Vulnerability code clone detection method based on context semantics and patch verification
A detection method and context technology, applied in the computer field, can solve the problems of difficulty in vulnerability detection, large execution time, limited application scenarios, etc., and achieve the effects of wide range of use, reduction of false positives, and high detection efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
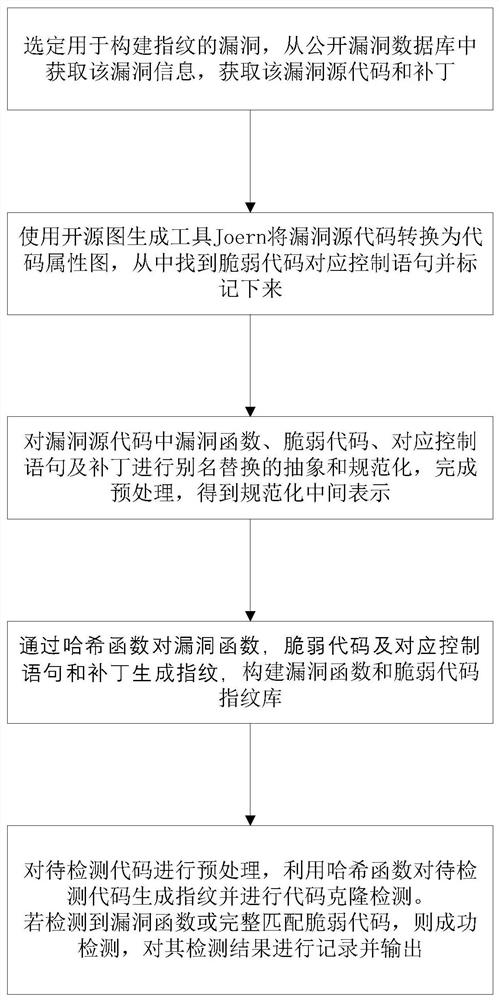
[0028] The application of software is becoming more and more extensive, the scale of software is also increasing, and the demand for software in scientific research and various industries is also increasing. The daily life of modern people is also inseparable from the support of software. Vulnerabilities inevitably appear in the software, and attackers can use the loopholes in the software to invade it, causing a large number of security incidents and threatening software security. Therefore, the detection of software loopholes can find loopholes in advance and reduce the probability of security incidents. Existing vulnerability detection methods cannot effectively detect code cloning of renaming and small additions, deletions and modifications of code, and lack of context and patch verification. The present invention proposes a vulnerability code cloning based on context semantics and patch verification after research and experiments on the above-mentioned status quo. Detectio...
Embodiment 2
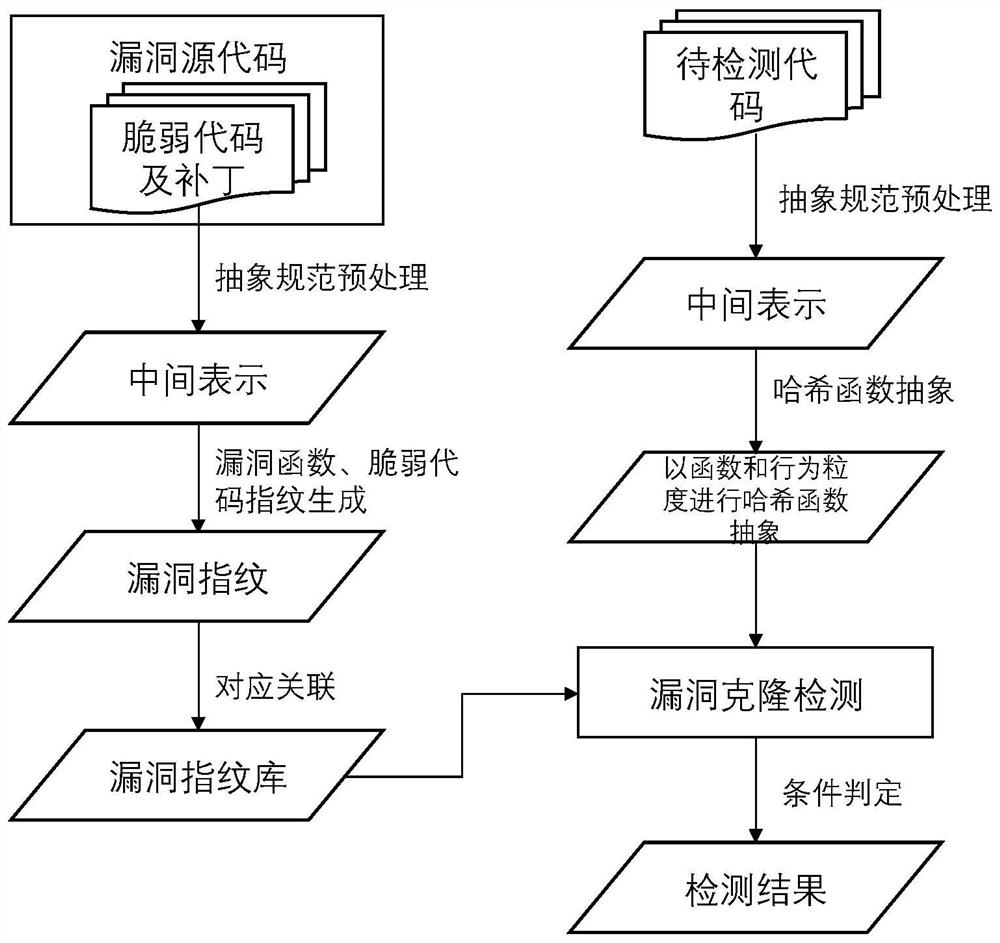
[0042] The vulnerability code clone detection method based on context semantics and patch verification is the same as in embodiment 1, the vulnerability source code and patch described in step 3 are preprocessed with abstract normalization for renaming clones, first by deleting comments, spaces, tabulations Characters and line breaks, and convert all characters to lowercase letters, normalize the source code of the vulnerability, and eliminate the influence of factors that have nothing to do with grammar on the detection results. Then perform uniform alias replacement for parameter names, local variables, data types and function call names in the code; collect formal parameters from the parameters of the function header, and replace each parameter variable that appears in the function with the symbol FPARAM. The present invention replaces all local variables that appear in the code with the symbol LVAR; Replaces the data type with the symbol DTYPE; In the present invention, the...
Embodiment 3
[0045] The flow analysis code clone detection method based on the vulnerability fingerprint is the same as that of the embodiment 1-2, step 4 to construct the vulnerability function and the vulnerability code fingerprint library, including the following steps:
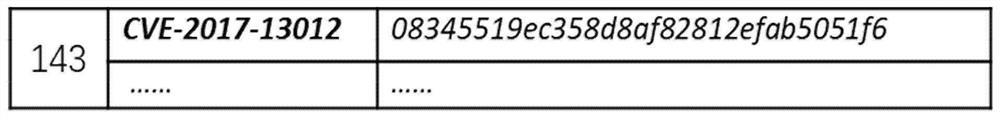
[0046] Step 4.1) By using the MD5 hash algorithm, process the vulnerable function of the vulnerable code, generate the fingerprint of the vulnerable function, and save the length of the vulnerable function, the CVE number of the vulnerable function and the fingerprint of the vulnerable function as three elements as a triplet. Enter the vulnerability function fingerprint library.
[0047] Step 4.2) Use the MD5 hash algorithm to process vulnerable codes, corresponding control statements, and patches, respectively generate vulnerable codes, corresponding control statements, and patch fingerprints line by line, store them in the vulnerable code fingerprint database in the order of statements, and then compare them with The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com