Method for detecting byte code similarity of N-Gram
A bytecode and similarity technology, applied in character and pattern recognition, electrical digital data processing, instruments, etc., can solve the problem of program running speed reduction and achieve fast execution speed, strong scalability, and simple operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
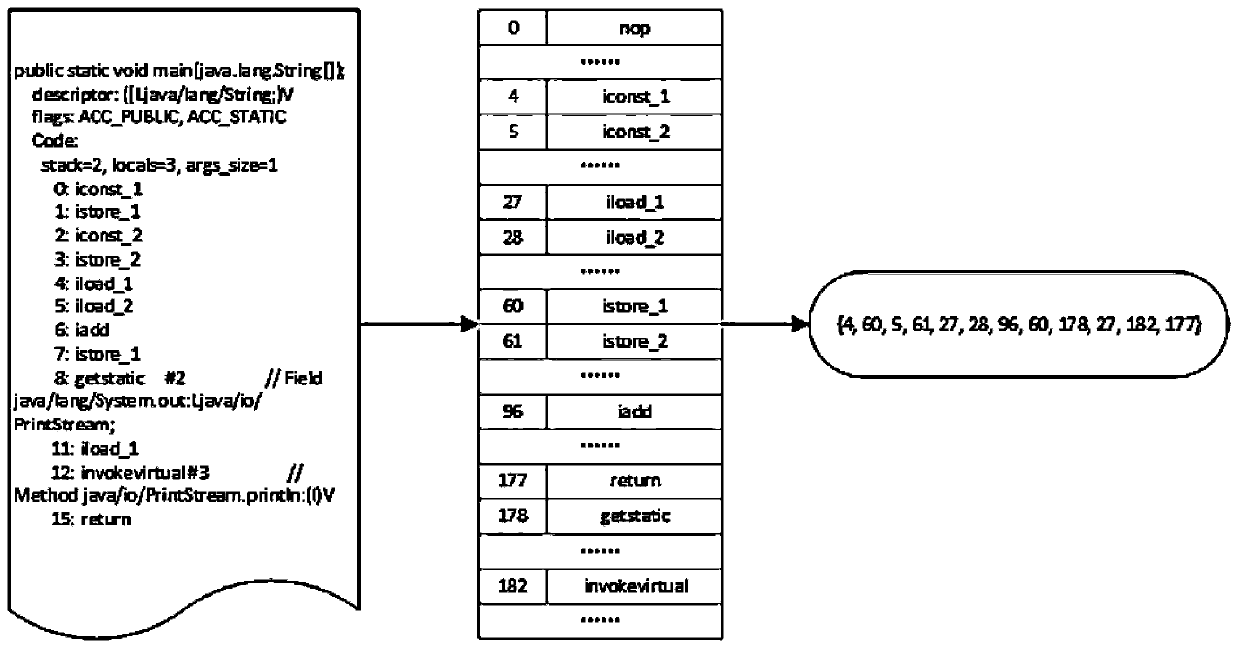
[0023] This embodiment uses Android R8 (ver.1.4.9). Android R8 is Google's new user-customizable bytecode obfuscator, which directly confuses and converts Java executable programs into Dalvikvm bytecodes, namely .dex files. The operating system is Ubuntu16.04, JDK1.8.
[0024] This embodiment includes the following steps:
[0025] Step 1) Data preparation: First, 50 obfuscation configuration files of Android R8 are randomly generated, and using different obfuscation configuration files will lead to differences in the final generated .dex files. Secondly, use Android R8 without any obfuscation configuration to convert the source Java program into a .dex file.
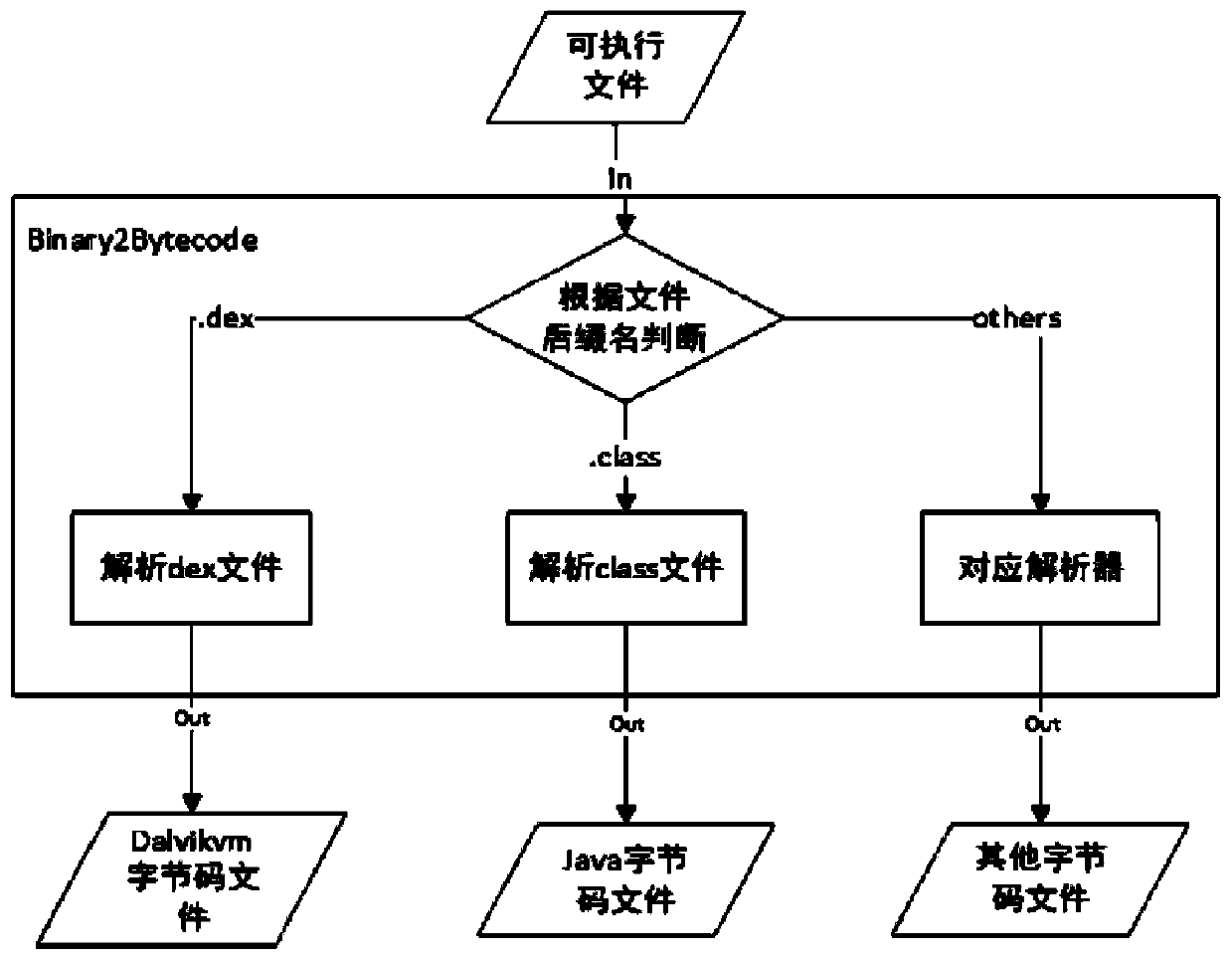
[0026] Transformation as described, using as figure 2 The shown Binary2Bytecode interface calls different decompilation tools by identifying the type of executable file. This design can shield the differences between executable files, and it is transparent to users who use this method.
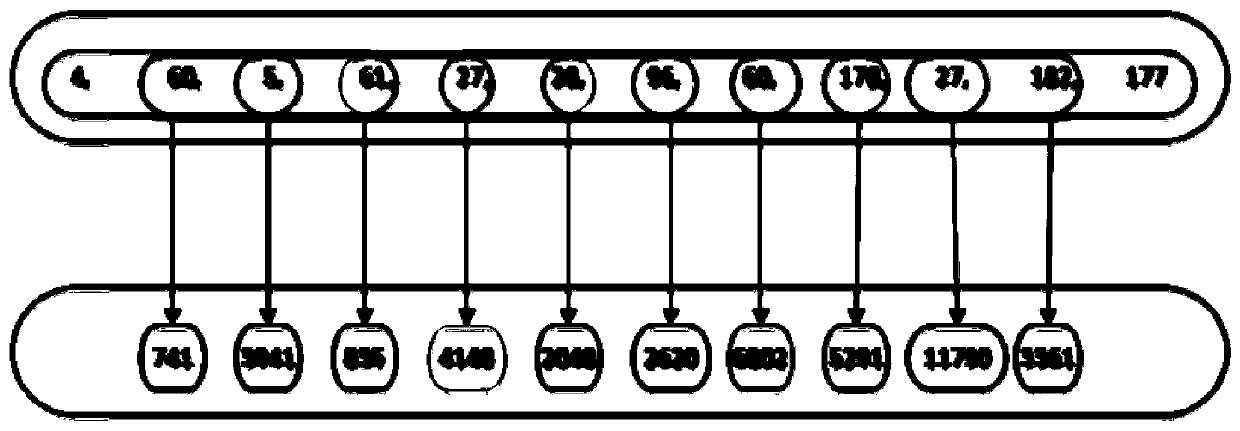
[0027] Step 2) Perform N-Gra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com