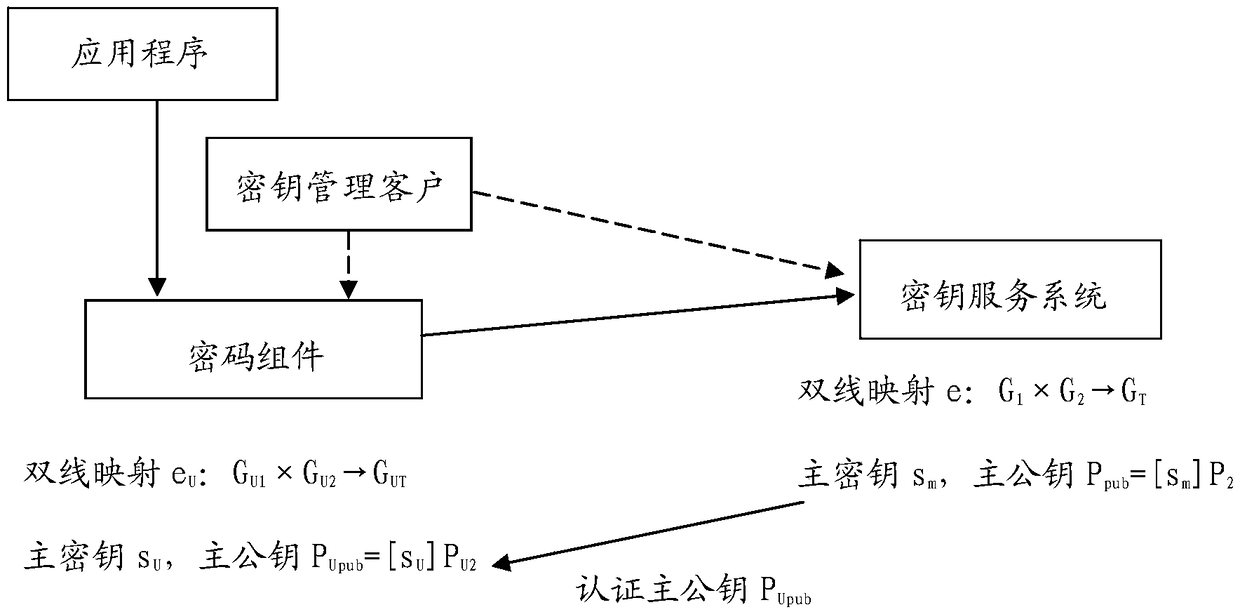
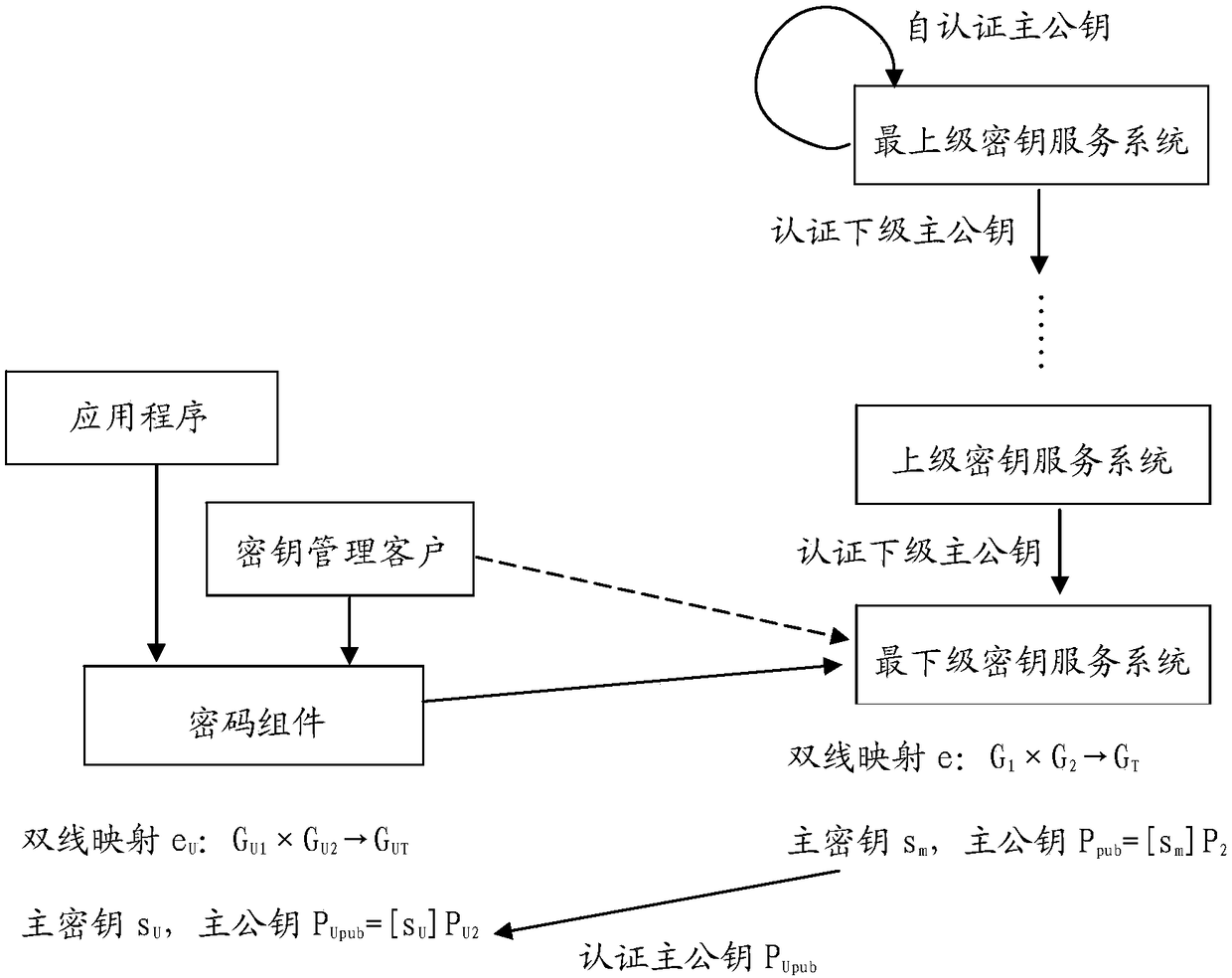
A cryptosystem and digital signature method
A cryptographic system, digital signature technology, applied in the field of cryptography
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The specific implementation of the present invention will be described below.
[0037] (1) Implementation of bilinear mapping (pairing) algorithm and group of bilinear mapping
[0038] There are multiple different bilinear mapping algorithms (pairing algorithm) at present, as Weil pairing, Tate pairing, Ate pairing, R-ate pairing etc., with regard to the present invention, what kind of bilinear mapping algorithm (pairing algorithm) is adopted ) is not limited, as long as the functions of the present invention can be realized.
[0039] The group used in the bilinear mapping (pairing operation) is not limited in the present invention, as long as the group suitable for the bilinear mapping (pairing operation) is used, usually an elliptic curve point group satisfying certain conditions.
[0040] (2) Regarding the implementation of user identification information and key qualification information
[0041] User identification information is information used to identify and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com