Detection method and system for cross comparison of malicious code of interior and exterior view based on virtual machine
A malicious code and detection method technology, which is applied in the field of malicious code behavior detection based on the cross-comparison of inside and outside views of a virtual machine, can solve the problems of complex logical relationship of malicious code, low detection accuracy, and inability to fully obtain functional semantic information, etc., to achieve The effect of improving detection accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
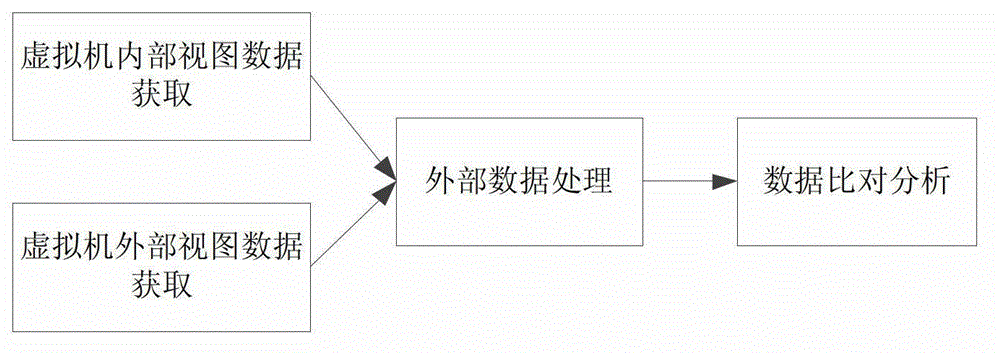
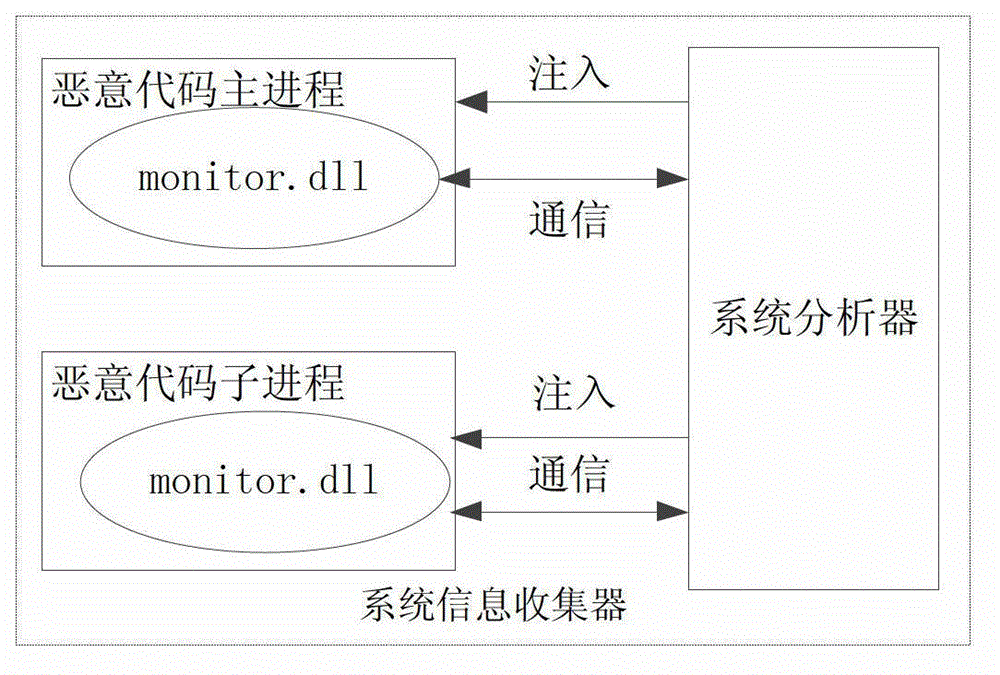
[0047] Below, refer to the attached Figure 1~6 Describe in detail the malicious code behavior detection method based on the cross-comparison of the inside and outside views of the virtual machine of the present invention.
[0048] The technical solution of the present invention is: combining the existing malicious code detection technology and virtual machine technology, by using the dynamic tracking detection method inside the virtual machine, detecting the execution flow of malicious software, and recording the execution path, and then from the outside of the virtual machine , analyze the raw memory data of the virtual machine through the host system, extract all information about malware in the memory, and record the execution information. Then feed back the information collected from the internal and external environment to the detection and analysis engine to analyze the logical relationship of the behavioral data, and determine whether it is malicious code by comparing ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com