User data authorization method, device and system
A user data and user technology, applied in the field of network services, can solve problems such as reducing the user's experience of online game services, failing to satisfy users, and failing to realize user authorization for third-party use.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
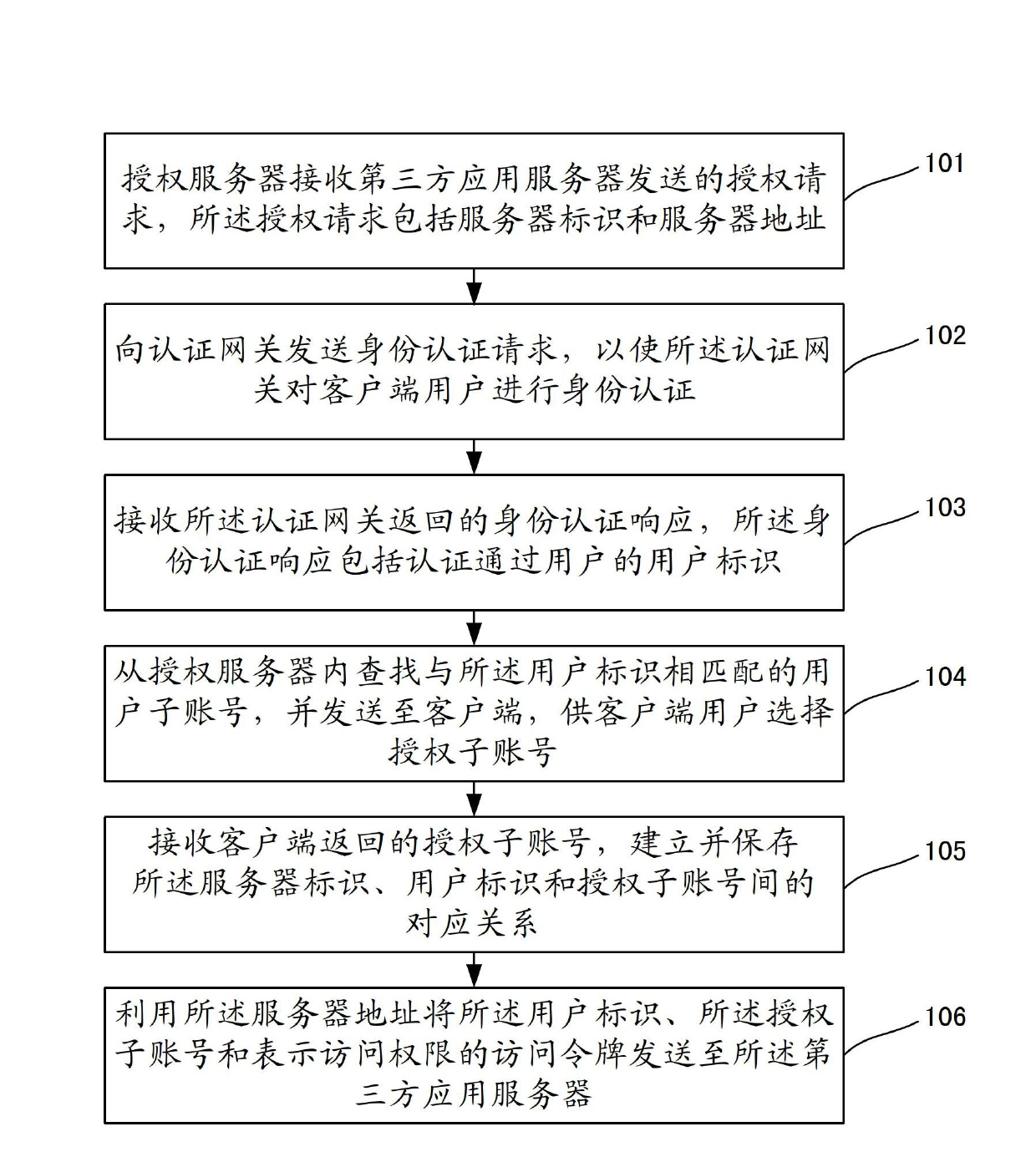
[0117] see figure 1 , which shows a flow chart of Embodiment 1 of a user data authorization method of the present invention, which may include the following steps:
[0118] Step 101, the authorization server receives an authorization request sent by a third-party application server, and the authorization request includes a server identifier and a server address.
[0119] If user A registers a user account on the platform of the game service provider, and creates three sub-accounts under the user account at the same time, they are game character A 1 、A 2 and A 3 (the game role can be embodied as the game identification, game area identification, game group identification and game role identification that each role has), then these data are stored in the platform of the game service provider. In addition, if the platform of the game service provider is opened to two third parties B 1 and B 2 , that is to say the third party B 1 and B 2 After completing the registration on...
Embodiment 2
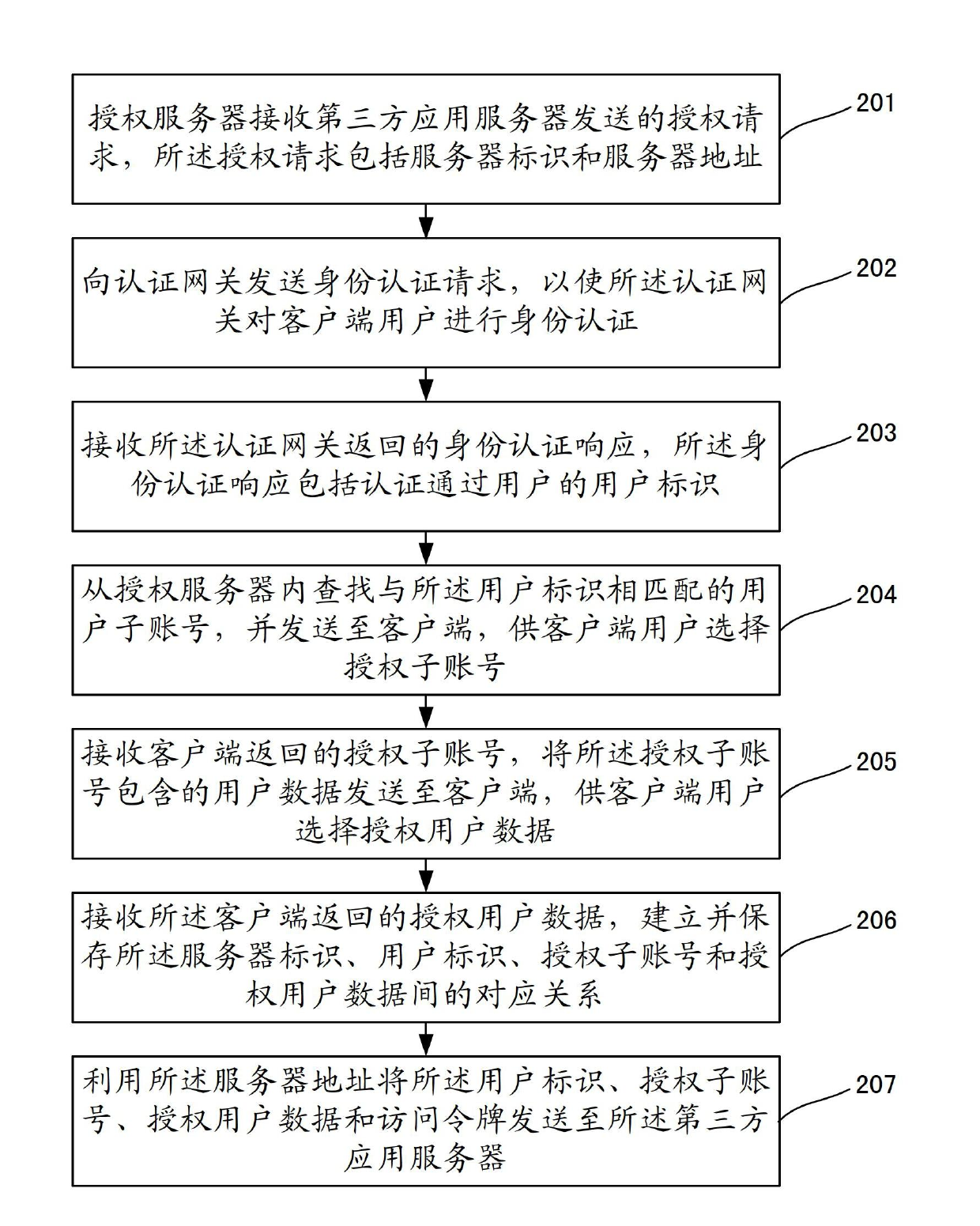
[0143] On the basis of Embodiment 1, the present invention further refines the authorization granularity for the third party, and uses the user data corresponding to the sub-account as a unit to authorize the use of the third party. see figure 2 , which shows a flow chart of Embodiment 2 of a user data authorization method of the present invention, which may include the following steps:
[0144] In step 201, the authorization server receives an authorization request sent by a third-party application server, and the authorization request includes a server identifier and a server address.
[0145] Step 202, sending an identity authentication request to the authentication gateway, so that the authentication gateway performs identity authentication on the client user.
[0146] Step 203: Receive an identity authentication response returned by the authentication gateway, where the identity authentication response includes the user identifier of the authenticated user.
[0147] St...
Embodiment 3
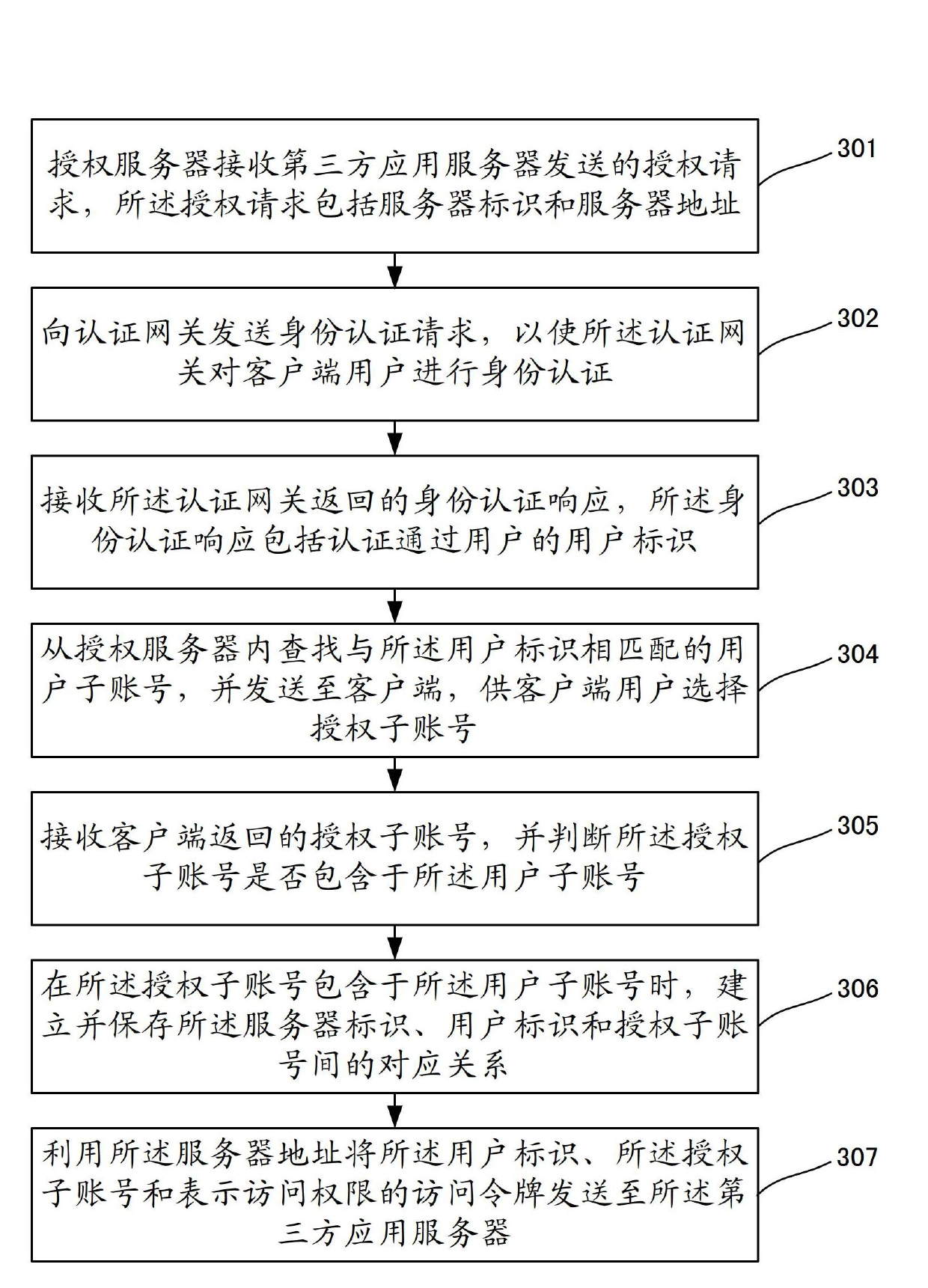
[0156] In order to improve authorization reliability and prevent users' authorization behavior from being maliciously tampered with, see image 3 , which shows a flow chart of Embodiment 3 of a user data authorization method of the present invention, which may include the following steps:
[0157] In step 301, the authorization server receives an authorization request sent by a third-party application server, and the authorization request includes a server identifier and a server address.
[0158] Step 302, sending an identity authentication request to the authentication gateway, so that the authentication gateway performs identity authentication on the client user.
[0159] Step 303: Receive an identity authentication response returned by the authentication gateway, where the identity authentication response includes the user identifier of the authenticated user.
[0160] Step 304, searching for a user sub-account matching the user ID from the authorization server, and sendi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com