High-performance superscalar elliptic curve cryptographic processor chip
An elliptic curve cryptography and superscalar technology, applied in the field of high-performance elliptic curve cryptographic processor chips, can solve problems such as low performance, low performance, and no support for finite field arithmetic operations, so as to improve processor performance and improve instruction throughput. , the effect of improving the operation speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
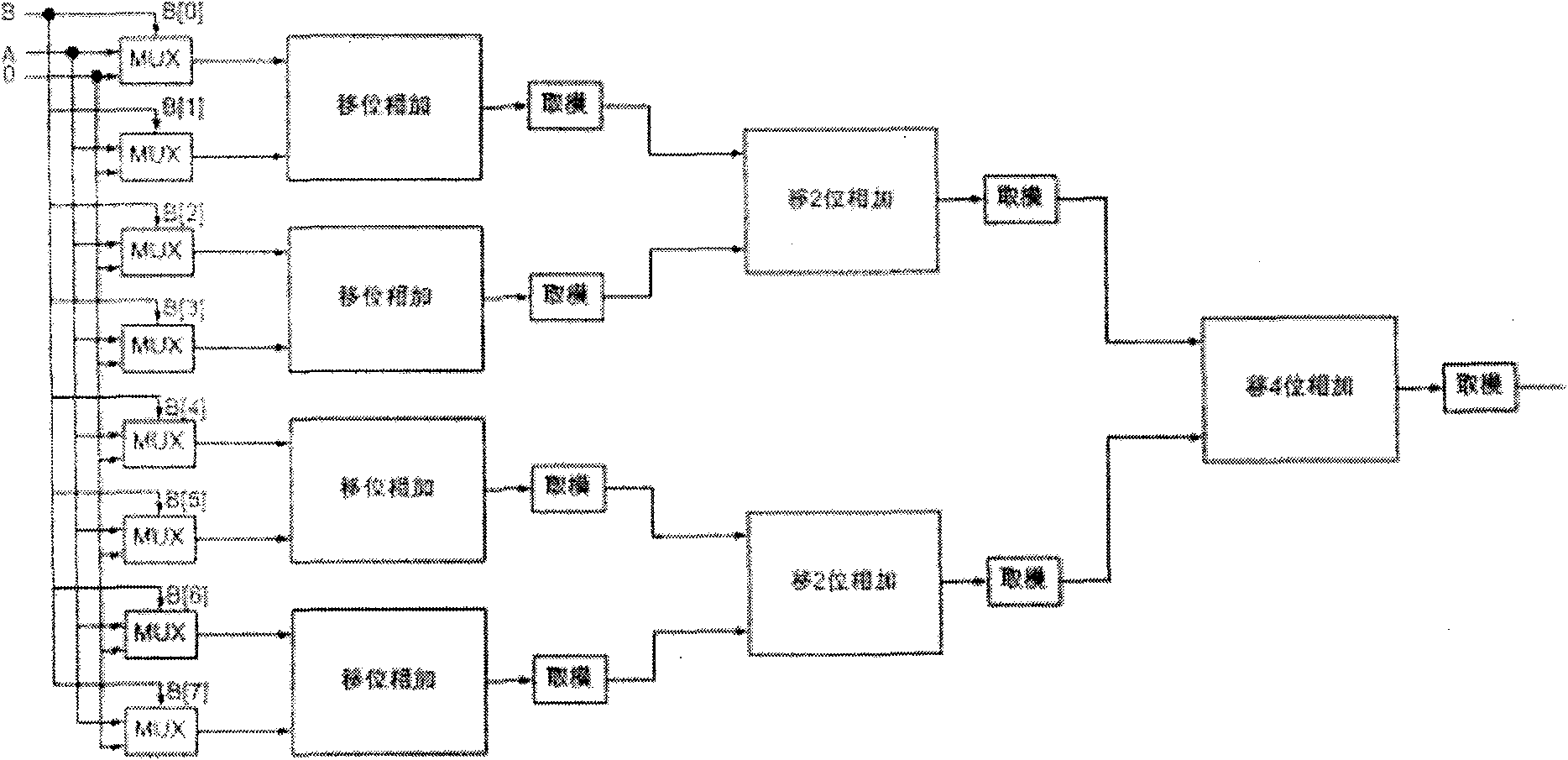
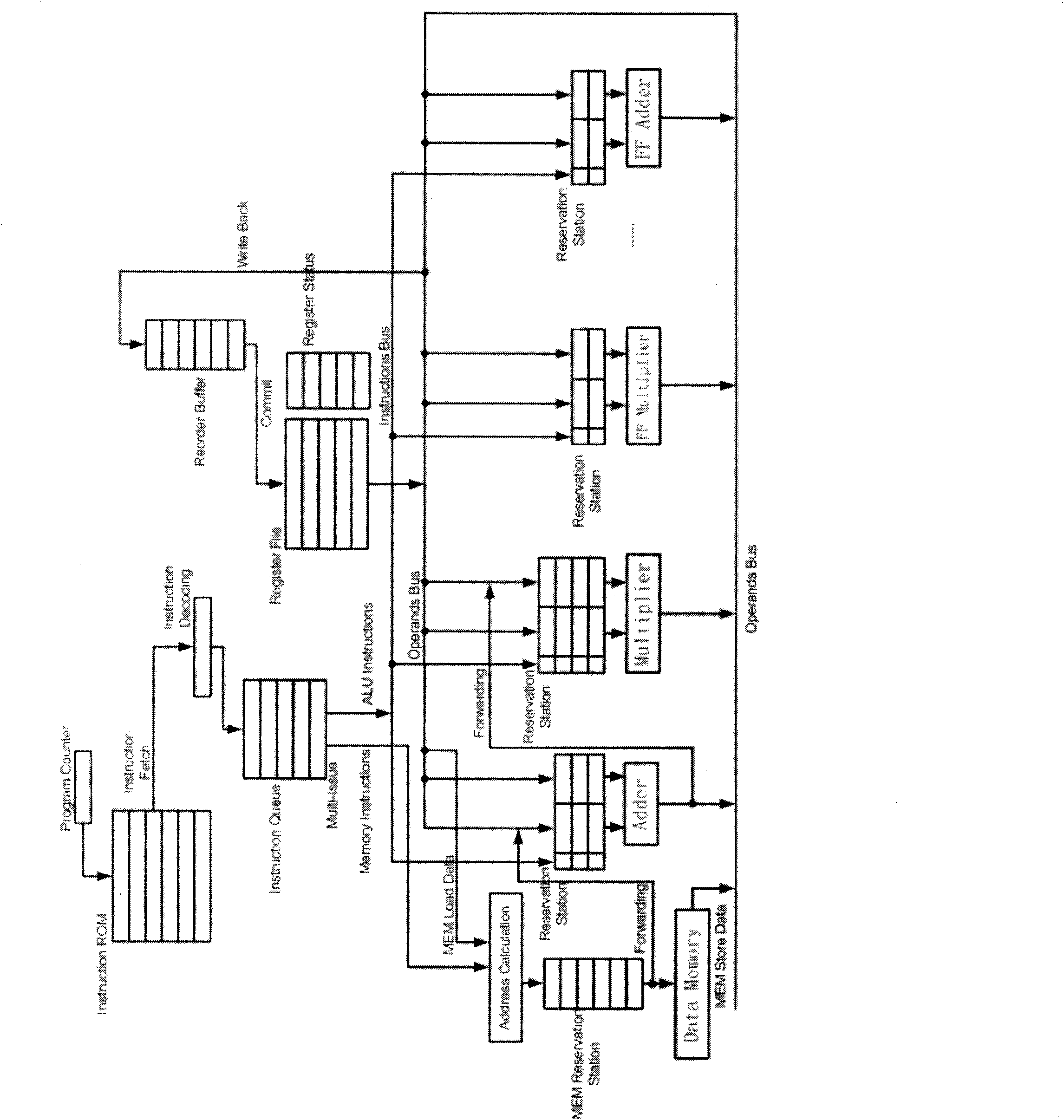
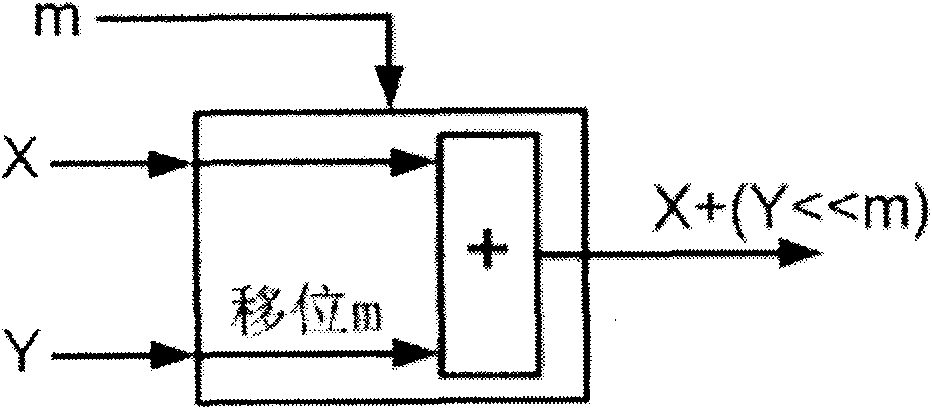
[0034] 1. Elliptic Curve Cryptographic Processor Microarchitecture
[0035] The processor chip designed by the present invention adopts the dynamic instruction scheduling technology with register renaming, and supports Speculation Multi-Issue at the same time. The method adopted by the processor is to adopt the RISC standard 8-stage pipeline, including instruction prefetching (IF, Instruction Fetch), instruction decoding (ID, Instruction Decoding), instruction emission (Issue), and operand fetching (RO, Read Operands), execute instructions (EX, Execution), execution results take effect (Commit), memory read and write (MEM, Memory Access), and register write back (WB, Write Back). Figure 4The overall logic block diagram of the processor pipeline, including instruction queues, data and instruction buses (Data and Instruction Bus), multiple multipliers and adders and their reservation stations (Reservation Station), multiple finite field adders and multipliers and Its reservati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com