Security protection method and security protection system for mobile terminal application
A mobile terminal and security protection technology, applied in security devices, electrical components, wireless communications, etc., can solve problems such as poor security, insufficient use of SIM card number device binding, legitimate users cannot be detected and protected in time, and improve Effects of Safety and Convenience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
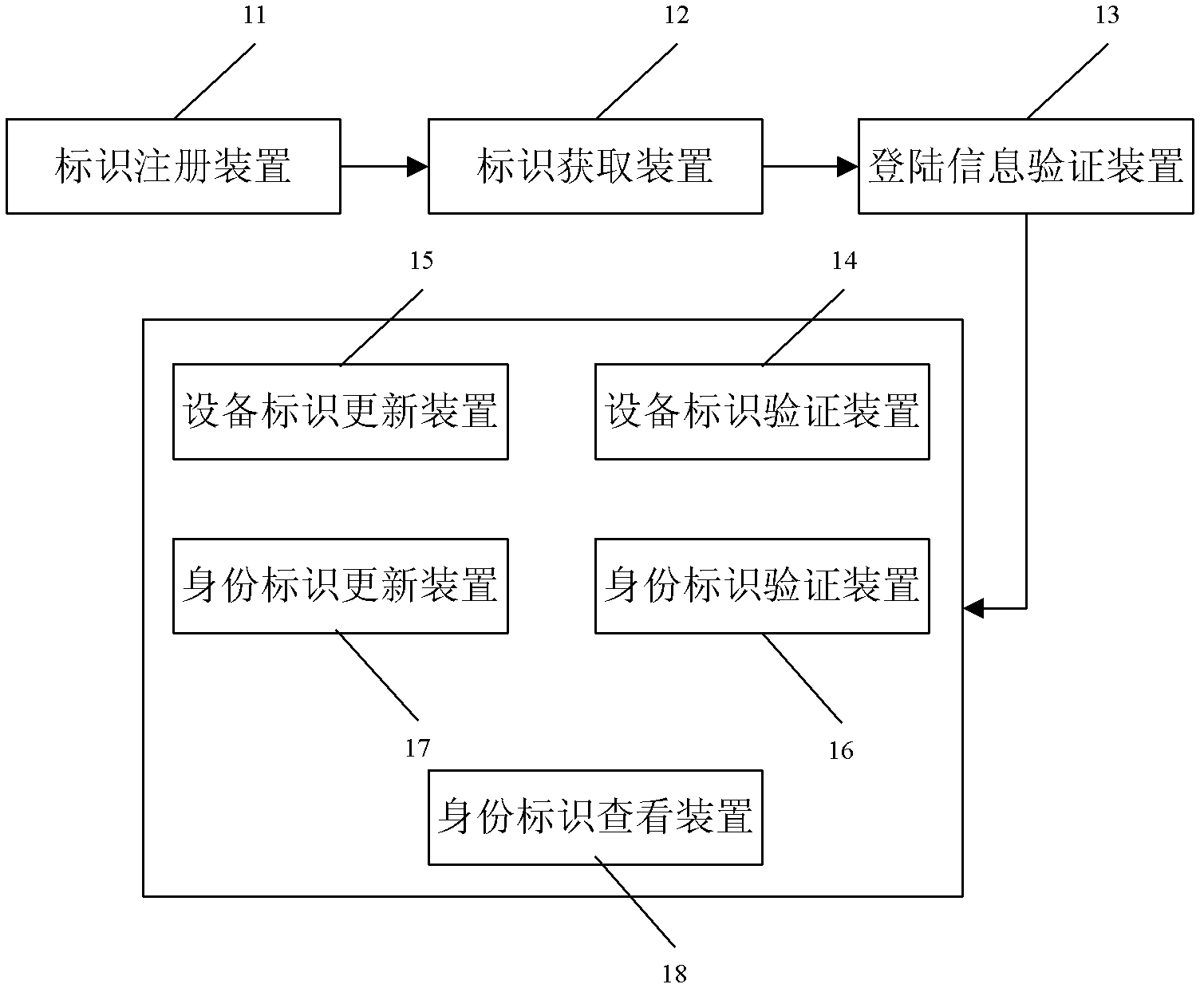
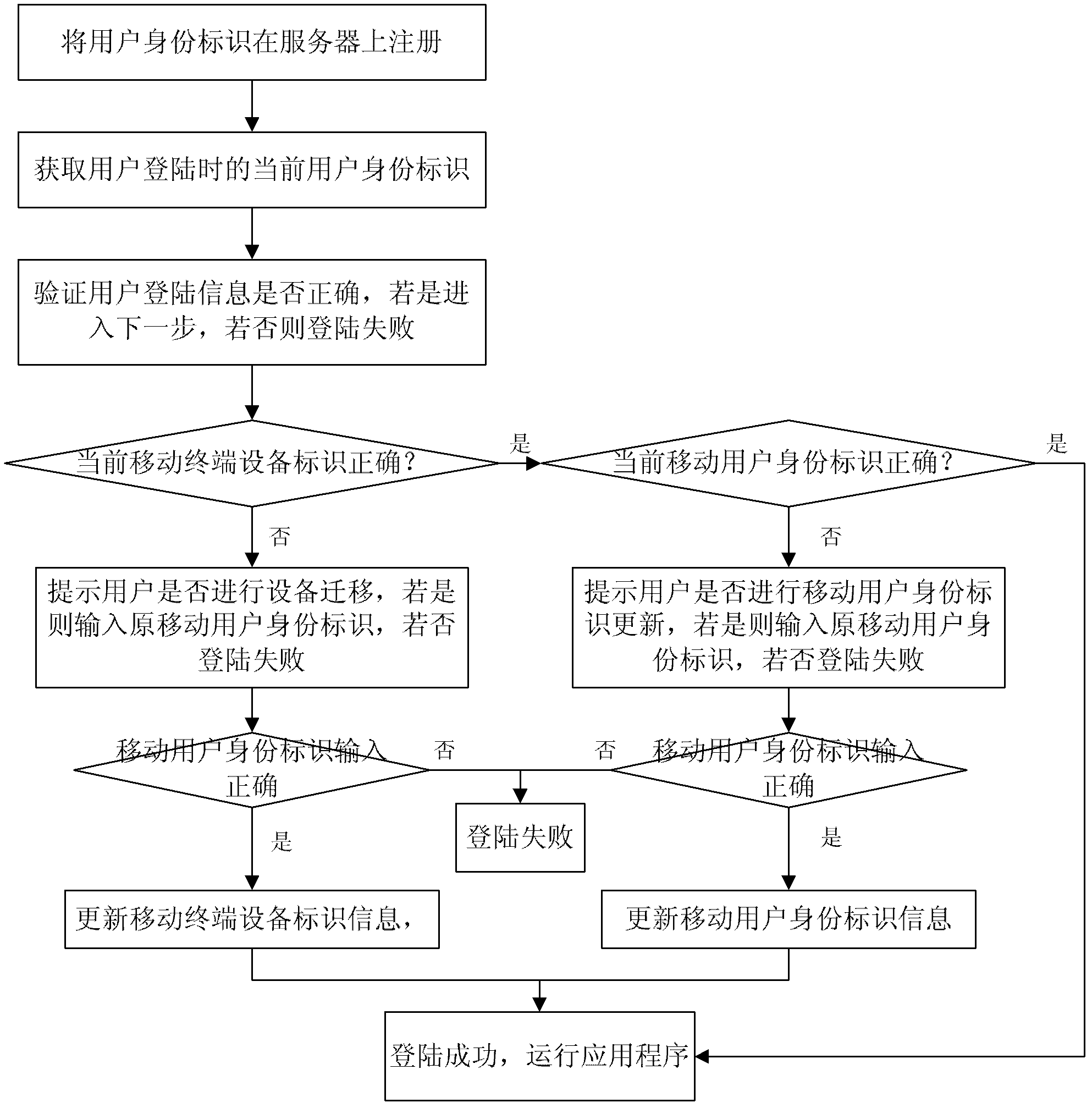
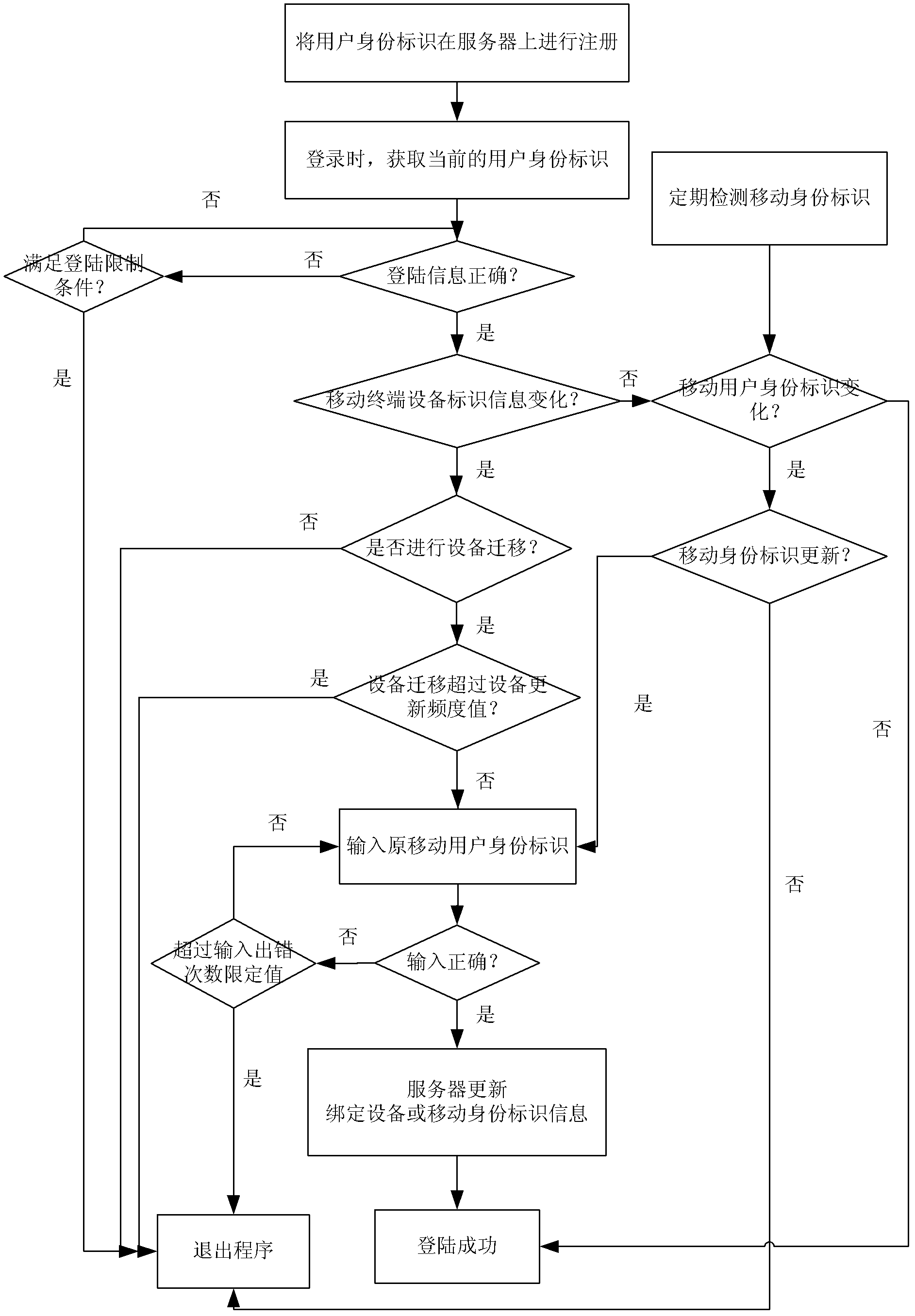
[0074] 1. First, when the user registers, the application automatically obtains the unique identifier of the mobile terminal equipment (IMEI number), the mobile user identity identifier (IMSI number), and sends it to the server for registration along with the registration information (login name, password) filled in by the user , and bind the login information with the equipment terminal identifier (IMEI) and SIM card information (IMSI) hardware information to form a user identity identifier, such as Figure 6 as shown,
[0075] When registering:
[0076] Mobile terminal equipment identification (IMEI number): 012154009774002
[0077] Mobile subscriber identity (SIM card number IMSI): 460006531643738
[0078] User registration name and password: whylcq, 123456
[0079] 2. Automatically detect and obtain the current user identity information and send it to the server when logging in.
[0080] When logging in:
[0081] Mobile terminal equipment identification (IMEI number):...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com