Patents
Literature
78results about How to "Reduce interaction process" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
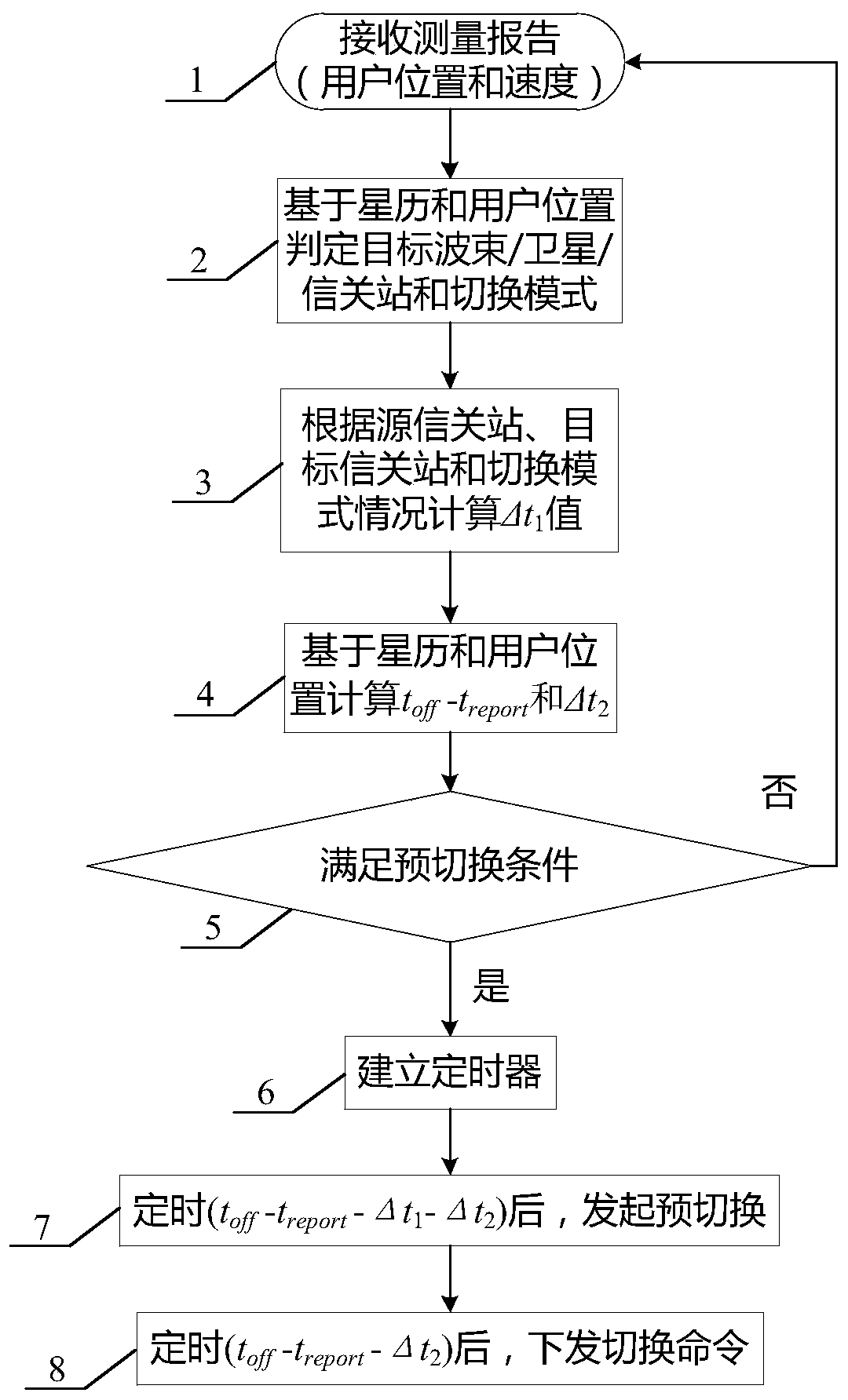
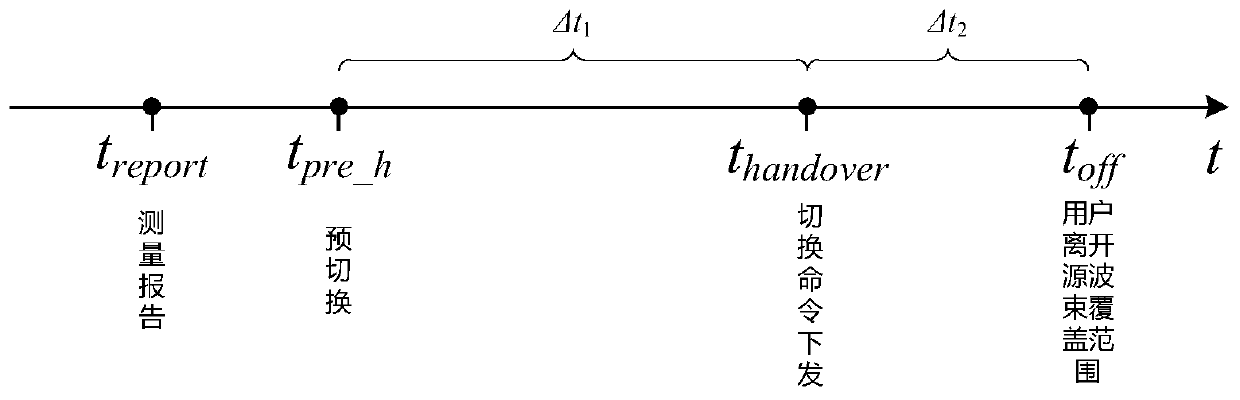
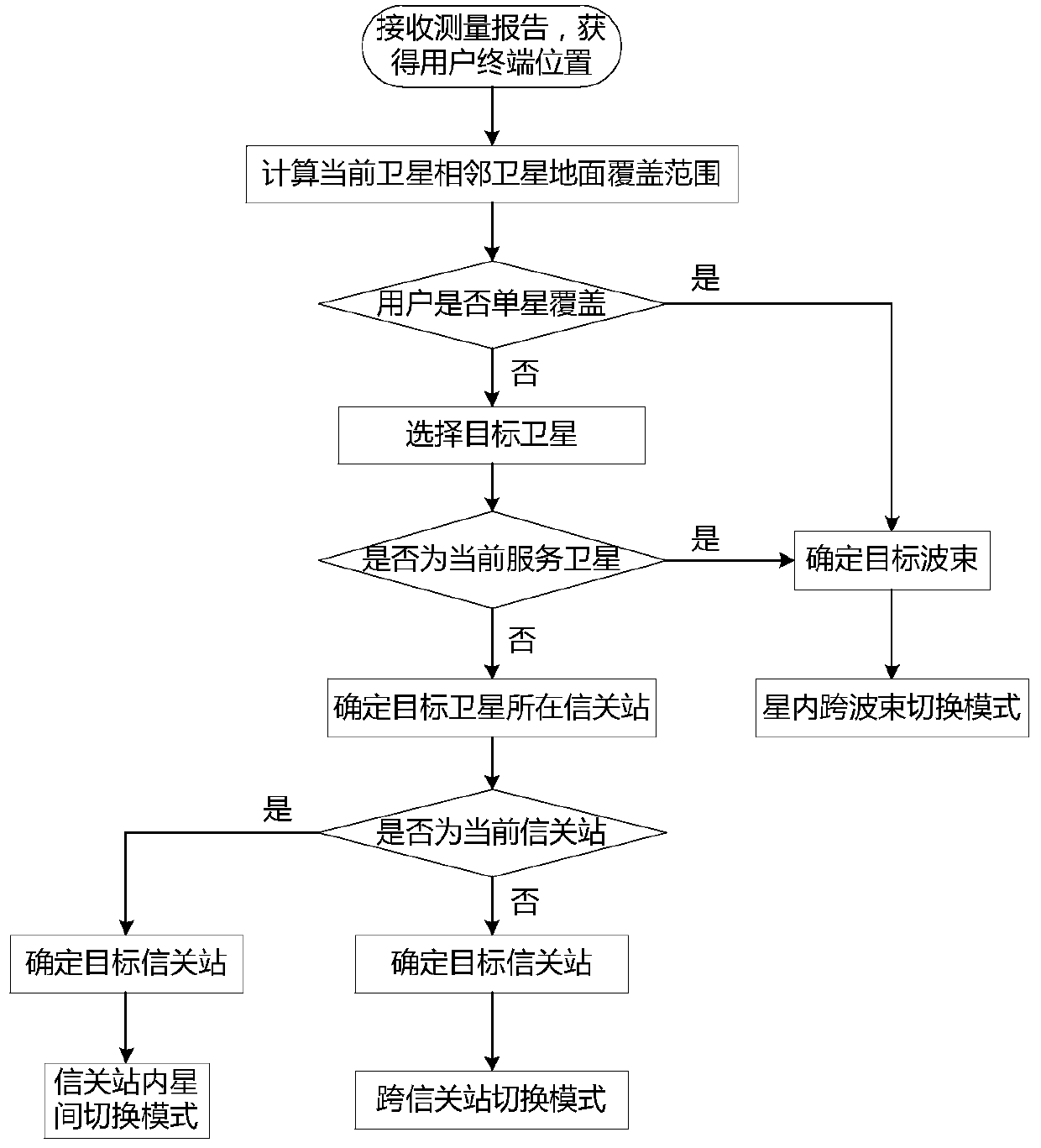
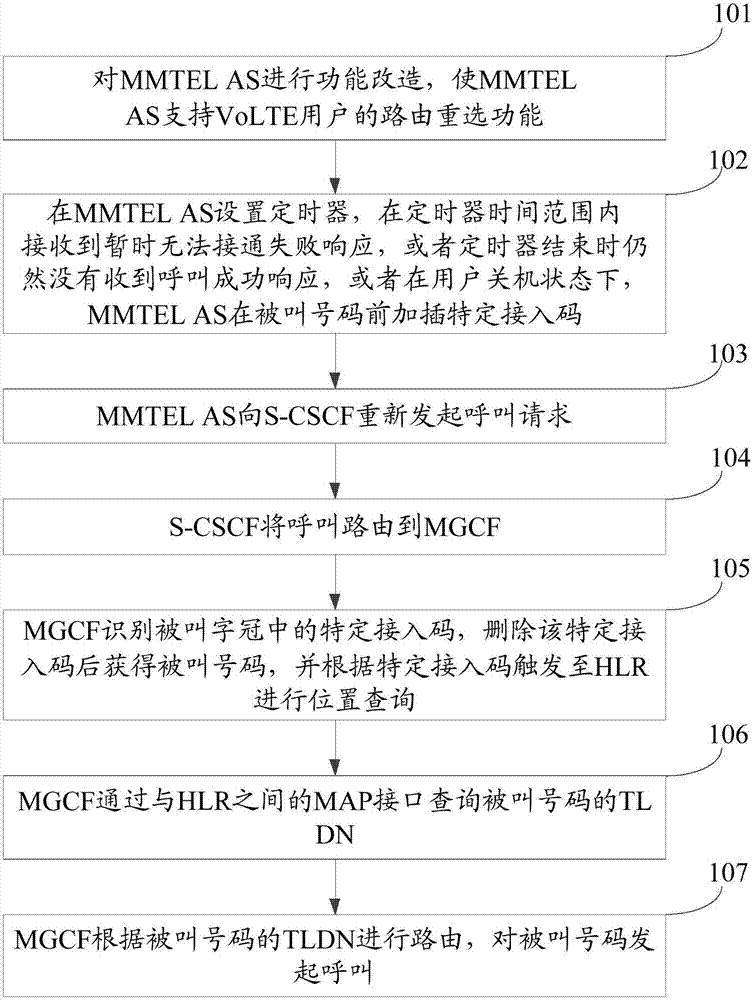
Timing trigger switching method based on ephemeris and user position calculation
ActiveCN110582094AFix switching issuesReduce interaction processRadio transmissionHigh level techniquesTelecommunicationsFrequency measurements
The invention discloses a timing trigger switching method based on ephemeris and user position calculation, and belongs to the field of low-orbit satellite communication. The working principle is as follows: (1) a gateway station receives a position and speed measurement report periodically sent by a user, (2) the gateway station calculates and judges a target wave beam / satellite / gateway station and a switching mode according to the ephemeris; (3) a delta t1 value is calculated according to the conditions of the source gateway station, the target gateway station and the switching mode, (4) a toff-treport value and a delta t2 value are calculated based on the ephemeris and the user position; (5) pre-switching judgment is carried out according to the calculated value; (6) if a pre-switchingcondition is met, a timer is established; (7), pre-switching is initiated by the gateway station according to the timing of the timer; and (8), a switching command is issued to a user by the gateway station after the timing of the timer (toff-treport-delta t1-delta t2). By means of the method, the low-orbit satellite system switching preparation stage depends on gateway station calculation, the terminal does not need to conduct neighbor cell / wave beam pilot frequency measurement, the switching problem of a small wave beam overlapping area is effectively solved, and meanwhile the method is widely applied to various scenes of the low-orbit satellite system.
Owner:成都天奥集团有限公司
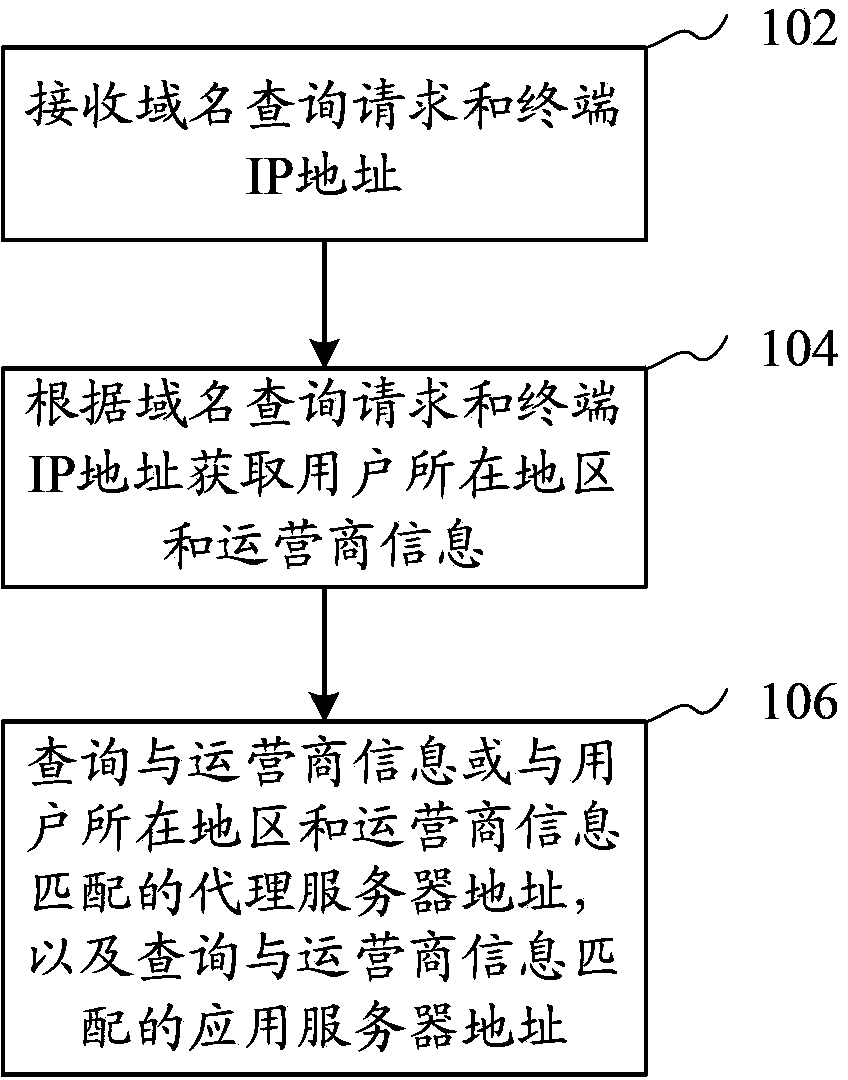
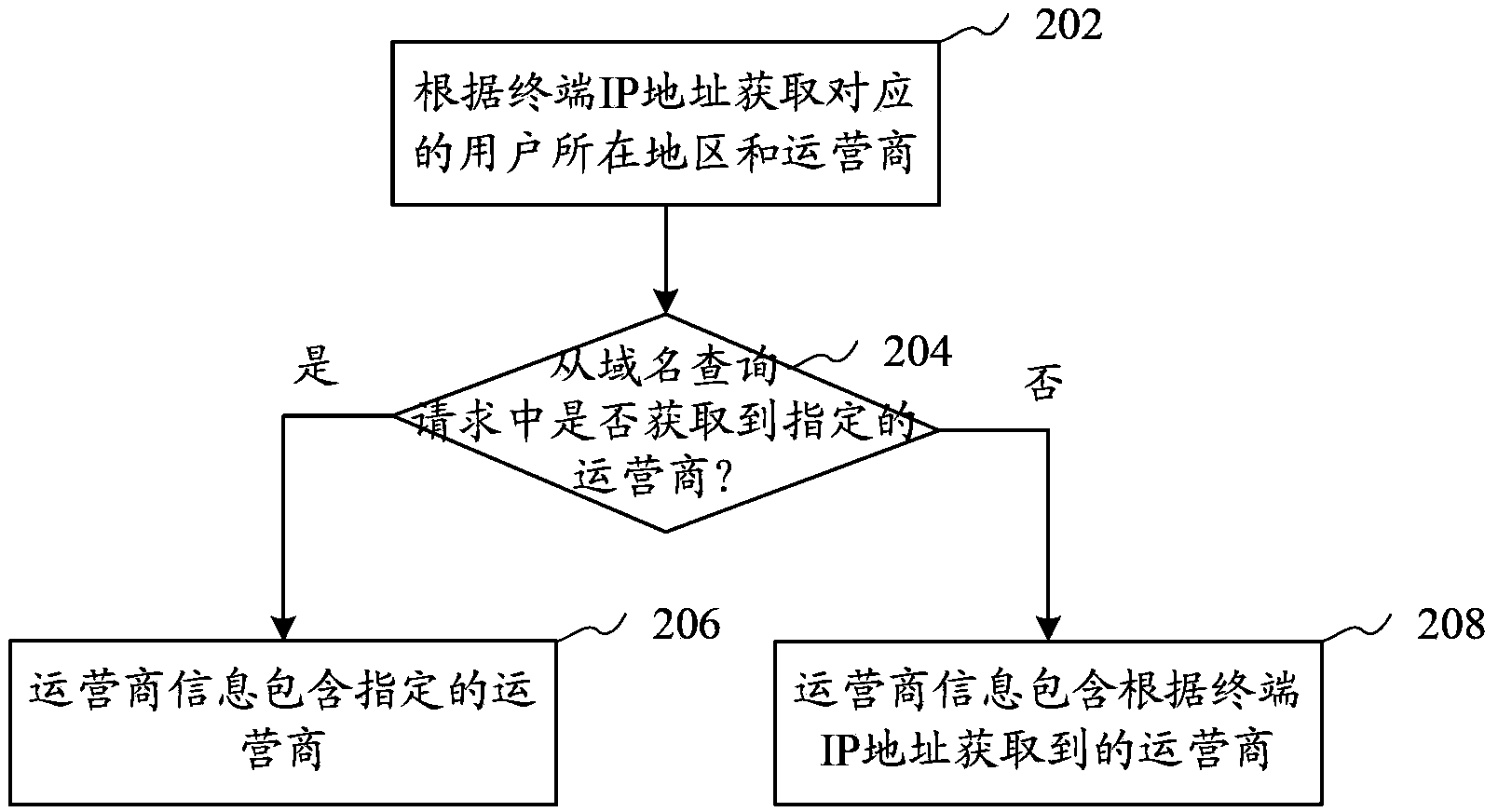
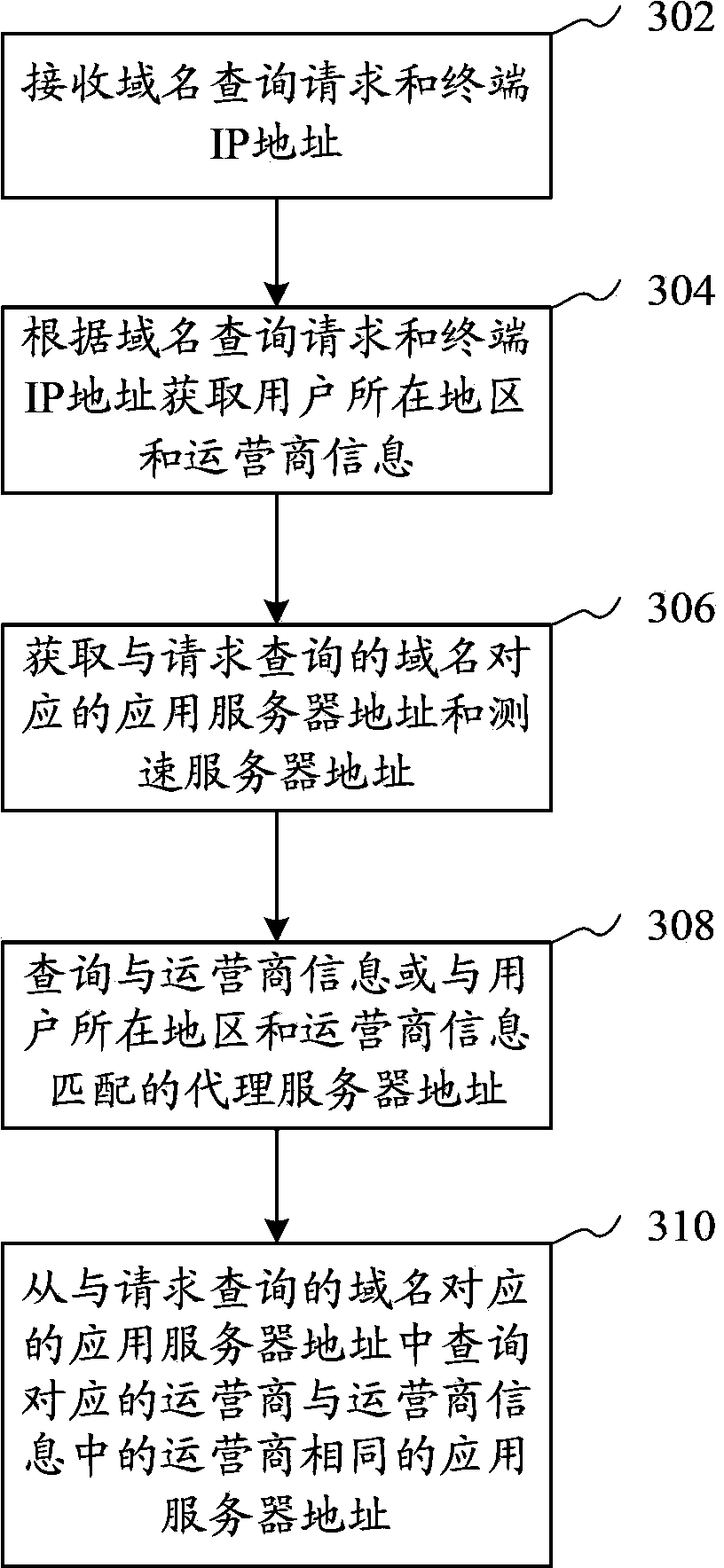
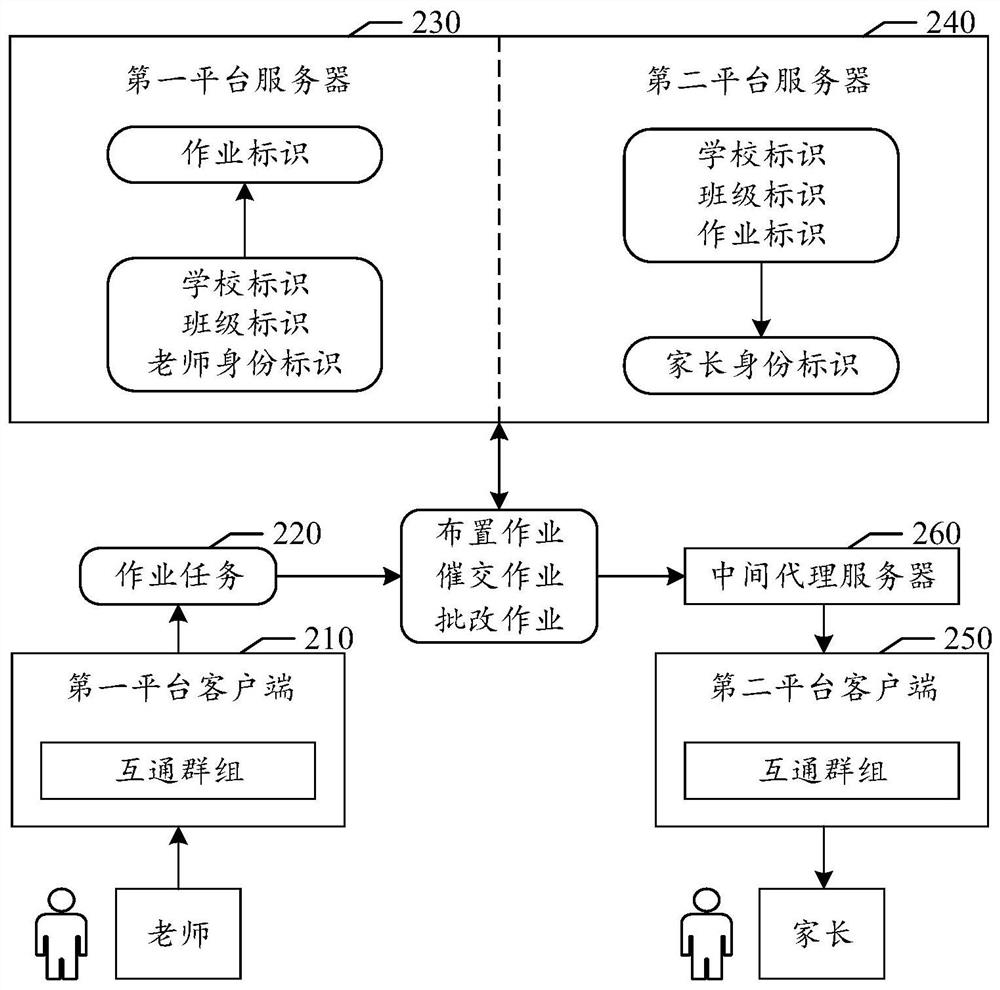
Domain name parsing method, domain name server, domain name access method, system and terminal
ActiveCN104253873AReduce interaction processImprove parsing speedTransmissionApplication serverService provider
The invention provides a domain name parsing method. The method comprises steps that: a domain name query request and a terminal IP address are received; a location region of a user and service provider information are acquired according to the domain name query request and the terminal IP address; an agency server address in matching with the service provider information or in matching with the location region of the user and the service provider information is queried, and an application server address in matching with the service provider information is further queried. The method can accelerate the domain name parsing speed and the domain name access speed. The invention further provides a domain name server, a domain name access method, a system and a terminal.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
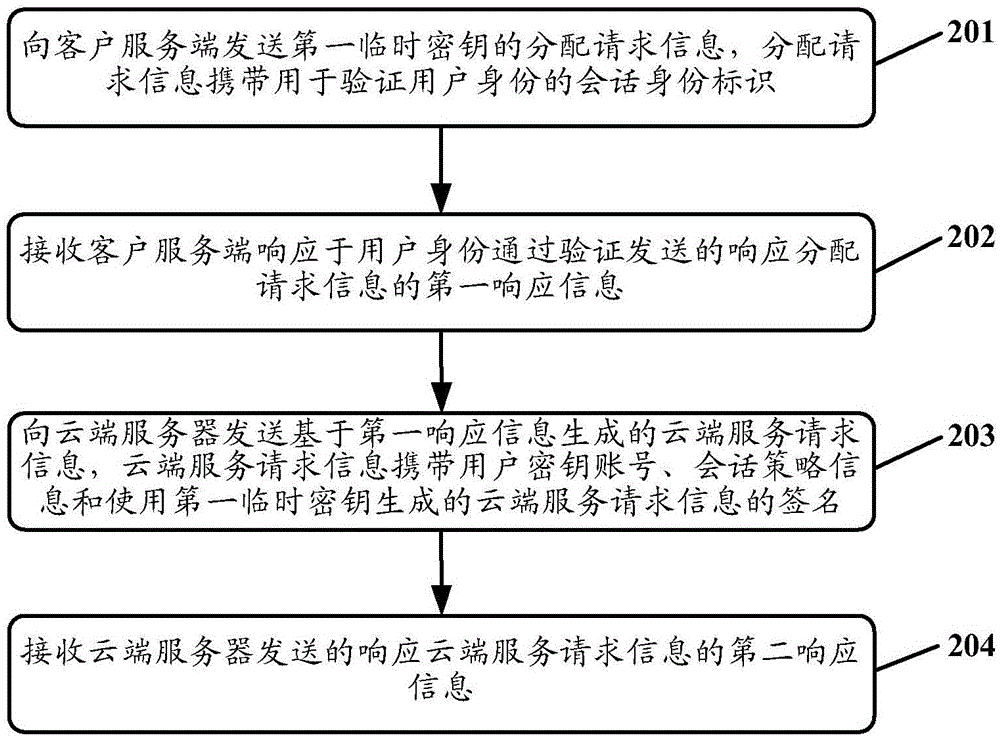
Authentication method and authentication system
ActiveCN105007279AReduce certification pressureReduce interaction processSecuring communicationAuthentication systemEphemeral key
The application discloses an authentication method and an authentication system. The authentication method comprises the steps that: a client transmits assignment request information of a first temporary key to a client server; the client server generates first responding information comprising a user key account, the first temporary key and conversation policy information and transmits to the client after checking the assignment request information; the client transmits cloud service request information generated on base of the first responding information to the cloud server;the cloud service request information carries the user key account, the conversation policy information and a signature of the cloud service request information generated by using the first temporary key; the signature of the cloud service request information is authenticated on base of the user key account and the conversation policy information via the cloud server; after authenticating, second responding information responding to the cloud service request information is transmitted to the client. According to the implementation mode of the application, the authentication method reduces the interactive flow between the client server and the cloud server and debases the authentication press of the cloud server.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Encryption method and system of mobile instant message
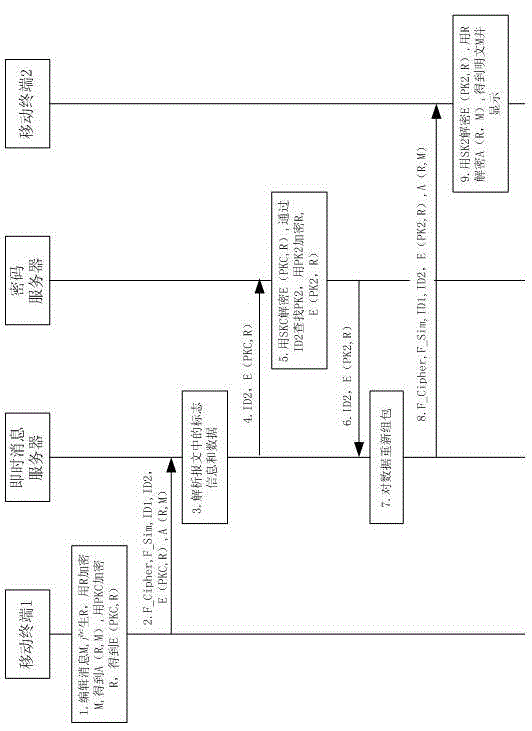
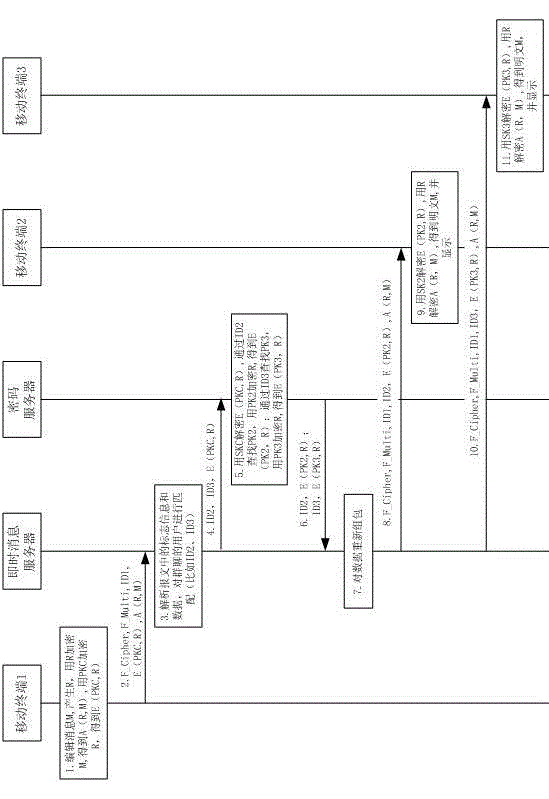
ActiveCN103338437AEffective encryptionNo changes to the communication flowMessaging/mailboxes/announcementsSecurity arrangementPasswordConfidentiality
The invention belongs to the technical field of instant messages and discloses an encryption method of a mobile instant message. The encryption method comprises the steps that the instant message is encrypted by a random number R; the random number R is encrypted by a public key of a password server simultaneously; the password server decrypts the random number R with a private key of the password server and encrypts the random number R with a public key of a mobile terminal of a receiver; the instant message and the random number are sent to the mobile terminal of the receiver; the mobile terminal of the receiver decrypts the random number R with a private key of the mobile terminal, and then decrypts the instant message with R; and the instant message is received and displayed. The instant message is encrypted by the random number R, and the private key R is encrypted during transmission. Confidentiality of the instant message is strengthened. Meanwhile, all password processing such as matching of a user identity with a password, and password conversion are performed on a server with higher processing capacity, so that the terminal burden is reduced, and the purposes of ensuring message transmission security and reducing the computation of the terminal are achieved. In addition, an additional communication flow is not required to be added between the terminal and the server when the encrypted message is transmitted, so that the limited wireless broadband resource is saved.
Owner:成都三零瑞通移动通信有限公司
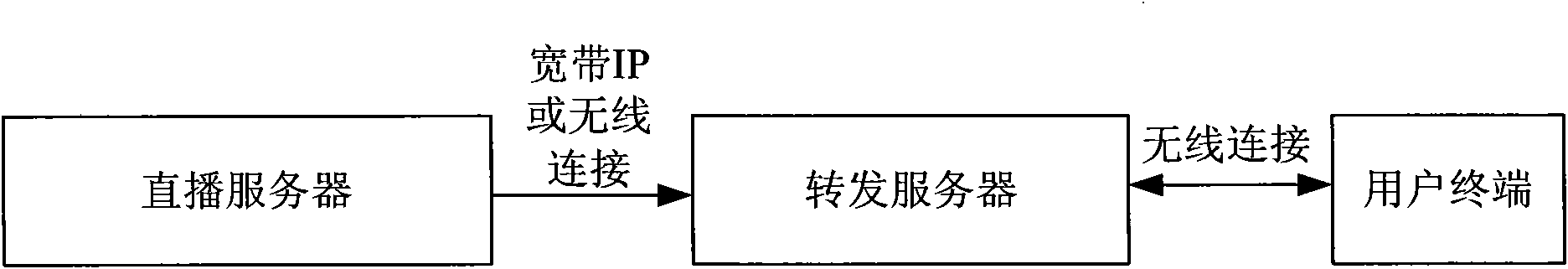
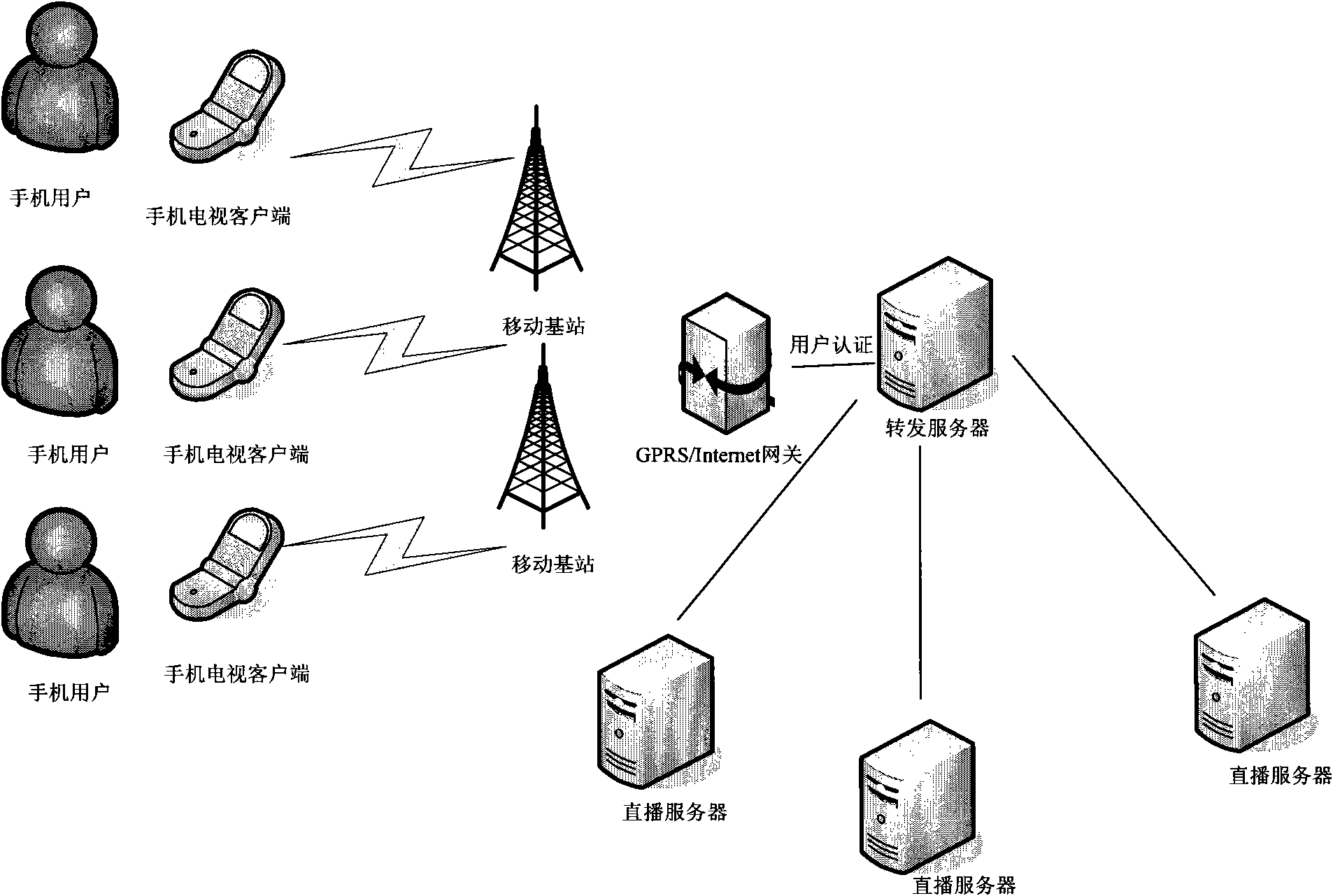
Wireless television live broadcasting system and live broadcasting method thereof
InactiveCN102404646ASmooth viewingReduce interaction processTransmissionSelective content distributionAccess networkData file
The invention discloses a wireless television live broadcasting system and a live broadcasting method thereof. The wireless television live broadcasting system mainly comprises a live broadcasting server, a forwarding server and a user terminal, wherein the live broadcasting server is used for converting live broadcasting information into streaming media data and sending the streaming media data; the forwarding server is used for receiving the streaming media data sent by the live broadcasting server and forwarding the streaming media data according to the HTTP (Hyper Text Transport Protocol); and the user terminal is used for sending an HTTP request to the forwarding server and watching live television according to the received streaming media data after being connected with the forwarding server through wireless network. According to the television live broadcasting system and the live broadcasting method, the forwarding server sends streaming media data to the user terminal through the HTTP, so that the defect can be avoided that the traditional broadband IP access network adopts the RTSP (Real Time Streaming Protocol) / RTP (Real-time Transport Protocol) to transmit multimedia data, so that the number of file headers is large, and signalling interaction is cumbersome.
Owner:SUZHOUSNGJIA INFORMATION TECH
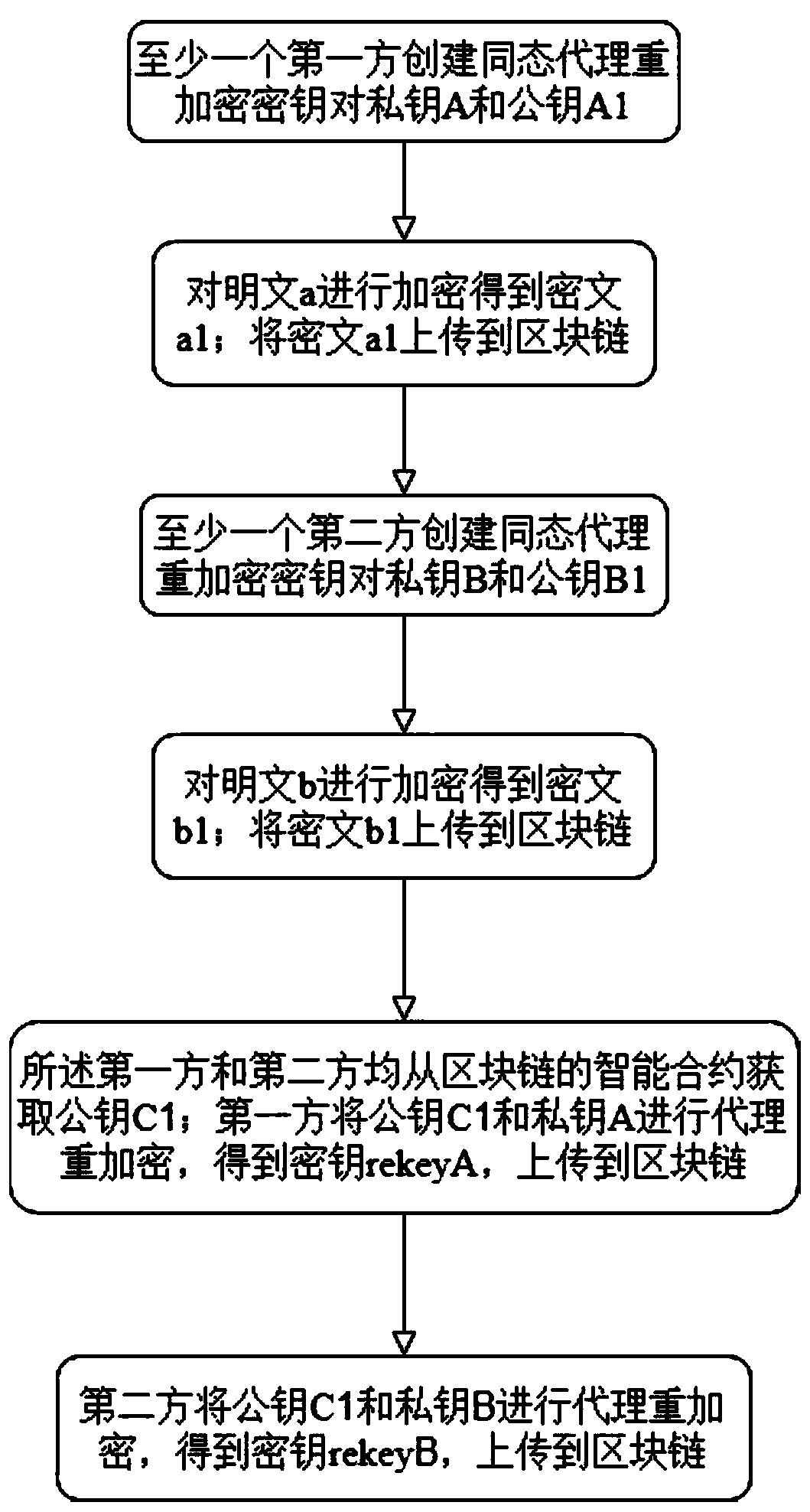
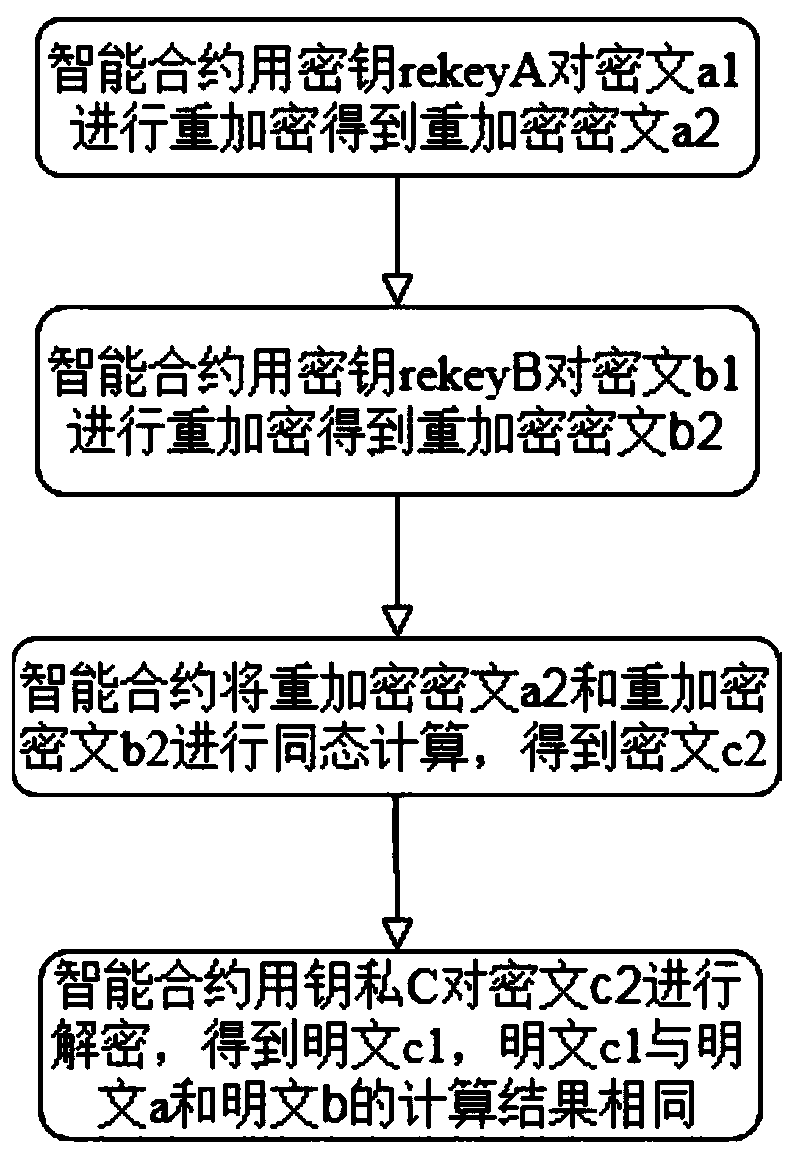
Blockchain data sharing encryption and decryption method, equipment, and storage medium
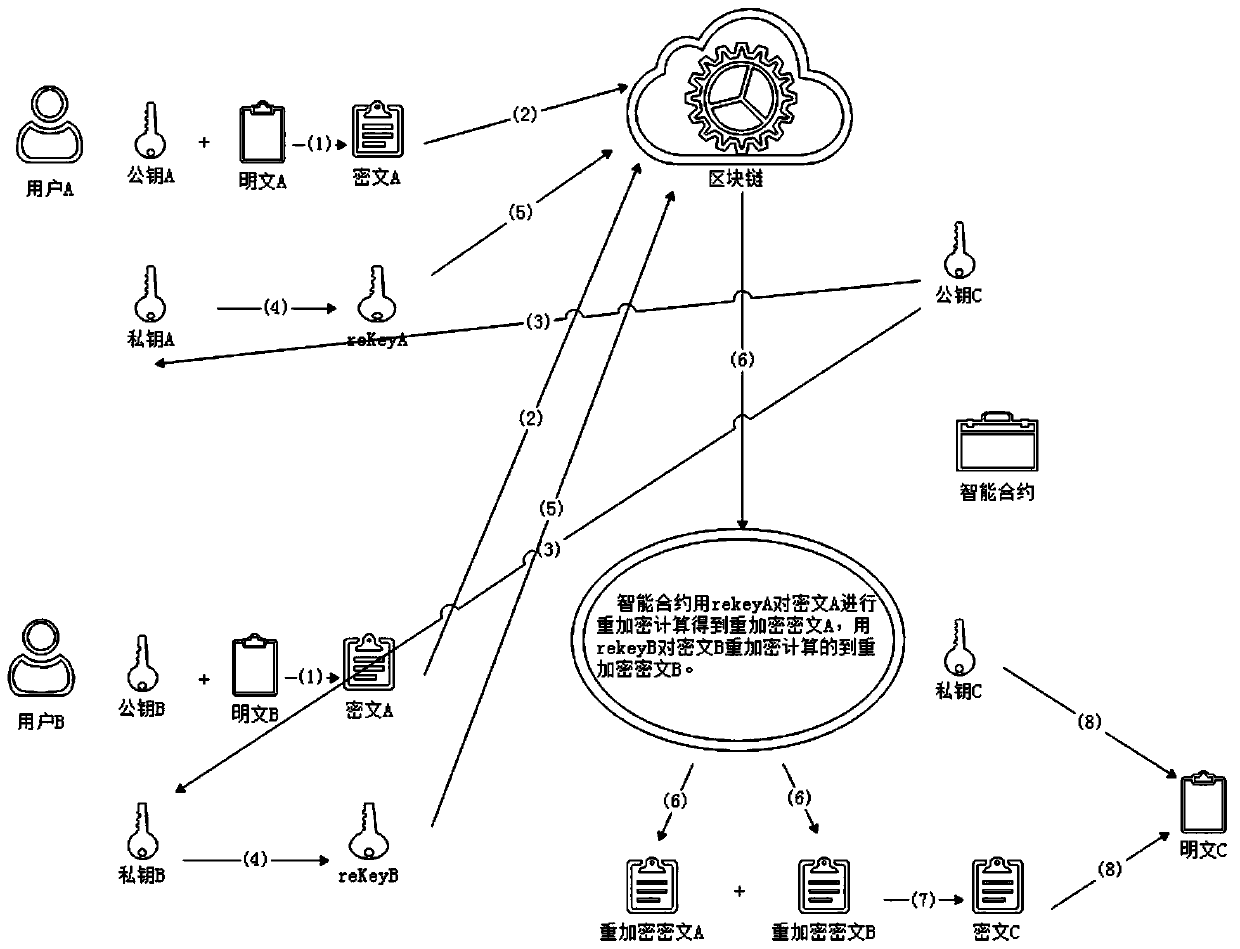
ActiveCN111385301AReduce interaction processImprove operational efficiencyCommunication with homomorphic encryptionPlaintextCiphertext
The invention discloses a blockchain data sharing encryption and decryption method, equipment and a storage medium, which belong to the technical field of blockchains. The blockchain data sharing encryption and decryption method comprises the steps of: creating a homomorphic proxy re-encryption key pair private key A and public key A1 by at least one first party; encrypting a plaintext a to obtaina ciphertext a1; uploading the ciphertext a1 to a blockchain; creating a homomorphic proxy re-encryption key pair private key B and public key B1 by at least one second party; encrypting a plaintextb to obtain a ciphertext b1; uploading the ciphertext b1 to the blockchain; acquiring a public key C1 from an intelligent contract of the blockchain by the first party and the second party; performingproxy re-encryption on the public key C1 and the private key A to obtain a secret key rekey A by the first party, and uploading the secret key rekey A to the blockchain; and performing proxy re-encryption on the public key C1 and the private key B to obtain a secret key rekey B by the second party, and uploading the secret key rekey B to the blockchain, wherein the intelligent contract creates akey pair private C and public key C1 through homomorphic encryption. The blockchain data sharing encryption and decryption method solves the homomorphic problem of conducting safety calculation basedon private data of the blockchain, reduces the interaction process between users and the blockchain and between the users, moves some operations under the chain to the chain, and makes calculation more credible.
Owner:湖南智慧政务区块链科技有限公司
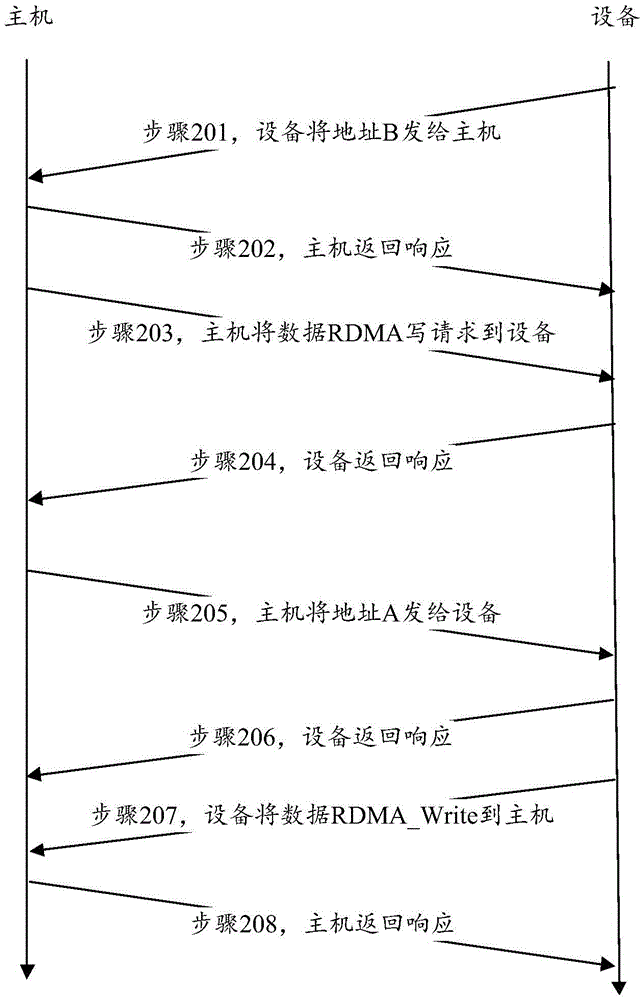
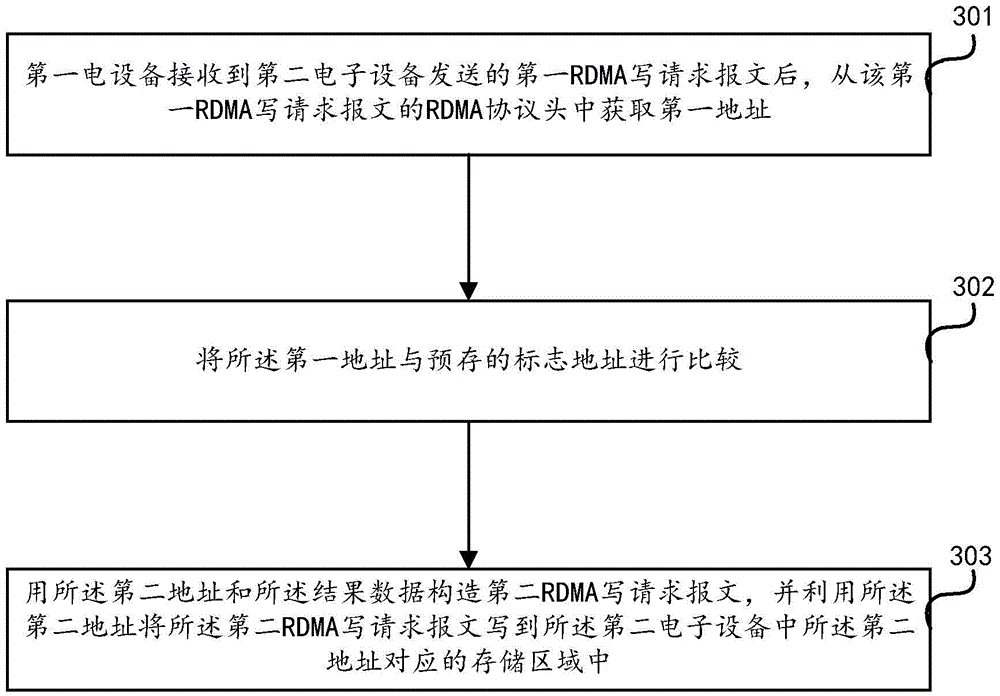
Method and device for remote direct memory access
ActiveCN105472023ALower latencyReduce interaction processDigital computer detailsTransmissionDirect memory accessRemote direct memory access
The invention discloses a method and device for remote direct memory access. The method is applied to first electronic equipment, and a remote direct memory access RDMA connection is established between the first electronic equipment and second electronic equipment; the method comprises the following steps: after receiving a first RDMA write request message transmitted by the second electronic equipment by the first electronic equipment through the RDMA connection, acquiring a first address from an RDMA protocol head of the first RDMA write request message; and comparing the first address with a pre-stored mark address, if the first address is the same as the mark address, then acquiring a second address from a protocol extension header of the first RDMA write request message, and using the second address to write the processed first RDMA write request message to a storage region corresponding to the second address in the second electronic equipment. The method and device for the remote direct memory access provided by the invention solve the problems in the prior art that partial invalid interaction is caused by using the standard RDMA, and delay of transmission bandwidth resources and data interaction is wasted
Owner:HUAWEI TECH CO LTD
Method and system for processing multi-media value-added business information and utilized gate equipment
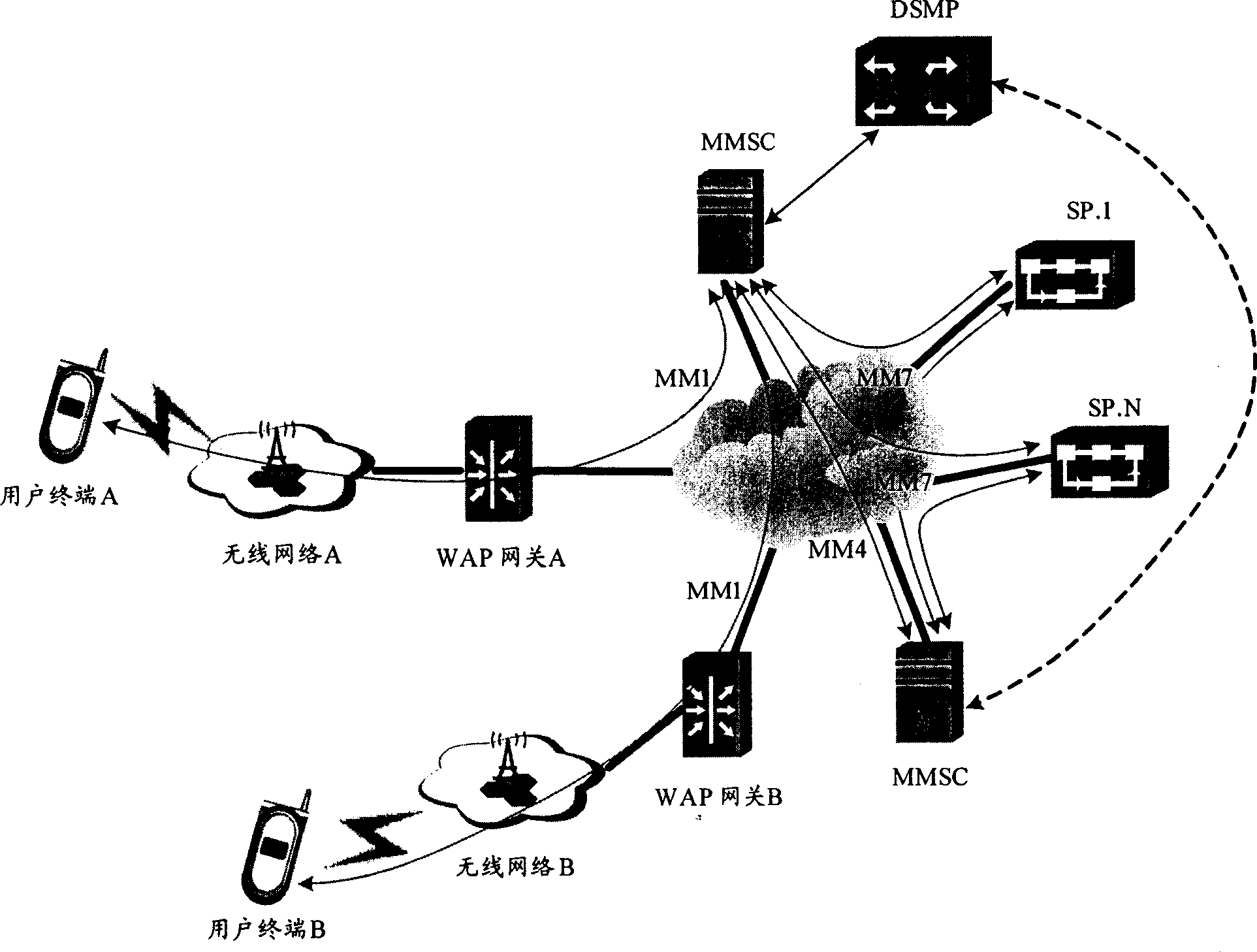
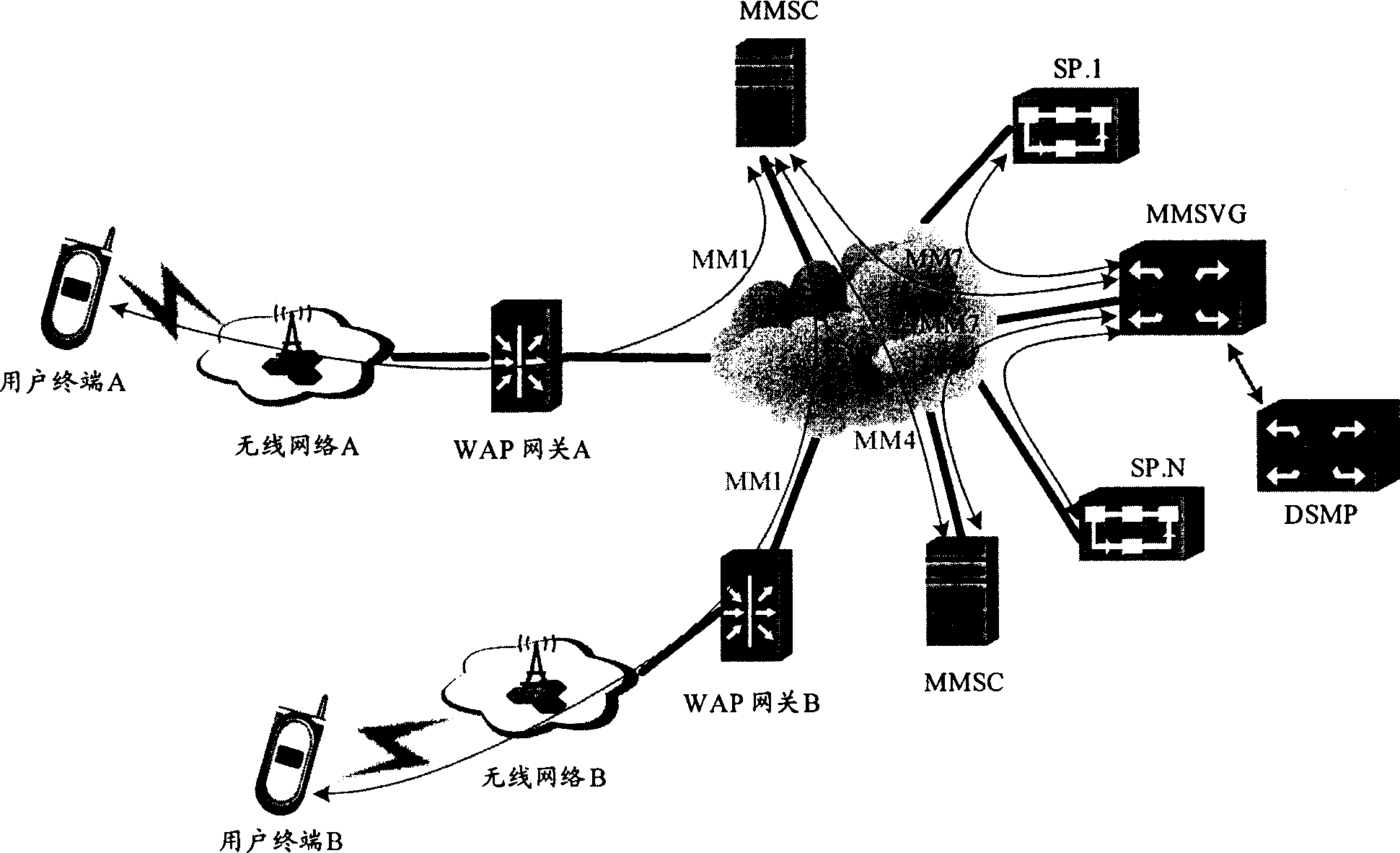
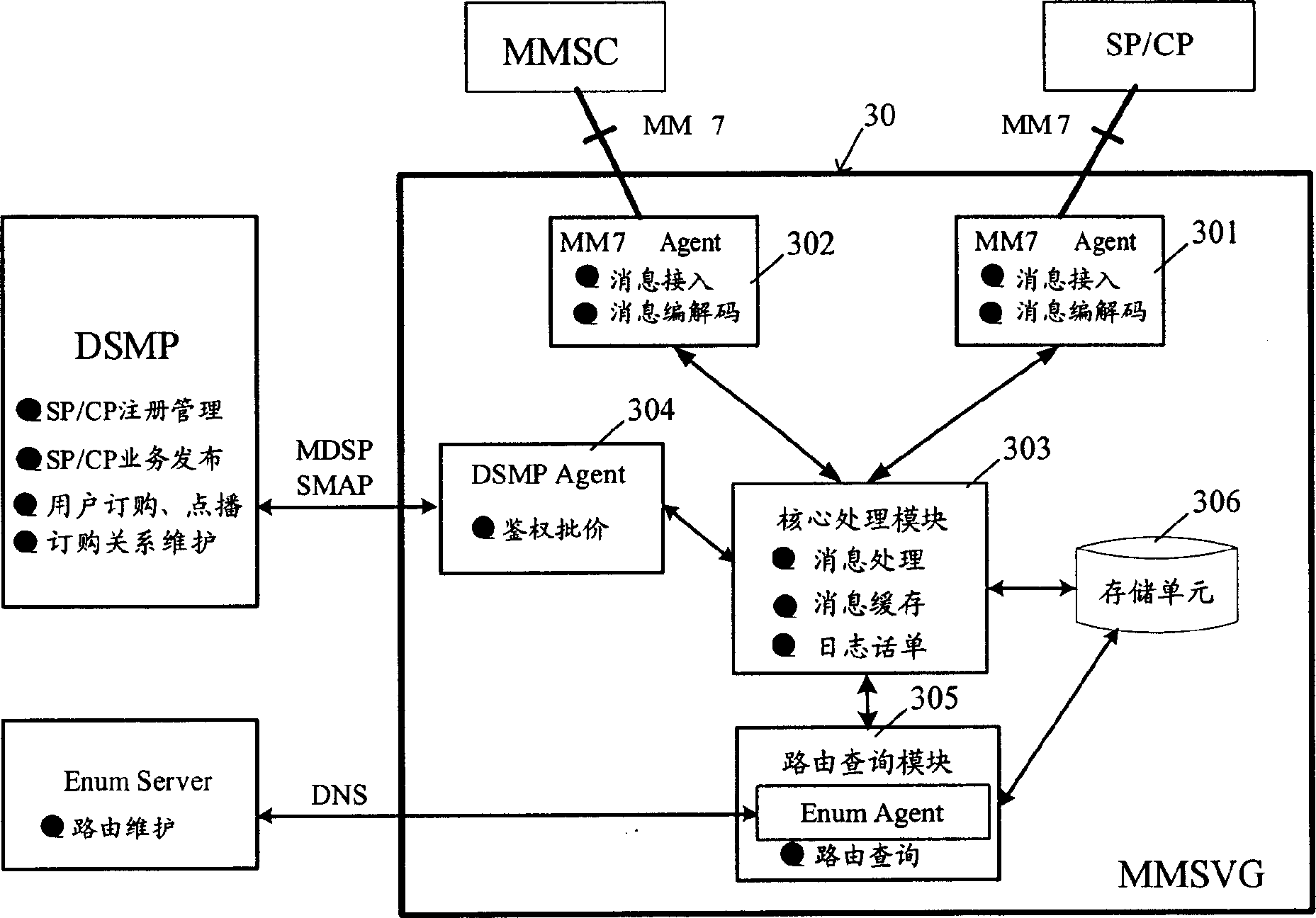
ActiveCN1889535AReduce development costsReduce maintenance costsData representation error detection/correctionPulse modulation television signal transmissionComputer moduleHandling system
A method for processing multimedia value-added service message utilizes gateway device to retransmit all interworking message between SP and MMSC. The system for realizing said method comprises multimedia value-added service server, multimedia message center and gateway device. The said gateway device consists of MM7 protocol interface for carrying out information interworking between SP and MMSC, storage module for storing SP attribute information query module for making route query and core processing module for calling said module and interface to finalize right certification and message down-send treatment.
Owner:HUAWEI TECH CO LTD
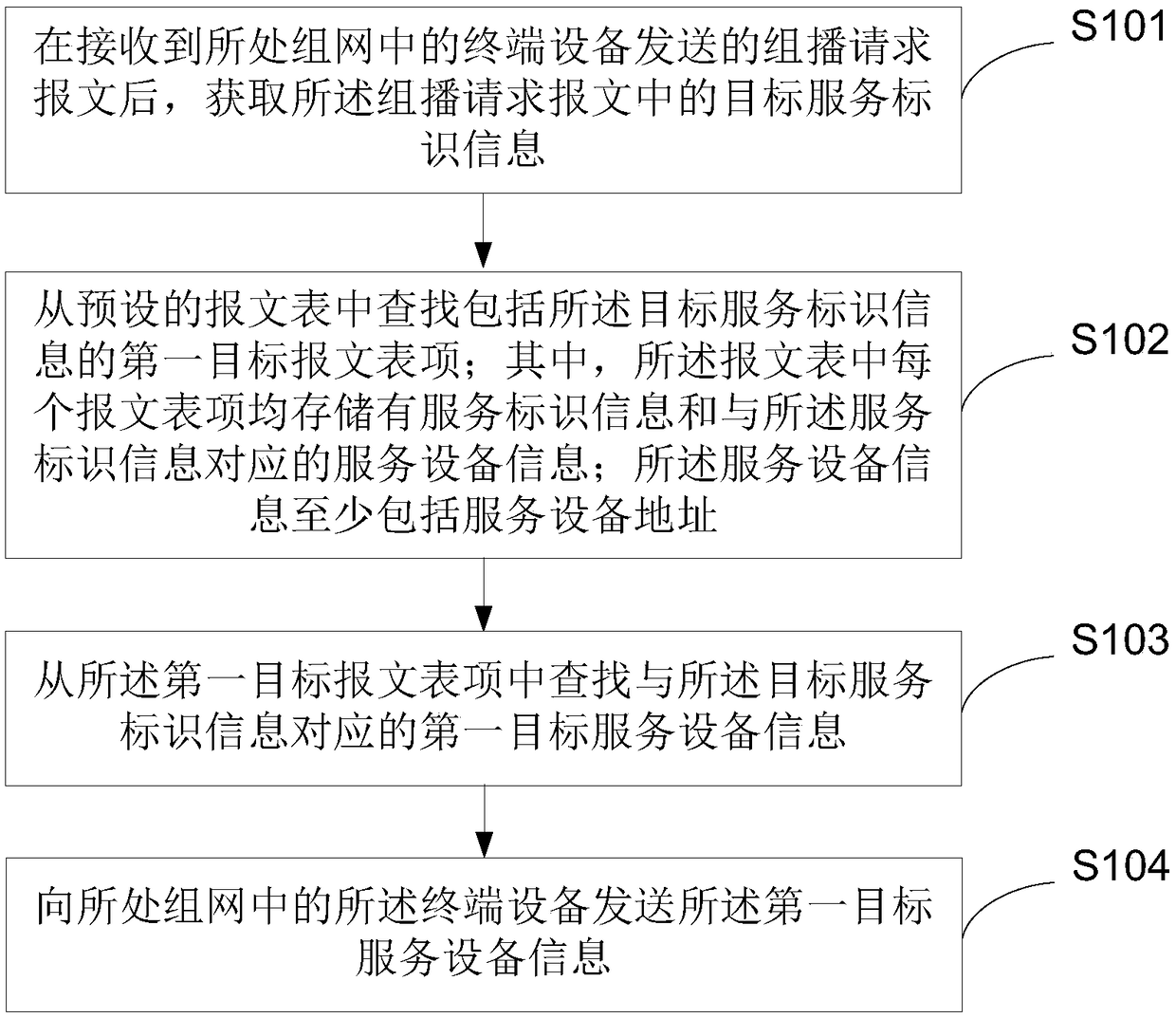
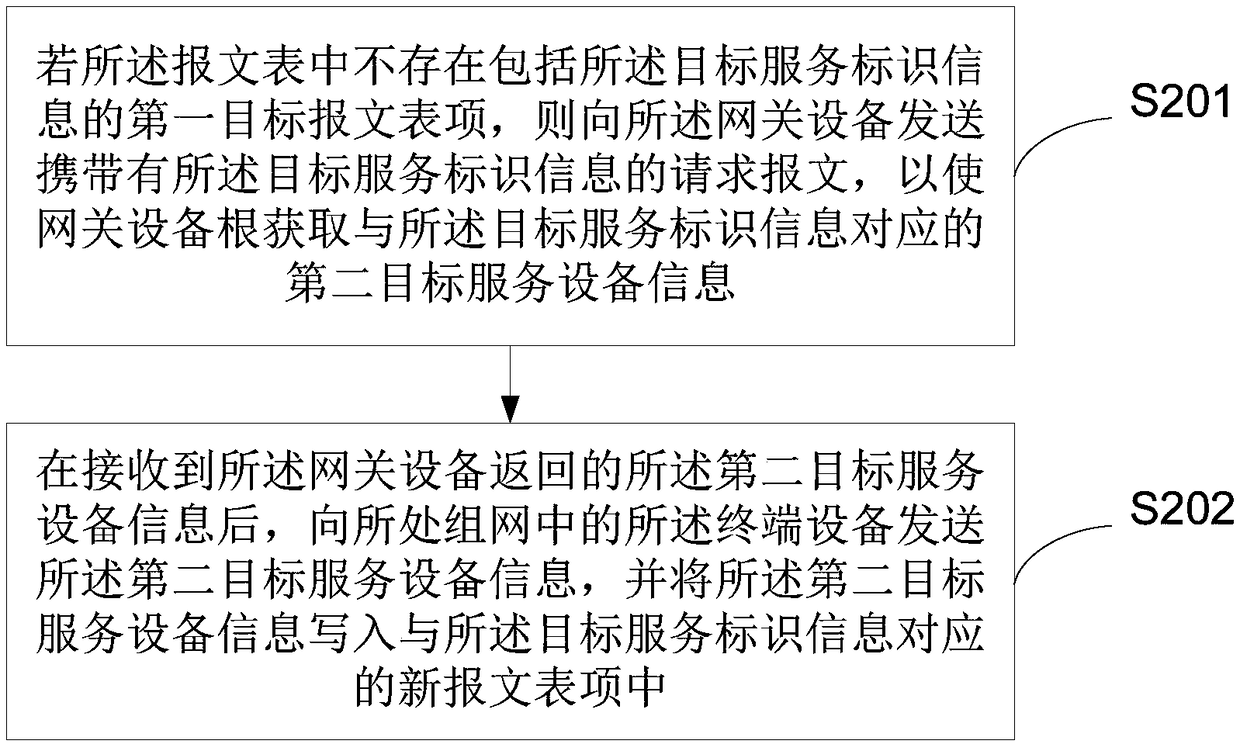
Processing method and device of service request in network
ActiveCN109379291AReduce interaction processRelieve pressureNetworks interconnectionTerminal equipmentRepeater
The application provides a processing method and device of a service request in a network, relates to the field of communication technology, and is applied to a repeater in the network. The method comprises the steps of acquiring target service identification information in a multicast request message after the multicast request message sent by a terminal device in the network is received, lookingup a first target message entry containing the target service identification information from a presetting message table, looking up first target service device information corresponding to the target service identification information from the first target message entry, and sending the first target service device information to the terminal device in the network. The first target service deviceinformation at least includes a first target service device address. Thus, the multicast request message transmitted to the gateway device by the repeater is reduced, and even the multicast request message is unnecessary to be transmitted; the interactive process of the message is reduced; and at the same time, the pressure of the gateway device is reduced and the business processing efficiency is improved.
Owner:NEW H3C TECH CO LTD
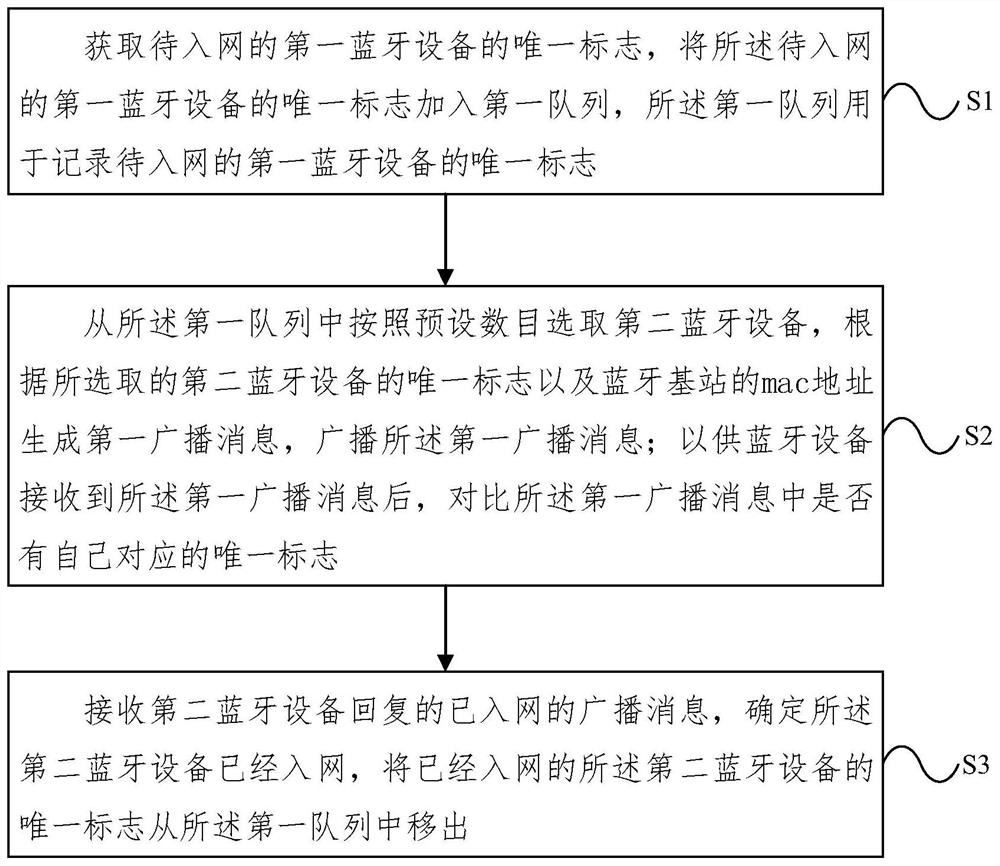
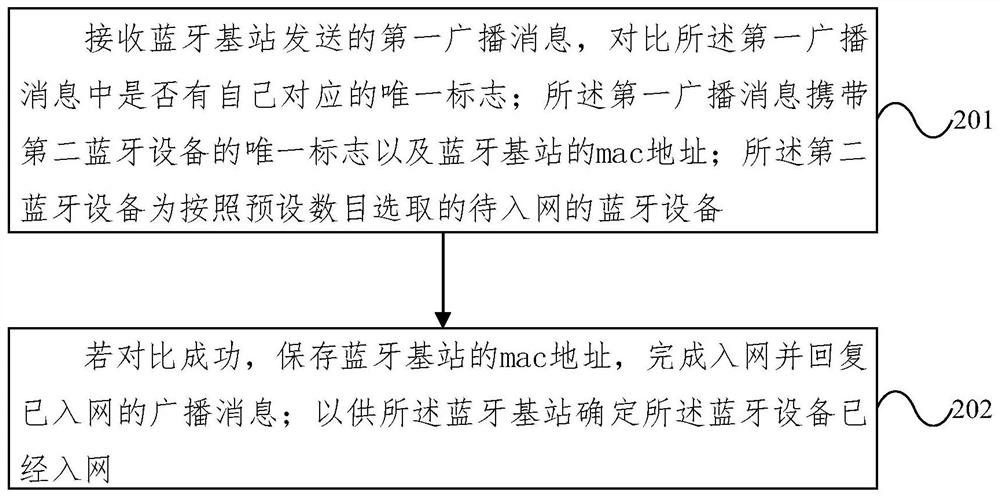
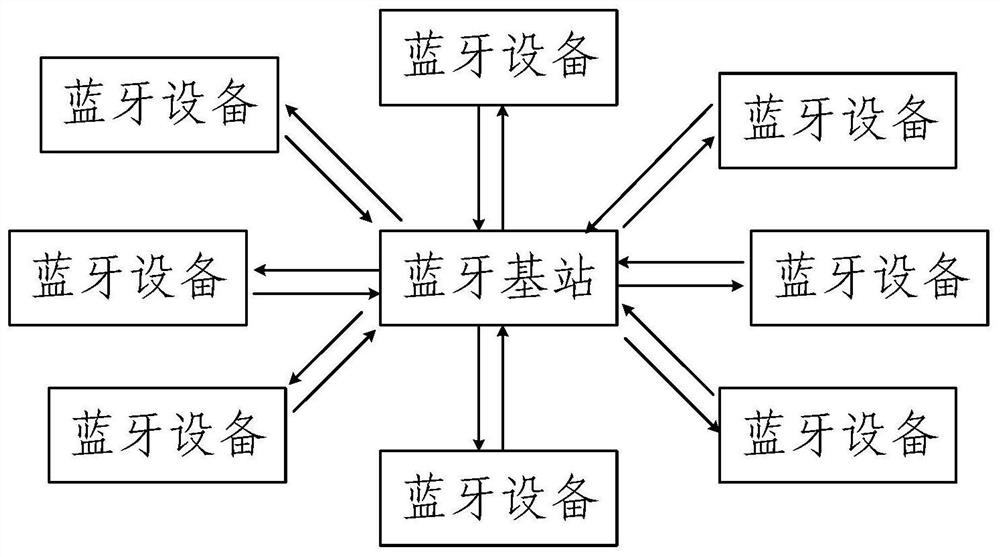
Bluetooth networking method and system
PendingCN111885562AReduce transfer volumeReduce interaction processNetwork topologiesConnection managementData transmissionUnique identifier
The embodiment of the invention provides a Bluetooth networking method and system, and the method comprises the steps: obtaining a unique mark of to-be-networked first Bluetooth equipment, adding theunique mark of the to-be-networked first Bluetooth equipment into a first queue, and enabling the first queue to be used for recording the unique mark of the to-be-networked first Bluetooth equipment;selecting a second Bluetooth device from the first queue according to a preset number, generating a first broadcast message according to the unique identifier of the selected second Bluetooth deviceand the mac address of the Bluetooth base station, and broadcasting the first broadcast message, so that after receiving the first broadcast message, the Bluetooth device compares whether a unique mark corresponding to the Bluetooth device exists in the first broadcast message or not; receiving a network-accessed broadcast message replied by the second Bluetooth device, determining that the secondBluetooth device accesses the network, and moving the unique identifier of the network-accessed second Bluetooth device out of the first queue. The complexity of the processing flow of the Bluetoothdevice can be reduced, and the real-time performance of Bluetooth data transmission can be improved.
Owner:ROUTON ELECTRONICS CO LTD
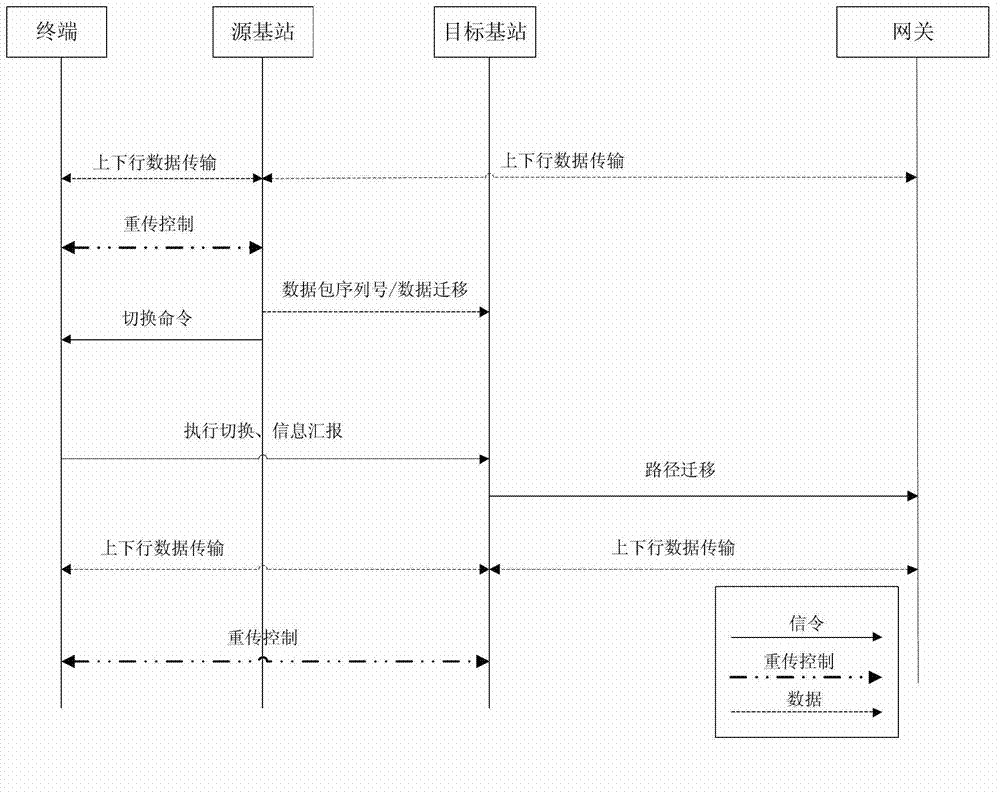
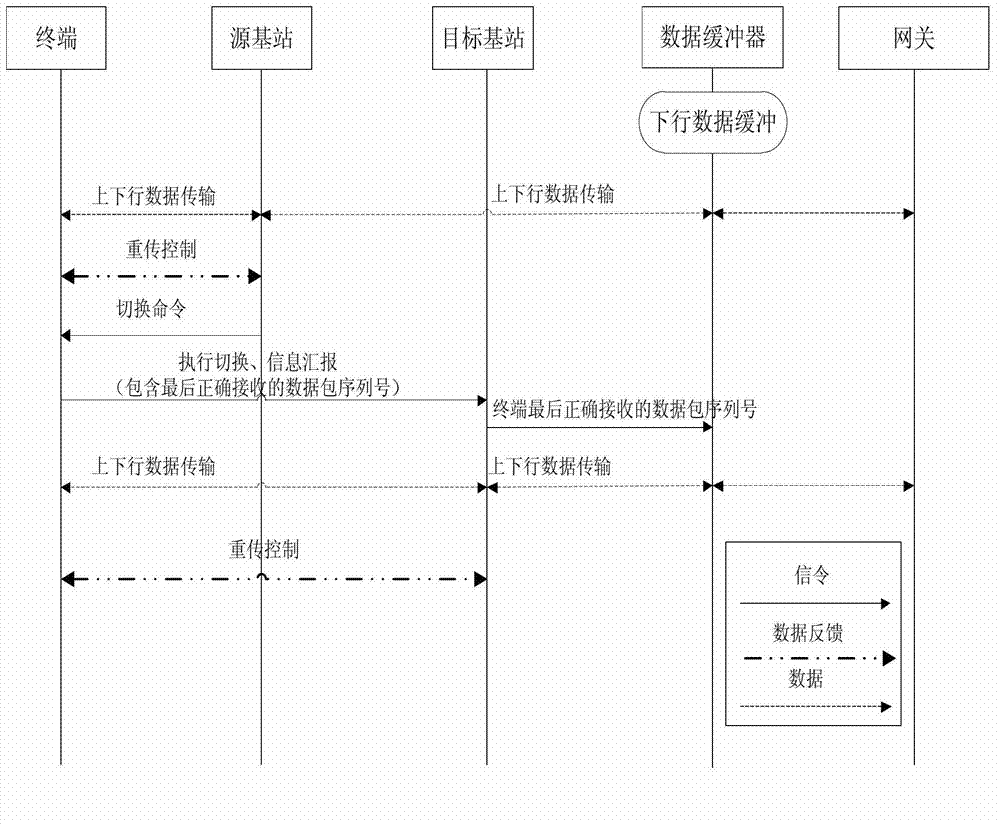
Inter-base station seamless handover method for terminal equipment in wireless communication system
ActiveCN103118403AReduce interaction processSolve the lossError preventionWireless communicationData bufferData transmission
The invention relates to an inter-base station seamless handover method for terminal equipment in a wireless communication system. The inter-base station seamless handover method includes: adding a data buffer entity on base stations of the wireless communication system, wherein a plurality of base stations correspond to one data buffer entity; for a downstream data communication process transmitted to a terminal at a network side, by the aid of the data buffer entity, adding sequence number information to downstream data packages transmitted to the terminal and directly transmitting the downstream data packages to the base station where the terminal is positioned, and continuously backing up the sequence number information added downstream data packages in a buffering area in the data buffer entity. By the aid of the inter-base station seamless handover method, a large number of signaling interaction processes are reduced, signaling, data transmission and receiving processes are simplified, and abnormal errors are not prone to generating.
Owner:北京久华信信息技术有限公司
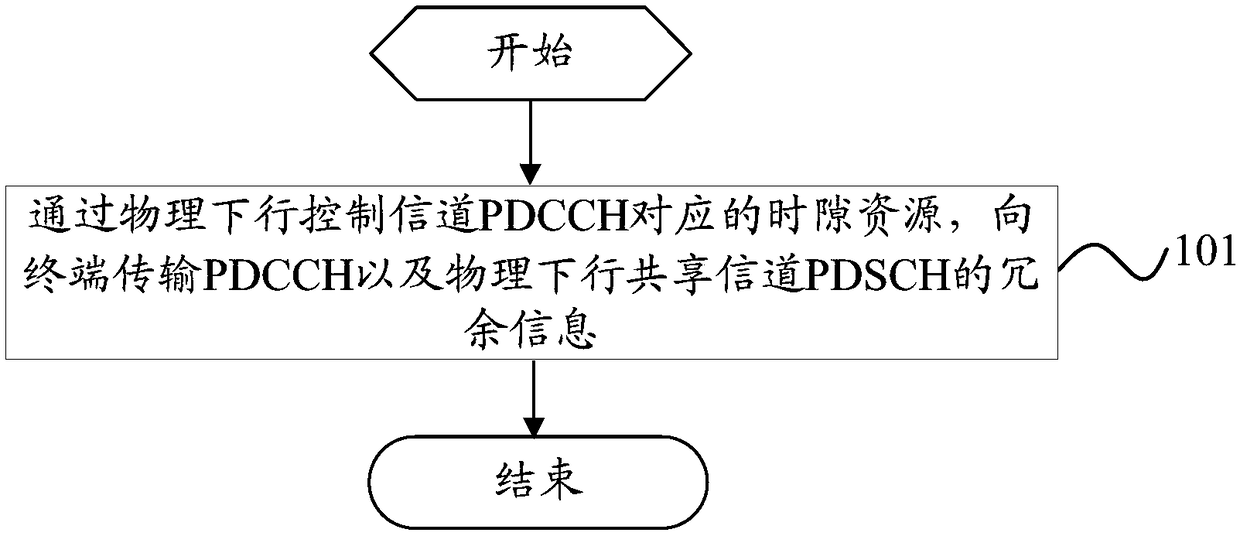
Data transmission method, base station and terminal
ActiveCN108809547AReduce interaction processSave signaling resourcesError preventionSignal allocationData transmissionControl channel
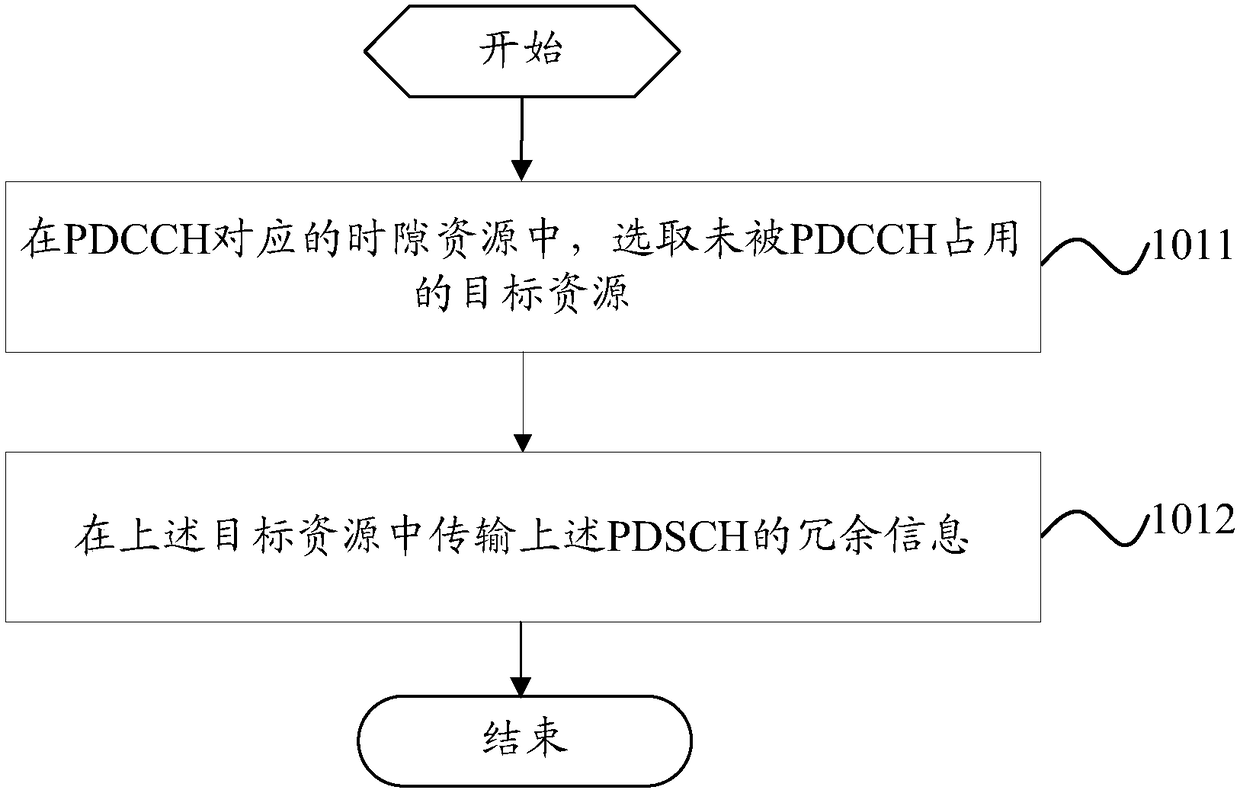
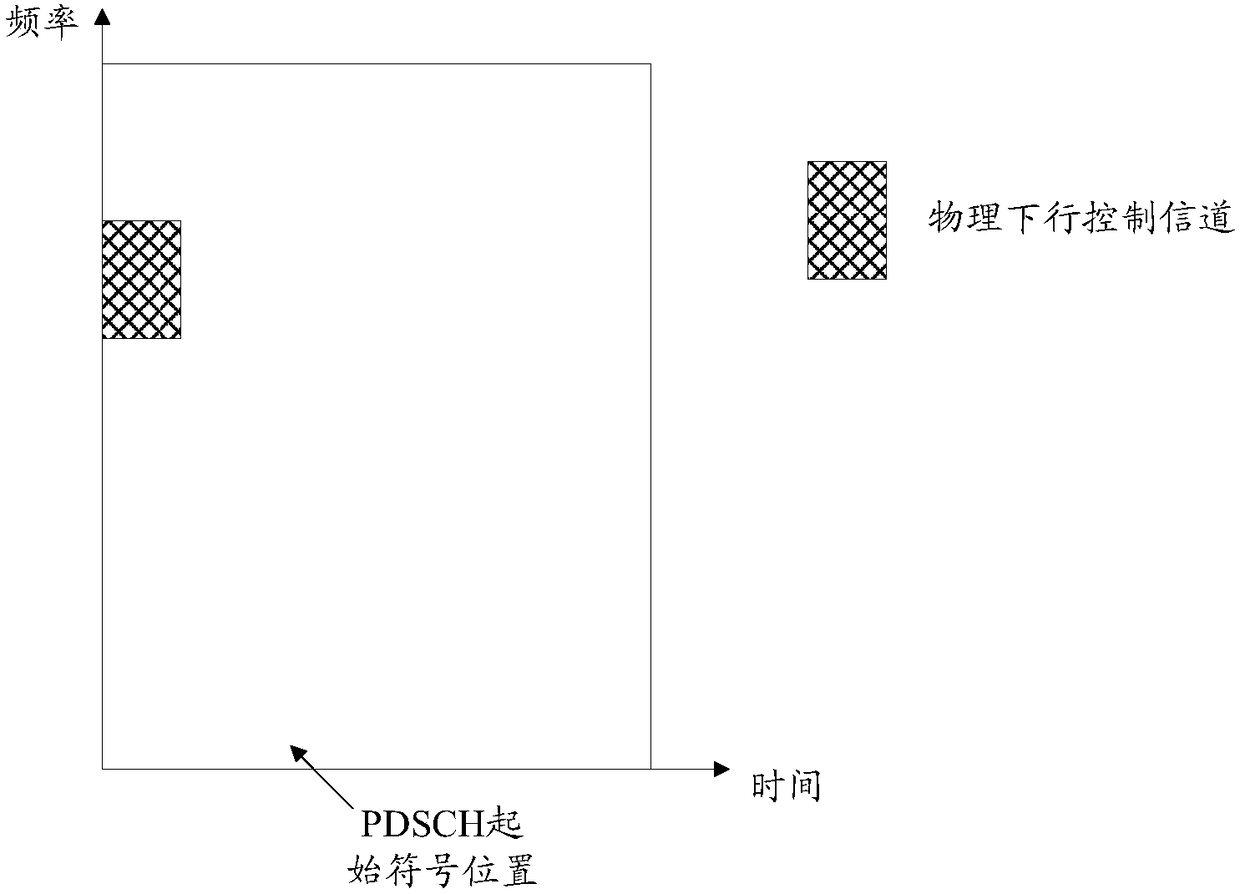
The invention provides a data transmission method, a base station and a terminal. The problem that the resource is wasted since partial resource is unutilized by the PDCCH, and the system signaling load is increased since the decoding is performed again by acquiring the redundancy information through retransmission when the data transmission is failed in the PDCCH transmission resource are solved.The data transmission method comprises the step of transmitting redundancy information of the PDCCH and physical downlink shared channel PDSCH to the terminal through the time slot resource corresponding to the physical downlink control channel PDCCH. The interaction process between the base station and the terminal is reduced since the terminal is unnecessary to acquire the redundancy information through the retransmission process, the signaling resource is saved, and the utilization rate of the transmission resource of the PDCCH is improved at the same time.
Owner:VIVO MOBILE COMM CO LTD
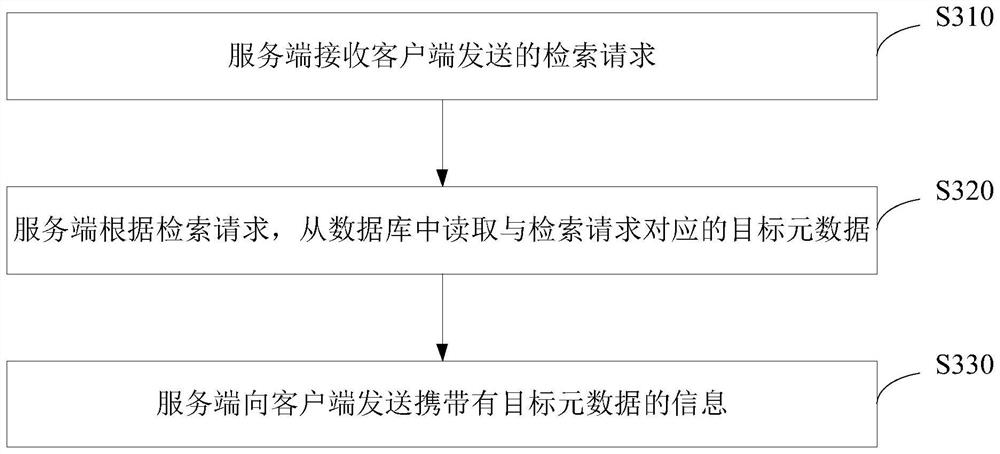
Metadata retrieval method and device, storage medium and electronic equipment
ActiveCN111858496AMeet storage needsMeet query needsFile/folder operationsSpecial data processing applicationsDistributed File SystemFile system
Embodiments of the invention provide a metadata retrieval method and device, a storage medium and electronic equipment. The retrieval method is applied to a server in a distributed file system, and the server is configured with a database for caching metadata. The retrieval method comprises the steps of receiving a retrieval request sent by a client; retrieving target metadata corresponding to theretrieval request from a database according to the retrieval request; and sending information carrying the target metadata to the client. According to the embodiment of the invention, the metadata iscached in the database, so when the server receives the retrieval request sent by the client, the server can directly obtain the target metadata by querying the database, the interaction process between the server and the file system is reduced, and the retrieval efficiency of the metadata is improved.
Owner:北京大道云行科技有限公司
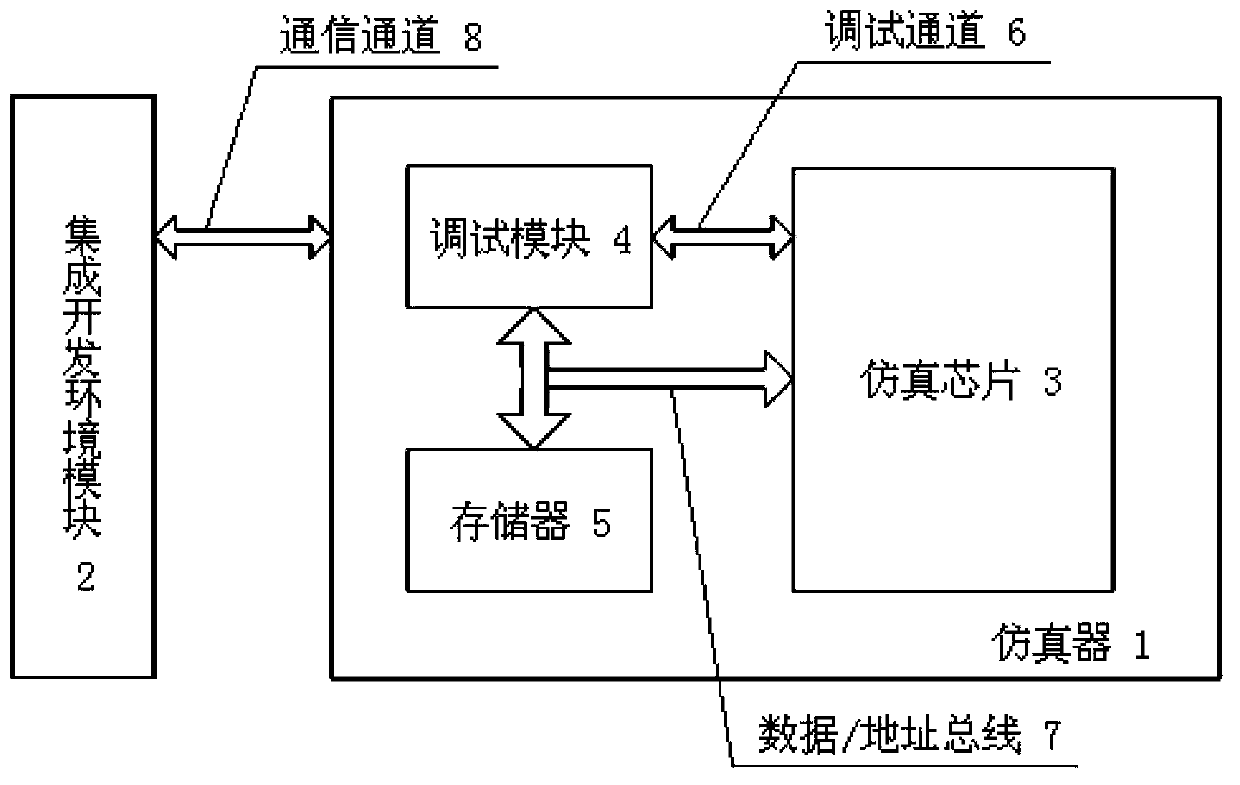
Simulation system
InactiveCN103678073AGuaranteed versatilityReduce interaction processFunctional testingLogical addressSystem stability
The invention discloses a simulation system. The simulation system comprises a simulator and an integrated development environment module. A user sets a breakpoint on a user program through the integrated development environment module, and the integrated development environment module transmits the Bank number and the logic address of a program statement where the breakpoint is located to a debugging module of the simulator through a communication channel. The debugging module reads the current configuration information of an MMU from a simulation chip through a debugging channel, and the Bank number and the logic address, obtained from the integrated development environment module, of the position of the breakpoint to be set and the configuration information of the MMU obtained from the simulation chip are converted into the physical address of the position of the breakpoint to be set. User program statements of all addresses in a memorizer are rewritten through a data / address bus and can be rewritten into software breakpoint statements. The simulation system can achieve the breakpoint function, and the work efficiency and the stability of the system can be improved.
Owner:SHANGHAI HUAHONG INTEGRATED CIRCUIT
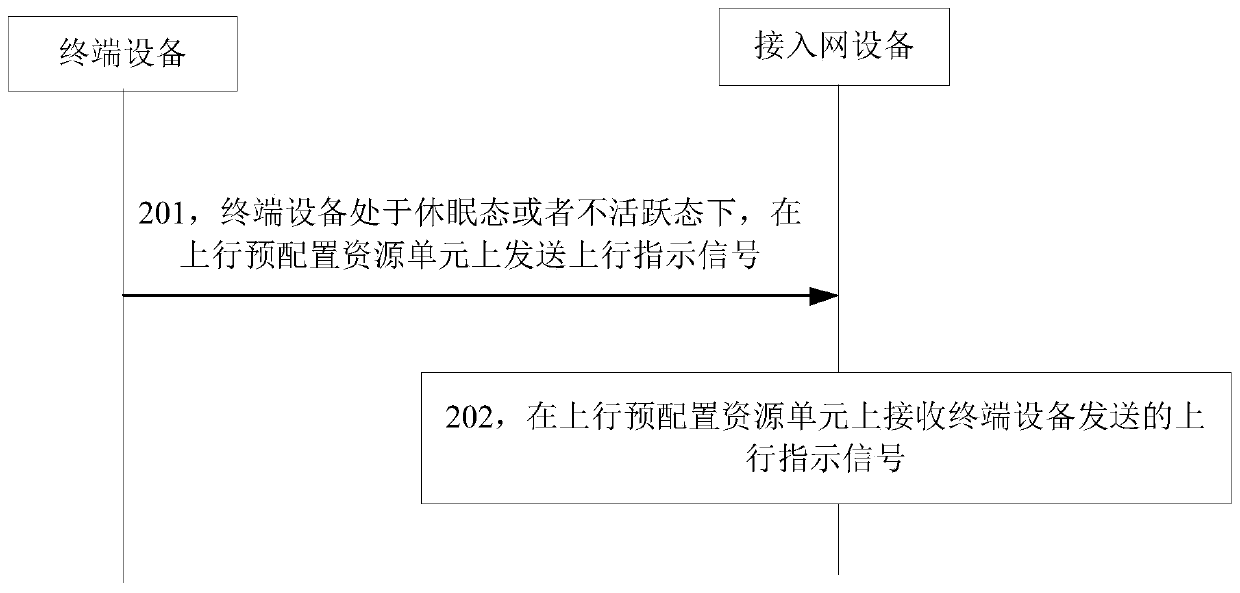
Data transmission method, device, equipment and storage medium
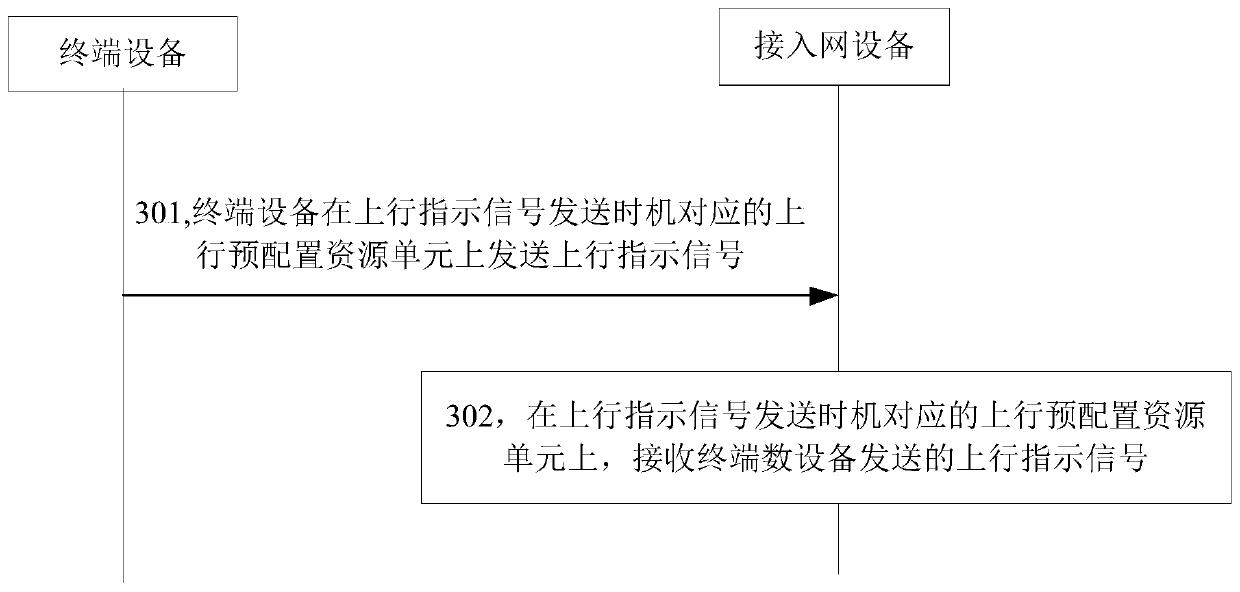
ActiveCN110493876AAvoid random access into the connected stateImprove transmission efficiencyConnection managementHigh level techniquesSignal onUplink transmission
The invention relates to the technical field of communication, in particular to a data transmission method, a data transmission device, equipment and a storage medium. The method is applied to the terminal equipment. The terminal equipment is in a dormant state or an inactive state, the method comprises the steps that an uplink indication signal is sent on an uplink pre-configured resource unit, the uplink pre-configured resource unit is a pre-configured periodic uplink transmission resource unit, and the uplink indication signal comprises an uplink sequence or uplink data. According to the embodiment of the invention, a pre-configured periodic uplink transmission resource unit, i.e., an uplink pre-configured resource unit, is introduced when the terminal equipment is in a dormant state oran inactive state; therefore, the terminal equipment can directly send the uplink indication signal on the uplink pre-configured resource unit, the condition that the terminal equipment needs to initiate random access to enter a connection state in the related technology is avoided, and the transmission efficiency of uplink data is improved.
Owner:SPREADTRUM SEMICON (NANJING) CO LTD
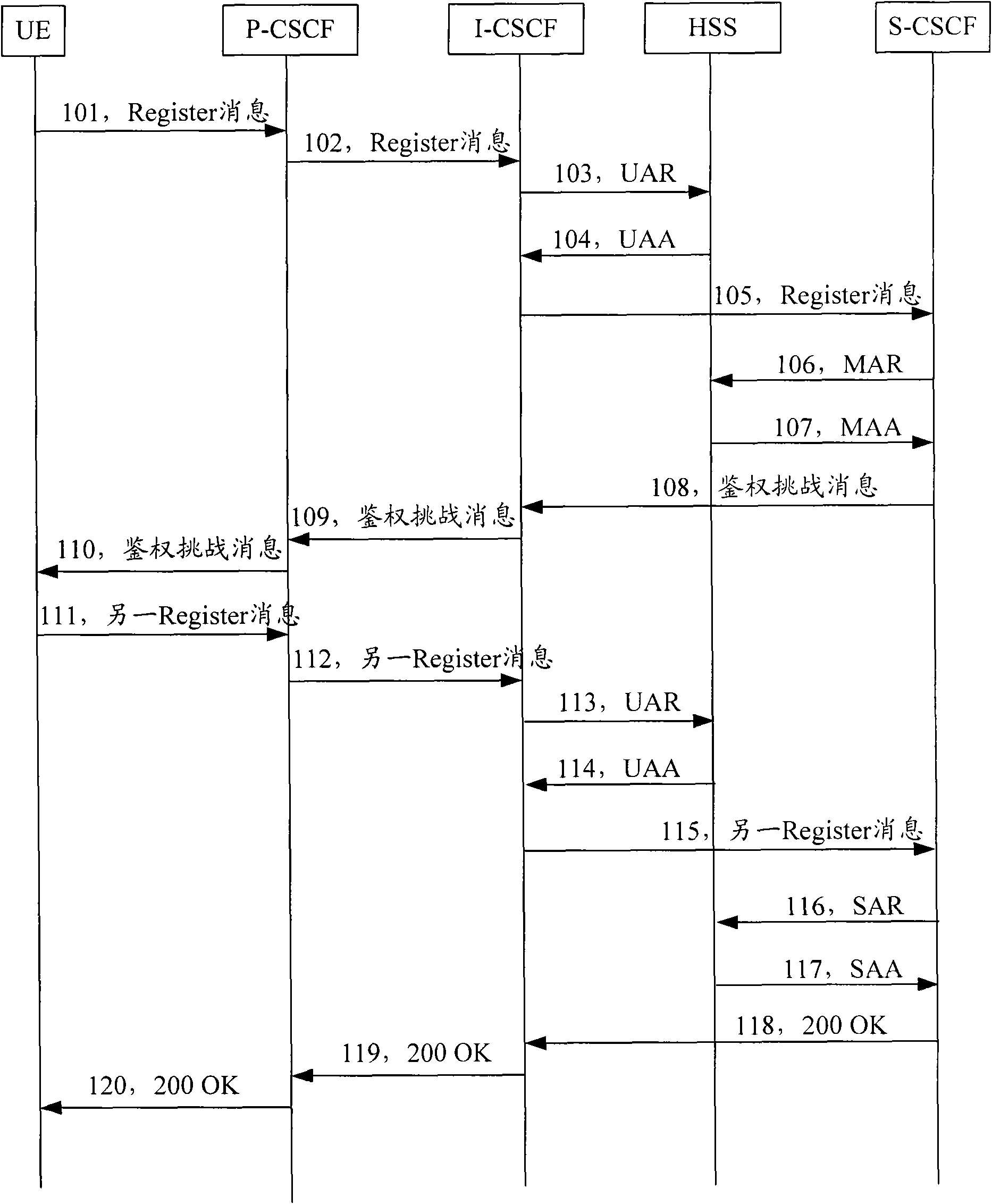
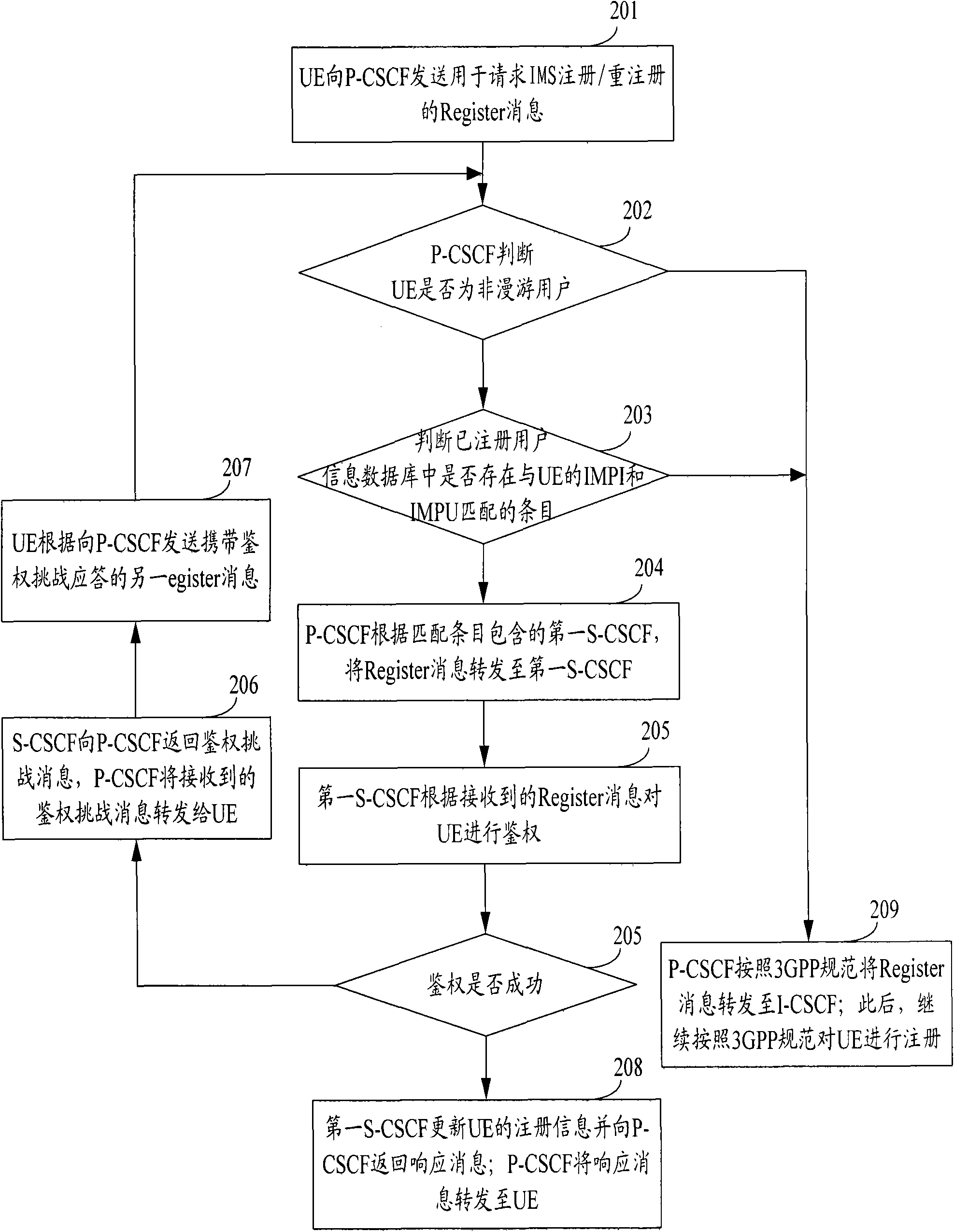
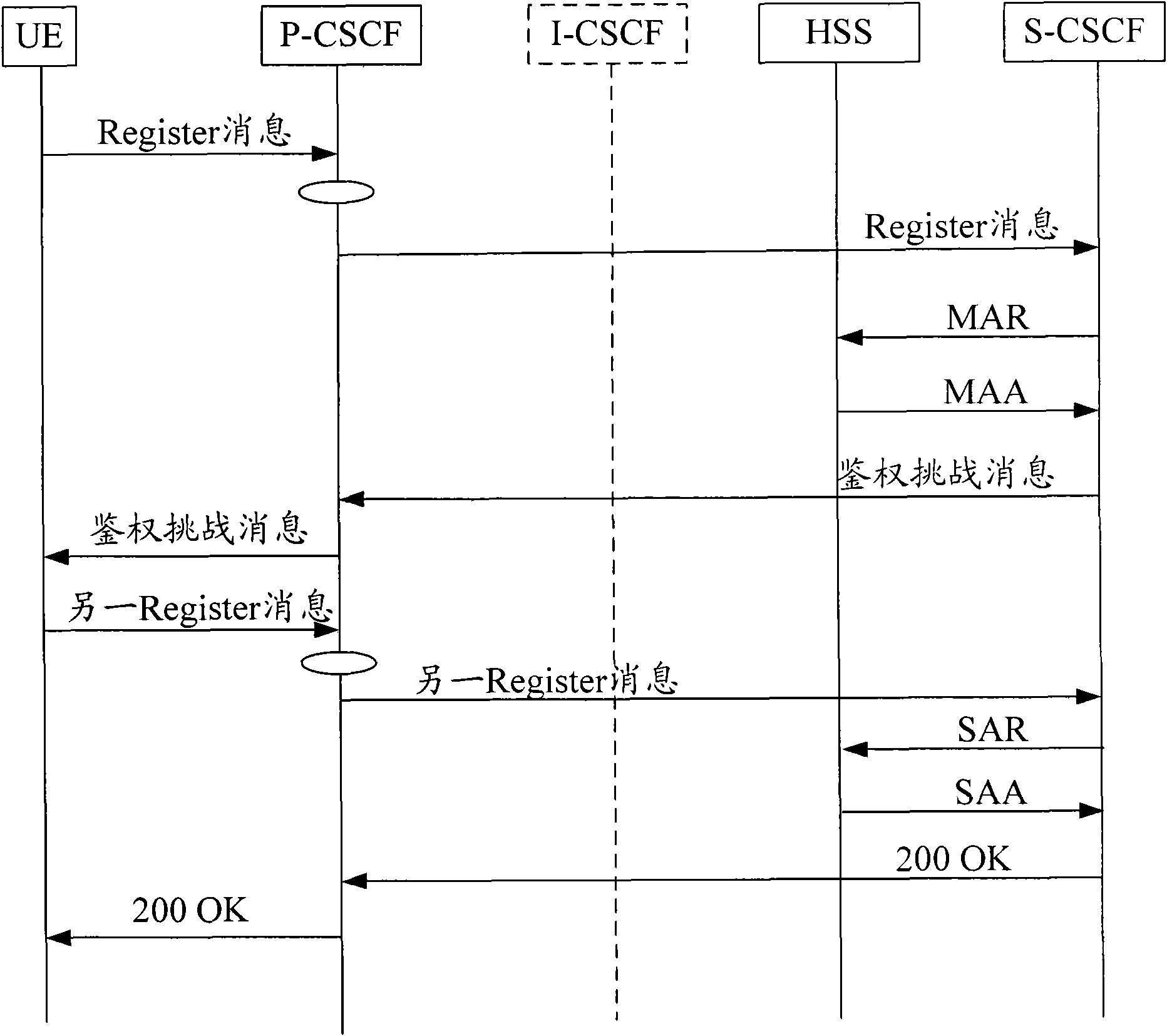
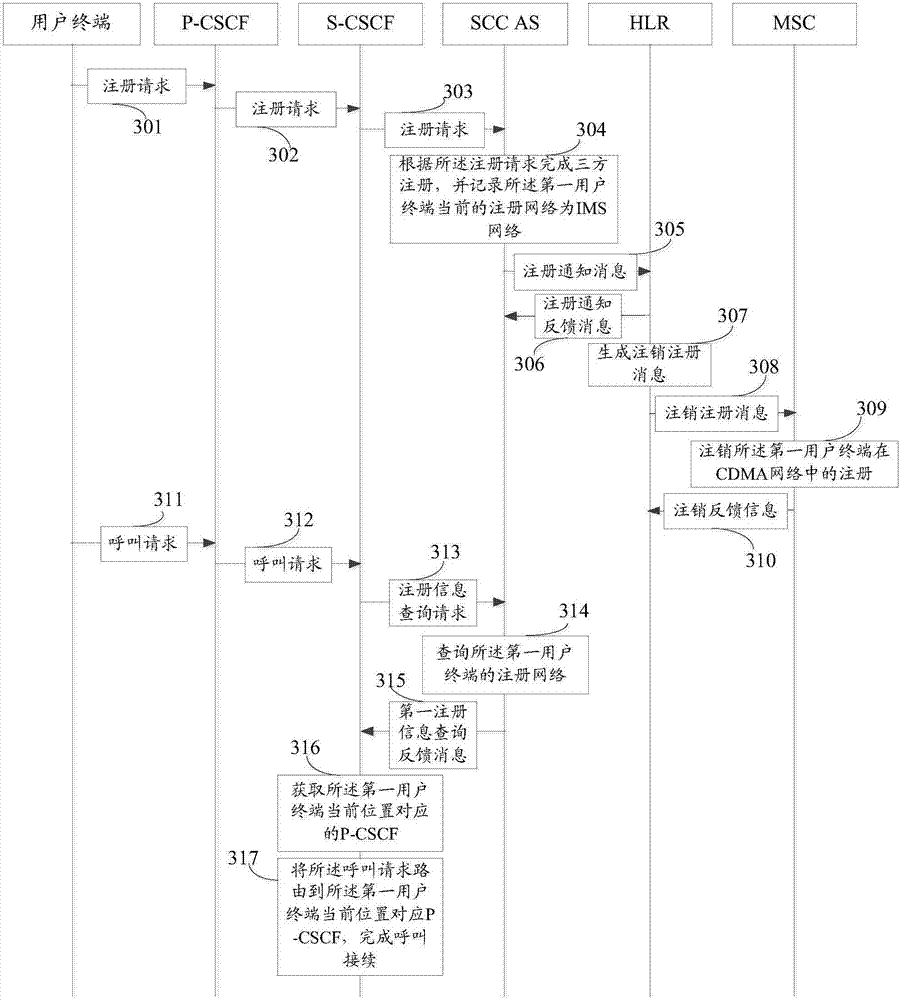
Method, device and network for network re-registration of Internet protocol multimedia subsystem (IMS)
ActiveCN101997828AEnsure safetyReduce interaction processTransmissionSecurity arrangementTime delaysSignal interaction
The invention provides a method, device and network for a network re-registration of an Internet protocol multimedia subsystem (IMS). In the method, S-CSCF information of registered user equipment (UE) saved in a registered user information database by using P-CSCF is adopted, a re-registration massage sent by the UE in the IMS domain is directly forwarded, thereby reducing the signalling interaction in the re-registration process, reducing the loading of an IMS device in a core net, and improving the experience of users on time delay in the re-registration process.
Owner:CHINA MOBILE COMM GRP CO LTD
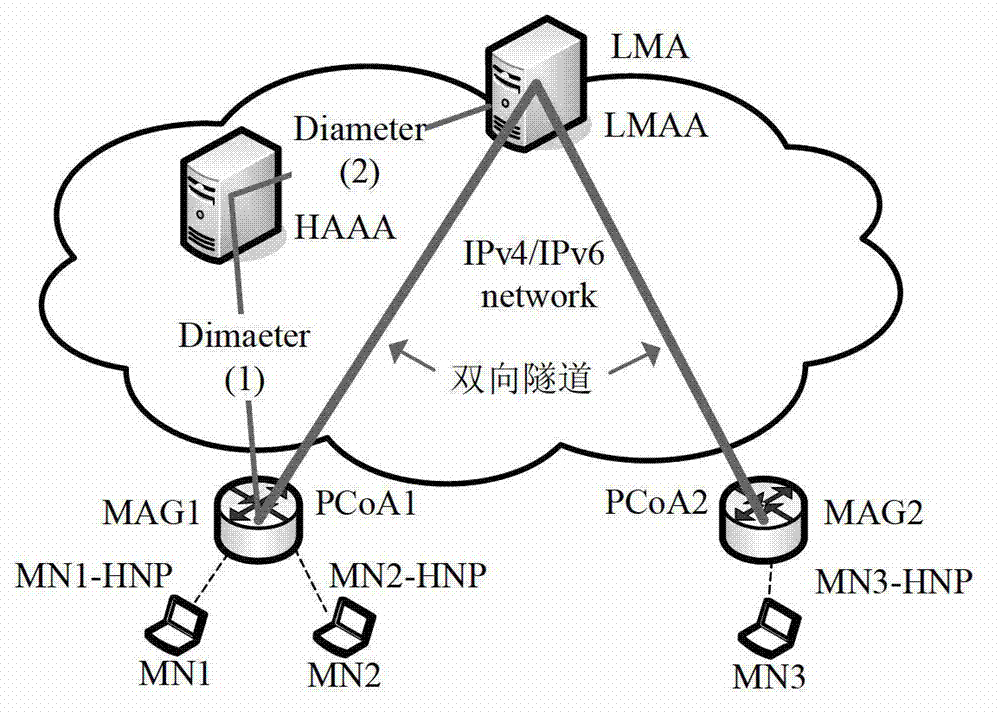
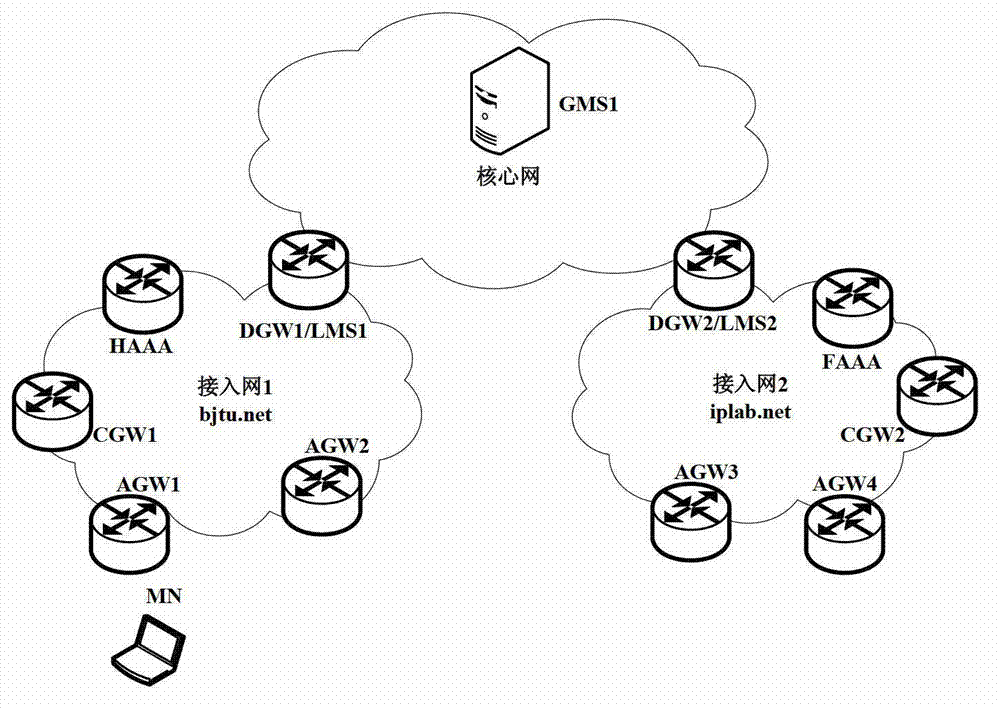
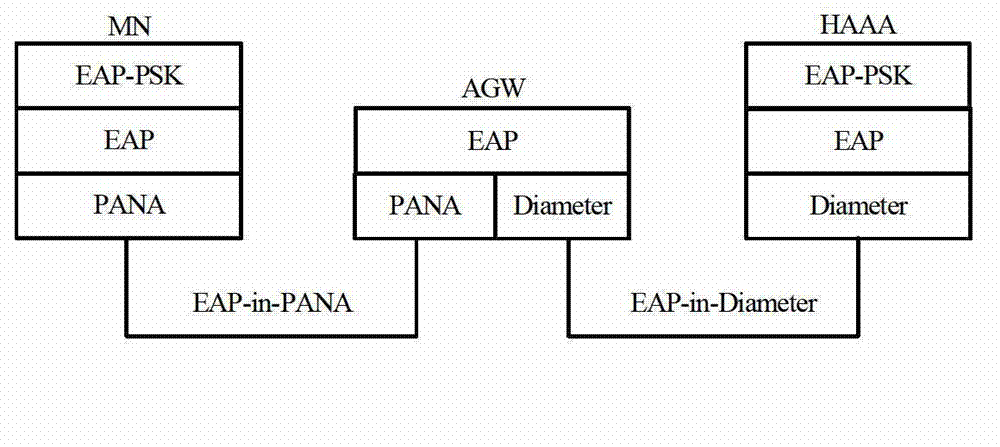
Certificate authorization method of separation-mechanism mobile management system
InactiveCN102869000AGuaranteed legalityEnsure safetySecurity arrangementNetwork data managementMobility managementAuthorization
The invention relates to a certificate authorization method of a separation-mechanism mobile management system. The method comprises the steps of: firstly, carrying out identity authentication on a moving node accessed into the separation-mechanism mobile management system, after successful authentication, adding routs and establishing a tunnel by all functional entities in the system through mobile signaling interaction, acquiring home network prefix information stored in a server by the mobile node, and acquiring a network service by the mobile node at the moment so as to realize the authorization of the separation mechanism mobile management to the mobile node. The method comprises home domain initial authentication, home domain reauthentication, foreign domain initial authentication, foreign domain reauthentication and authentication to the mobile node. According to the invention, an AGW (Access Gateway), a CGW (Customer GateWay), a DGW (Data Gateway) and an AAA (Authentication, Authorization and Accounting) server are taken as main functional entities, and a series message interaction among the AGW, CGW, DGW and AAA server is used to complete the authentication of the legality of the mobile node so as to guarantee network safety.
Owner:BEIJING JIAOTONG UNIV
Communication method and device
ActiveCN111491393AReduce latencySave access processError preventionSignal allocationTime delaysTerminal equipment
An embodiment of the invention discloses a communication method and a communication device, which are used for reducing the time delay of random access of terminal equipment. The communication methodprovided by the embodiment of the invention comprises the following steps that: the terminal equipment transmits a first message to network equipment, wherein the first message comprises a random access signal and information used for competition resolution, and the random access signal and the information used for competition resolution are transmitted through pre-allocated resources; and the terminal equipment receives a response message of the first message from the network equipment, wherein the response message is used for indicating a random access state of the terminal equipment.
Owner:HUAWEI TECH CO LTD
Network switching method, convergence network element, communication system and storage medium
PendingCN114599065AImprove switching efficiencyAvoid interruptionWireless communicationService gatewayNetwork element
The embodiment of the invention provides a network switching method, a convergence network element, a communication system and a storage medium, and belongs to the field of mobile communication. The method comprises: according to a session context request, performing a first PFCP session update with a user plane convergence network element to initiate a network switching process, so that a user equipment is switched between a 4G session and a 5G session, the user plane fusion network element is a network element obtained by fusing a service gateway user plane network element and an intermediate user plane network element in the core network. According to the technical scheme of the embodiment of the invention, the PFCP session is updated according to the session context request and the user plane convergence network element, so that the interaction process can be reduced, the network switching efficiency is improved, and the session and service continuity is ensured.
Owner:ZTE CORP
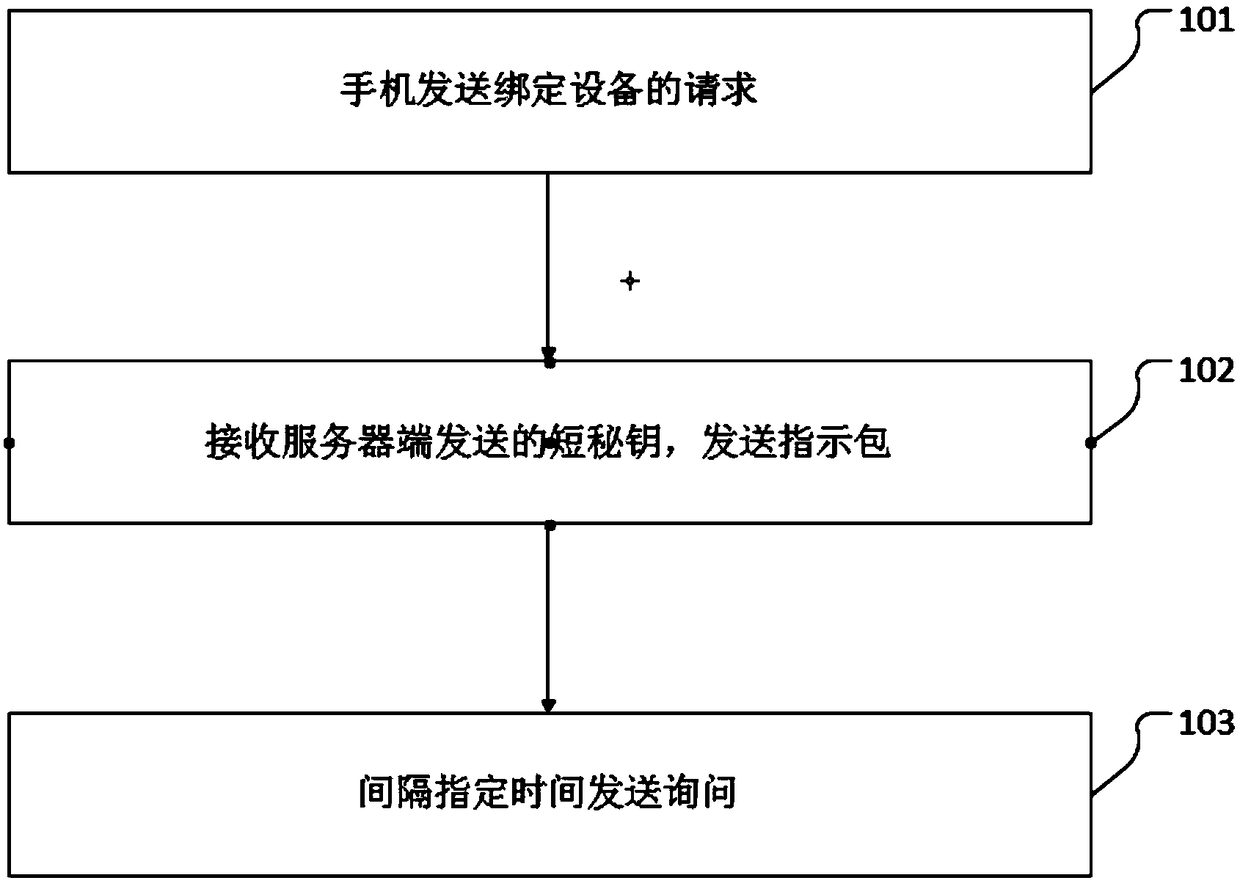
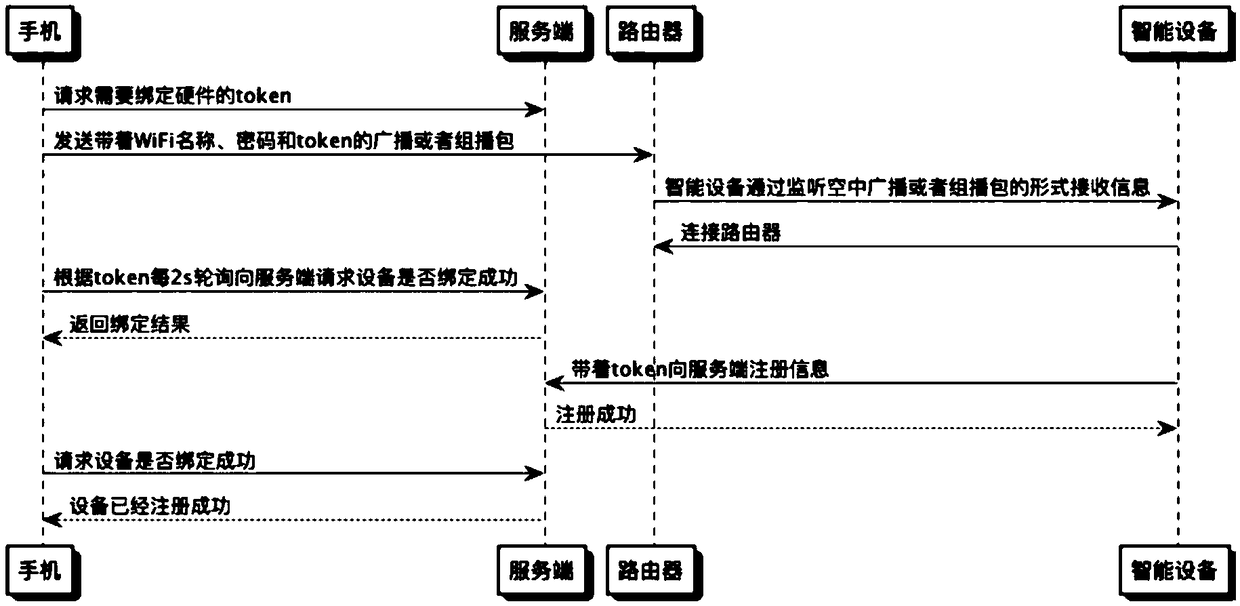
A distribution network method for registering devices to the cloud based on SmartConfig mode
InactiveCN109089299AReduce interaction process and distribution network processImprove distribution network speed and success rateAssess restrictionHome automation networksDistribution networksMobile phone
The invention discloses a distribution network method based on SmartConfig mode for equipment registration to cloud end, which comprises the following steps: step 1, a mobile phone sends a request tobind the equipment; step 2, the mobile phone sends a request to bind the equipment to the cloud end. 2, receiving a short secret key sent by a server end and sending an indication packet; 3, sending aquery at specified interval until the distribution network is displayed to be successful. The invention discloses a distribution network method based on SmartConfig mode for registering equipment tocloud end, which enables mobile phone to interact with intelligent equipment only once, reduces interaction flow to realize cloud end registration, simplifies distribution network process, and improves success rate and speed of distribution network.
Owner:HANGZHOU TUYA INFORMATION TECH CO LTD
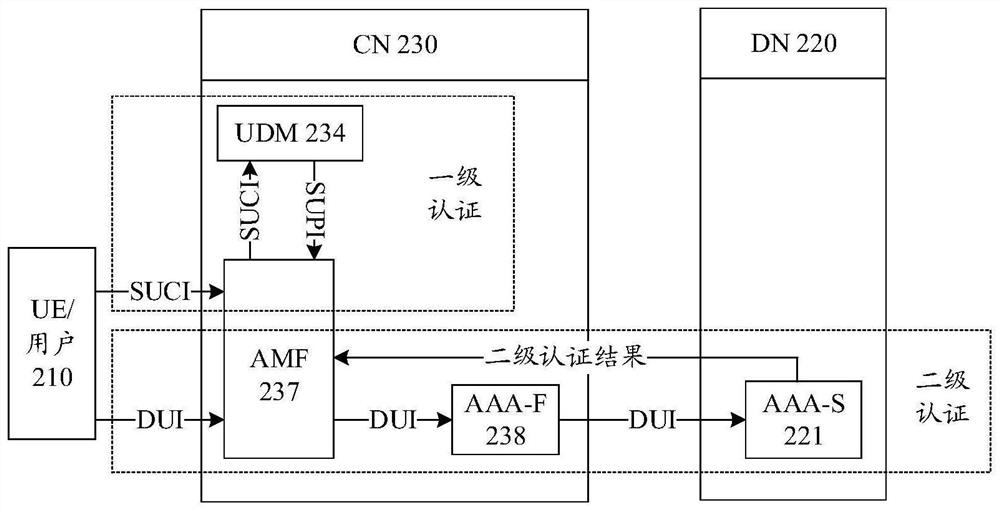
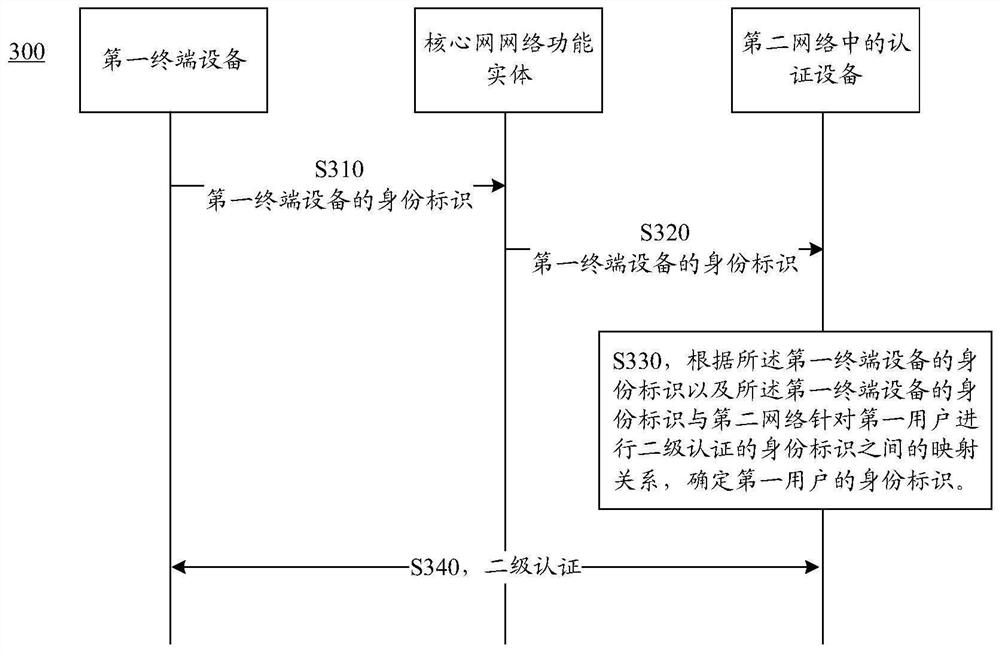
Secondary authentication method and device
ActiveCN112105015AImprove protectionEffective protectionTransmissionSecurity arrangementTerminal equipmentEngineering
The embodiment of the invention provides a secondary authentication method and device, and the method comprises the steps that a core network function entity obtains the identity of first terminal equipment, and the identity of the first terminal equipment is the identity of a first network; and the core network function entity sends the identity identifier of the first terminal device to an authentication device in a second network, the identity identifier of the first terminal device is used for determining an identity identifier of the second network for performing secondary authenticationon a first user, and the identity identifier of the first user is different from the identity identifier of the first terminal device. According to the method, the core network function entity can send the identity identifier of the first terminal device to the authentication device in the second network, and the identity identifier of the first user can be determined through the identity identifier of the first terminal device; the implicit transmission of the identity of the first user can enhance the security protection of the identity of the user in the secondary authentication process.
Owner:HUAWEI TECH CO LTD
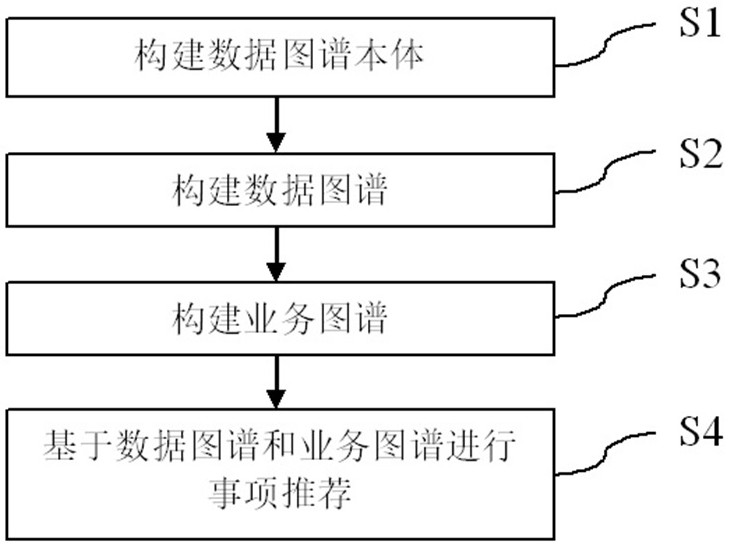
Item handling intelligent recommendation method based on data graph and service graph
ActiveCN112330307AReduce interaction processImprove accuracyRelational databasesOffice automationData graphData mining
The invention discloses an item handling intelligent recommendation method based on a data graph and a service graph. The method comprises the steps: S1, constructing a data graph body; S2, constructing a data graph; and S3, constructing a service map. After the S3, item recommendation can be further carried out based on the data graph and the service graph. After the S3, the method can further comprise: S4, updating the service graph data; and S5, recommending a potential item. By means of the item handling intelligent recommendation method based on the data graph and the service graph, iteminformation can be automatically recommended, the interaction process of a user and a system is reduced, and meanwhile the item recommendation accuracy is improved.
Owner:江苏数兑科技有限公司
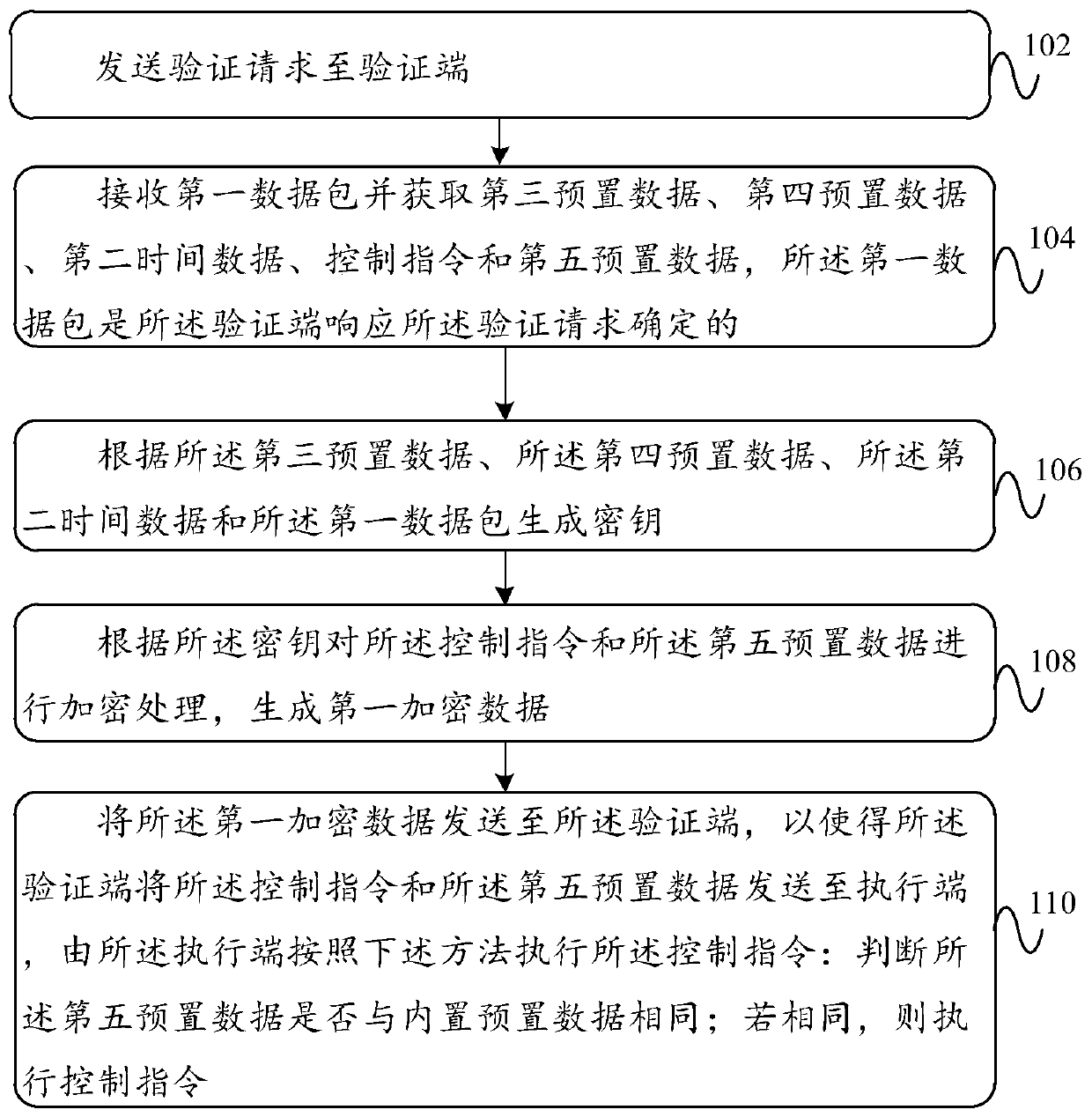
Security authentication method and device and electronic equipment
ActiveCN111432373AReduce interaction processImprove latency experienceParticular environment based servicesVehicle wireless communication serviceExecution controlSecurity authentication
The invention discloses a security authentication method and apparatus, and an electronic device. The method comprises the steps of sending a verification request to a verification terminal; receivinga first data packet and obtaining third preset data, fourth preset data, second time data, a control instruction and fifth preset data, wherein the first data packet is determined by the verificationend in response to the verification request; generating a key according to the third preset data, the fourth preset data, the second time data and the first data packet; encrypting the control instruction and fifth preset data according to the key to generate first encrypted data; sending the first encrypted data to a verification end, so that the verification end sends the control instruction and fifth preset data to an execution end, and the execution end executes the control instruction according to the following method: judging whether the fifth preset data is the same as the built-in preset data or not; and if so, executing the control instruction. According to the invention, the interaction process can be reduced, the time delay experience is improved, and the risk of malicious power consumption caused by NFC-Key encryption and decryption behaviors triggered by fake messages of the card reader is reduced.
Owner:GEELY AUTOMOBILE INST NINGBO CO LTD +1
Embedded device batch upgrading method and system
PendingCN106559301AImprove the efficiency of batch upgradeReduce interaction processNetworks interconnectionIp addressClient-side
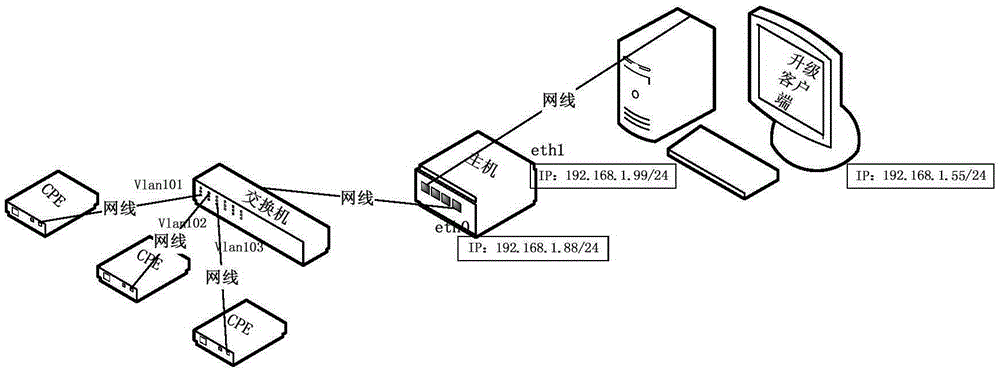
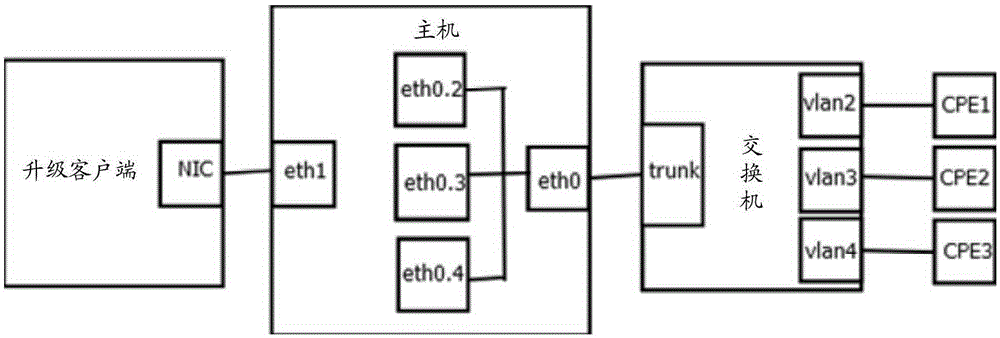
The invention discloses an embedded device batch upgrading method. The method includes after a host creates a plurality of virtual network ports and creates a bridge, the VLAN IDs of the different virtual network ports are set to match the IDs of the different VLANs on a switch, and the plurality of virtual network ports and the ethernet ports connecting with an upgrading client are added into the bridge; the upgrading client sends the message carrying the target address to a corresponding virtual network port in the host; after the host changes the target address to the IP address of an embedded device, the host forwards the message to the embedded device connected with the host through the VLANs matched on the switch according to the VLAN IDs; and the embedded device verifies the target address correctly and then feeds the message back to the upgrading client and downloads the upgrade file for the upgrade. The invention further discloses an embedded device batch upgrading system. When the embedded device needs to be upgraded, the IP address is not needed to be modified, the interaction between the upgrading client and the embedded device is reduced, and the efficiency of the batch upgrading of the embedded devices is improved.
Owner:ZTE CORP
Image display method and electronic equipment
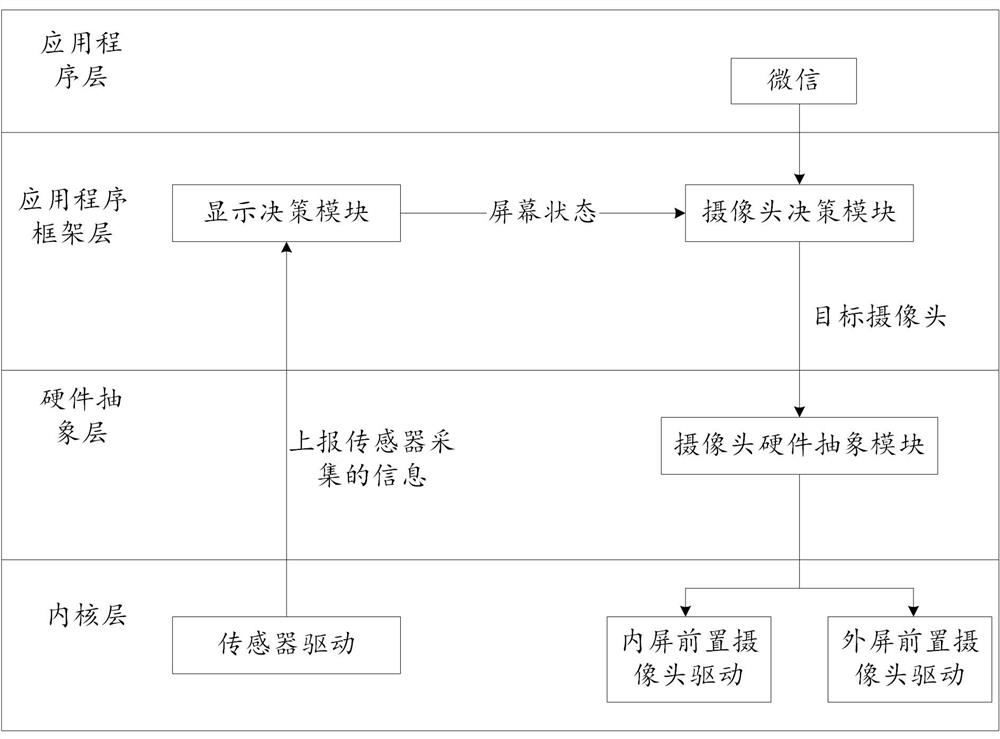
ActiveCN114257671AImprove efficiencyImprove switching efficiencyTelevision system detailsInterprogram communicationEngineeringComputer hardware
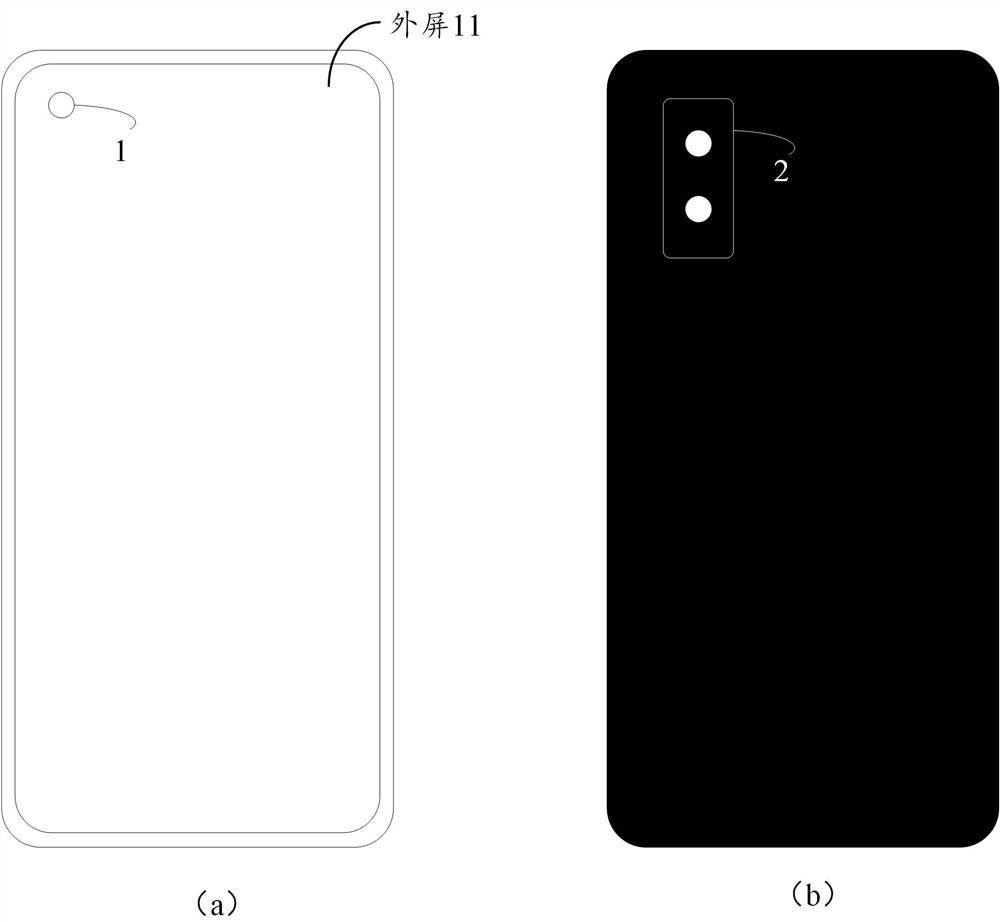
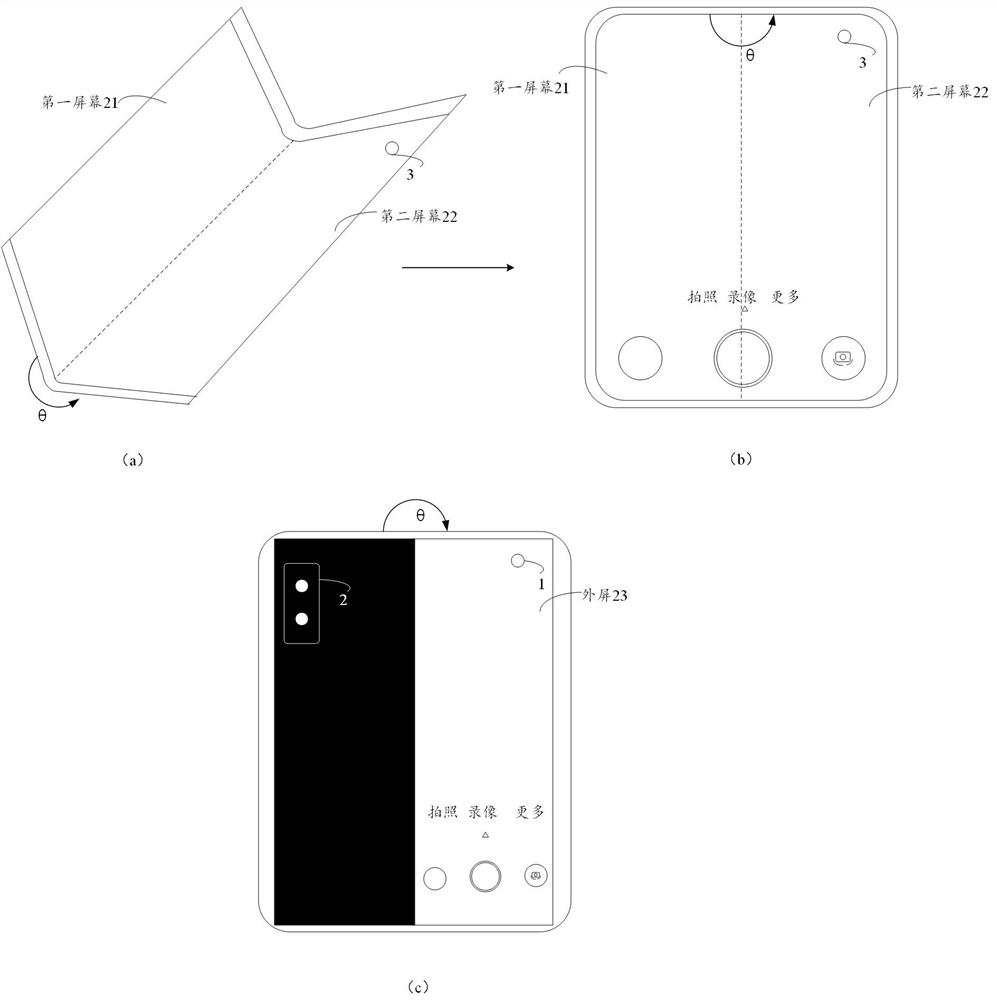
The invention discloses an image display method and electronic equipment, relates to the technical field of terminals, and can improve the sending and displaying efficiency of a target camera in the folding screen switching process of the electronic equipment. The method is applied to the electronic equipment with a folding screen, the electronic equipment comprises an inner screen and an outer screen, the inner screen comprises a first screen and a second screen, the electronic equipment comprises a first camera and a second camera, the first camera is arranged below the inner screen, and the second camera is arranged below the outer screen. The electronic equipment further comprises an application program framework layer and a first layer, the first layer is located between the application program framework layer and a hardware unit of the electronic equipment, and the method comprises the steps that the first layer determines an included angle between a first screen and a second screen; and when the included angle between the first screen and the second screen reaches a preset angle range, the first layer triggers an image collected by a target camera in the first camera and the second camera to be displayed.
Owner:HONOR DEVICE CO LTD
Method and device for operating logic space by SSD (Solid State Disk), storage medium and SSD equipment
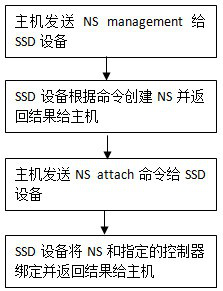
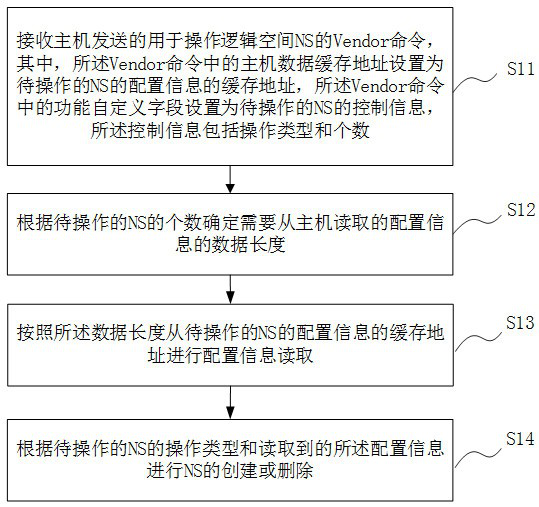
ActiveCN114415974AReduce interaction processShorten the timeInput/output to record carriersSolid-stateEngineering
The invention relates to the technical field of data storage, and provides a method and device for operating a logic space by an SSD, a storage medium and SSD device.The method comprises the steps that a Vendor command sent by a host and used for operating the logic space NS is received, and a host data cache address in the Vendor command is set as a cache address of configuration information of the NS to be operated, a function custom field in the Vendor command is set as the operation type and number of the NS to be operated; determining the data length of the configuration information required to be read from the host according to the number of the NS to be operated; reading the configuration information from the cache address of the configuration information of the NS to be operated according to the data length; and creating or deleting the NS according to the operation type of the NS to be operated and the read configuration information. According to the method, the interaction process of the host and the equipment in the NS creating and deleting process can be greatly reduced, and the time for configuring the NS is saved.
Owner:DERA CO LTD
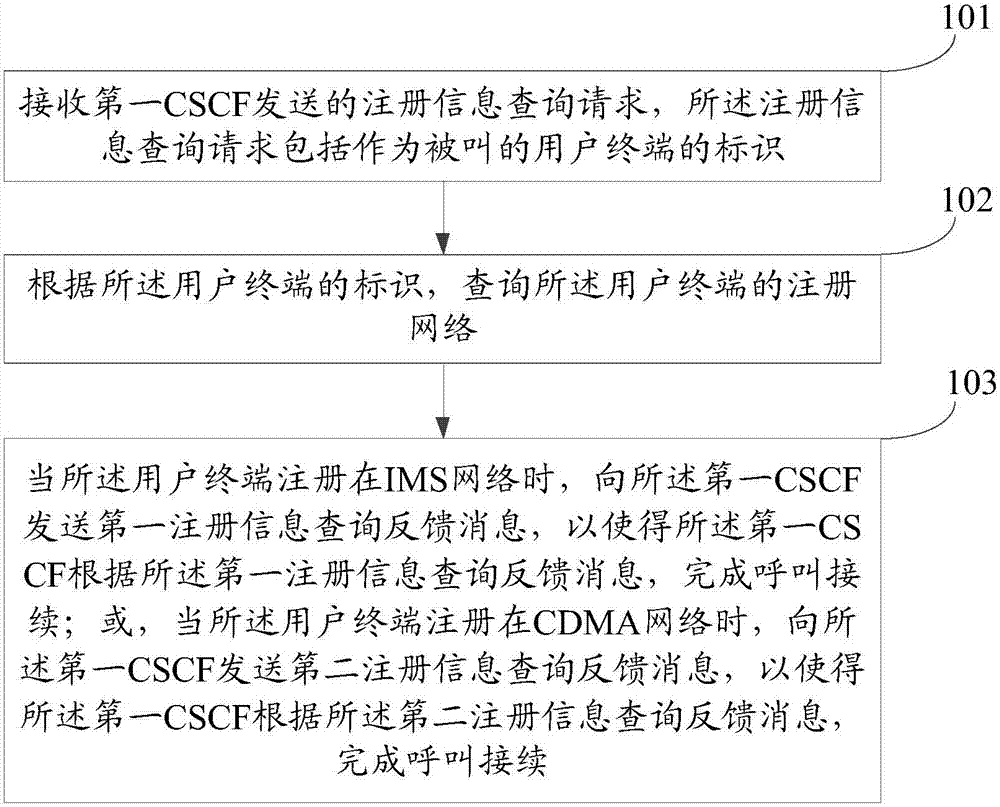
Domain selection method and server
InactiveCN107222452AReduce interaction processShorten call delayCommmunication supplementary servicesData switching networksSession controlA domain
The embodiment of the invention discloses a domain selection method. The method comprises the following steps: receiving a registration information inquiry request sent by a first call session control function network element CSCF, wherein the registration information inquiry request comprises an identifier of a user terminal that is used as the called; inquiring a registered network of the user terminal according to the identifier of the user terminal; when the user terminal is registered in an IP multimedia subsystem IMS network, sending a first registration information inquiry feedback message to the first CSCF; or when the user terminal is registered in a code division multiple access CDMA network, sending a second registration information inquiry feedback message to the first CSCF. Further, the embodiment of the invention further discloses a domain selection server.
Owner:ZTE CORP
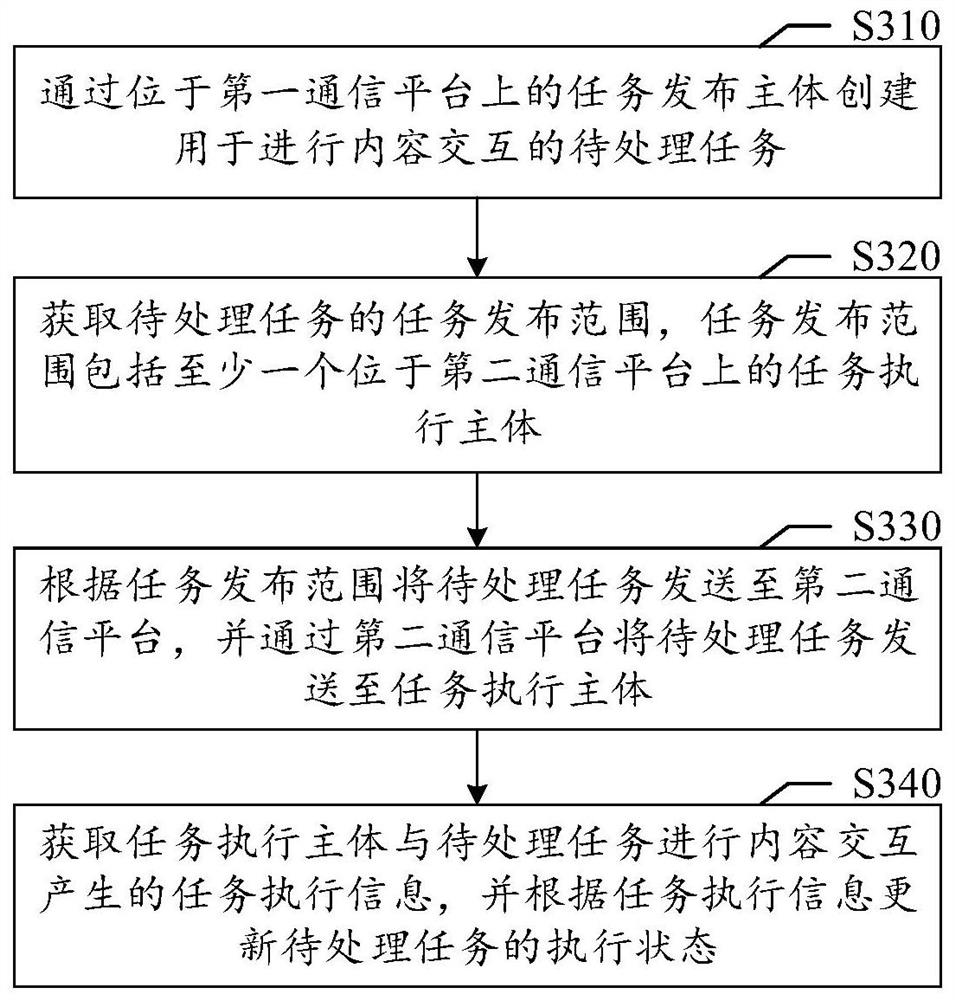
Task processing method and device
PendingCN113703990AReduce interaction processReduce interaction costsInterprogram communicationComputer hardwareComputer architecture
The invention relates to the technical field of networks and computers, in particular to a task processing method, a task processing device, a computer readable medium and electronic equipment. The task processing method in the embodiment of the invention comprises the following steps: creating a to-be-processed task for content interaction through a task publishing main body located on a first communication platform; obtaining a task release range of the to-be-processed task, wherein the task release range comprises at least one task execution main body located on a second communication platform; sending the to-be-processed task to a second communication platform according to the task release range, and sending the to-be-processed task to a task execution main body through the second communication platform; and obtaining task execution information generated by content interaction between the task execution main body and the to-be-processed task, and updating the execution state of the to-be-processed task according to the task execution information. According to the method, the task processing efficiency and the task management convenience can be improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
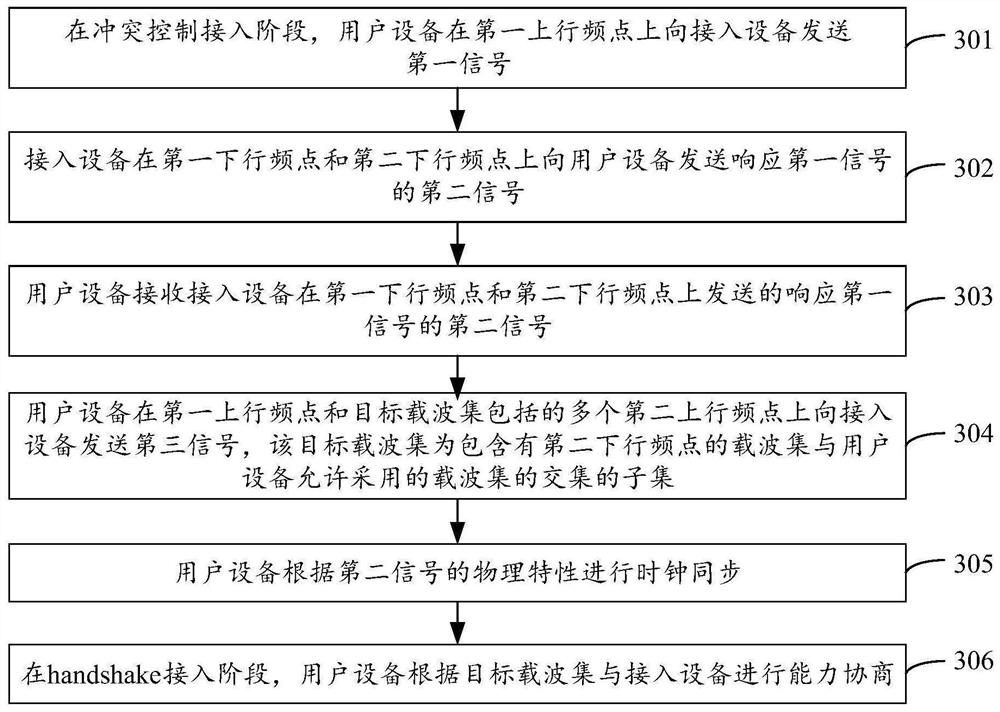
User equipment online method and user equipment
ActiveCN112448871AShorten the onboarding processShorten the time to marketMultiplex system selection arrangementsTime-division multiplexComputer networkSignal on
The invention discloses a user equipment online method and user equipment, and belongs to the technical field of communication. According to the invention, in a conflict control access stage, user equipment can send a first signal to access equipment at a first uplink frequency point, then receive a second signal which is sent by the access equipment at a first downlink frequency point and a second downlink frequency point and responds to the first signal, and sends a third signal on the first uplink frequency point and an uplink frequency point included in the target carrier set to complete selection of the carrier set. In a handshake access stage, the user equipment can perform capability negotiation with the access equipment according to the determined target carrier set. Therefore, inthe embodiment of the invention, when the user equipment is on line, the selection of the carrier set can be completed in the conflict control access stage, so that the carrier set selection can be carried out in the handshake access stage subsequently, i.e., independent signaling interaction is not needed, the interaction process is reduced, and the access time is shortened.
Owner:HUAWEI TECH CO LTD
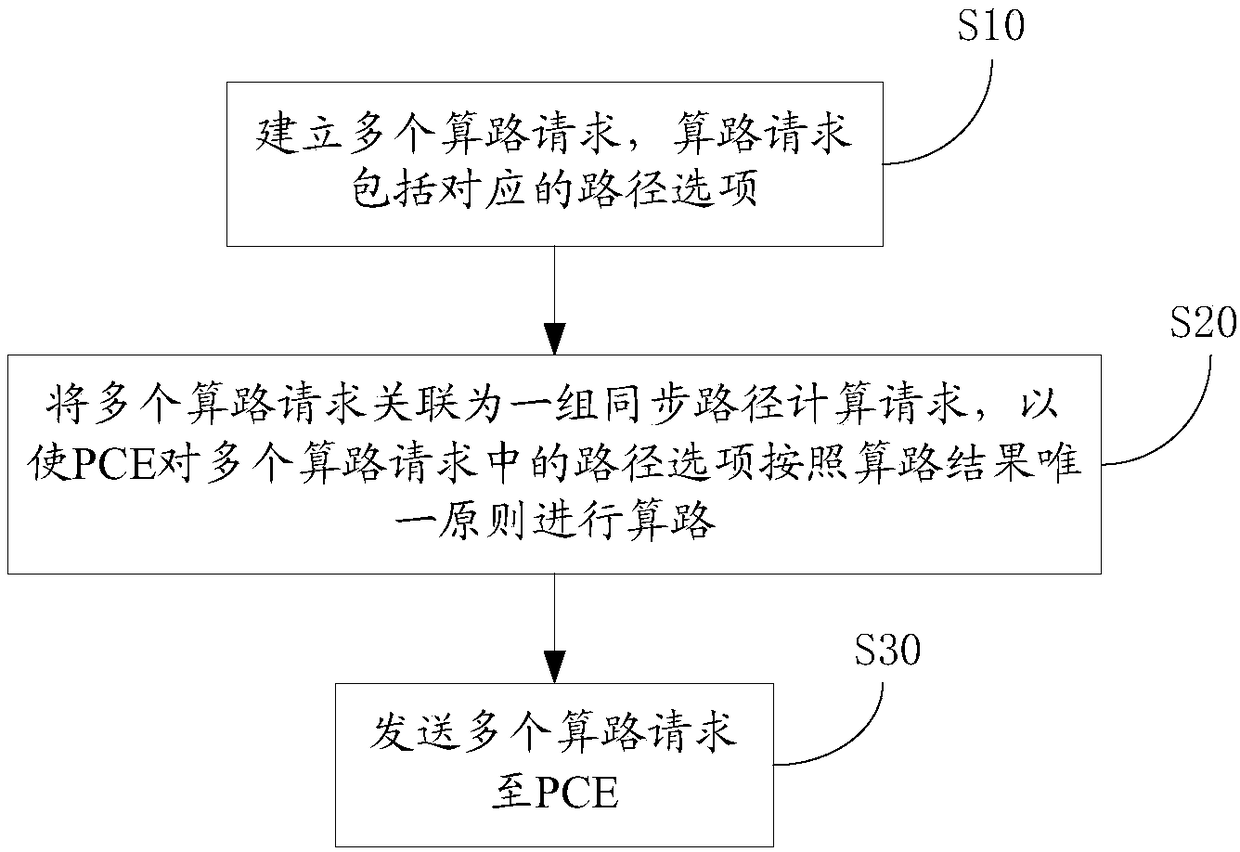
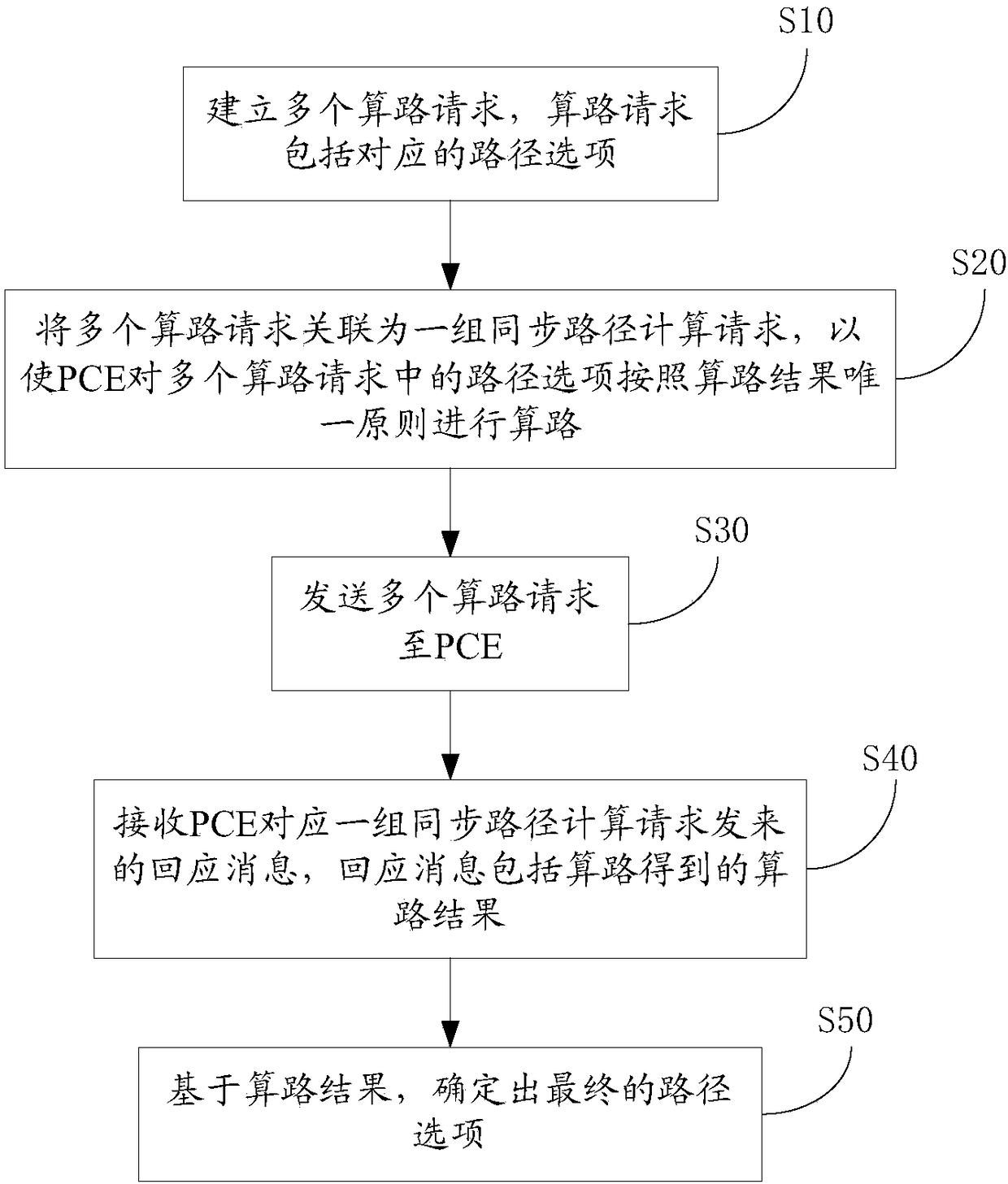
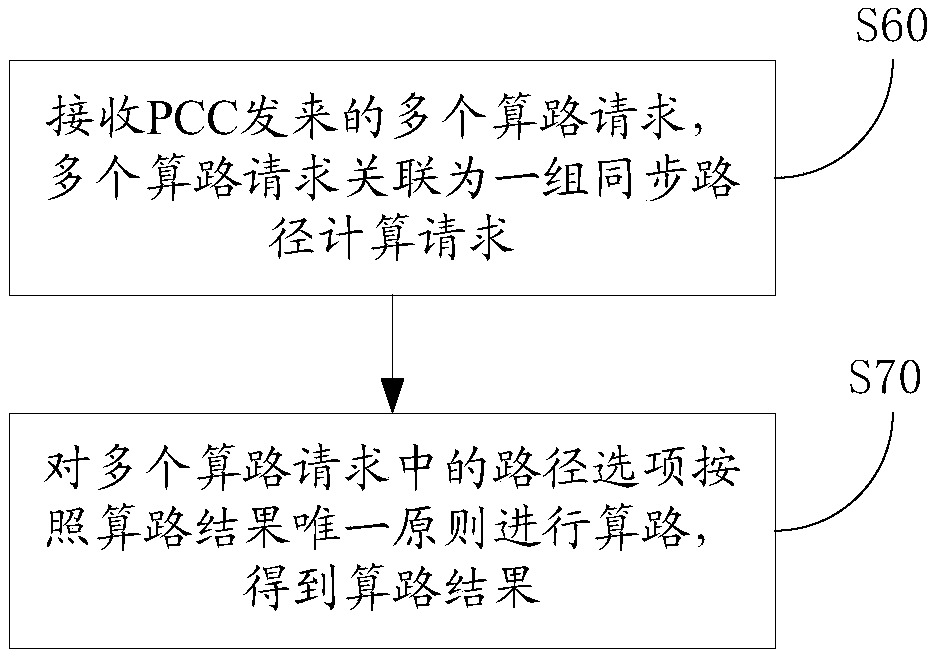
Path computation method and device, PCC, PCE and path computation system
ActiveCN108243105AReduce interaction processImprove path calculation efficiencyData switching networksPath computation elementParallel computing
The invention provides a path computation method, a path computation device, a PCC, a PCE and a path computation system. The path computation method comprises the steps, executed at a PCC side, of: establishing a plurality of path computation requests, wherein the plurality of path computation requests respectively comprises a corresponding path option; associating the plurality of path computation requests to be a group of synchronous path computation requests, so that the PCE can perform path computation on the path options in the plurality of path computation requests according to a path computation result unique principle; and sending the plurality of path computation requests to the PCE. Therefore, the path computation efficiency of the PCE for the plurality of path options is improved.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com