Privacy protection efficient aggregation and access control method for power grid data
An access control and privacy protection technology, applied in digital data protection, data processing applications, instruments, etc., can solve problems such as the ineffective utilization of computing resources of edge devices and the difficulty of cloud computing bandwidth resources to meet low-latency transmission, etc. High speed, low value density, and the effect of reducing dependencies
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
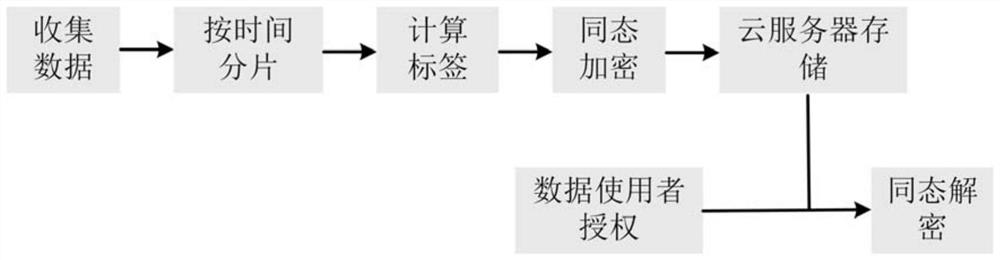
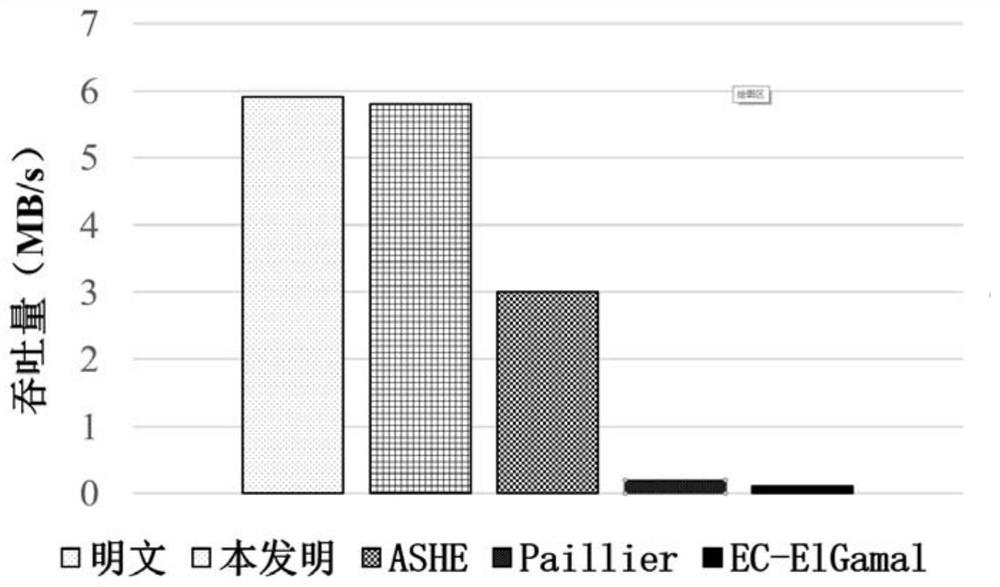
[0034] The present invention improves the existing cloud-based privacy protection data aggregation scheme, and proposes a power grid data privacy protection aggregation method based on edge computing to protect power grid data, and at the same time realizes power grid data security through a fine-grained access control method shared. When a data user requests to access data, the invention can support low-latency data processing and improve the throughput of system data processing.
[0035] The present invention comprises the following steps:
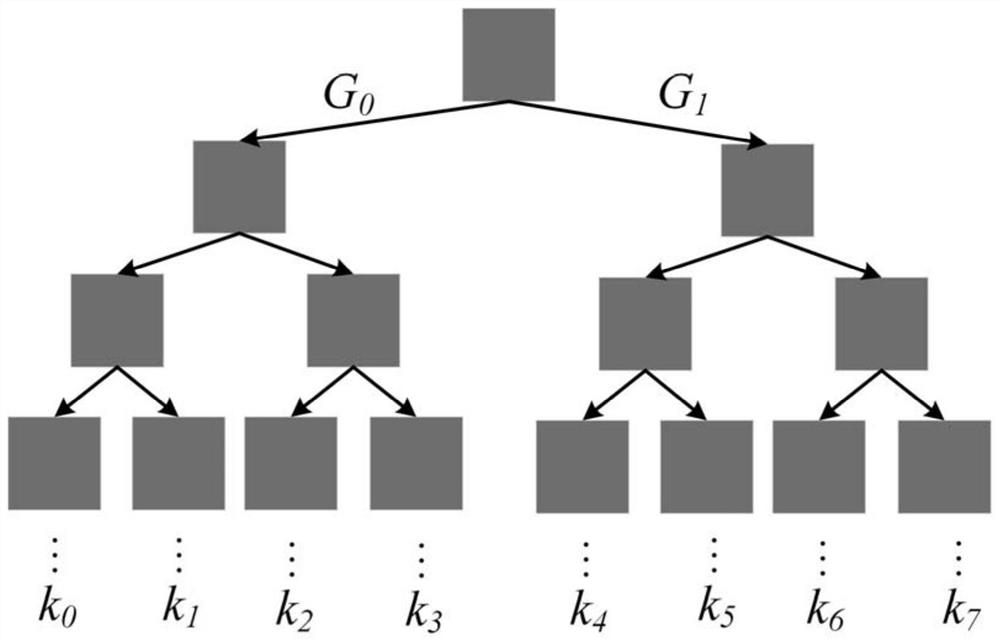
[0036] Step 1: The smart terminal uses the pseudo-random number generator and the master key to generate all n key sequences k required within a fixed period of time (for example, one hour) 1 ,...,k n+1 .
[0037] Step 2: The intelligent terminal divides the data generated during the time period into n independent data blocks according to the time segment, and calculates the data aggregation summary (such as summation and average valu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com