Mobile application security system and method
a mobile application and security system technology, applied in the field of applications, can solve the problems of user access denied, user id and password system not considered the most secure, and it is extremely difficult for a different person to replicate the biometric characteristic of the authentic user
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
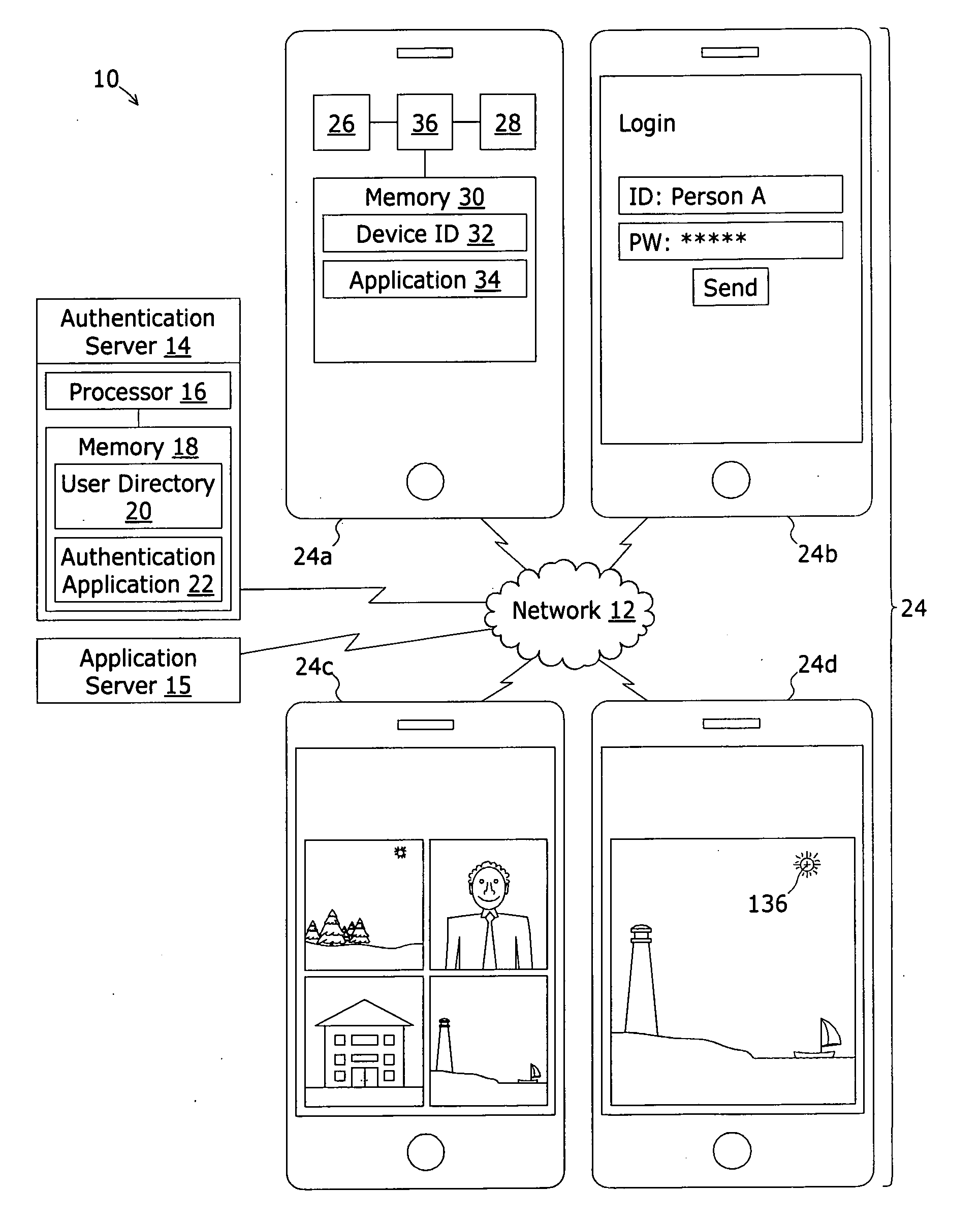
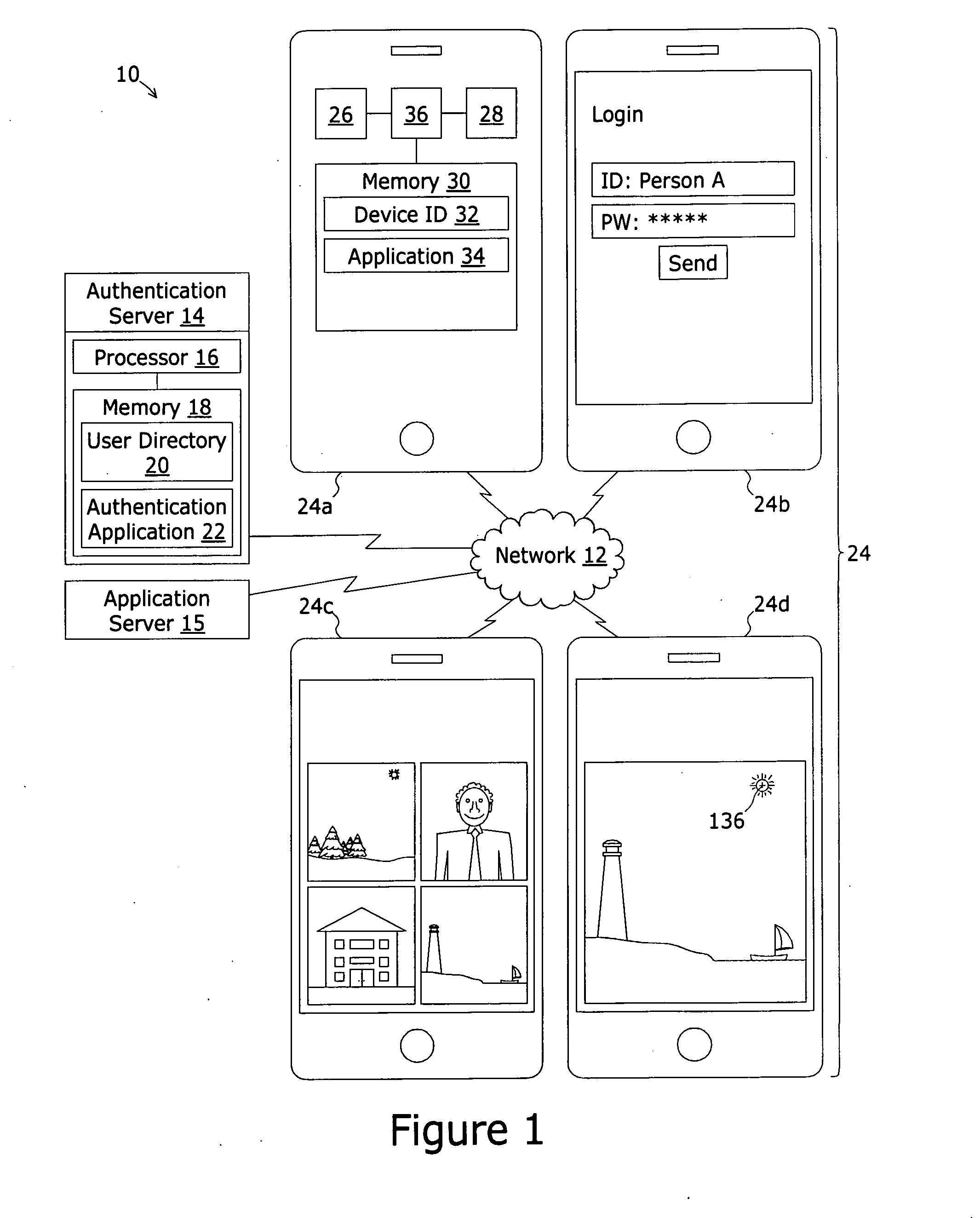
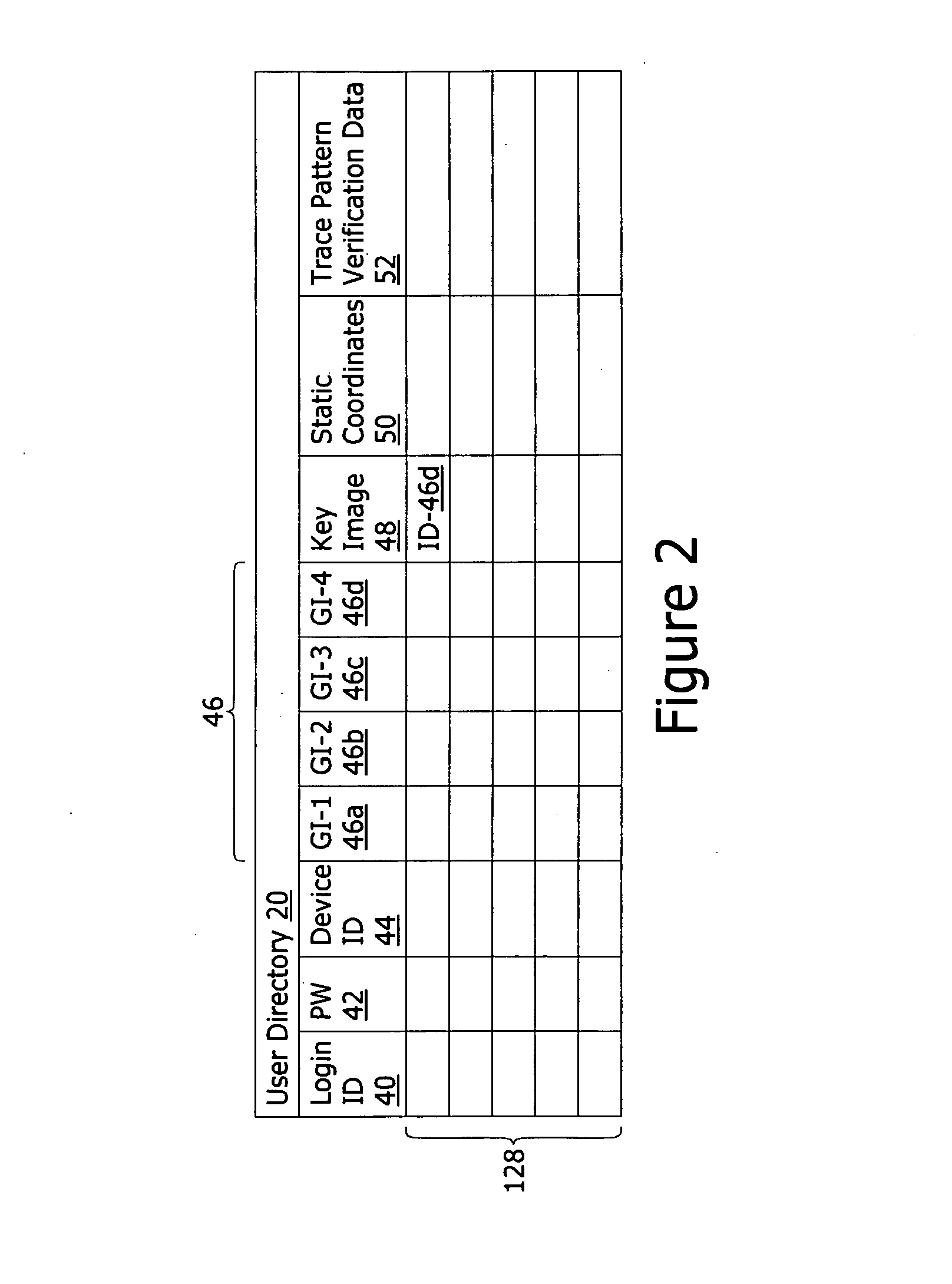
[0049]The present invention is now described in detail with reference to the drawings. In the drawings, each element with a reference number is similar to other elements with the same reference number independent of any letter designation following the reference number. In the text, a reference number with a specific letter designation following the reference number refers to the specific element with the number and letter designation and a reference number without a specific letter designation refers to all elements with the same reference number independent of any letter designation following the reference number in the drawings.
[0050]It should also be appreciated that many of the elements discussed in this specification may be implemented in a hardware circuit(s), a processor executing software code / instructions which is encoded within computer readable media (volatile memory, non volatile memory, magnetic media, RAM, ROM, Flash, ect) accessible to the processor, or a combination...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com