Data protection method and system with anti-theft function
A data protection and functional technology, applied in the field of information authentication, can solve problems such as inconsistency between verification products and verification information, and achieve the effect of improving immutability, authenticity and uncertainty, and reducing the possibility of imitation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
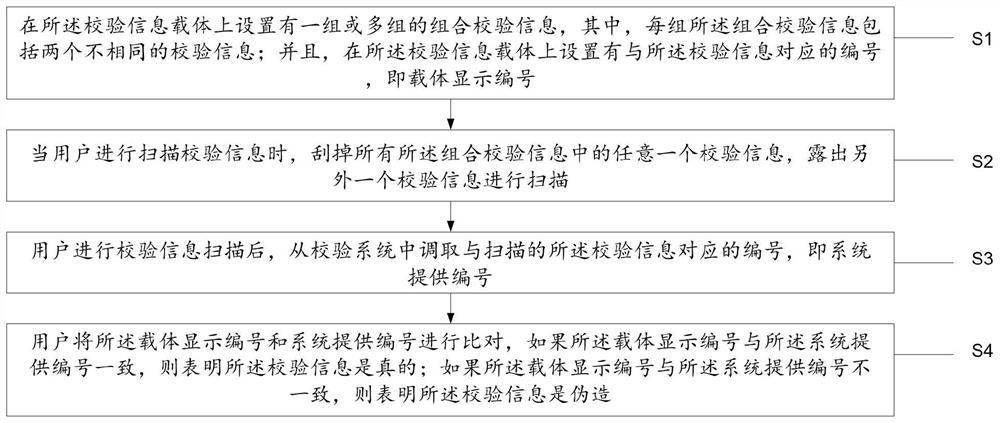
[0053] This embodiment proposes a data protection method with anti-theft function, such as figure 1 As shown, the method includes:
[0054] S1. Set one or more sets of combined check information on the check information carrier, wherein each set of combined check information includes two different check information; and, in the check information The number corresponding to the verification information is set on the carrier, that is, the carrier display number; wherein, the carrier display codes are set on the carrier in a non-overlapping manner;
[0055] S2. When the user scans the verification information, scrape off any verification information in all the combined verification information to expose another verification information for scanning;
[0056] S3. After the user scans the verification information, the number corresponding to the scanned verification information is retrieved from the verification system, that is, the system provides the number; wherein, the verific...
Embodiment 2
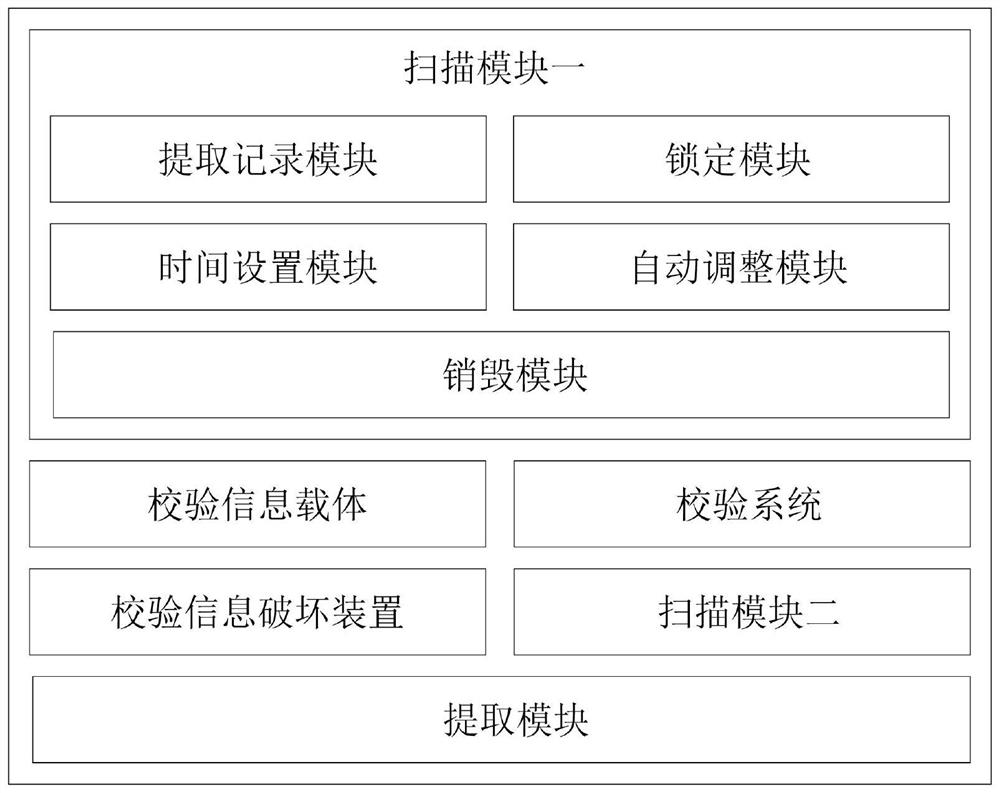
[0068] In this embodiment, the scheme is added on the basis of Embodiment 1. Specifically, the method also includes:
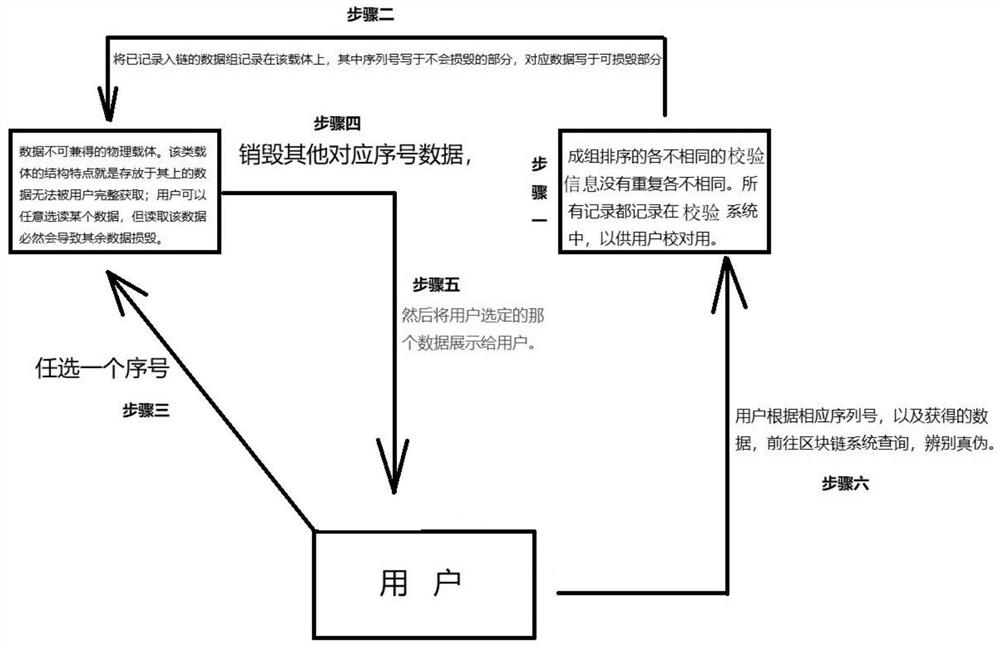
[0069] Step 1. When multiple groups of combined verification information are set on the verification information carrier, when the user randomly scrapes off any one of the verification information in any group of combined verification information, the verification information carrier Immediately destroy the verification information of all other combined verification information that has not been scraped by the user;
[0070] Step 2. The user obtains another verification information in the same combined verification information corresponding to the scraped verification information according to the randomly selected scraped verification information, and scans it;
[0071] Step 3. After the user scans the verification information, the number corresponding to the scanned verification information is retrieved from the verification system, that is, the system provid...
Embodiment 3
[0076] This embodiment is a further limitation of the data protection method with an anti-theft function proposed in Embodiment 1, specifically, the number corresponding to the scanned verification information is retrieved from the verification system in S3, include:
[0077] S301. When multiple groups of combined verification information are set on the verification information carrier, the verification system stores a system display code corresponding to each verification information in each group of combined verification information;
[0078] S302. After the user selects and scans the verification information, the verification system extracts and displays the system display code corresponding to the verification information, and at the same time records the time when the system display code corresponding to the verification information is displayed for the first time;
[0079] S303. Lock the verification information carrier where the verification information corresponding to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com