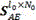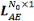Patents
Literature
54 results about "Relative probability" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Relative probability in British. (ˈrɛlətɪv ˌprɒbəˈbɪlɪtɪ) noun. statistics. a measure or estimate of the degree of confidence one may have in the occurrence of an event, defined as the limit of the proportion observed in a sample as the sample size tends to infinity.
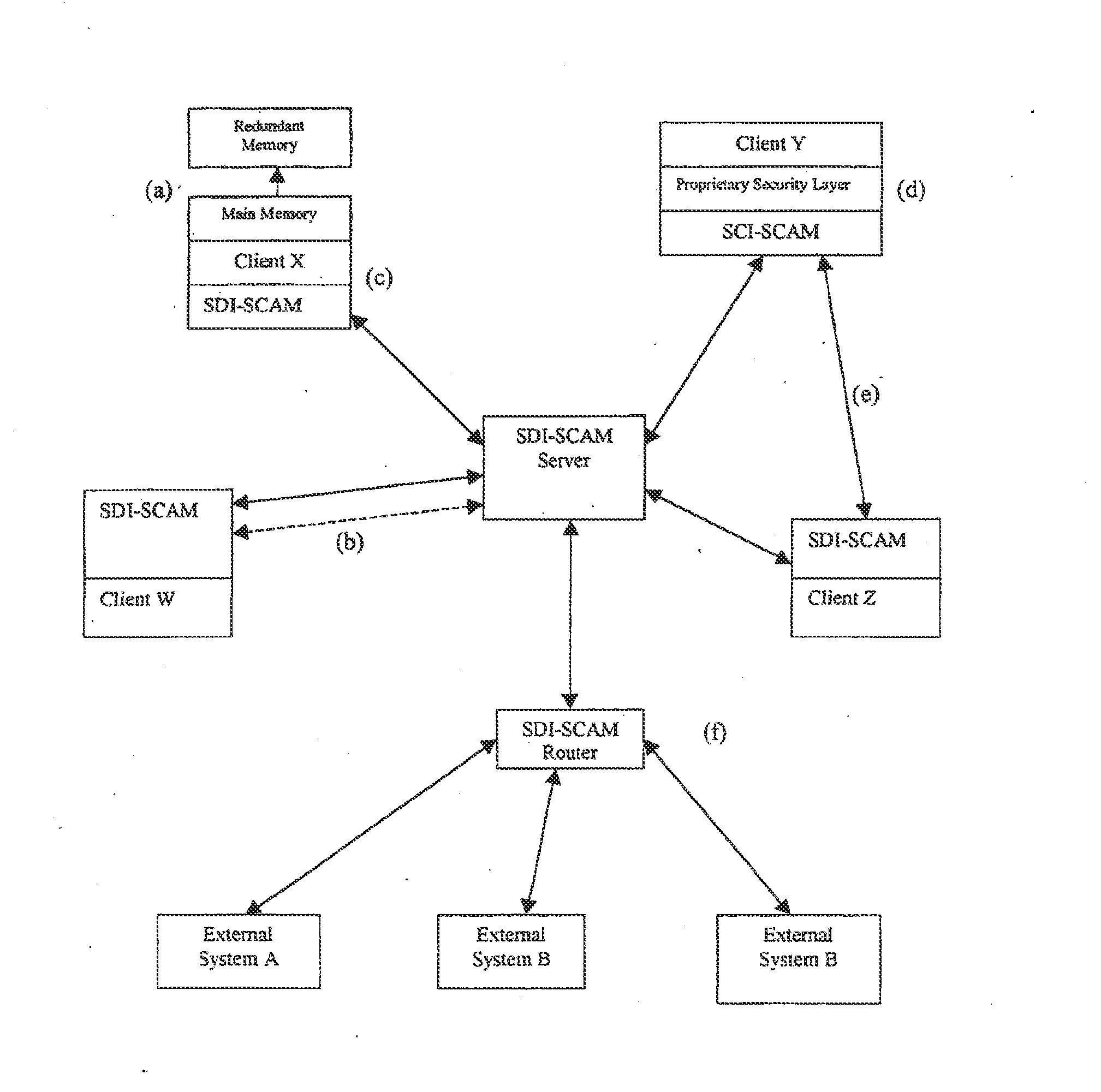
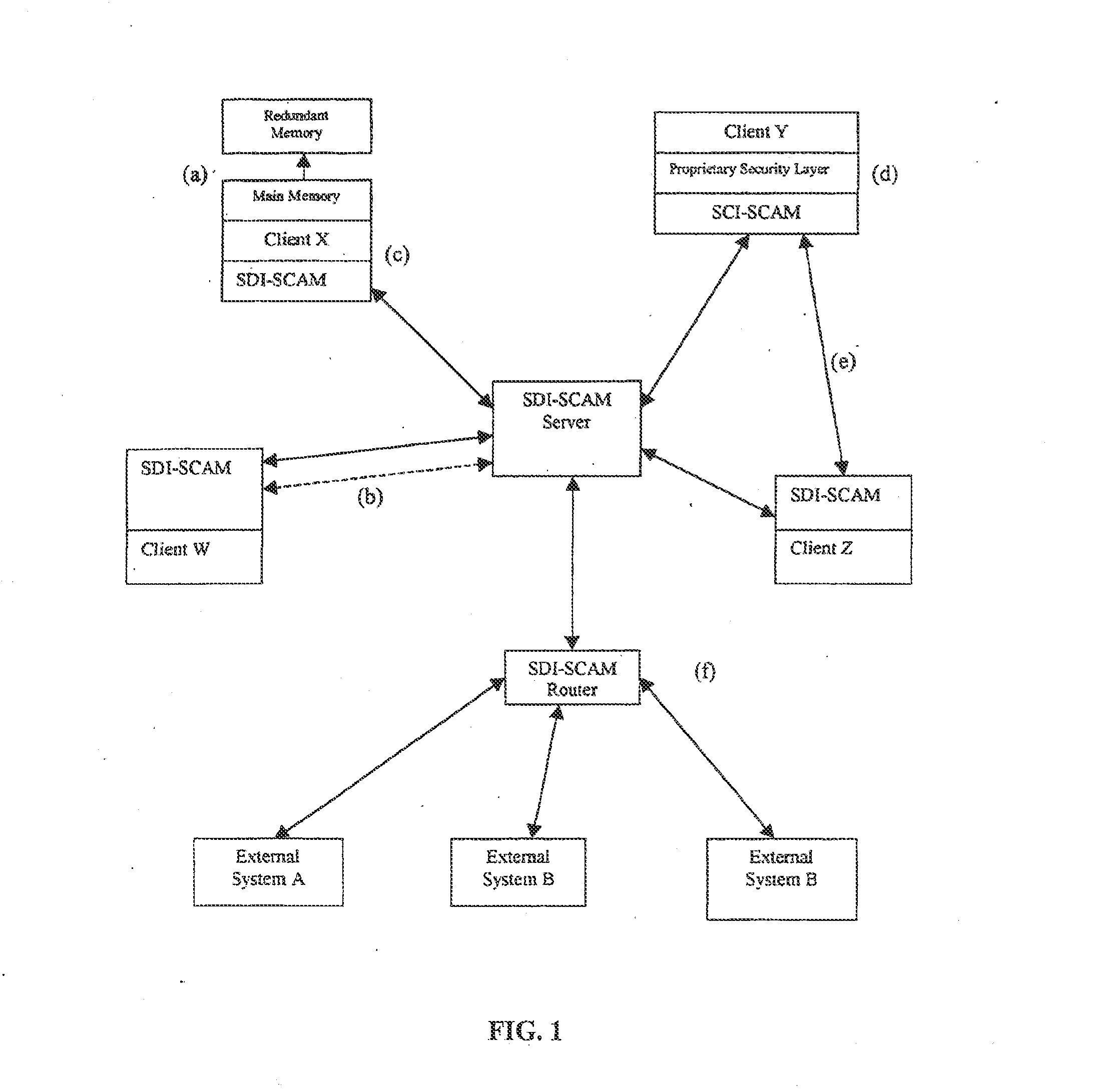
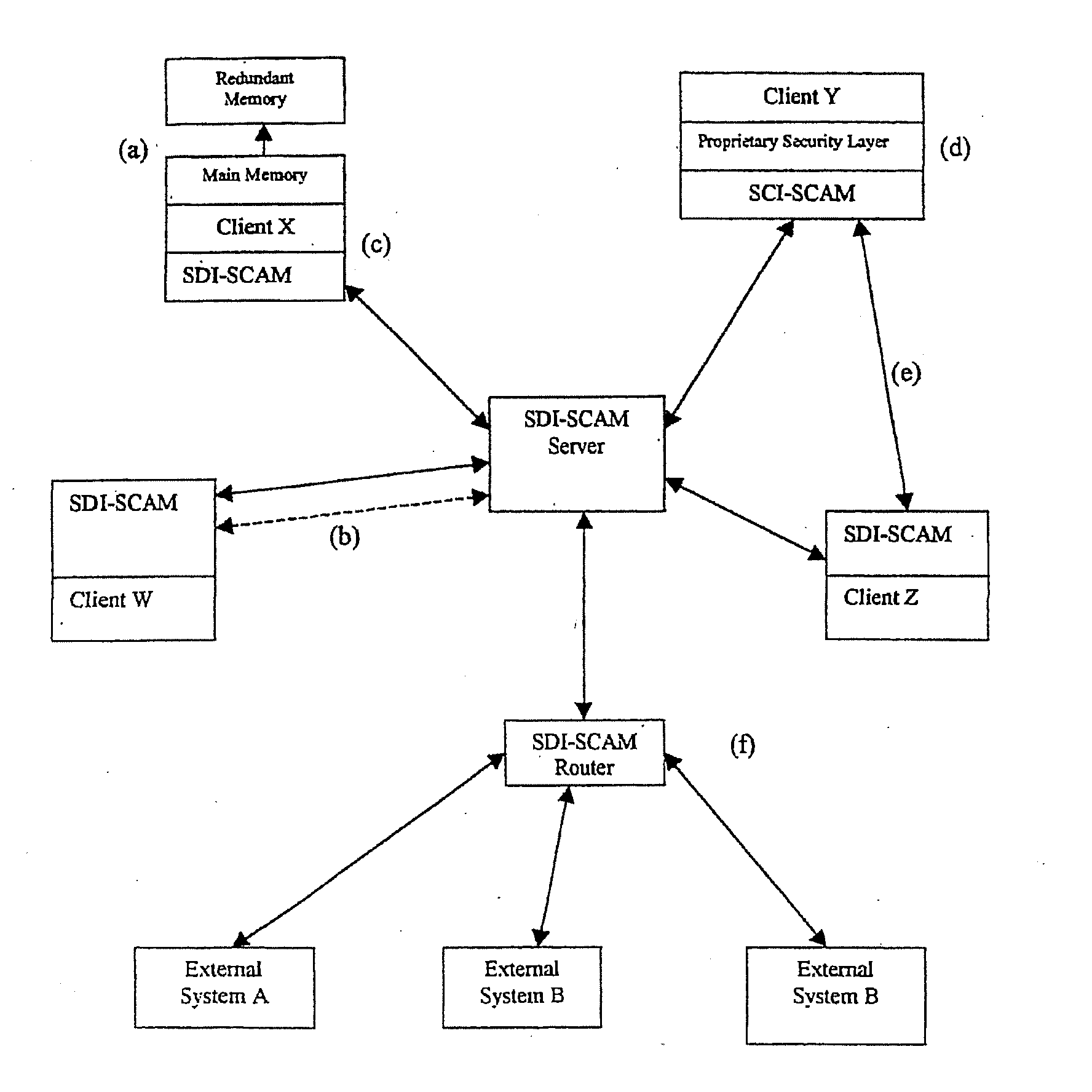
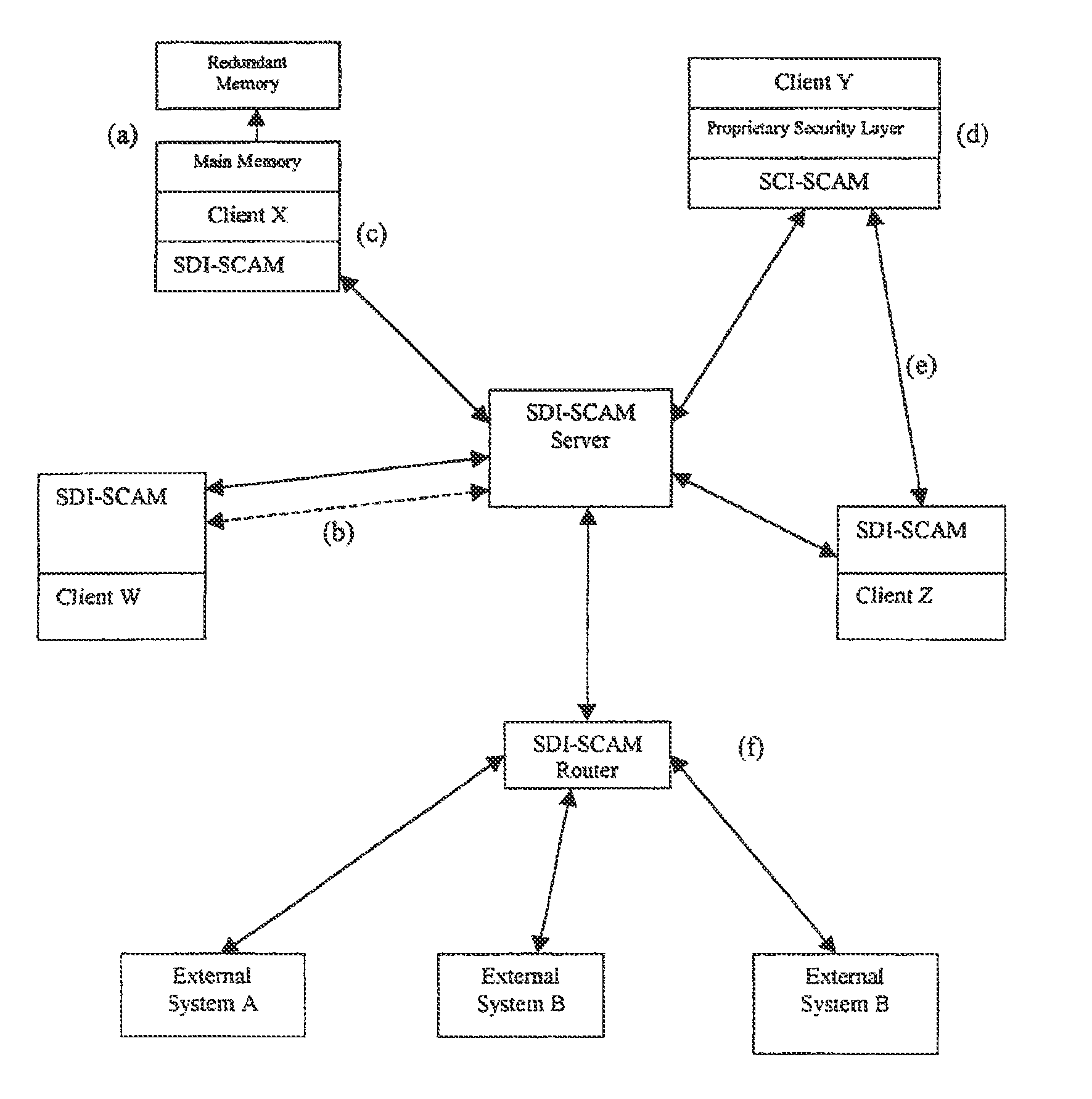
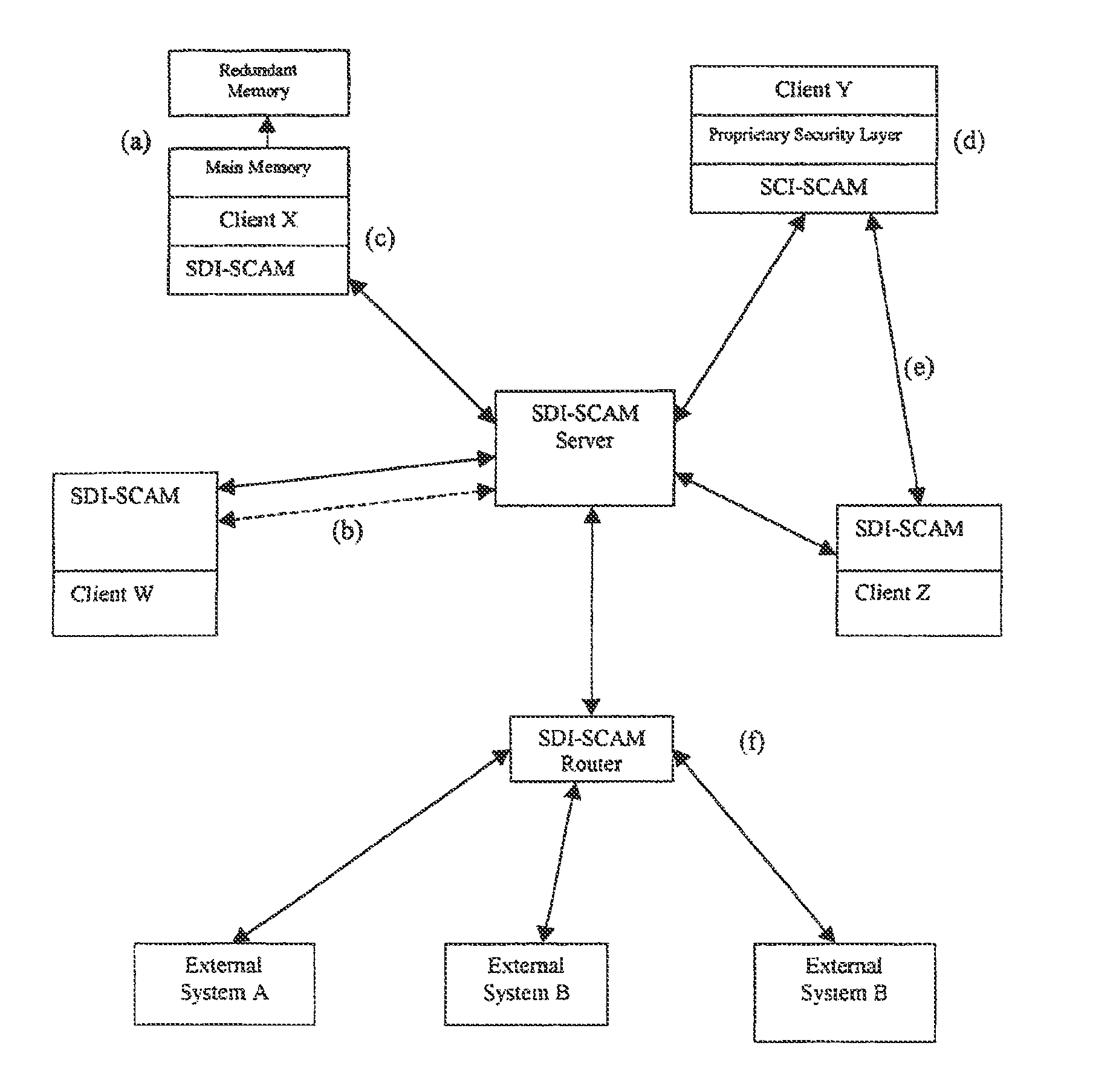
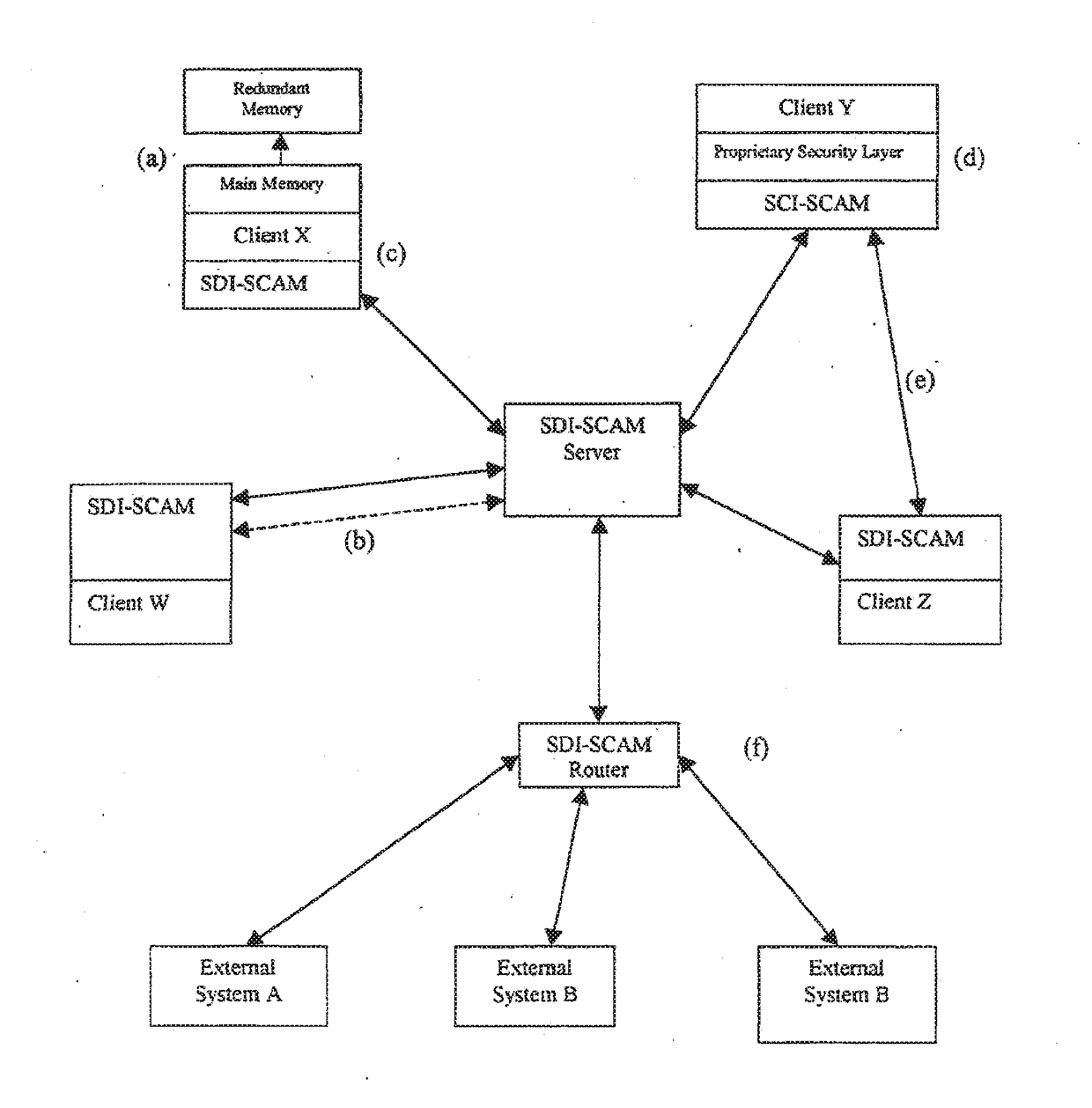
Distributed agent based model for security monitoring and response
ActiveUS20140237599A1Quick checkHigh and uniform level of securityMemory loss protectionError detection/correctionCountermeasureAgent-based model
An architecture is provided for a widely distributed security system (SDI-SCAM) that protects computers at individual client locations, but which constantly pools and analyzes information gathered from machines across a network in order to quickly detect patterns consistent with intrusion or attack, singular or coordinated. When a novel method of attack has been detected, the system distributes warnings and potential countermeasures to each individual machine on the network. Such a warning may potentially include a probability distribution of the likelihood of an intrusion or attack as well as the relative probabilistic likelihood that such potential intrusion possesses certain characteristics or typologies or even strategic objectives in order to best recommend and / or distribute to each machine the most befitting countermeasure(s) given all presently known particular data and associated predicted probabilistic information regarding the prospective intrusion or attack. If any systems are adversely affected, methods for repairing the damage are shared and redistributed throughout the network.
Owner:INVENTSHIP LLC
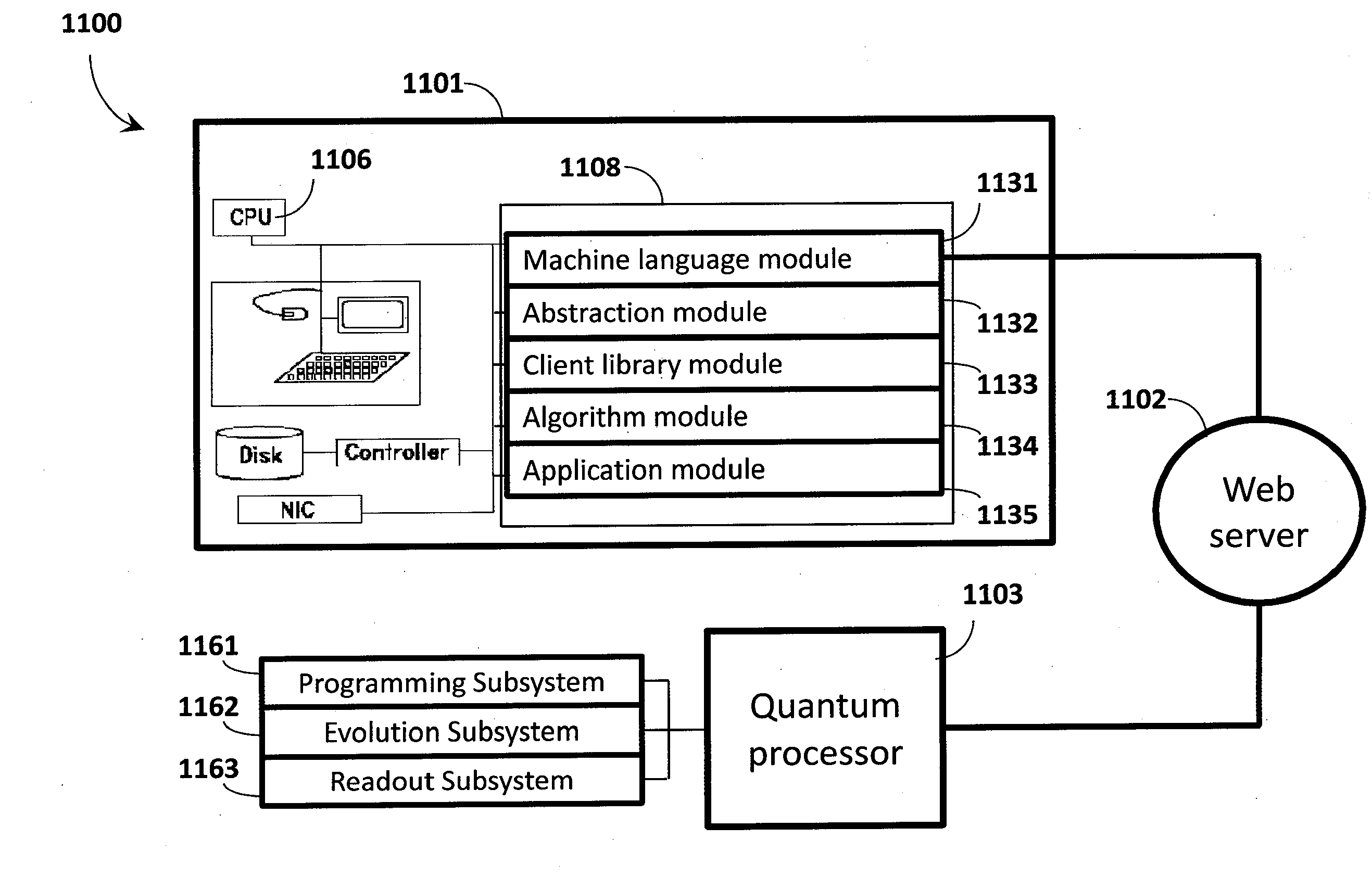
Quantum processor based systems and methods that minimize an objective function
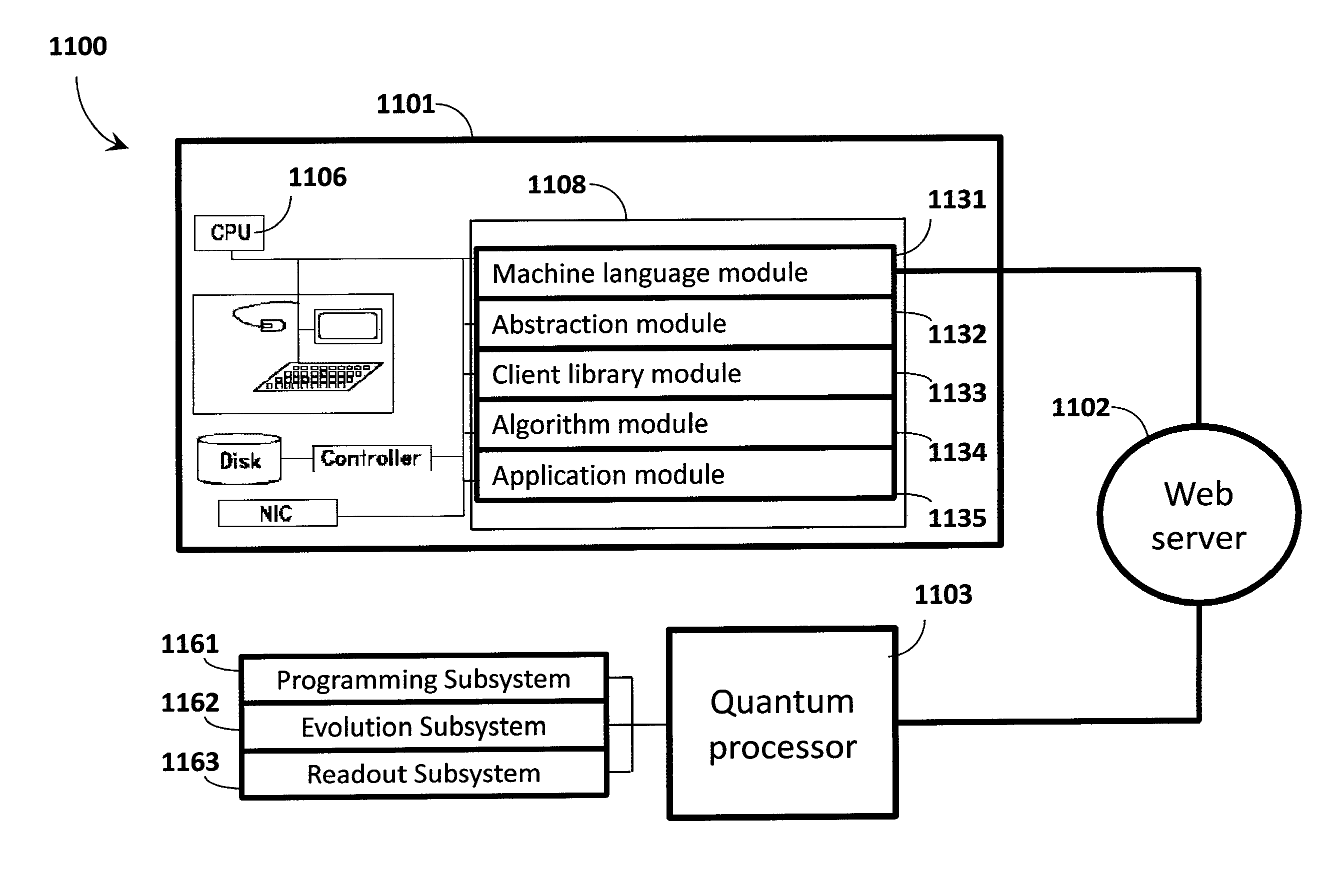
ActiveUS20140187427A1Accurate solutionQuick mergeQuantum computersMathematical modelsAlgorithmHigh probability
Quantum processor based techniques minimize an objective function for example by operating the quantum processor as a sample generator providing low-energy samples from a probability distribution with high probability. The probability distribution is shaped to assign relative probabilities to samples based on their corresponding objective function values until the samples converge on a minimum for the objective function. Problems having a number of variables and / or a connectivity between variables that does not match that of the quantum processor may be solved. Interaction with the quantum processor may be via a digital computer. The digital computer stores a hierarchical stack of software modules to facilitate interacting with the quantum processor via various levels of programming environment, from a machine language level up to an end-use applications level.
Owner:D WAVE SYSTEMS INC
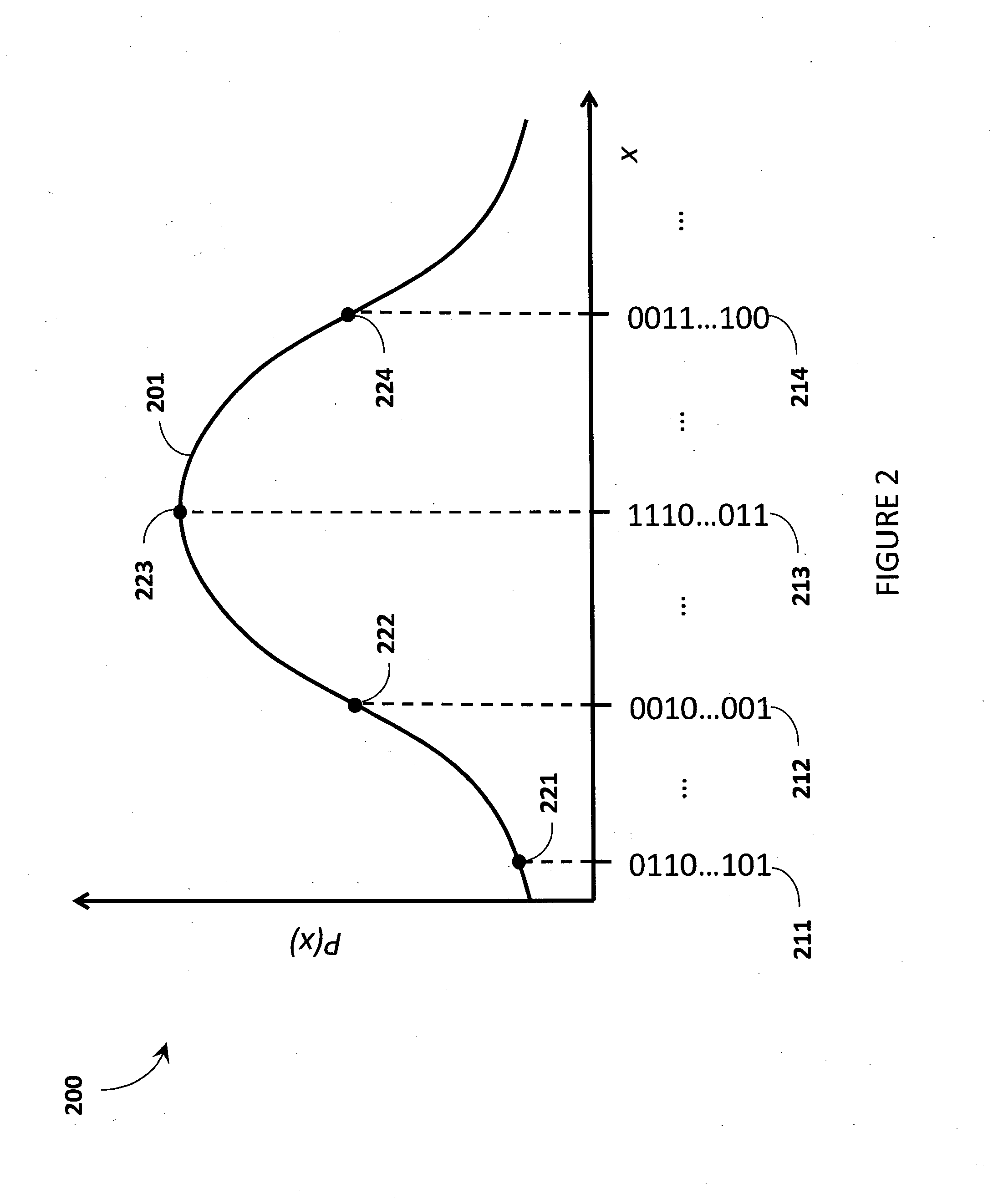
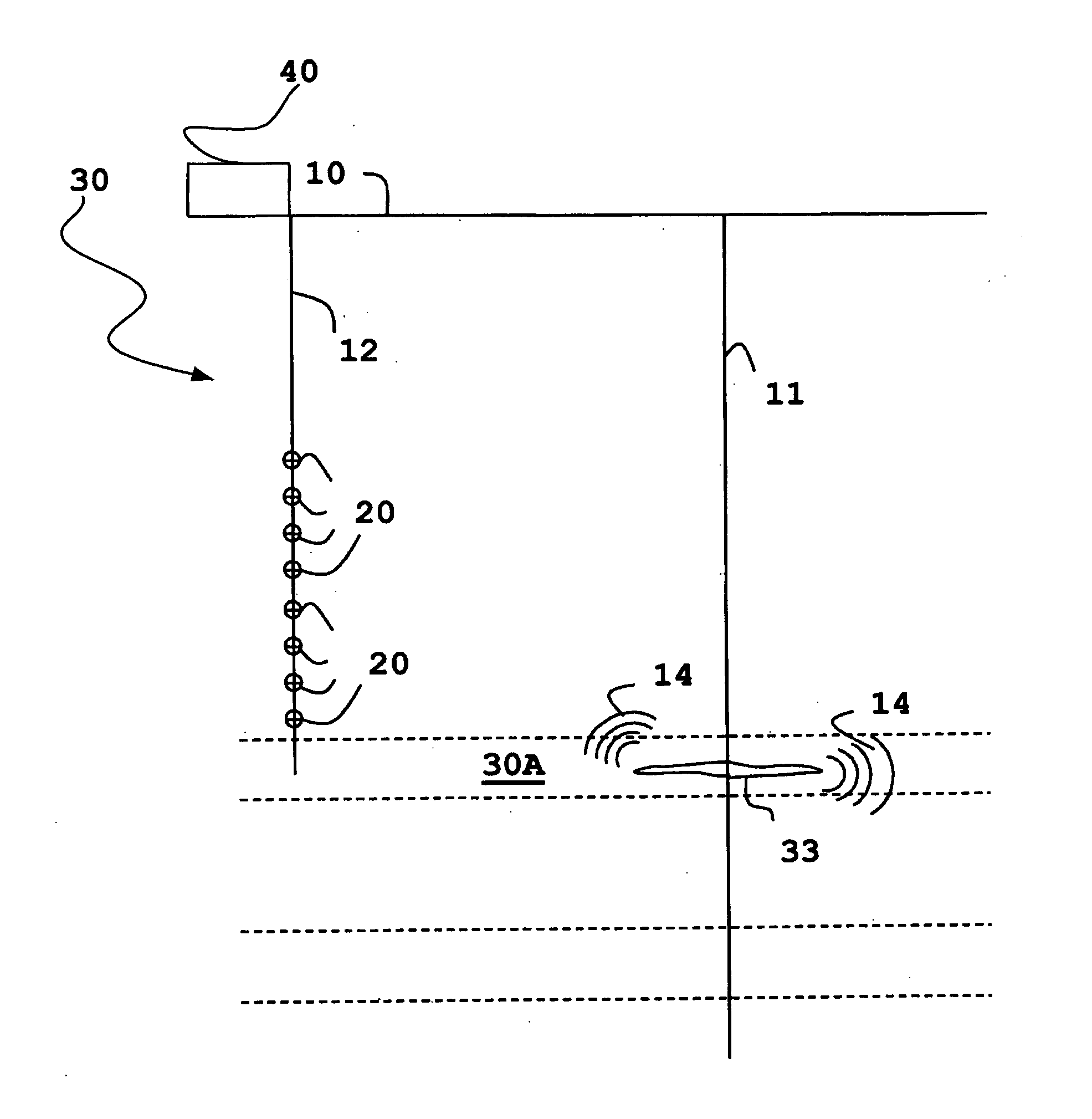
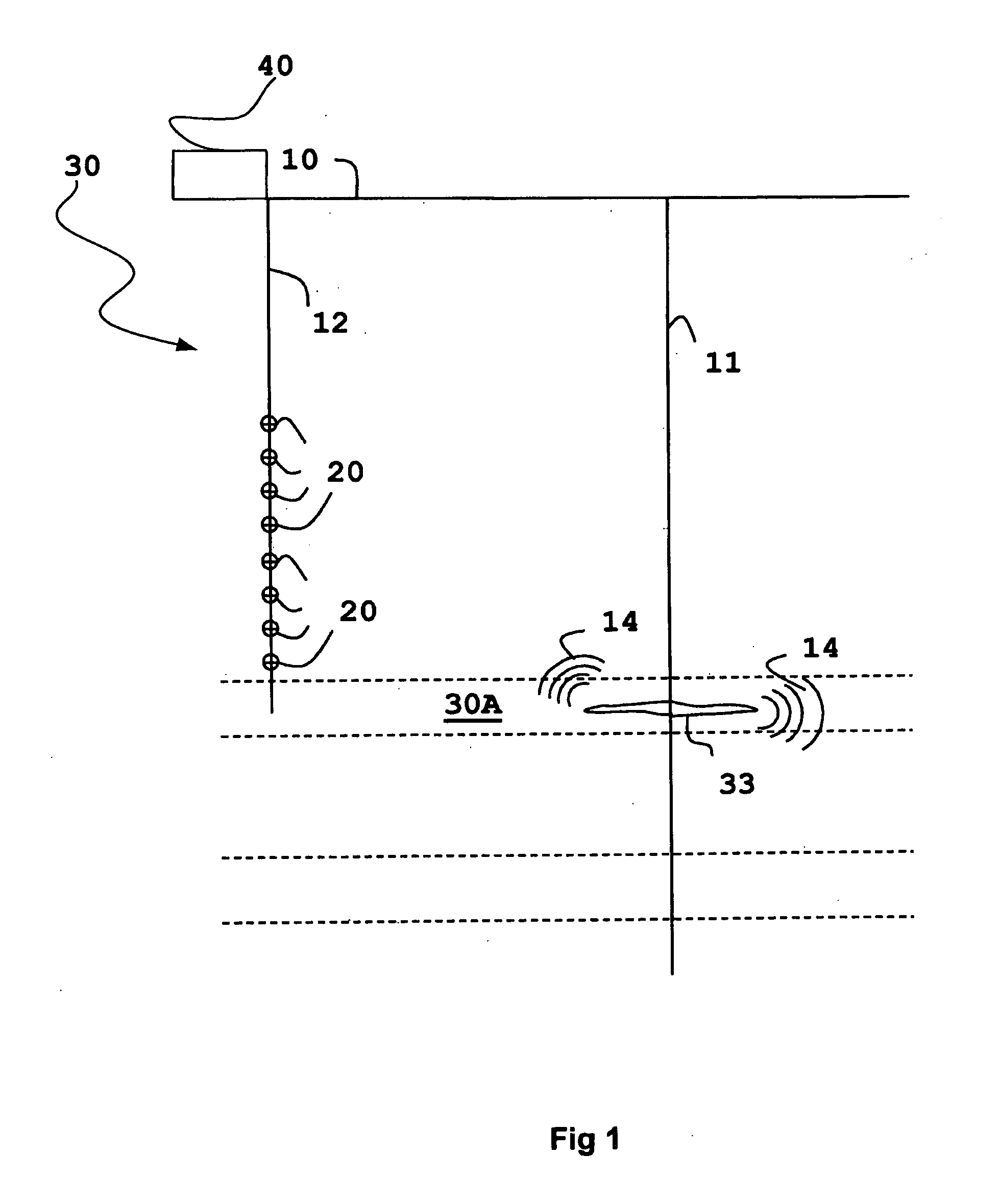
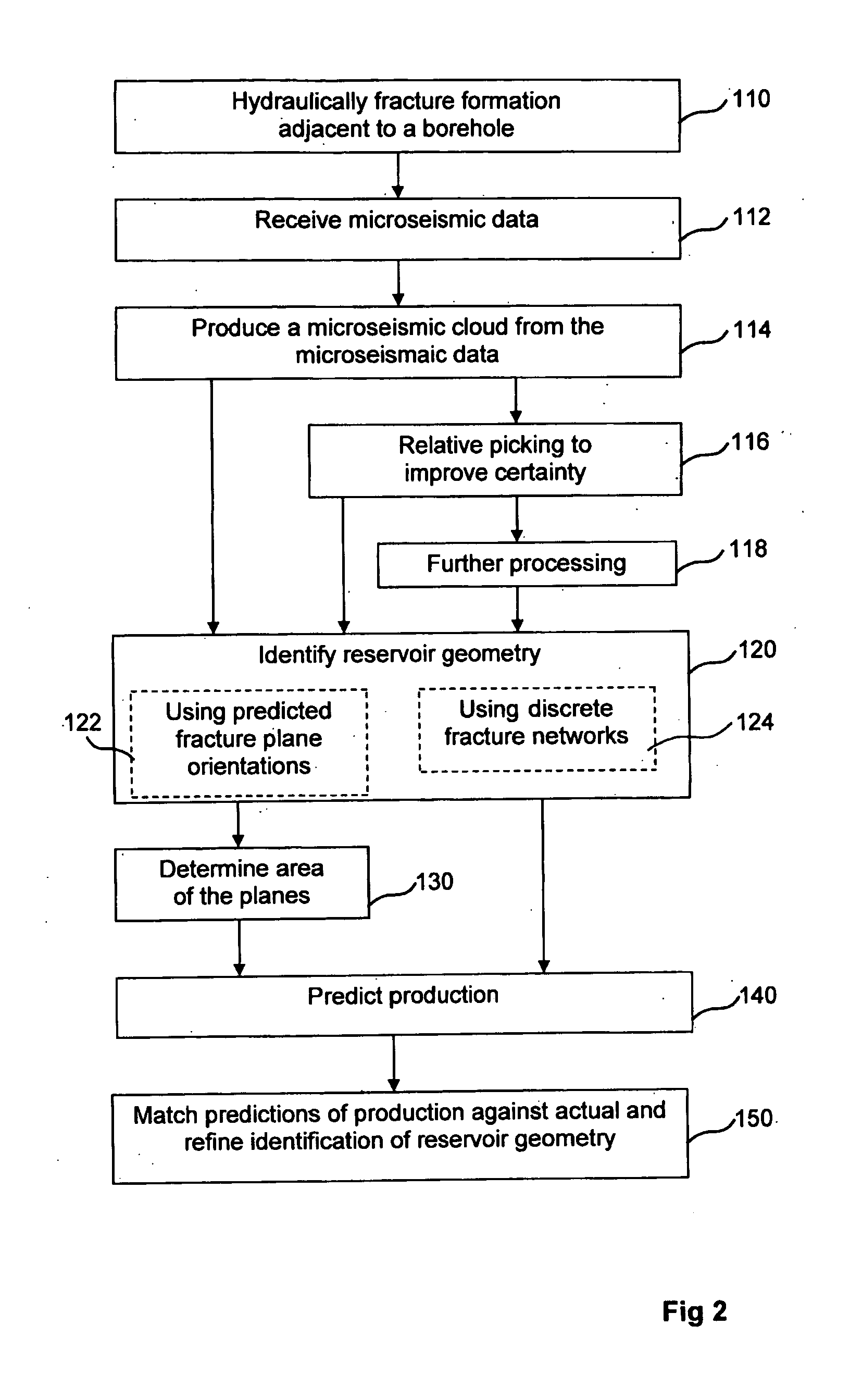
Identification of reservoir geometry from microseismic event clouds
InactiveUS20130144532A1Provide benefitsElectric/magnetic detection for well-loggingSeismic signal processingNumber densityHydraulic fracturing
A method for characterizing fracture planes generated during a hydraulic fracturing process, comprises receiving microseismic data from the hydraulic fracturing process and processing a microseismic event cloud from the received microseismic data. This is followed by determining at least one reservoir geometry from the microseismic event cloud. The determination of geometry may consist of determining multiple candidate geometries and probability of each. In some forms of the invention the method may comprise postulating a set of candidate geometries with differing numbers of fracture planes, determining the most probable locations of the postulated fracture planes in each member of the set of candidate geometries and also determining relative probabilities of the candidate geometries in the postulated set. Determining a location of a fracture plane may comprise calculating a number density for each microseismic event, dependent on distance from some possible location of a fracture plane or fracture network. Finding the location of a plane may then be finding the location for which the number density is greatest. The determination of reservoir geometry may be followed by determination of the area of the fracture planes and / or by a prediction of production.
Owner:SCHLUMBERGER TECH CORP
System and method for a distributed application of a network security system (SDI-SCAM)
InactiveUS20130091573A1Memory loss protectionError detection/correctionCountermeasureRelative probability
A widely distributed security system (SDI-SCAM) that protects computers at individual client locations, but which constantly pools and analyzes information gathered from machines across a network in order to quickly detect patterns consistent with intrusion or attack, singular or coordinated. When a novel method of attack has been detected, the system distributes warnings and potential countermeasures to each individual machine on the network. Such a warning may potentially consist of a probability distribution of the likelihood of an intrusion or attack as well as the relative probabilistic likelihood that such potential intrusion possesses certain characteristics or typologies or even strategic objectives in order to best recommend and / or distribute to each machine the most befitting countermeasure(s) given all presently known particular data and associated predicted probabilistic information regarding the prospective intrusion or attack. If any systems are adversely affected, methods for repairing the damage are shared and redistributed throughout the network.
Owner:INVENTSHIP LLC
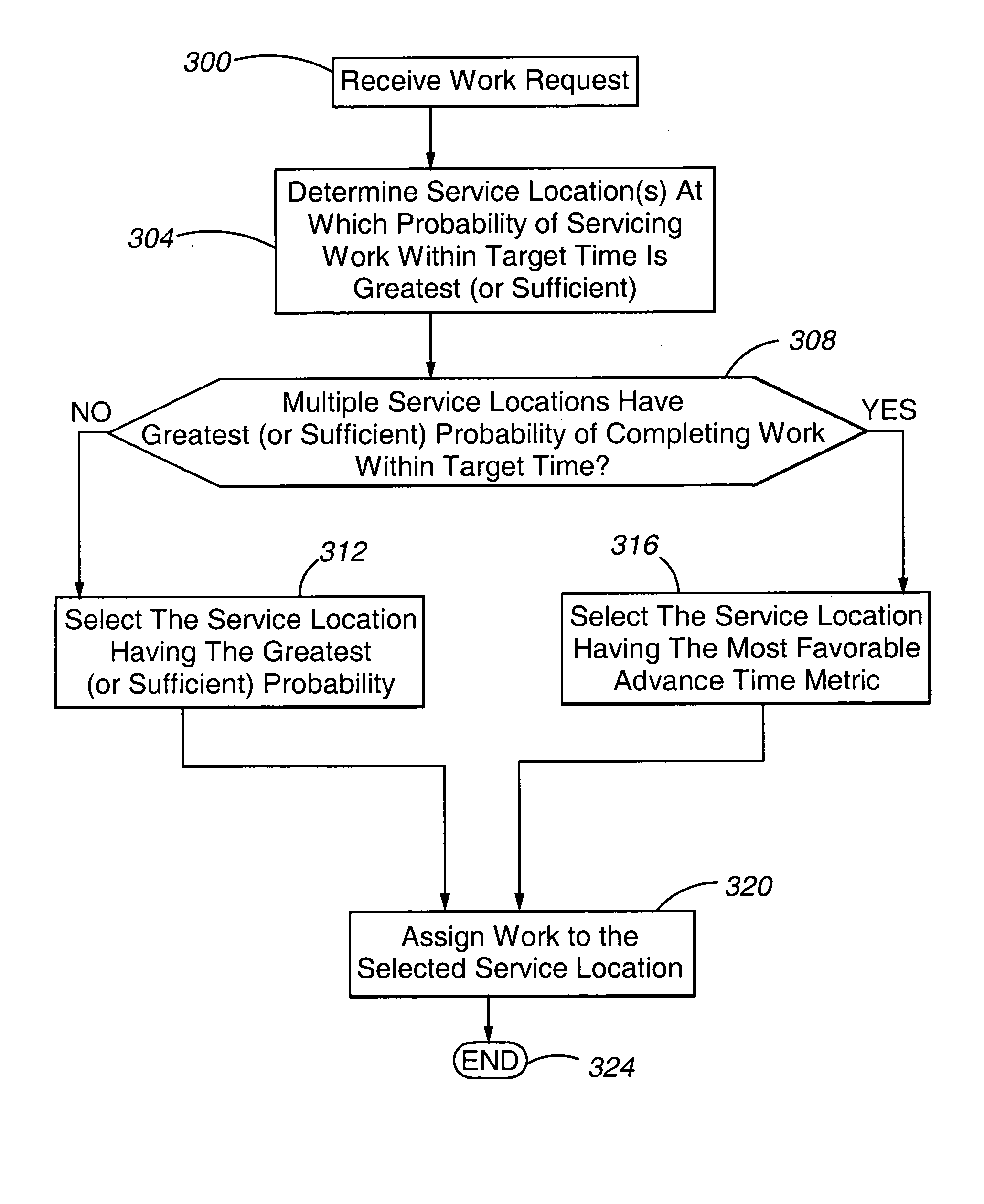
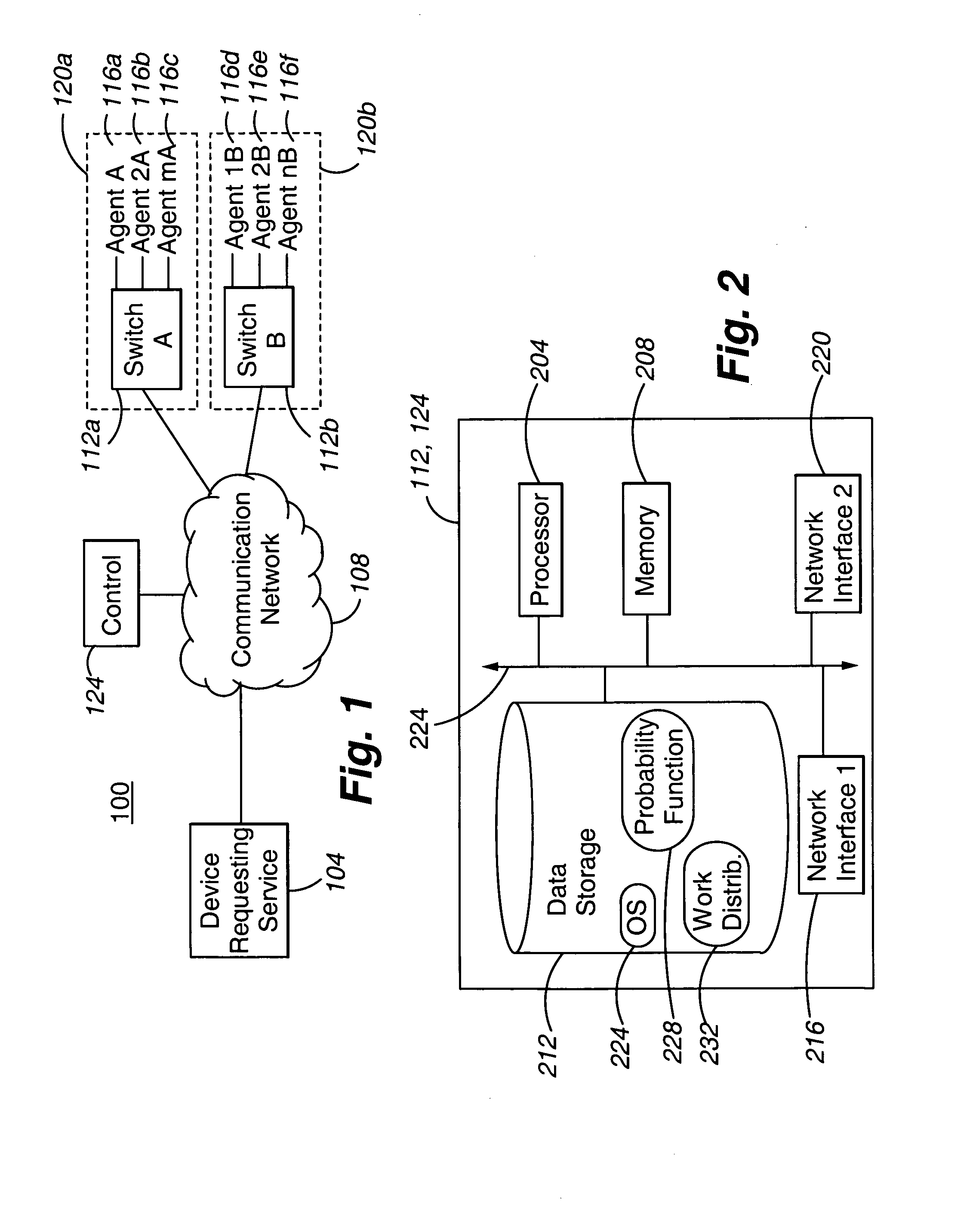
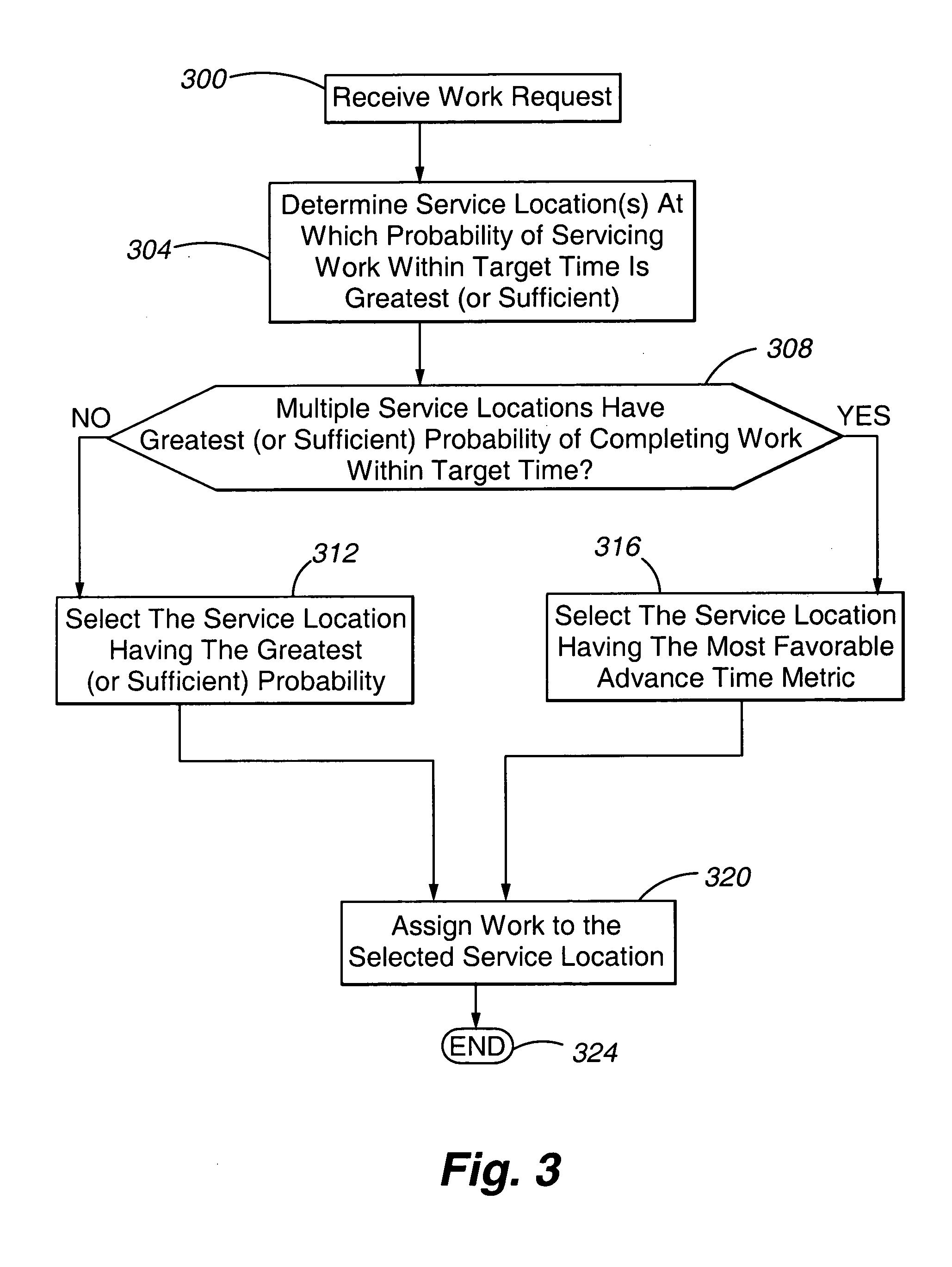
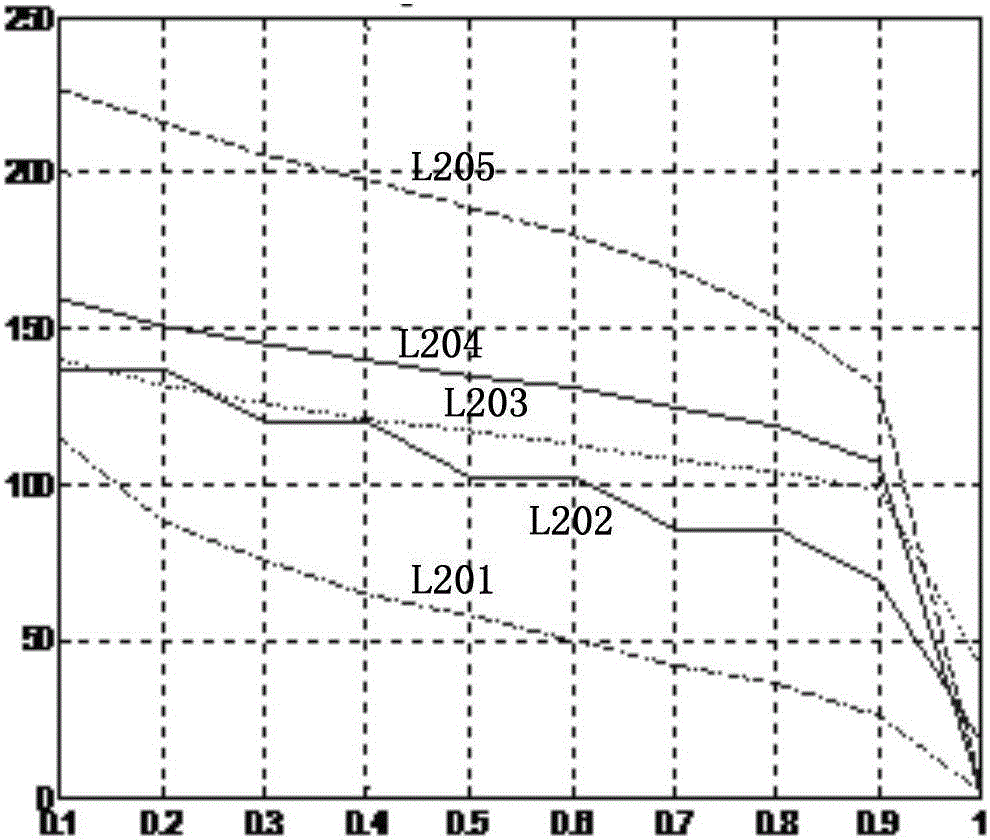
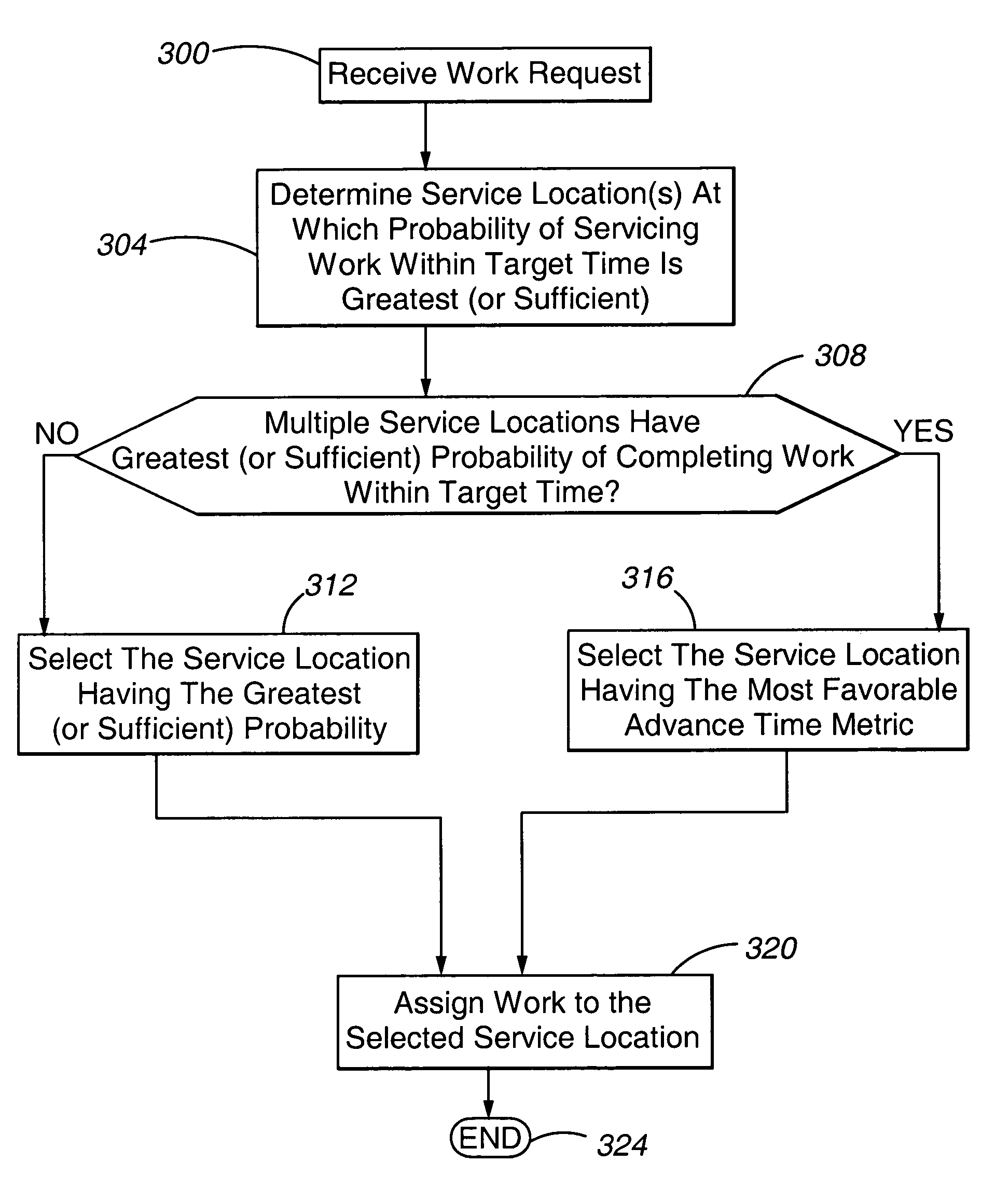
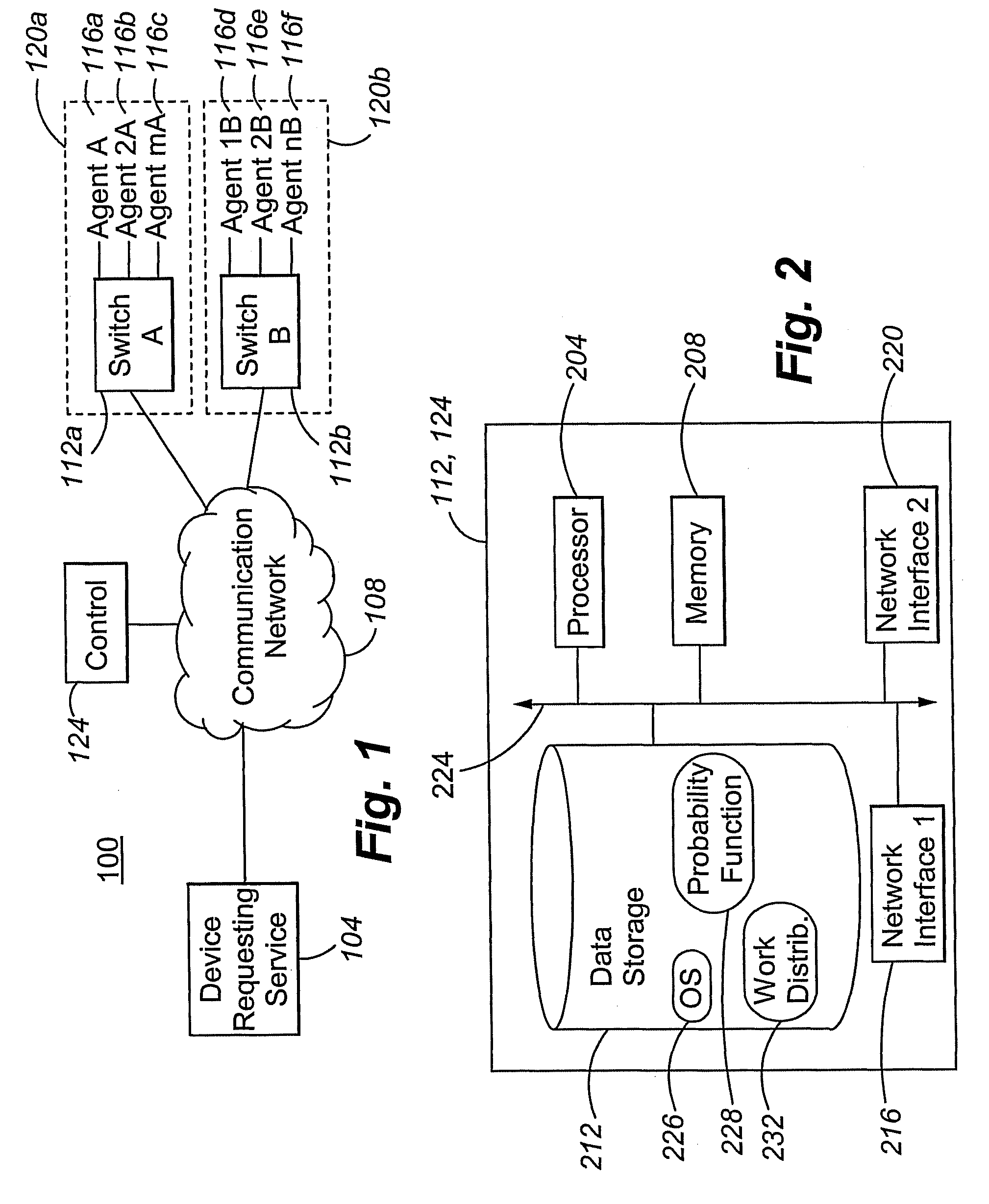
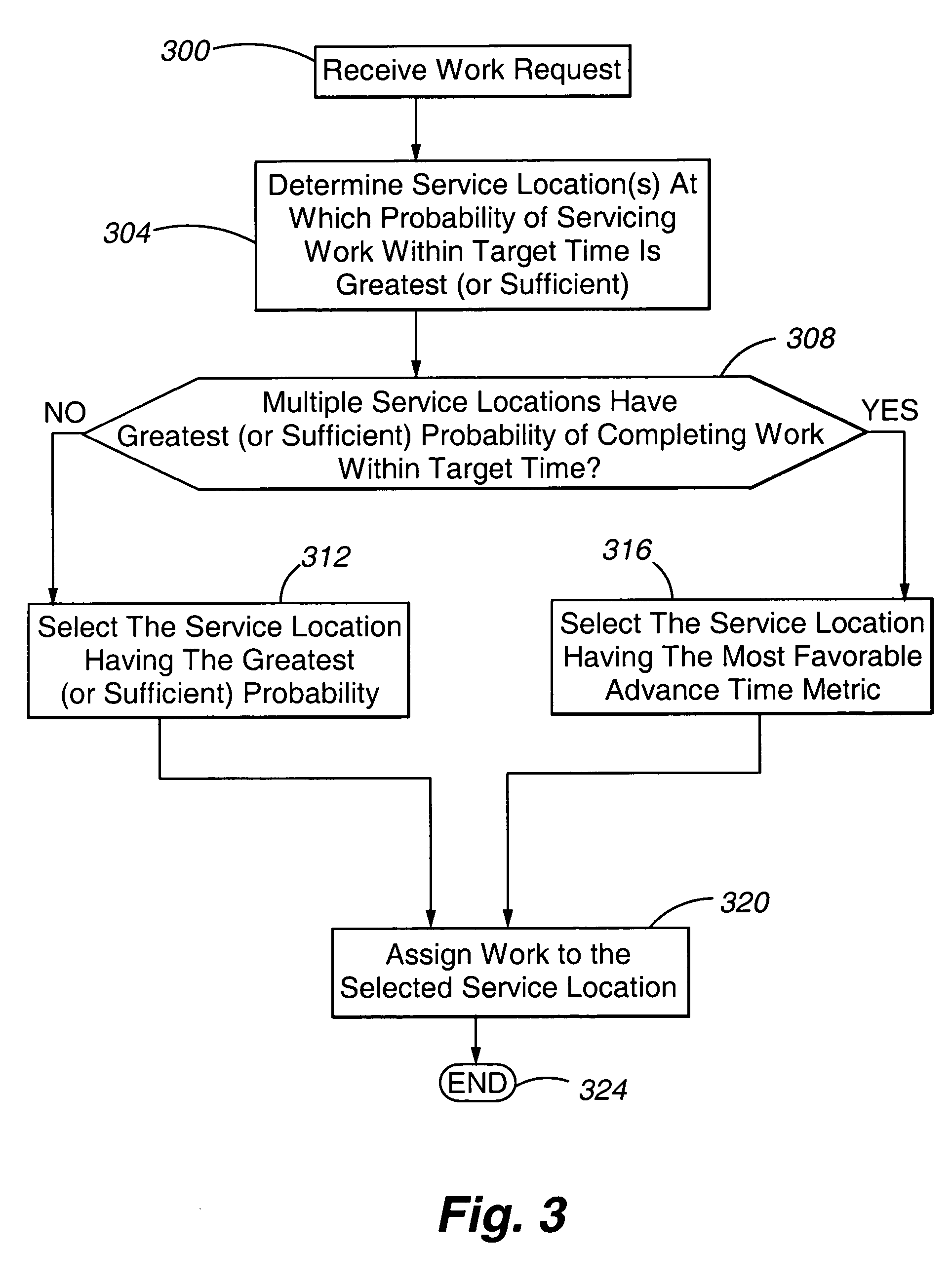
Method and apparatus for load balancing work on a network of servers based on the probability of being serviced within a service time goal
ActiveUS20050071844A1Reduce overheadGuaranteed to workResource allocationManual exchangesWork distributionRelative probability
Owner:AVAYA INC
Distributed agent based model for security monitoring and response
An architecture is provided for a widely distributed security system (SDI-SCAM) that protects computers at individual client locations, but which constantly pools and analyzes information gathered from machines across a network in order to quickly detect patterns consistent with intrusion or attack, singular or coordinated. When a novel method of attack has been detected, the system distributes warnings and potential countermeasures to each individual machine on the network. Such a warning may potentially include a probability distribution of the likelihood of an intrusion or attack as well as the relative probabilistic likelihood that such potential intrusion possesses certain characteristics or typologies or even strategic objectives in order to best recommend and / or distribute to each machine the most befitting countermeasure(s) given all presently known particular data and associated predicted probabilistic information regarding the prospective intrusion or attack. If any systems are adversely affected, methods for repairing the damage are shared and redistributed throughout the network.
Owner:INVENTSHIP LLC
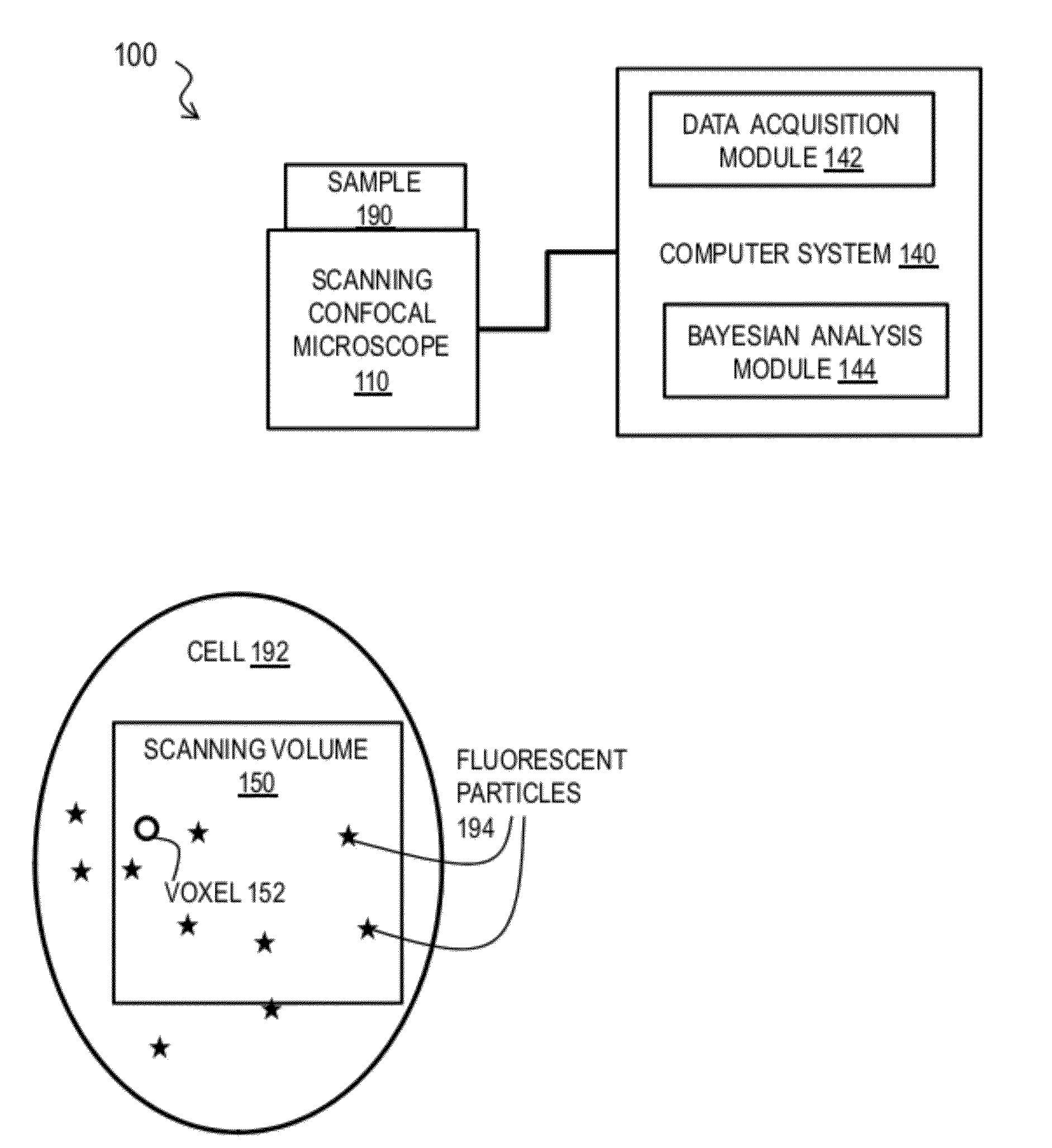
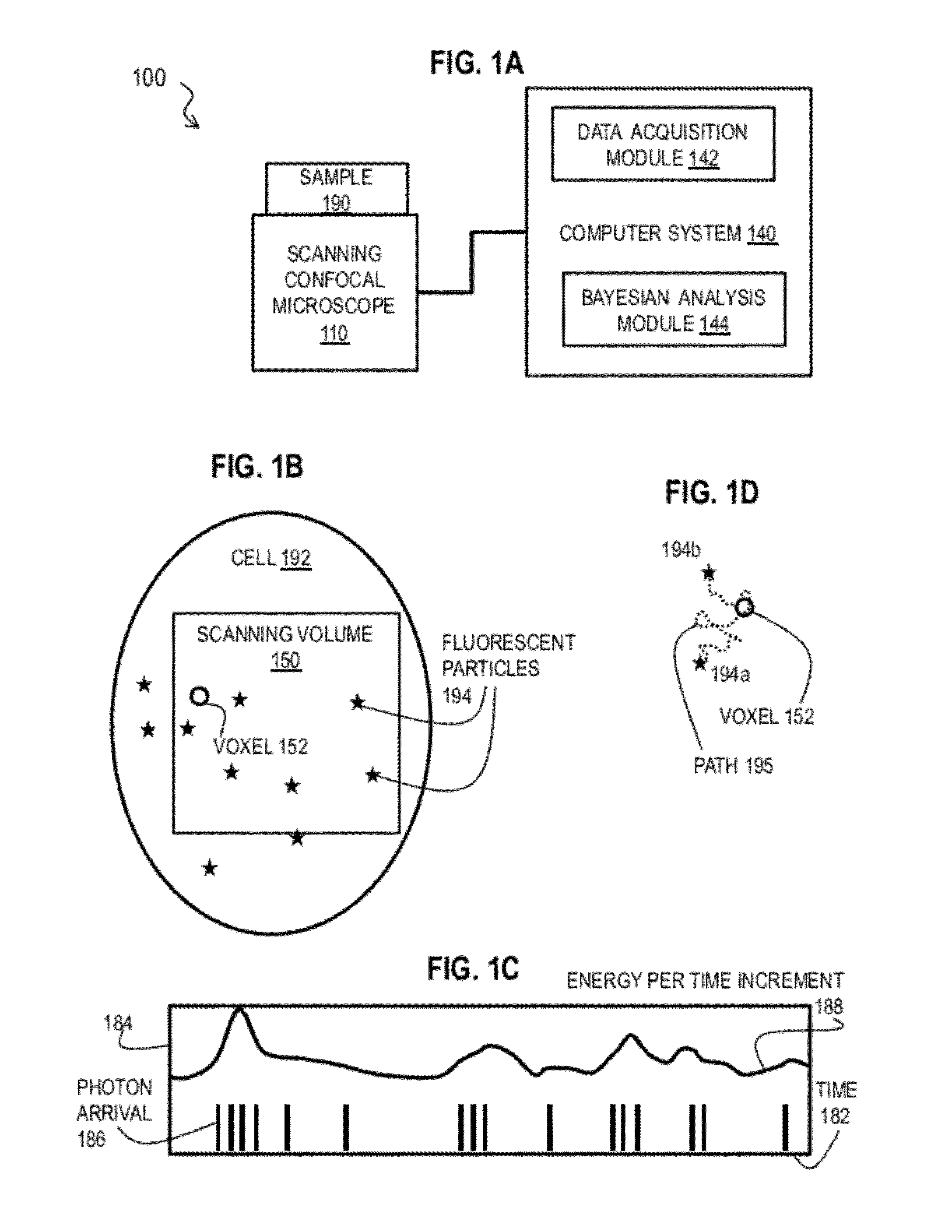
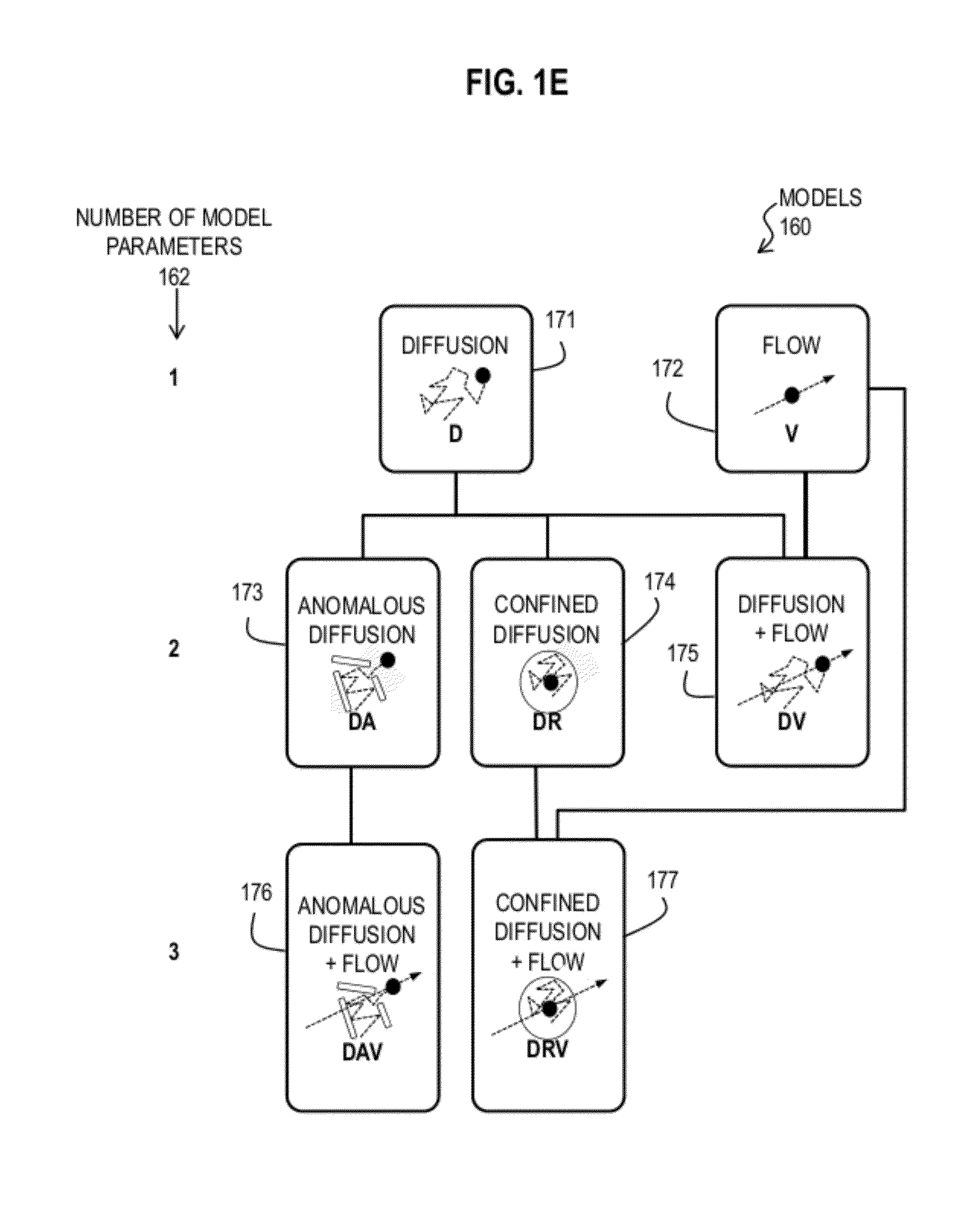
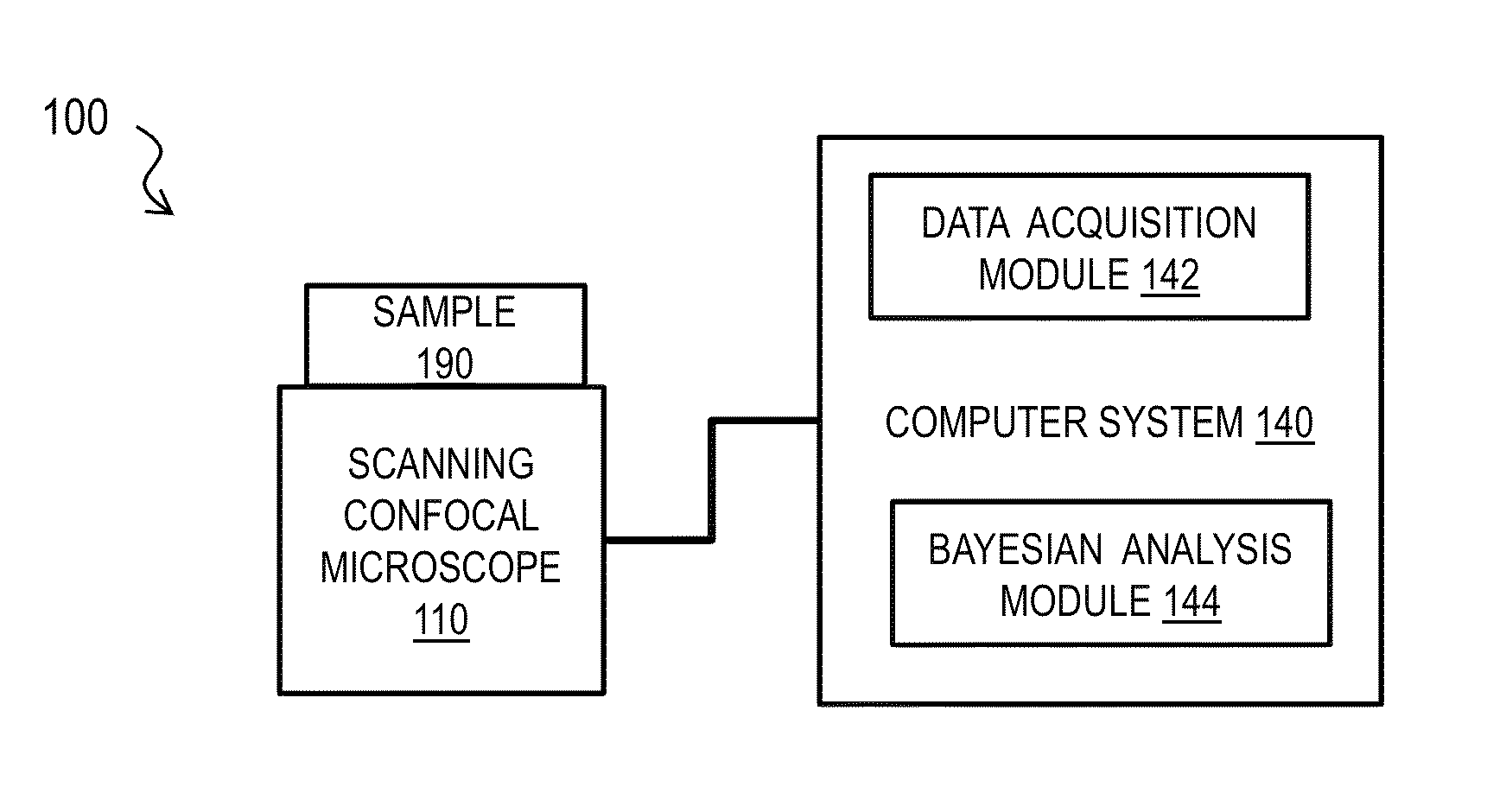
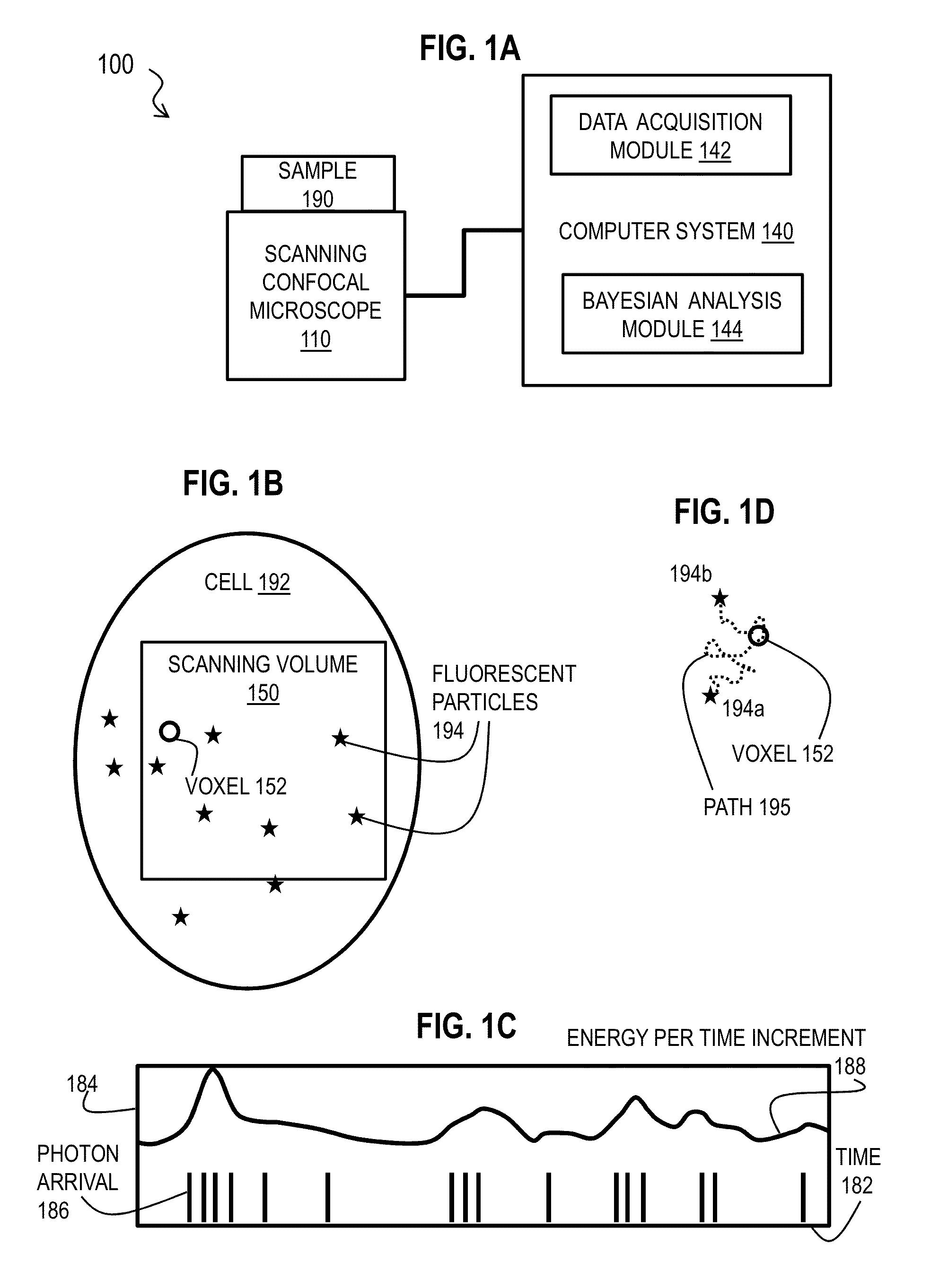
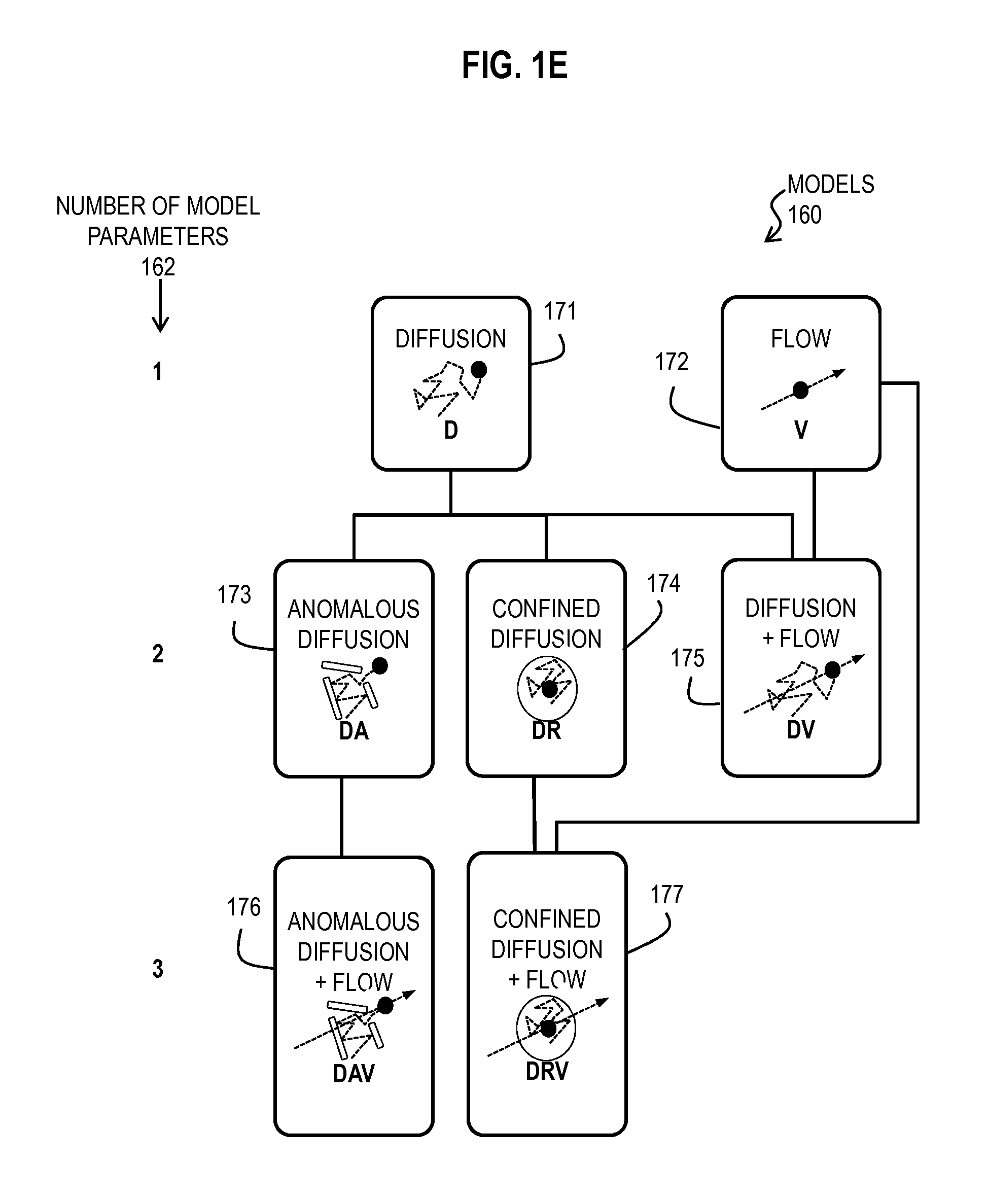
Bayesian Inference of Particle Motion and Dynamics from Single Particle Tracking and Fluorescence Correlation Spectroscopy
Techniques for inferring particle dynamics from certain data include determining multiple models for motion of particles in a biological sample. Each model includes a corresponding set of one or more parameters. Measured data is obtained based on measurements at one or more voxels of an imaging system sensitive to motion of particles in the biological sample; and, determining noise correlation of the measured data. Based at least in part on the noise correlation, a marginal likelihood is determined of the measured data given each model of the multiple models. A relative probability for each model is determined based on the marginal likelihood. Based at least in part on the relative probability for each model, a value is determined for at least one parameter of the set of one or more parameters corresponding to a selected model of the multiple models.
Owner:MASSACHUSETTS INST OF TECH
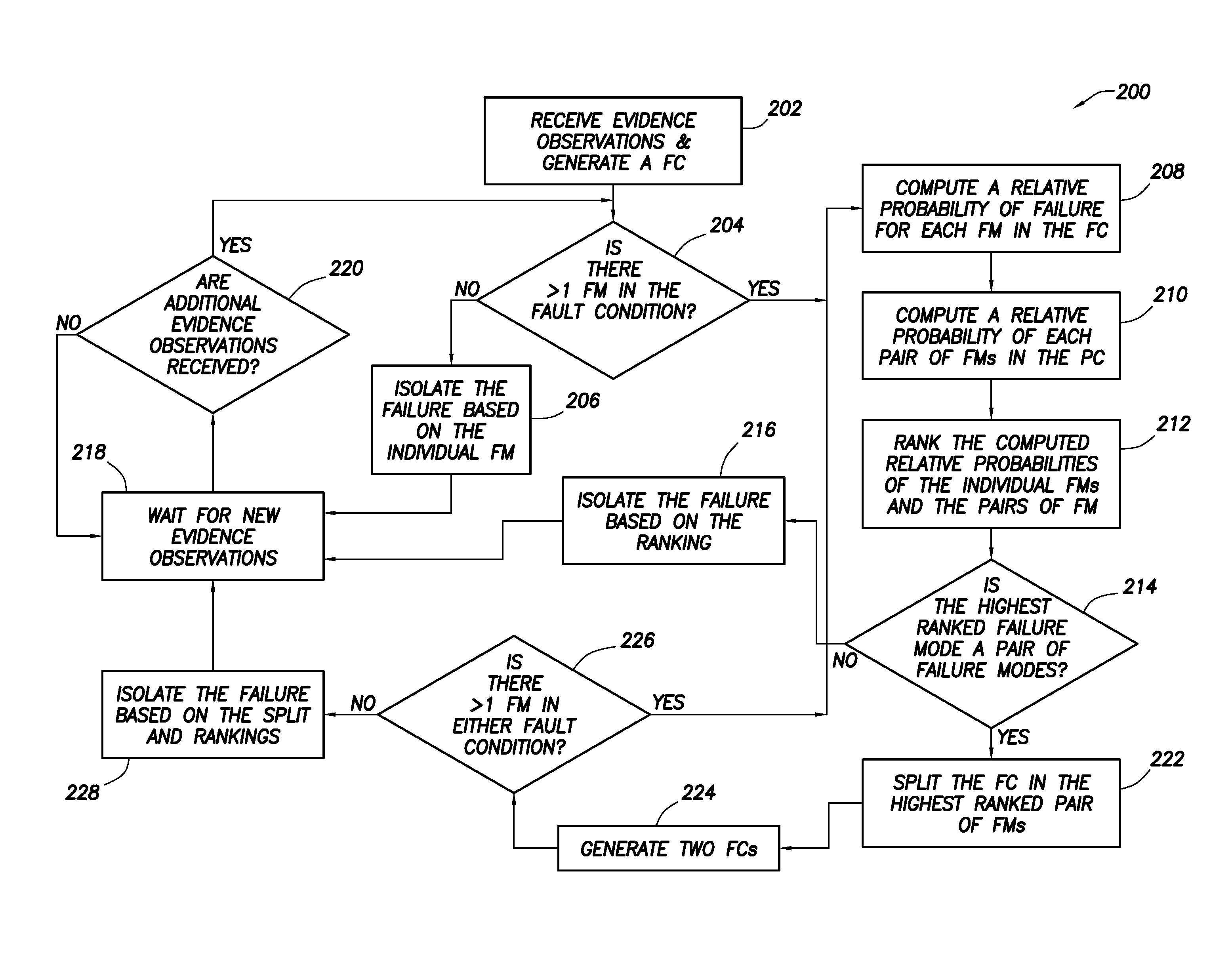
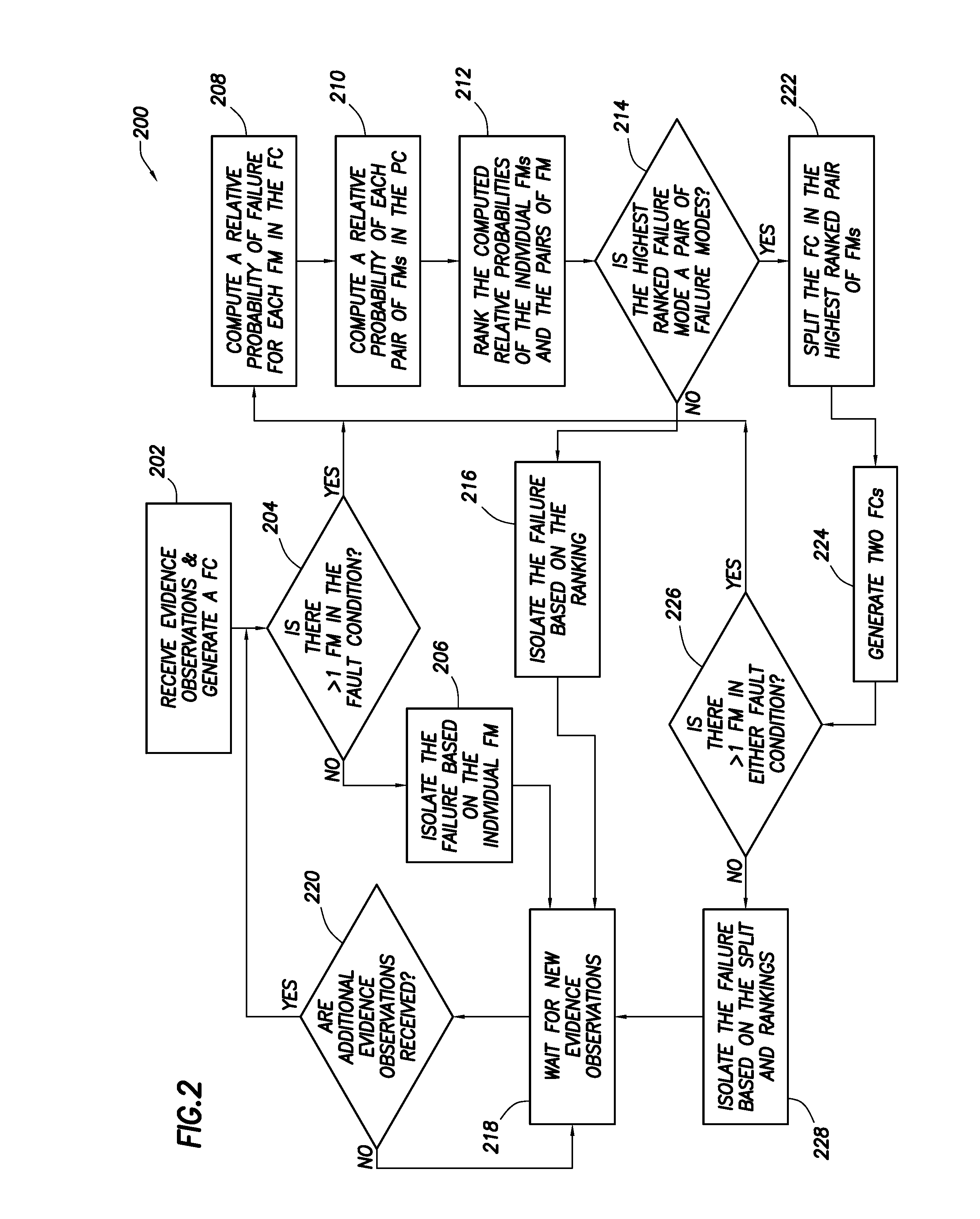
Fault splitting algorithm
The present application relates to a method of splitting a fault condition including receiving evidence observations of a monitored system from monitors connected in a many-to-many relationship to the failure modes, generating a fault condition, computing a relative probability of failure for each failure mode in the fault condition. When there is more than one failure mode in the fault condition, the method includes computing a relative probability of each pair of failure modes in the fault condition, ranking the computed relative probabilities of the individual failure modes and the computed relative probabilities of the pairs of failure modes. If the highest ranked failure mode is a pair of failure modes, the fault condition is split based on the failure modes in the highest ranked pair of failure modes are split. If the highest ranked failure mode is an individual failure mode, a failure is isolated based on the ranking.
Owner:HONEYWELL INT INC
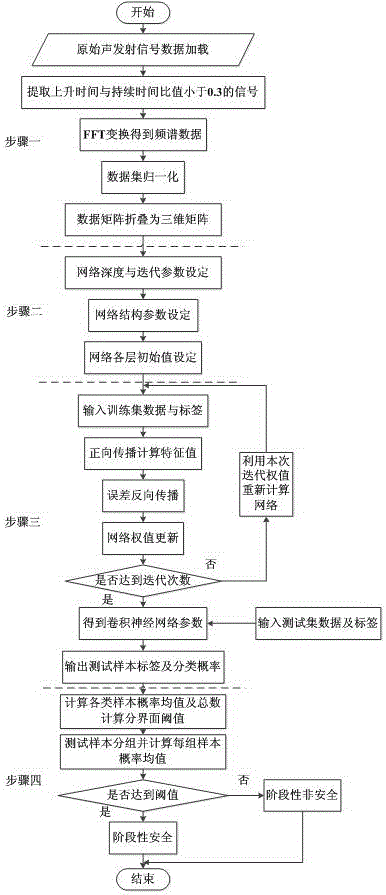
Steel rail crack detection method based on multiple acoustic emission event probabilities
ActiveCN106248801AAvoid false detectionImprove detection accuracyMaterial analysis using acoustic emission techniquesProcessing detected response signalFrequency spectrumAlgorithm
The invention relates to a steel rail crack detection method based on multiple acoustic emission event probabilities. According to the steel rail crack detection method, the relative probability output by a convolutional neural network is used as the probability of an acoustic emission event, and the problem that temporal information between samples is not fully used by an existing steel rail crack detection method is solved. The steel rail crack detection method comprises the steps of (1) loading an acoustic emission time domain signal data matrix, and performing FFT (Fast Fourier Transformation) and pretreatment on acoustic emission signals, so that a spectral matrix which is folded into a three-dimensional matrix and a label vector are obtained; (2) setting structural parameters and an initial value of the convolutional network; (3) inputting the spectral matrix, calculating and iterating errors of a convolutional neural network model layer by layer, updating a weight matrix and bias, performing feature extraction, and outputting classification results and classification probabilities of a test set; (4) correcting the outputting of the convolutional neural network on the basis of the multiple acoustic emission event probabilities, and optimizing the classification results. According to the steel rail crack detection method, the classification results are improved according to the multiple acoustic emission event probabilities, so that the detection precision of steel rail crack damages is increased, and high theoretical and practical engineering significance is obtained.
Owner:HARBIN INST OF TECH
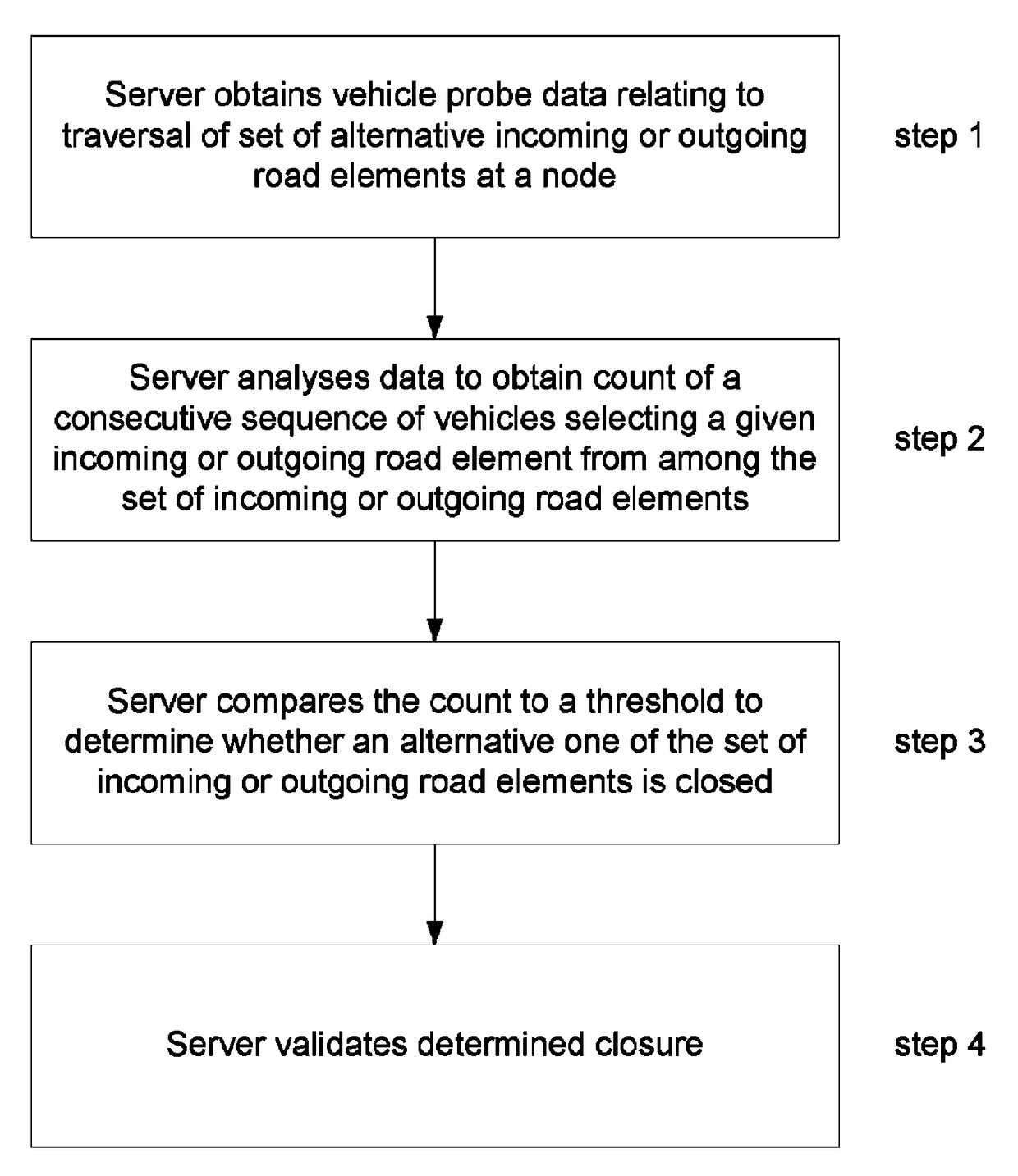
Methods and systems for detecting a closure of a navigable element
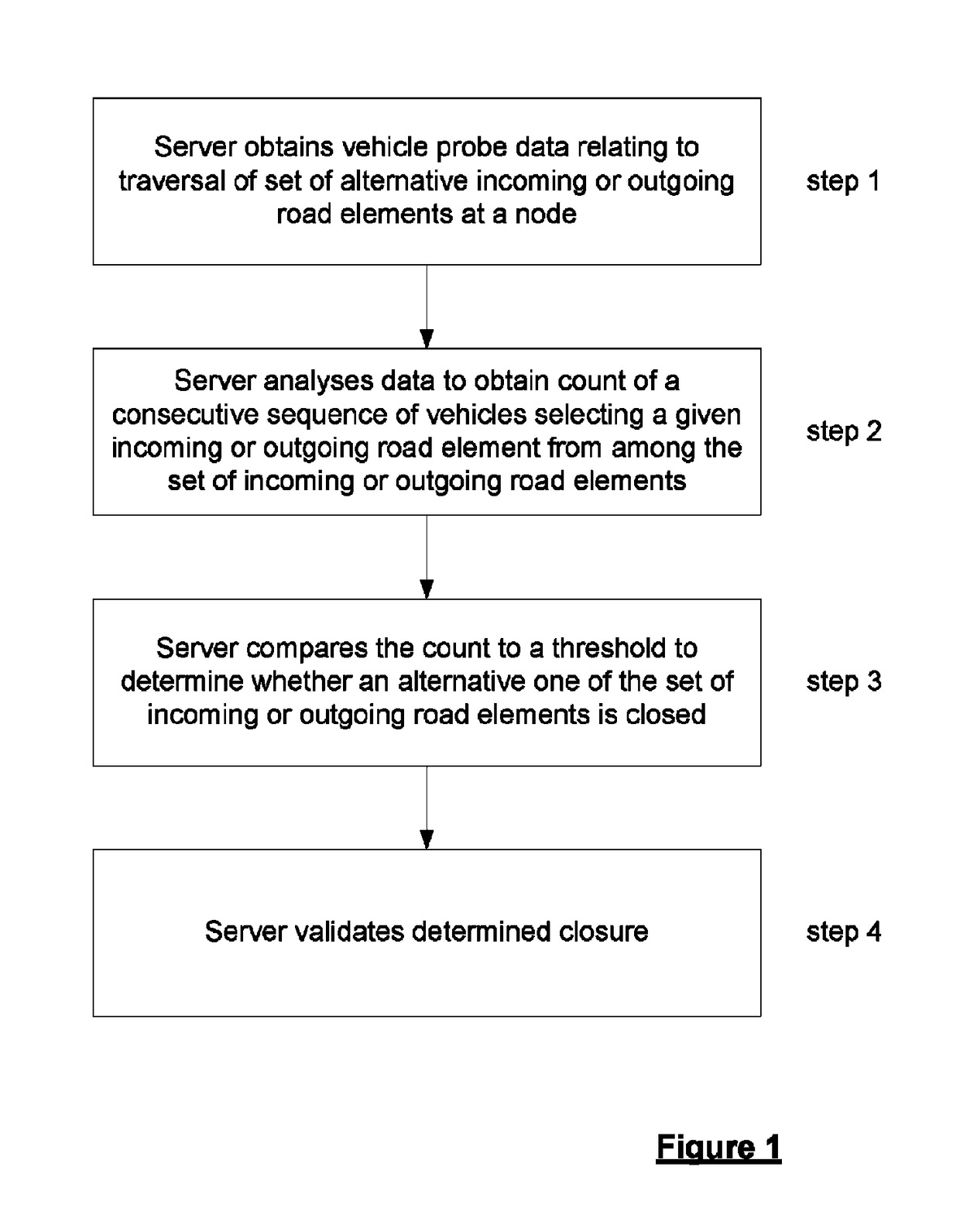
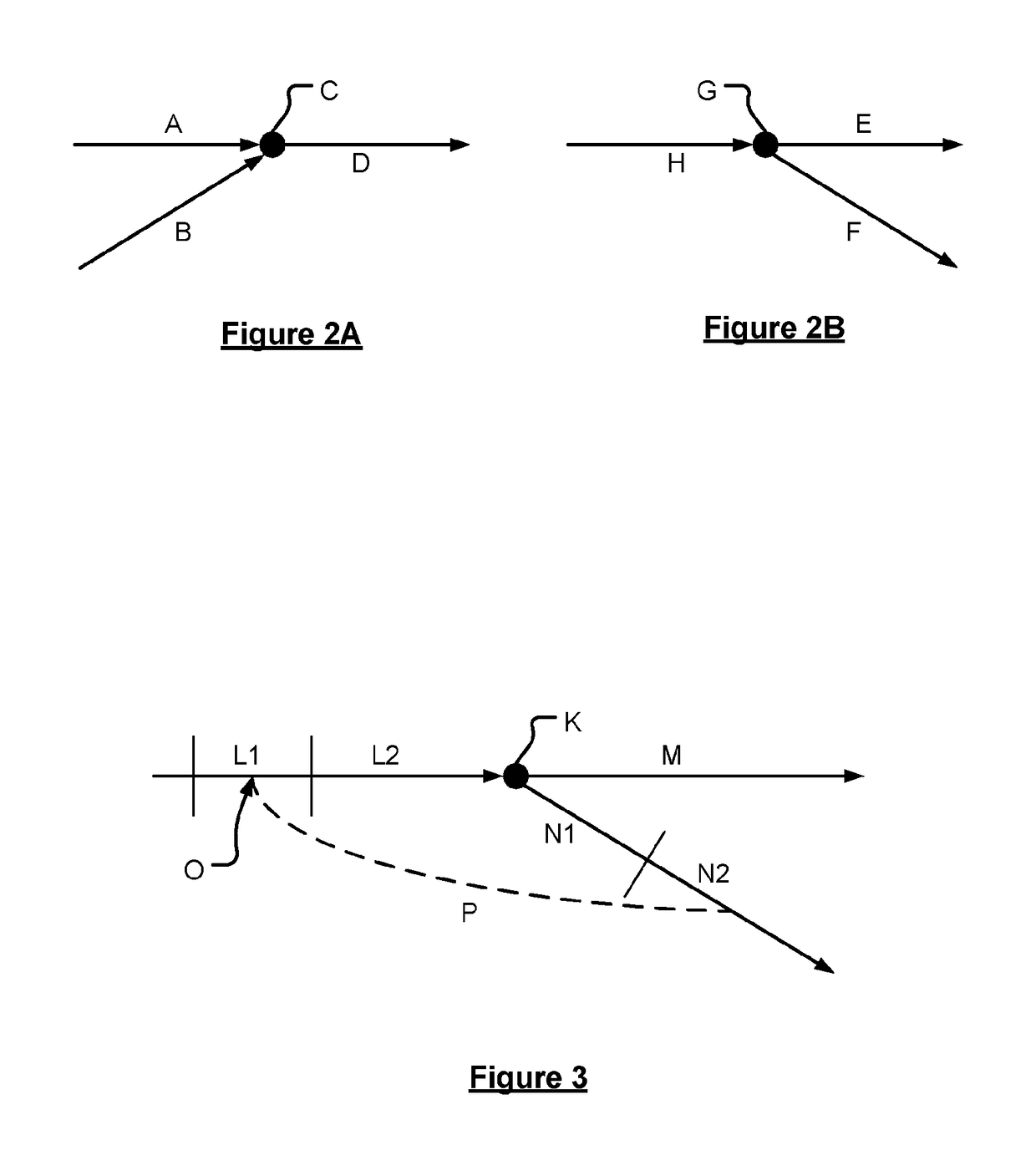
ActiveUS20160275787A1Reduce delaysAccurate measurementDetection of traffic movementSatellite radio beaconingSimulationRelative probability
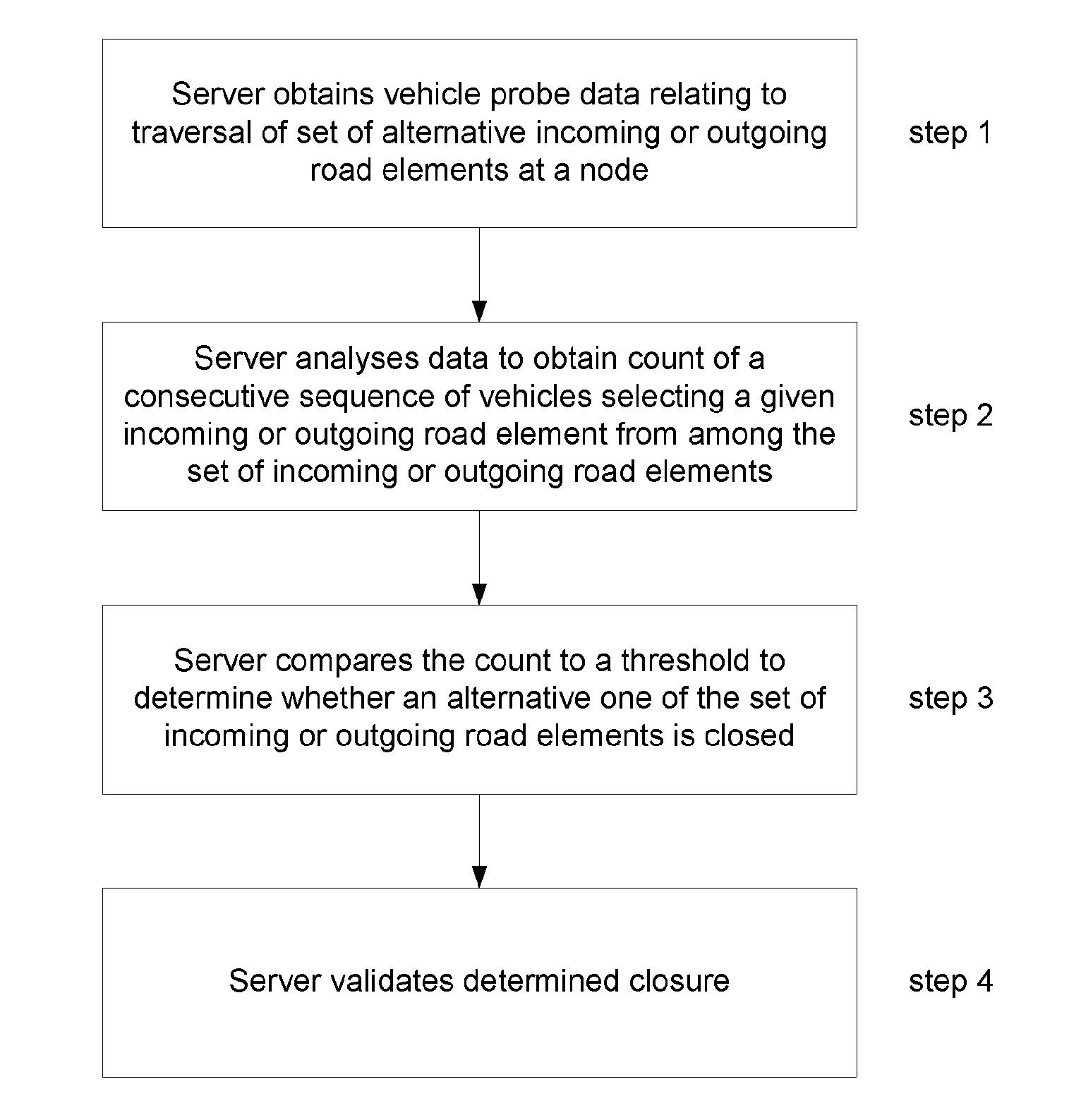
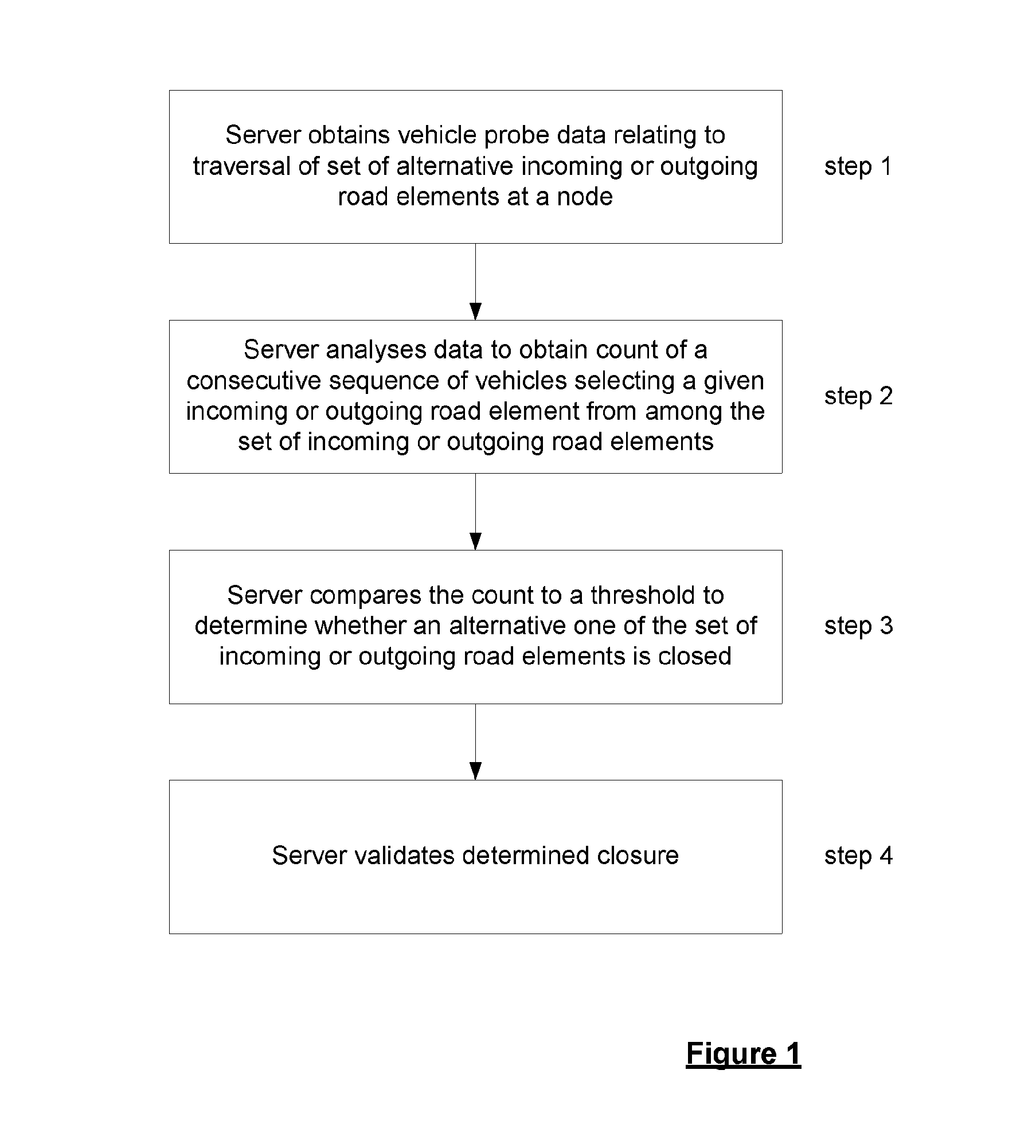
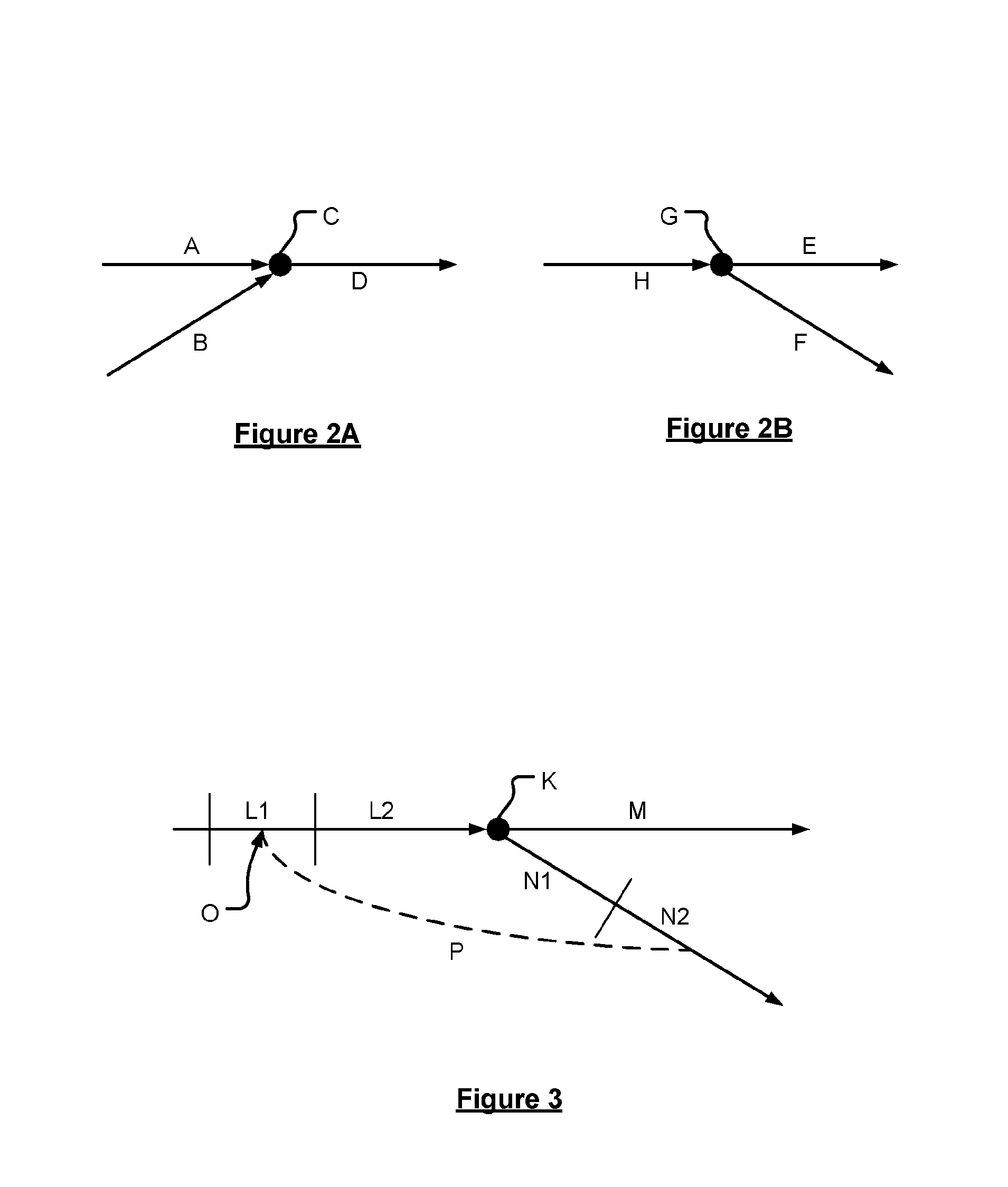
A method of detecting the closure of a road element is disclosed; the road element being one of a set of alternative incoming or outgoing elements at a node in a network of navigable elements. A server obtains positional data relating to the position of a plurality of devices with respect to time traversing the node. A count is determined of the number of devices in a consecutive sequence of device selecting a given one of the navigable elements from among the set of elements. The count is compared to a predetermined threshold to determine whether another one of the elements is closed. The threshold is based upon the relative probability of the element to which the count relates being taken from the set of road elements.
Owner:TOMTOM DEV GERMANY
Load balancing
ActiveUS20130077490A1Error preventionFrequency-division multiplex detailsLoad SheddingCarrier signal
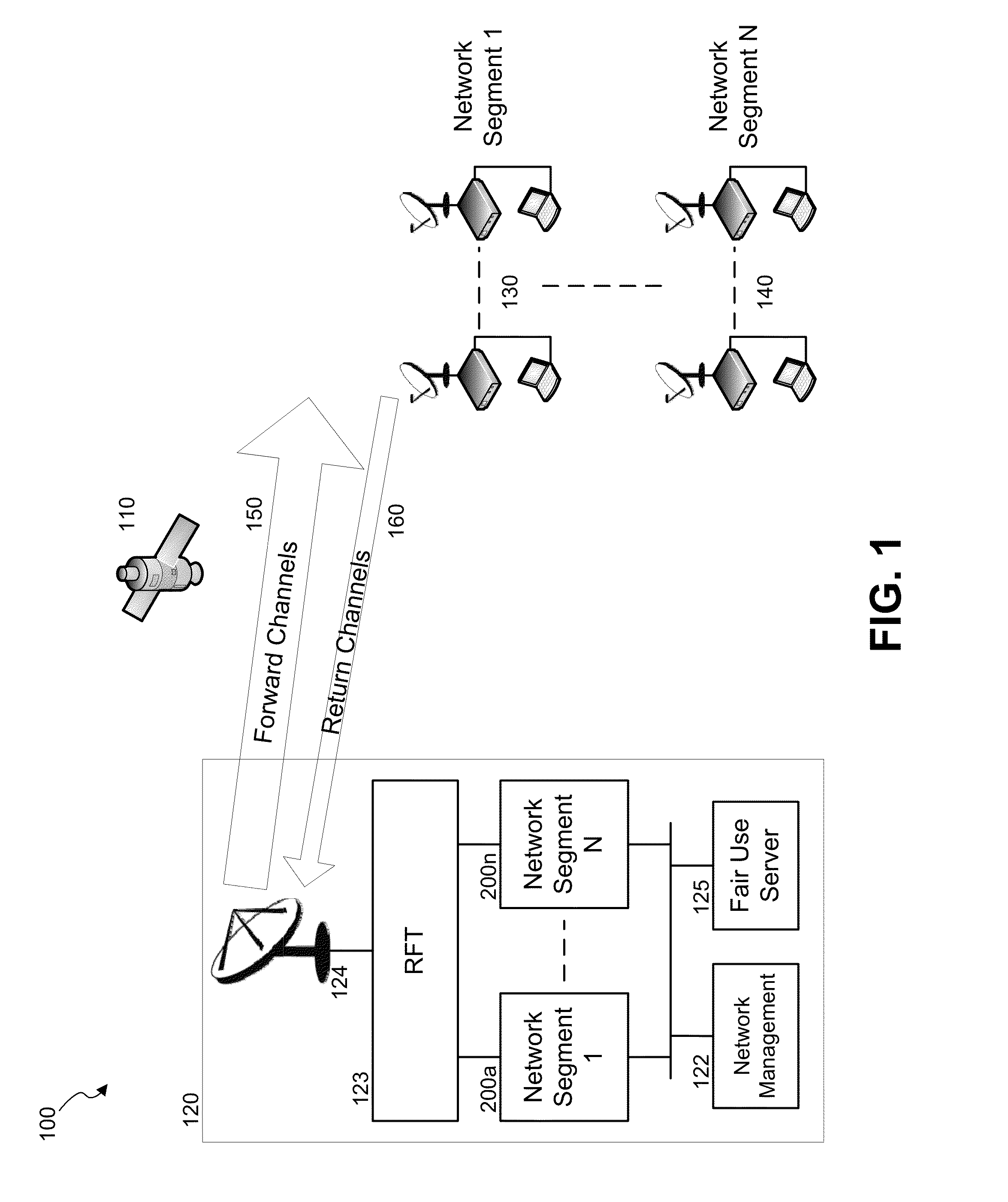
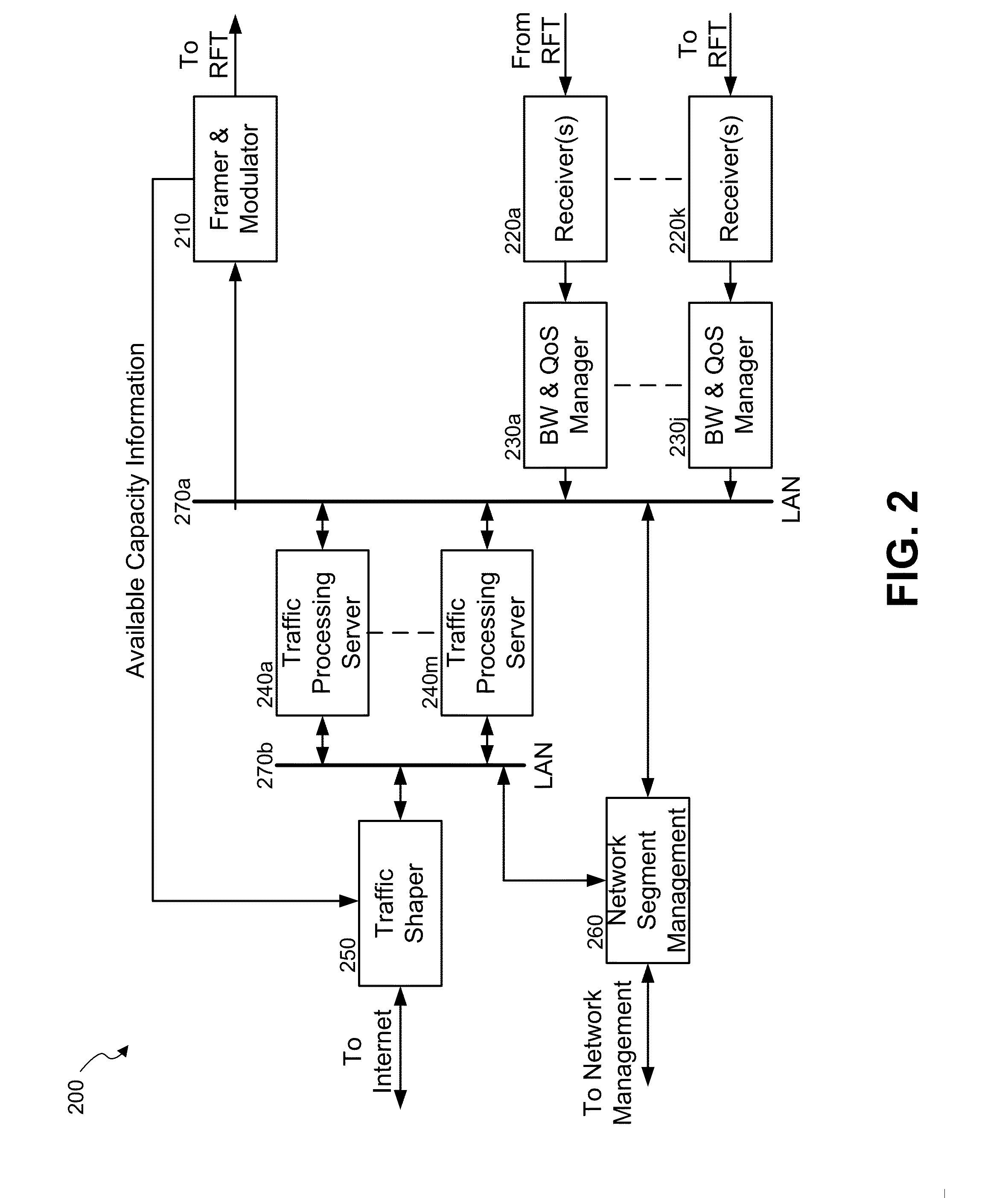
A satellite communication system comprising a hub and plurality of terminals may be divided into multiple segments, wherein each segment may support part of the terminals. A method for decentralized balancing of traffic between the system segments is presented herein. One segment in each coverage beam may be designated as home carrier and include load balancing information. The terminals may be configured to tune on a home carrier, receive the load balancing information and then use it for selecting a least loaded segment on which they may remain operational until reset or powered off. In some embodiments of the invention, said load balancing information may be used for calculating relative probabilities for selecting segments through a weighted random selection algorithm.
Owner:GILAT SATELLITE NETWORKS
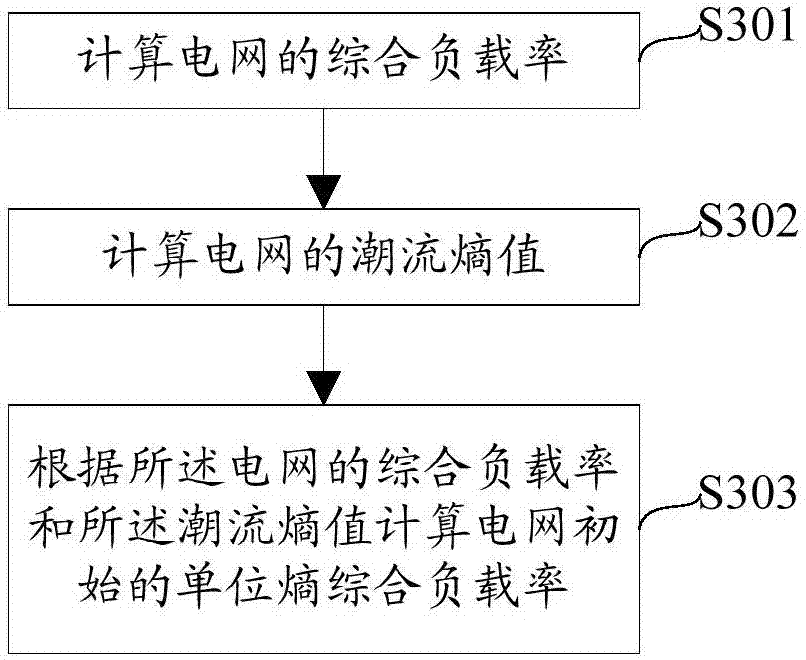
Calculation method and device for power grid line vulnerability
ActiveCN106934246AReasonable and comprehensive identificationInformaticsSpecial data processing applicationsPower gridRelative probability
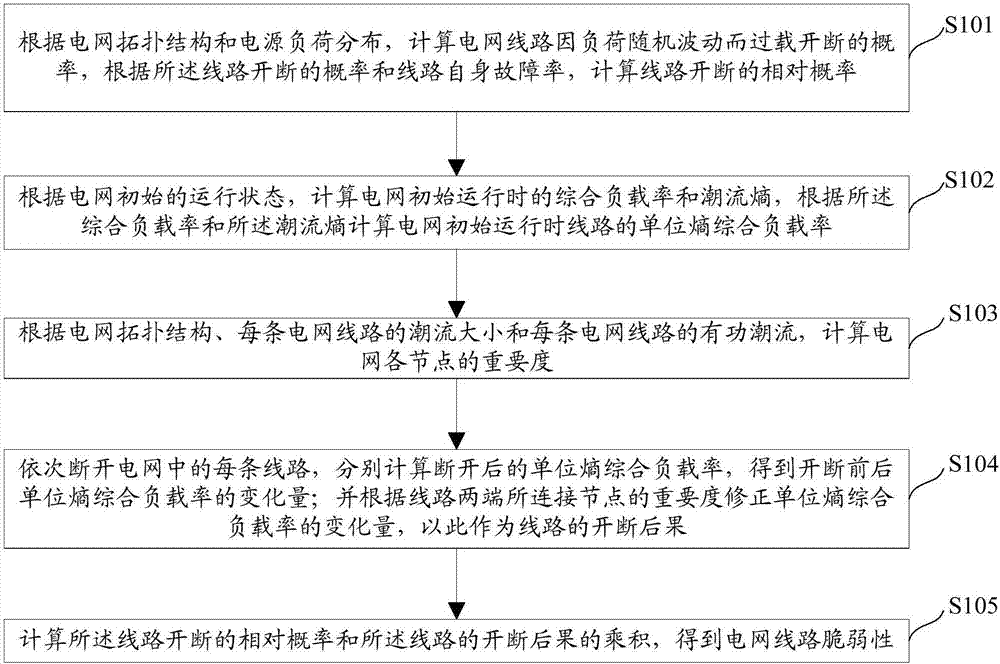
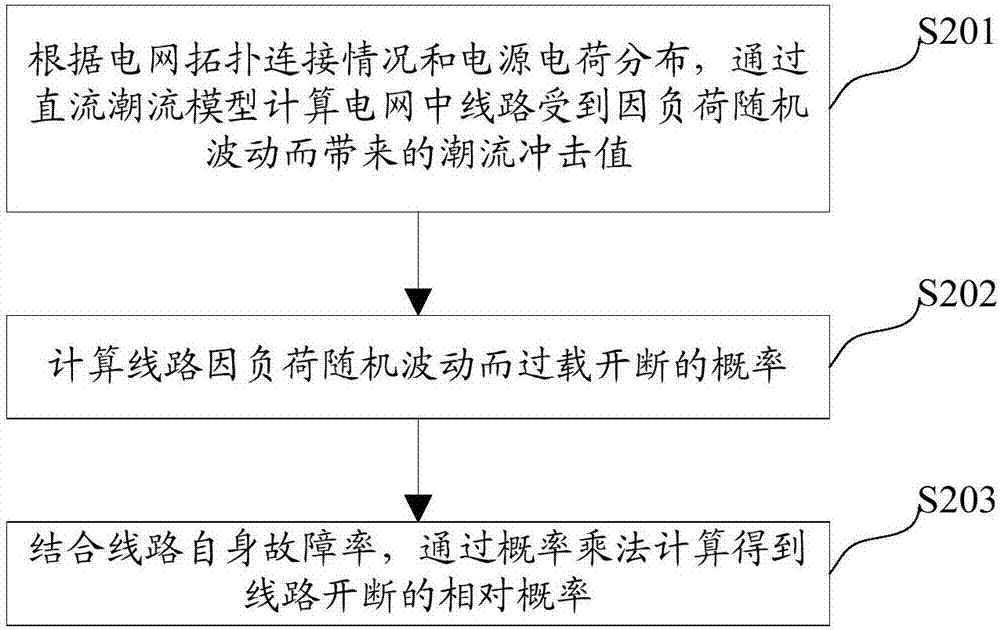
The invention relates to a calculation method and device for power grid line vulnerability. The calculation method comprises the following steps that: calculating the off-on relative probability of the line; calculating the initial unit entropy comprehensive loading rate of a power grid; calculating the importance degree of each node of a power grid; calculating the off-on consequence of the line; and calculating the product of the off-on relative probability of the line and the off-on consequence of the line, and taking the product as the vulnerability of the circuit. By use of the technical scheme provided by the invention, the physical characteristics of a power grid topological structure are fully considered, the physical states of each line and each node in the power grid topological structure a are fully combined, and the power grid line vulnerability obtained by calculation can more reasonably and comprehensively distinguish the vulnerable line of the power grid.
Owner:HUIZHOU POWER SUPPLY BUREAU OF GUANGDONG POWER GRID CO LTD +1
Bayesian inference of particle motion and dynamics from single particle tracking and fluorescence correlation spectroscopy
Techniques for inferring particle dynamics from certain data include determining multiple models for motion of particles in a biological sample. Each model includes a corresponding set of one or more parameters. Measured data is obtained based on measurements at one or more voxels of an imaging system sensitive to motion of particles in the biological sample; and, determining noise correlation of the measured data. Based at least in part on the noise correlation, a marginal likelihood is determined of the measured data given each model of the multiple models. A relative probability for each model is determined based on the marginal likelihood. Based at least in part on the relative probability for each model, a value is determined for at least one parameter of the set of one or more parameters corresponding to a selected model of the multiple models.
Owner:MASSACHUSETTS INST OF TECH
Distributed Agent Based Model For Security Monitoring And Response
An architecture is provided for a widely distributed security system (SDI-SCAM) that protects computers at individual client locations, but which constantly pools and analyzes information gathered from machines across a network in order to quickly detect patterns consistent with intrusion or attack, singular or coordinated. When a novel method of attack has been detected, the system distributes warnings and potential countermeasures to each individual machine on the network. Such a warning may potentially include a probability distribution of the likelihood of an intrusion or attack as well as the relative probabilistic likelihood that such potential intrusion possesses certain characteristics or typologies or even strategic objectives in order to best recommend and / or distribute to each machine the most befitting countermeasure(s) given all presently known particular data and associated predicted probabilistic information regarding the prospective intrusion or attack. If any systems are adversely affected, methods for repairing the damage are shared and redistributed throughout the network.
Owner:INVENTSHIP LLC
System and method for interferometrically tracking objects using a low-antenna-count antenna array
InactiveUS20150220488A1Direction finders using radio wavesDigital computer detailsPhase differenceMotion parameter
A radio-frequency interferometry method for determining parameters of motion of a moving object from phase difference information from an antenna baseline formed of two antennas. At each of a plurality of observation events, compute a posterior probability density function from the phase differences from the baseline, separate the modes with a threshold value of probability density, and compute a probability of each mode. For each possible sequence of modes, determine a mode sequence probability as the product of the probabilities of each mode in that sequence, estimate a χ2 goodness of fit function based on an assumed type of motion. Determine the net probability of each possible sequence of modes as the product of a relative probability derived from the χ2 and the mode sequence probability. Alternately, two or more parallel or colinear baselines are used, and the posterior PDF is a combined PDF over each of the baselines.
Owner:THE UNITED STATES OF AMERICA AS REPRESENTED BY THE SECRETARY OF THE NAVY
Quantum processor based systems and methods that minimize an objective function
ActiveUS9218567B2Quick mergeMinimize objective functionQuantum computersMathematical modelsAlgorithmHigh probability
Quantum processor based techniques minimize an objective function for example by operating the quantum processor as a sample generator providing low-energy samples from a probability distribution with high probability. The probability distribution is shaped to assign relative probabilities to samples based on their corresponding objective function values until the samples converge on a minimum for the objective function. Problems having a number of variables and / or a connectivity between variables that does not match that of the quantum processor may be solved. Interaction with the quantum processor may be via a digital computer. The digital computer stores a hierarchical stack of software modules to facilitate interacting with the quantum processor via various levels of programming environment, from a machine language level up to an end-use applications level.
Owner:D WAVE SYSTEMS INC
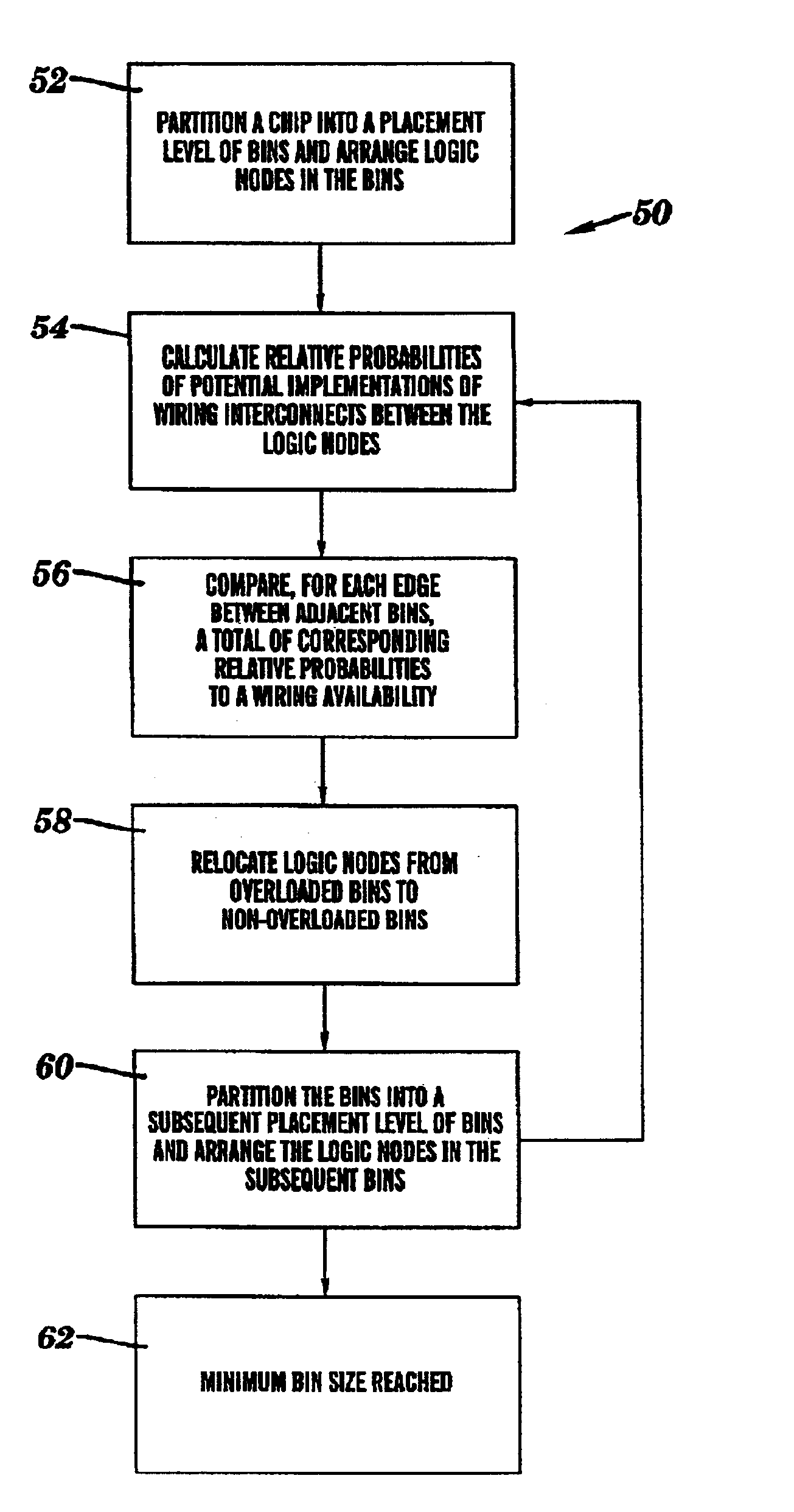
Method and system for placing logic nodes based on an estimated wiring congestion
InactiveUS6904584B2Computer aided designSpecial data processing applicationsRelative probabilityRouting congestion
A method and system for placing logic nodes based on an estimated wiring congestion are provided. Specifically, under the present invention, relative probabilities for potential implementations of wiring interconnects between logic nodes are determined. Then, for each edge between adjacent bins, a total of corresponding relative probabilities is compared to a wiring availability. Based on the comparison, the logic nodes can be placed within wiring constraints.
Owner:GLOBALFOUNDRIES INC
Method and system of handling the selection of alternates for recognized words
InactiveUS7130798B2Good choiceEasy to browseCharacter and pattern recognitionSpeech recognitionNatural language processingRelative probability
In a computing device that receives handwritten data, a method and system that facilitates the selection of alternates for a hand written word. A mechanism uses rules to select a word for the user based on the operating mode (state) of the system. In a cursor operating mode, a word is selected and the alternates are provided for the word based on the position of on screen cursor relative to the word (within or adjacent the word). If not on a word having alternates, the selection can move to another word that has alternates. If multiple words are selected, (selection mode), the system selects the first word of those selected that has alternates. Menu options to go to the next or previous recognized word may also be placed on the menu for easy navigation among words, and a user can automatically walk through multiple word sets to receive alternates for each word, one-word at a time. Words that the recognizer believes correct to a high actual or relative probability may be skipped over in the automatic process, and the display of words that the recognizer is less confident are correct can be modified. The user can adjust such sensitivity settings for determining the probability of correctness.
Owner:MICROSOFT TECH LICENSING LLC
Unit temperature response monitoring value based correction method for finite element model of large-span steel bridge
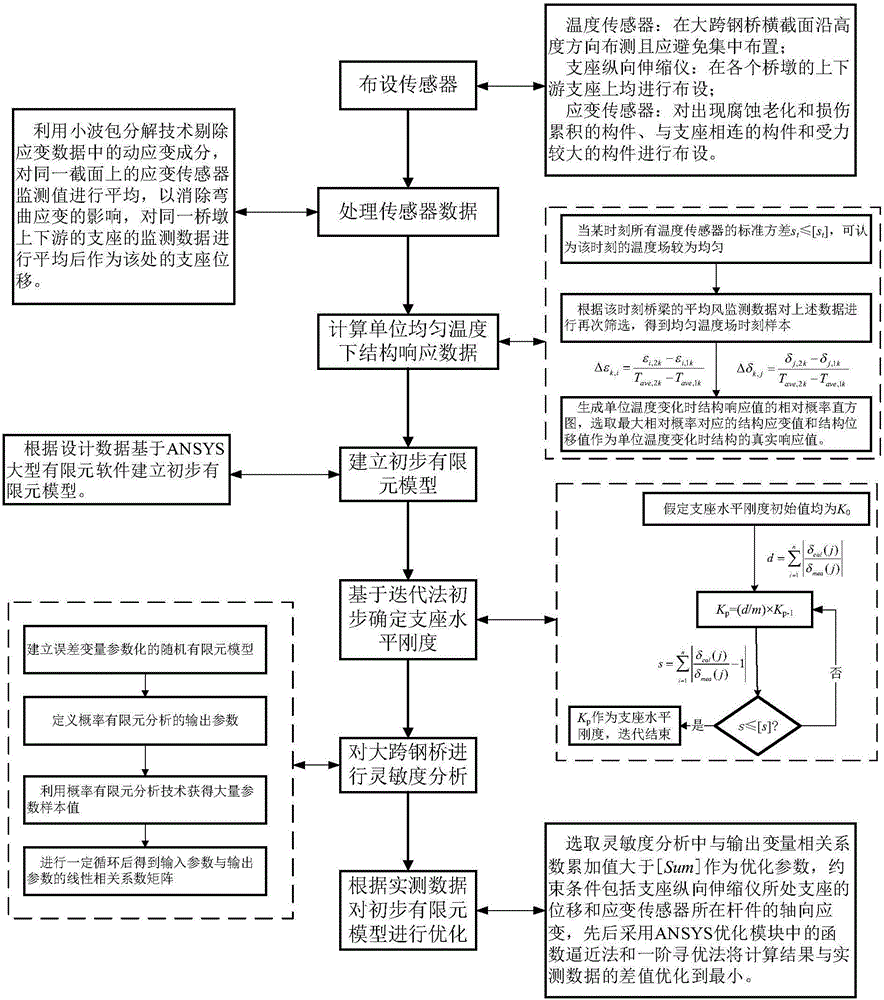
ActiveCN105930571AInput and output are clearImprove stabilityGeometric CADDesign optimisation/simulationTemperature responseElement model
The invention discloses a unit temperature response monitoring value based correction method for a finite element model of a large-span steel bridge. The method comprises the following major steps of 1) analyzing annual monitoring data of the large-span steel bridge and determining static strain and displacement generated by unit uniform temperature change based on a relative probability histogram of a structure response value during unit temperature change; 2) establishing a primary finite element model according to design data; 3) preliminarily determining the horizontal stiffness of a steel bridge support by adopting an iterative method; 4) performing sensitivity analysis on the large-span steel bridge based on actual measurement data of displacement at the large-span steel bridge support and strain in a key position, and determining a design variable with a relatively high coefficient of correlation with the actual measurement data; and 5) performing optimization analysis on the finite element model of the large-span steel bridge by reducing a difference value of a finite element calculation result and the actual measurement data. Compared with a generally adopted finite element model correction method based on dynamic response results of test modal data and the like, the method has the advantages of simplicity, accuracy, relatively low expense and high security.
Owner:SOUTHEAST UNIV
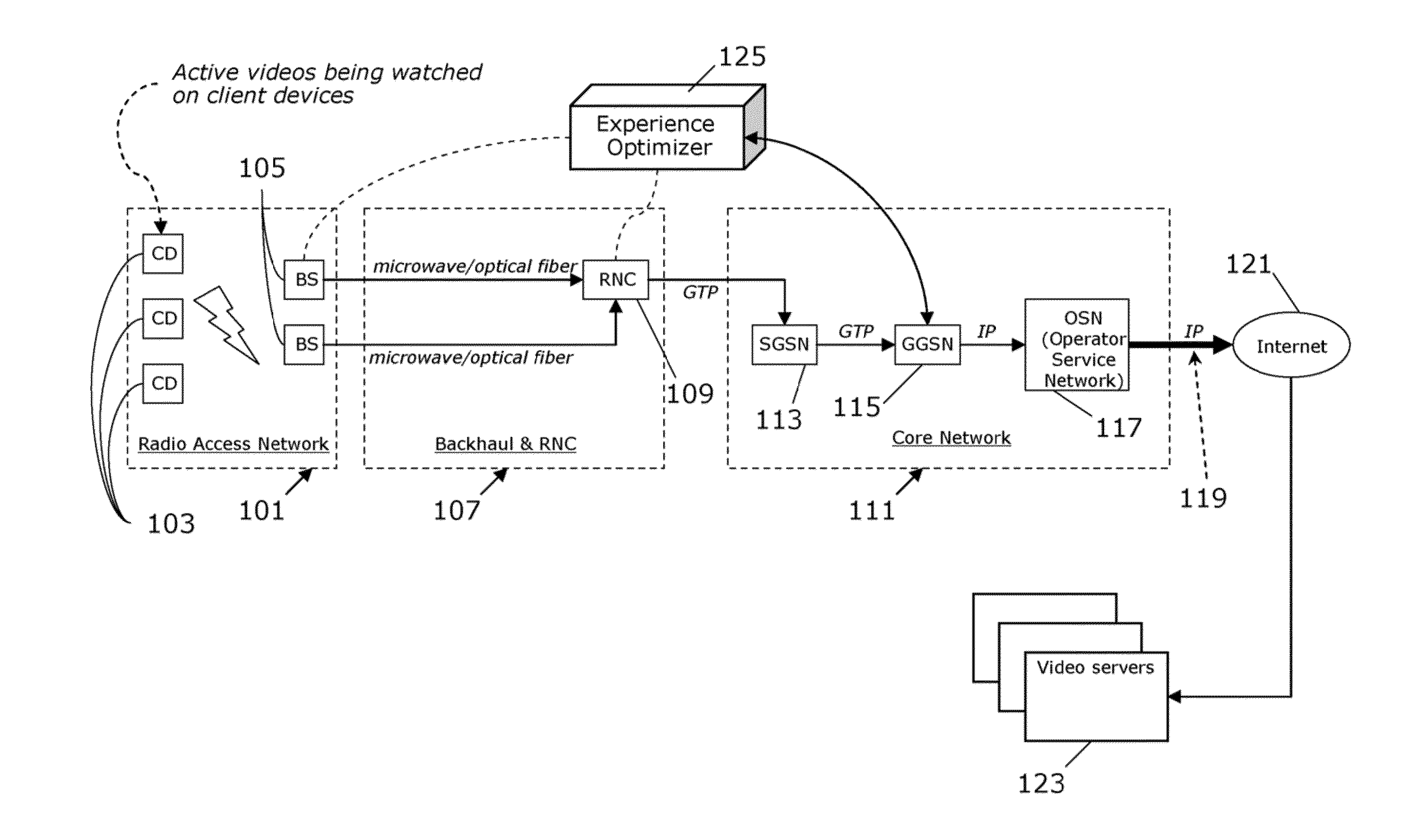
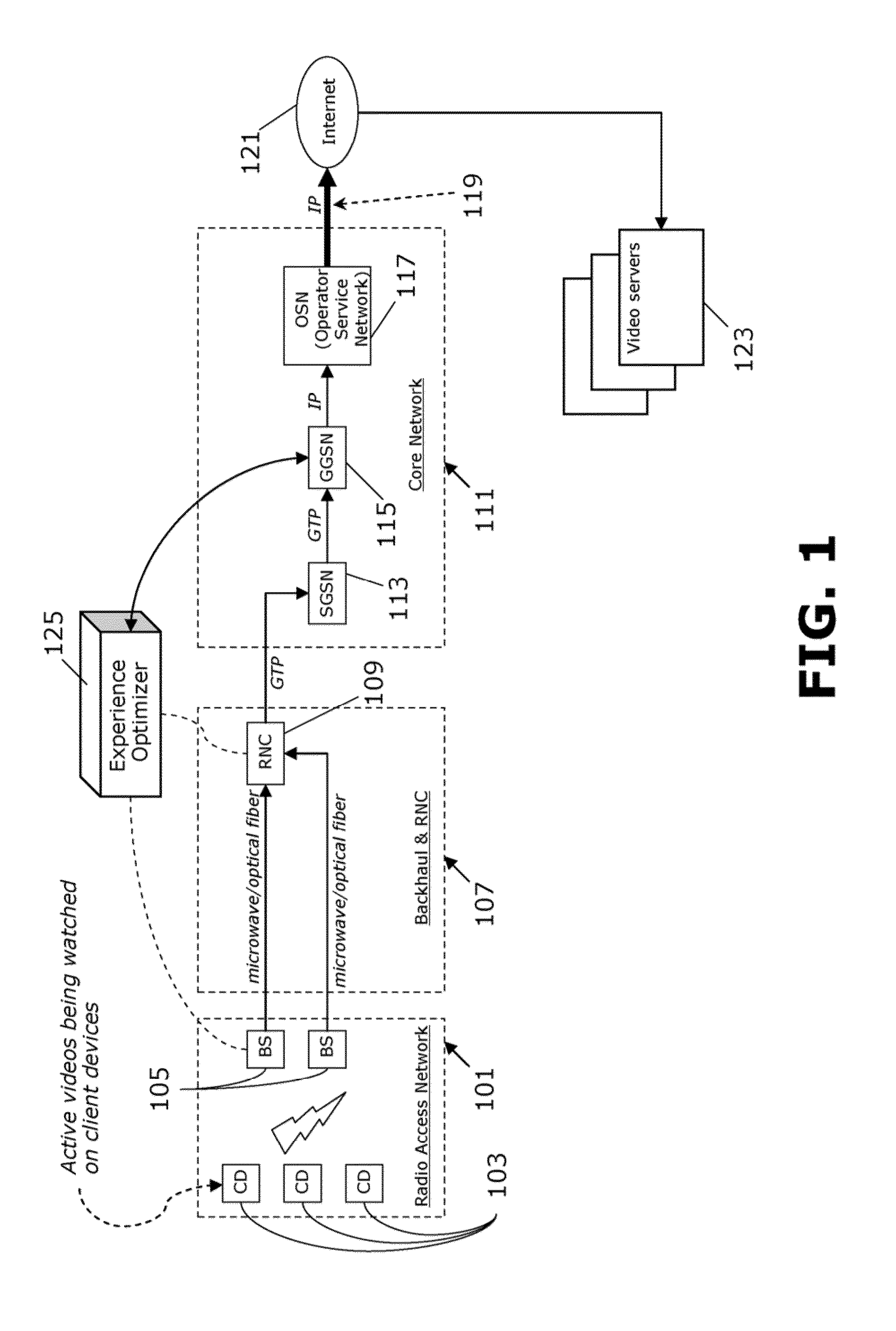
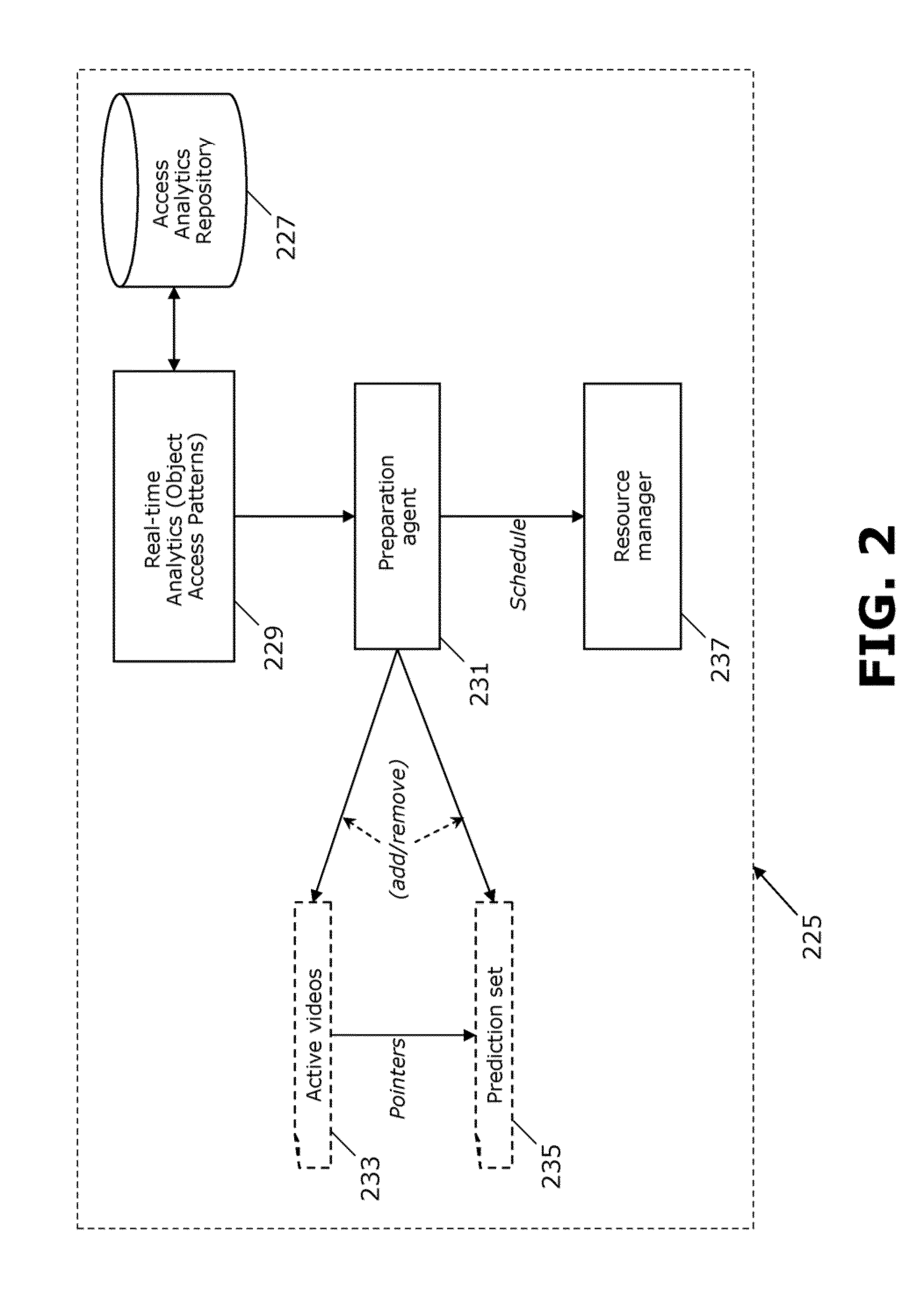
Incremental preparation of videos for delivery
ActiveUS20140006950A1Input/output for user-computer interactionMultiple digital computer combinationsVideo deliveryRelative probability
Methods and arrangements for video delivery preparation. A video, being accessible online, is displayed at an interface in response to a user request. A relative probability of video access by the user with respect to at least two other online-accessible videos is qualitatively determined. An ordered prediction set is created with respect to the other videos. The other videos are prepared incrementally based on the prediction set, so that the user is able to access and view the videos. The preparing includes preparing a first one of the other videos over a first time period and a second one of the other videos over a second time period, wherein at least a portion of the first time period is coincident with at least a portion of the second time period. An element is displayed at the interface which provides a connection to at least one of the other videos.
Owner:IBM CORP
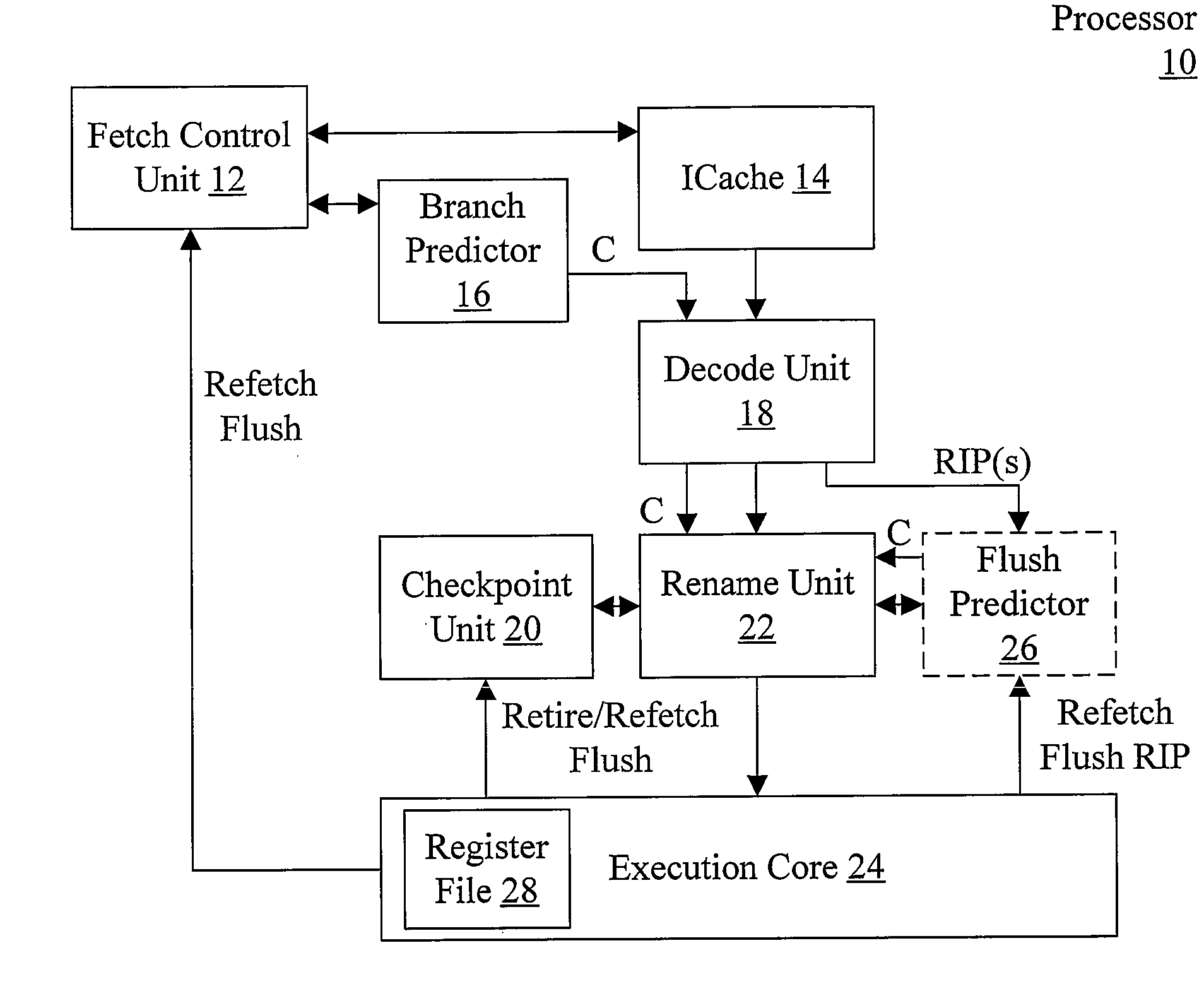
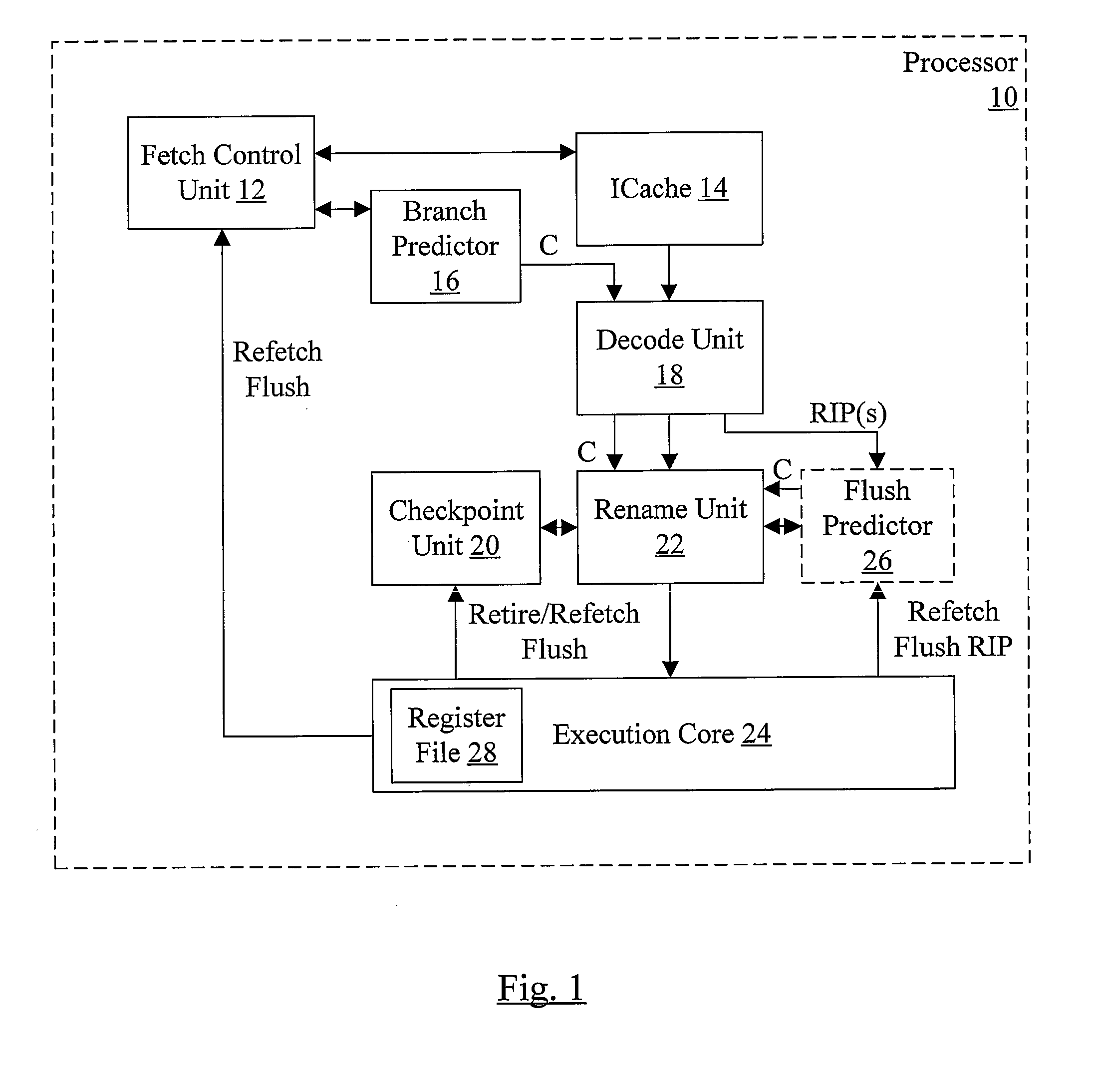
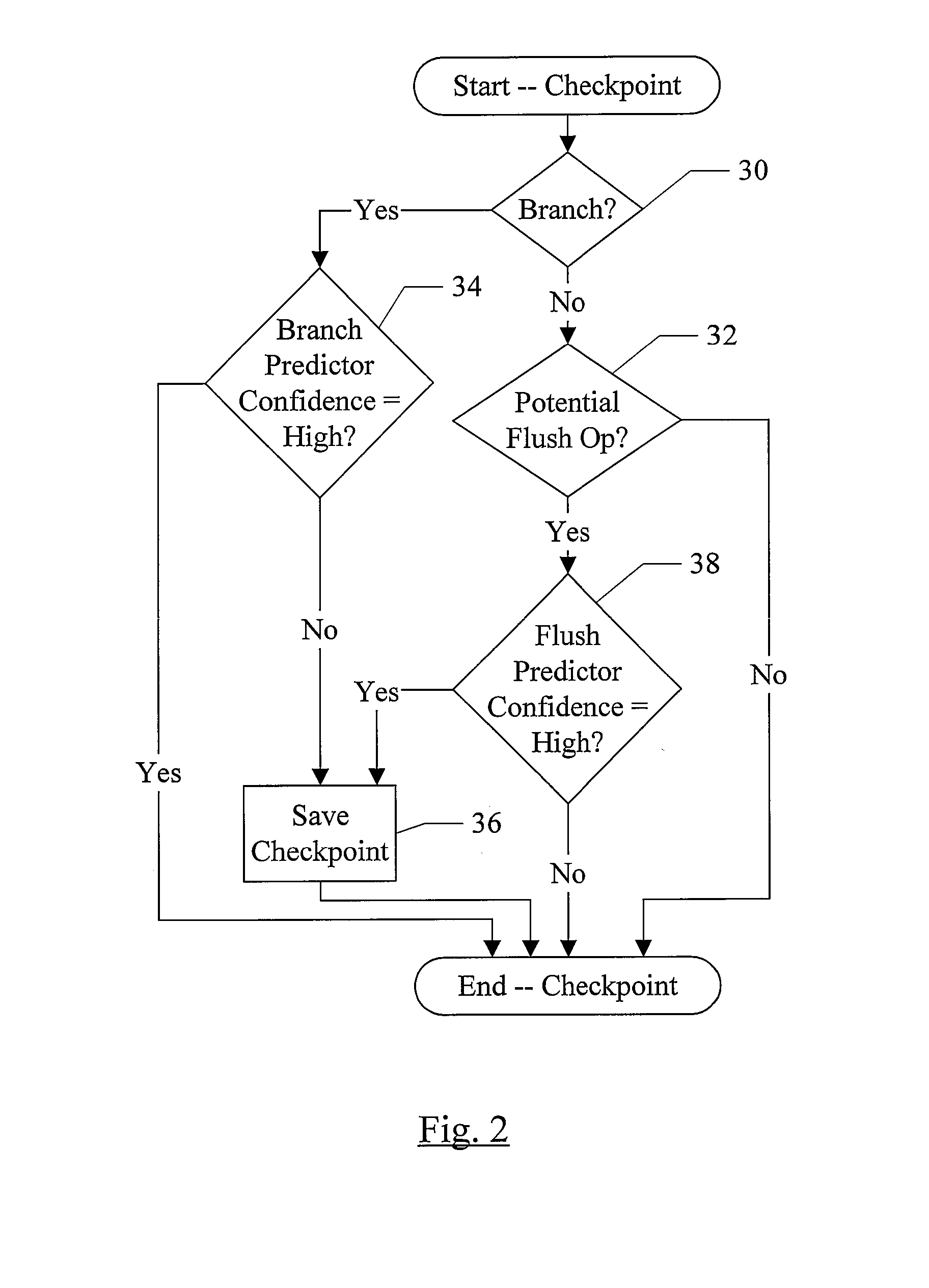
Checkpoint Efficiency Using a Confidence Indicator
InactiveUS20080148026A1Digital computer detailsSpecific program execution arrangementsConfidence factorRelative probability
In one embodiment, a processor comprises a predictor, a checkpoint unit, and circuitry coupled to the checkpoint unit. The predictor is configured to predict an event that can occur during an execution of an instruction operation in the processor. Furthermore, the predictor is configured to provide a confidence indicator corresponding to the prediction. The confidence indicator indicates a relative probability of a correctness of the prediction. The checkpoint unit is configured to store checkpoints of speculative state corresponding to respective instruction operations. Coupled to receive the confidence indicator, the circuitry is configured to save a first checkpoint of speculative state corresponding to the instruction operation if the confidence indicator indicates a first level of probability of correctness. The circuitry is further configured not to save the first checkpoint if the confidence indicator indicates a second level of probability.
Owner:ADVANCED MICRO DEVICES INC
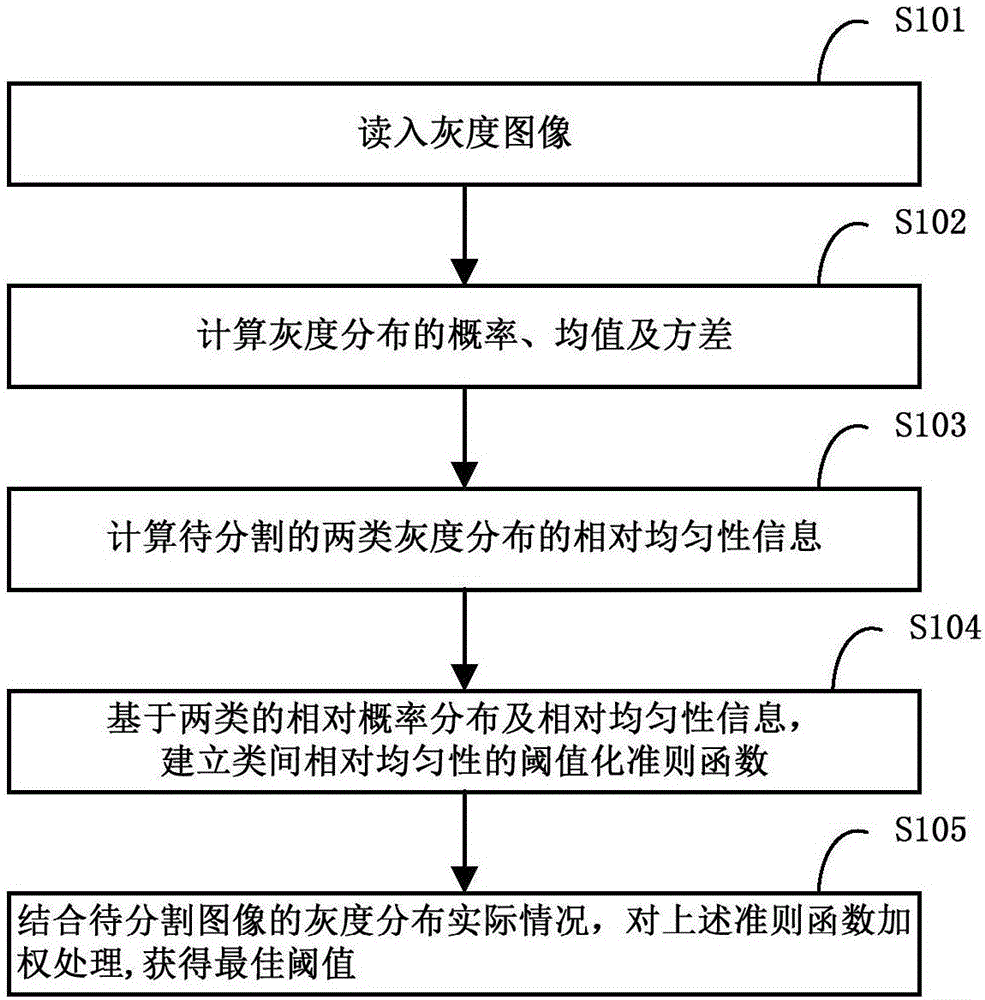
Inter-class relative uniformity-based image adaptive thresholding method and apparatus
InactiveCN106780534ATarget integrityClear edgesImage analysisPattern recognitionRelative probability
The invention discloses an inter-class relative uniformity-based image adaptive thresholding method and apparatus. The method comprises the following steps of reading a grayscale image; calculating a probability, a mean value and a variance of grayscale distribution; calculating relative uniformity information of two types of to-be-segmented grayscale distribution, wherein two types of grayscales are a target grayscale and a background grayscale respectively; and based on relative probability distribution and relative uniformity information of the two types, establishing a thresholding criterion function of inter-class relative uniformity. According to the method and the apparatus, a target obtained by segmentation is completer, and the edge is clearer, so that the applicability can be improved.
Owner:XIAN UNIV OF POSTS & TELECOMM
Method and apparatus for load balancing work on a network of servers based on the probability of being serviced within a service time goal
ActiveUS7770175B2Guaranteed to workReduce overheadResource allocationManual exchangesWork distributionRelative probability
Owner:AVAYA INC
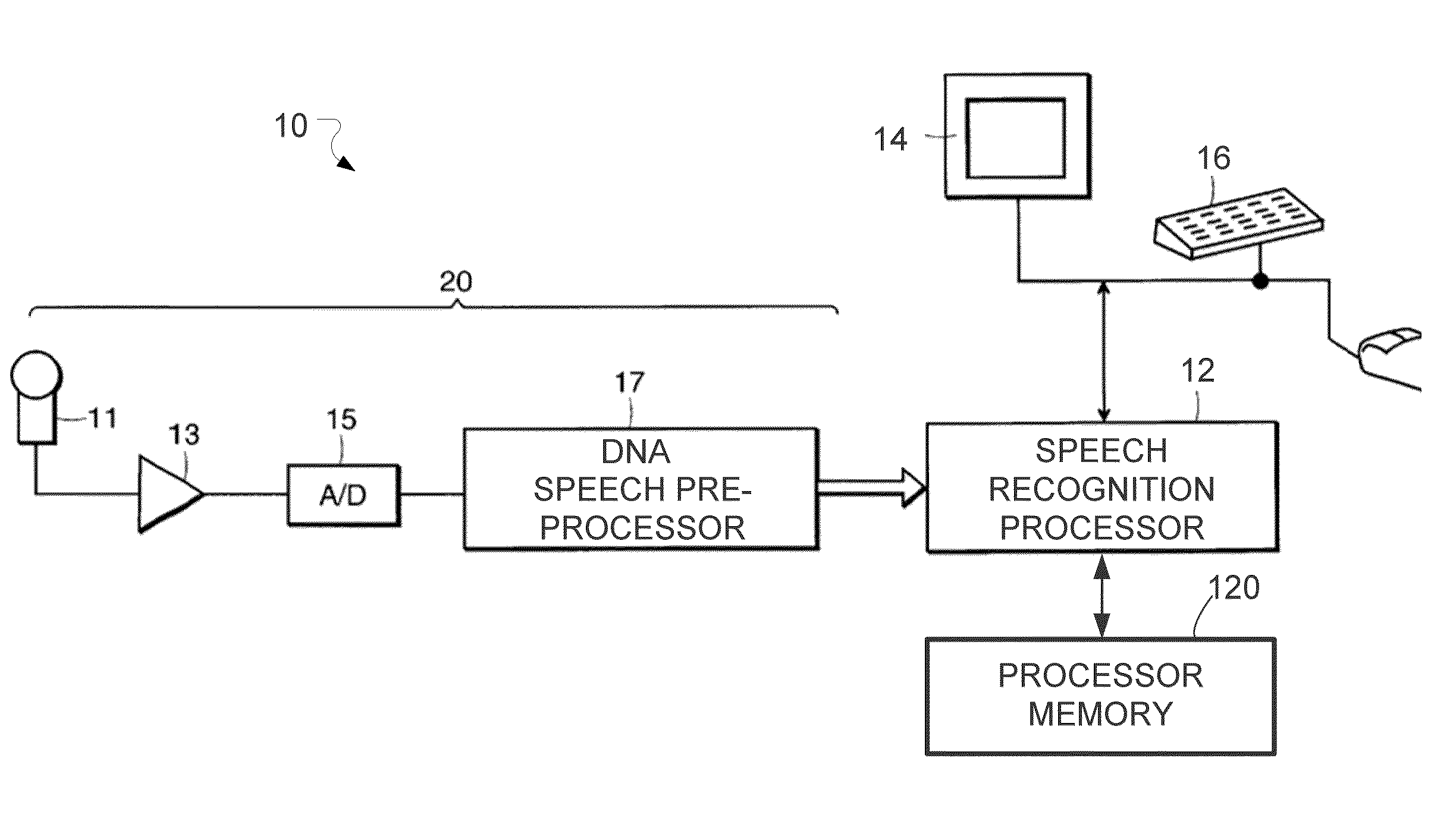
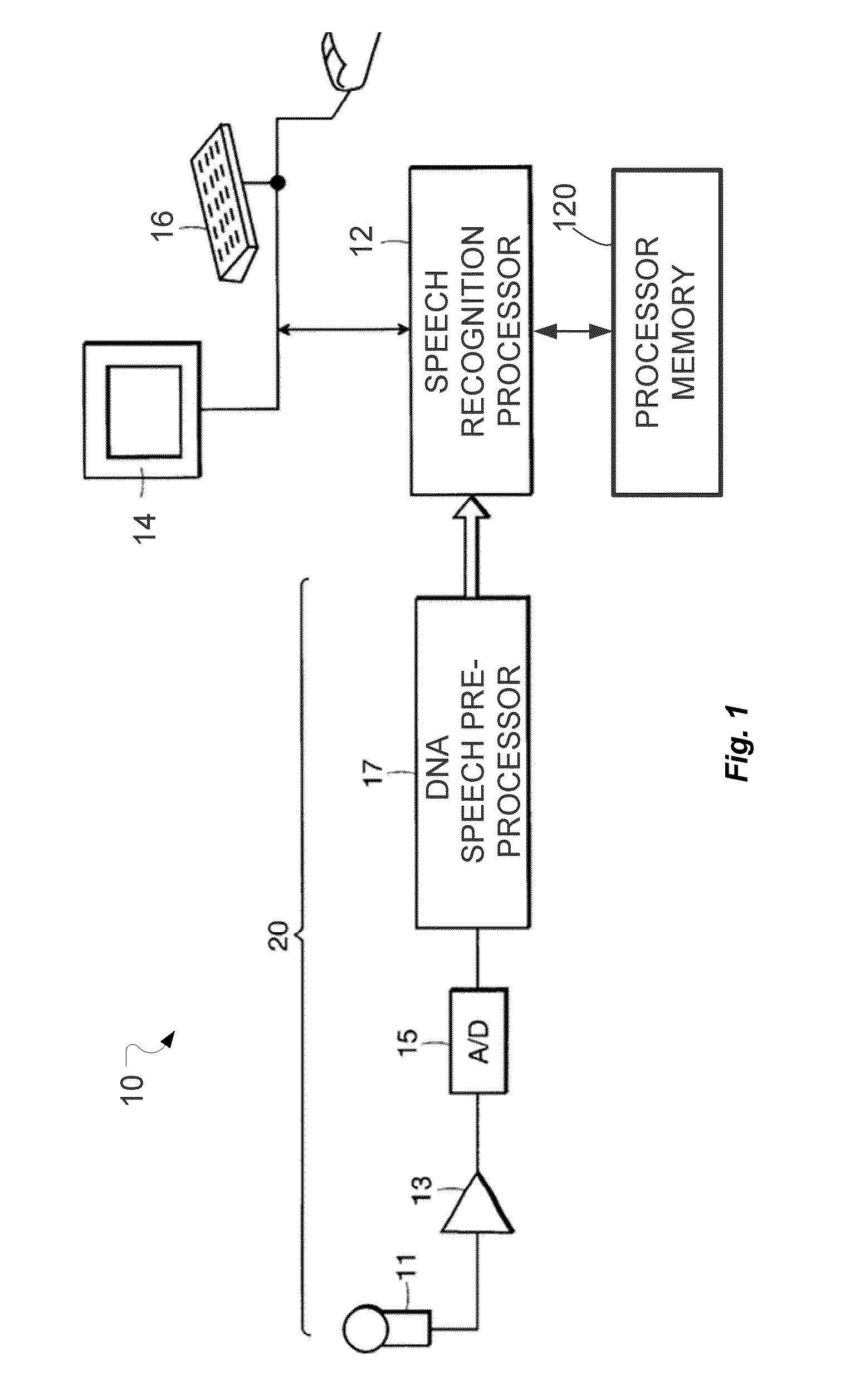
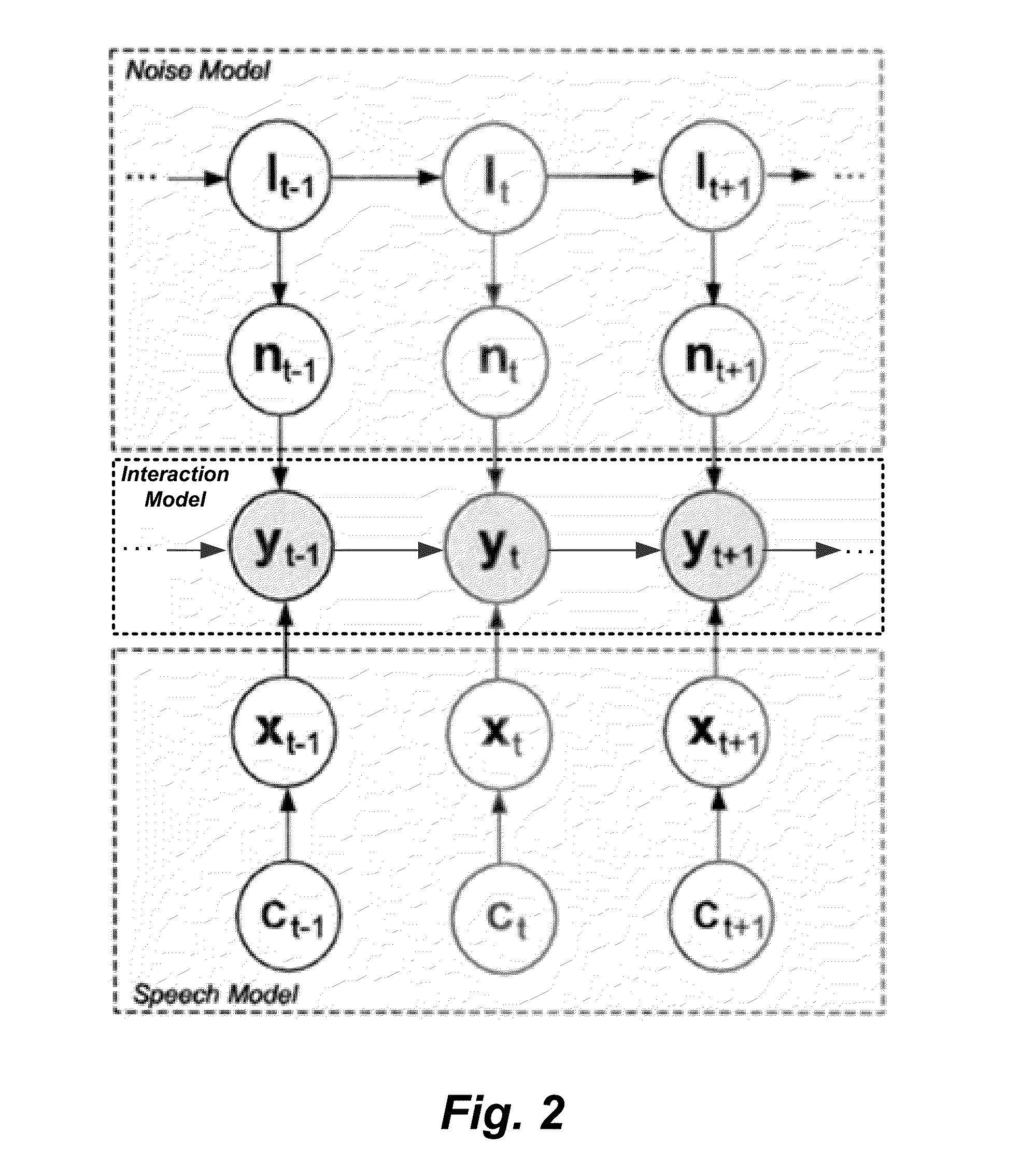
System and Method for Dynamic Noise Adaptation for Robust Automatic Speech Recognition
A speech processing method and arrangement are described. A dynamic noise adaptation (DNA) model characterizes a speech input reflecting effects of background noise. A null noise DNA model characterizes the speech input based on reflecting a null noise mismatch condition. A DNA interaction model performs Bayesian model selection and re-weighting of the DNA model and the null noise DNA model to realize a modified DNA model characterizing the speech input for automatic speech recognition and compensating for noise to a varying degree depending on relative probabilities of the DNA model and the null noise DNA model.
Owner:CERENCE OPERATING CO
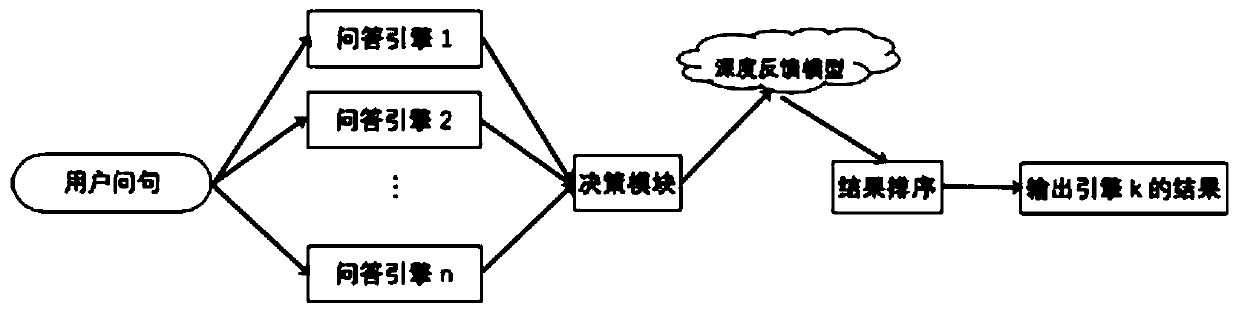
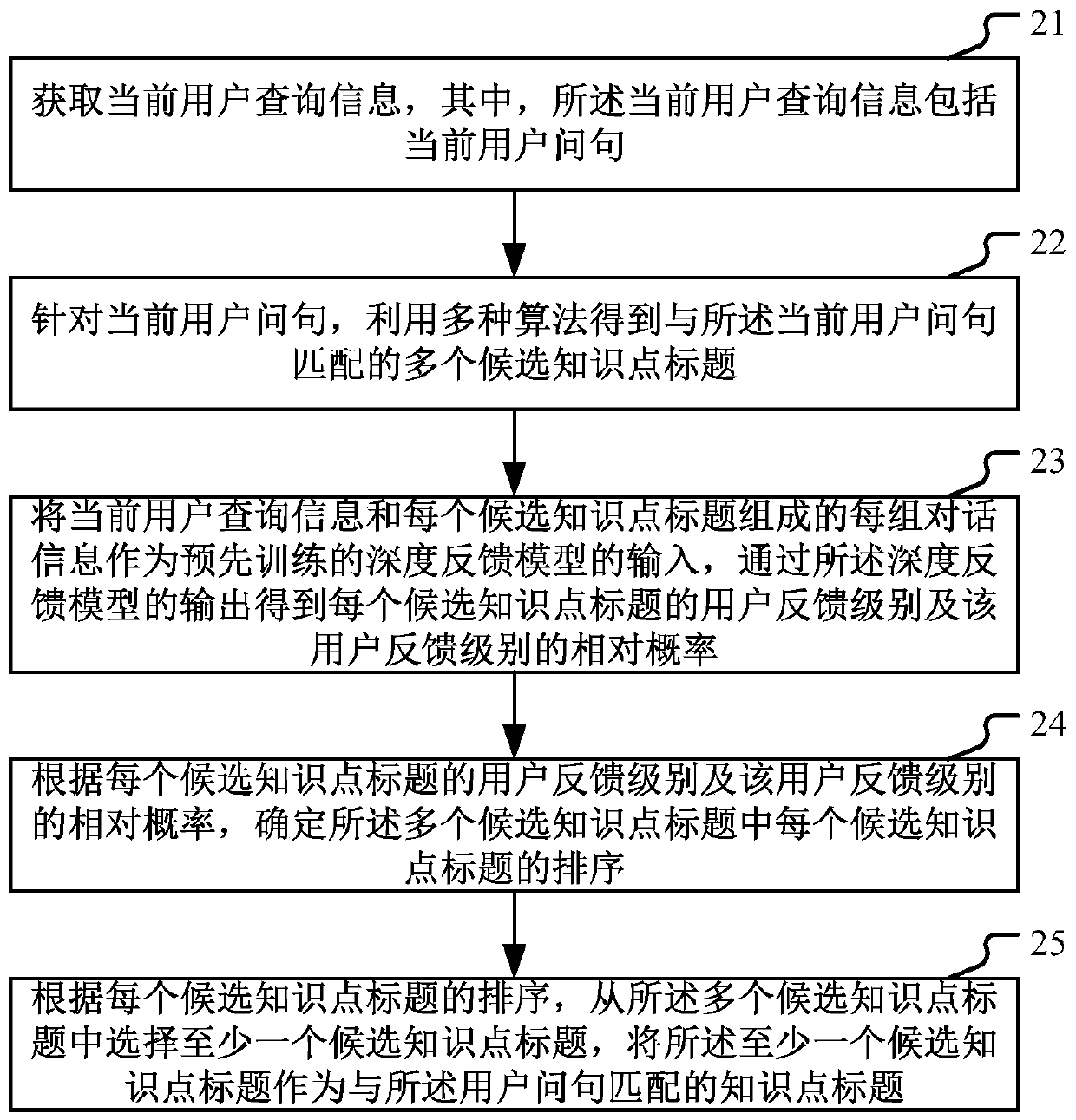
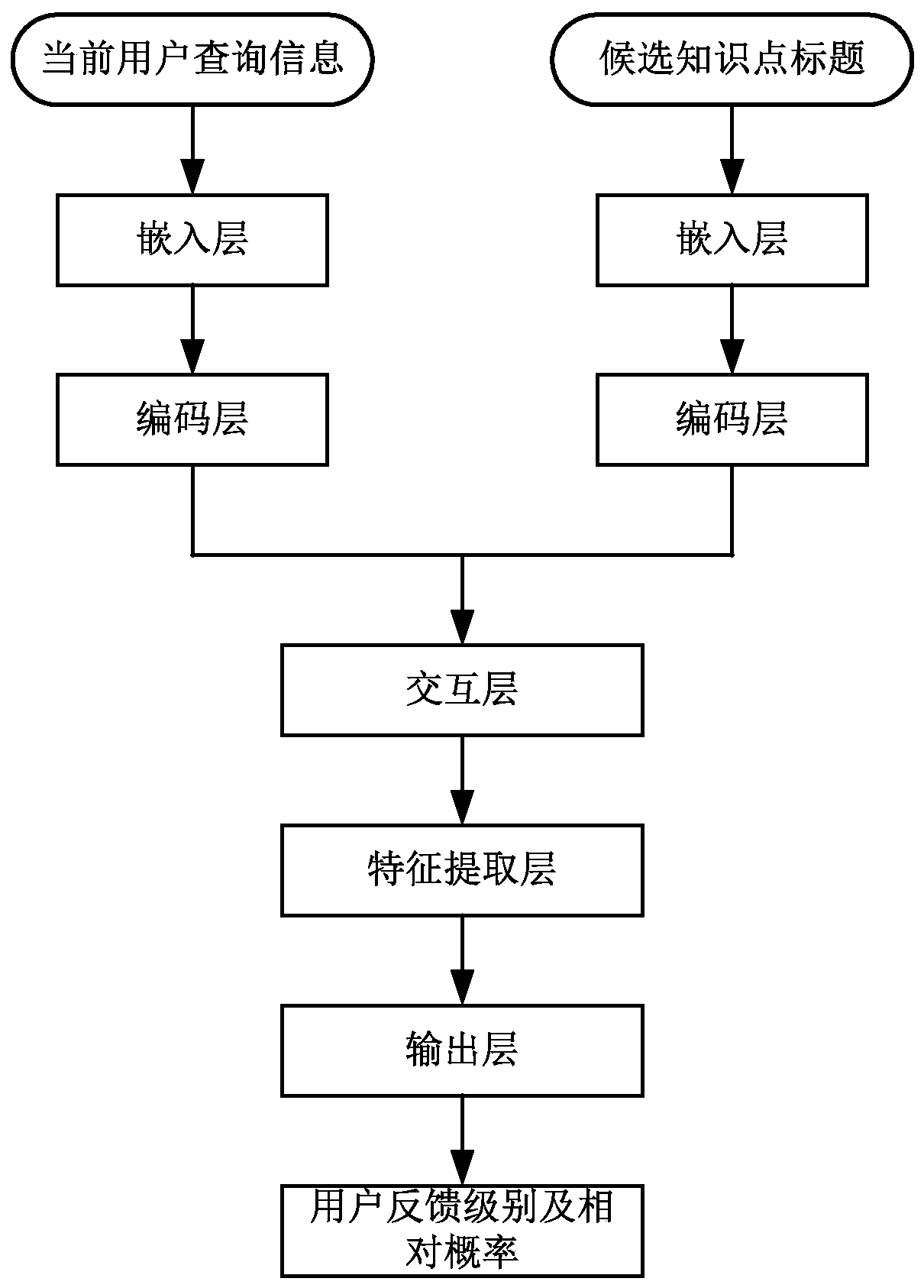
User question and knowledge point title matching method and device
ActiveCN110032623AImprove satisfactionText database queryingSpecial data processing applicationsRelative probabilityData mining
The embodiment of the invention provides a user question and knowledge point title matching method and device, and the method comprises the steps: obtaining current user query information which comprises a current user question; for the current user question, obtaining a plurality of candidate knowledge point titles matched with the current user question by using a plurality of algorithms; takingeach group of dialogue information consisting of the current user query information and each candidate knowledge point title as the input of a pre-trained depth feedback model, and obtaining the userfeedback level of each candidate knowledge point title and the relative probability of the user feedback level through the output of the depth feedback model; according to the user feedback level of each candidate knowledge point title and the relative probability of the user feedback level, selecting at least one candidate knowledge point title from the plurality of candidate knowledge point titles, and taking the at least one candidate knowledge point title as a knowledge point title matched with the user question, thereby improving the overall user satisfaction degree of the robot answer.
Owner:ADVANCED NEW TECH CO LTD
Methods and systems for detecting a closure of a navigable element
ActiveUS9818295B2Accurate measurementAccurate informationInstruments for road network navigationTransmission systemsSimulationRelative probability
A method of detecting the closure of a road element is disclosed; the road element being one of a set of alternative incoming or outgoing elements at a node in a network of navigable elements. A server obtains positional data relating to the position of a plurality of devices with respect to time traversing the node. A count is determined of the number of devices in a consecutive sequence of device selecting a given one of the navigable elements from among the set of elements. The count is compared to a predetermined threshold to determine whether another one of the elements is closed. The threshold is based upon the relative probability of the element to which the count relates being taken from the set of road elements.
Owner:TOMTOM DEV GERMANY
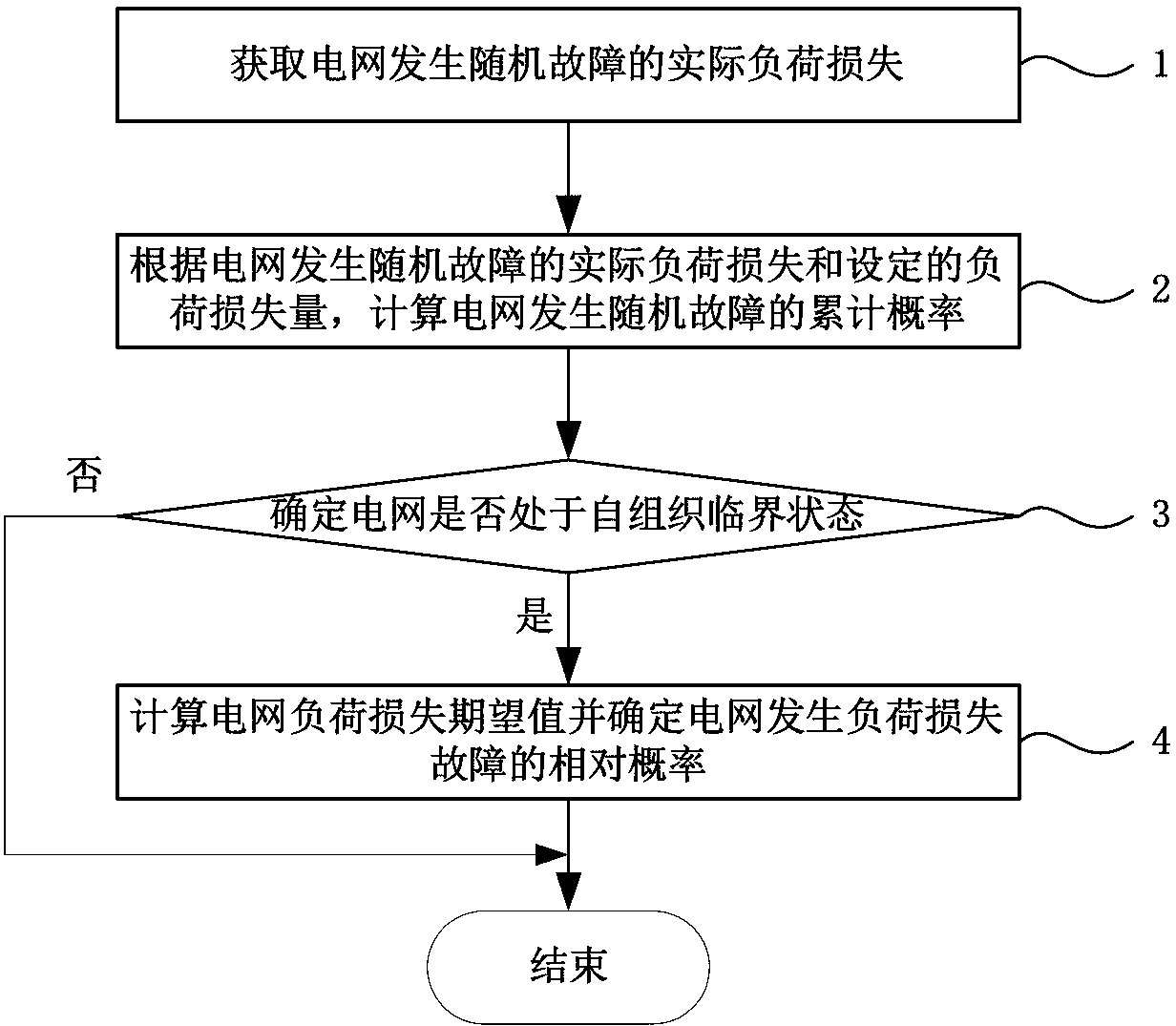
Identification method of complex power grid self-organization critical state
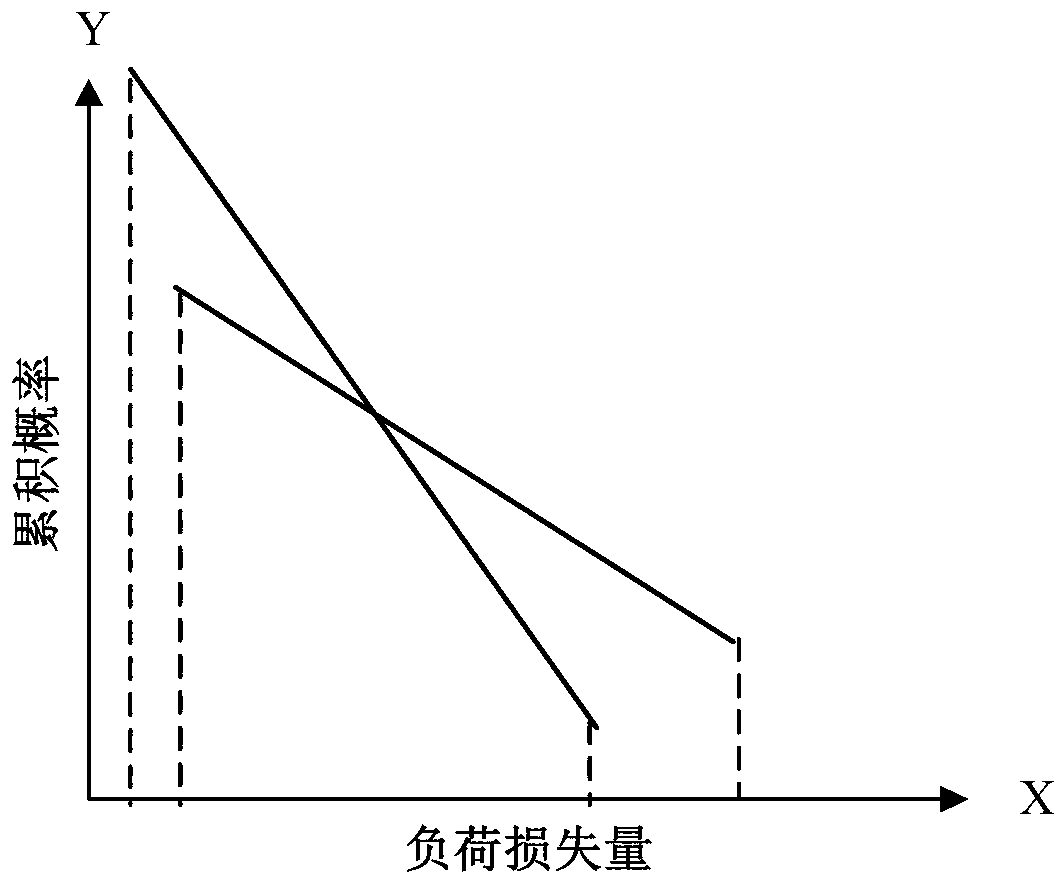
InactiveCN103311925AData processing applicationsAc network circuit arrangementsCascading failureRegression analysis
The invention discloses an identification method of a complex power grid self-organization critical state in the technical field of electric power system cascading failure prevention. The method includes: obtaining actual load loss caused by random failures occurring on a power grid; calculating cumulative probability of the random failures occurring on the power grid according to the actual load loss caused by the random failures occurring on the power grid and set load loss amount; performing regression analysis on the set load loss amount and the cumulative probability so as to determine whether the power grid is in a self-organization critical state; calculating a power grid load loss expectancy value and determining relative probability of load loss failures occurring on the power grid when the power grid is in the self-organization critical state. The identification method enables users to accurately judge whether the power grid is in the self-organization critical state at present, obtain probability of cascading failures occurring on the power grid, calculate load loss amount after the cascading failures occur and meanwhile estimate relative probability of large-scale power failures caused by the load loss.
Owner:STATE GRID CORP OF CHINA +2
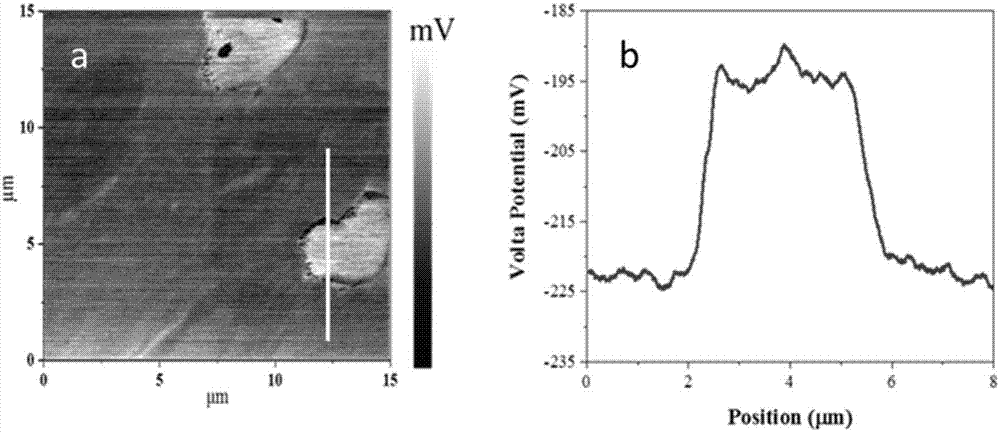
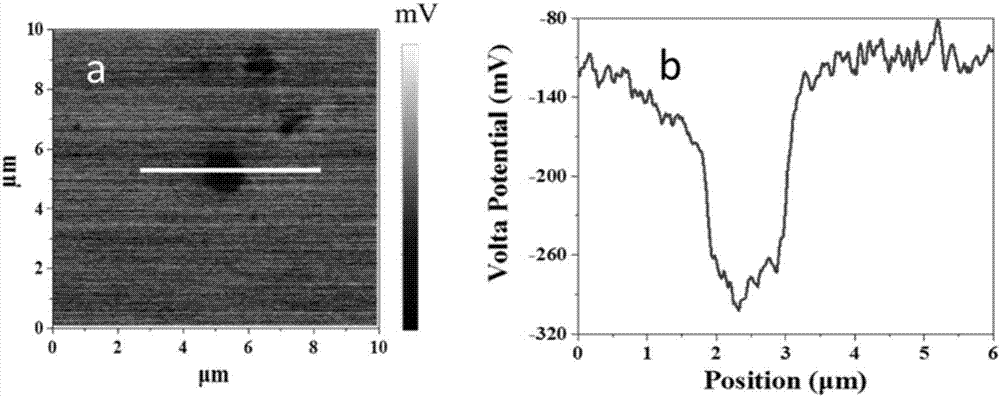
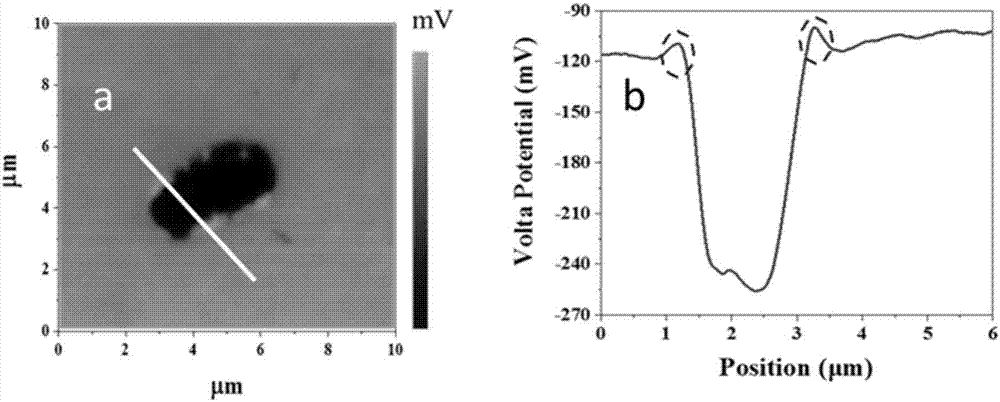
Method for evaluating inclusion types of steel and induced pitting trend thereof
The invention relates to a method for evaluating inclusion types of the steel and an induced pitting trend thereof and belongs to the corrosion evaluation field. The inclusions of the steel are an important factor for induced pitting and other local corrosion. According to volt potential distribution of the inclusions of the steel, the types of the inclusions are discriminated, and the probabilityof induced pitting of the inclusions is evaluated. According to the method, the atomic force microprobe technology is employed for test, the types of the inclusions and the induced pitting difficultydegree can be clearly determined, moreover, the induced pitting phenomenon of the inclusions of the steel is further quantified, relative induced pitting probabilities of different inclusions can beacquired, corrosion resistance of the steel can be evaluated through utilizing the relative probabilities, and the evaluation result is of great importance for development of novel steel products, engineering structure design material selection and steel corrosion life evaluation .
Owner:UNIV OF SCI & TECH BEIJING
Method for Developing and Applying Databases for Idenfication of Microorganisms by MALDI-TOF Mass Spectrometry
InactiveUS20160350475A1Time-of-flight spectrometersLibrary screeningMicroorganismRelative probability
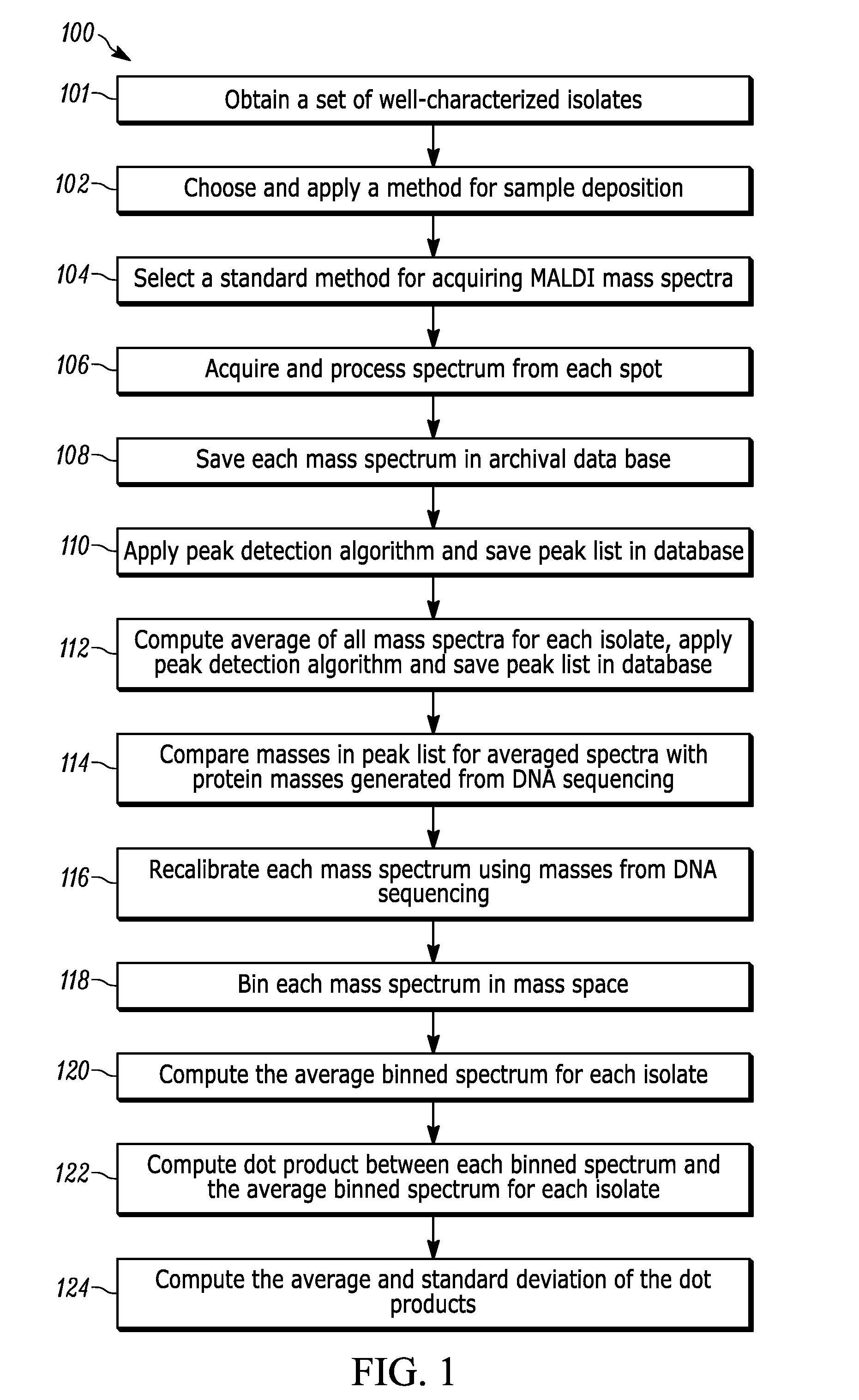
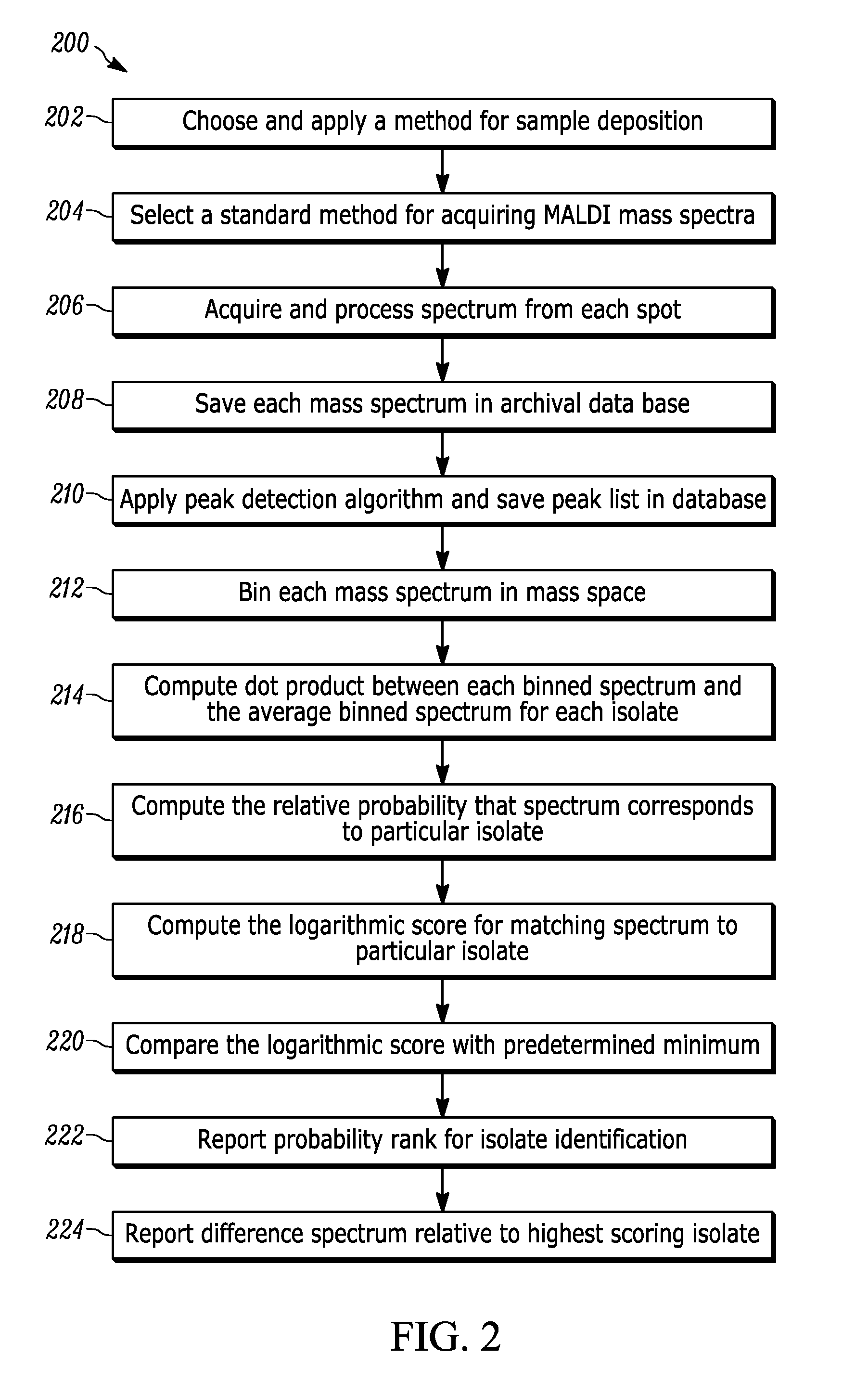
A method for organism identification using MALDI TOF mass spectrometry includes generating a searchable database. A mass spectrum is acquired from a sample. Peak detection of the acquired mass spectrum is performed, binned, and a vector is generated. Dot products are computed between the generated vector of peak detected mass spectrum and averaged binned spectrum for each isolate. A relative probability that acquired mass spectrum matches a spectrum from each isolate in the searchable database is computed. A logarithmic score for matching the acquired mass spectrum with the mass spectrum is computed from each isolate. The logarithmic score for matching the acquired mass spectrum is compared with the mass spectrum from each isolate to a predetermined minimum passing score. A list of isolates is generated with greater than the predetermined minimum score. The probability rank and logarithmic score are then reported for each isolate with a minimum passing score.
Owner:VIRGIN INSTR CORP
Method for identifying single-parent water buffalo parental right, primer and reagent kit thereof
InactiveCN101509033ALower requirementHigh copy numberMicrobiological testing/measurementWater buffaloMitochondrion inheritance
The invention discloses a method for identifying single-parent buffalo paternity relationship as well as primers and kits thereof, belonging to the technical filed of genetic engineering. The method comprising the steps: screening out eight microsatellite primers with rich polymorphism; PCR amplifying by taking detected buffalo genome DNA as a template; detecting PCR amplified fragment through polyacrylamide gel electrophoresis; judging individual genotype according to the detected result; counting single-parent paternity index PI value and parent-child relative probability value W value according to the genotype; and judging whether the paternity relationship is existed or not according to the W value. In order to further improve identification stability, accuracy and sensitivity, the method designs primers so as to identify mitochondrial inheritance according to the D-Loop region of common cattle mtDNA. The method combines microsatellite method with mitochondrial inheritance marker method, and identifies from different angles and reaches consistent result, thereby improving identification stability, accuracy and sensitivity and having the advantages of wider identifying range and lower sample requirement.
Owner:SOUTHWEST UNIVERSITY FOR NATIONALITIES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com