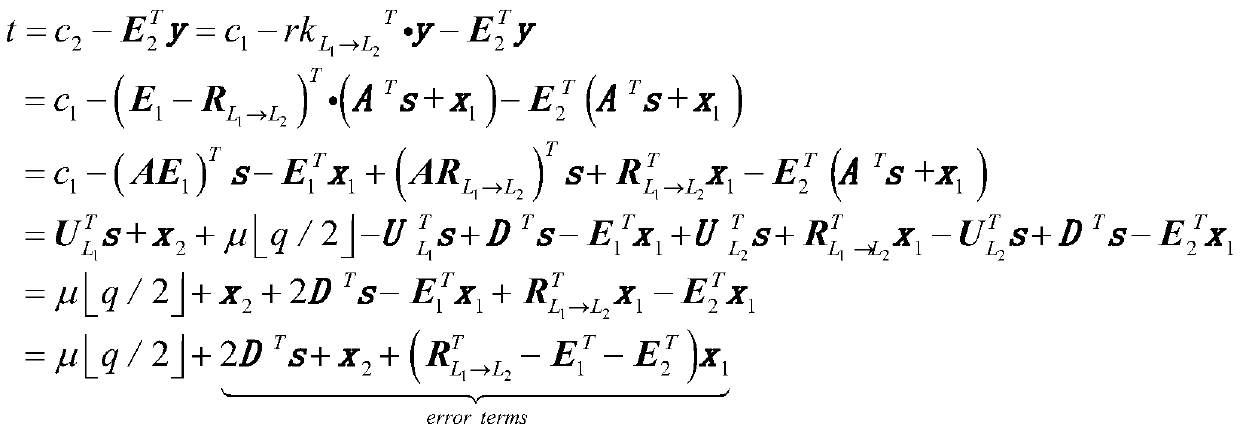Attribute-based anti-collusion attack proxy re-encryption method
A technology of proxy re-encryption and collusion attack, which is applied in the countermeasures of attacking encryption mechanism, the usage of multiple keys/algorithms, and the public key of secure communication. attack and other issues, to achieve the effect of safe sharing and guarantee safe sharing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
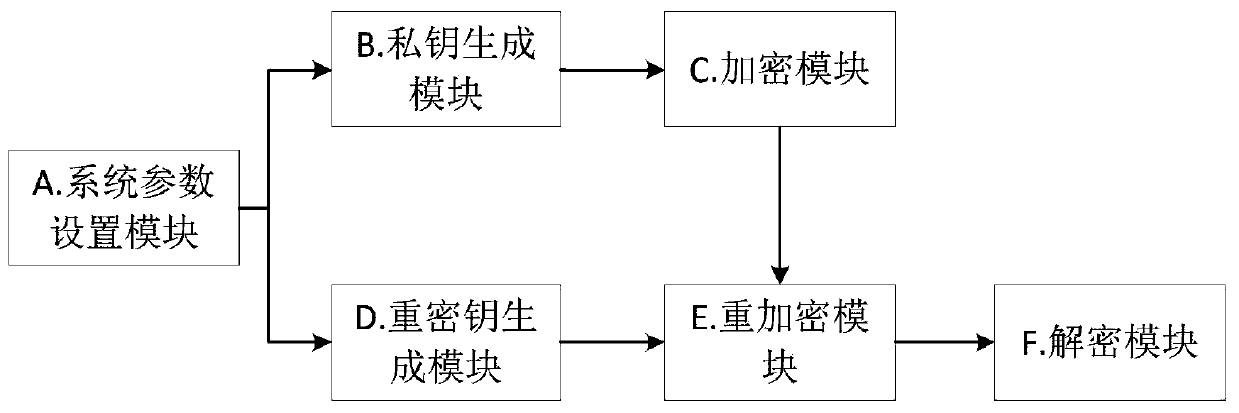
[0040] The attribute-based proxy re-encryption method provided in this embodiment includes the following six modules:
[0041] 1. System parameter setting module Setup(1 n ): Enter security parameter 1 n , to generate a system public parameter params and a master private key MSK.
[0042] 2. Private key generation module KeyGen(params,MSK,L): For an attribute list L, input params and MSK to generate a private key SK L and the corresponding public key PK L .
[0043] 3. The encryption module Encrypt(params,L,PK L ,(W,ρ),M): input params, L, PK L , accessing the structure (W, ρ) and the message M, the algorithm returns a ciphertext
[0044] 4. Re-key generation module Enter params, attribute list L 1 , L 2 and the property list L 1 key of The algorithm returns the re-encryption key
[0045] 5. Re-encryption module Enter params, New access structure (W',ρ') and property list L 1 corresponding ciphertext The algorithm returns L after re-encryption 2 corre...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com