Blockchain data sharing encryption and decryption method, equipment, and storage medium
A data sharing and encryption method technology, applied in the blockchain field, can solve problems such as low credibility, differences in data calculation results, false information, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
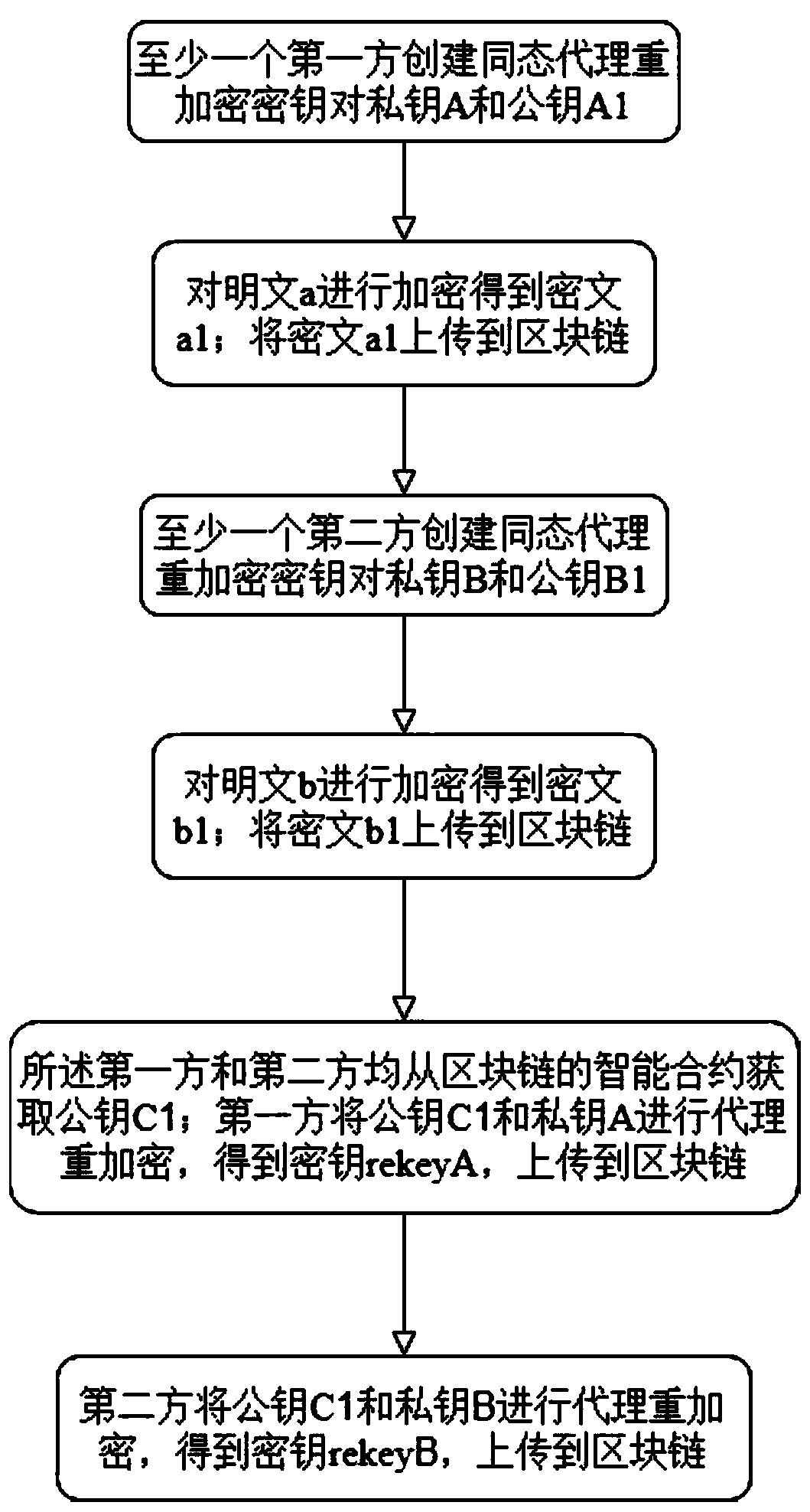
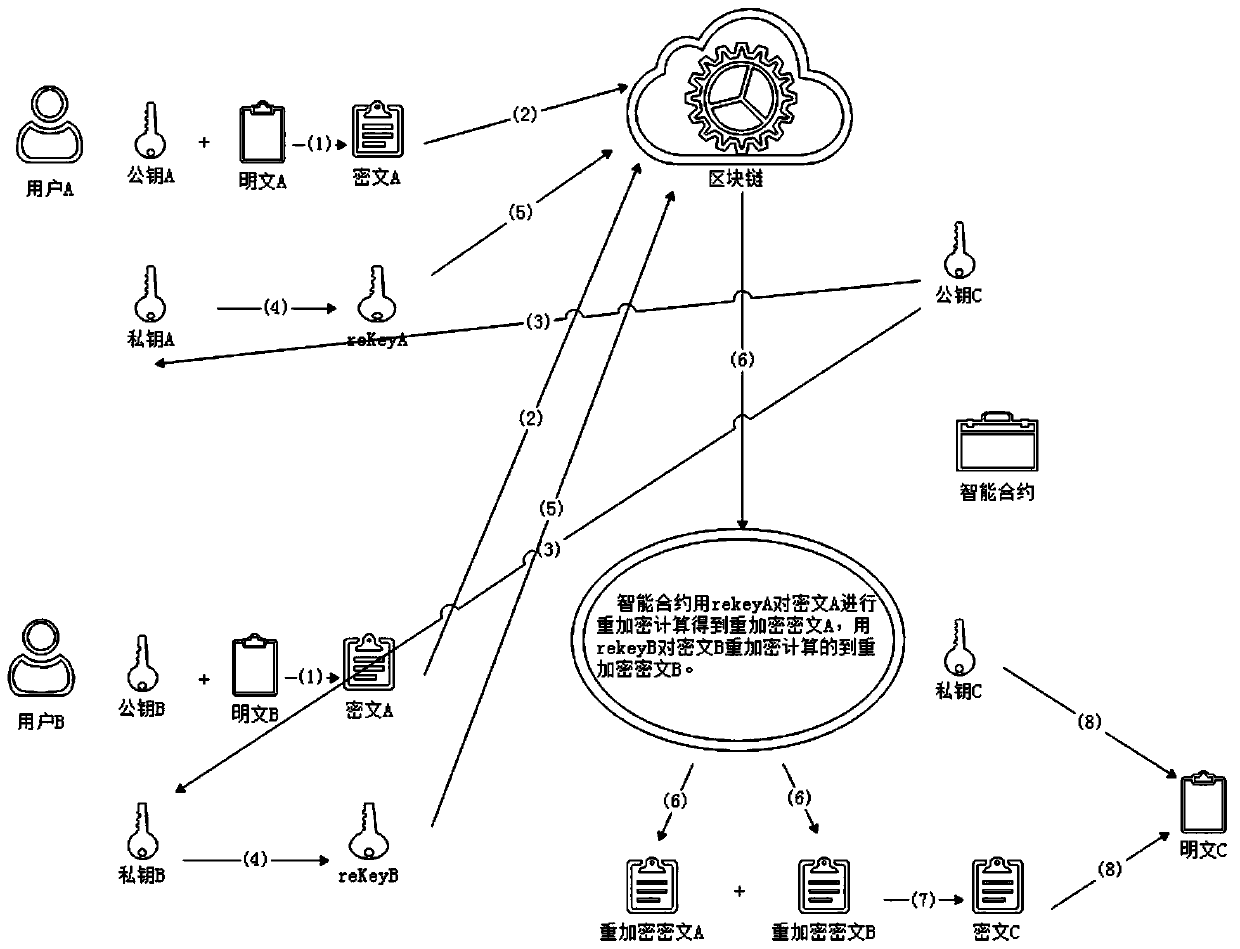
[0032] A blockchain data sharing encryption method, such as figure 1 , 3 As shown, it includes: at least one first party creates a homomorphic proxy re-encryption key pair private key A and public key A1; encrypts plaintext a to obtain ciphertext a1; uploads ciphertext a1 to the blockchain; at least one first The two parties create a homomorphic proxy re-encryption key pair private key B and public key B1; encrypt the plaintext b to obtain the ciphertext b1; upload the ciphertext b1 to the blockchain; The smart contract of the blockchain obtains the public key C1; the first party re-encrypts the public key C1 and the private key A, obtains the key rekeyA, and uploads it to the blockchain; the second party re-encrypts the public key C1 and the private key B. The agent re-encrypts, obtains the key rekeyB, and uploads it to the blockchain; among them, the smart contract creates the key pair private key C and public key C1 through homomorphic encryption.
[0033] The proxy re-en...
Embodiment 2
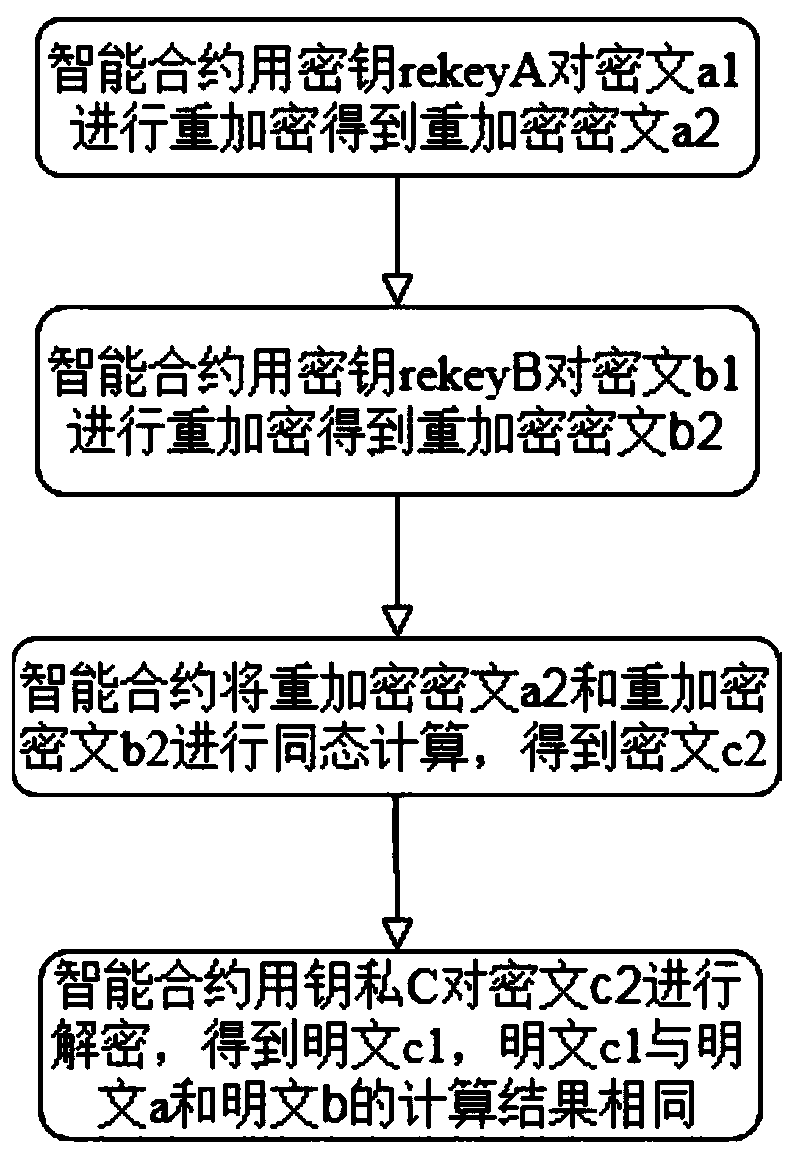
[0036] A blockchain data sharing decryption method, according to a blockchain data sharing encryption method described in Embodiment 1, such as figure 2 , 3 It includes: the smart contract re-encrypts the ciphertext a1 with the key rekeyA to obtain the re-encrypted ciphertext a2; the smart contract re-encrypts the ciphertext b1 with the key rekeyB to obtain the re-encrypted ciphertext b2; the smart contract re-encrypts the ciphertext b2 The ciphertext a2 and the re-encrypted ciphertext b2 are subjected to homomorphic calculation to obtain the ciphertext c2; the smart contract decrypts the ciphertext c2 with the private key C to obtain the plaintext c1, which is the same as the calculation result of the plaintext a and the plaintext b. The proxy re-encryption is based on multiple re-encryption algorithms, such as bls12, or bn256. The homomorphic encryption algorithm is rsa-based multiplication homomorphism, Paillier's additive homomorphism, or Gentry full homomorphism.
[00...
Embodiment 3
[0039] An apparatus comprising: one or more processors; a memory for storing one or more programs that, when executed by the one or more processors, cause the one or more programs One or more processors perform the method as described above.
[0040] A storage medium storing a computer program, when the program is executed by a processor, implements the method described in Embodiment 1 above.
[0041] Figure 4 It is a schematic structural diagram of a device provided by an embodiment of the present invention.
[0042] like Figure 4 As shown, as another aspect, the present application also provides a device 500, comprising one or more central processing units (CPUs) 501, which can operate according to a program stored in a read only memory (ROM) 502 or from a storage portion 508 performs various appropriate actions and processes by loading a program into random access memory (RAM) 503 . In the RAM 503, various programs and data necessary for the operation of the device 500 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com