Code injection based privacy information protection method
A privacy information, code injection technology, applied in digital data protection, instruments, electrical digital data processing, etc., can solve the problems of complex operation, poor applicability, poor reliability, etc., and achieve the effect of easy and deep optimization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be further described below in conjunction with the accompanying drawings.
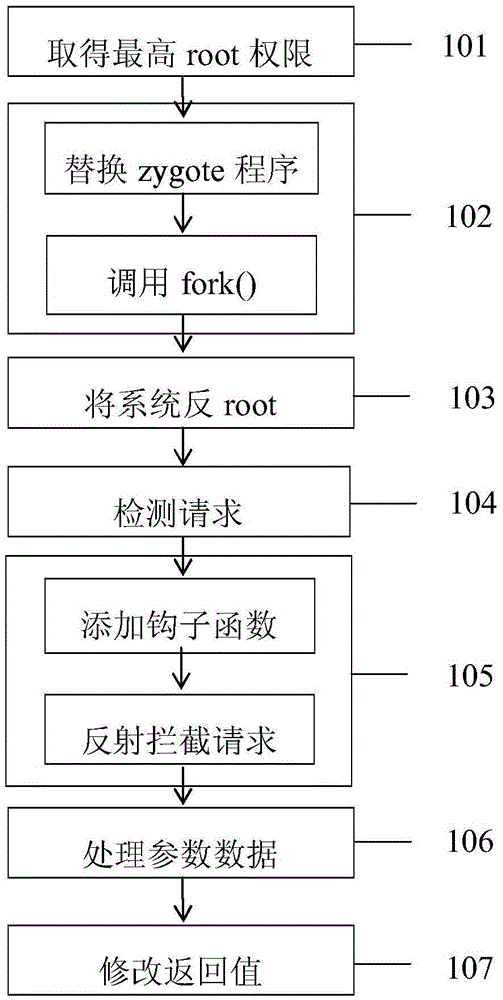
[0023] refer to figure 1 , a method for protecting private information based on code injection, comprising the following steps:
[0024] 101 Obtain the highest root authority of the Android system;
[0025] 102 Use the file manager to download the zygote program of the Android system (Reference 1: "Source Code Analysis of the Android System Process Zygote Startup Process", the source of the document is: http: / / blog.csdn.net / luoshengyang / article / details / 6768304 ) to replace, and create a new process through the system call fork() function (Reference 2: "Fork(systemcall)", the source of the document is: https: / / en.wikipedia.org / wiki / Fork_(system_call)), so that When a new process is generated, it can reflect and intercept the new process, and inject new code for a specific function call;
[0026] 103 reverse root the system after replacing the zygote program;
[0027...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com