IOT equipment behavior credibility supervision method based on block chain
A blockchain and behavioral technology, applied in wireless communication, secure communication devices, digital transmission systems, etc., can solve the problems of IoT equipment being easily hijacked, network node denial of service, and damage to network equipment, etc., to avoid network crashes, Satisfy the effect of trust building and promoting mutual cooperation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
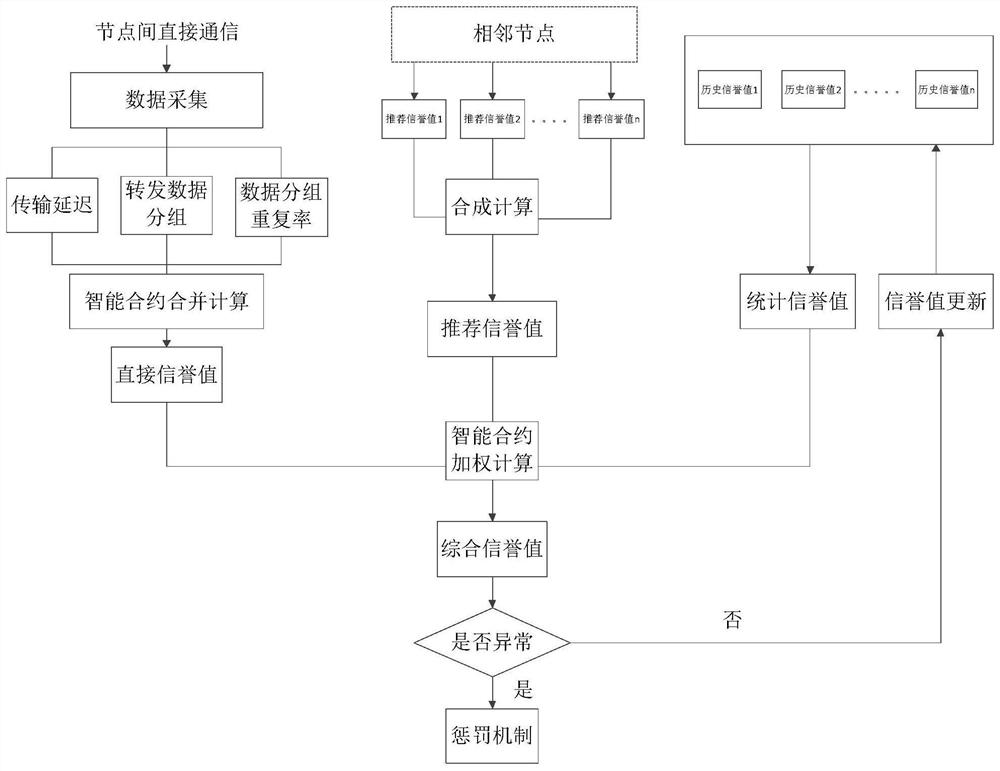
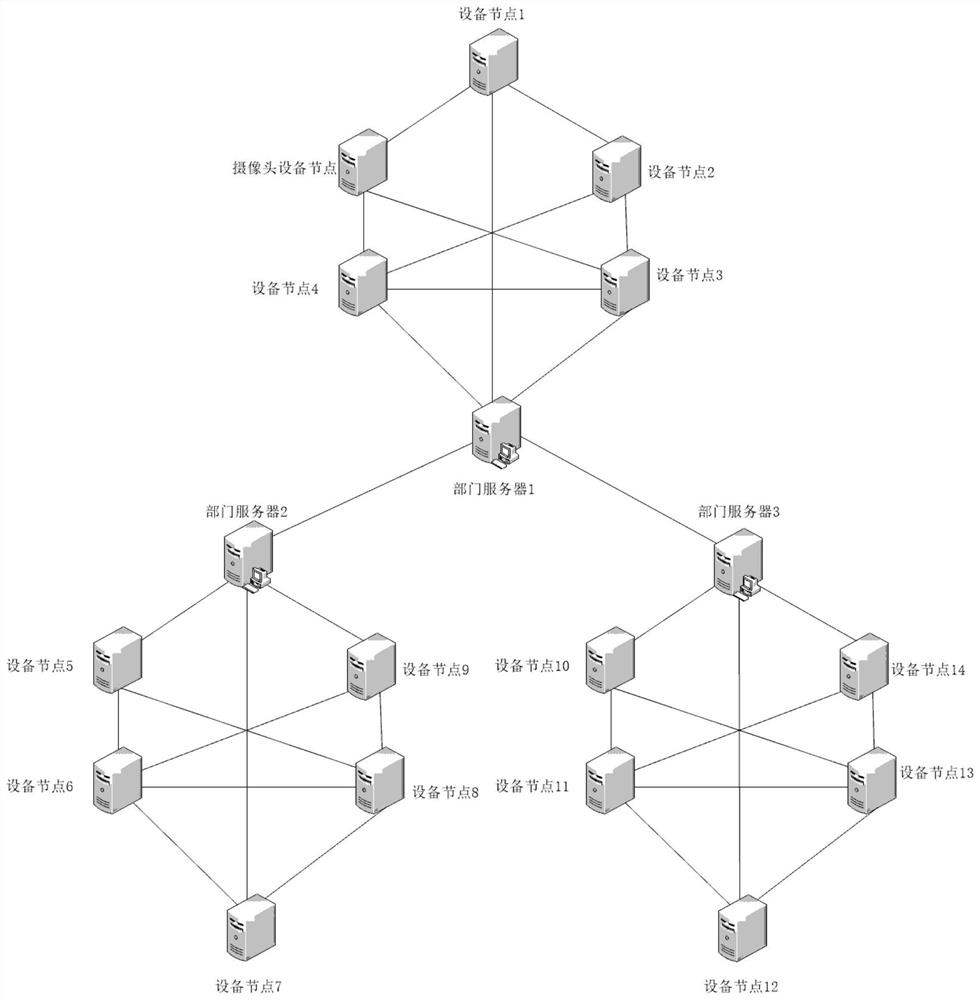
[0022] The implementation process of the present invention will be described below by taking the smart IOT device used in the company's smart office as an example. Suppose the solution includes smart door locks, smart switches, smart sockets, smart lights, smart speakers, smart air conditioners, smart water heaters, smart refrigerators, smart environmental sensors, smart sweeping robots, smart gateways, smart security alarms, cameras and other IOT devices , the communication protocols used by these devices are often very simple and extremely easy to be invaded.
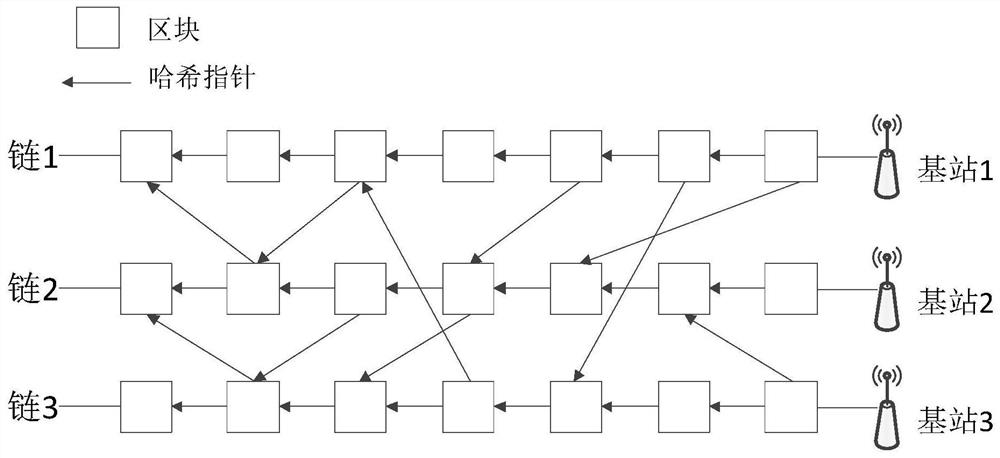
[0023] During the implementation of this plan, the company's internal department classification is used as the standard to divide the company into multiple parts, and each department sets up a server by itself, establishes and maintains a blockchain network, and each department's own The maintained blockchains together form a blockchain architecture based on the DAG directed acyclic graph structure, covering the entir...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com