Guaranteed delivery of changes to security policies in a distributed system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
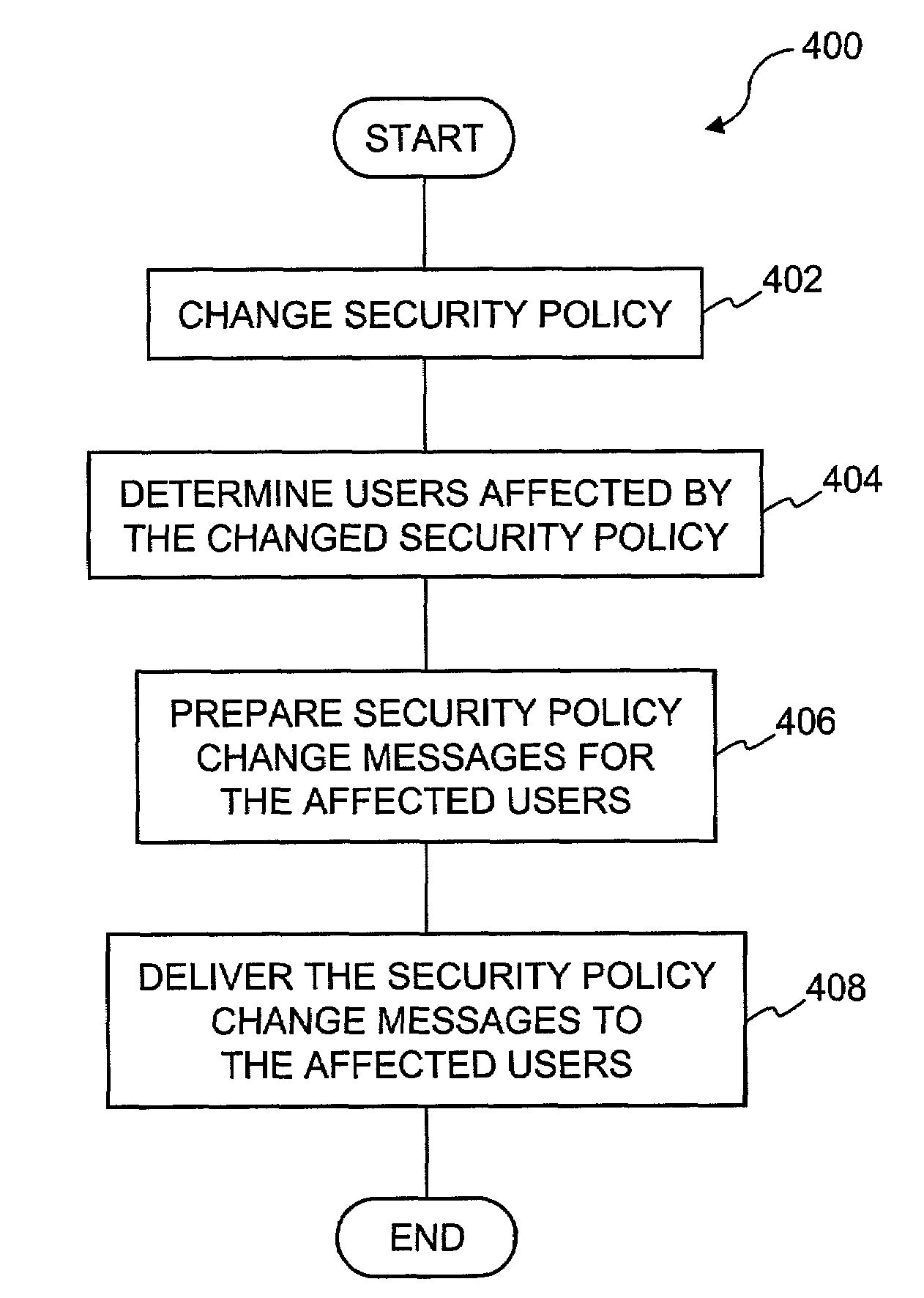
[0034]The present invention relates to improved approaches for effectuating and communicating changes to security policies in a distributed security system. The changes to security policies are distributed to those users in the security system that are affected. As used herein, the user may mean a human user, a software agent, a group of users, a device and / or application(s). Besides a human user who needs to access a secured document, a software application or agent sometimes needs to access the secured document in order to proceed forward. Accordingly, unless specifically stated, the “user” as used herein does not necessarily pertain to a human being. The distribution of such changes to security policies can be deferred for those affected users that are not activated (e.g., logged-in or on-line) with the security system.
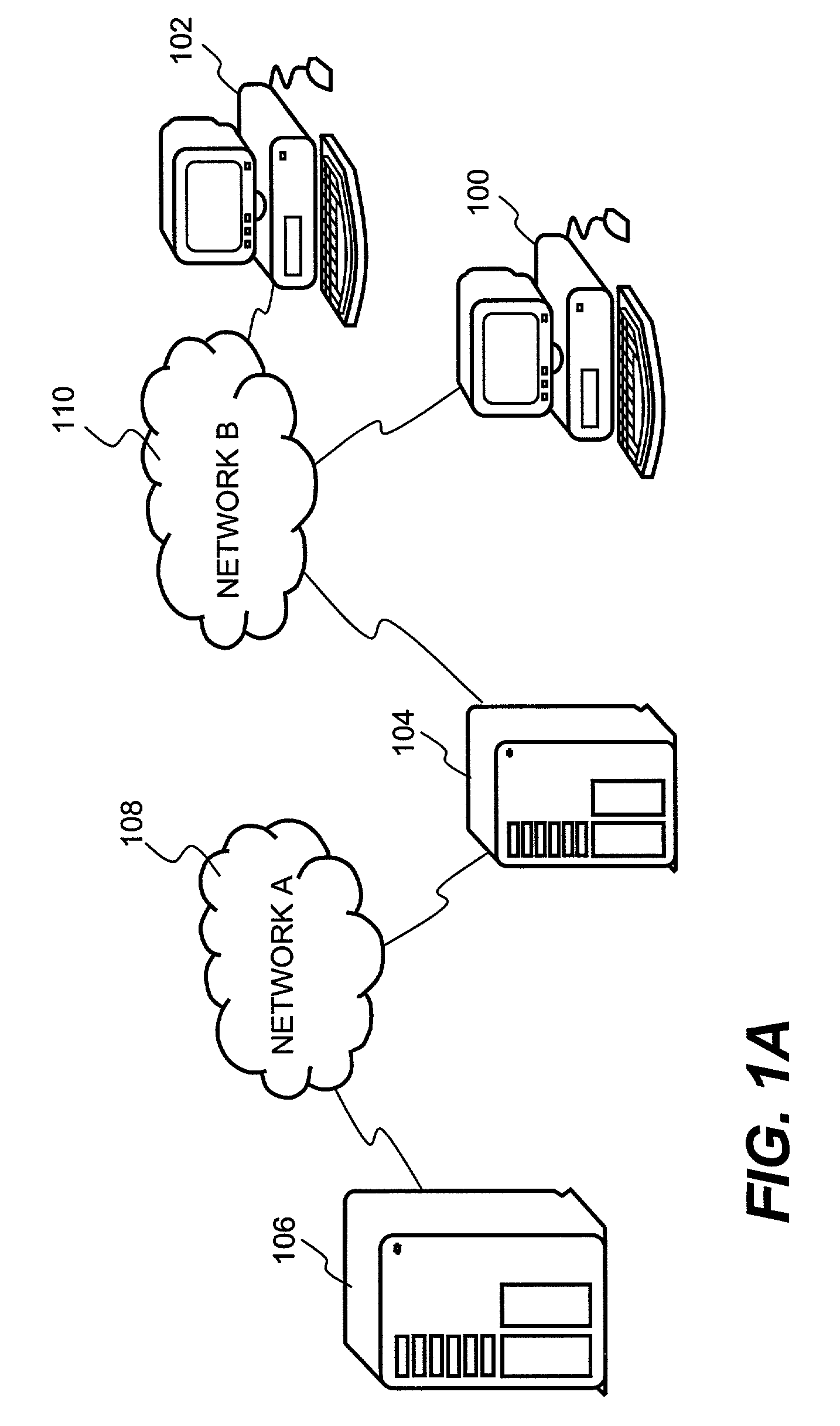
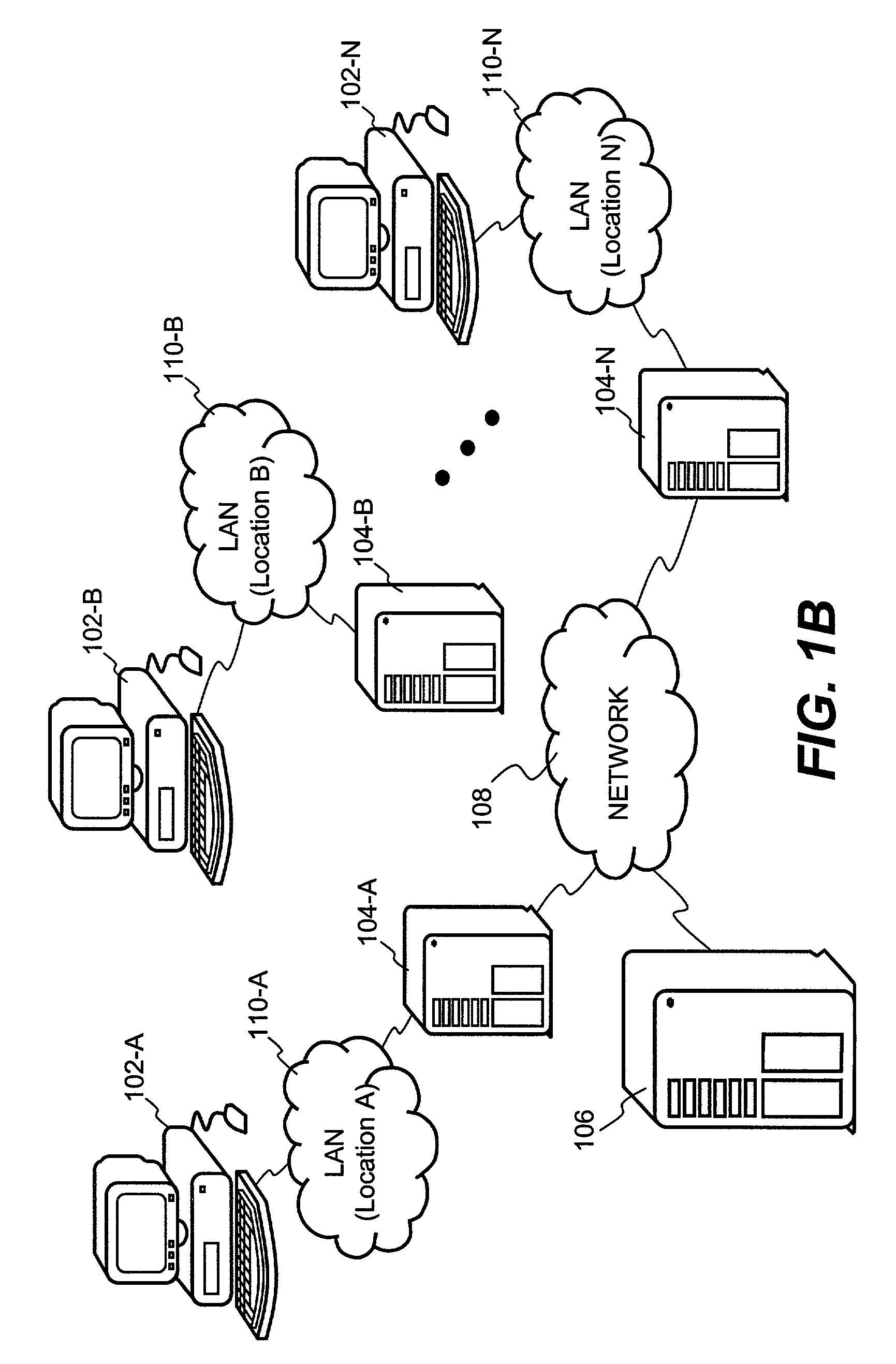
[0035]The present invention is related to processes, systems, architectures and software products for providing pervasive security to digital assets. The present i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com