Privacy protection method and device based on blockchain smart contract
A smart contract, privacy protection technology, applied in the field of blockchain, to achieve the effect of fast proof and verification process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
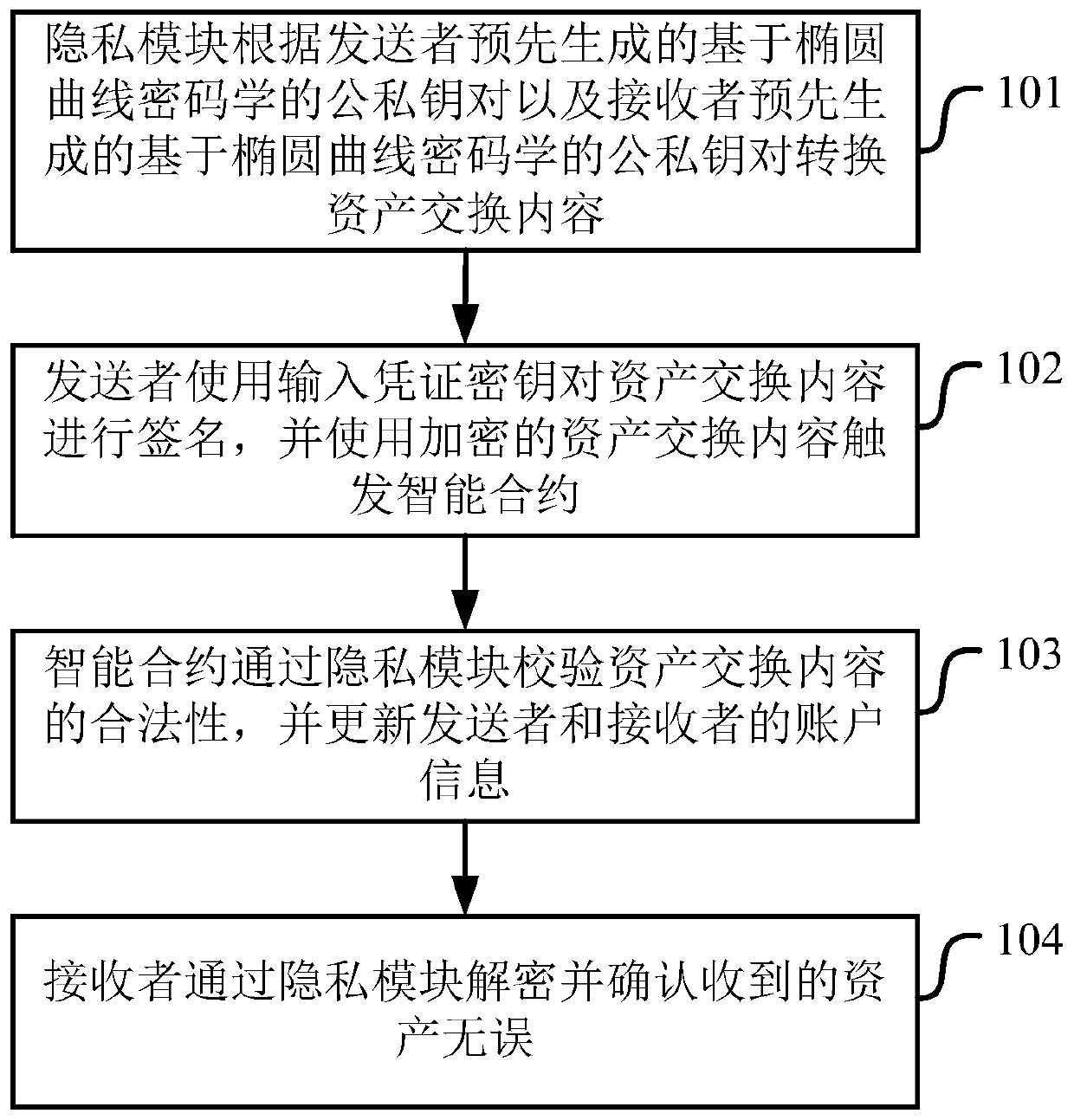
[0038] figure 1 It shows a schematic flowchart of the implementation of the privacy protection method based on the blockchain smart contract in Embodiment 1 of the present application.
[0039] As shown in the figure, the privacy protection method based on blockchain smart contract includes:
[0040] Step 101, the privacy module generates the public-private key pair E(r based on elliptic curve cryptography in advance) 发 , R发 ) and the public-private key pair E(r 收 , R 收 ) to convert asset exchange content; R 发 = r 发 *G,R 收 = r 收 *G, r 发 、r 收 Both are random numbers, and G is a base point on the elliptic curve;
[0041] Step 102, the sender uses the input certificate key S to sign the asset exchange content, and uses the encrypted asset exchange content to trigger the smart contract;
[0042] Step 103, the smart contract verifies the legality of the asset exchange content through the privacy module, and updates the account information of the sender and receiver;
[0...
Embodiment 2
[0071] Based on the same inventive concept, the embodiment of the present application provides a privacy protection device based on a blockchain smart contract. The principle of the device to solve technical problems is similar to a privacy protection method based on a blockchain smart contract. Let me repeat.
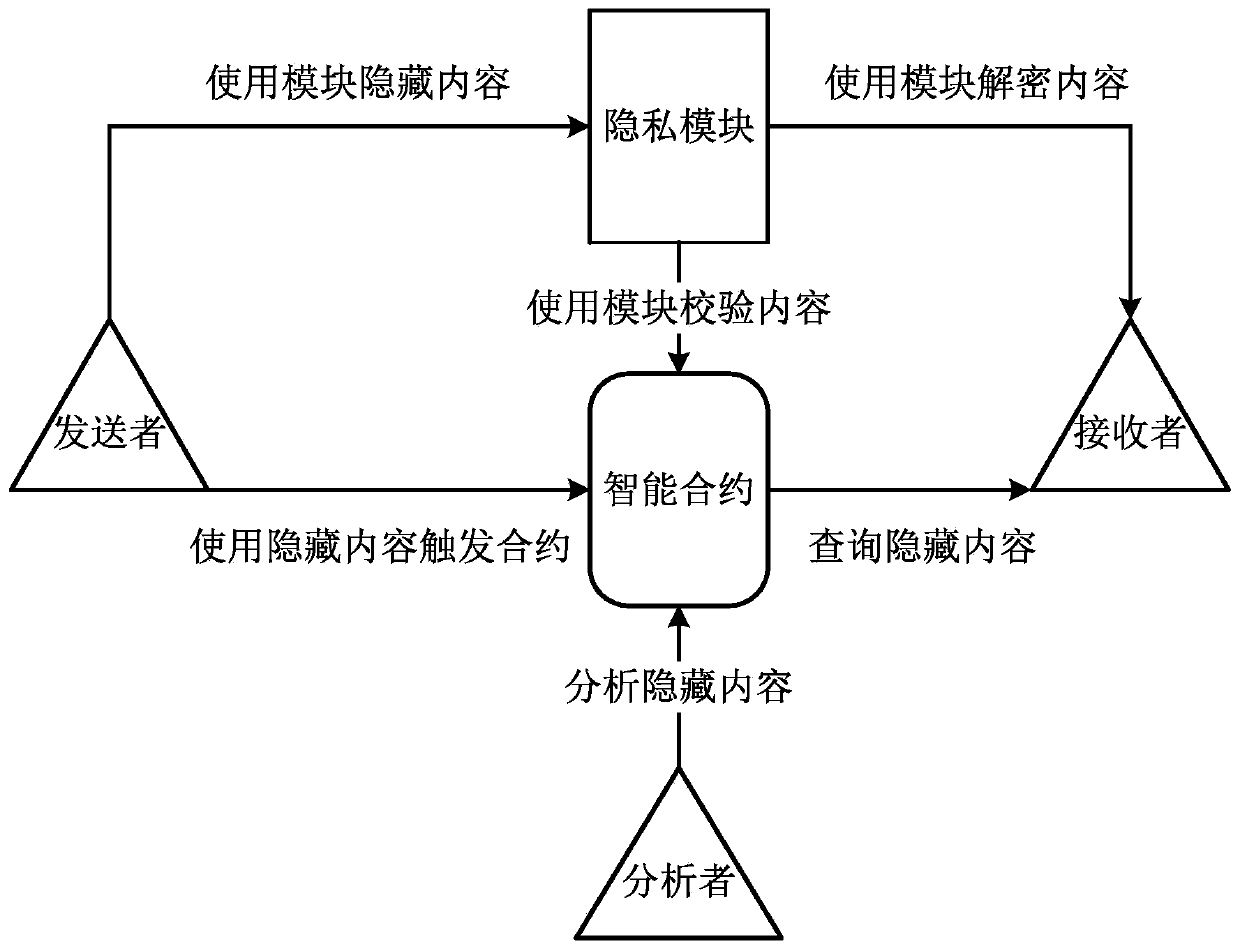
[0072] figure 2 A schematic structural diagram of a privacy protection device based on a blockchain smart contract in Embodiment 2 of the present application is shown.
[0073] As shown in the figure, the privacy protection device based on blockchain smart contract includes:
[0074] The privacy module is used for the public-private key pair E(r 发 , R 发 ) and the public-private key pair E(r 收 , R 收 ) to convert asset exchange content; R 发 = r 发 *G,R 收 = r 收 *G, r 发 、r 收 Both are random numbers, and G is a base point on the elliptic curve;
[0075] The sender module is used to sign the asset exchange content with the input credential key S, and use the encr...
Embodiment 3
[0097] Based on the same inventive concept, an embodiment of the present application further provides a computer storage medium, which will be described below.
[0098] The computer storage medium has a computer program stored thereon, and when the computer program is executed by the processor, the steps of the privacy protection method based on the blockchain smart contract as described in Embodiment 1 are implemented.
[0099] Using the computer storage medium provided in the embodiment of this application, according to the homomorphic nature of the ECC algorithm, it is implemented using simple cryptographic primitives, and can completely hide identity information and asset exchange content information. The asset transfer process does not require interaction between the two parties, proof and The verification process is fast and can be completed within milliseconds.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com