Data hiding query security sharing system and method based on multi-party security computing
A security and data technology, applied in the field of big data technology and cryptography
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0057] Assume that institution A is the main institution, institution B is the data asset institution, the main institution is the data query initiator, and the data asset institution is the data provider.
[0058] Step 1: Through two-two handshakes between system institutions, the sharing of public key information between institutions and the two-two privacy interaction of private keys are realized. The detailed steps are as follows:
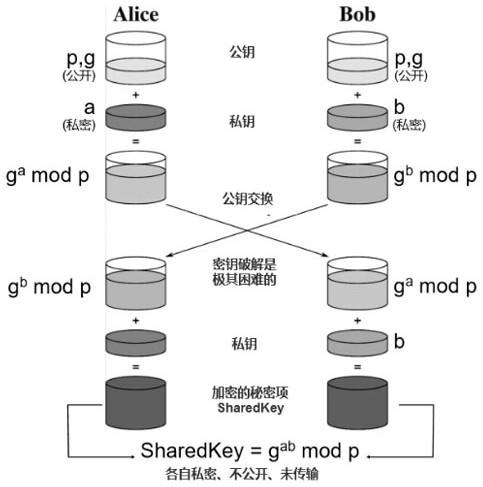
[0059] Step 1.1: Subject institution A generates a dynamic public key. The public key information of one inter-organization is randomly and dynamically generated by the main institution A. In order to improve the security of the data sharing system, the public key meets the requirement of 256 bytes, and the public key information changes dynamically. The change period is generated by a random number, such as 5 minutes Change once. Assume that the public key information between the main institution A and the data asset institution B is p.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com