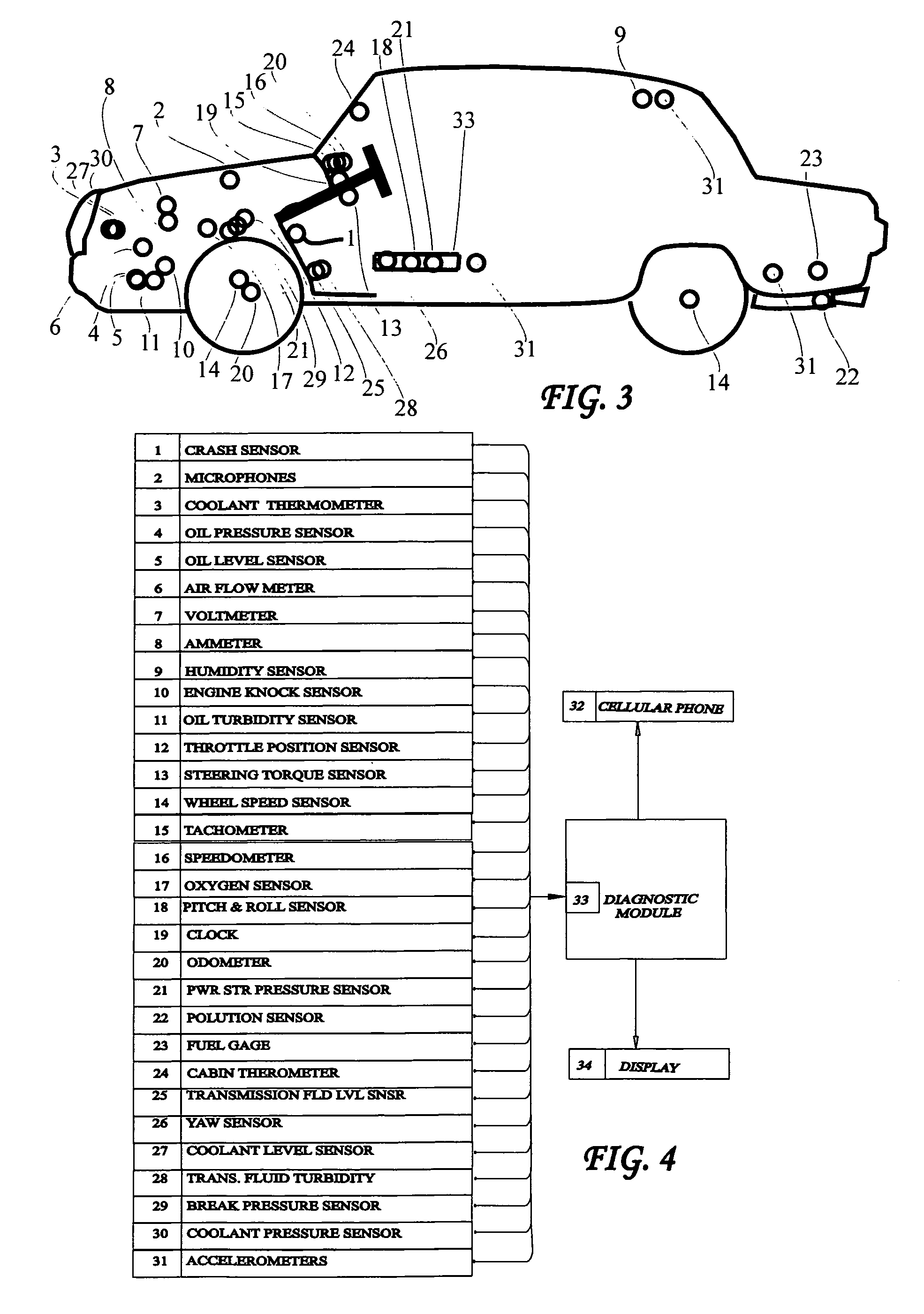
System and method for vehicle diagnostics
InactiveUS7103460B1Low costPrecise positioningVehicle testingRegistering/indicating working of vehiclesReliability engineeringDiagnostic methods
Method and system for diagnosing whether vehicular components are operating abnormally based on data obtained from sensors arranged on a vehicle. In a training stage, output from the sensors during normal operation of the components is obtained, each component is adjusted to induce abnormal operation thereof and output from the sensors is obtained during the induced abnormal operation. A determination is made as to which sensors provide data about abnormal operation of each component based on analysis of the output from the sensors during normal operation and during induced abnormal operation of the components. During operation of the vehicle, the output from the sensors is obtained and analyzed, e.g., by inputting it into a pattern recognition algorithm or neural network generated during the training stage, in order to output an indication of abnormal operation of any components being diagnosed.
Owner:AMERICAN VEHICULAR SCI
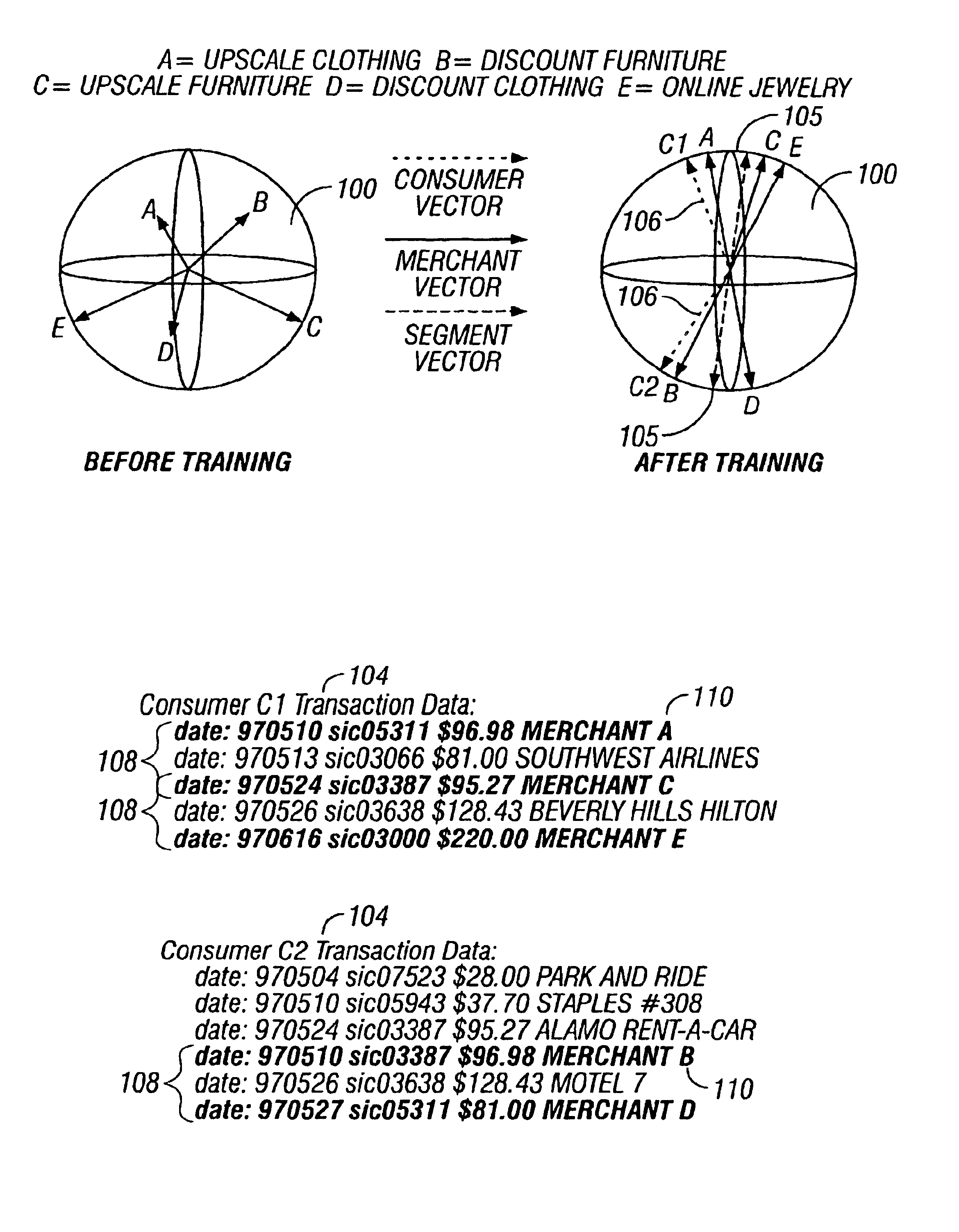
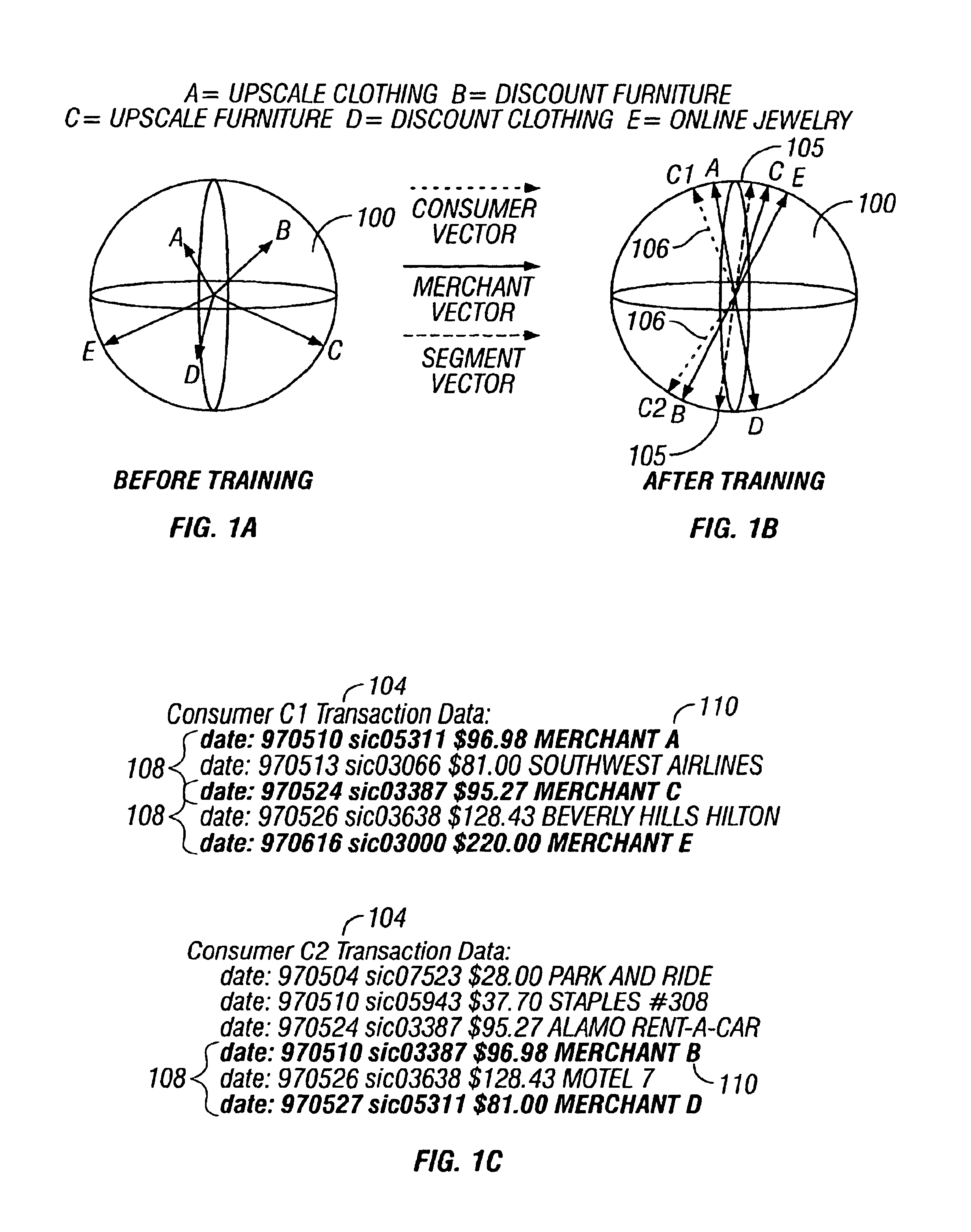
Predictive modeling of consumer financial behavior using supervised segmentation and nearest-neighbor matching
InactiveUS6839682B1Specific accurate targetingIncrease valueDiscounts/incentivesDigital computer detailsPredictive modellingAlgorithm
Predictive modeling of consumer financial behavior, including determination of likely responses to particular marketing efforts, is provided by application of consumer transaction data to predictive models associated with merchant segments. The merchant segments are derived from the consumer transaction data based on co-occurrences of merchants in sequences of transactions. Merchant vectors represent specific merchants, and are aligned in a vector space as a function of the degree to which the merchants co-occur more or less frequently than expected. Consumer vectors are developed within the vector space, to represent interests of particular consumers by virtue of relative vector positions of consumer and merchant vectors. Various techniques, including clustering, supervised segmentation, and nearest-neighbor analysis, are applied separately or in combination to generate improved predictions of consumer behavior.
Owner:CALLAHAN CELLULAR L L C
System, method, and computer program product for providing location based services and mobile e-commerce
ActiveUS7487112B2Facilitate communicationTelevision system detailsColor television detailsData fileDisplay device
A system, method, apparatus and computer program product for providing location based functions and mobile e-commerce comprising a central processing unit including a processor, a storage device, and programming stored in the storage device, a display device, an audio input device, an audio output device, a communications module, a commerce module, an image module, and a location module. The programming controls the operation of the present invention to provide functions based on location data, to facilitate commercial exchanges by wirelessly exchanging payment and product information with venders, to identify services such as venders meeting selection criteria, to wirelessly exchange select information with other users and systems, to restrict and / or monitor the use of the device based on authorized user parameters, selecting one of a plurality networks through which to communicate, detecting a trigger for performing an action based on a change in location and sensed data, storing a voice annotation with a computer data file, determining service providers and associated communication parameters, contemporaneously maintaining a wireless voice and data link, providing a system for selecting and delivering mobile advertisements, and many other functions and services that are described herein.
Owner:GULA CONSULTING LLC
Method and System for Coordinating Transportation Service
InactiveUS20120041675A1Instruments for road network navigationRoad vehicles traffic controlMobile deviceComputer science
A method and system for coordinating transportation service is provided. A request is received for a trip generated by a client application executing on a mobile device. Which one of a set of transportation vehicles is best suited to provide the trip is determined. The one transportation vehicle to provide the trip is automatically dispatched.
Owner:JULIVER STEVEN +2
Intelligent portal engine
ActiveUS7092928B1Improve system performanceReduce ambiguityDigital computer detailsNatural language data processingGraphicsHuman–machine interface
Owner:OL SECURITY LIABILITY CO
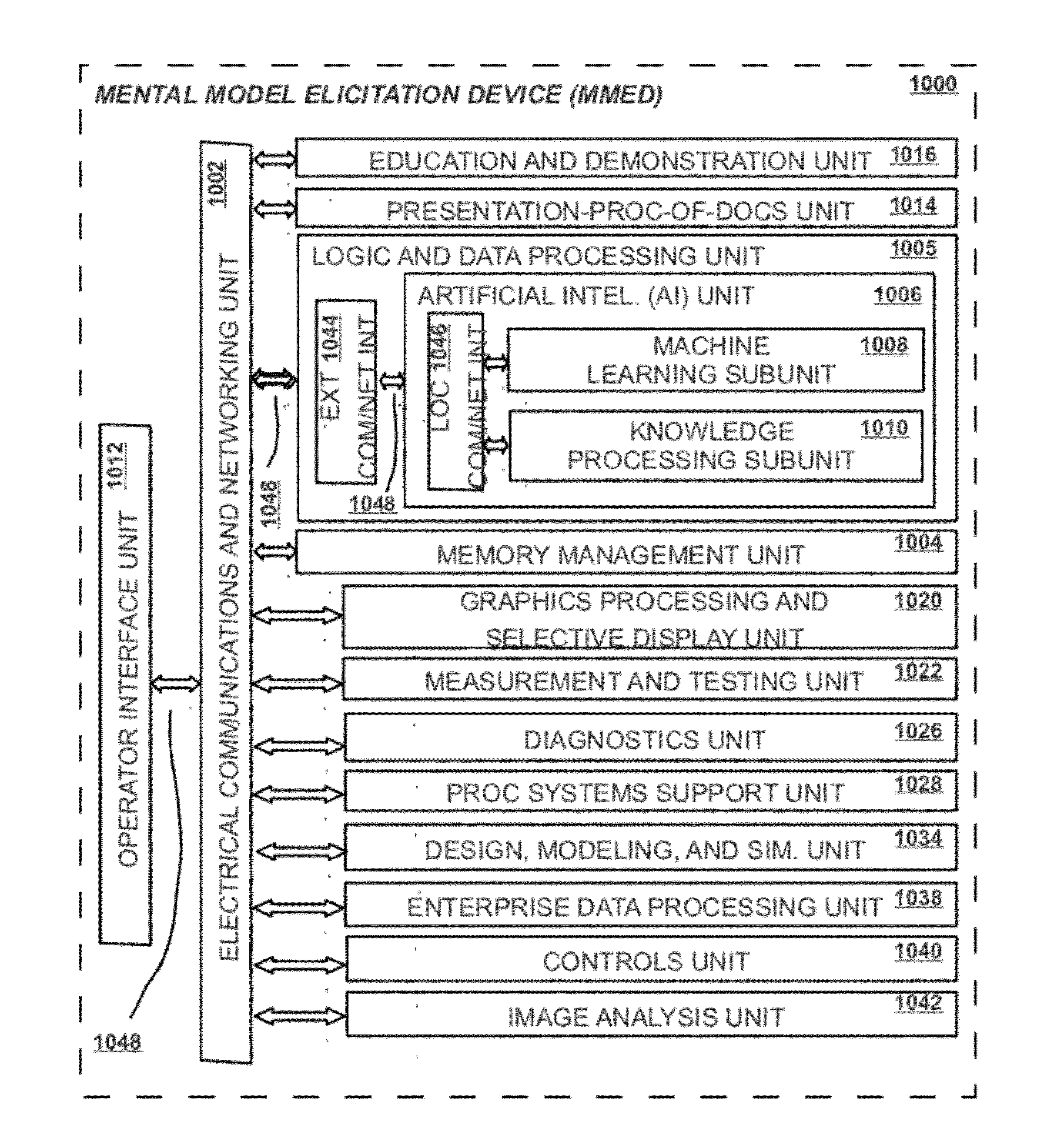
Mental Model Elicitation Device (MMED) Methods and Apparatus
InactiveUS20120330869A1Facilitate the necessary orientationEasy to createDigital computer detailsBiological neural network modelsVision basedEngineering
A mental-model elicitation process and apparatus, called the Mental-Model Elicitation Device (MMED) is described. The MMED is used to give rise to more effective end-user mental-modeling activities that require executive function and working memory functionality. The method and apparatus is visual analysis based, allowing visual and other sensory representations to be given to thoughts, attitudes, and interpretations of a user about a given visualization of a mental-model, or aggregations of such visualizations and their respective blending. Other configurations of the apparatus and steps of the process may be created without departing from the spirit of the invention as disclosed.
Owner:DURHAM JAYSON THEORDORE
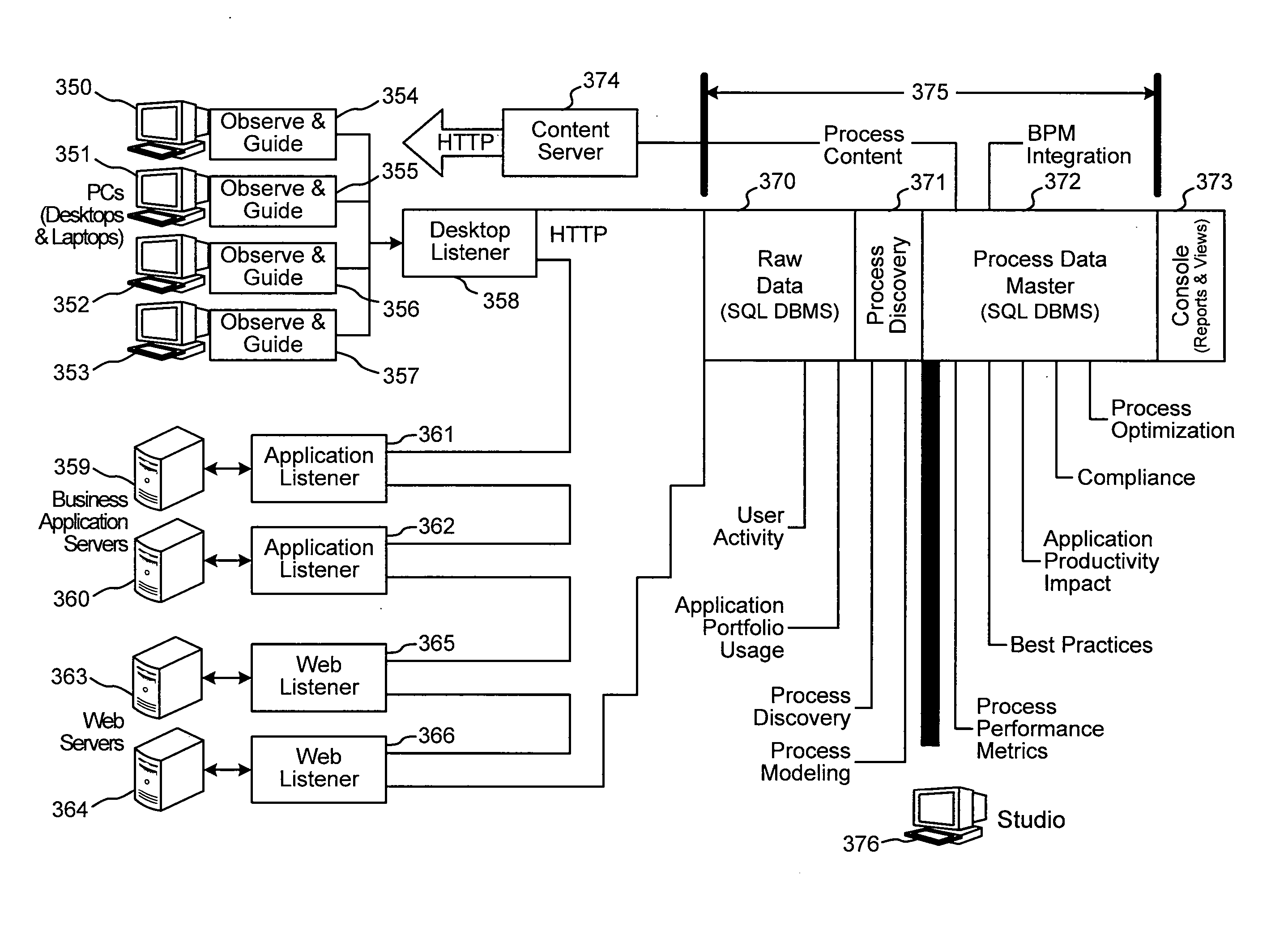
System and method for capture of user actions and use of capture data in business processes
InactiveUS20060184410A1Prevent wrong actionEnsure complianceDigital computer detailsOffice automationGood practiceData storing
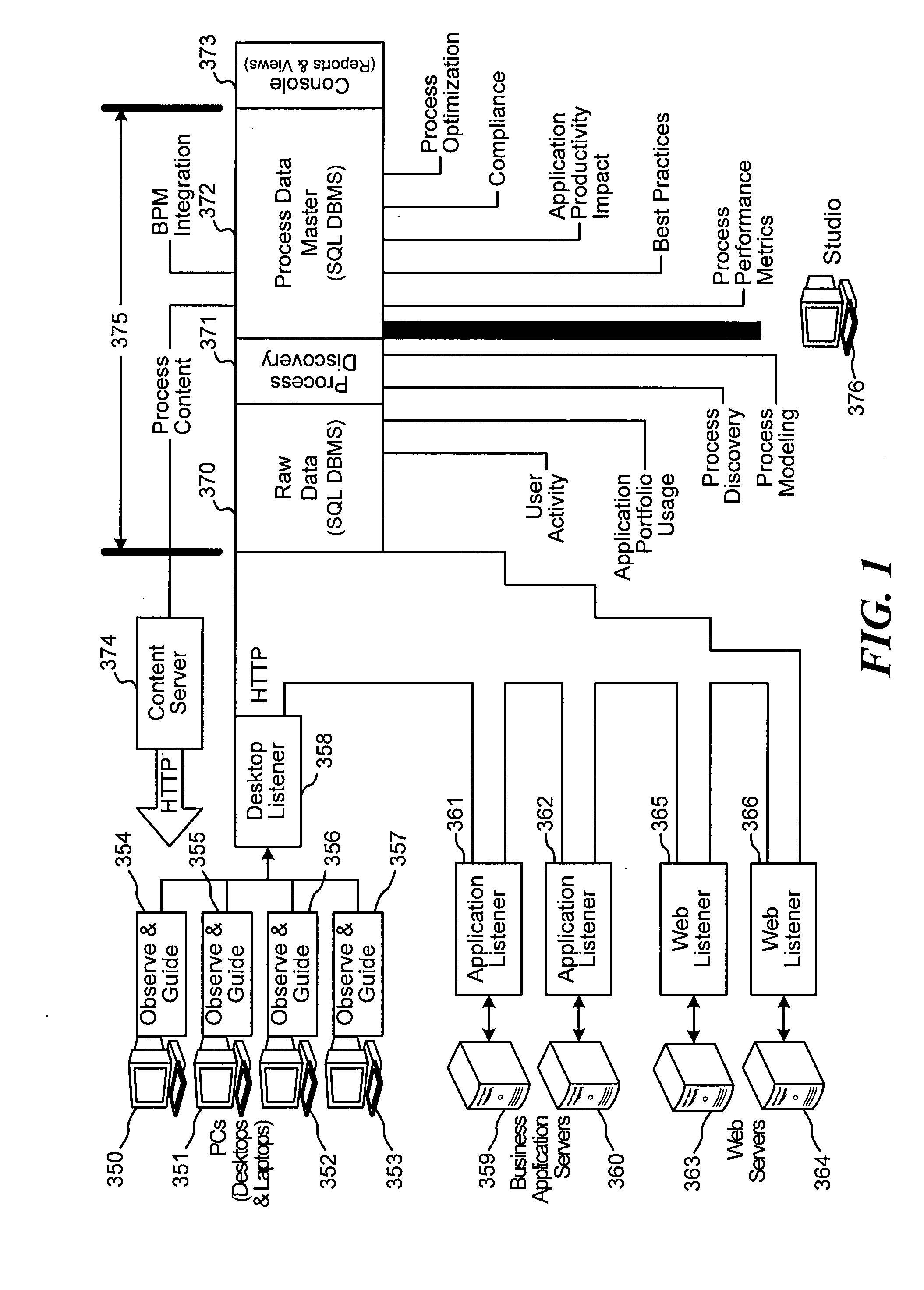
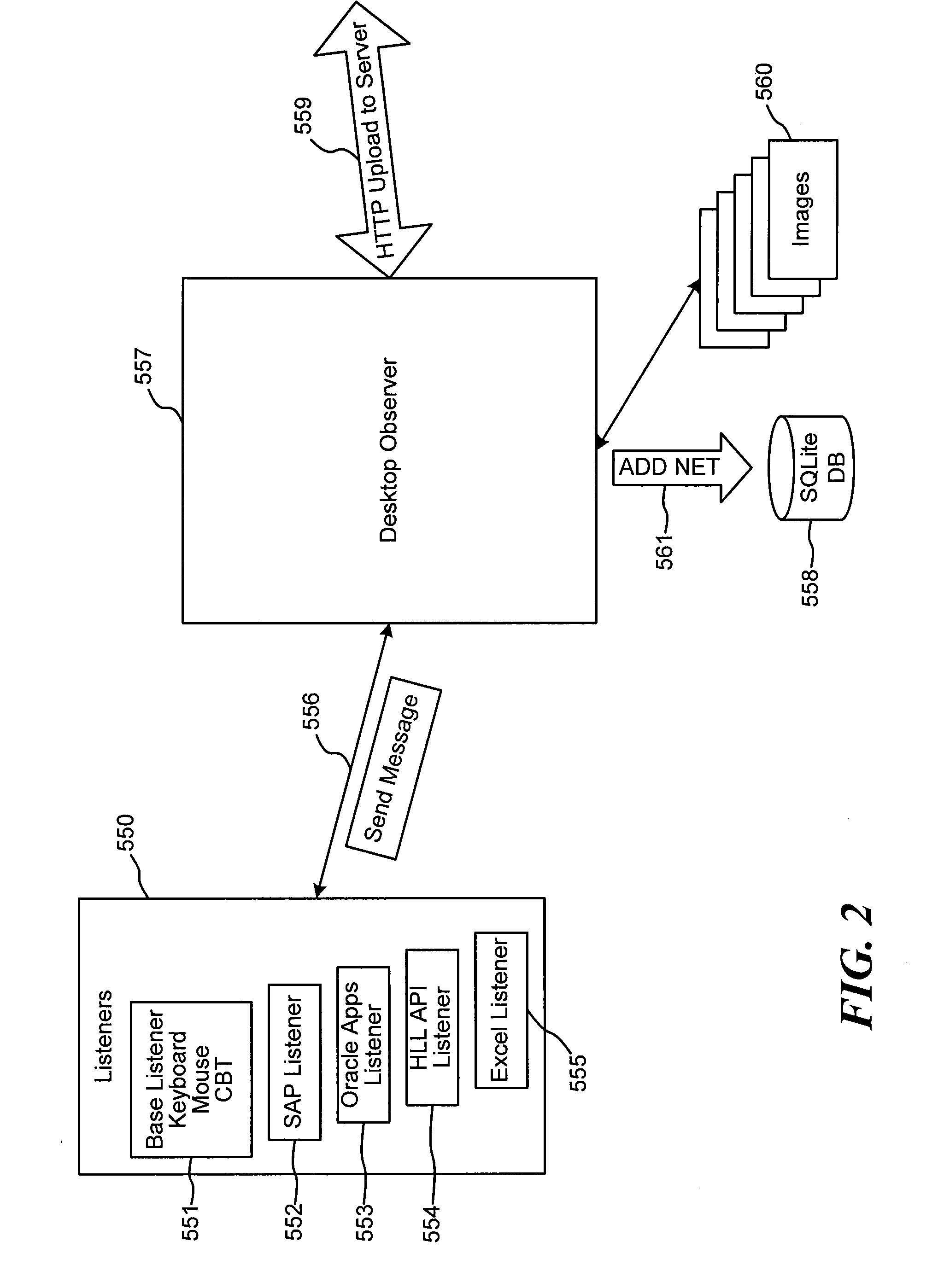
Systems and methods are disclosed for capturing data representative of user interactions with a desktop computer, and processing the capture data to identify and analyze business processes performed by the user. The disclosed system comprises listeners that capture key actuations, mouse-clicks, screen information, and other data representative of user interaction with a desktop computer. A desktop observer is provided to accept capture data from listeners, to temporarily store the capture data if necessary, and to pass the capture data to a process intelligence server. The process intelligence server includes a process discovery module the analyzes the capture data and identifies business processes corresponding to the capture data, or models business processes. A process data master storage is provided. A process analysis module is provided to determine performance metrics, best practices, application productivity impacts, compliance, and optimization analysis on the data stored in the process master storage. Methods are disclosed for capture, catalog, combination, correlation, change, compression, and certification.
Owner:QLIP MEDIA
Score based decisioning
InactiveUS7251624B1Reduce riskReduce the possibilityFinanceDigital computer detailsCredit cardThe Internet
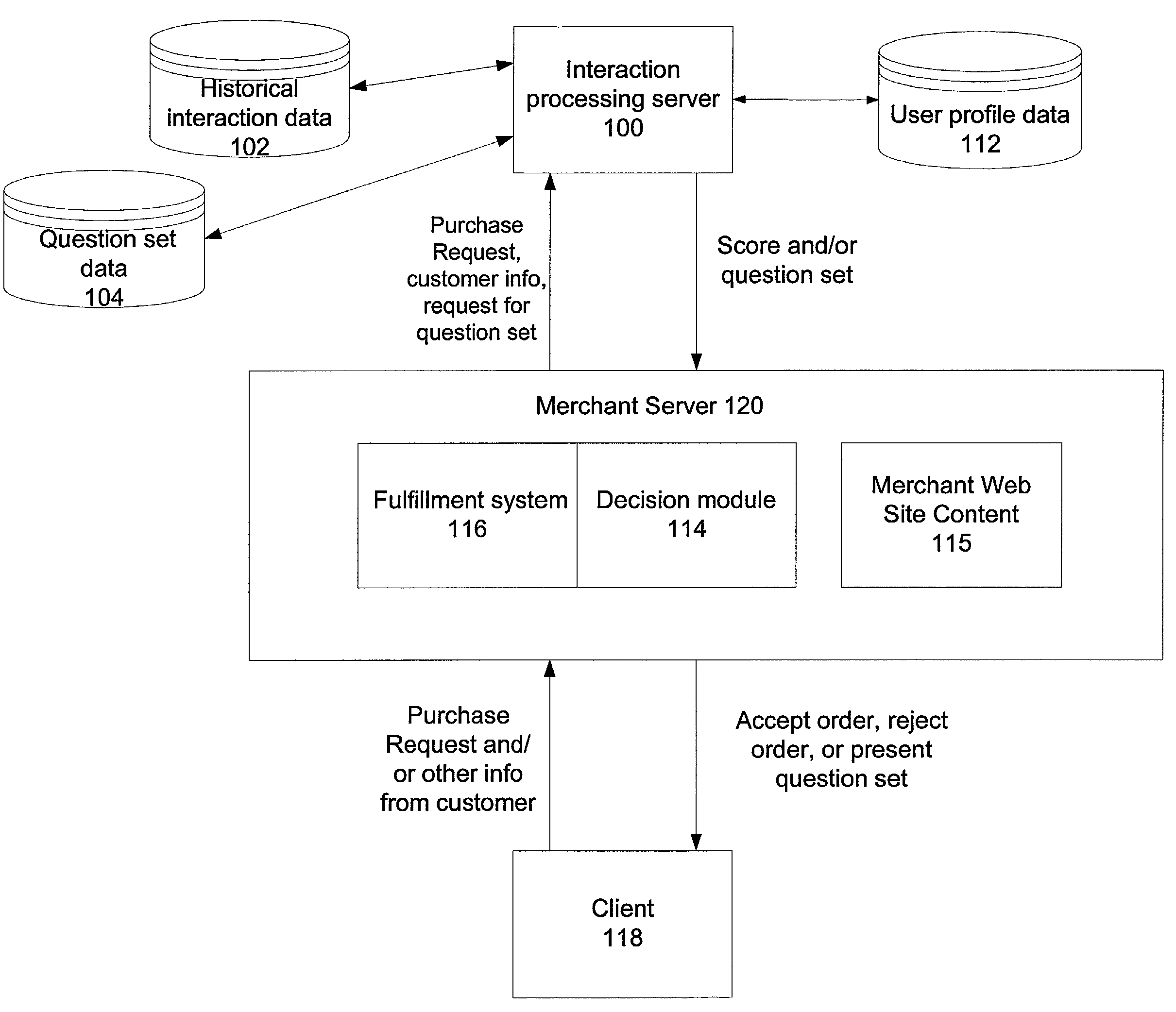
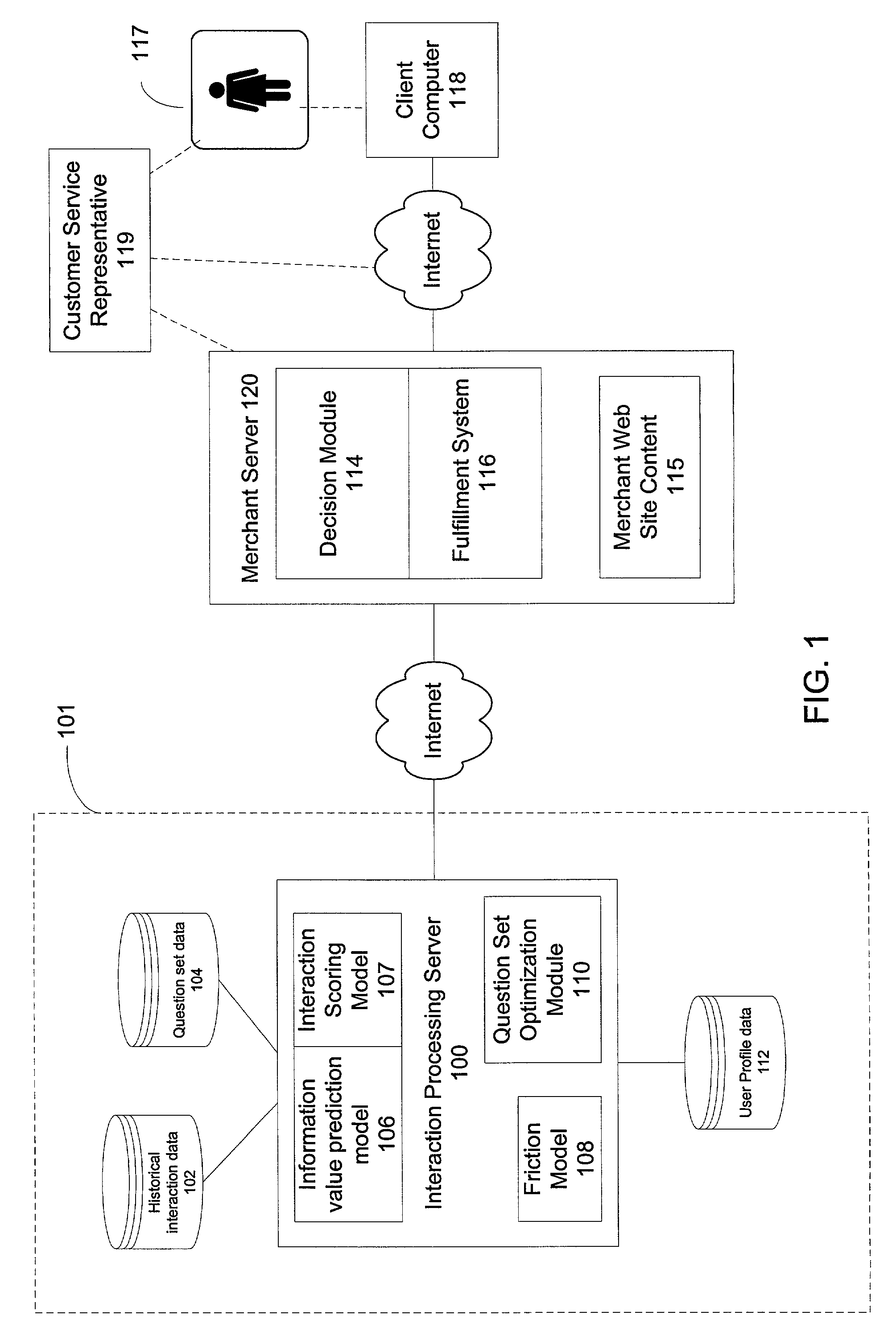
The invention aids an entity to selectively request additional data about a user to serve the needs of the entity without causing the user to have an adverse reaction. The invention helps an entity to determine the condition under which to request additional data so as to reduce the likelihood of causing the user to have an adverse reaction, e.g., terminate the interaction. One embodiment of the invention concerns customers requesting transactions with on-line merchants. More specifically, this embodiment aids merchants by detecting Internet credit card transactions that are likely to be fraudulent, and providing the merchants with mechanisms for managing a suspected transaction as it occurs to obtain additional information that can be useful to reducing the likelihood of fraud.
Owner:FAIR ISAAC & CO INC
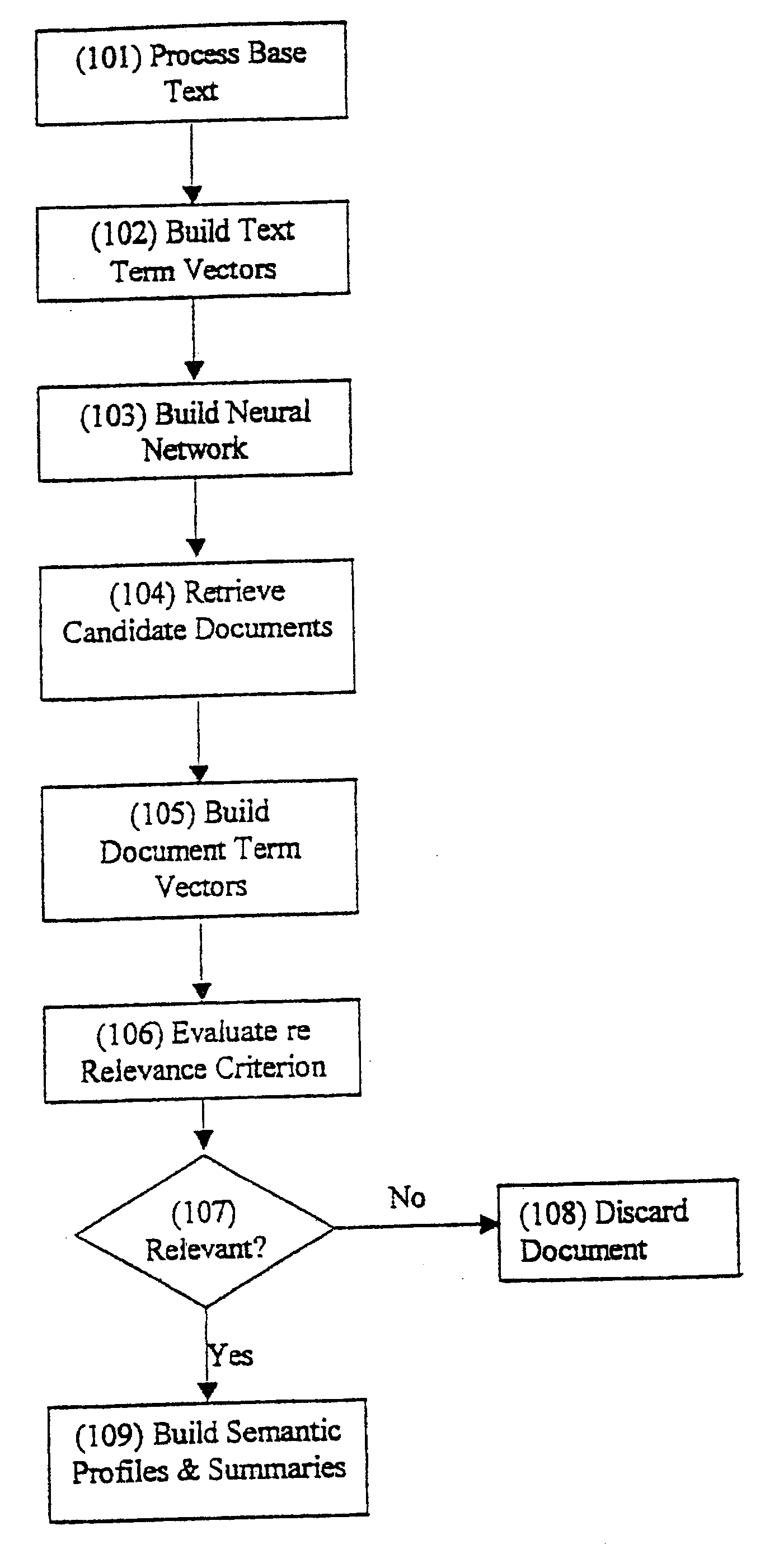
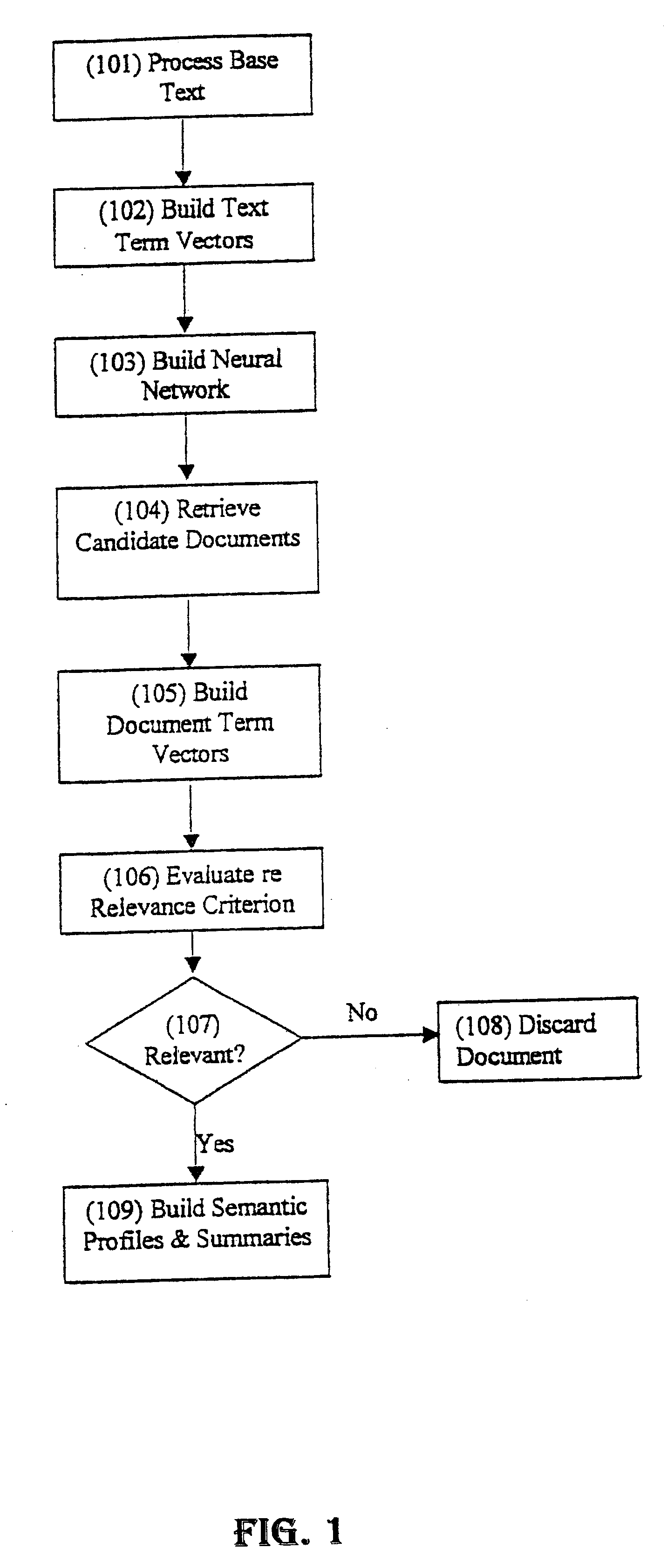
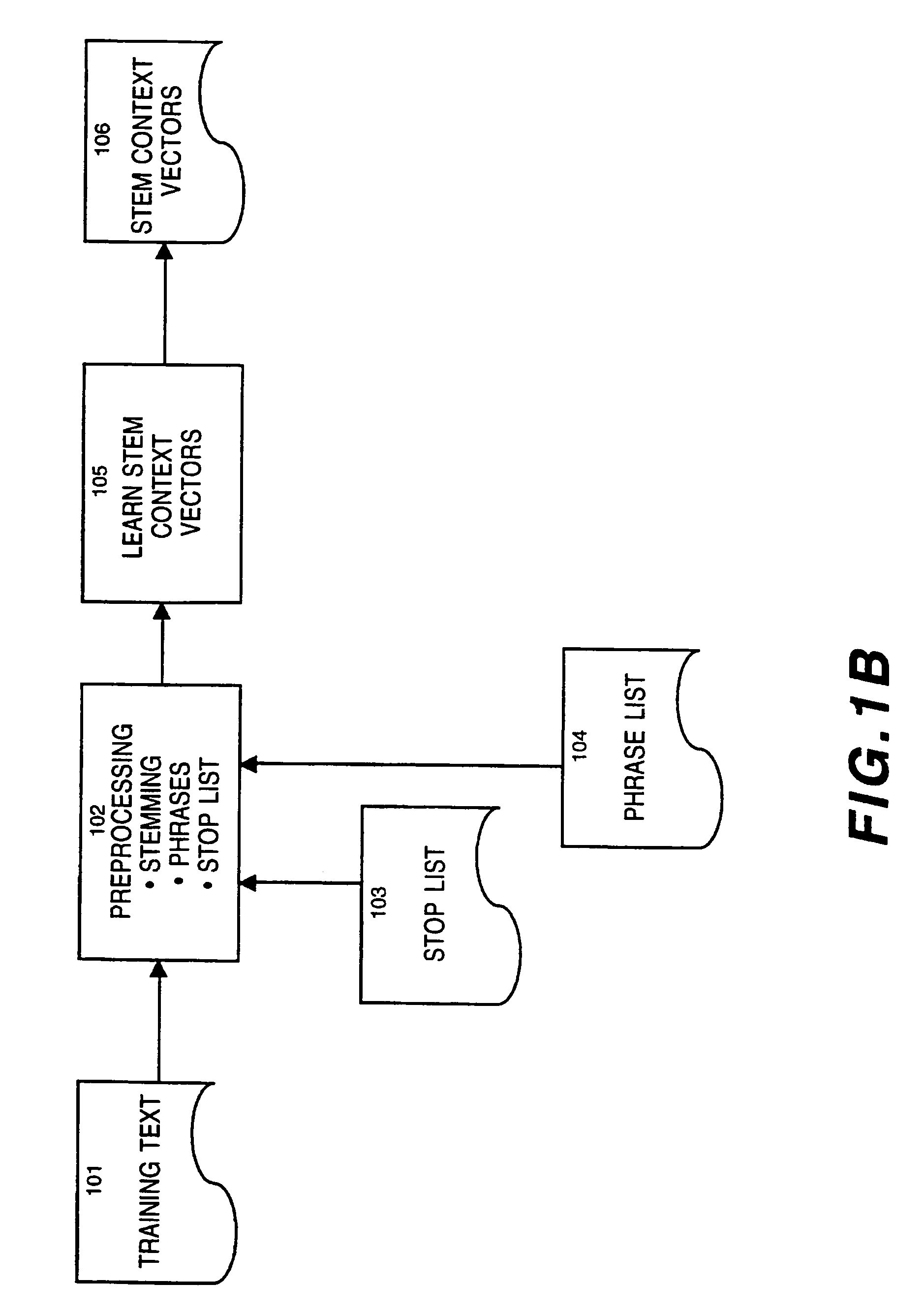
Process and system for retrieval of documents using context-relevant semantic profiles
InactiveUS6189002B1Minimize timeData processing applicationsDigital computer detailsThe InternetDocument preparation
A process and system for database storage and retrieval are described along with methods for obtaining semantic profiles from a training text corpus, i.e., text of known relevance, a method for using the training to guide context-relevant document retrieval, and a method for limiting the range of documents that need to be searched after a query. A neural network is used to extract semantic profiles from text corpus. A new set of documents, such as world wide web pages obtained from the Internet, is then submitted for processing to the same neural network, which computes a semantic profile representation for these pages using the semantic relations learned from profiling the training documents. These semantic profiles are then organized into clusters in order to minimize the time required to answer a query. When a user queries the database, i.e., the set of documents, his or her query is similarly transformed into a semantic profile and compared with the semantic profiles of each cluster of documents. The query profile is then compared with each of the documents in that cluster. Documents with the closest weighted match to the query are returned as search results.
Owner:DTI OF WASHINGTON
Monitoring system for determining and communicating a cost of insurance
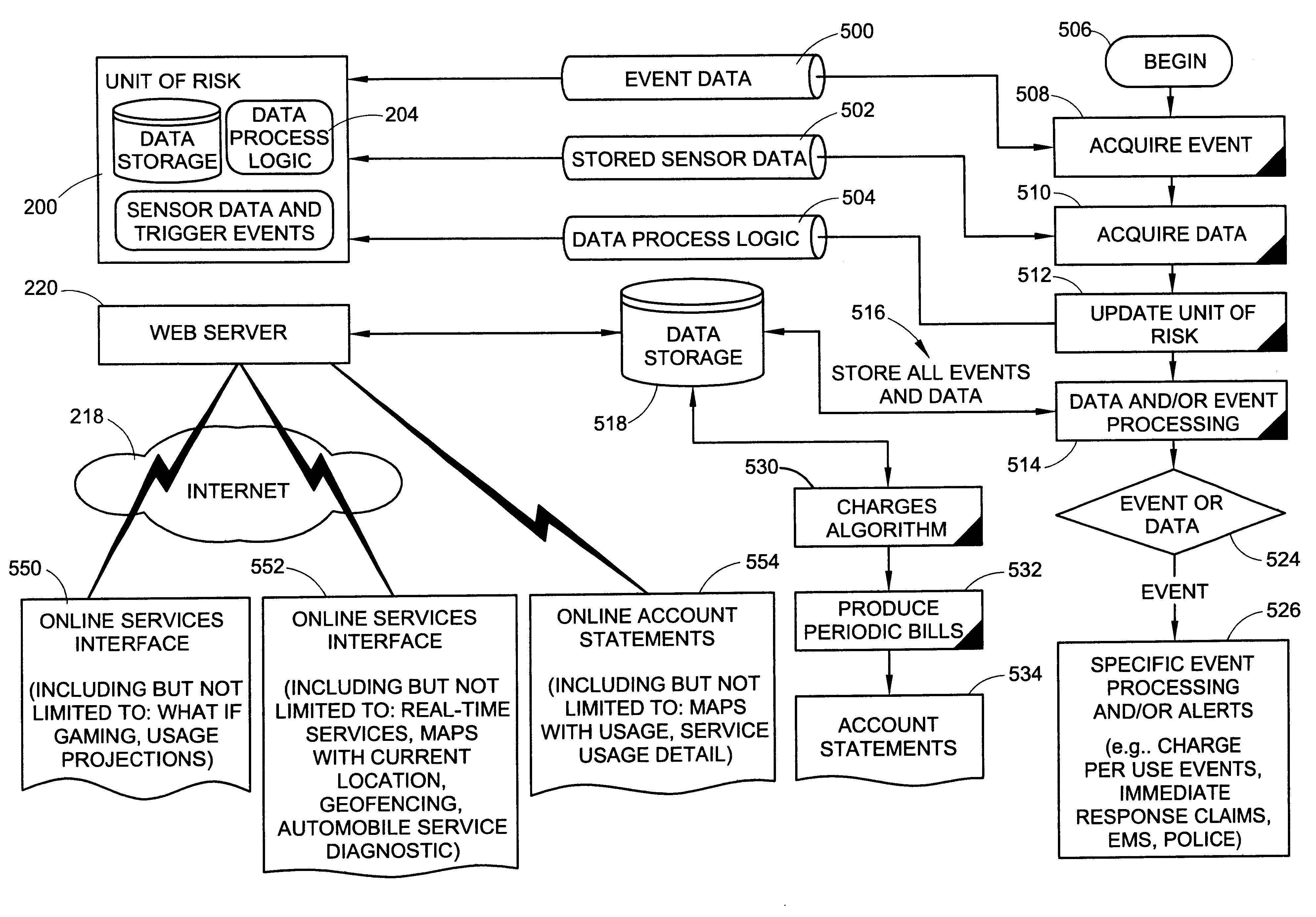
InactiveUS6868386B1Accurate measurementError rateElectric signal transmission systemsFinanceInternet communicationMonitoring system
A method and system for communicating insurance related services between an insured and an insurer through an Internet communication scheme includes a processing system for processing acquired event and sensored data to compute the cost of insurance for the same period as the data is acquired. An enhanced Internet communication scheme provides an insured access to the acquired data and its processing through enhanced presentation systems (e.g., maps with usage, service or special event processing or even automobile service diagnostics.) In addition, communication packages can provide estimates based upon user-supplied information identifying projected usages.
Owner:PROGRESSIVE CASUALTY INSURANCE
Neural network drug dosage estimation
InactiveUS6658396B1Improve accuracyGood precisionDrug and medicationsBiological neural network modelsNerve networkPatient characteristics
Neural networks are constructed (programmed), trained on historical data, and used to predict any of (1) optimal patient dosage of a single drug, (2) optimal patient dosage of one drug in respect of the patient's concurrent usage of another drug, (3a) optimal patient drug dosage in respect of diverse patient characteristics, (3b) sensitivity of recommended patient drug dosage to the patient characteristics, (4a) expected outcome versus patient drug dosage, (4b) sensitivity of the expected outcome to variant drug dosage(s), (5) expected outcome(s) from drug dosage(s) other than the projected optimal dosage. Both human and economic costs of both optimal and sub-optimal drug therapies may be extrapolated from the exercise of various optimized and trained neural networks. Heretofore little recognized sensitivities-such as, for example, patient race in the administration of psychotropic drugs-are made manifest. Individual prescribing physicians employing deviant patterns of drug therapy may be recognized. Although not intended to prescribe drugs, nor even to set prescription drug dosage, the neural networks are very sophisticated and authoritative "helps" to physicians, and to physician reviewers, in answering "what if" questions.
Owner:PREDICTION SCI
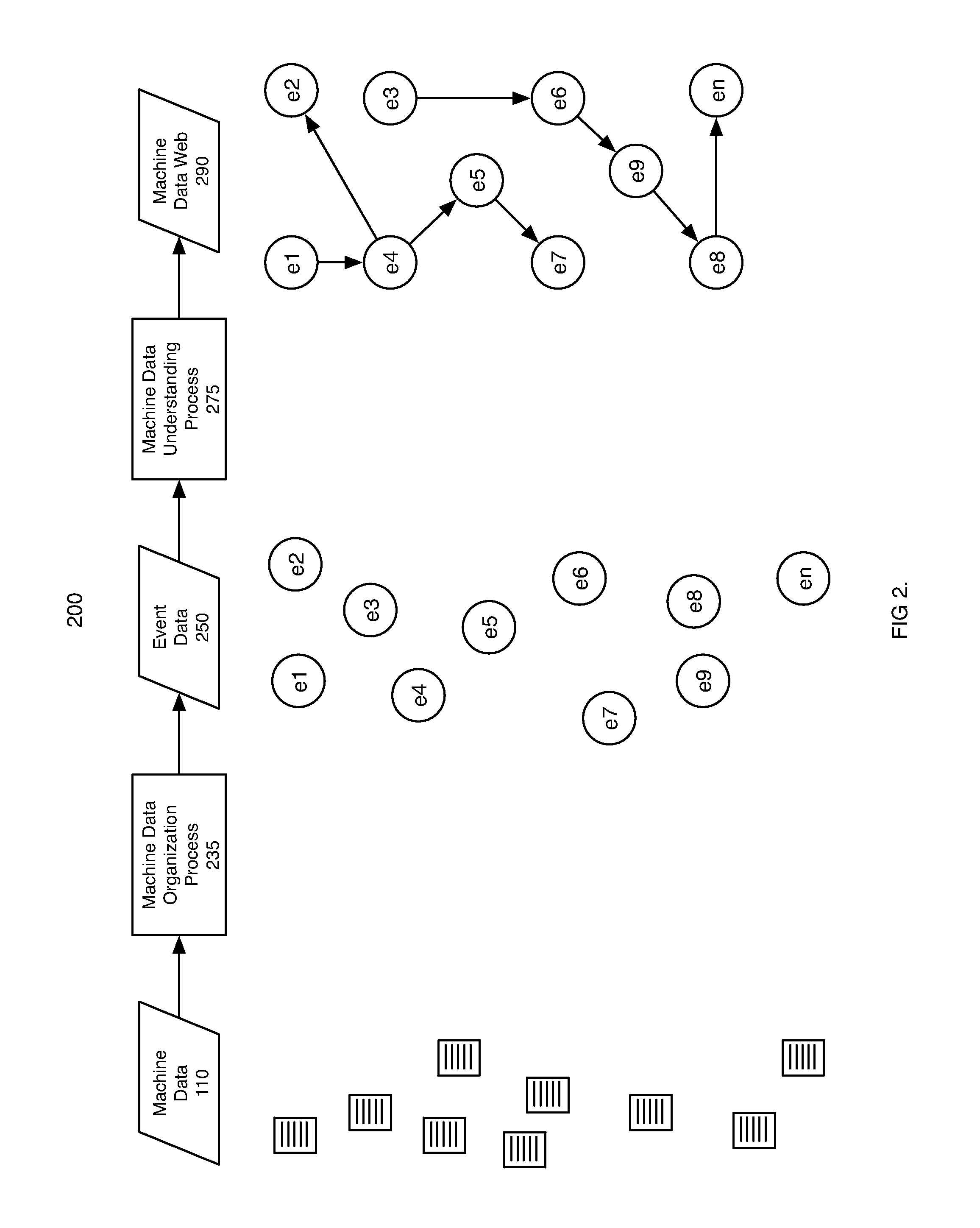
Machine data web
ActiveUS7937344B2Preserve integrityError detection/correctionInterprogram communicationInformation processingOriginal data
Methods and apparatus consistent with the invention provide the ability to organize and build understandings of machine data generated by a variety of information-processing environments. Machine data is a product of information-processing systems (e.g., activity logs, configuration files, messages, database records) and represents the evidence of particular events that have taken place and been recorded in raw data format. In one embodiment, machine data is turned into a machine data web by organizing machine data into events and then linking events together.
Owner:SPLUNK INC
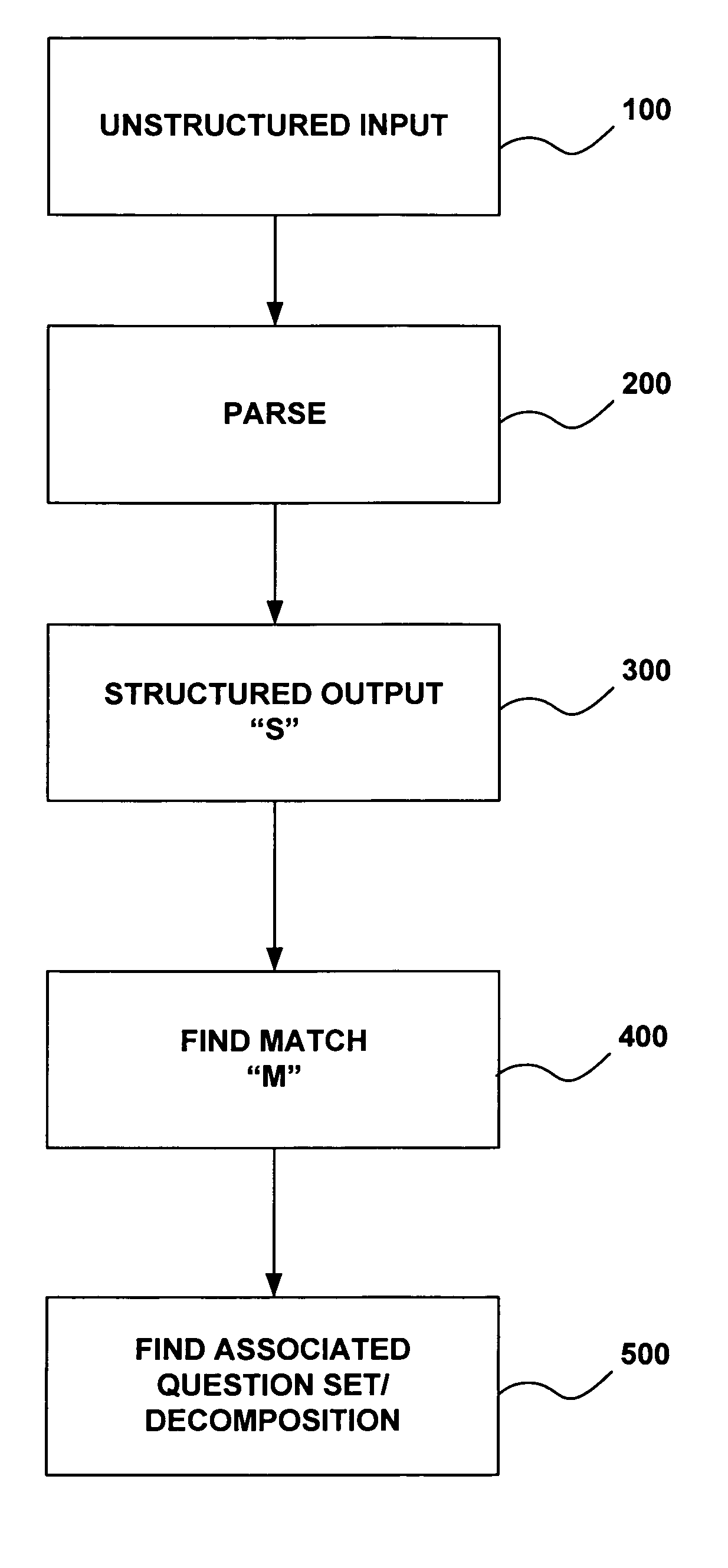
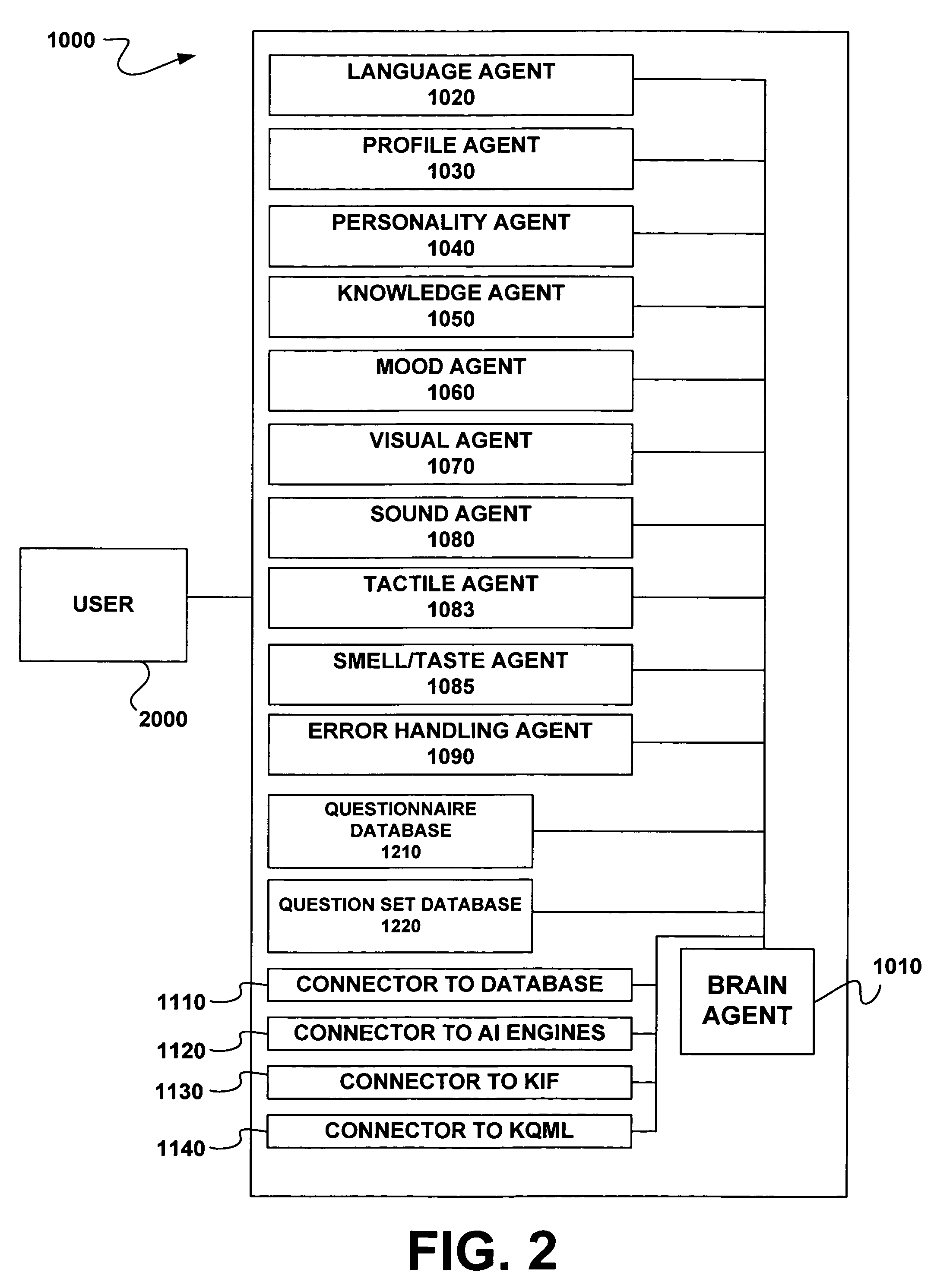
Apparatus and method for problem solving using intelligent agents
The present invention relates to a system and method for problem solving using intelligent agents. The intelligent agents may be embodied as processor-readable software code stored on a processor-readable medium. The intelligent agents may include a brain agent to parse the input and direct the parsed input query to other intelligent agents within the system. The apparatus and method may use, for example, a personality agent, a language agent, a knowledge agent, a mood agent, a visual agent, sound agent, a tactile agent, and a smell / taste agent and various connectors to external data sources or other intelligent systems to interpret questions and provide responses back to the user. The apparatus and method may further parse questions in a conceptual manner. The apparatus and method may further optimize its system performance by evolving with and reacting to specific user interactions. Thus, the present invention may be configured to receive a human question and to output a human answer.
Owner:GEN DYNAMICS ADVANCED INFO SYST
Pricing and auctioning of bundled items among multiple sellers and buyers
InactiveUS7840447B2Buying/selling/leasing transactionsElectric/magnetic computingGroup buyingComputer science
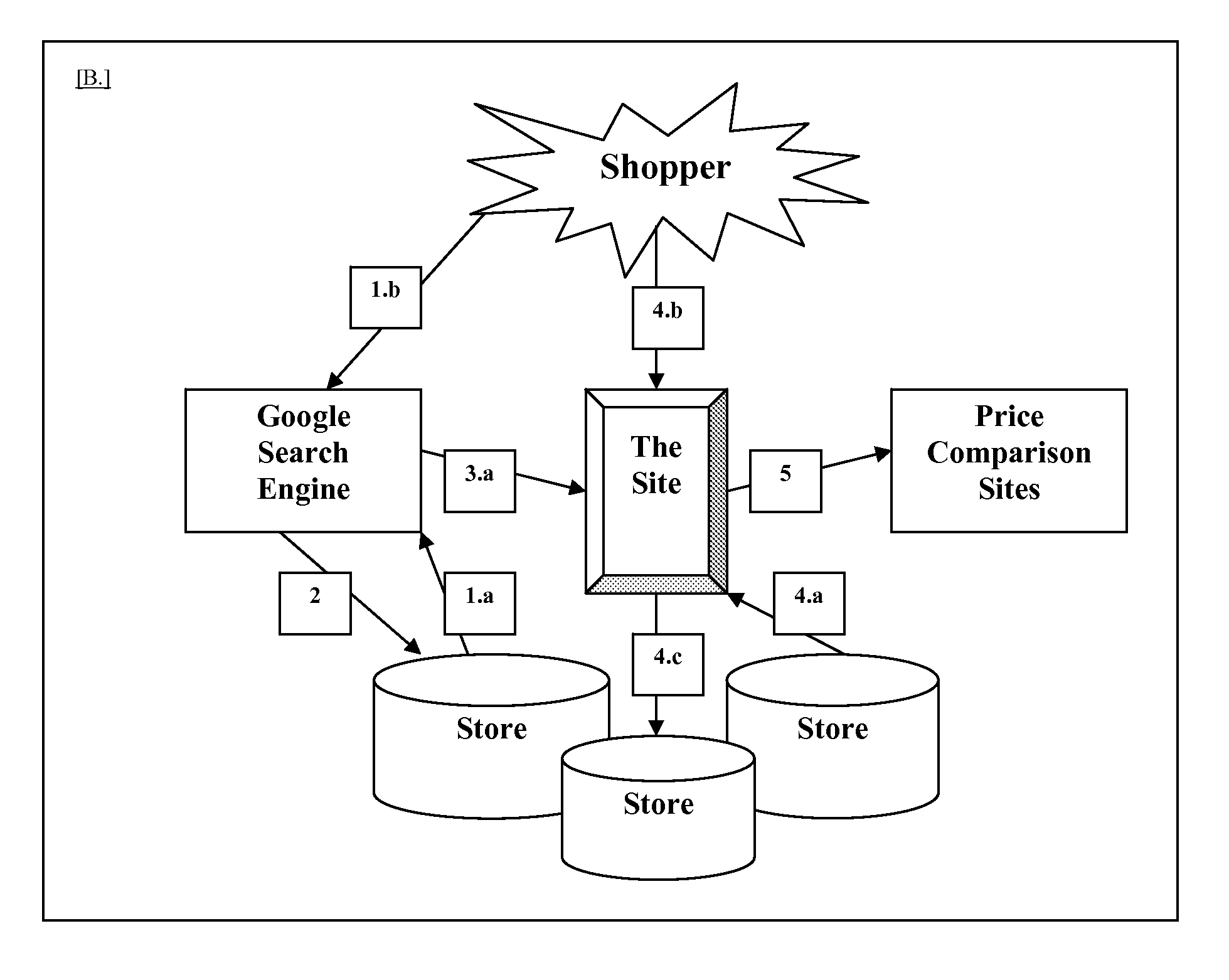
A number of sets of methods and apparatuses applicable to online shopping are disclosed. One set, “Bin Packing Methods with Approximate Membership”, includes methods in pricing and auctioning a bundle of items, some of which could belong to another bundle. Significantly, the membership of a bundle, during pricing and auction, could change. Another set, the “Shopping Console”, puts a structure into the online shopping experience, so that through one interface various shopping activities can be facilitated, including but not limited to researching, pricing, negotiation, group buying, and tracking of purchases. Still another set, “Flash Mob Shopping”, allows sellers and a (spontaneous) group of shoppers to connect on prices without requiring shoppers' hard commitments, and with sellers revealing only necessary price information.
Owner:TAMIRAS PER PTE LTD LLC
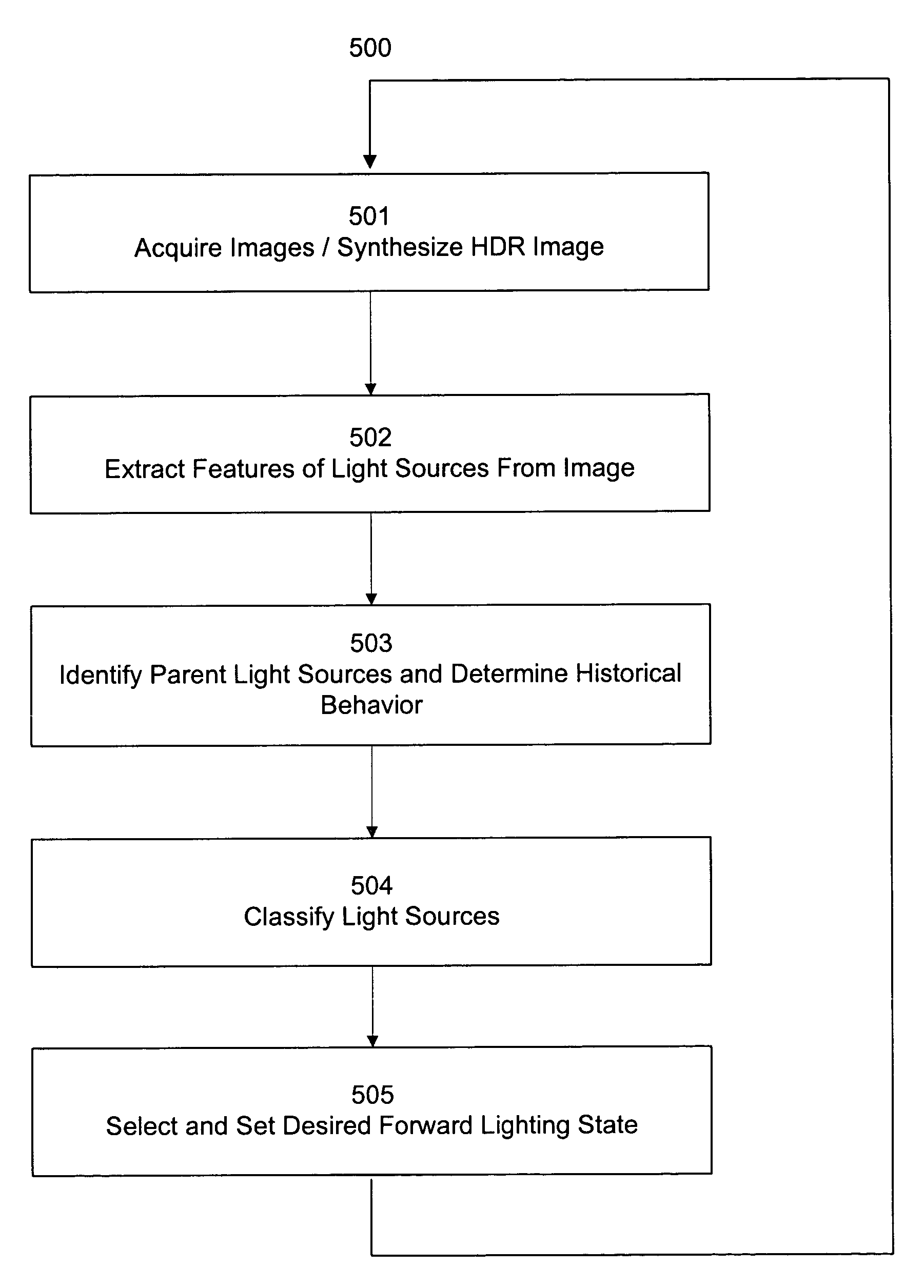
Image acquisition and processing methods for automatic vehicular exterior lighting control
The present invention relates to various apparatus, algorithms and methods for acquiring and processing images of a scene. Details of various aspects of the associated images are identified and may be utilized to generate various vehicular equipment control signals.
Owner:GENTEX CORP
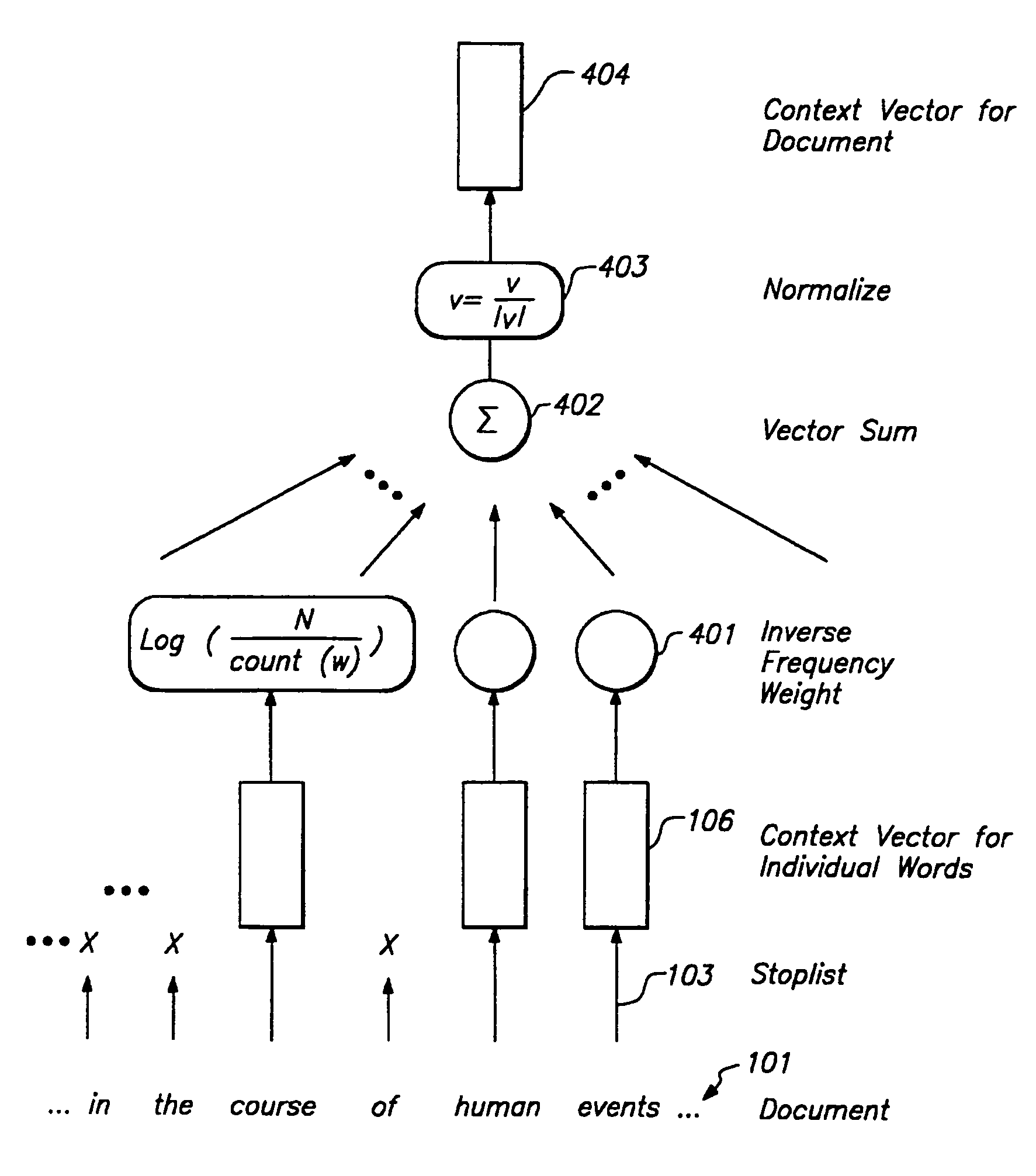
Context vector generation and retrieval
InactiveUS7251637B1Reduce search timeRapid positioningDigital computer detailsBiological neural network modelsCo-occurrenceDocument preparation
A system and method for generating context vectors for use in storage and retrieval of documents and other information items. Context vectors represent conceptual relationships among information items by quantitative means. A neural network operates on a training corpus of records to develop relationship-based context vectors based on word proximity and co-importance using a technique of “windowed co-occurrence”. Relationships among context vectors are deterministic, so that a context vector set has one logical solution, although it may have a plurality of physical solutions. No human knowledge, thesaurus, synonym list, knowledge base, or conceptual hierarchy, is required. Summary vectors of records may be clustered to reduce searching time, by forming a tree of clustered nodes. Once the context vectors are determined, records may be retrieved using a query interface that allows a user to specify content terms, Boolean terms, and / or document feedback. The present invention further facilitates visualization of textual information by translating context vectors into visual and graphical representations. Thus, a user can explore visual representations of meaning, and can apply human visual pattern recognition skills to document searches.
Owner:FAIR ISAAC & CO INC
Task computing
InactiveUS20040230636A1General purpose stored program computerMultiprogramming arrangementsProcedure callsWeb service
A computer-based system includes task computing enabling users to define tasks by combining available functionality and to execute such tasks. The computer-based system of includes available functionality which originates in devices, computing applications and electronic services available through local and remote procedure calls including Web Services, UPnP, CORBA, RMI, RPC, DCE, DCOM or comprises previously defined tasks. All available functionality is abstracted to the user as a service and each service is expressed in a service description language, and the services have a semantic description associated with them.
Owner:FUJITSU LTD
Method and system for exploring similarities
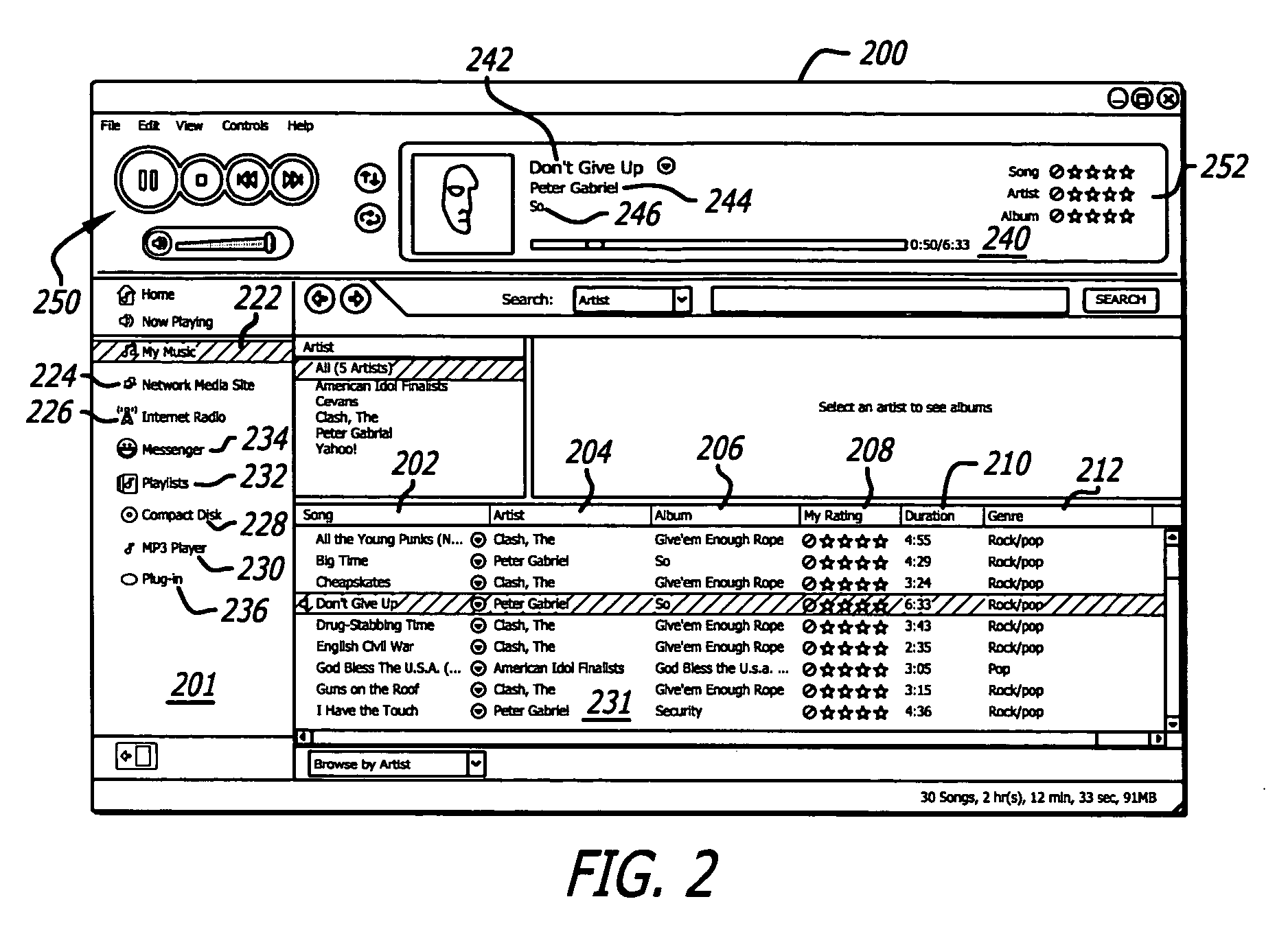
InactiveUS20060195790A1Record information storageData switching by path configurationDegree of similarityUser interface
A method and computer readable medium for exploring similar users and items of a media service. In one aspect, a user can explore for similar users iteratively. In one aspect, a user interface is generated that displays a user selectable indicia representing a similar member function for allowing a user to search a media service for at least one other user which has a degree of similarity with respect to the searching user. In another aspect, a method facilitates the search of such a similar user within a media service.
Owner:HUAWEI TECH CO LTD
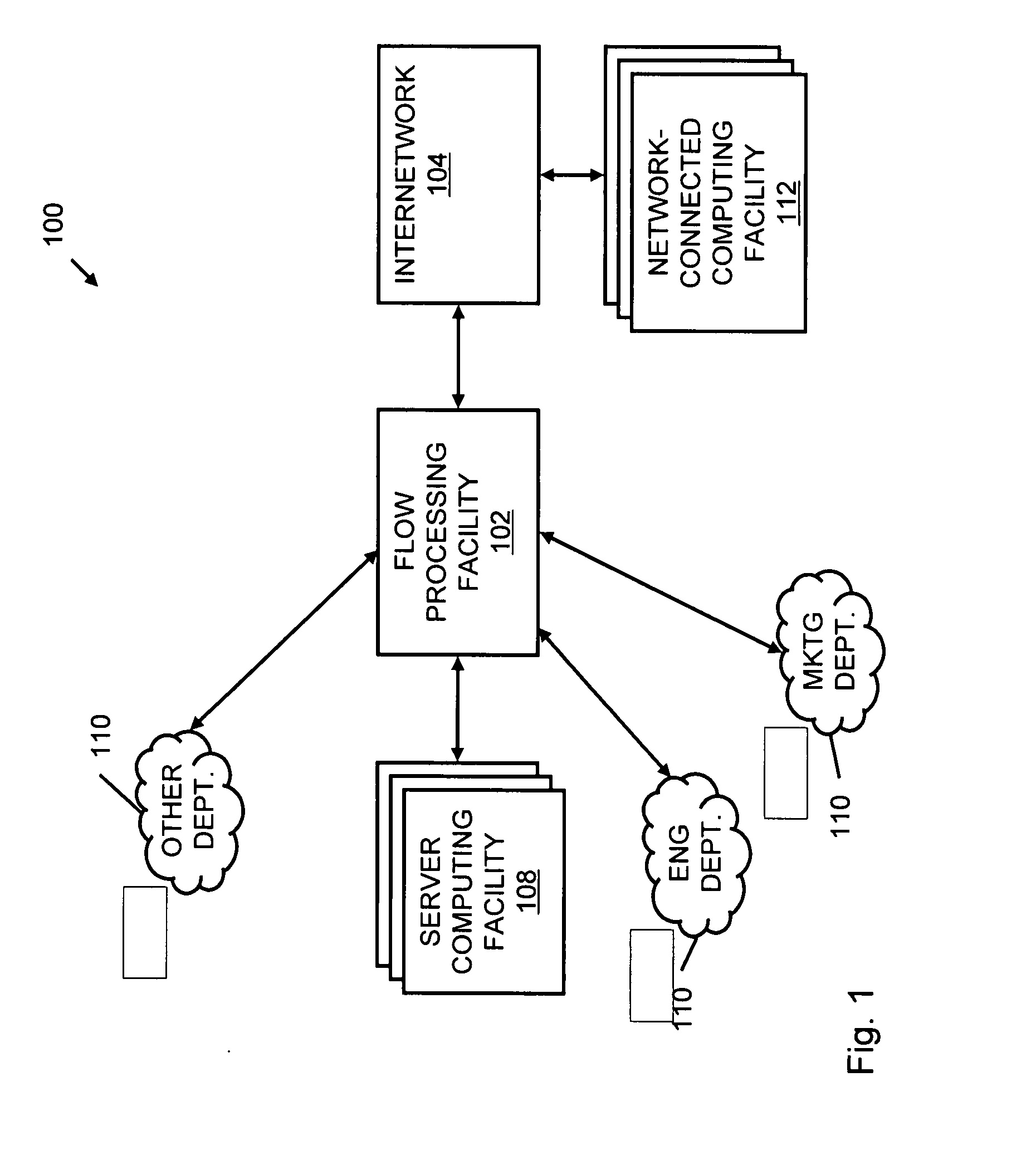
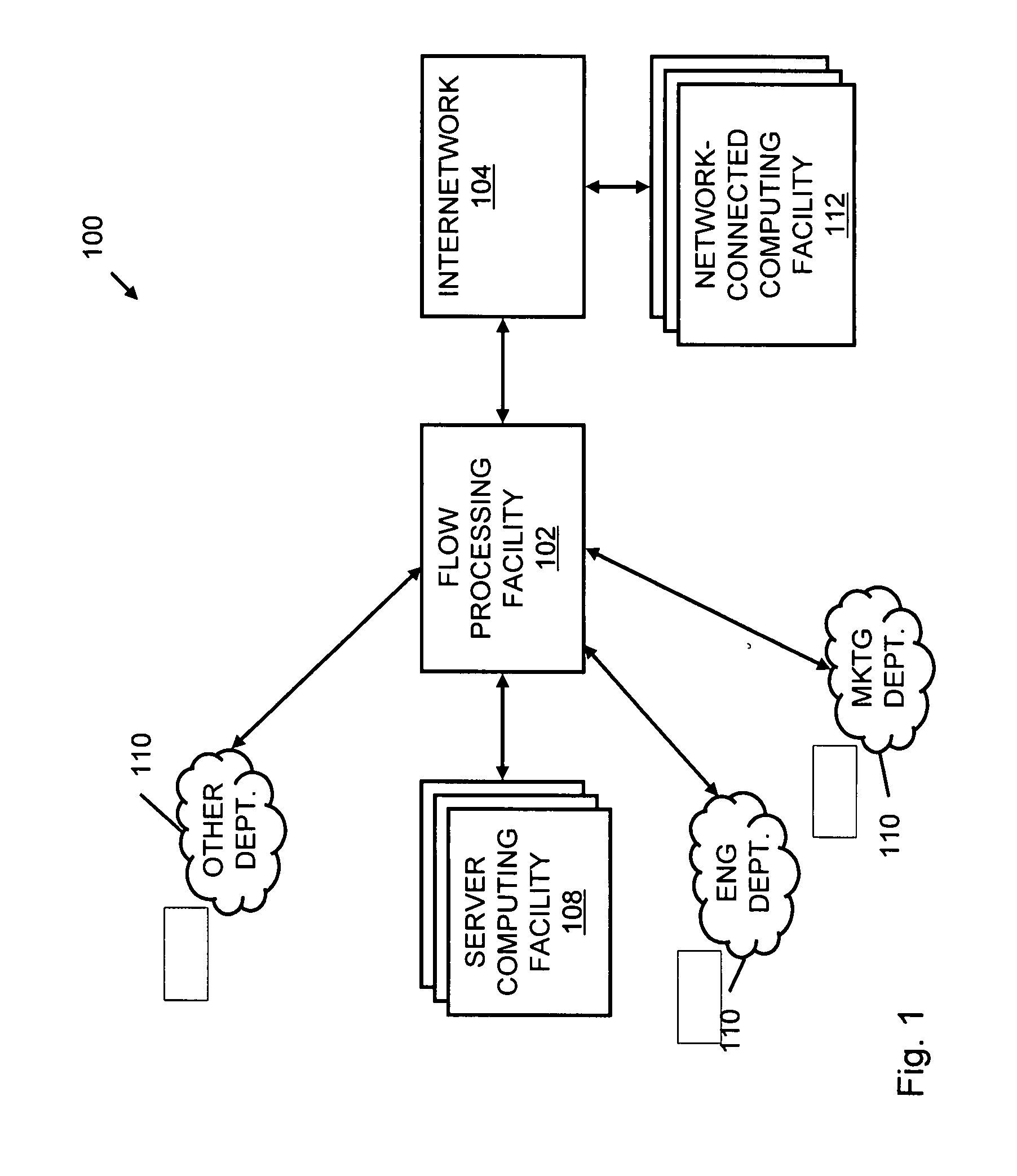
Systems and methods for processing data flows
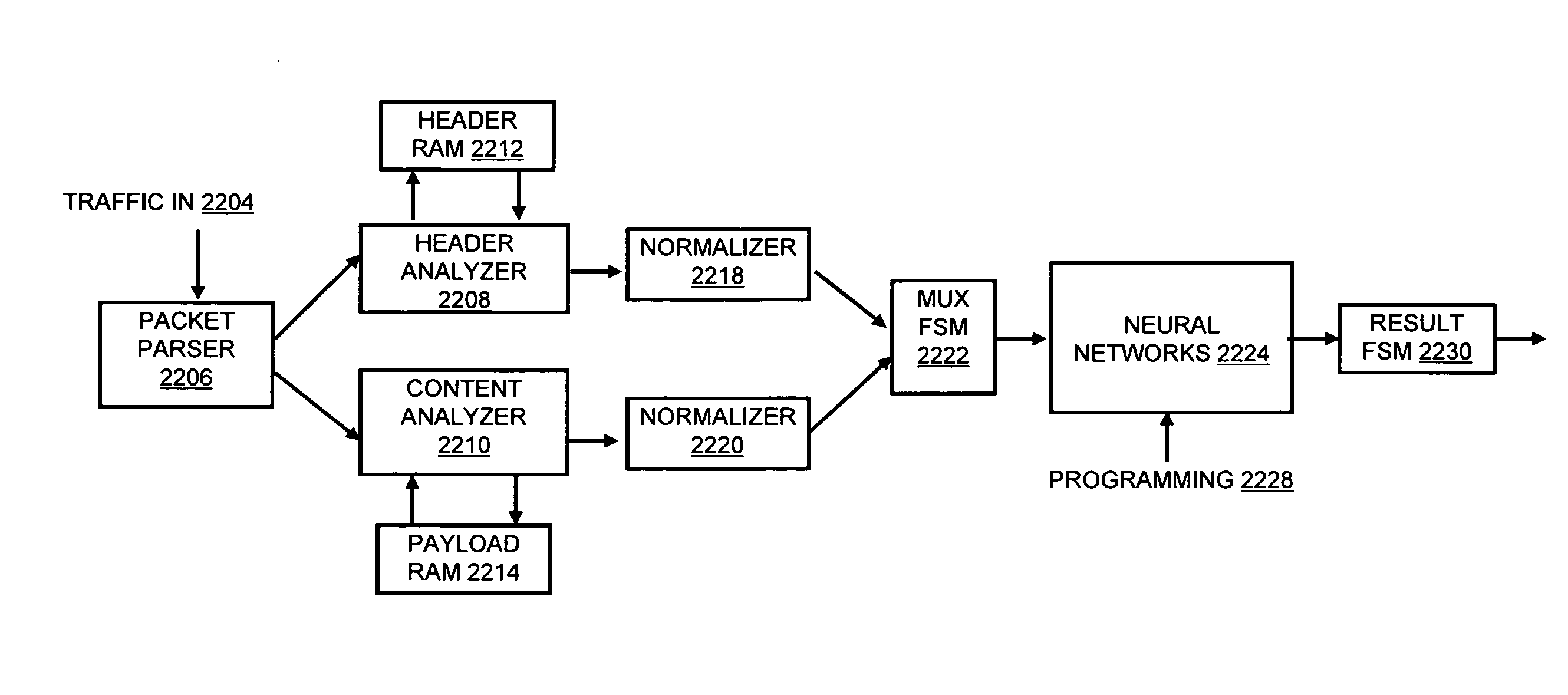
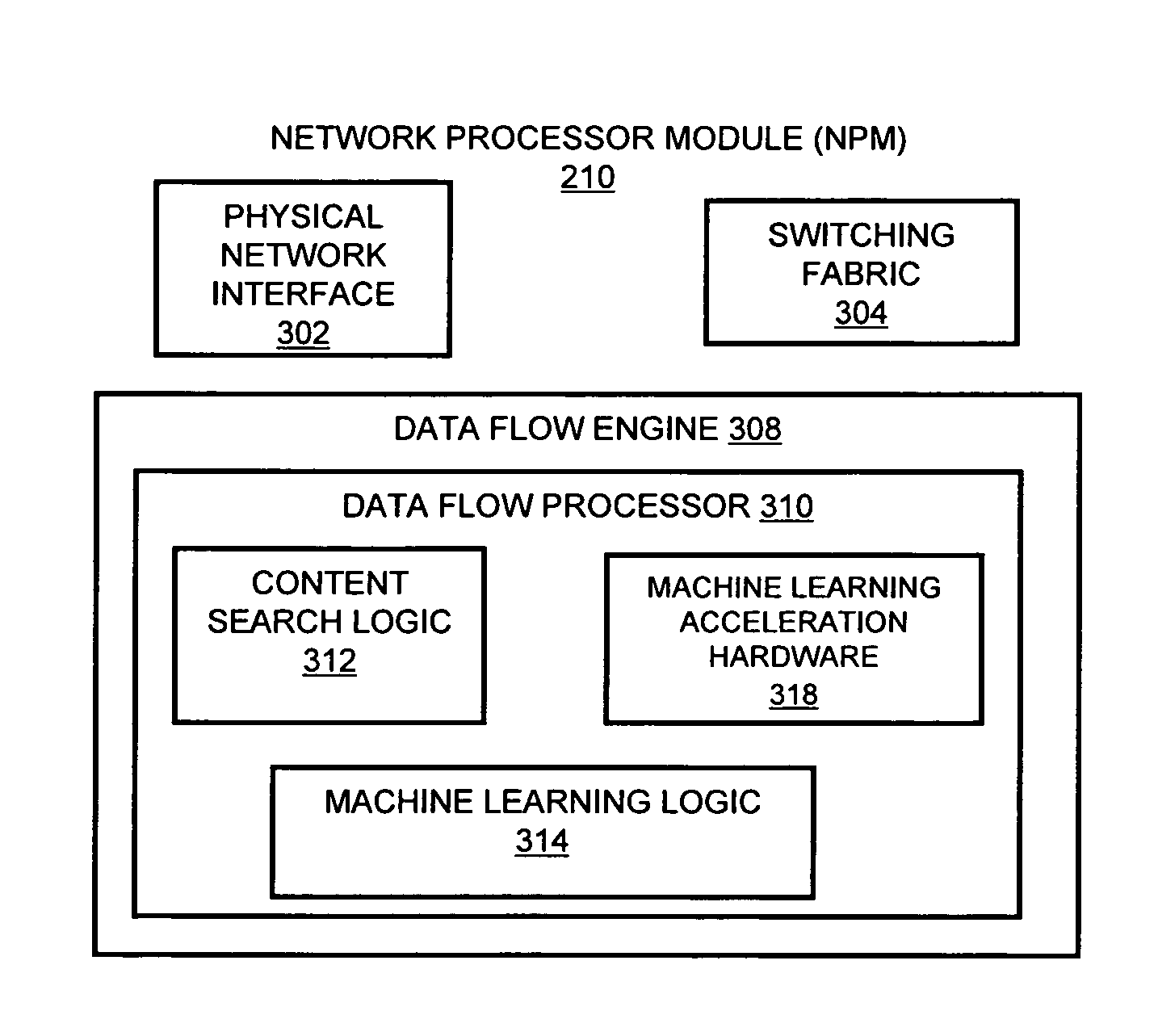
InactiveUS20080262991A1Easy to detectPreventing data flowDigital computer detailsBiological neural network modelsData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
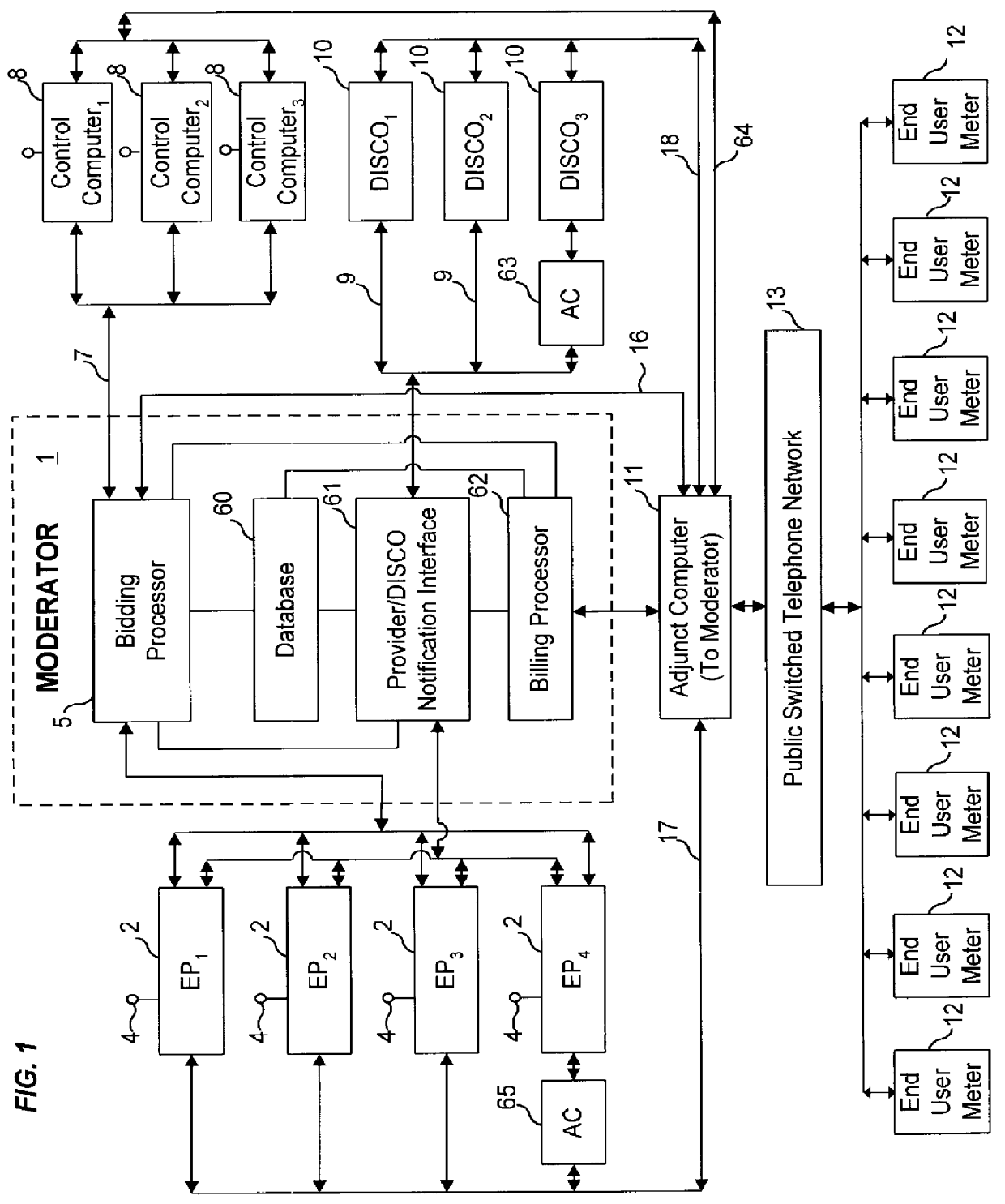
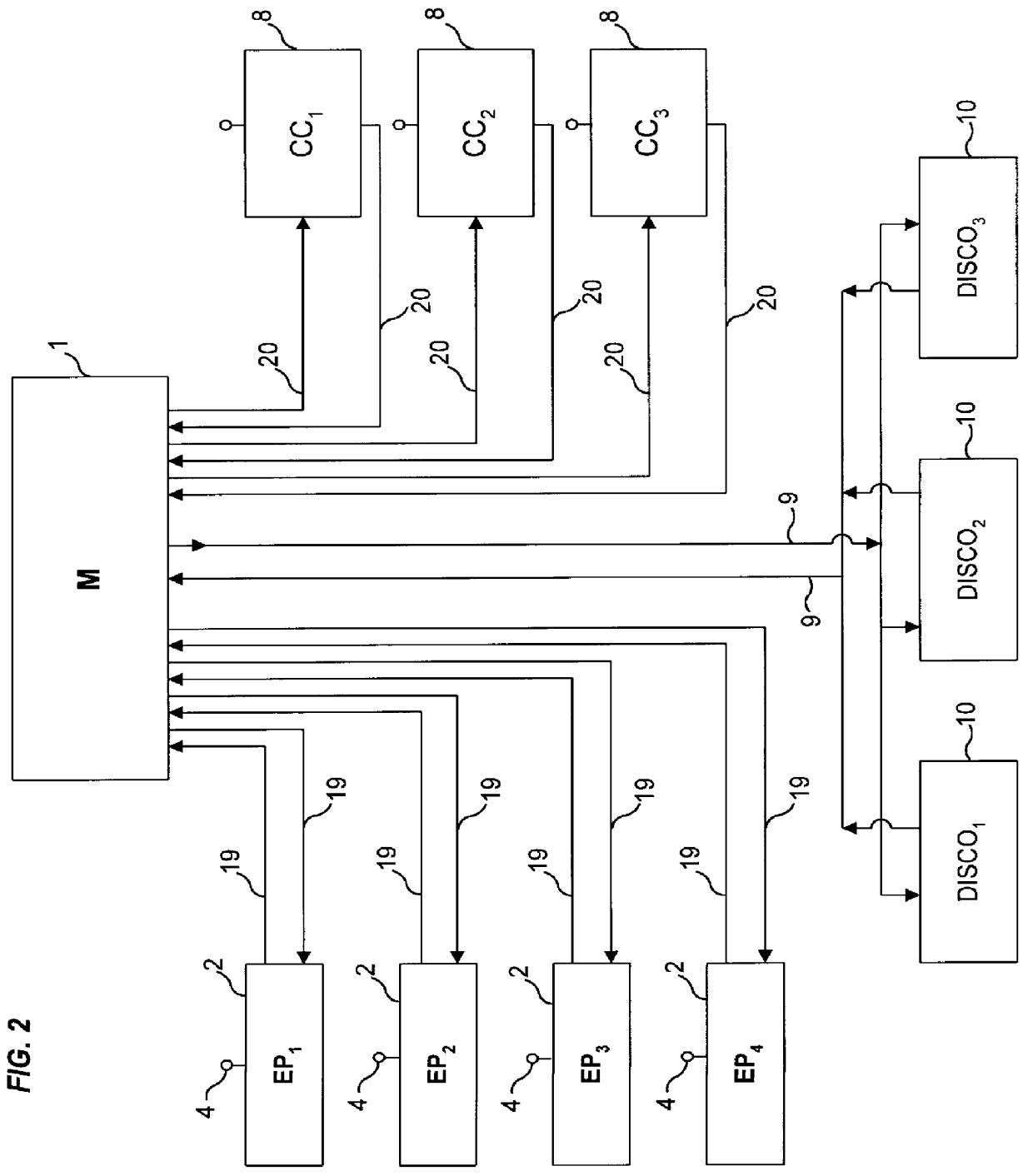
Bidding for energy supply
An auction service is provided that stimulates competition between energy suppliers (i.e., electric power or natural gas). A bidding moderator (Moderator) receives bids from the competing suppliers of the rate each is willing to charge to particular end users for estimated quantities of electric power or gas supply (separate auctions). Each supplier receives competing bids from the Moderator and has the opportunity to adjust its own bids down or up, depending on whether it wants to encourage or discourage additional energy delivery commitments in a particular geographic area or to a particular customer group. Each supplier's bids can also be changed to reflect each supplier's capacity utilization. Appropriate billing arrangements are also disclosed.
Owner:GEOPHONIC NETWORKS
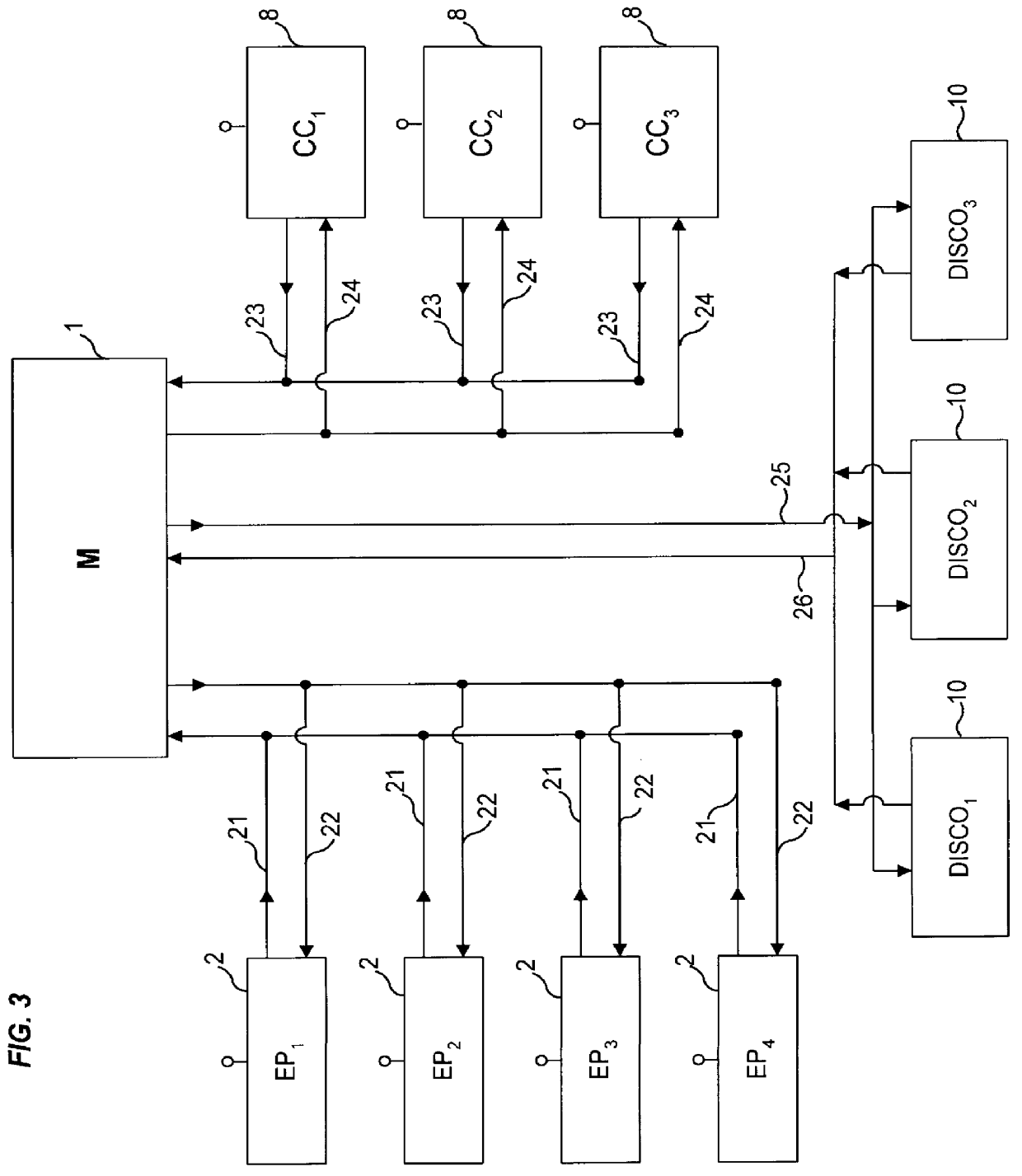
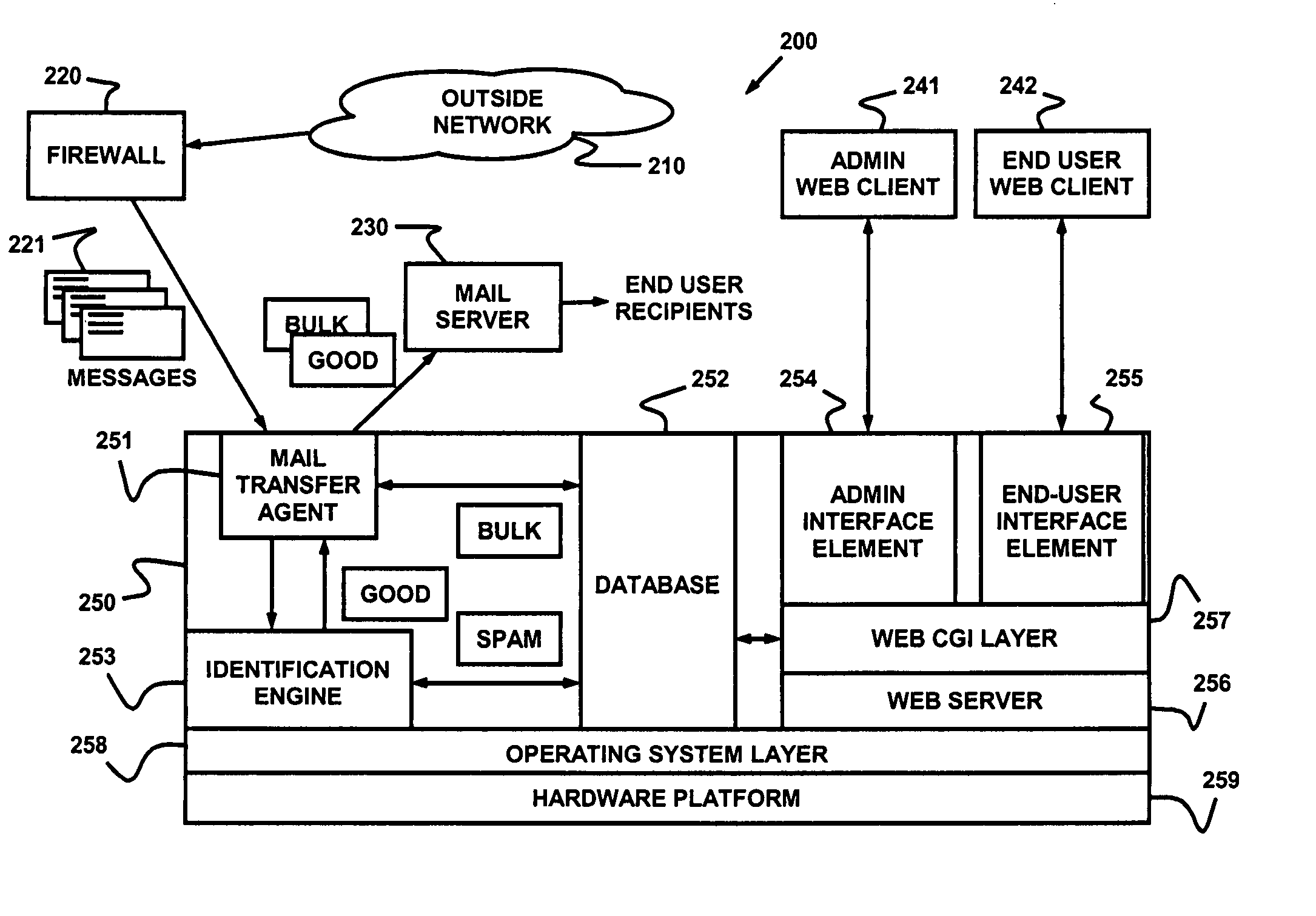
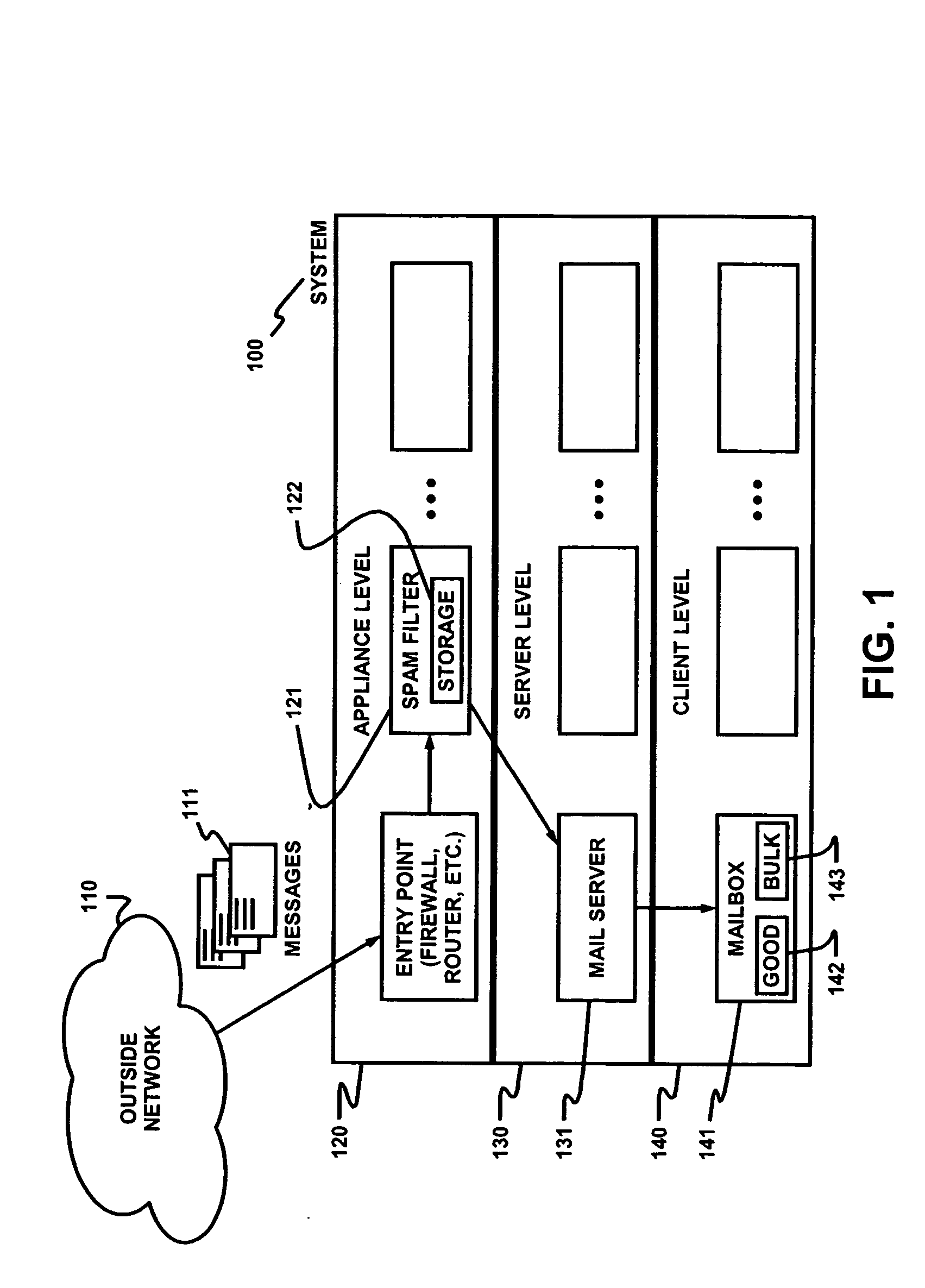
Dynamic message filtering
ActiveUS20050076084A1Reduce in quantityMake fastError detection/correctionGenetic modelsSpammingWhitelist
Dynamically filtering and classifying messages, as good messages, bulk periodicals, or spam. A regular expression recognizer, and pre-trained neural networks. The neural networks distinguish “likely good” from “likely spam,” and also operate at a more discriminating level to distinguish among the three categories above. A dynamic whitelist and blacklist; sending addresses are collected when the number of their messages indicates the sender is good or a spammer. A dynamically selected set of regular expressions input to the neural networks.
Owner:MAILGATE LLC
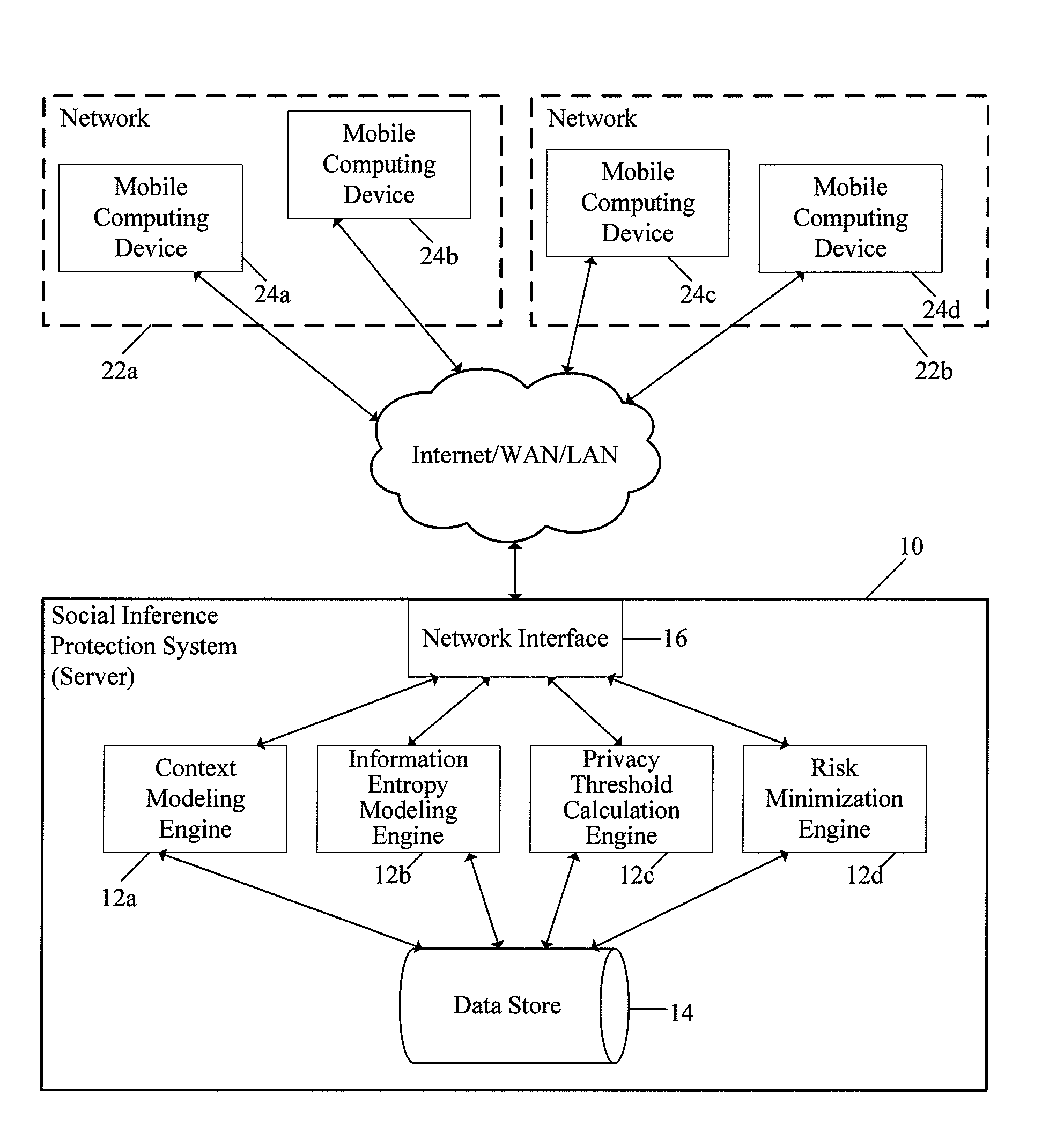
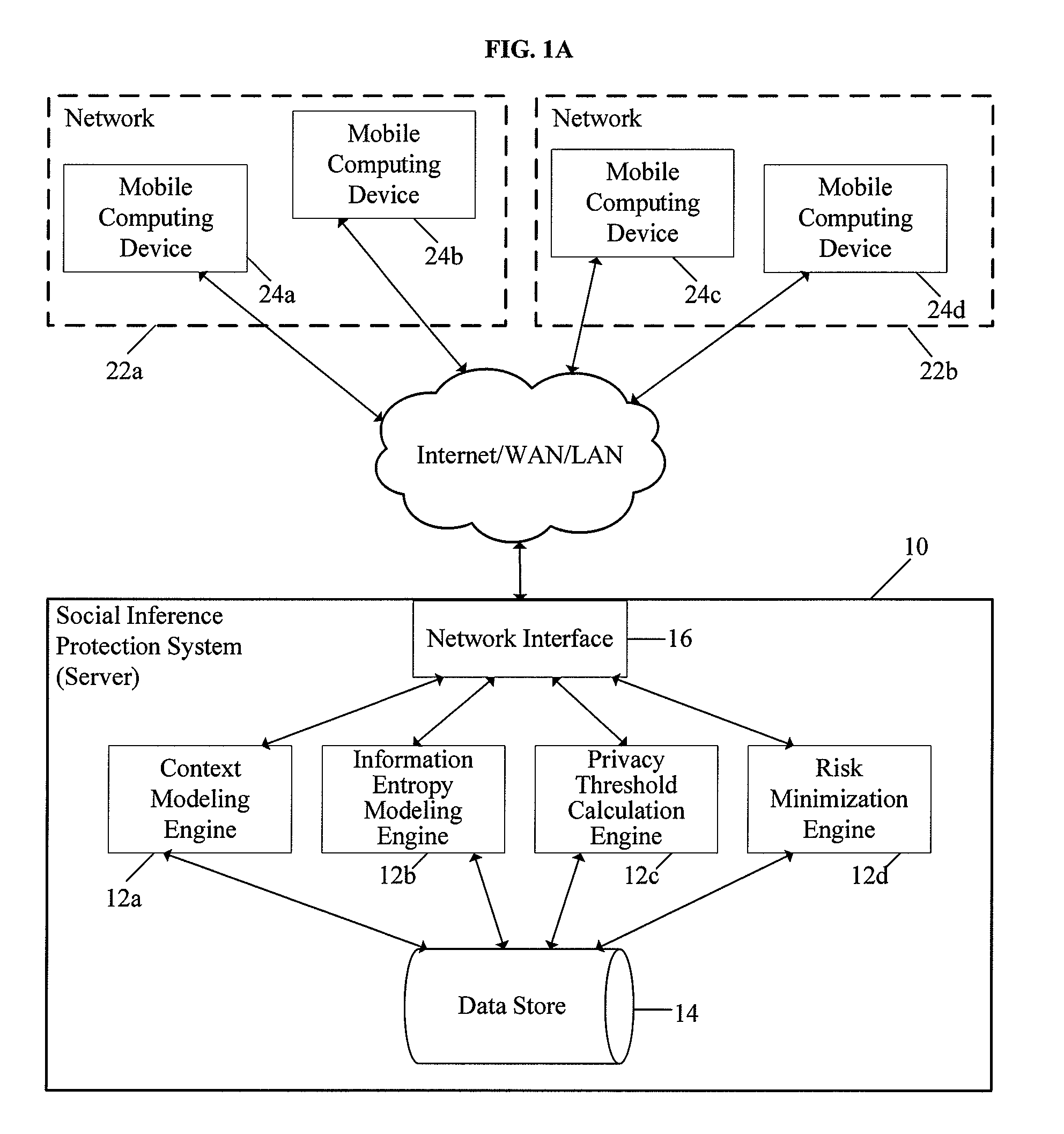
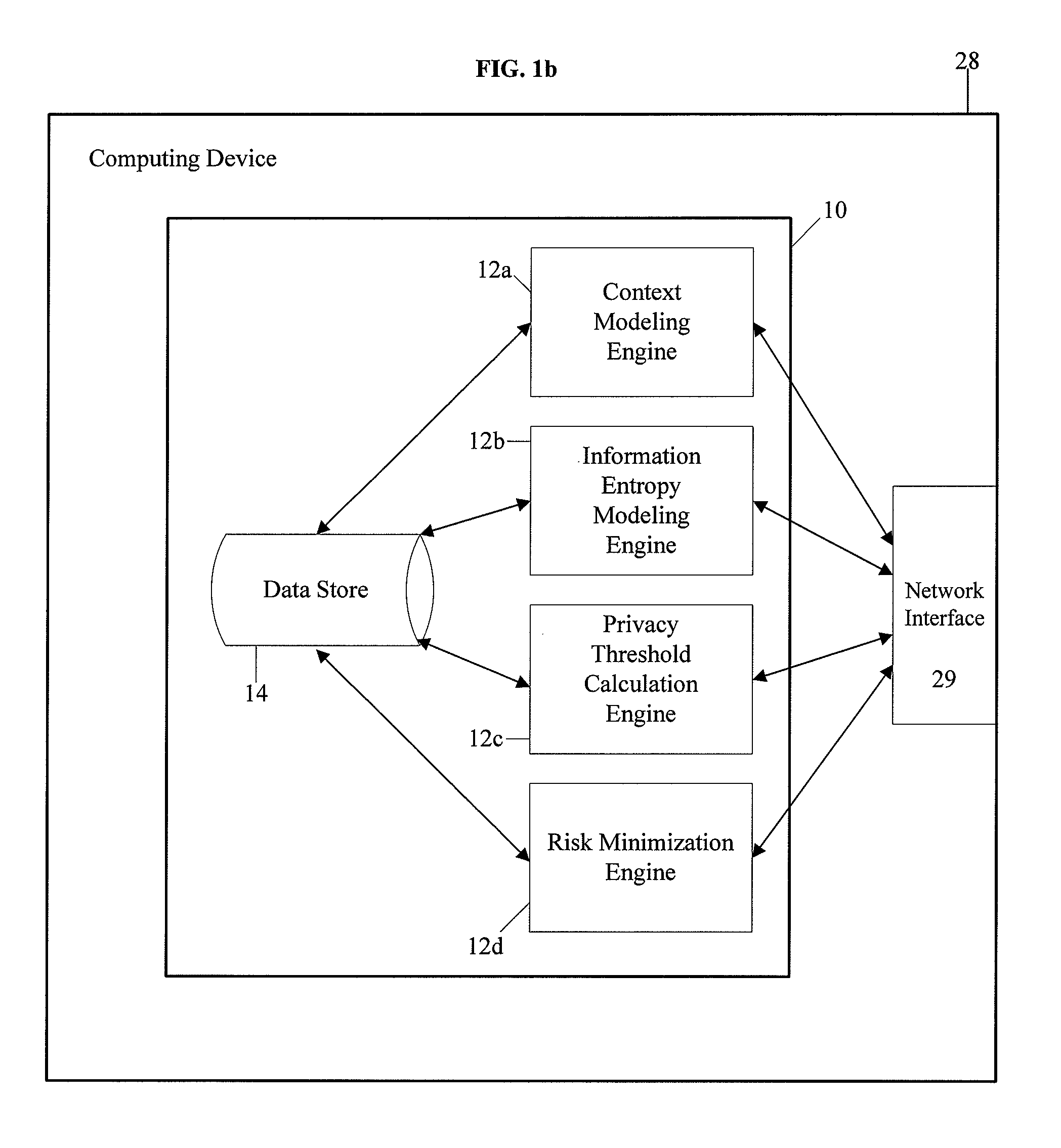
System and method for protecting user privacy using social inference protection techniques
InactiveUS8504481B2Minimize privacy riskInhibit exchangeDigital data processing detailsAnalogue secracy/subscription systemsInternet privacyUser privacy
A system and method for protecting user privacy using social inference protection techniques is provided. The system executes a plurality of software modules which model of background knowledge associated with one or more users of the mobile computing devices; estimate information entropy of a user attribute which could include identity, location, profile information, etc.; utilize the information entropy models to predict the social inference risk; and minimize privacy risks by taking a protective action after detecting a high risk.
Owner:NEW JERSEY INSTITUTE OF TECHNOLOGY
Dynamic pricing system and method for complex energy securities
A dynamic pricing system for complex energy securities, comprising a communications interface executing on a network-connected server and adapted to receive information from a plurality of iNodes, an event database coupled to the communications interface and adapted to receive events from a plurality of iNodes via the communications interface, a pricing server coupled to the communications interface, and a statistics server coupled to the event database and the pricing server, is disclosed. According to the invention, the pricing server, on receiving a request to establish a price for an energy security, requests at least one statistical indicia of risk from the statistics server, the statistical indicia of risk being computed by the statistics server based on a plurality of historical data obtained from the event database, and the pricing server computes a price for the security based at least in part on the statistical indicia of risk.
Owner:CRABTREE JASON +3
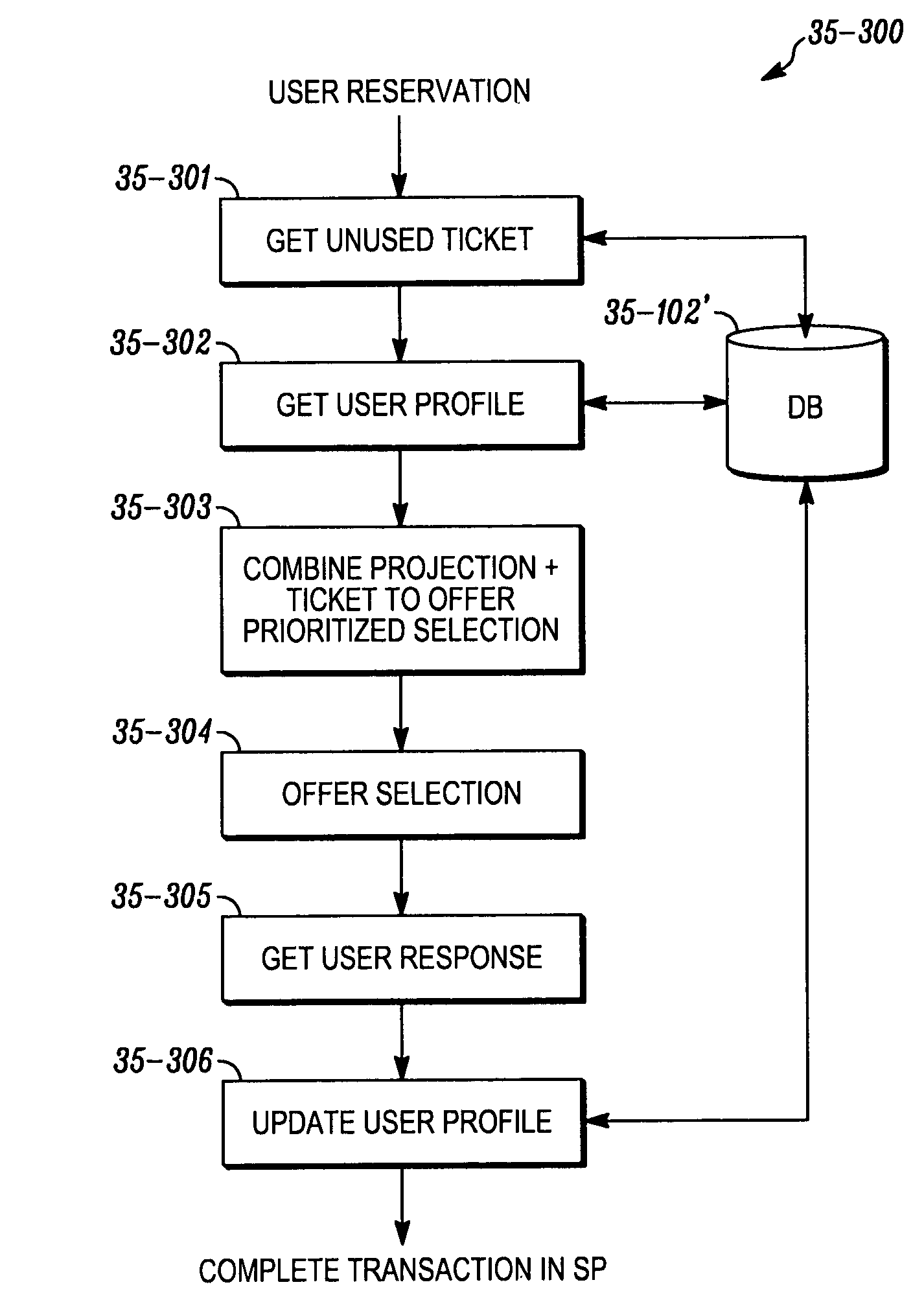
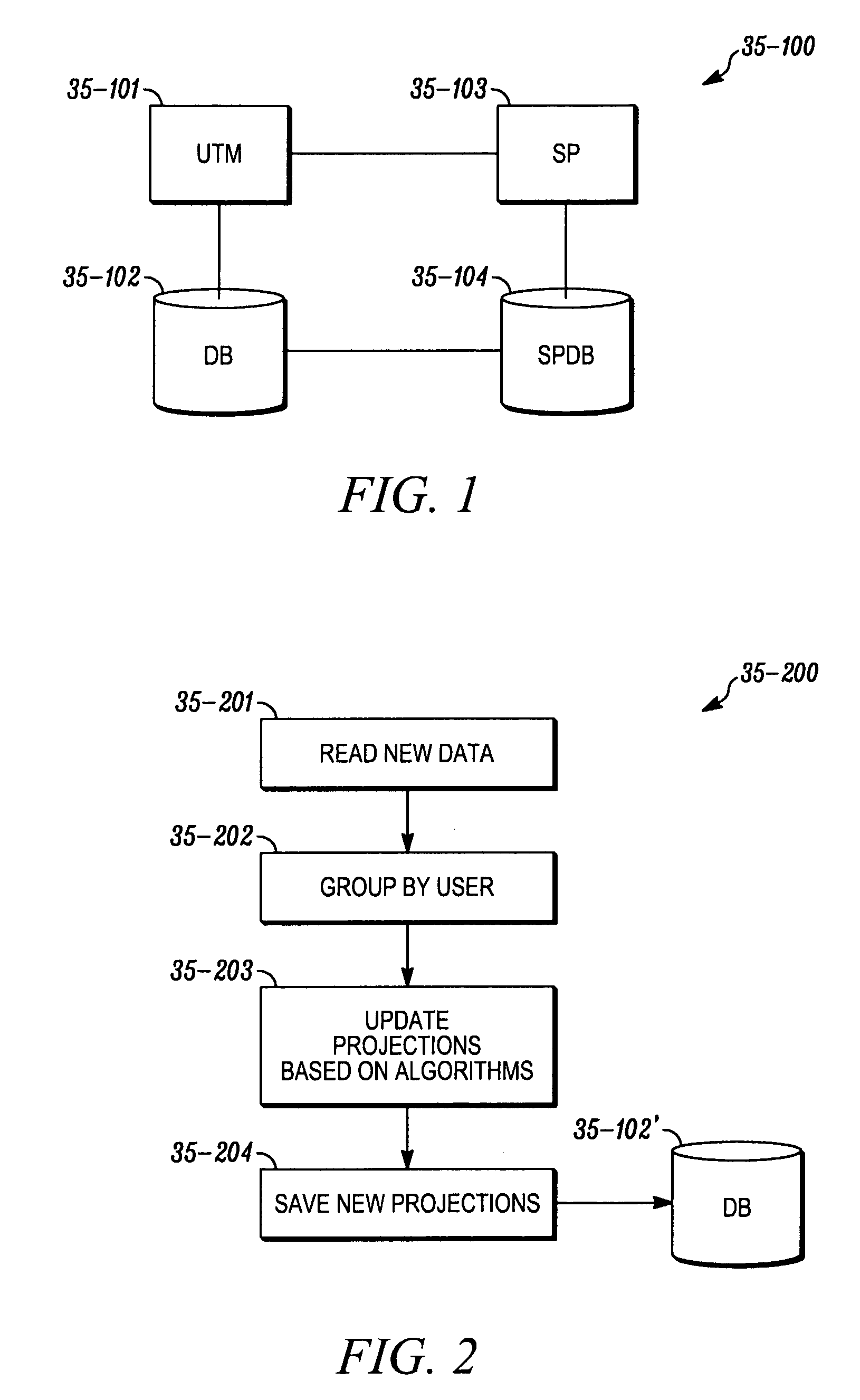
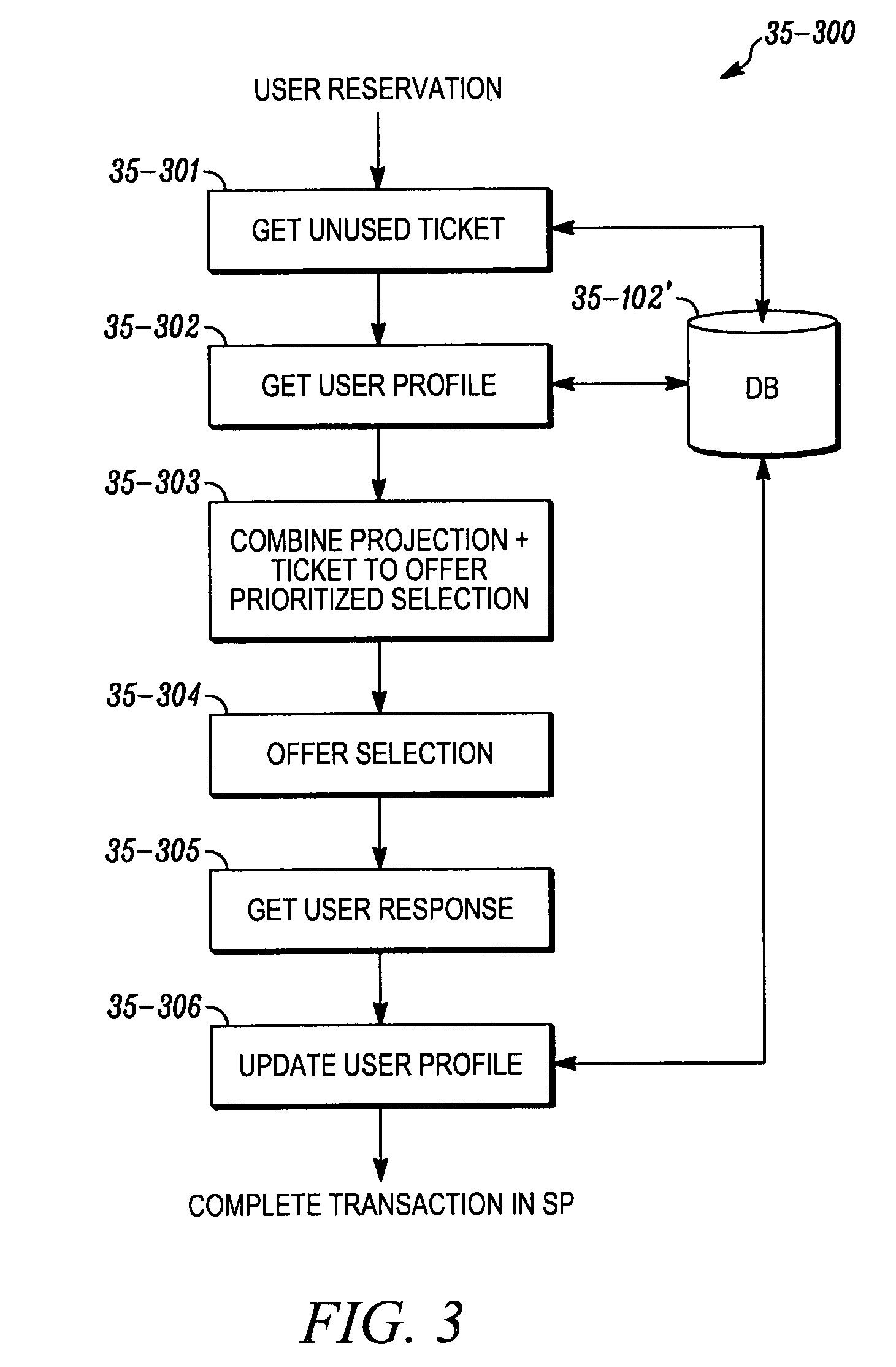
Method and system for unused ticket management
A method and system for unused ticket management, that identifying travel data related to one of future or past travel data for one or more travelers; identifying one or more unused travel purchase; generating a value for the unused travel purchase, the value corresponding to the one or more travelers, the respective values based at least in part on the travel data of the one or more travelers; and presenting to at least one of the one or more travelers, one or more options of unused travel purchases and the respective generated values.
Owner:DEEM
Systems and methods for processing data flows
InactiveUS20080262990A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData streamData integrity
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
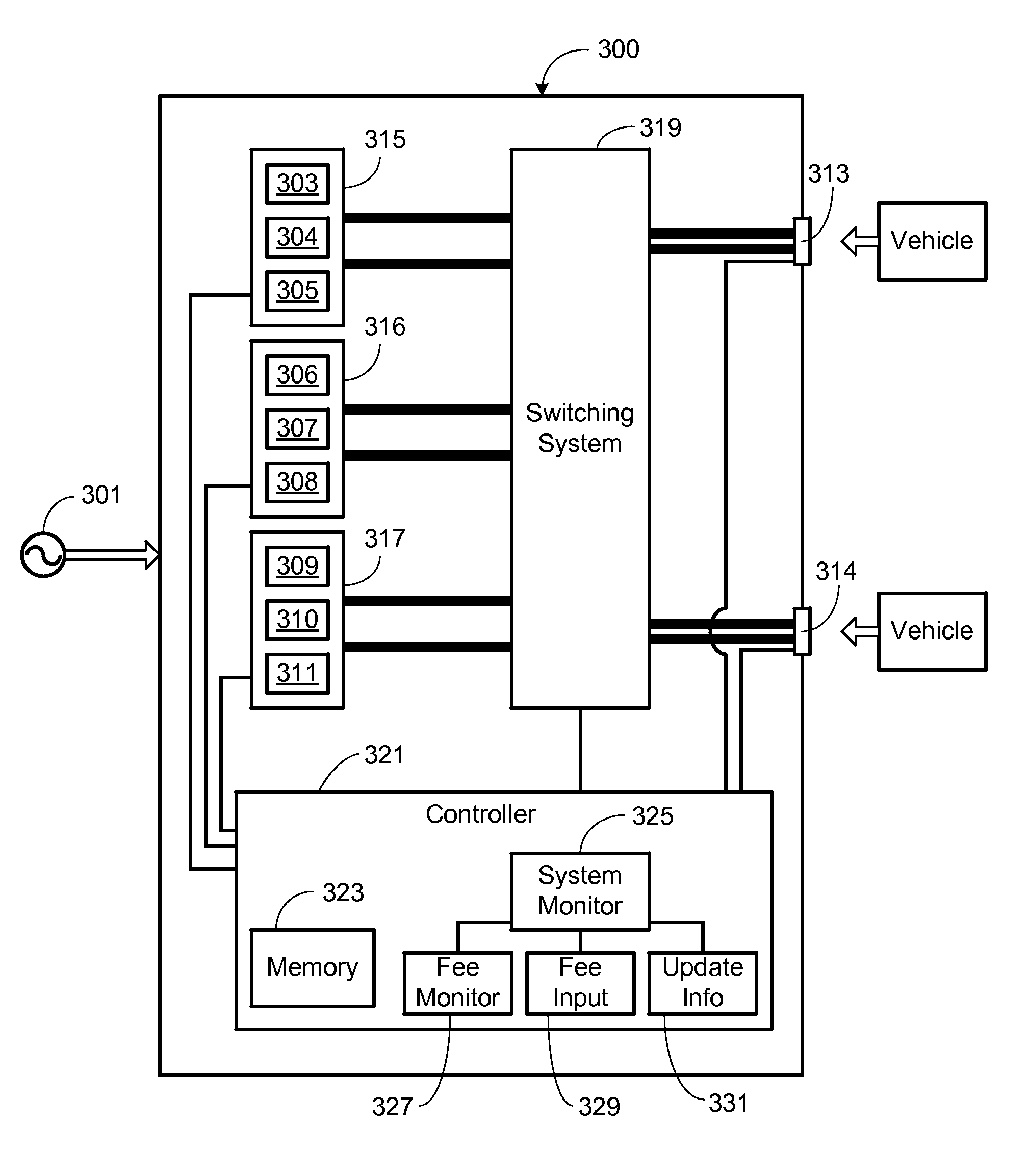
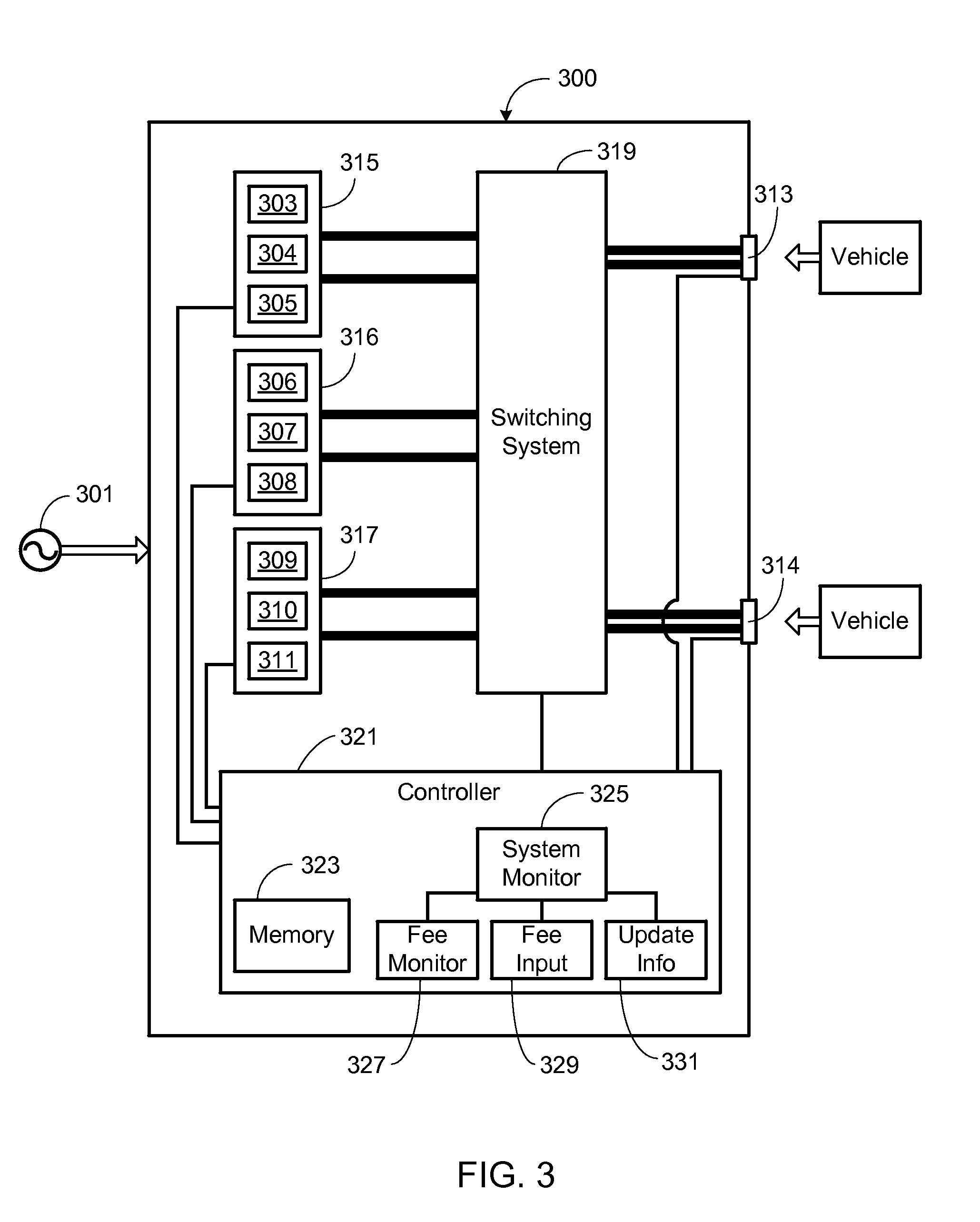
Method of Operating a Multiport Vehicle Charging System
ActiveUS20130057210A1Avoid direct connectionMobile unit charging stationsPower to auxillary motorsBattery chargeElectrical battery
A method of distributing charging power among a plurality of charge ports of a battery charging station is provided, where the battery charging station includes a plurality of power stages where each power stage includes an AC to DC converter and provides a portion of the charging station's maximum available charging power, the method comprising the steps of (i) monitoring battery charging station conditions and operating conditions for each charging port; (ii) determining current battery charging station conditions, including current operating conditions for each charging port; (iii) determining power distribution for the battery charging station and the charging ports in response to the current battery charging conditions and in accordance with a predefined set of power distribution rules; and (iv) coupling the power stages to the charging ports in accordance with the power distribution.
Owner:TESLA INC
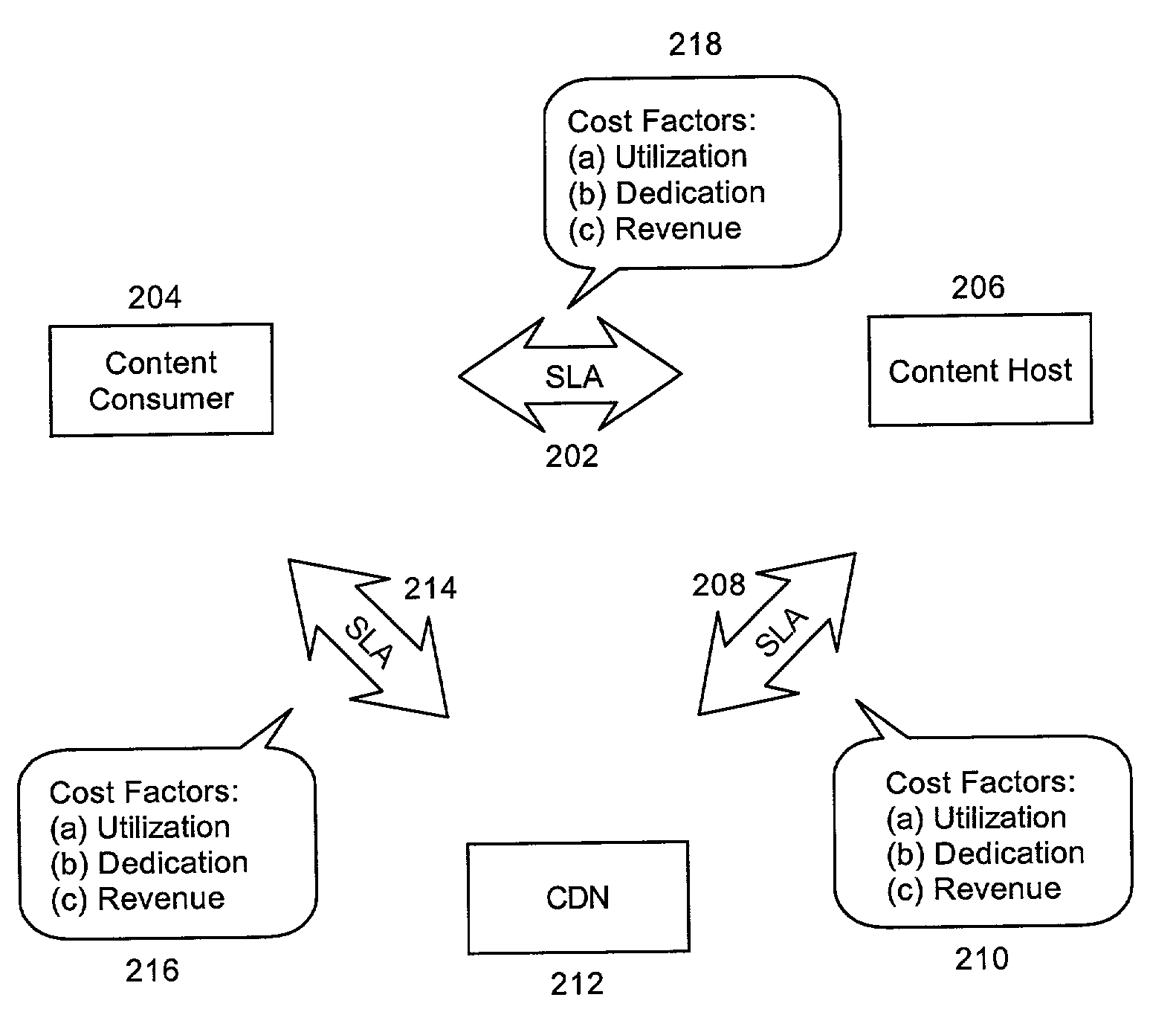
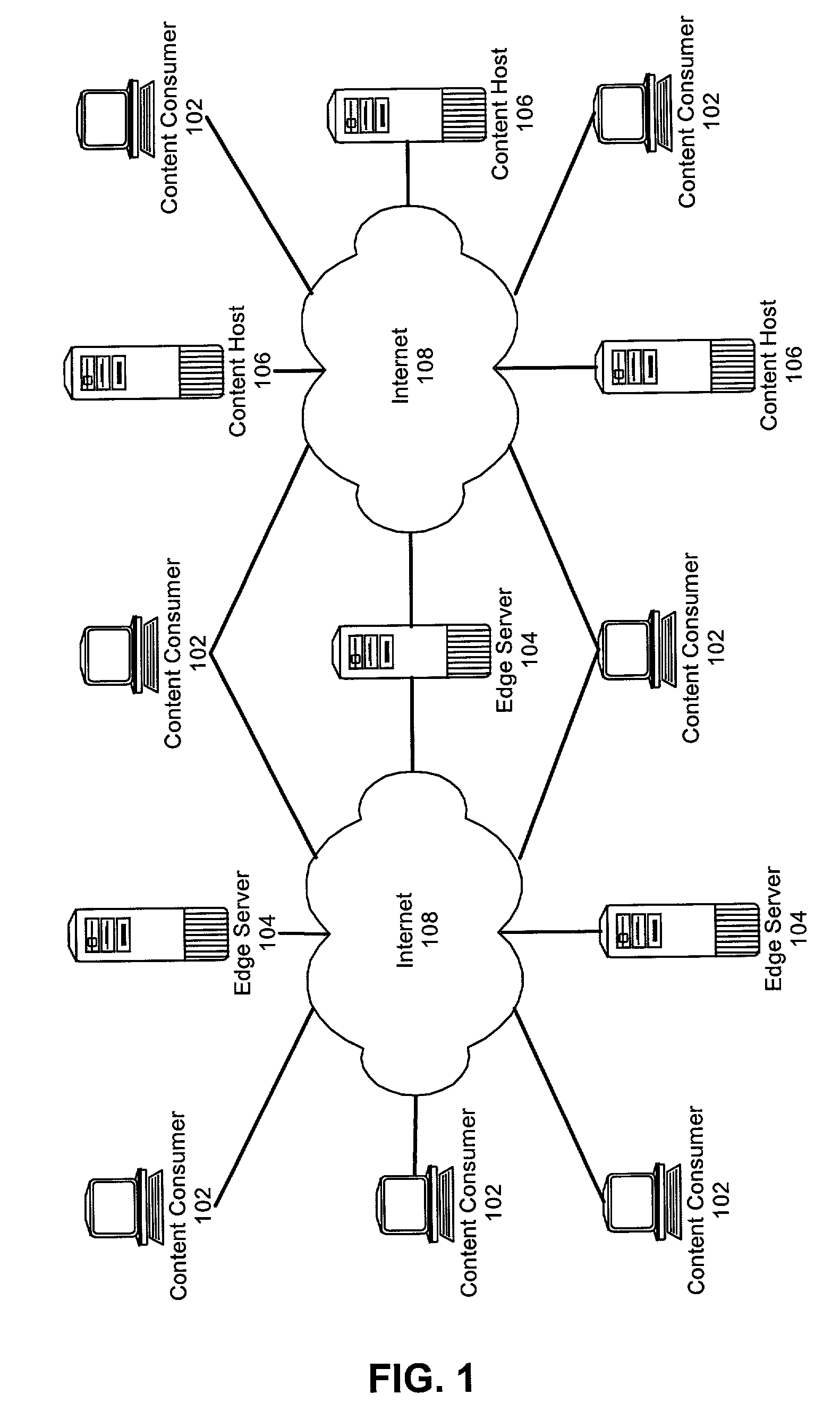
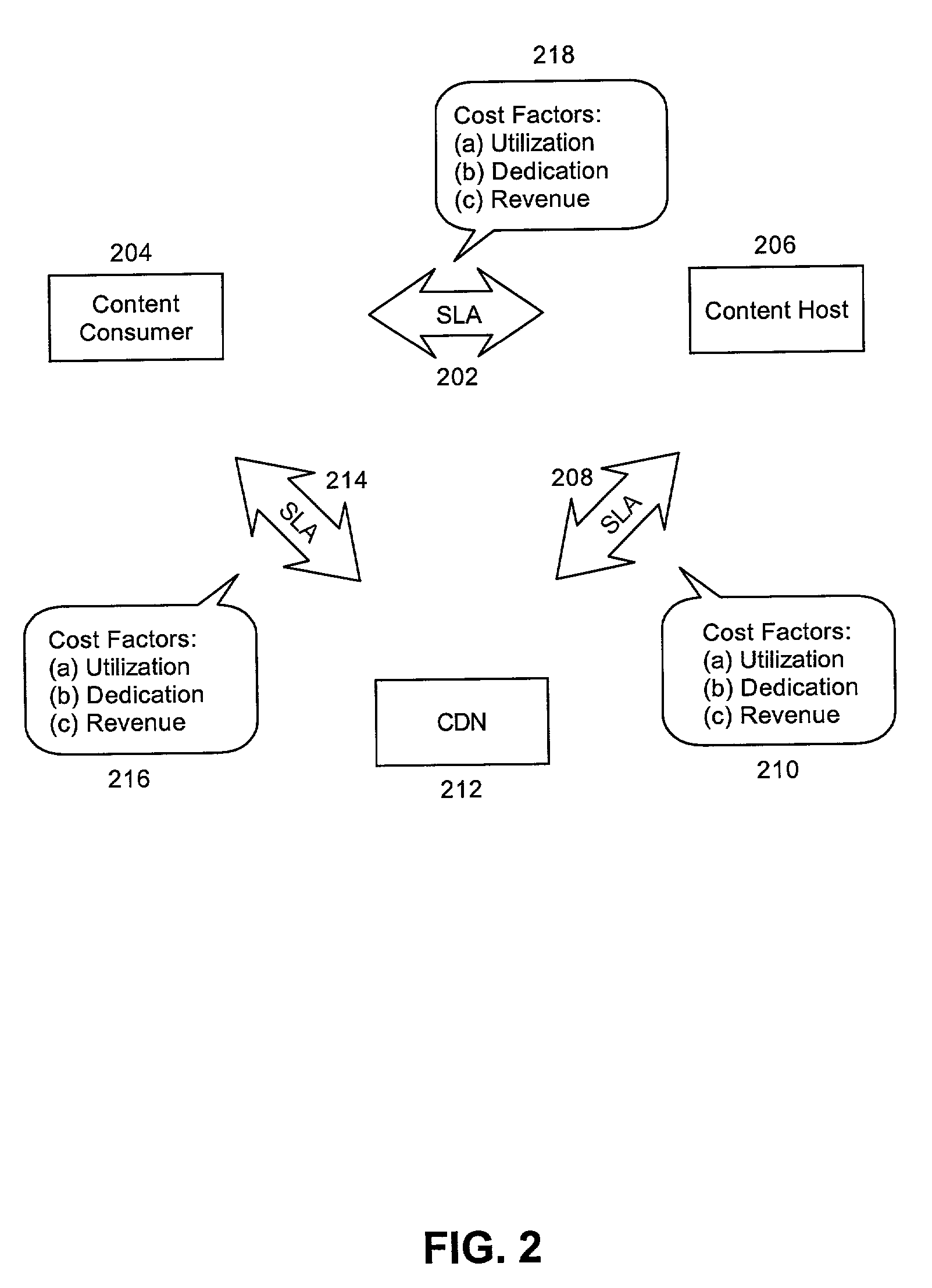
Multi-tier service level agreement method and system
ActiveUS7099936B2Overcome limitationsMultiple digital computer combinationsResourcesService-level agreementEdge server
A method for managing multi-tier SLA relationships. The method can include first computing costs of utilizing edge server resources in a CDN, costs of dedicating content host resources in a content host in lieu of the utilization, and prospective revenues which can be generated by the content host providing services based on the resources to content consumers. Minimum QoS levels can be identified which must be maintained when providing the services to the content consumers according to QoS terms in established SLAs between the content host and individual ones of the content consumers. Finally, a new SLA can be established between the content host and the CDN. Importantly, the new SLA can include QoS terms for selectively allocating resources in the CDN. Moreover, the QoS terms can optimize revenues generated by the content host providing services based on the selective allocation of resources and the computed costs.
Owner:IBM CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com