Pervasive-network-oriented remote identity authentication system and method
An identity authentication and remote verification technology, applied in the field of remote identity authentication systems, can solve problems such as difficulty for ordinary users to grasp, increase hardware costs, and user rejection, avoid deployment and maintenance work, expand the scope of access, and improve universality. sex and effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
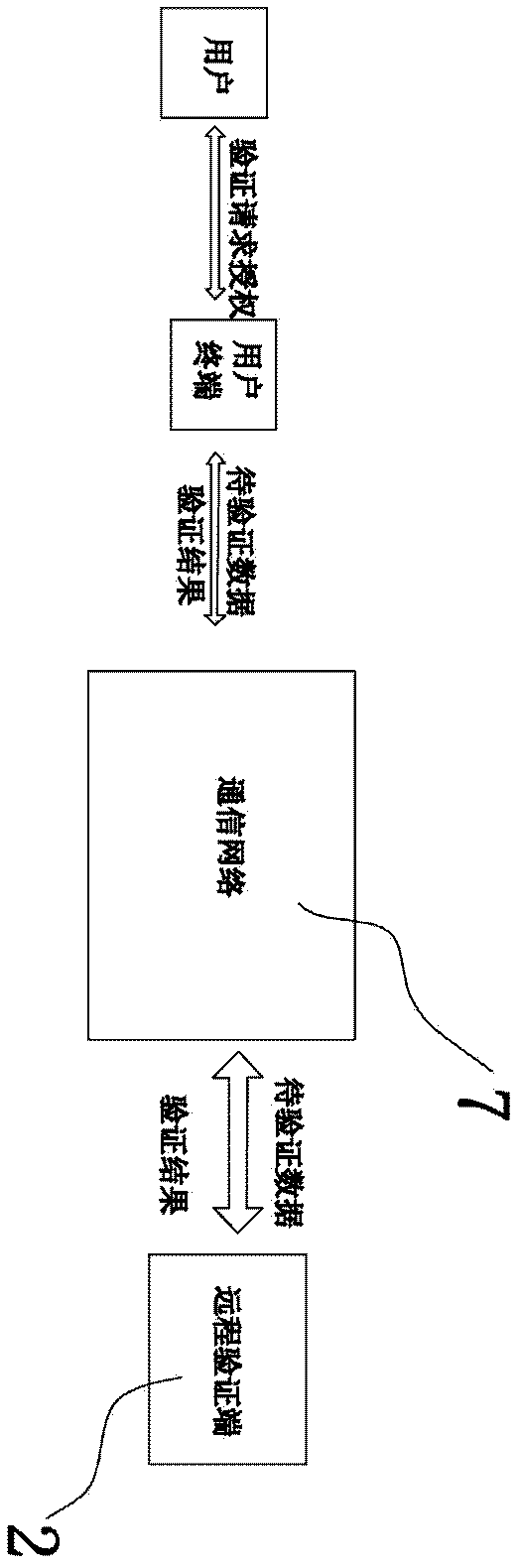
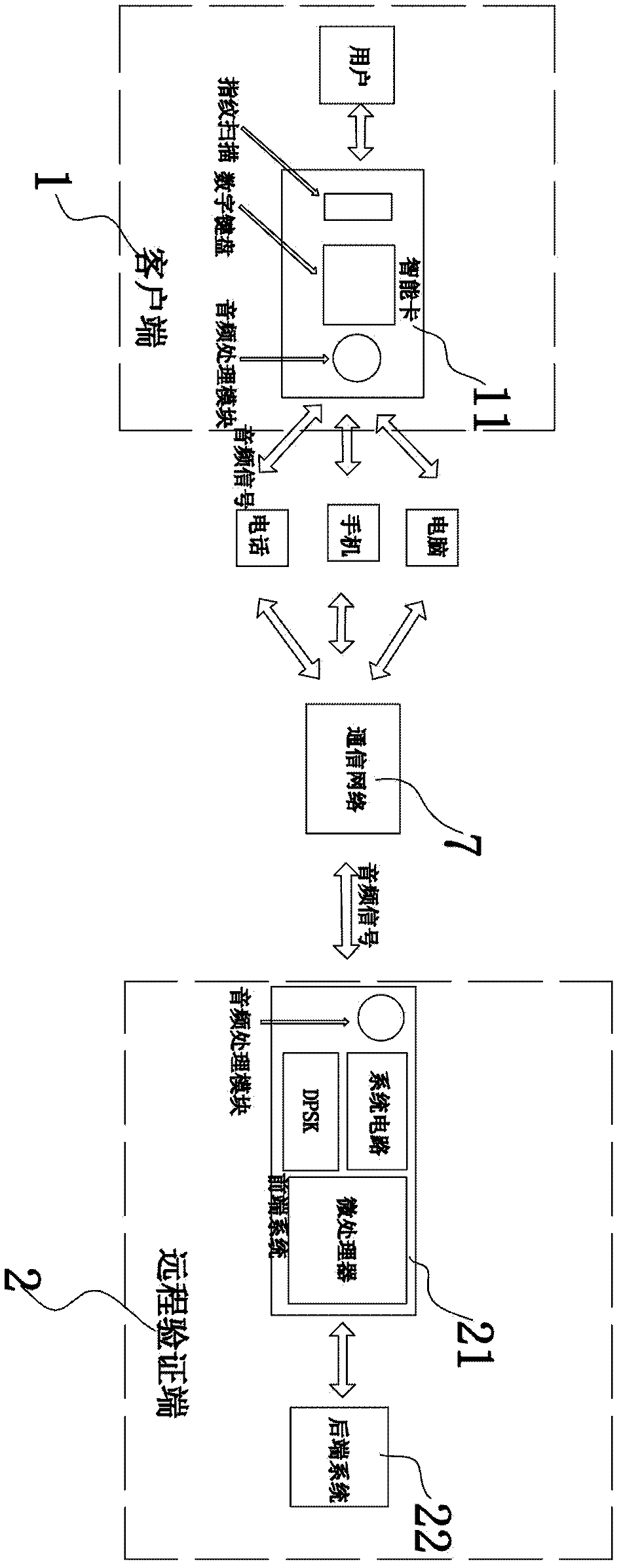
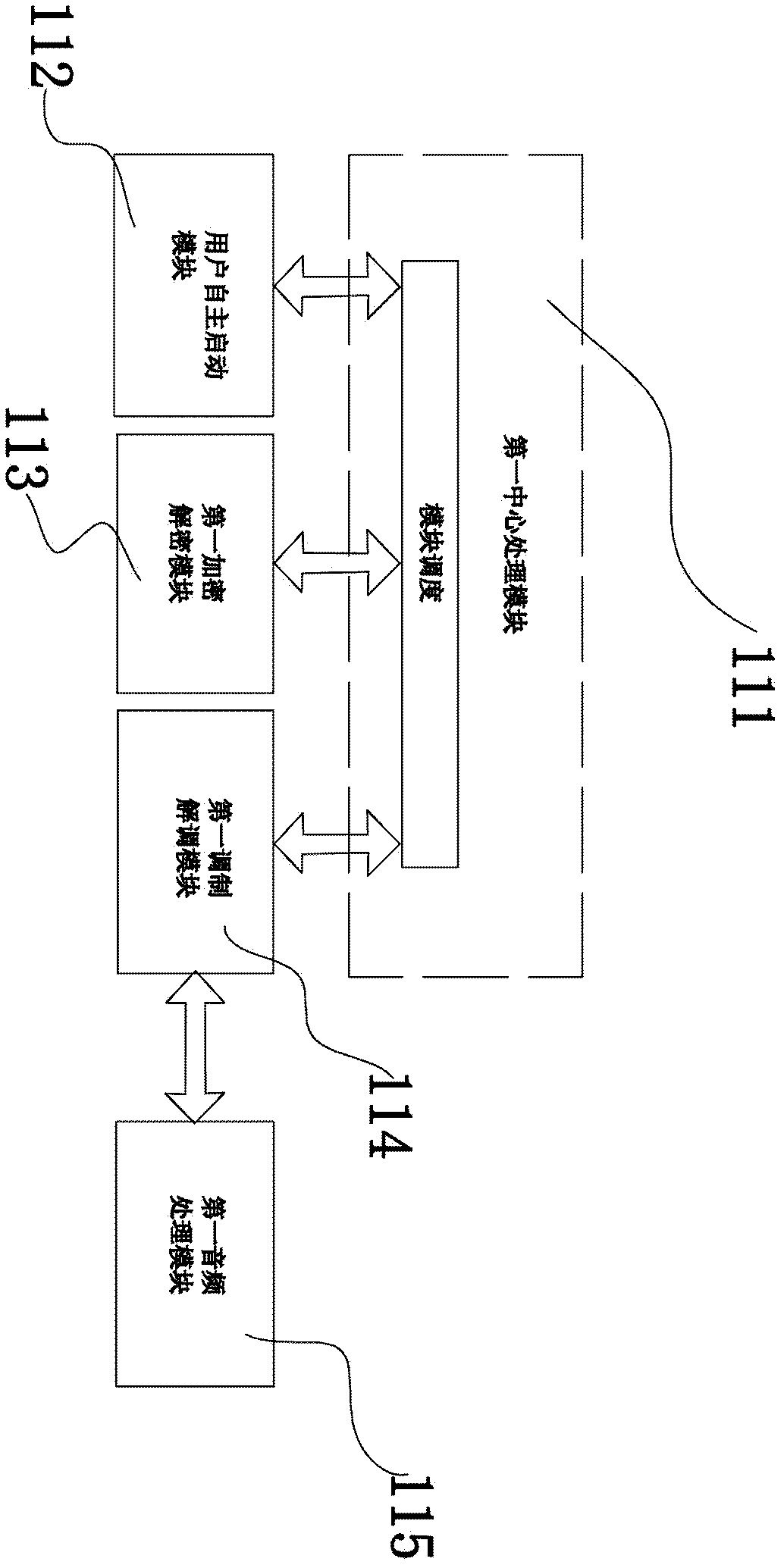
[0049] A pervasive network-oriented remote identity authentication system proposed in this embodiment, such as figure 2 As shown, it includes a user terminal located at the client 1, a back-end system 22 located at the remote verification terminal 2, and a front-end system 21 connected to the back-end system 22. The user terminal adopts a smart card 11, which is a device with audio signal playback , receiving and hardware processing functions of the user card, the smart card 11 can be activated by the user, that is, the user needs to input the user credentials to make the smart card start and take effect. The user credentials can be fingerprint information with high security requirements, or it can be universal Stronger and less expensive user passwords, such that the smart card 11 is similar to a current user authentication terminal, allowing communication only when valid user credentials are entered. The smart card 11 has a paired private key and a public key. The smart car...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com