Webpagehanging trojan detecting and protecting method and system as well as method for extracting corresponding code
A webpage hanging horse and protection system technology, applied in the field of network security, can solve problems such as difficult to extract tag codes, and achieve the effect of improving performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0110]The present embodiment relates to a method for extracting the code of the label related to the web page hanging horse in the web page, including:
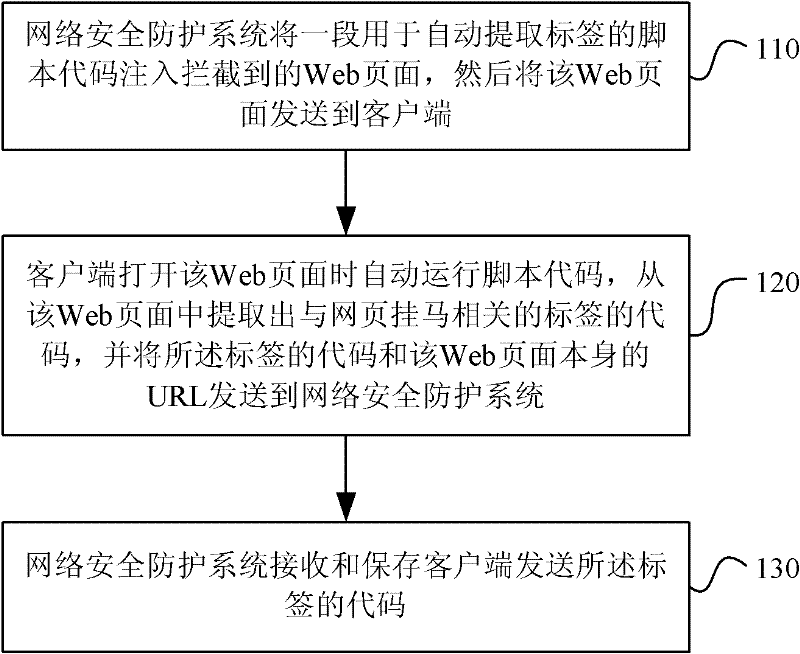
[0111] Step 10, the network security protection system (also referred to as the system in the text) injects a section of script code for automatically extracting tags into the intercepted Web page, and then sends the Web page to the client;
[0112] Wherein, the above-mentioned script code is configured as follows: when the client opens the injected web page, the script code is triggered to run automatically, and the code of the label related to the webpage hanging horse is extracted from the web page, and the code of the extracted label is combined with the code of the web page The URL itself is sent to the system, where the code of the extracted tag contains the URL to be detected.
[0113] The above script code may include startup extraction code and label extraction code, wherein:
[0114] The tag extraction code include...
no. 2 example
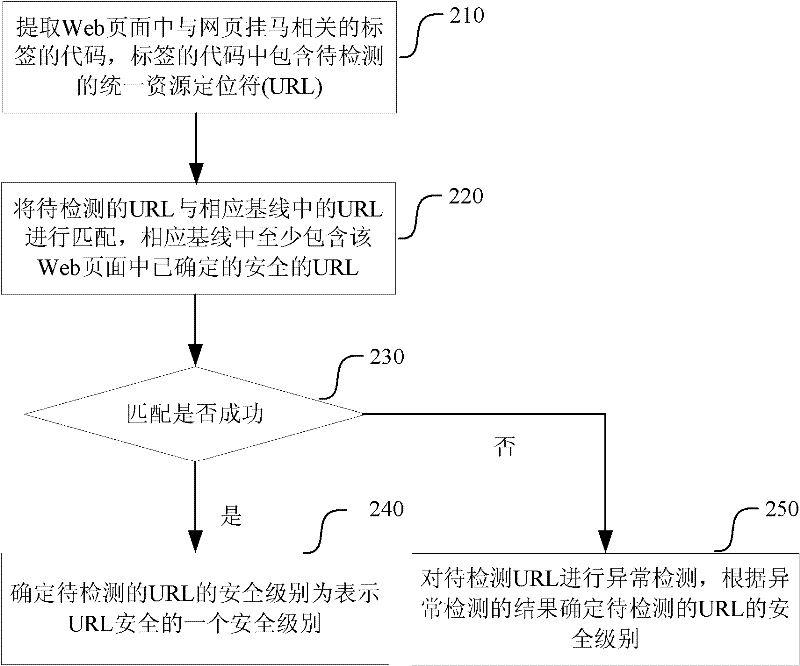
[0125] This embodiment relates to the detection of a web page Trojan, mainly for detecting the URL in the code of the tag related to the web page Trojan extracted from the web page, and judging its security level.
[0126] Usually, the system sets multiple security levels for URLs. When there are only two security levels, it is equivalent to only judging whether the URL is safe or not. When there are more than three security levels, a more precise indication of the security level of the URL can be made. For example, in one example, 5 security levels, security level 1 to security level 5, are set for the URL. Security level 1 has the highest security level, that is, the safest, and security level 5 has the lowest security level, that is, the least safe or the most dangerous.
[0127] Part of the security level can be set to indicate that the URL is safe, and another part of the security level can be set to indicate that the URL is not safe, such as being set by the administrat...
no. 3 example
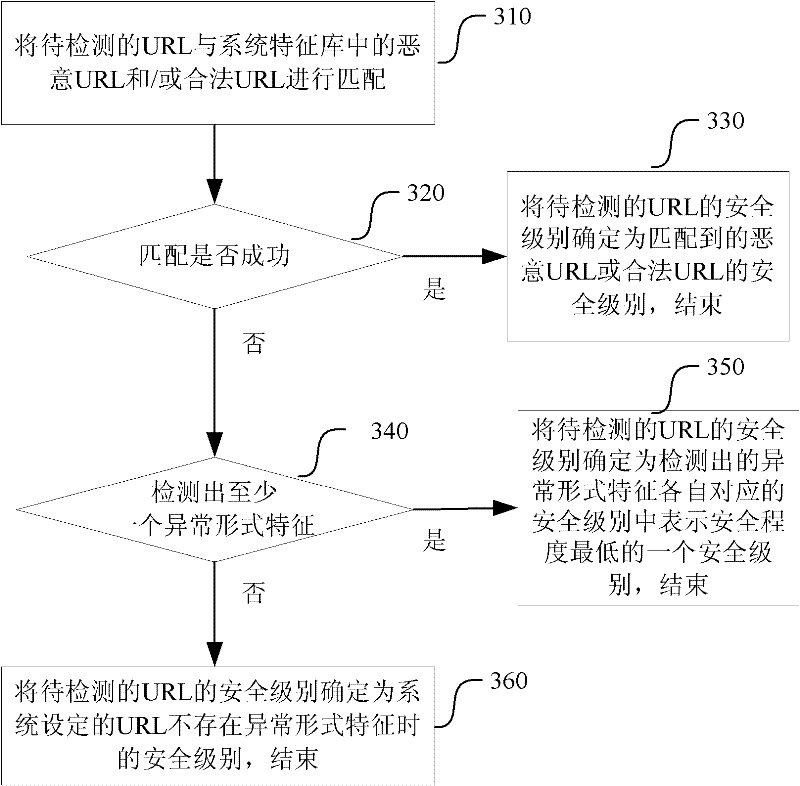
[0185] This embodiment relates to a method for detecting and protecting a Trojan on a web page. Wherein, the webpage Trojan detection adopted may be the same as that in the second embodiment. This embodiment mainly discusses how to start the detection of Trojan Trojans on webpages, so as to avoid frequent detections that occupy too many computing resources, or failure to detect Trojan Trojans on webpages in time.
[0186] After the network security protection system detects the web page Trojan, it also records the identification information of the Web page, the security level related to the web page and Trojan, and the detection time in the Web page security level table, and the Web page can The URL of the Web page itself can be identified. In the Web page security level table, unsafe URLs in the Web page or URLs other than safe URLs can also be recorded. Then use the Web page security level table to realize security protection.
[0187] Such as Figure 4 As shown, the pres...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com