Equivalent query method for lightweight privacy protection
A technology of privacy protection and query method, which is applied in the direction of public keys for secure communication, digital transmission systems, electrical components, etc., and can solve problems such as potential safety hazards
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
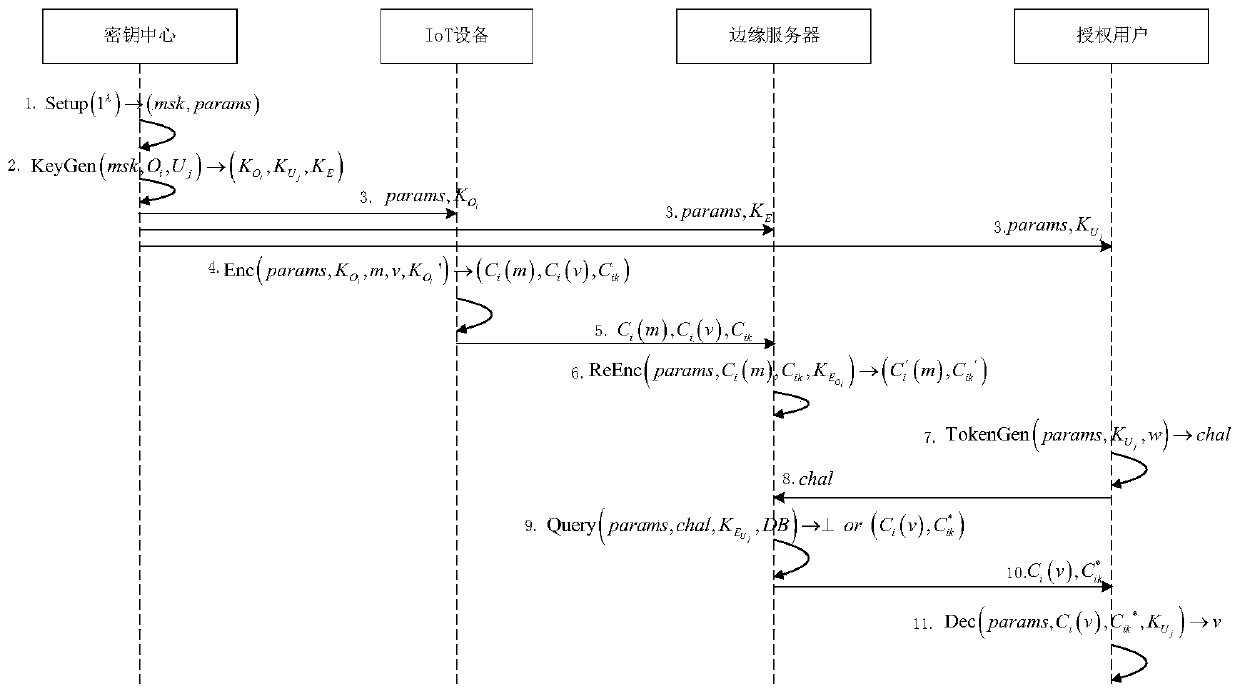
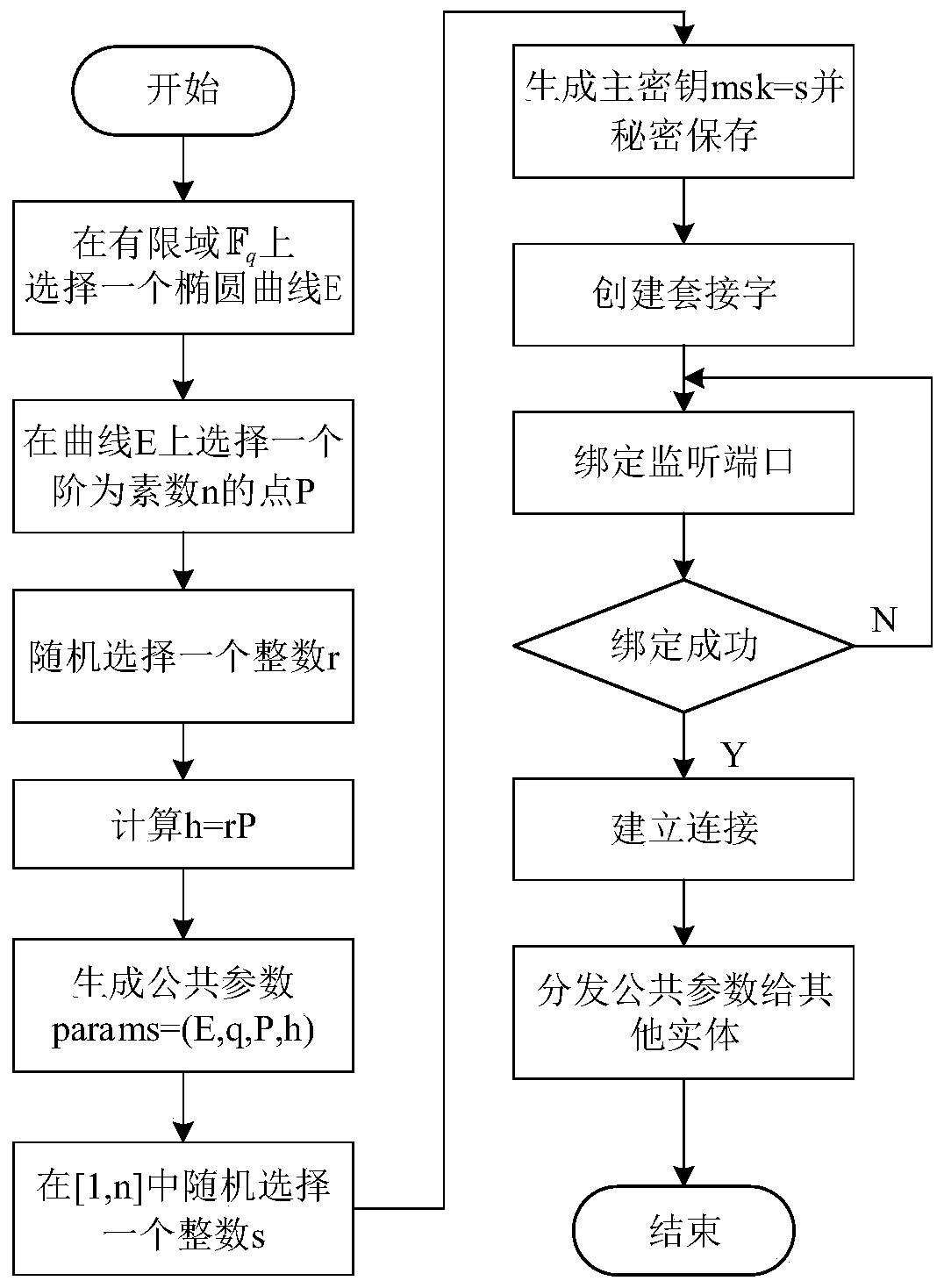
[0053] The technical solution of the present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments, so as to make the technical features and advantages of the present invention more obvious.
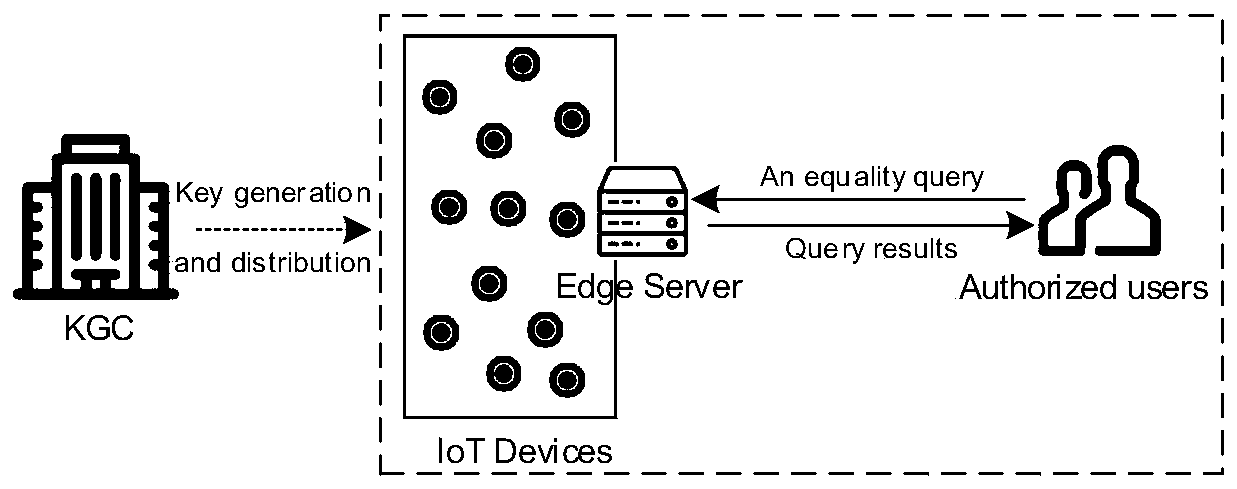
[0054] A light-weight privacy-preserving equivalent query method such as figure 1 As shown, there are four roles including key center, IoT device, edge server, and authorized user:
[0055] Key center: a trusted entity, mainly responsible for the generation and distribution of public parameters and keys, including master keys, keys of data owners and users, computing keys of edge nodes, etc. These processes are performed offline;
[0056] IoT device: a semi-trusted entity. Each device not only has sensing capabilities, but also has communication capabilities. It can be regarded as a data owner, directly contacts with the data source, encrypts the data locally, and then outsources the ciphertext data to nearby edge servers;
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com