Side channel attack resistant SM2 dot product architecture based on algorithm layer and operation method thereof
A channel attack and point product technology, applied in the field of cryptography, can solve the problem that the SM2 point product algorithm cannot effectively defend against multiple side channel attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
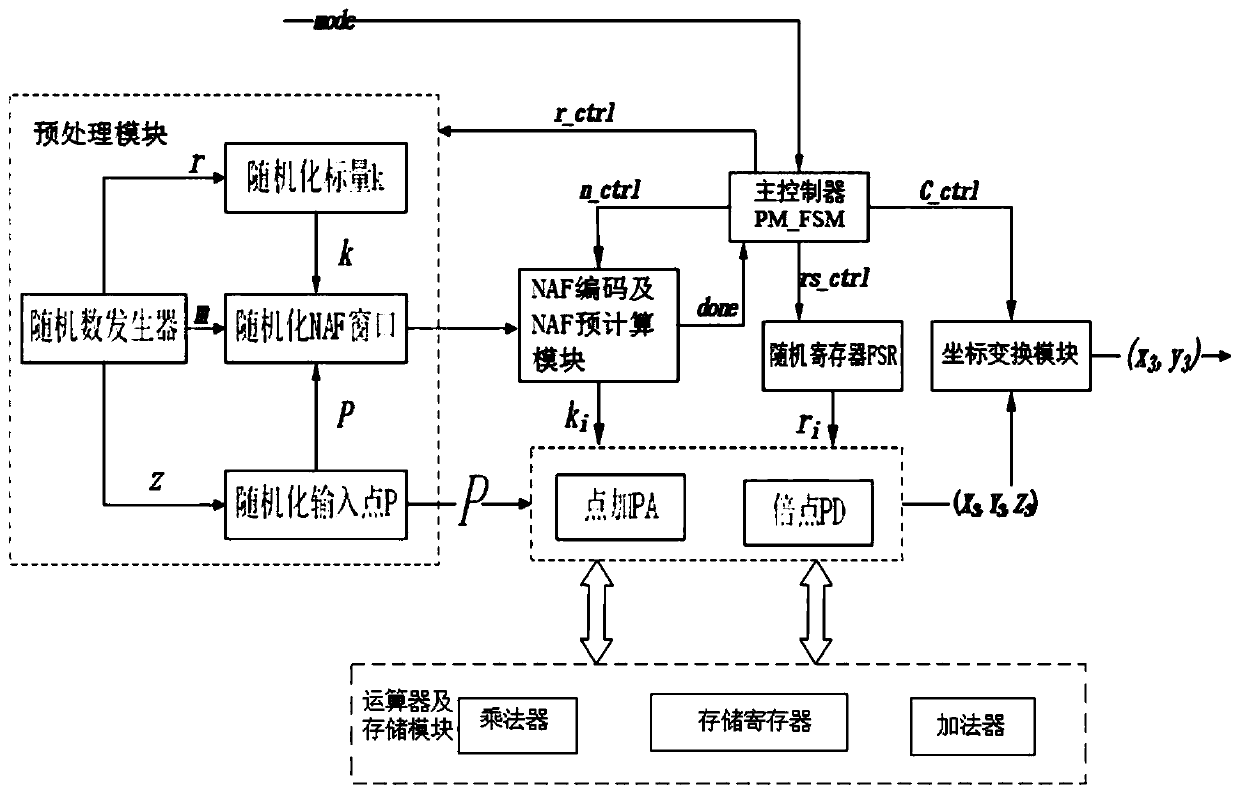
[0054] Anti-side channel attack SM2 point product architecture based on the algorithm layer, such as figure 1 Shown, comprise preprocessing module, main control module, NAF coding and NAF precalculation module, NAF dot product module, random register module, coordinate transformation module, result output module, arithmetic unit and storage module; In the present embodiment, main The control module is the main controller PM_FSM, the random register module is the random register FSR,
[0055] The main controller PM_FSM is used to control the data transmission and operation status among the preprocessing module, NAF encoding and NAF precomputing module, random register FSR, coordinate transformation module, arithmetic unit and storage module, and control the result output module Output the final result;
[0056] The preprocessing module is used to perform randomization processing to generate three kinds of random information, and the random information is generated by a random ...
Embodiment 2
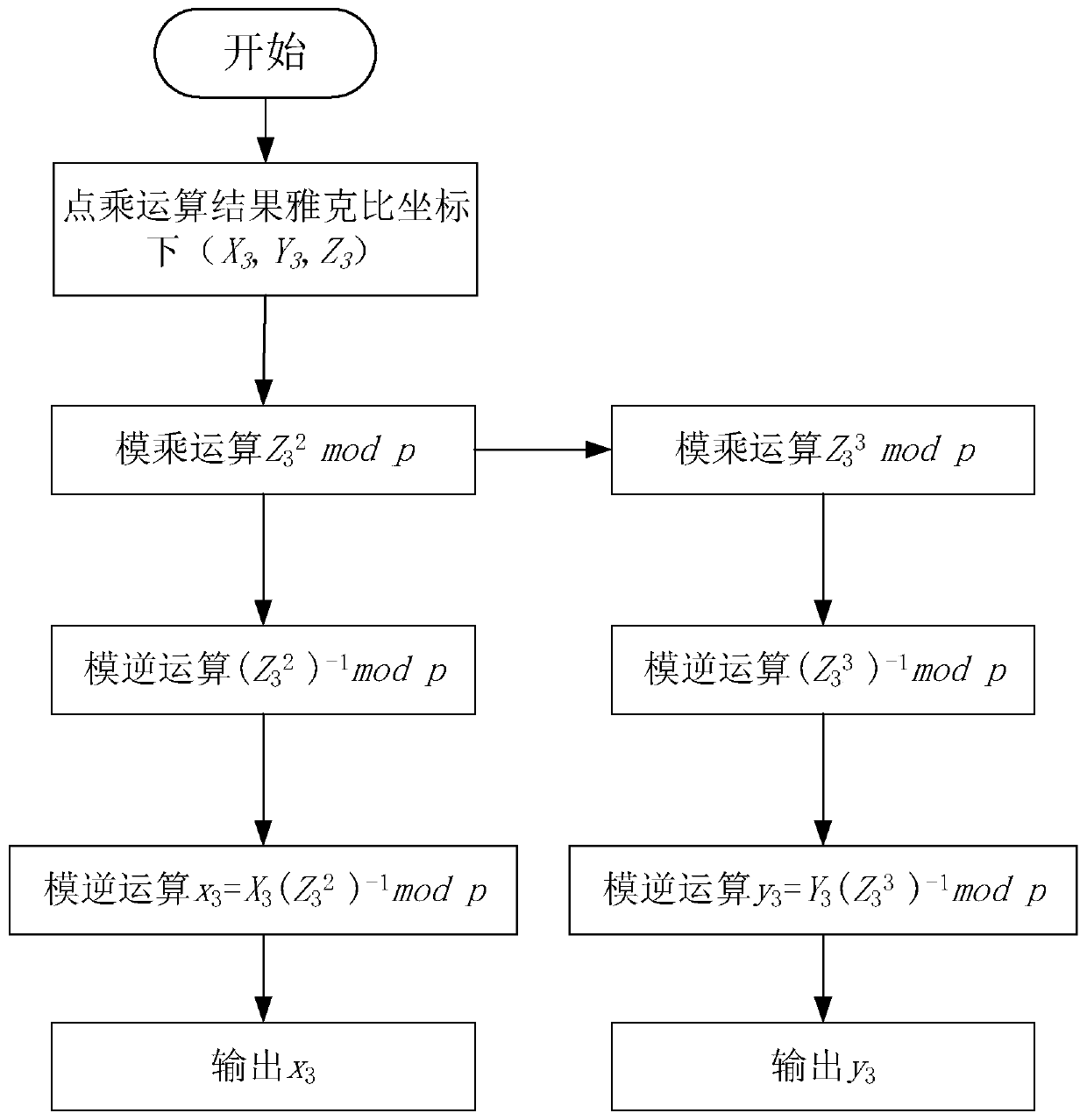
[0079] This embodiment 2 provides a calculation method based on the algorithm layer-based anti-side channel attack SM2 point product architecture of embodiment 1, such as Figure 4 shown, including the following steps:
[0080] S1. After the main controller PM_FSM receives the mode control signal and sends the dot multiplication start command, it uses the r_ctrl signal to start the preprocessing module;
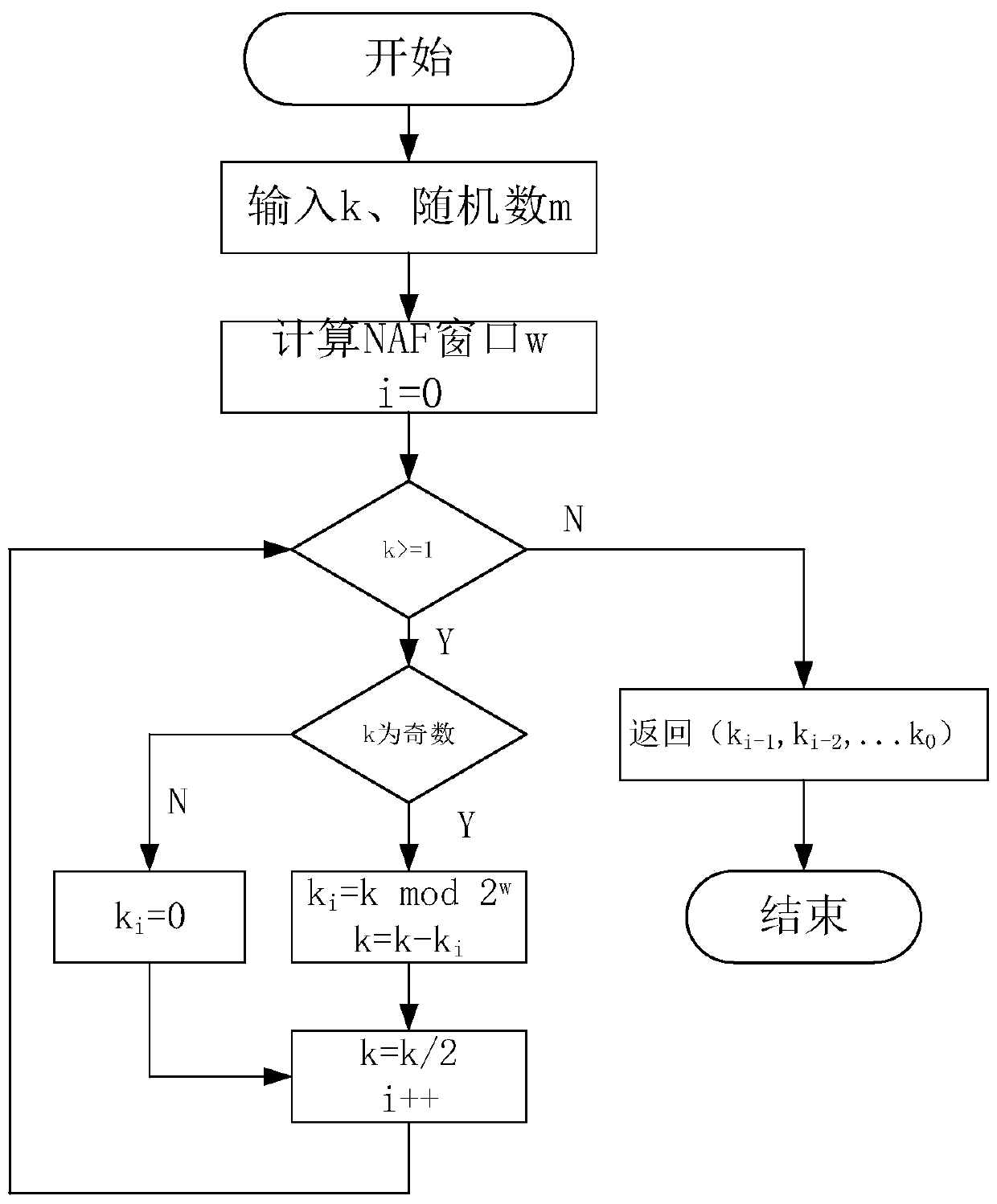
[0081] S2. The preprocessing module randomizes the input of the anti-side-channel attack SM2 point product architecture based on the algorithm layer, including the initial scalar value k, the point product input base point P coordinates falling on the elliptic curve, Random numbers r, z, m, where the base point P is expressed as an equivalent projected coordinate point (xz 2 ,yz 3 , z); Let the randomized scalar value k=k+rN, N be the order of the elliptic curve;
[0082] S3. Determine the randomized NAF window value w=[2,m by the NAF encoding and NAF pre-calculation modul...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com