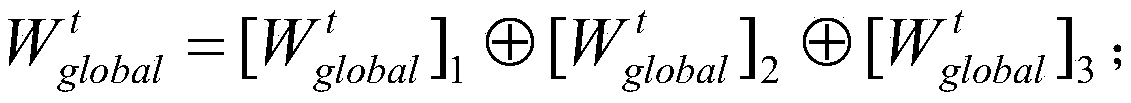Data security sharing method, storage medium and computing equipment
A technology of data security and local data, applied in patient-specific data, medical data mining, computer-aided medical procedures, etc., can solve problems such as not considering evil, leaking data privacy, not considering collaborative learning, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
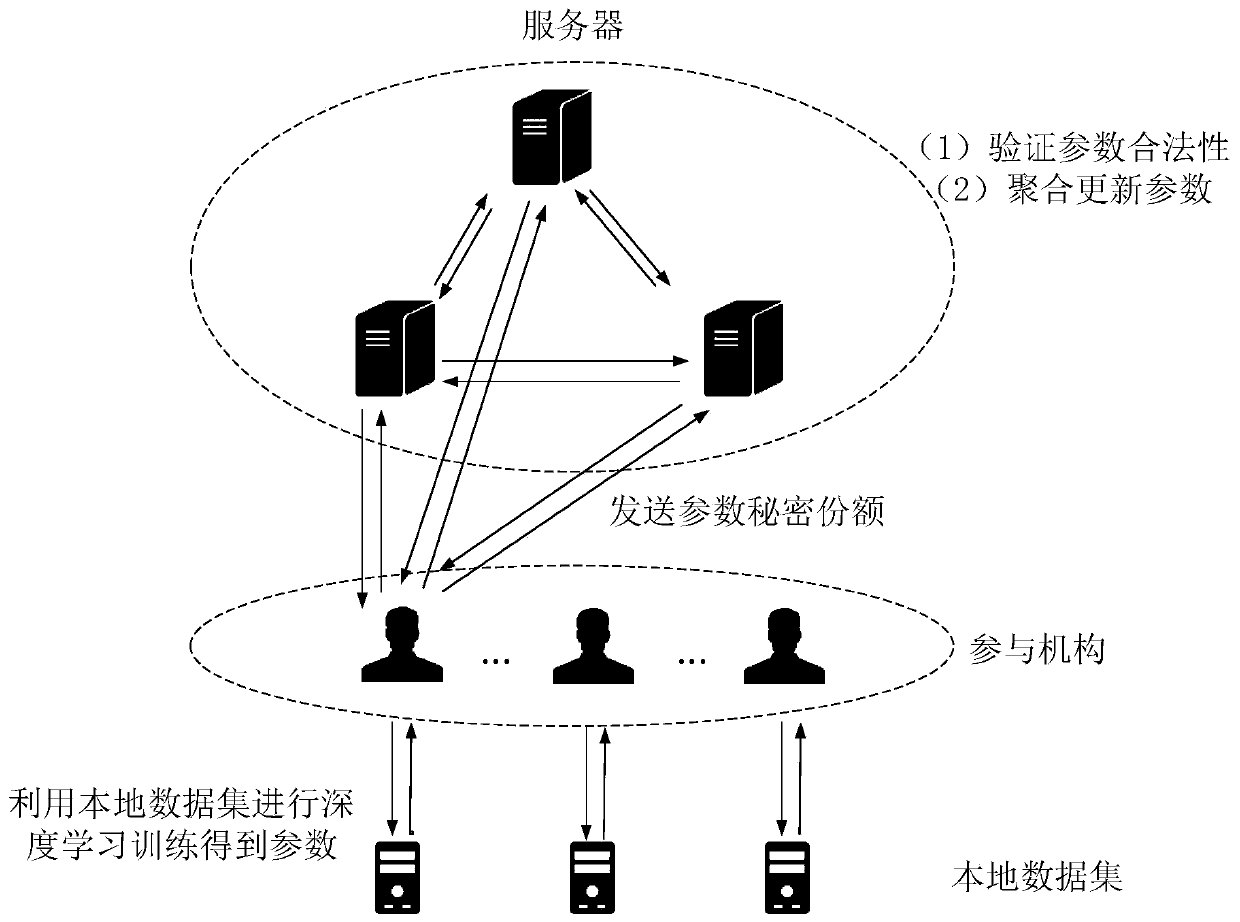
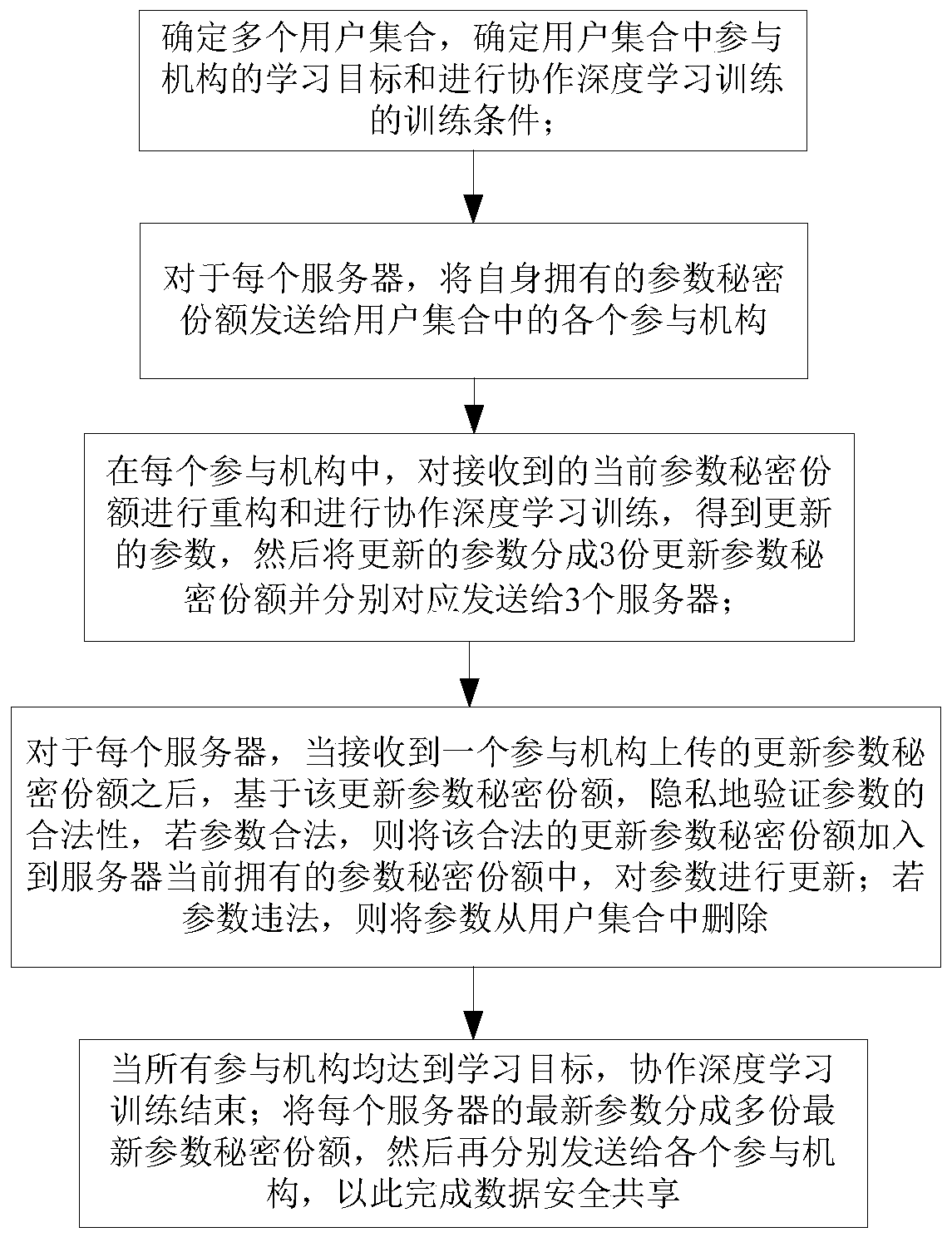
[0061] This embodiment discloses a data security sharing method, such as figure 1 with figure 2 shown, including the following steps:
[0062] S1. Multiple user sets Ω are determined, and each user set includes multiple participating organizations that communicate with the three servers.
[0063] Identify learning objectives for participating institutions and training conditions for collaborative deep learning training.
[0064] Among them, the participating institutions have local data sets and server environments for local collaborative deep learning training. The local data sets have local data with classification labels. Invalid model parameters can be uploaded during the process. In this embodiment, the participating institutions are medical institutions, the local data is medical image data, and each medical image carries a corresponding disease classification label. The learning objective of participating institutions is to train a model to classify diseases.
[0...
Embodiment 2
[0106] This embodiment discloses a storage medium that stores a program, and when the program is executed by a processor, implements the data security sharing method described in Embodiment 1, specifically as follows:
[0107] S1. Determine multiple user sets Ω, each user set includes multiple participating organizations that communicate with 3 servers;
[0108] Identify learning objectives for participating institutions and training conditions for collaborative deep learning training;
[0109] S2. For each server, send the parameter secret share owned by itself to each participating organization in the user set;
[0110] S3. In each participating organization, reconstruct the received current parameter secret shares and carry out collaborative deep learning training to obtain updated parameters, and then divide the updated parameters into 3 update parameter secret shares and send them to 3 respectively server;
[0111] S4. For each server, after receiving the update paramet...
Embodiment 3
[0116] This embodiment discloses a computing device, including a processor and a memory for storing a program executable by the processor. When the processor executes the program stored in the memory, it implements the data security sharing method described in Embodiment 1, specifically as follows :
[0117] S1. Determine multiple user sets Ω, each user set includes multiple participating organizations that communicate with 3 servers;
[0118] Identify learning objectives for participating institutions and training conditions for collaborative deep learning training;
[0119] S2. For each server, send the parameter secret share owned by itself to each participating organization in the user set;
[0120] S3. In each participating organization, reconstruct the received current parameter secret shares and carry out collaborative deep learning training to obtain updated parameters, and then divide the updated parameters into 3 update parameter secret shares and send them to 3 res...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com