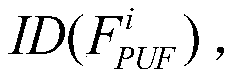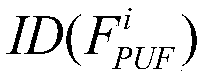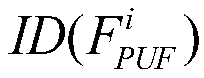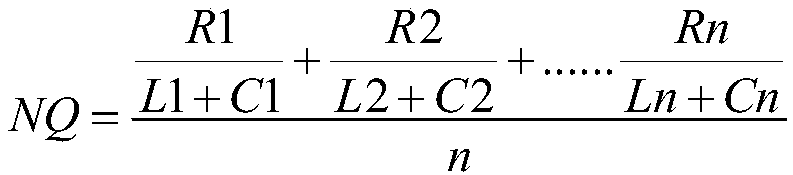Patents
Literature
70results about How to "Occupies less system resources" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
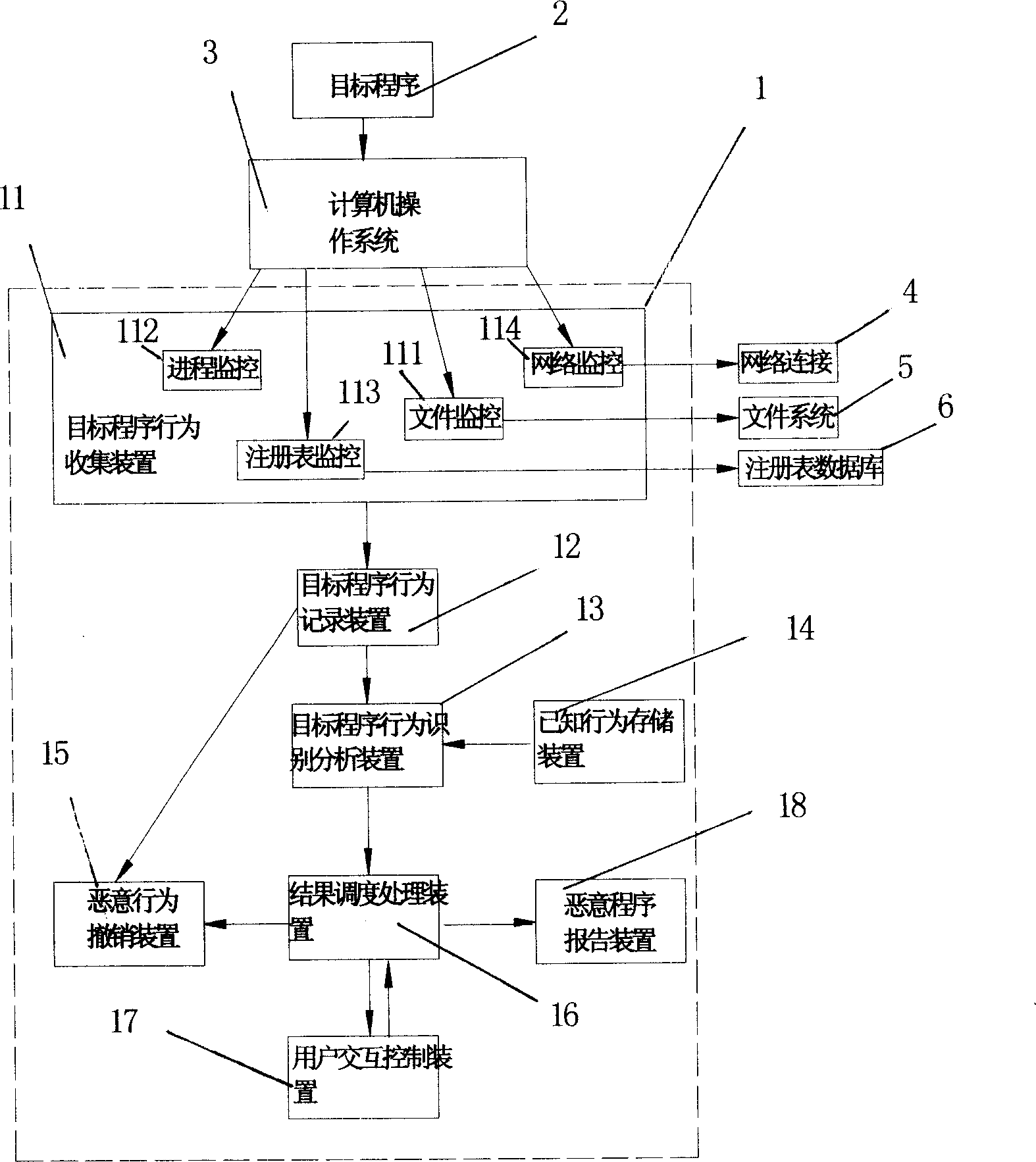
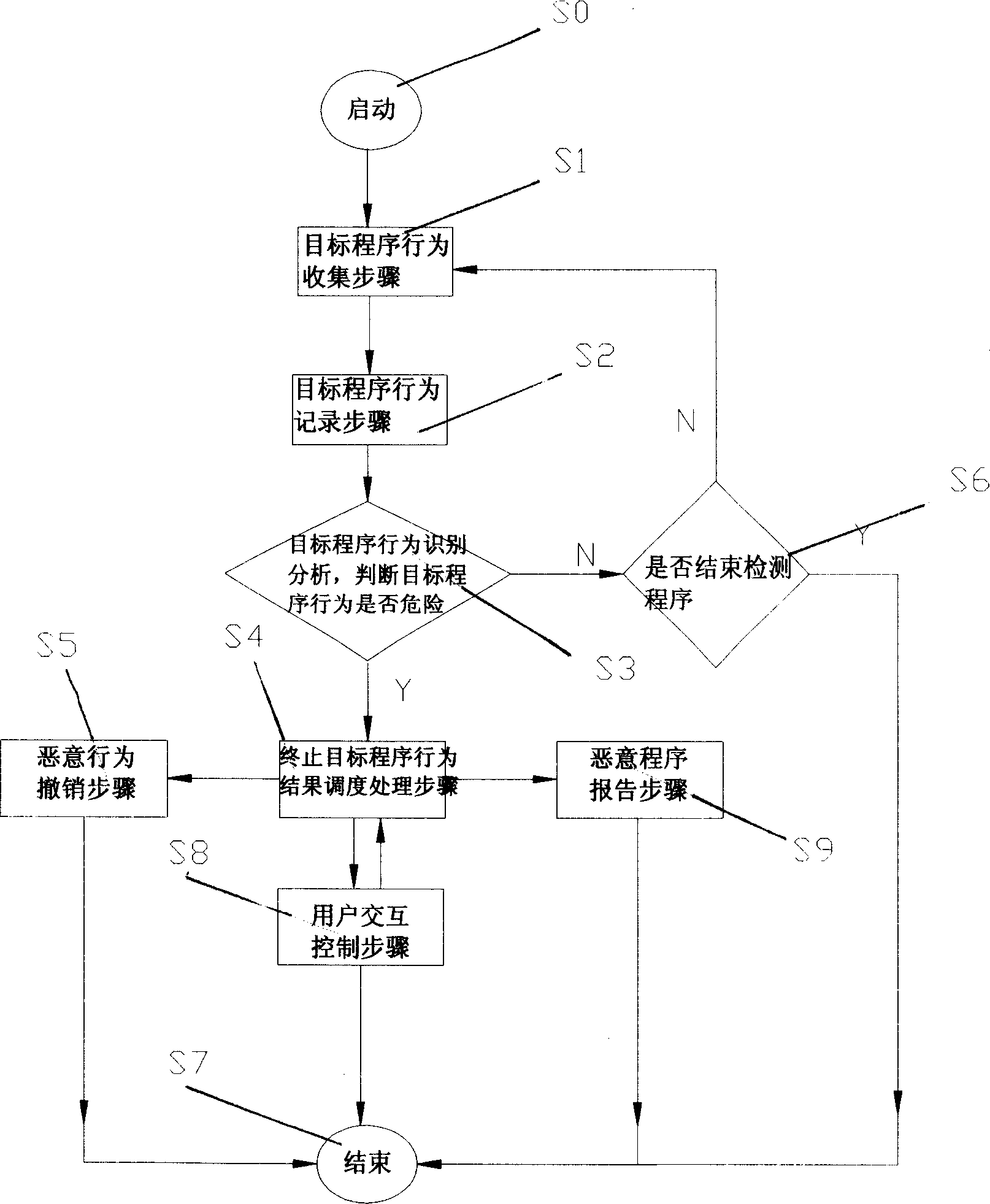
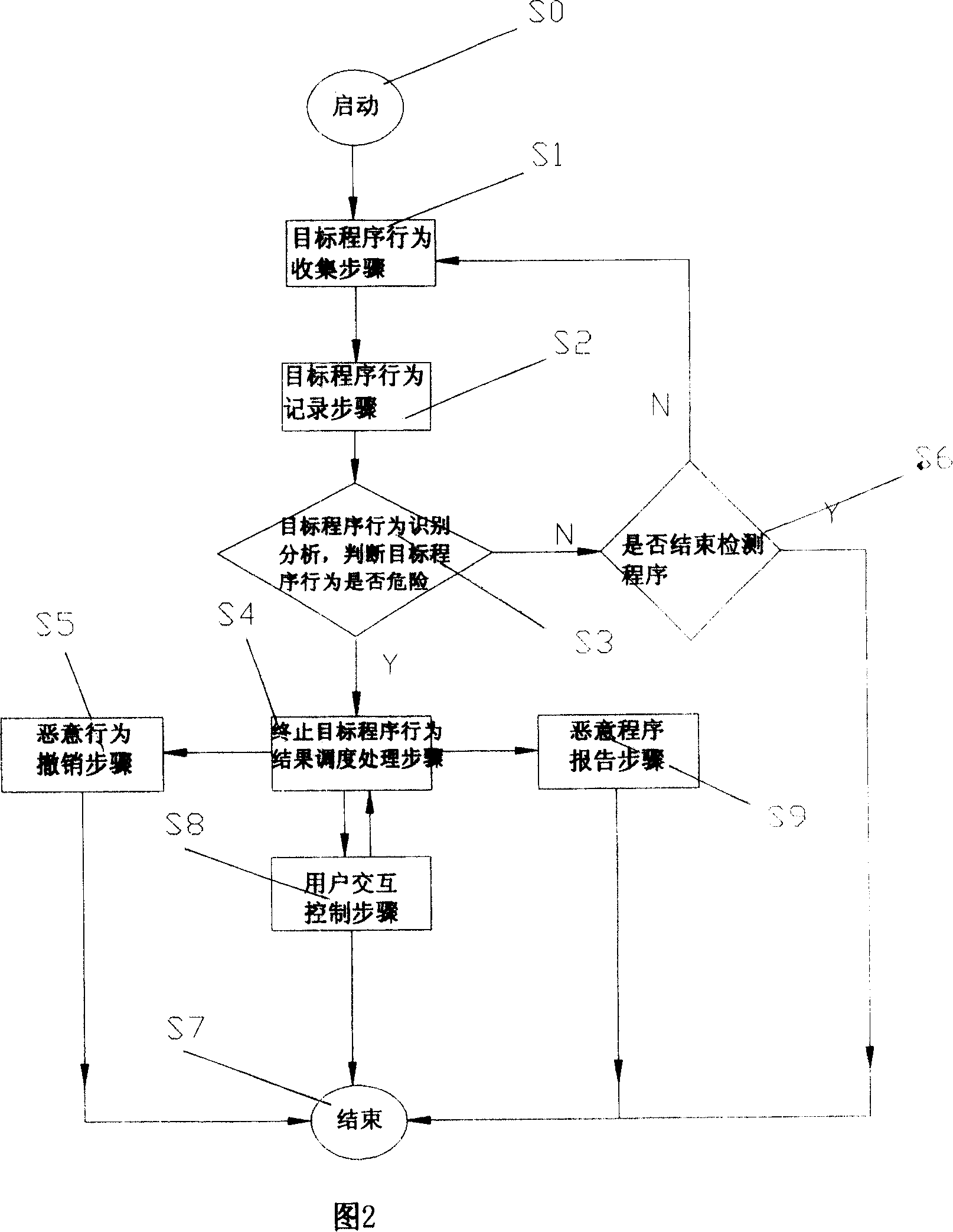
System and method for detecting and defending computer worm
ActiveCN1737722AEffective defenseOccupies less system resourcesDigital data processing detailsComputer wormOperational system
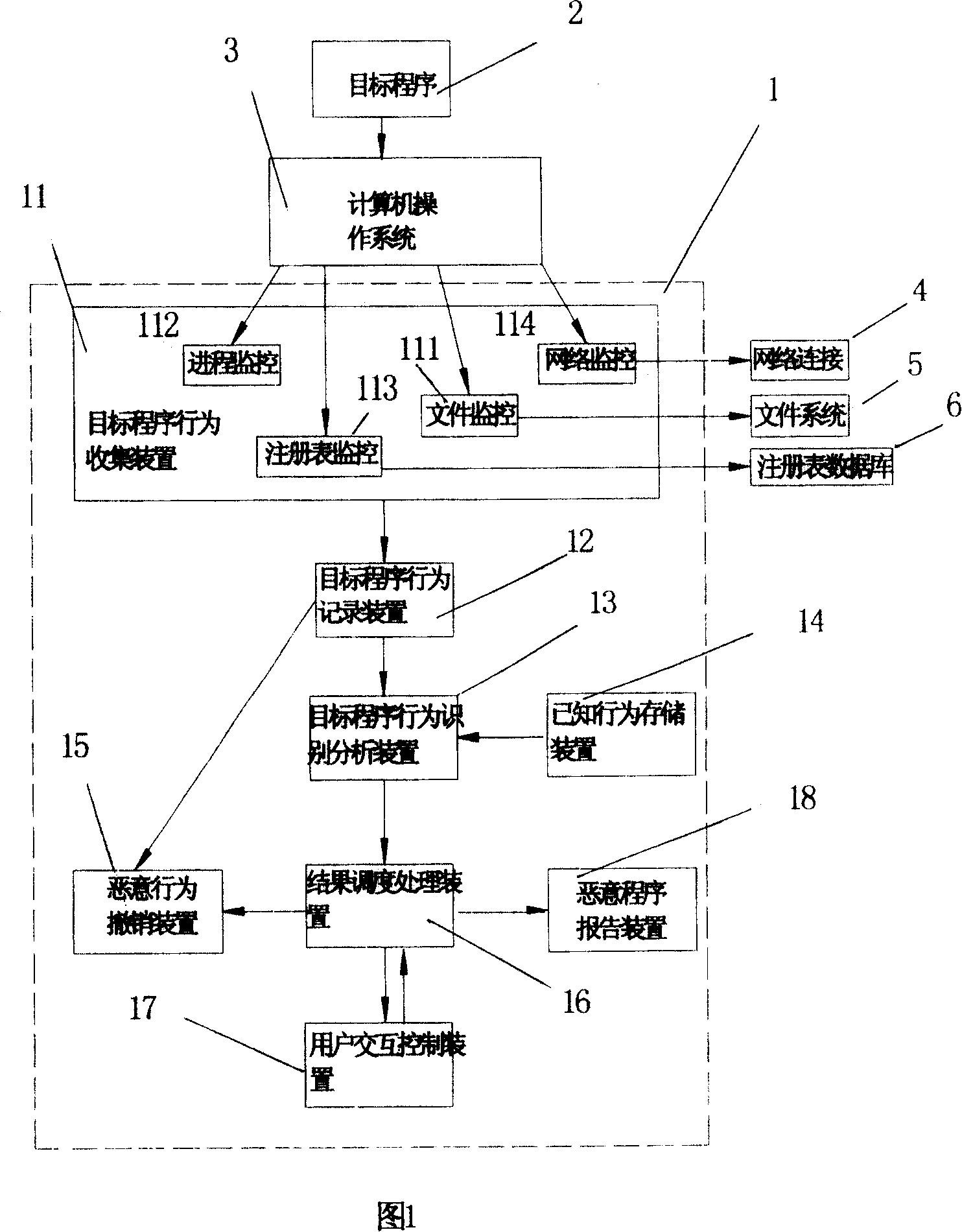
This invention relates to test and protective computer ill-purpose program system, which comprises the following parts: computer operation system monitor device to collect aim programs operation information; aim program operation record device to store aim programs operation records and to record repaired files, register form; known action characteristics memory device to store known, processed operation information and to store each operation relative danger degree weigh; aim program action identification analysis device to compare the aim program with known action; ill-purpose action removal device to remove the ill-purpose program.
Owner:ZHUHAI KINGSOFT SOFTWARE CO LTD
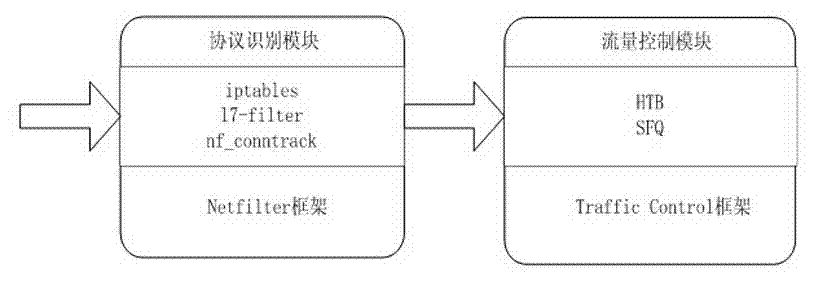
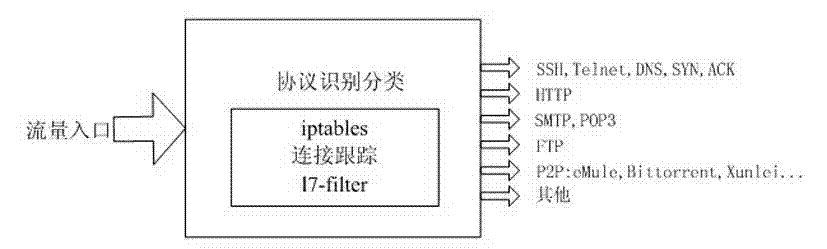
Flow control method based on application layer detection
InactiveCN103036803AImprove service qualitySuppress trafficData switching networksWeb serviceThe Internet
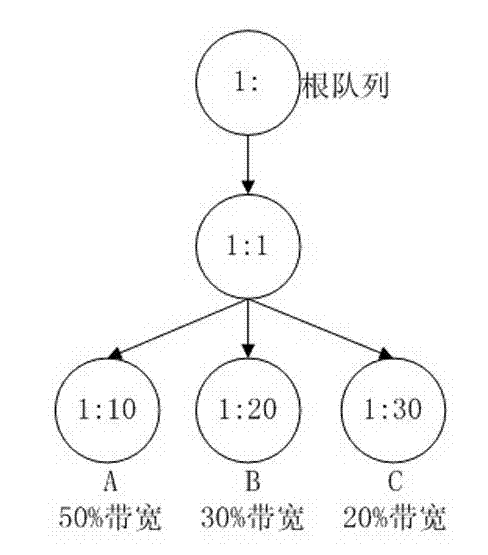
The invention relates to a flow control method based on application layer detection .The flow control method based on the application layer detection is a systematic method of identification and control for the flow of a variety of web services. Bandwidth management is carried out for different user groups. Different bandwidths are distributed to different user groups according to difference of businesses of departments in enterprises. The bandwidths of some users are limited. Each group of users can obtain the minimum guaranteed bandwidth whenever the users surf the internet and network congestion can be avoided. Maximum bandwidth which can be borrowed and borrowing priority of each group are set at the same time. Therefore, waste of resources caused by excess bandwidths of sub-networks can be avoided and users of high priority can borrow more remaining bandwidths. Bandwidth management is carried out for different application protocols. Different bandwidths are distributed to different application protocols according to criticality of businesses. Different priority levels are set, and non-critical business flow of peer-to-peer (P2P) and the like are restrained. Therefore, service quality of critical businesses is guaranteed.
Owner:NANJING UNIV OF POSTS & TELECOMM
Massive operation and maintenance implementation method
InactiveCN106844171AImprove throughputSolve data storageHardware monitoringSpecial data processing applicationsFull life cycleData profiling
The invention provides a massive operation and maintenance implementation method and belongs to the technical field of product full-life-cycle operation and maintenance. In the method, in the perspective of a whole business system, according to log information of a host, a database, middleware and a business system related to the whole business system, massive logs are analyzed through big data, and function and performance problems, which possibly occur in software and hardware environments, of an information system are analyzed. Problems of the information system or even specific business functions in the levels of hardware, software and services are effectively monitored, the service capacity is enhanced, the overall operation and maintenance risk is controlled, and the operation and maintenance efficiency is improved.
Owner:INSPUR QILU SOFTWARE IND
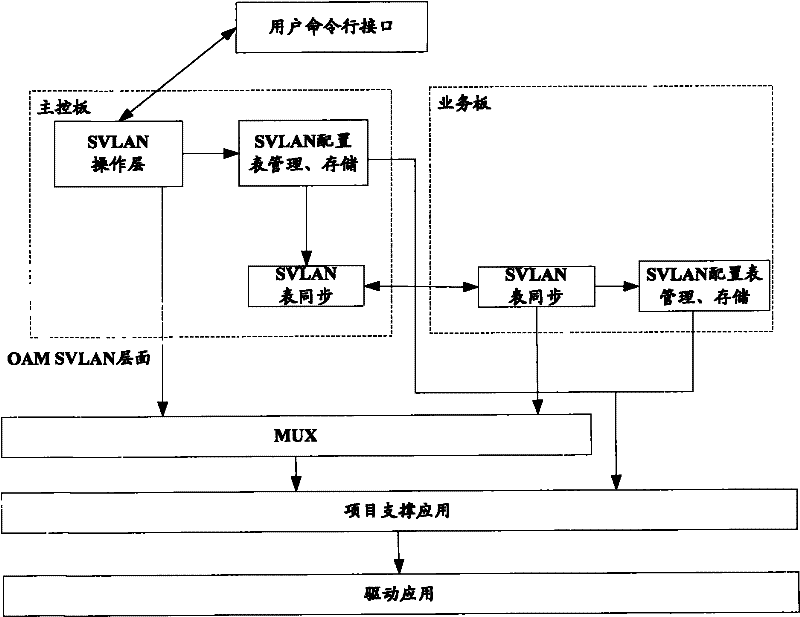
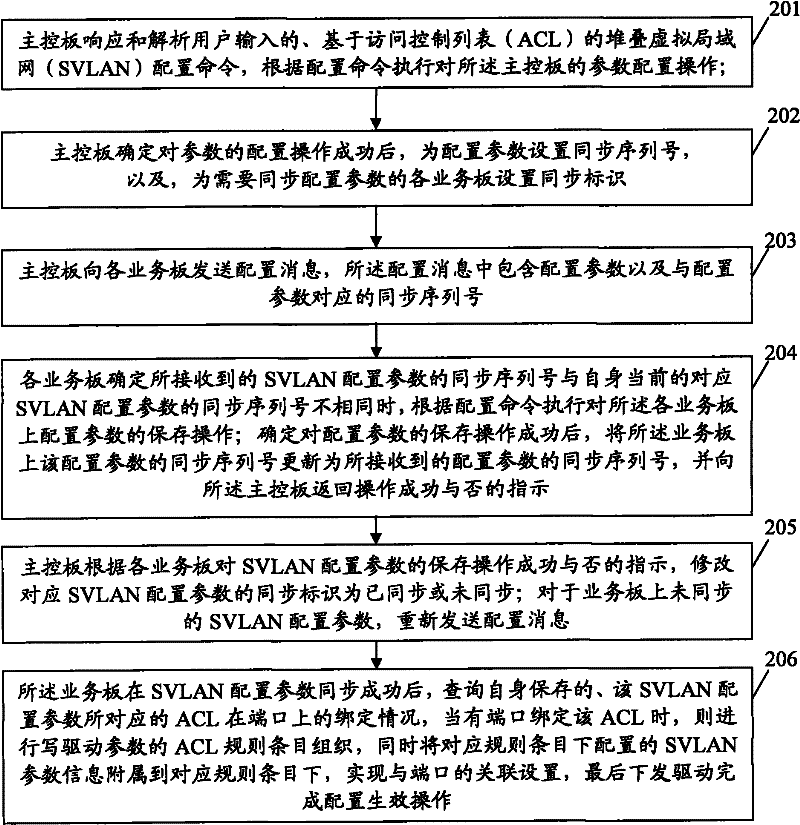
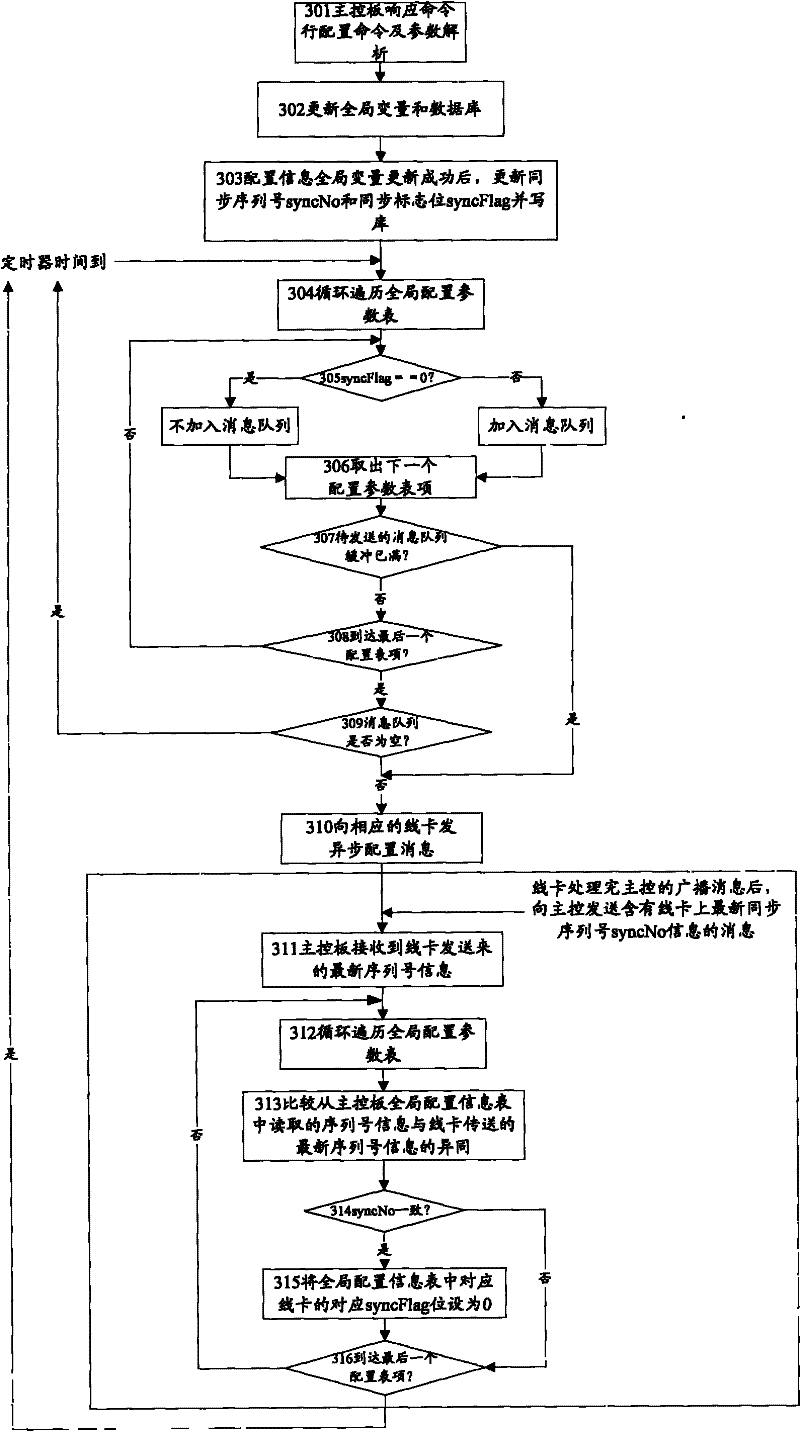
Configuring method and device of stacking virtual local area network of distributed network device
InactiveCN101753362ASave communication resourcesEasy to implementNetworks interconnectionVirtual LANDependability
The invention discloses a configuring method of a stacking virtual local area network (SVLAN) of a distributed network device. By adopting a unique synchronization technology, the synchronous process of the SVLAN service based on an access control list (ACL) is realized both in the aspect of responding user instruction configuration and parameter analysis by a master control board and in the aspect of transmitting the configuration information from the master control board to each service board on the distributed network device, configuration release and function validation of each service board are realized, conventional configuration and processing flow are improved, and system resources are optimized, thereby improving operation efficiency and reliability of the system. The invention also discloses a configuring device of the SVLAN of the distributed network device. The invention has simple realization and strong practicability.
Owner:ZTE CORP
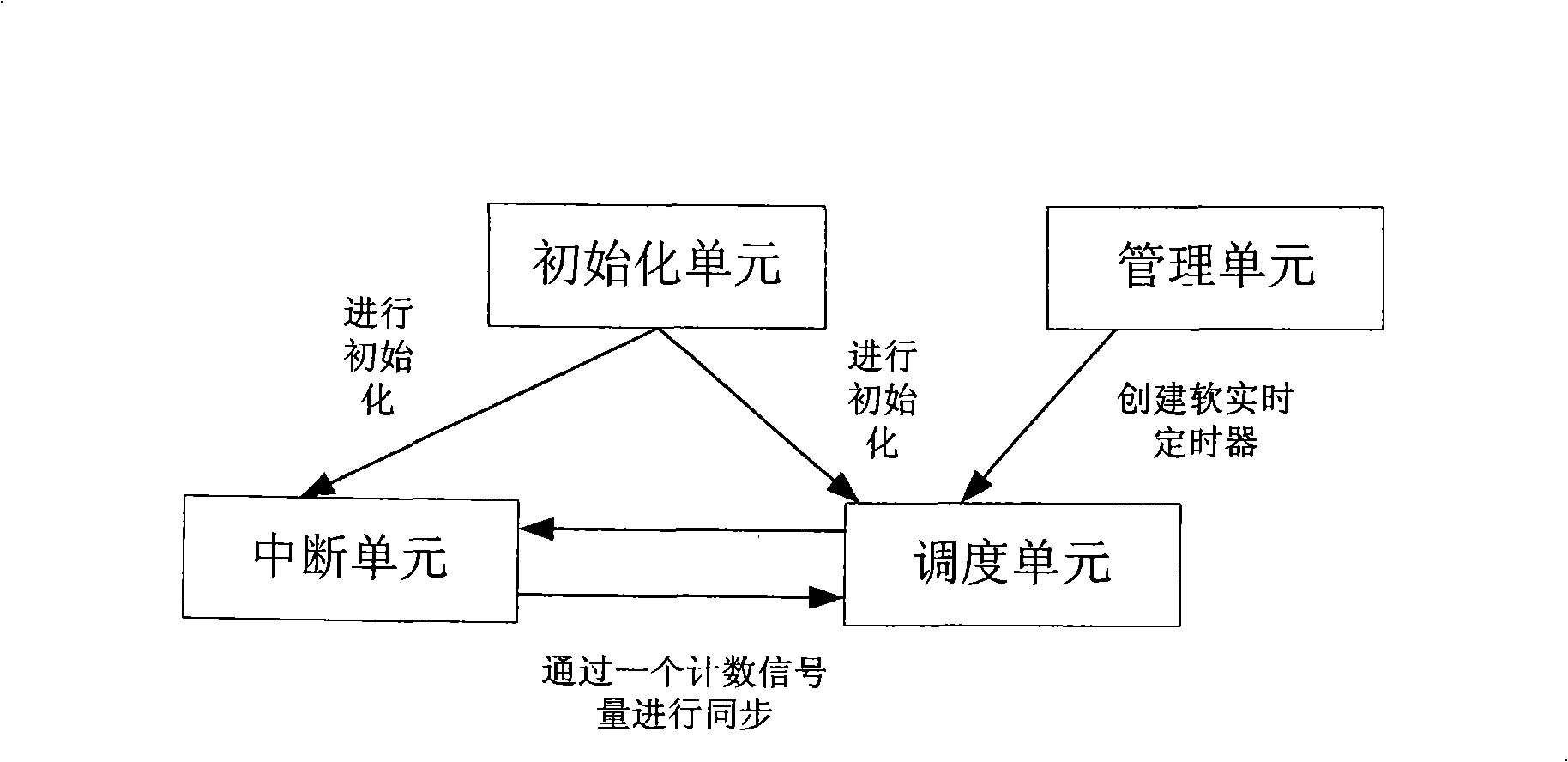
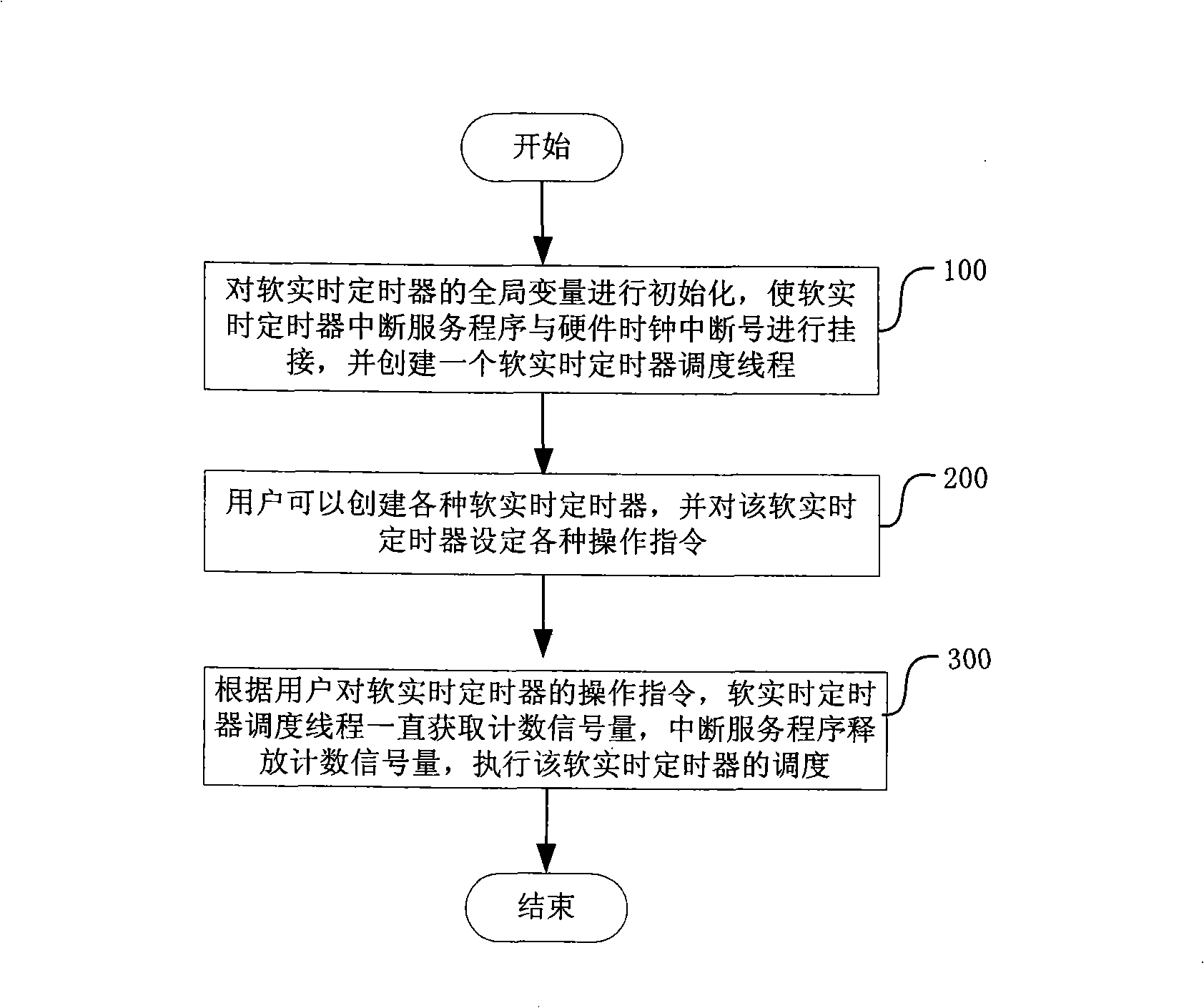
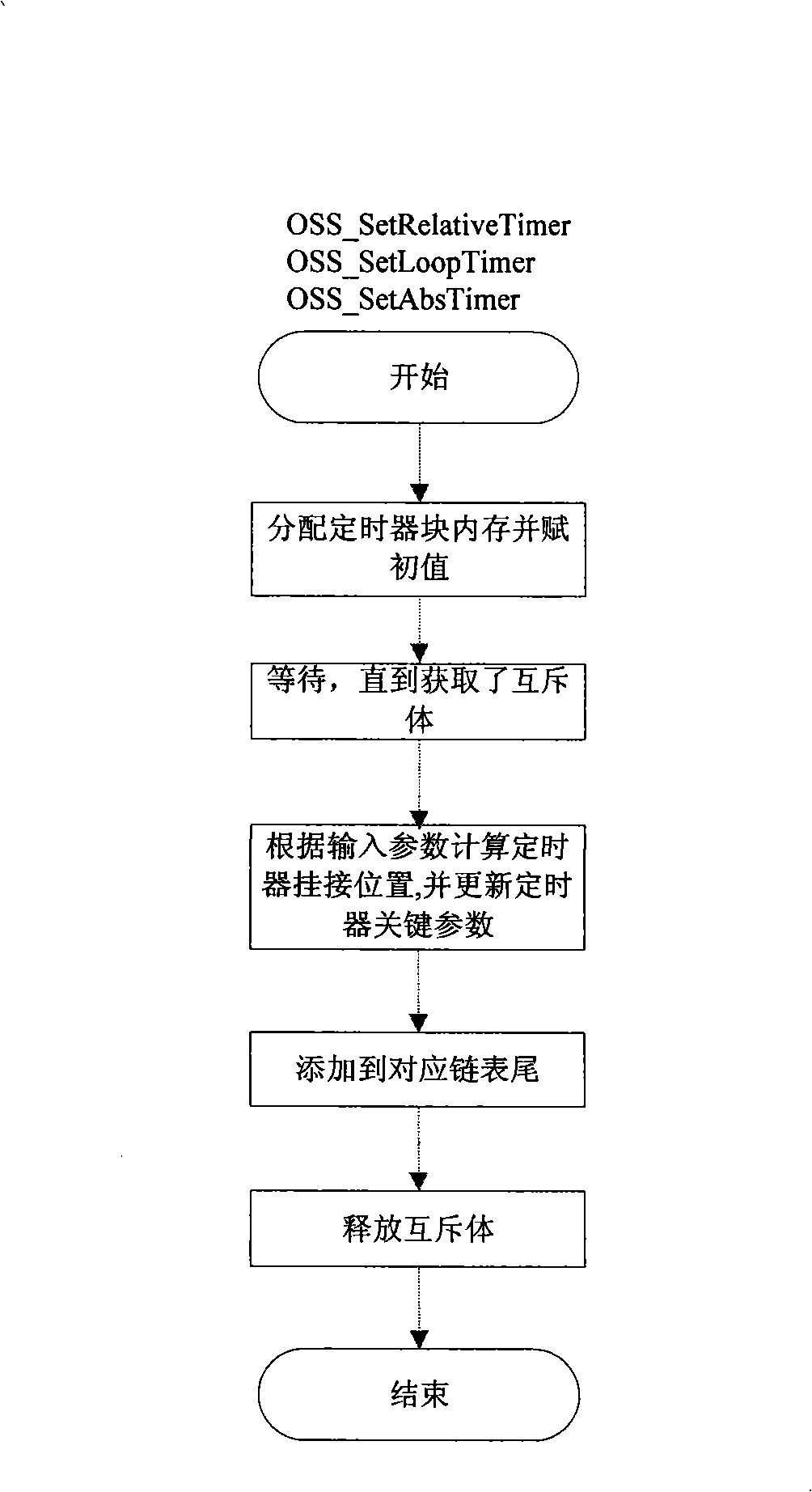
Soft real-time timing device module and method for soft real-time timing device scheduling
InactiveCN101272564AEasy to useOccupies less system resourcesMultiprogramming arrangementsRadio/inductive link selection arrangementsManagement unitComputer module
The invention relates to a method for dispatching a soft real-time timer and a module thereof, which comprises a dispatching unit, an interrupting unit, an initializing unit and a management unit. The dispatching unit is used for controlling a timer dispatching thread of a set up soft real-time timer, and the inside of the dispatching unit is an unlimited circulation body always obtaining counting semaphores; the interrupting unit is used for controlling the interrupting of the timer and releasing the counting semaphores; wherein, the dispatching unit is synchronous with the interrupting unit through a counting semaphore; the initializing unit is used for initializing overall variation of the timer so as to connect the interrupting unit and interrupting signals of a hardware clock and to initialize the dispatching unit; the overall variation comprises the counting semaphores; the management unit is a front desk window for users to control the timer, and users set up various soft real-time timers through the management unit and then set various operation instruments for the timer. By applying the invention, through an information mechanism, when the timer sends out appointed information to a senior user at time, the portability of a cell phone platform and various demands of the senior user on the cell phone platform can be met.
Owner:ZTE CORP
Application system for high grade multiple line distance management
InactiveCN1987792ATimely and reliable responsivenessTimely and Reliable ProcessingMultiprogramming arrangementsData switching networksComputerized systemEngineering
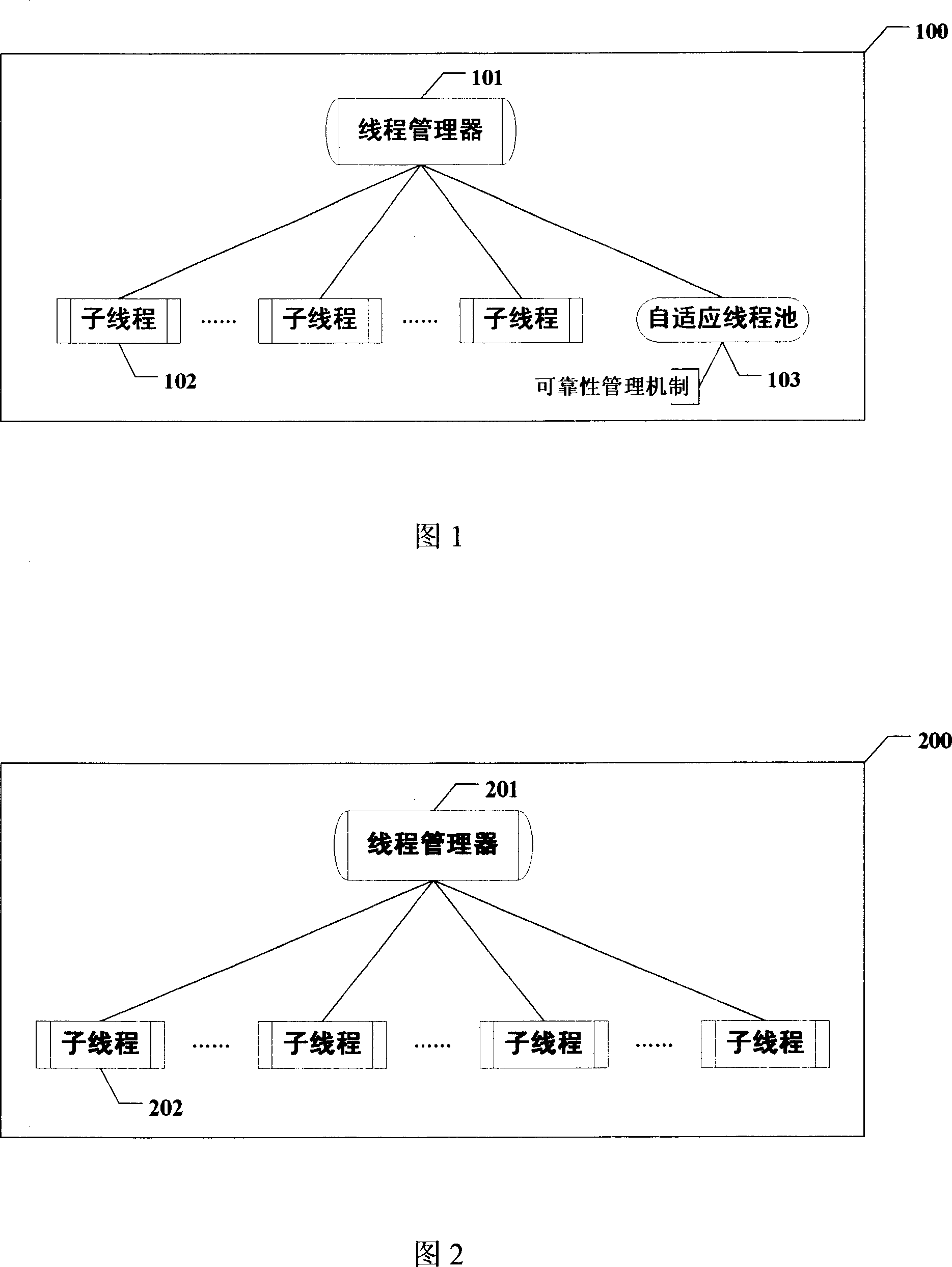
Senior multi-lines administrative application system, it relates to a senior multi-lines administrative application of the computer, especially directing to the reliability administrative system and the safety of the computer net the scale of which is large and the running situation is complex. It includes the senior lines administrative element which has the name of the line, the parameter of the line, the sequence of the line, the numbering of the line phase and the lines which is used to apply the save memory and found the administrative lines, and registers a timer. It also includes a self adjustable line pool which is founded by the senior line administer, the number of the line is the minimal value of the defined range, and the administrative line also sets the overtime according to every lines in the line pool. This invention applies to the net computer system.
Owner:沈阳通用软件有限公司
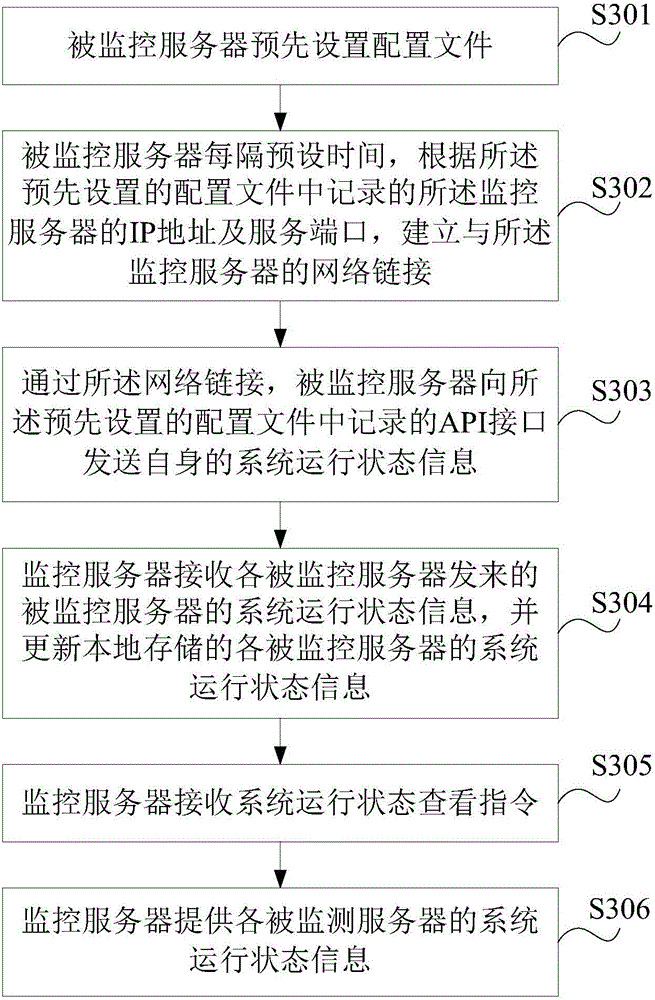
Method and system for monitoring server system running state information
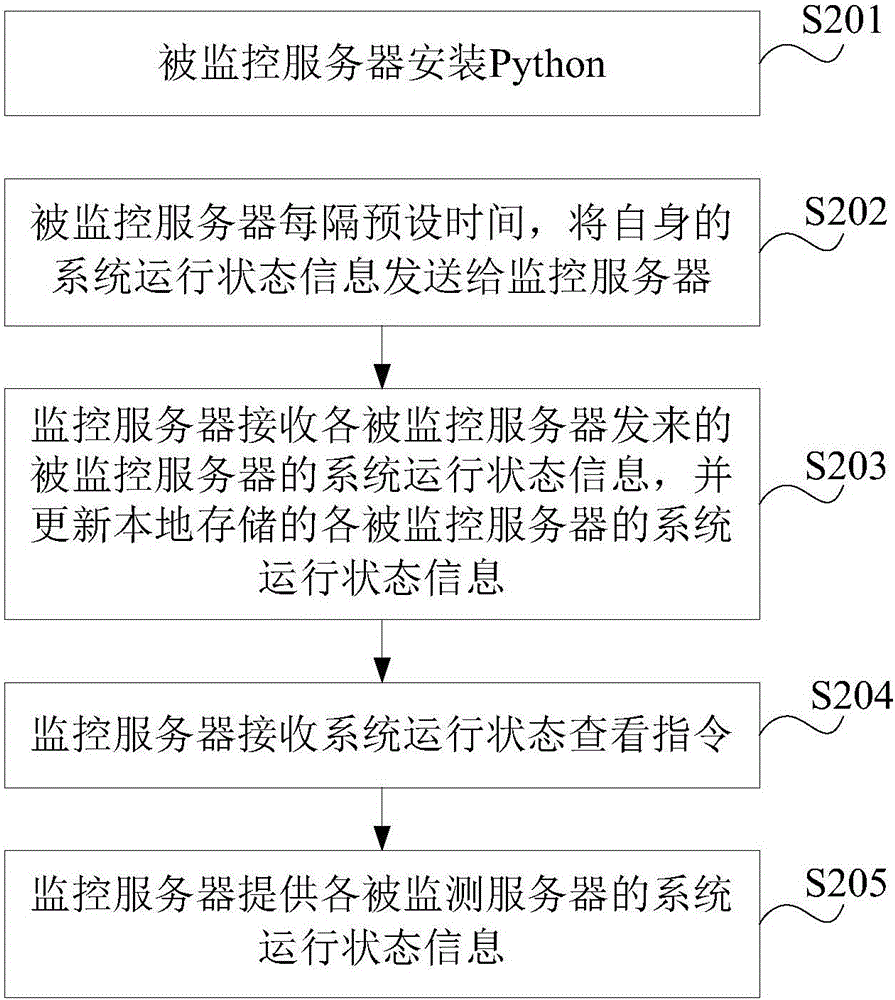
InactiveCN106161145AEasy maintenanceOccupies less system resourcesHardware monitoringData switching networksInformation monitoringSoftware
The invention discloses a method and a system for monitoring server system running state information, and belongs to the field of computer communication, and the method and the system are used for providing a server system running state information monitoring scheme with advantages of few occupied system resources and convenient maintenance. The method comprises the steps: a monitored server transmits self system running state information to a monitor server every preset time; the monitor server receives system running state information of the monitored server transmitted by the monitored server and updates system running state information of each monitored server saved locally; the monitor server receives a system running state check instruction; and the monitor server provides the system running state information of each monitored server. According to the invention, a large special monitoring software has no need to be set, the occupied system resources are few, and the maintenance is convenient.
Owner:TVMINING BEIJING MEDIA TECH
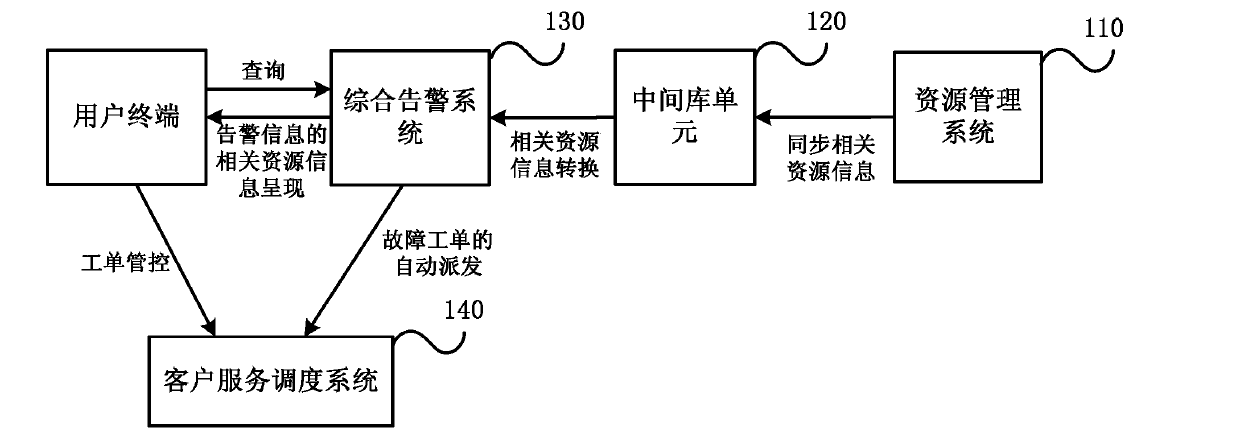
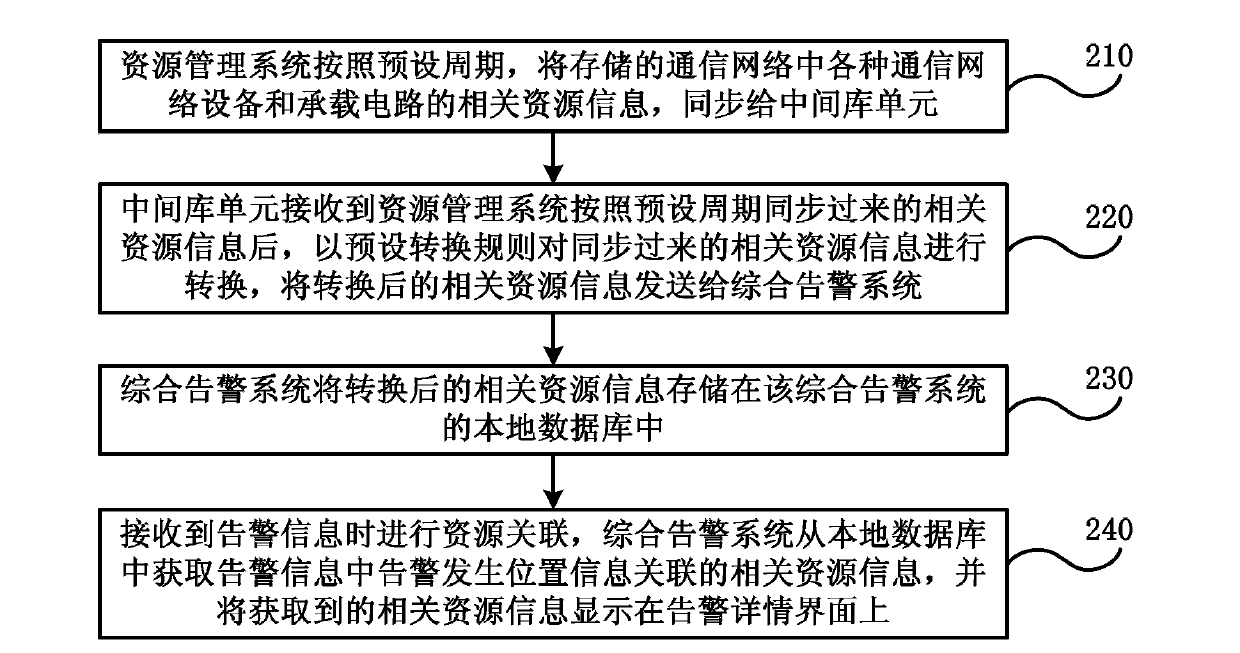
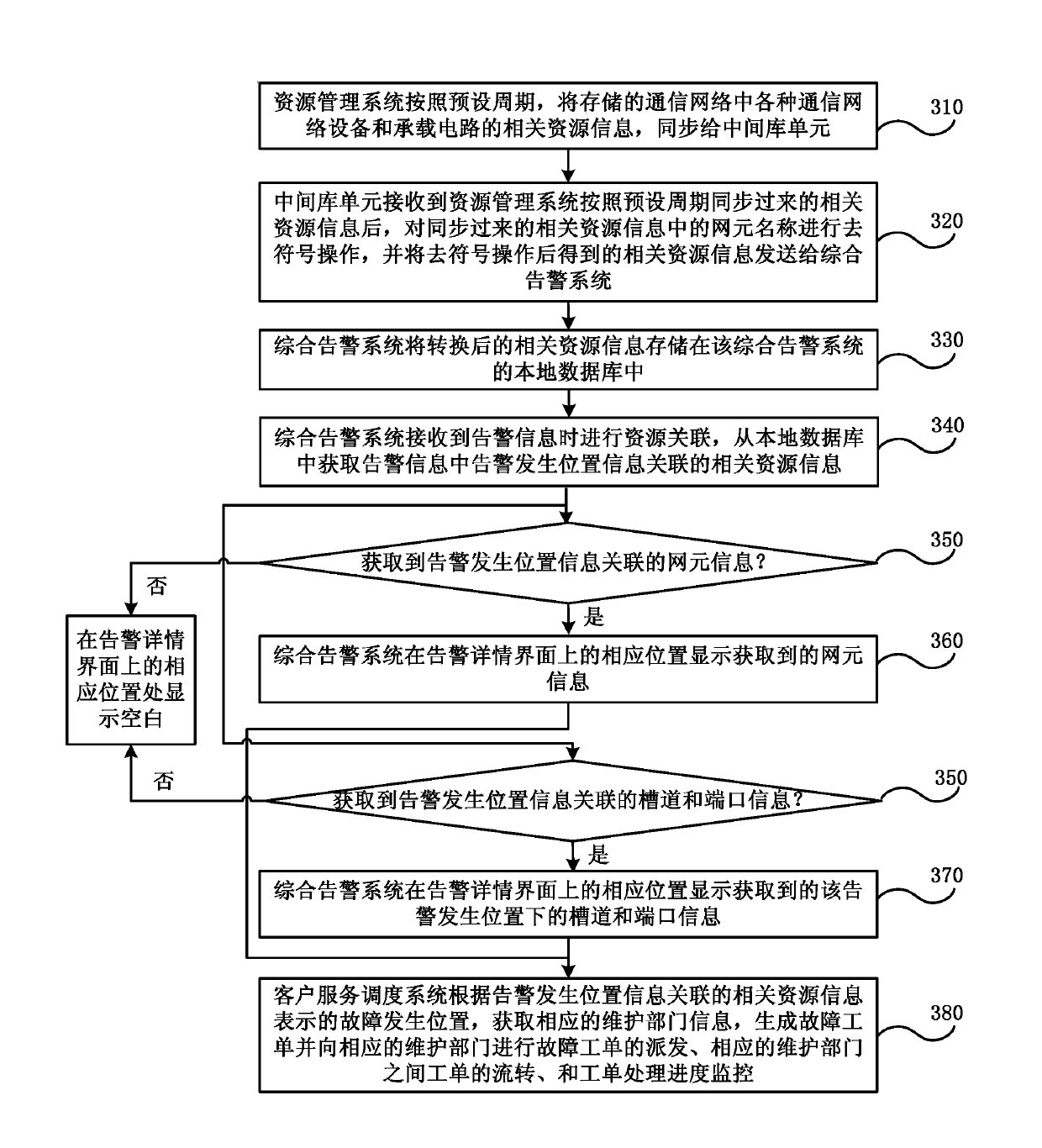
System and method for positioning failures of communication network equipment based on alarm information
ActiveCN103873288APrecise positioningReduce occupancyData switching networksResource Management SystemReal-time computing
The embodiment of the invention discloses a system and a method for positioning failures of communication network equipment based on alarm information. The method comprises the following steps that a resource management system synchronizes the stored related resource information of various kinds of communication network equipment and bearer circuits in a communication network to a middle base unit according to a preset period; the middle base unit converts the synchronized related resource information according to the requirements of a comprehensive alarming system on the format of alarm position information by using preset conversion rules, and transmits the converted related resource information to the comprehensive alarming system; the comprehensive alarming system stores the converted related resource information in a local database, performs resource association when receiving the alarm information, acquires the related resource information associated with the alarm position information in the alarm information from the local database, and displays the acquired related resource information on an alarm detail interface. According to the embodiment of the invention, the alarm position can be rapidly and accurately determined.
Owner:CHINA TELECOM CORP LTD
Anti-interference method for millimeter-wave anti-collision radar
InactiveCN109856600ASolve the problem of target misjudgmentImprove practicalityWave based measurement systemsRadarPhase Code
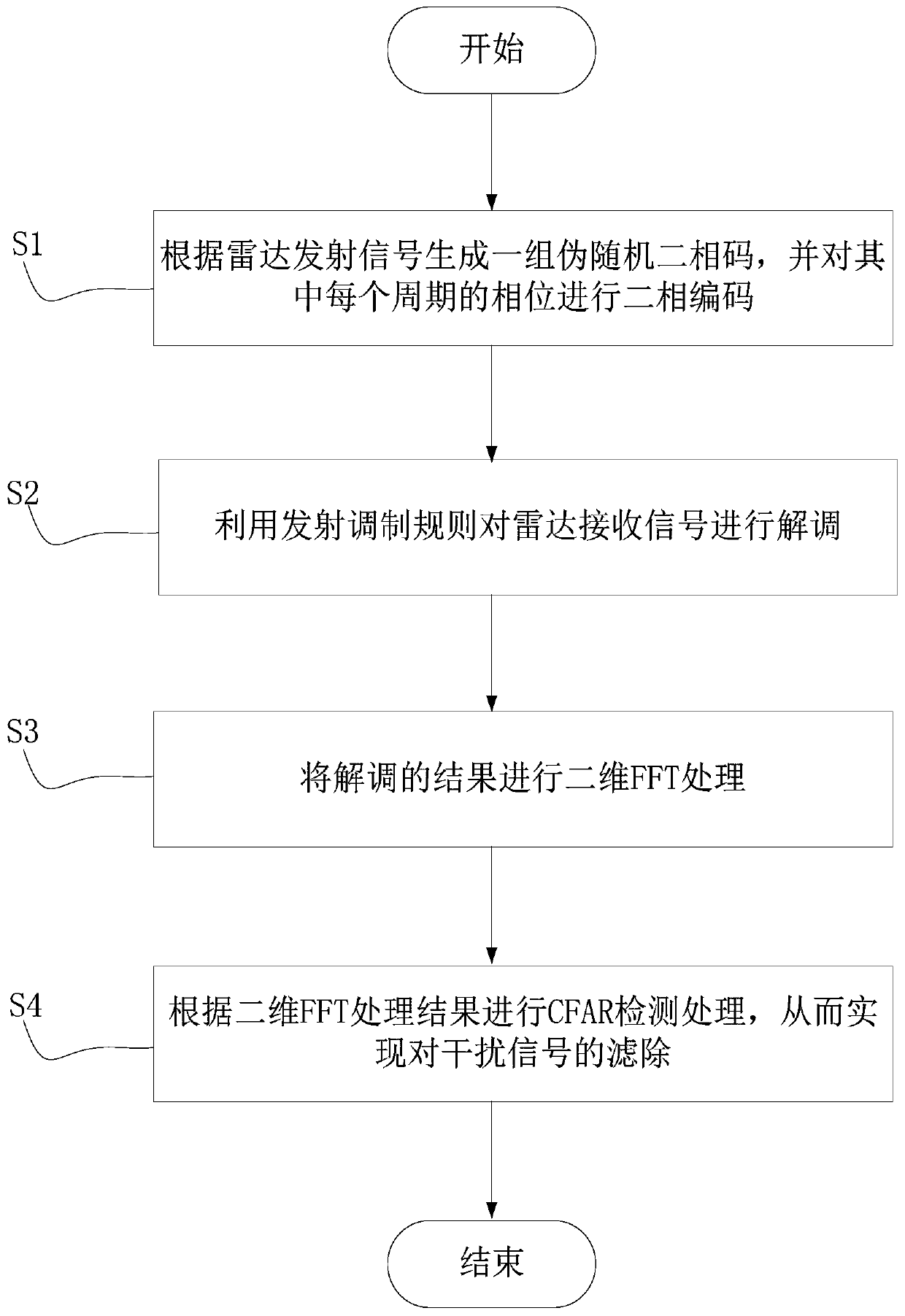
The invention provides an anti-interference method for a millimeter-wave anti-collision radar. The anti-interference method comprises: S1, generating a set of pseudo-random two-phase codes according to a radar transmission signal and carrying out two-phase encoding on the phases of all periods; S2, demodulating a radar receiving signal by using a transmitting modulation rule; S3, carrying out two-dimensional FFT processing on the demodulated result; and S4, carrying out CFAR detection processing according to the two-dimensional FFT processing result, thereby filtering an interference signal. According to the invention, a problem of the wrong target determination caused by the mutual interference between radars is solved; and the practicability and accuracy of the millimeter-wave anti-collision radar in a complex environment are improved. The less system resources are occupied; the method is flexible and is easy to implement; and the support is provided for the follow-up system upgrading and application extension. Therefore, the method has the great practical value and promotion value.
Owner:CHENGDU SEEKCON MICROWAVE COMM
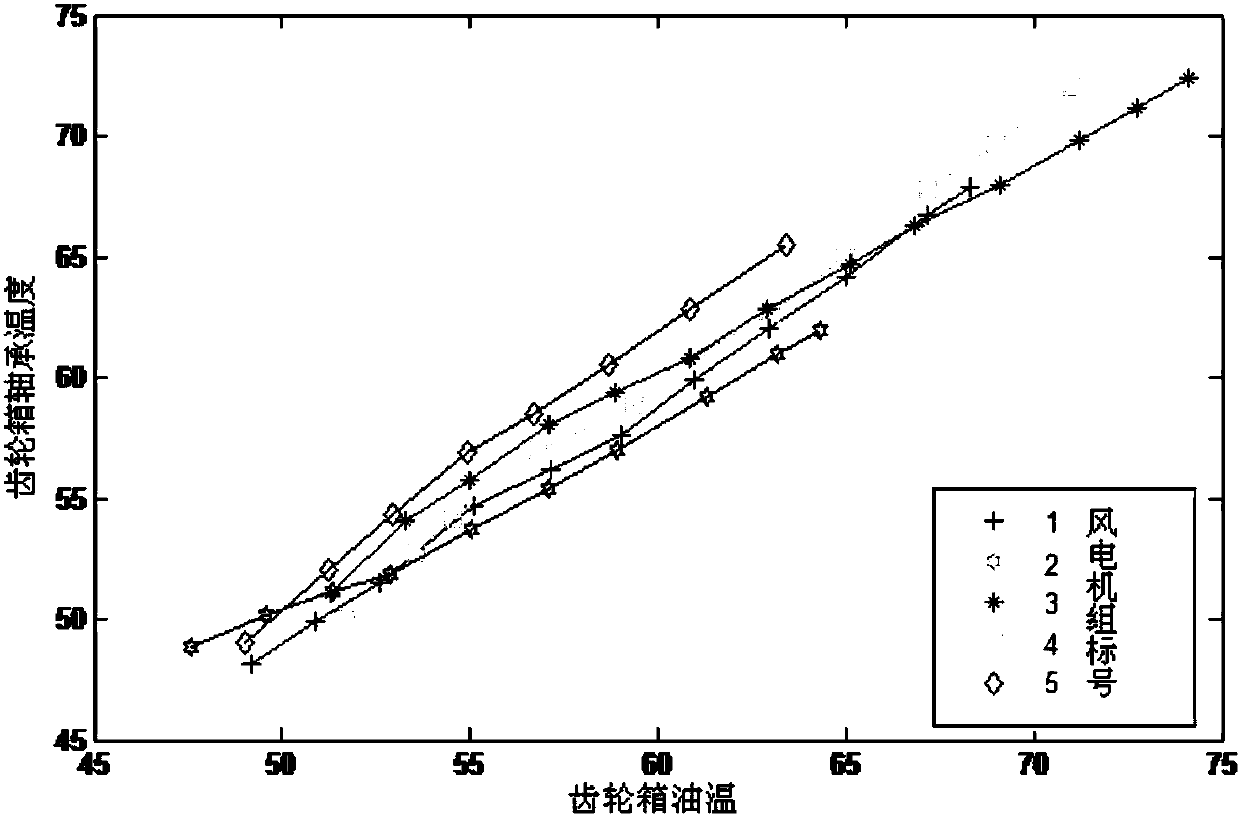
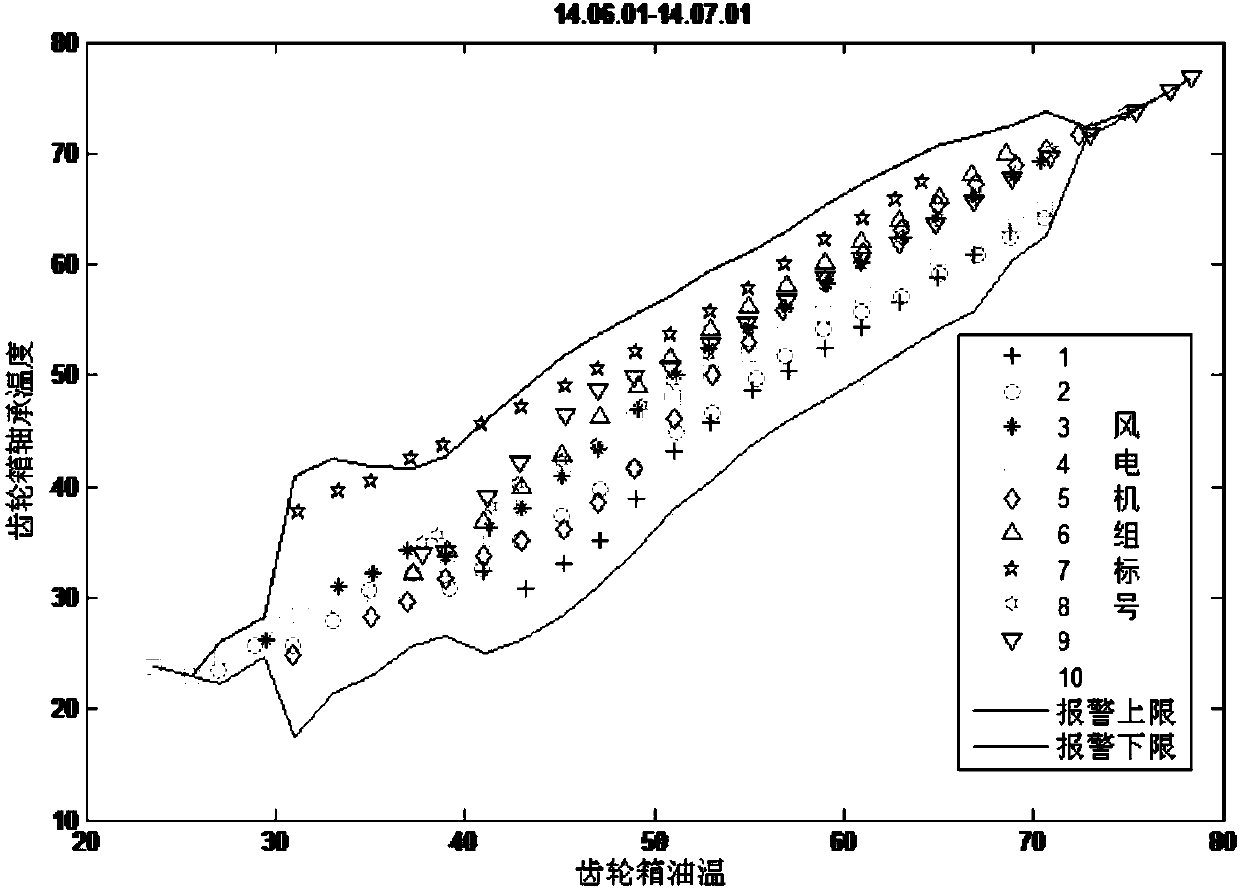
Early-warning method for gear case bearing fault of wind turbine generator system
ActiveCN108072524AGood effectThe calculation method is concise and efficientMachine bearings testingElectricityCorrelation coefficient
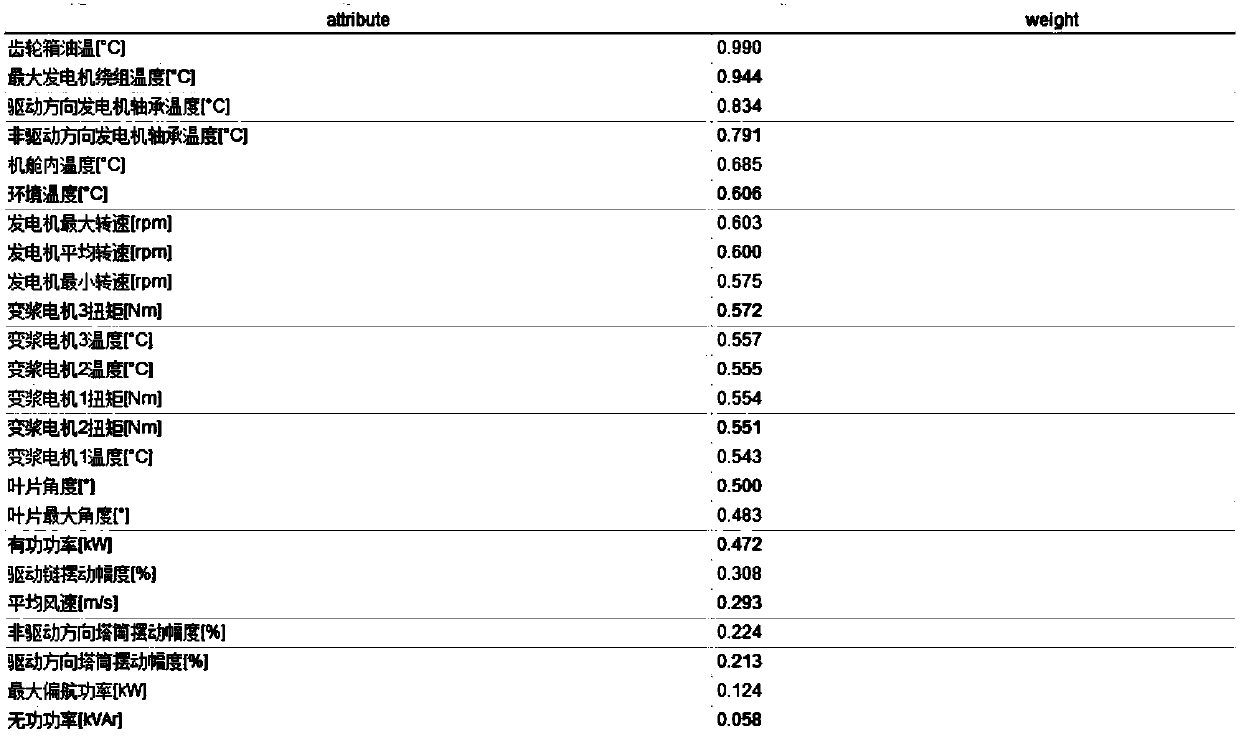
The invention provides an early-warning method for gear case bearing faults of a wind turbine generator system. The method comprises the following steps: collecting SCADA operation data, selecting parameters, analyzing parameter correlation, determining target variables and analysis variables, conducting interval analysis of the target variables, conducting target variable cluster statistic analysis, and determining states of a wind turbine generator system, wherein the selected parameters include gear case bearing temperature, gear case oil temperature, average wind speed, generator rotatingspeed and active power, correlation coefficients between the parameters are calculated, interval analysis is conducted by taking the analysis variables as an x-axis and the target variables as a y-axis, cluster statistic analysis of the target variables in the same interval is conducted, and whether gear case bearing faults of the wind turbine generator system exist is judged on the basis of faultalarm threshold values. According to the technical solution of the invention, an operation method is simple and highly efficient, the cost is not increased additionally, and fewer system resources are occupied.
Owner:CHINA ELECTRIC POWER RES INST +2
Applied system and its data processing method for computer
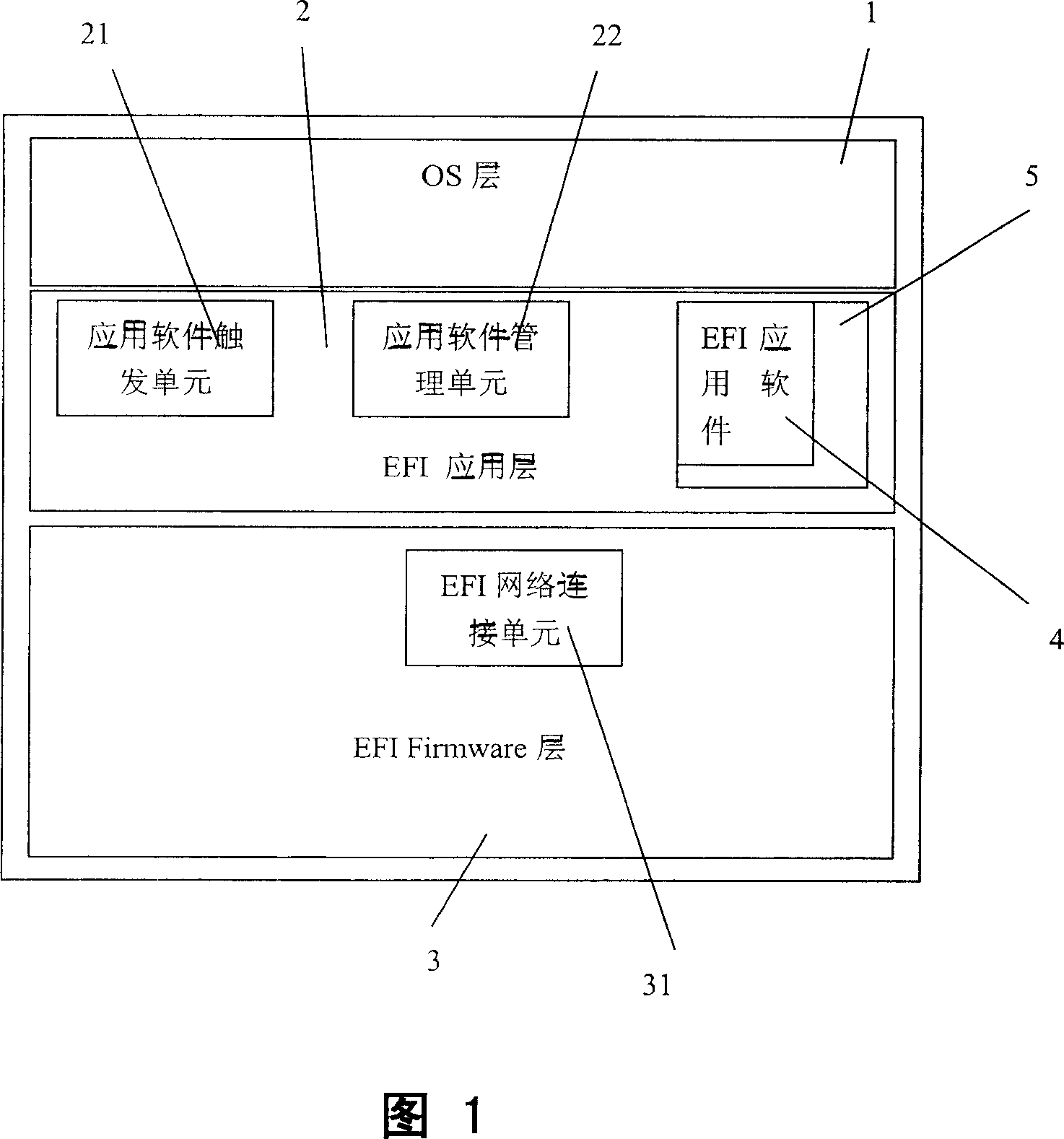
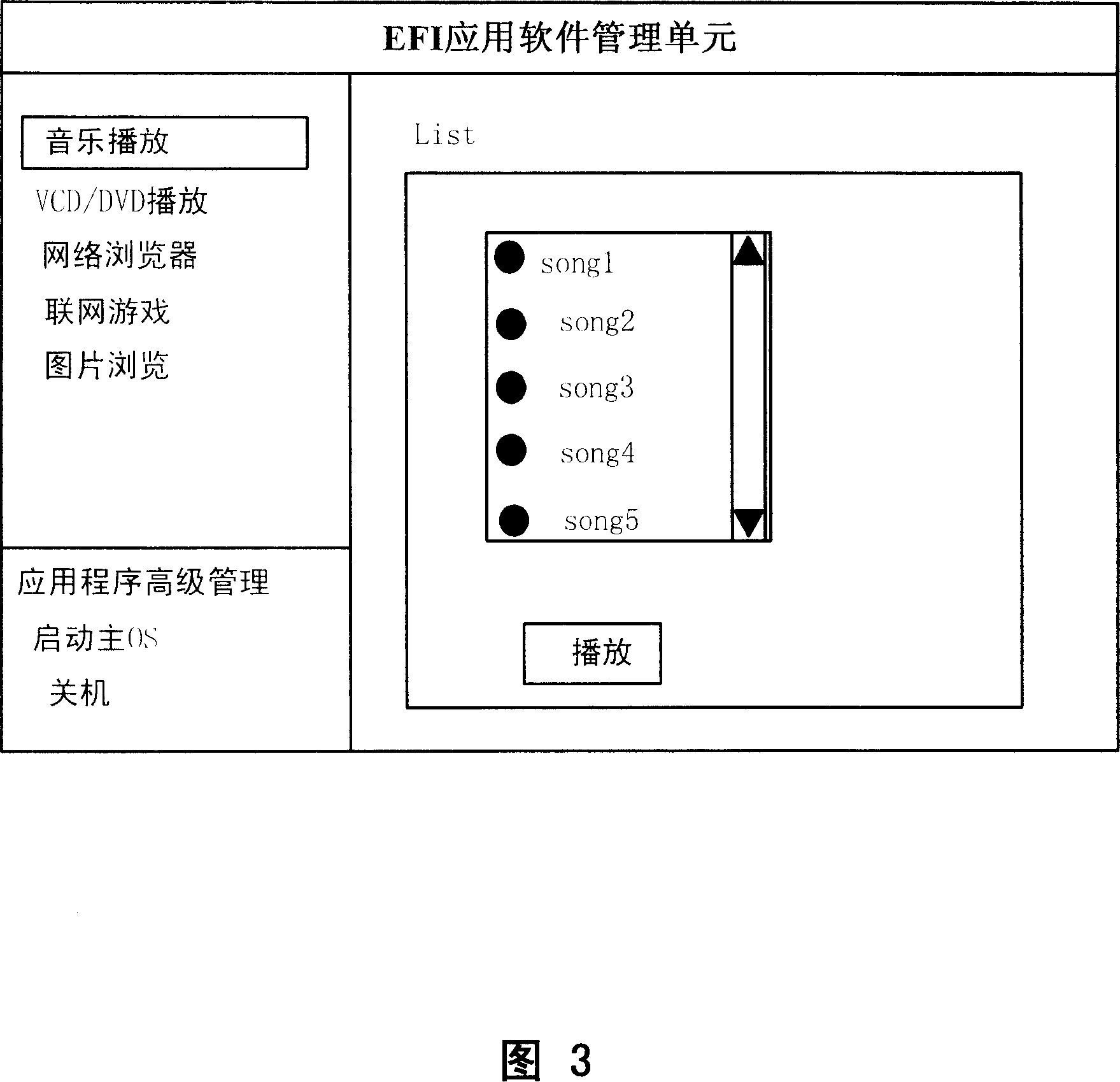
InactiveCN1940868AImprove experienceLow costProgram loading/initiatingManagement unitOperational system
A computer application system comprises hardware, software with EFI application software, EFI application software triggering unit, EFI application software management unit and EFI network connection unit. It is featured as starting up computer and EFI application software management unit, scanning EFI safety storage region by said management unit to display out all listings of EFI application software, executing EFI application software if starting up of EFI application software is selected by user and switching off computer when application software is no longer executing by user.
Owner:LENOVO (BEIJING) LTD
Core copyright anonymous authentication method
ActiveCN109766672AAchieve protectionRealize traceabilityDigital data authenticationProgram/content distribution protectionAnonymous authenticationSoftware
The invention discloses a core copyright anonymous authentication method, which adopts an application principle of a double-PUF structure to realize copyright authentication of a hardware FPGA and a software IP. Due to the use of the double-PUF structure, the FPGA provider does not need to pre-store all excitation response pairs of the PUF, the occupied system resources are few, and the safety andthe applicability are higher. Before the IP circuit performs transaction, the IP provider embeds copyright information and the anonymous identity of the purchaser into the IP core to realize passiveIP copyright protection and piracy tracking. The anonymity ensures the rights and interests of the purchaser, and the tracking and tracing of piracy behaviors can be realized under the participation of the trusted equipment provider.
Owner:HUNAN UNIV
Control method for peer-to-peer calculation set-top box player
InactiveCN101442627AImprove healthImprove reliabilityTelevision system detailsColor television detailsPeer to peer computingRequirements analysis
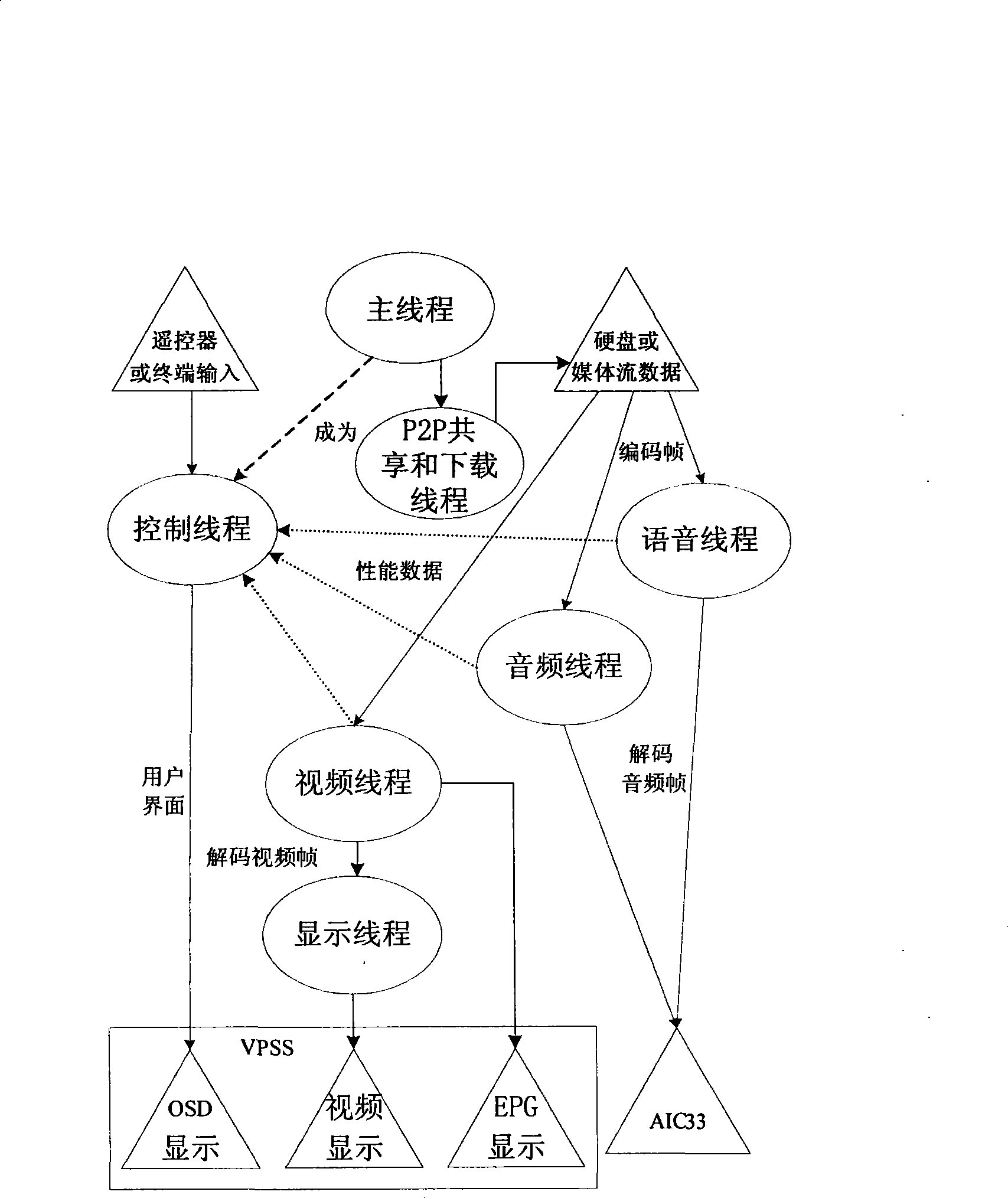
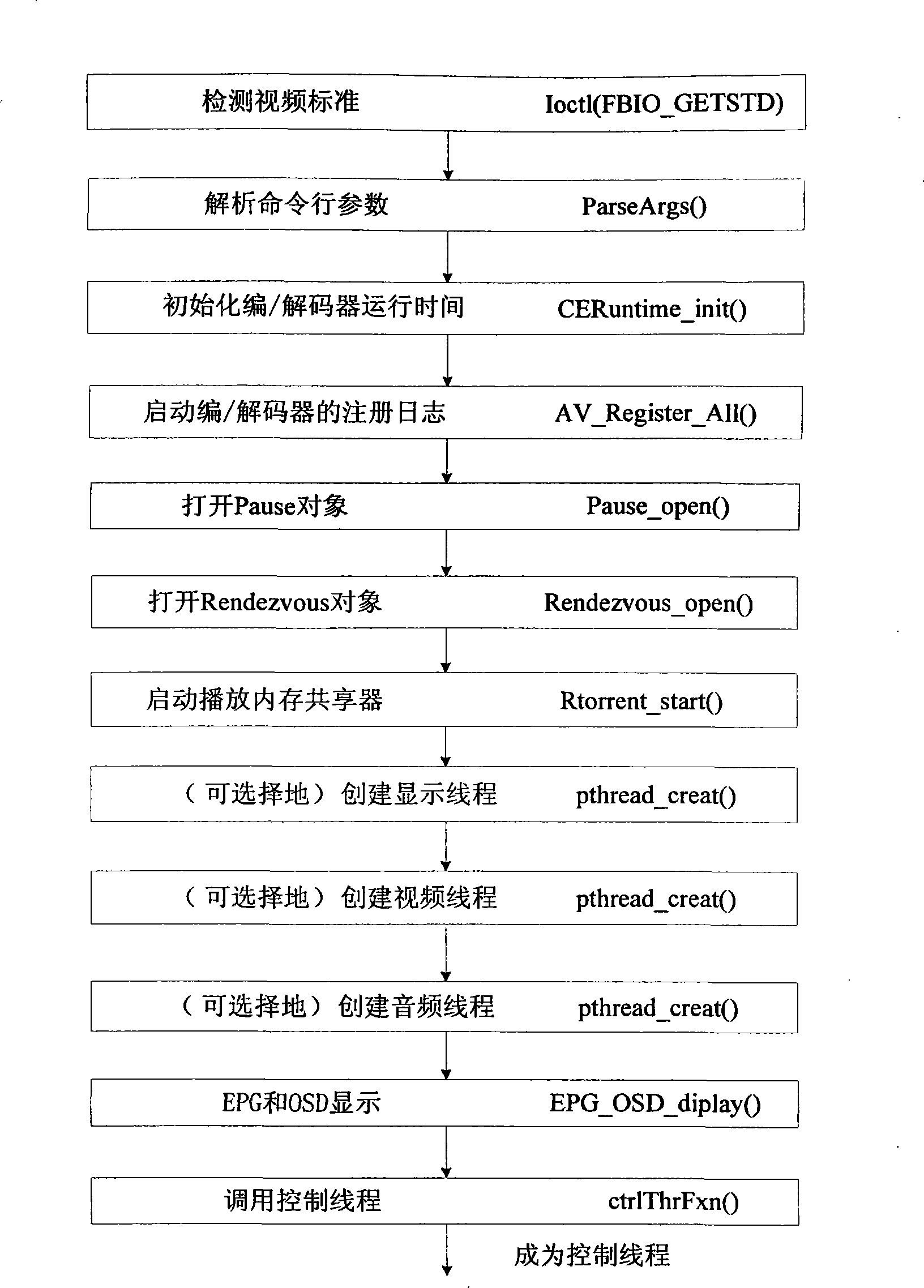
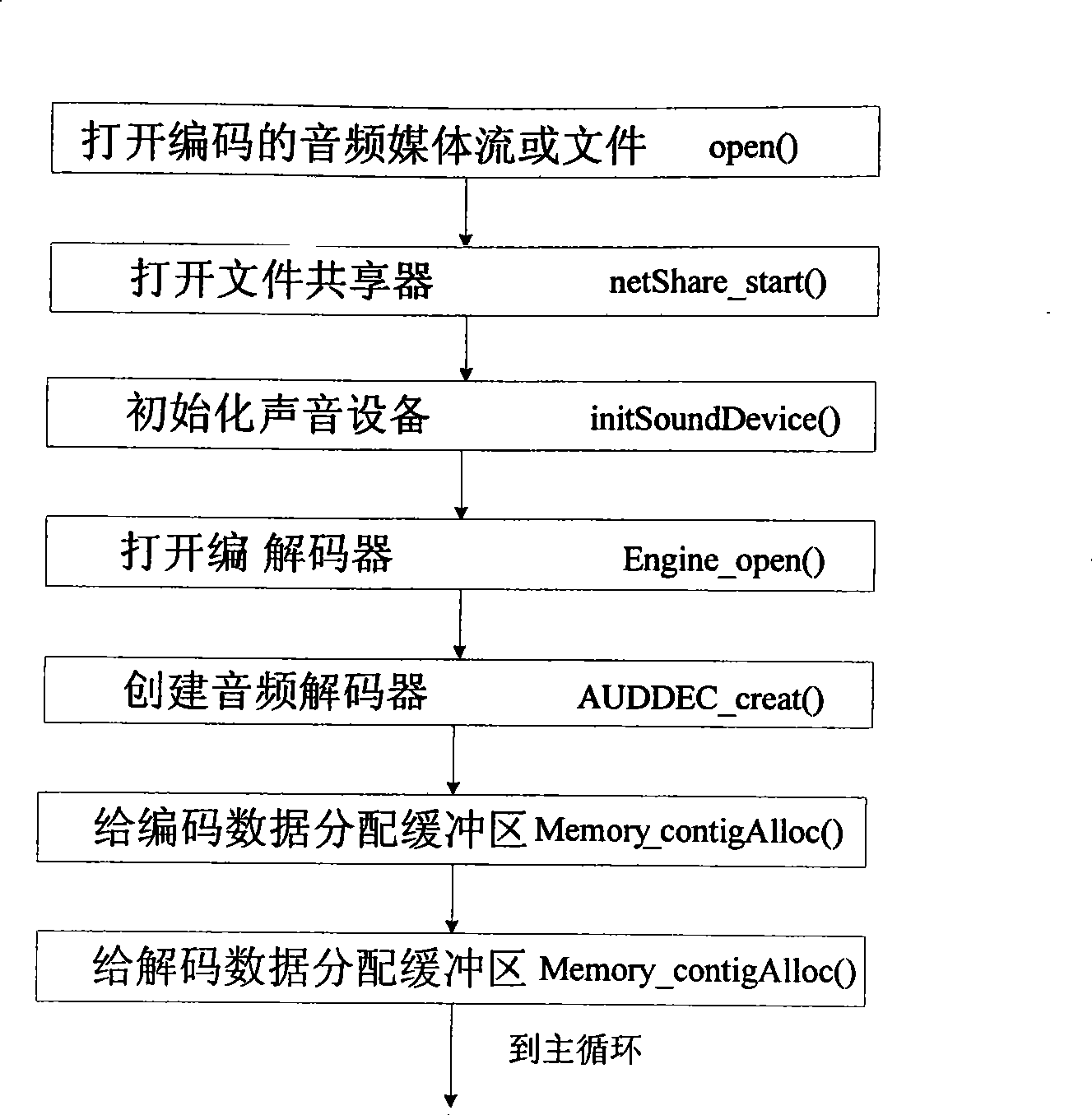
The invention provides a controlling method used for a player of a peer-to-peer computing set top box, which is used for a player of a P2P (Peer-to-Peer) set top box to play a media file which is not completely downloaded in the P2P set top box, thereby solving the problem of downloading, playing while sharing of the P2P set top box. The realizing method of the player comprises: step 1) analyzing requirement; step 2) designing a module according to the analysis file of the step 1); step 3) designing and realizing a main thread and a control thread of the player according to the file of the step 2); step 4) designing and realizing decoding and playing of an audio file and a video file according to the file of the step 2); step 5) designing and realizing a file loading and sharing module according to the file of the step 2); and step 6) providing functions, namely play, pause, stop, position, fast forward and quick backward, for the player so as to ensure that the player can be automatically positioned to corresponding time to start playing after a user fills the time and presses the enter key.
Owner:NANJING UNIV OF POSTS & TELECOMM
Multi-target tracking method, and touch screen control method and system
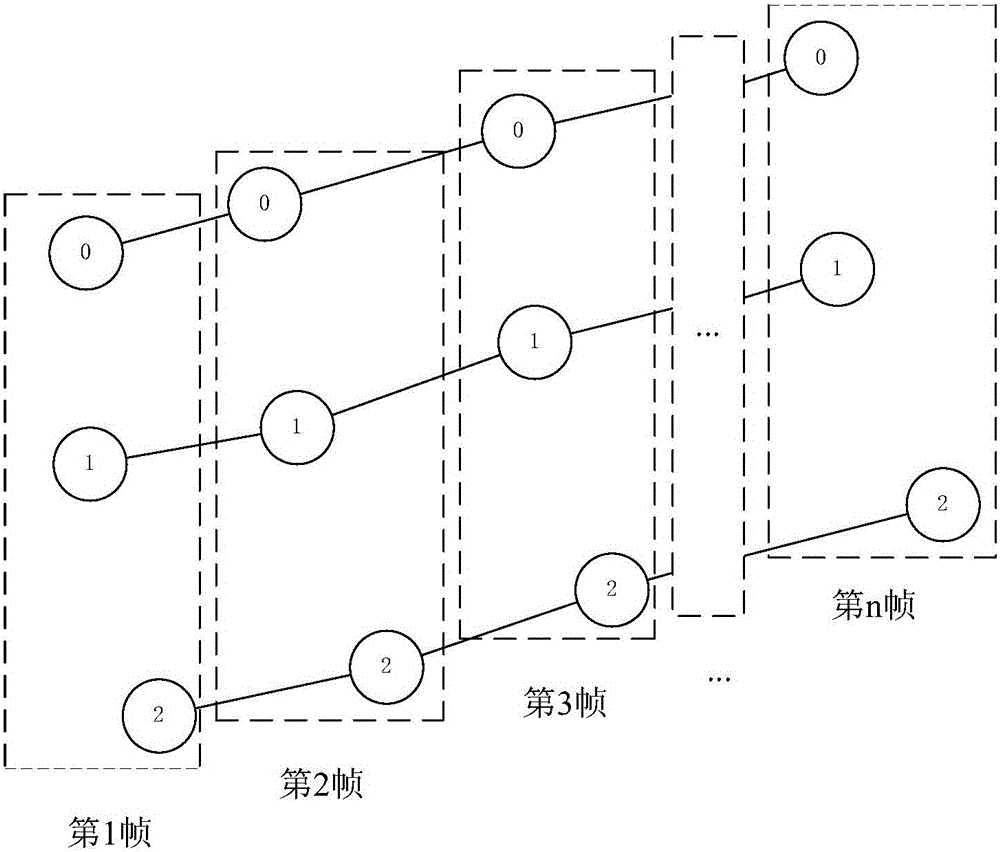
ActiveCN105975119ASimple distribution methodAllocation is fastInput/output processes for data processingMulti target trackingTouchscreen
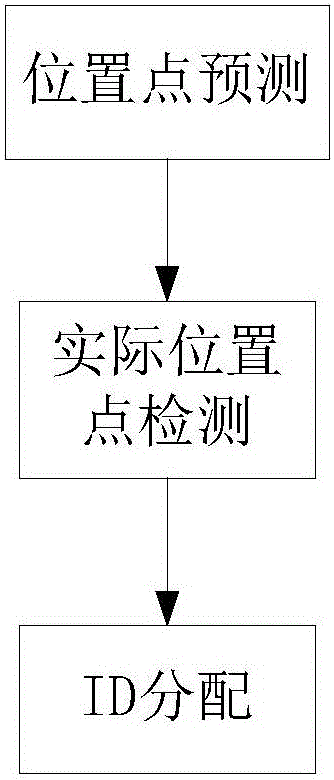
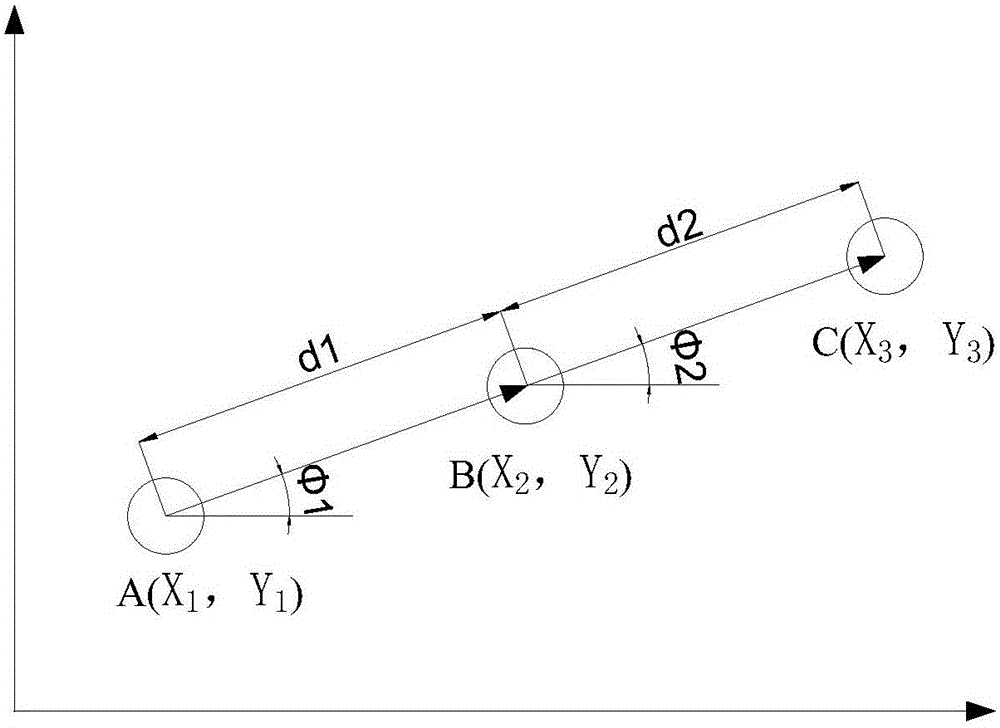
The invention discloses a multi-target tracking method, and a touch screen control method and system. The multi-target tracking method comprises the steps of obtaining a predicted position point of each target in an (n+1)th frame according to the position of each target in first n frames, wherein n is greater than or equal to 2; detecting an actual position point of the target in the (n+1)th frame; and allocating an ID of the target corresponding to the predicted position point to the actual position point corresponding to the predicted position point in the (n+1)th frame. According to the multi-target tracking method provided by the invention, the predicted position point of each target is obtained at first and then the ID of the target corresponding to the predicted position point is allocated to the actual position point corresponding to the predicted position point, so that the allocation method is simple, the allocation speed is high, and the system resource occupation is small.
Owner:CHIPONE TECH BEIJINGCO LTD
Live broadcast content positioning method in video picture-in-picture architecture
ActiveCN110276769ARapid positioningOccupies less system resourcesImage analysisEnergy efficient computingImage areaMultimedia
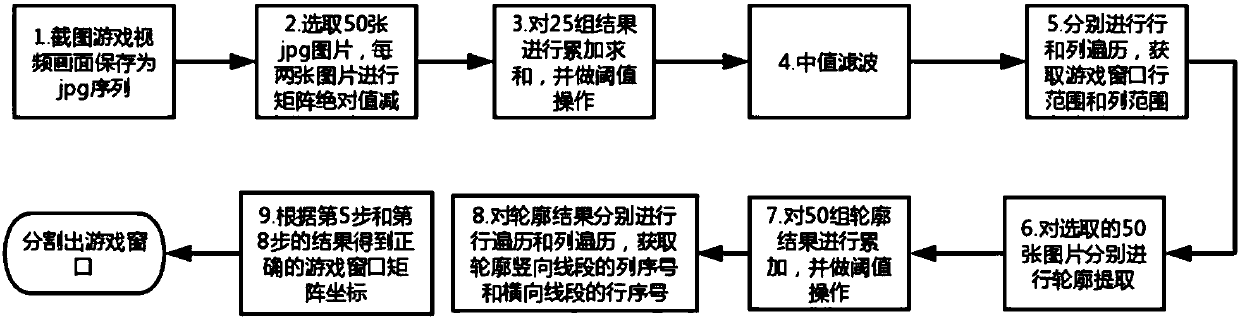
The invention discloses a live broadcast content positioning method in a video picture-in-picture architecture. The live broadcast content positioning method comprises the following steps: S1, intercepting a video picture and storing the video picture in a picture format; S2, selecting a plurality of pictures in the intercepted pictures, selecting the number of the pictures to be recorded as L, performing rectangular subtraction calculation on two pictures in the selected pictures as a group, taking an absolute value of a difference, and performing a plurality of groups of rectangular subtraction calculation to obtain a plurality of groups of results; S3, accumulating and summing the results in the step S2, and carrying out threshold operation; S4, performing filtering operation on the data obtained in the step S3; S5, carrying out row traversal and column traversal respectively, and obtaining a game window row range and a game window column range; and S9, obtaining correct game window matrix coordinates according to the result of the step S5, and segmenting the game window. According to the live broadcast content positioning method in the video picture-in-picture architecture provided by the invention, the live broadcast image area can be quickly positioned, and the influence caused by live broadcast image change is very small, and the occupied system resource is relatively low.
Owner:上海薇龙文化传播有限公司
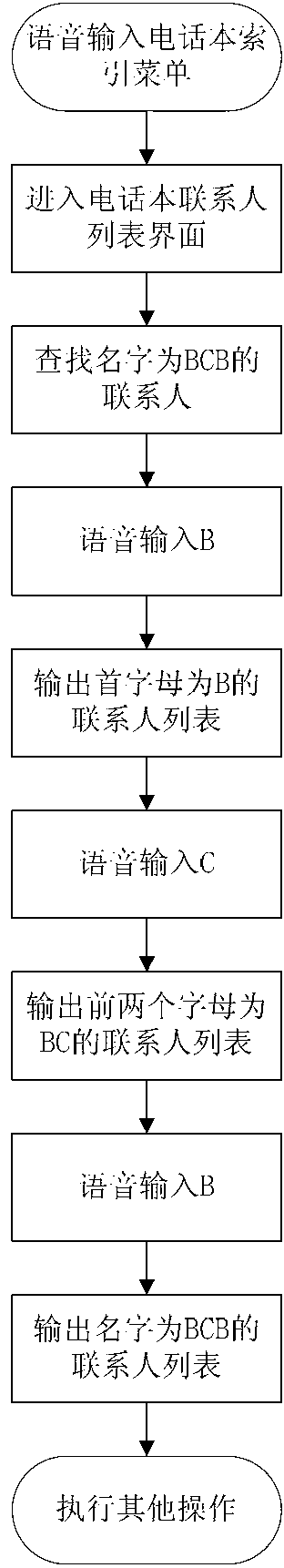
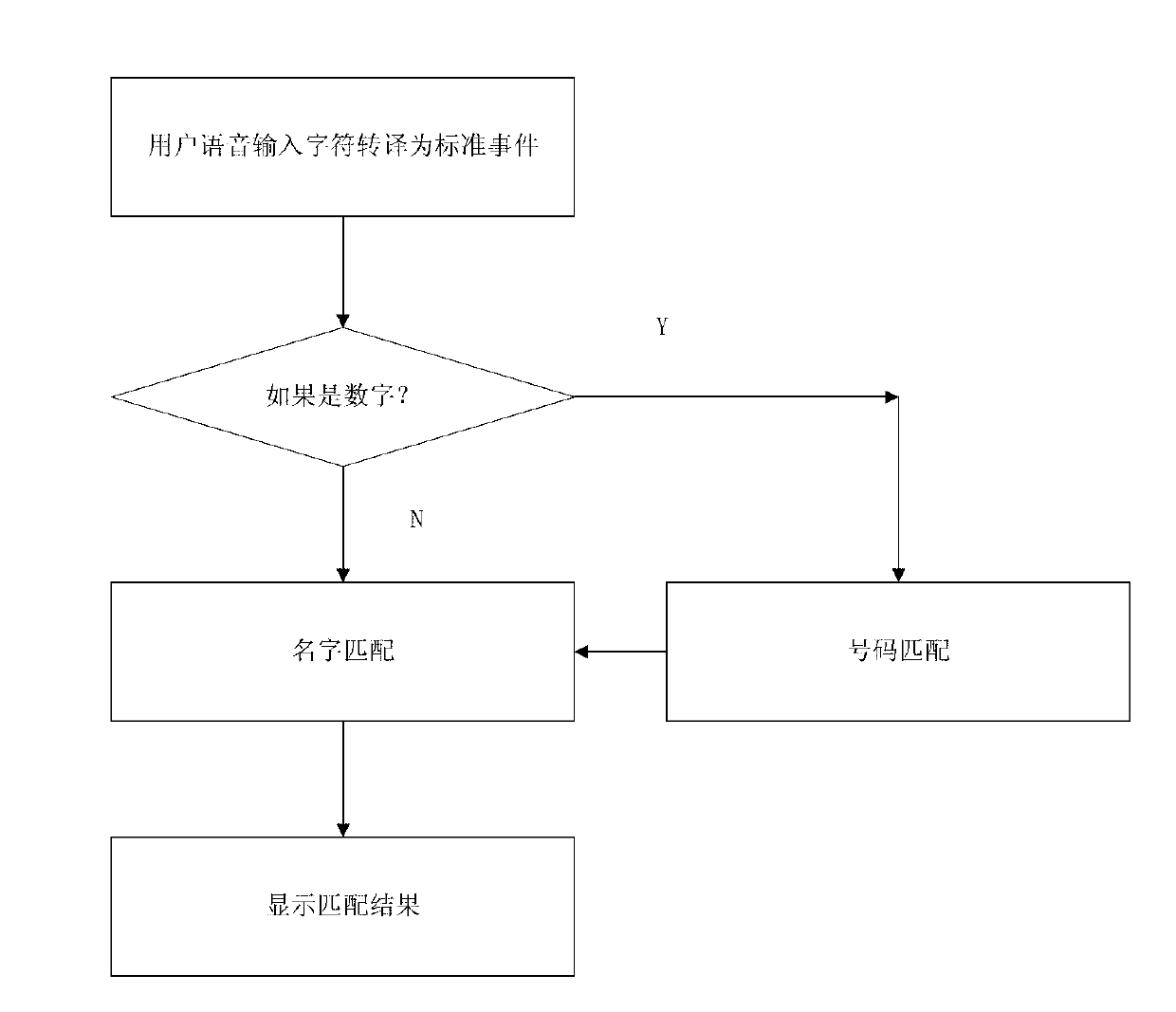
Speech recognition character index based method and system for searching
ActiveCN102999639ASmall amount of calculationImprove recognition accuracySpeech recognitionSpecial data processing applicationsUser inputSpeech sound
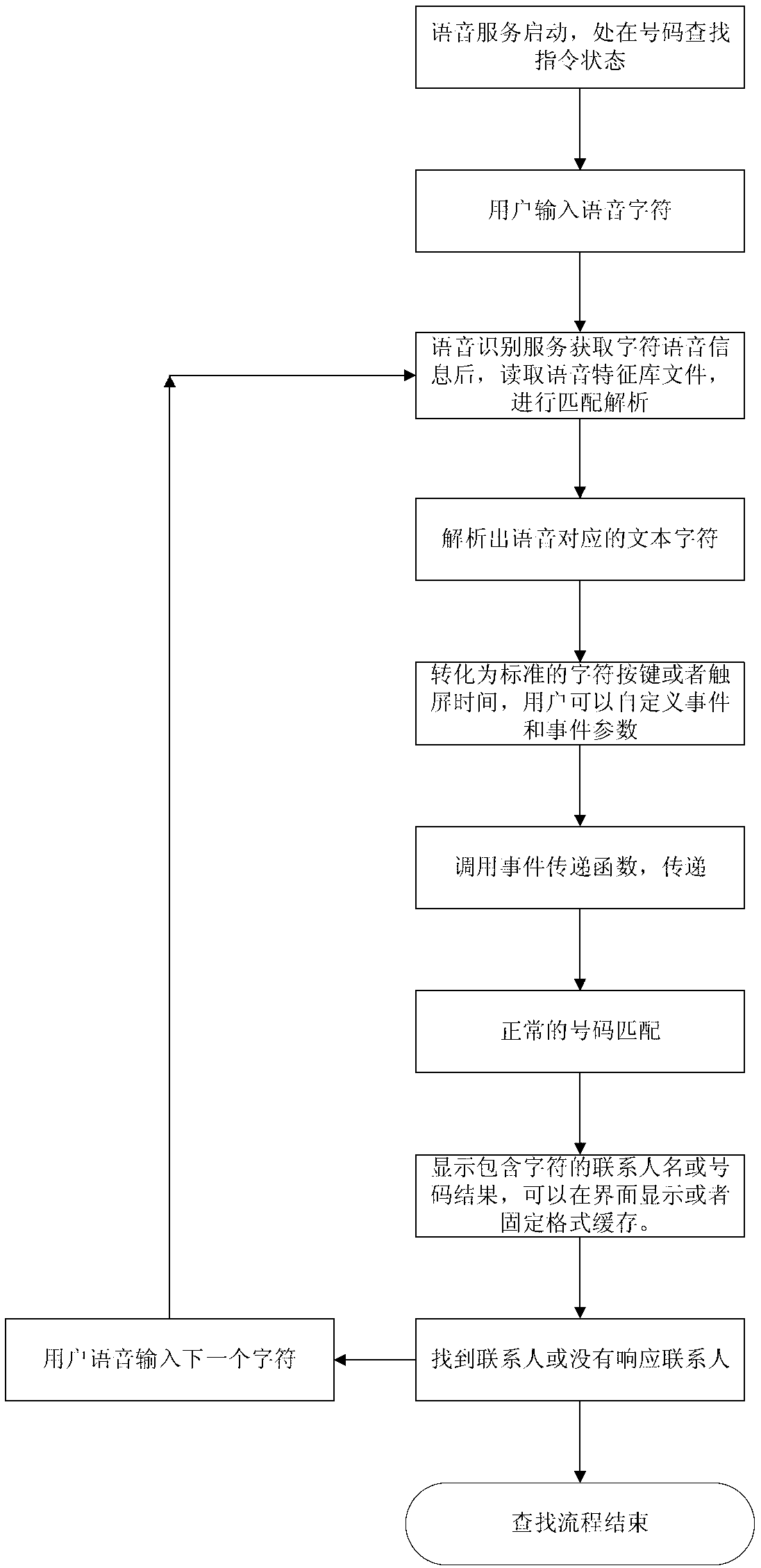
The invention discloses a speech recognition character index based method and a system for searching. The method comprises that a user inputs basic characters through speeches, and speeches of all basic character combinations read out by the user are recognized, translated into basic character combination text indexes, further translated into standard key events, touch screen events and user-defined events recognized by the user and transferred to an application scenario or an application interface to be searched through a standard event transfer function, so that searching of speech recognition character indexes can be achieved. The system comprises a speech recognition engine service device, a reading and translating device, a translating recognition device and a matching device, wherein the speech recognition engine service device is used for recognizing basic characters input by the user through speeches, and basic characters serve as character indexes for speech recognition. By the aid of the method and the system, the quick searching function of speech recognition character indexes is achieved.
Owner:NUBIA TECHNOLOGY CO LTD
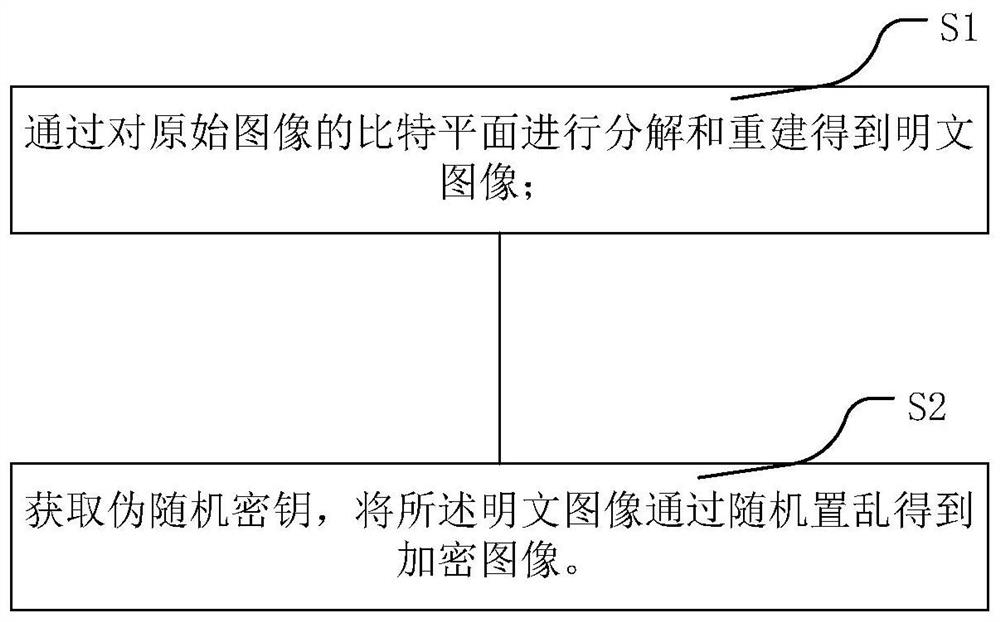
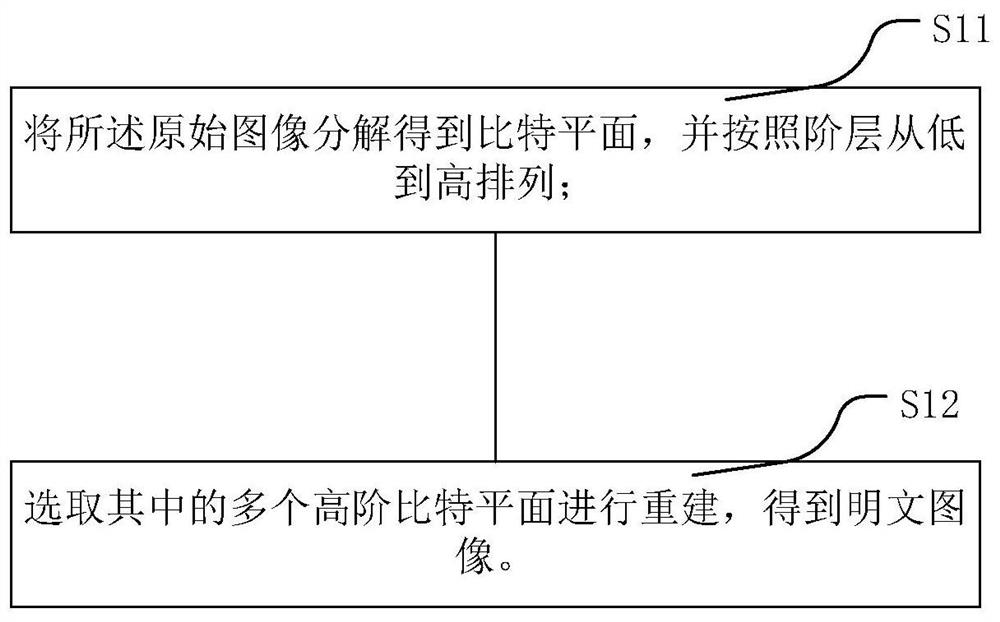
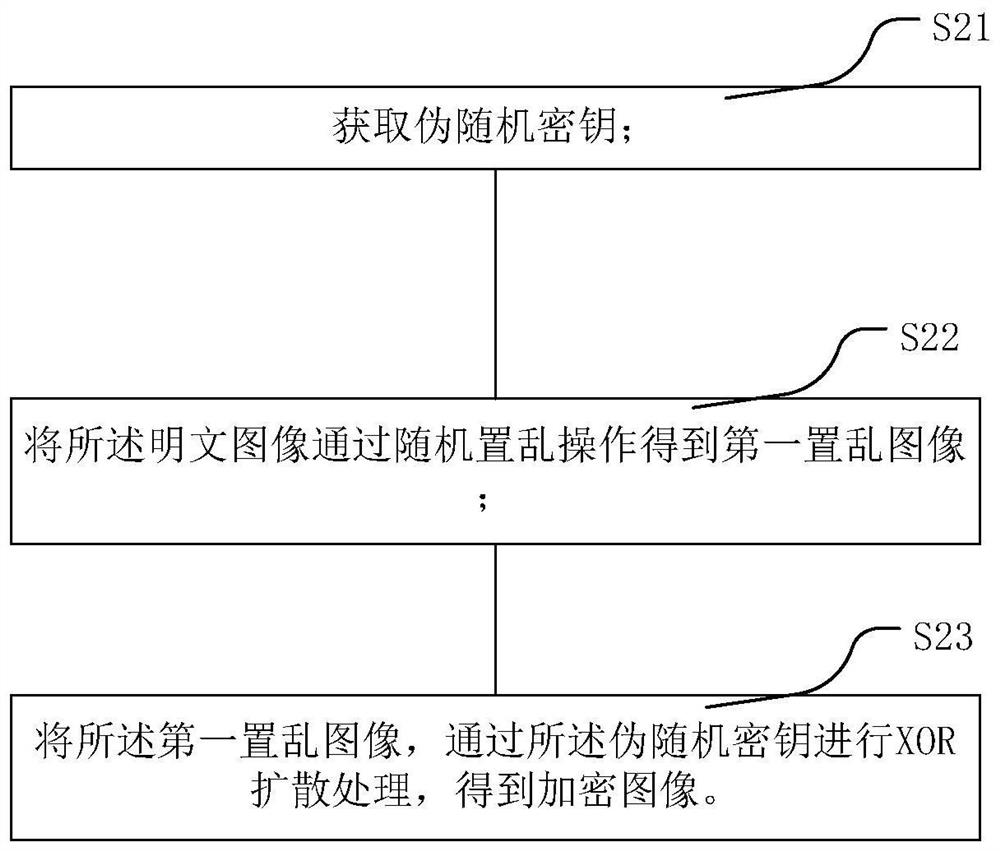
Image encryption and decryption method and image encryption and decryption system
PendingCN112636895ASave storage spaceSave resourcesKey distribution for secure communicationSecuring communication by chaotic signalsEncryption decryptionComputer vision
The invention relates to an image encryption and decryption method and an image encryption and decryption system. The invention discloses an image encryption and decryption method, and the method comprises an image encryption operation step: S1, carrying out the decomposition and reconstruction of a bit plane of an original image, and obtaining a plaintext image; and S2, acquiring a pseudo-random key, and randomly scrambling the plaintext image to obtain an encrypted image. According to the image encryption and decryption method provided by the invention, the encrypted image obtained by using the encryption operation is subjected to security analysis and differential attack resistance analysis, so that the effectiveness of the algorithm is ensured, and the pixel correlation of the encrypted image tends to 0. Compared with an existing encryption algorithm in performance, a result obtained by feedback proves that the encrypted image obtained by using the image encryption method provided by the invention is excellent in safety performance.
Owner:CHANGSHA UNIVERSITY OF SCIENCE AND TECHNOLOGY
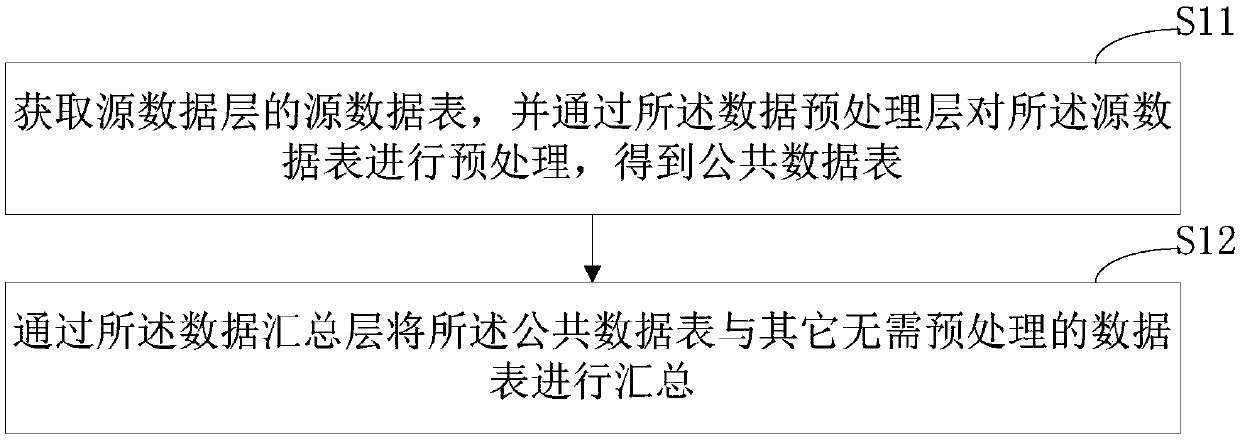
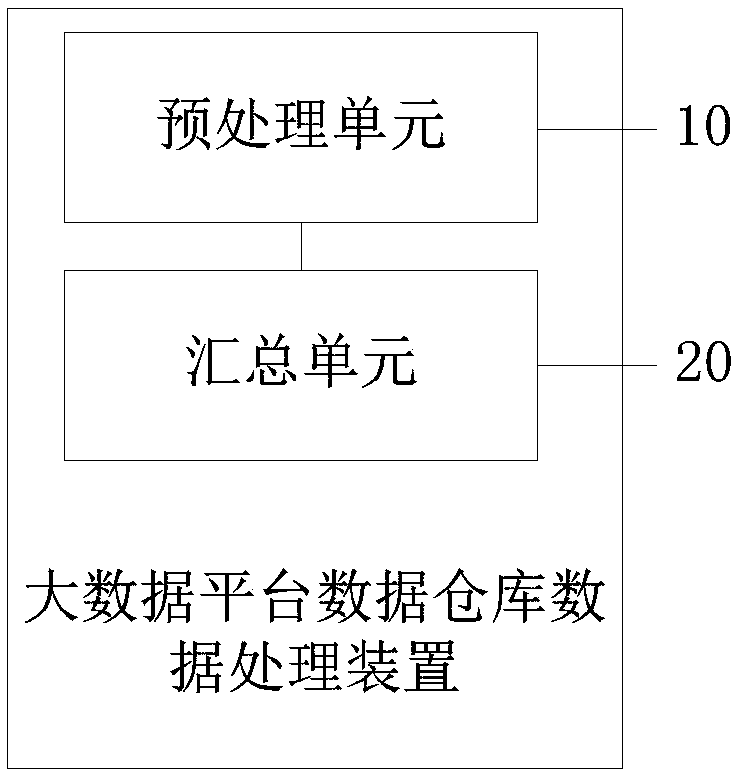
Big data platform data warehouse data processing method and device and computer equipment
PendingCN109597846AOccupies less system resourcesReduce latencyDatabase management systemsData warehouseData pre-processing
The invention discloses a big data platform data warehouse data processing method and device and computer equipment. A data warehouse layer of a data warehouse comprises a data preprocessing layer anda data summarizing layer, and the data summarizing layer depends on the data preprocessing layer; The processing method comprises the steps of obtaining a source data table of a source data layer, and preprocessing the source data table through a data preprocessing layer to obtain a public data table; And summarizing the public data table and other data tables which do not need to be preprocessedthrough the data summarizing layer. According to the invention, the data warehouse layer of the data warehouse is divided into the data preprocessing layer and the data summarizing layer; According to the method, the common data table is obtained by cleaning the data and placing the data in the data preprocessing layer, repeated processing on the same source data table is not needed, repeated processing of the data is avoided, occupation of system resources is reduced, the same data processing amount is achieved, and the delay condition of the method is far lower than that of the prior art.
Owner:PING AN TECH (SHENZHEN) CO LTD
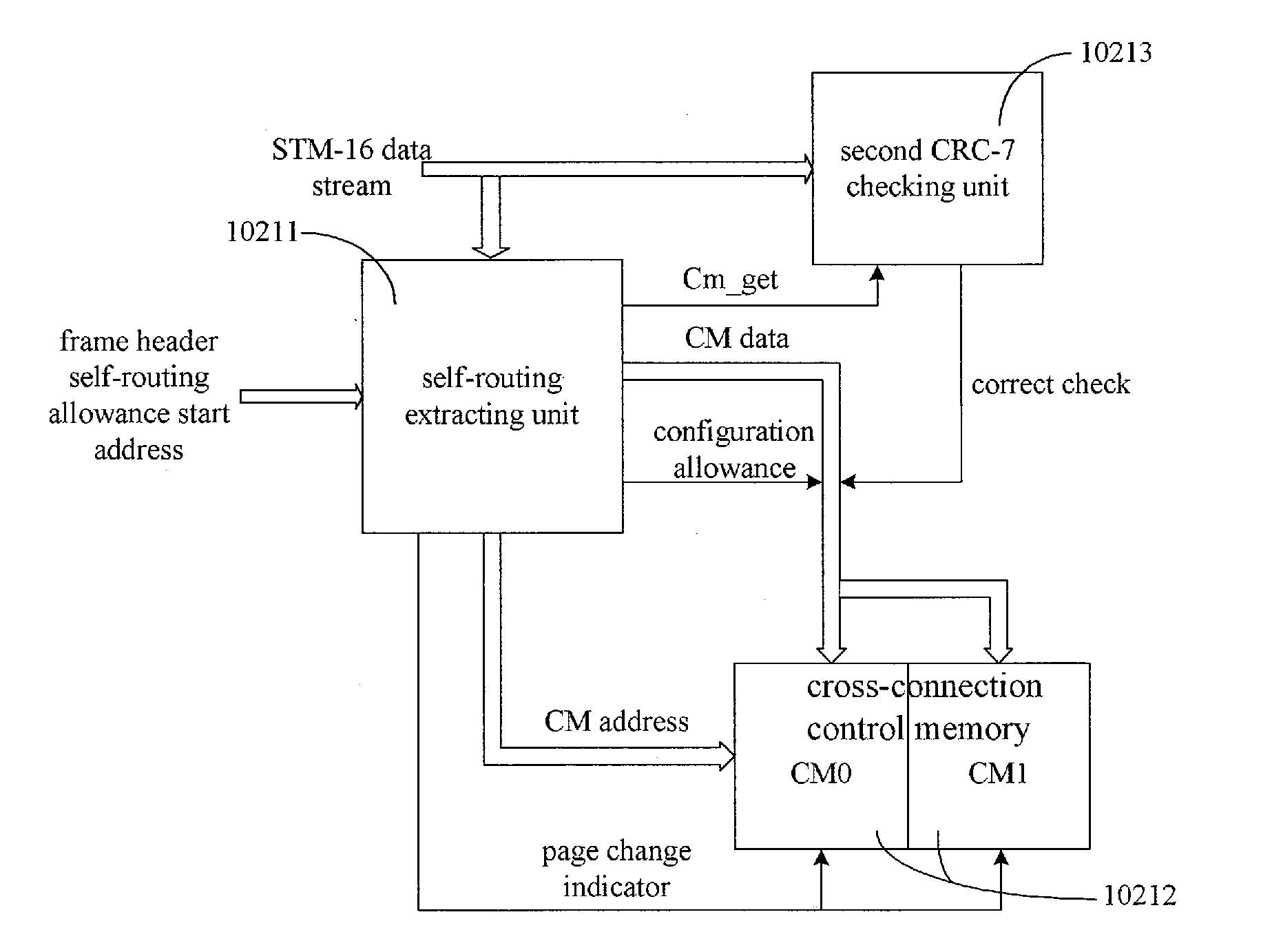
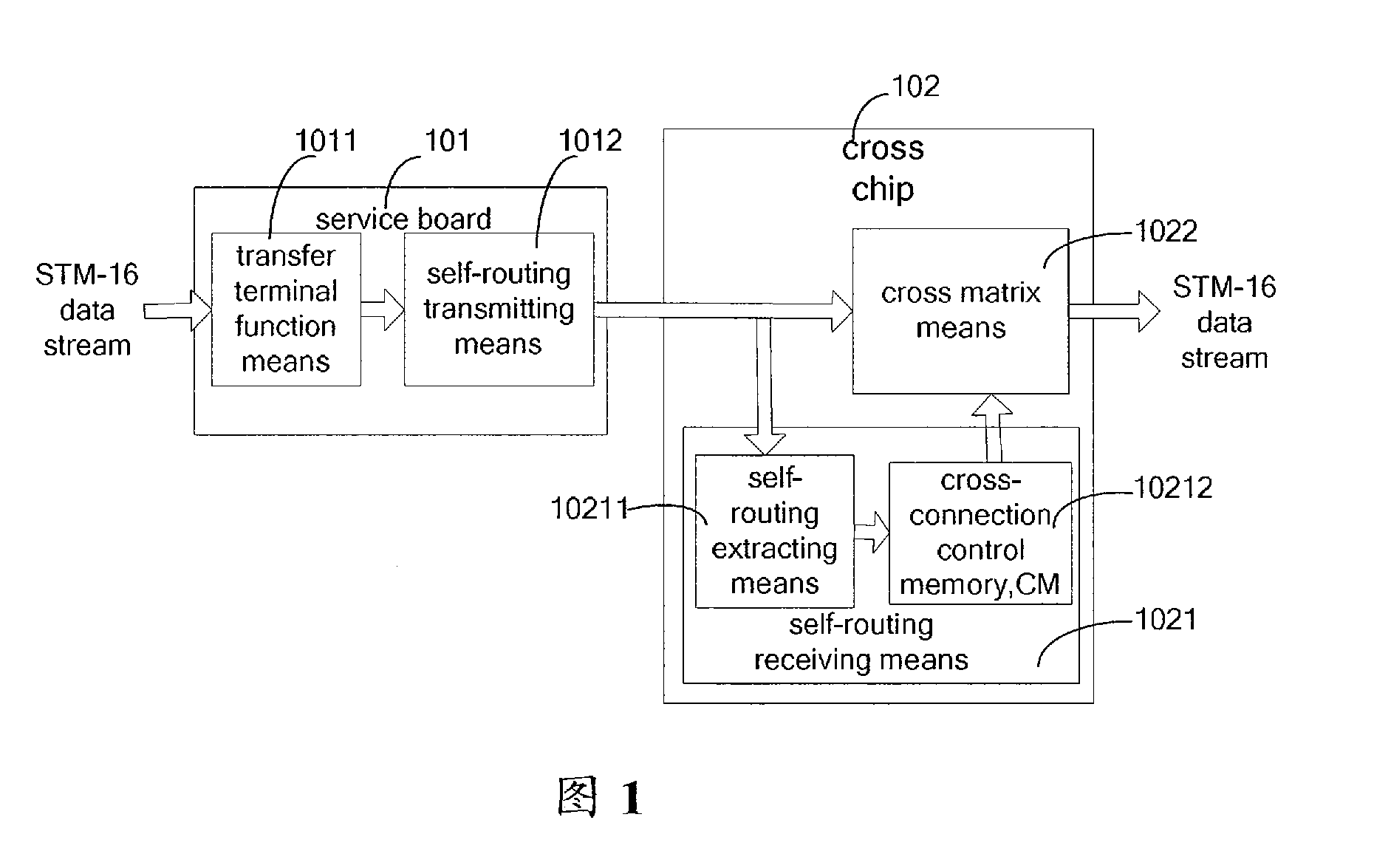
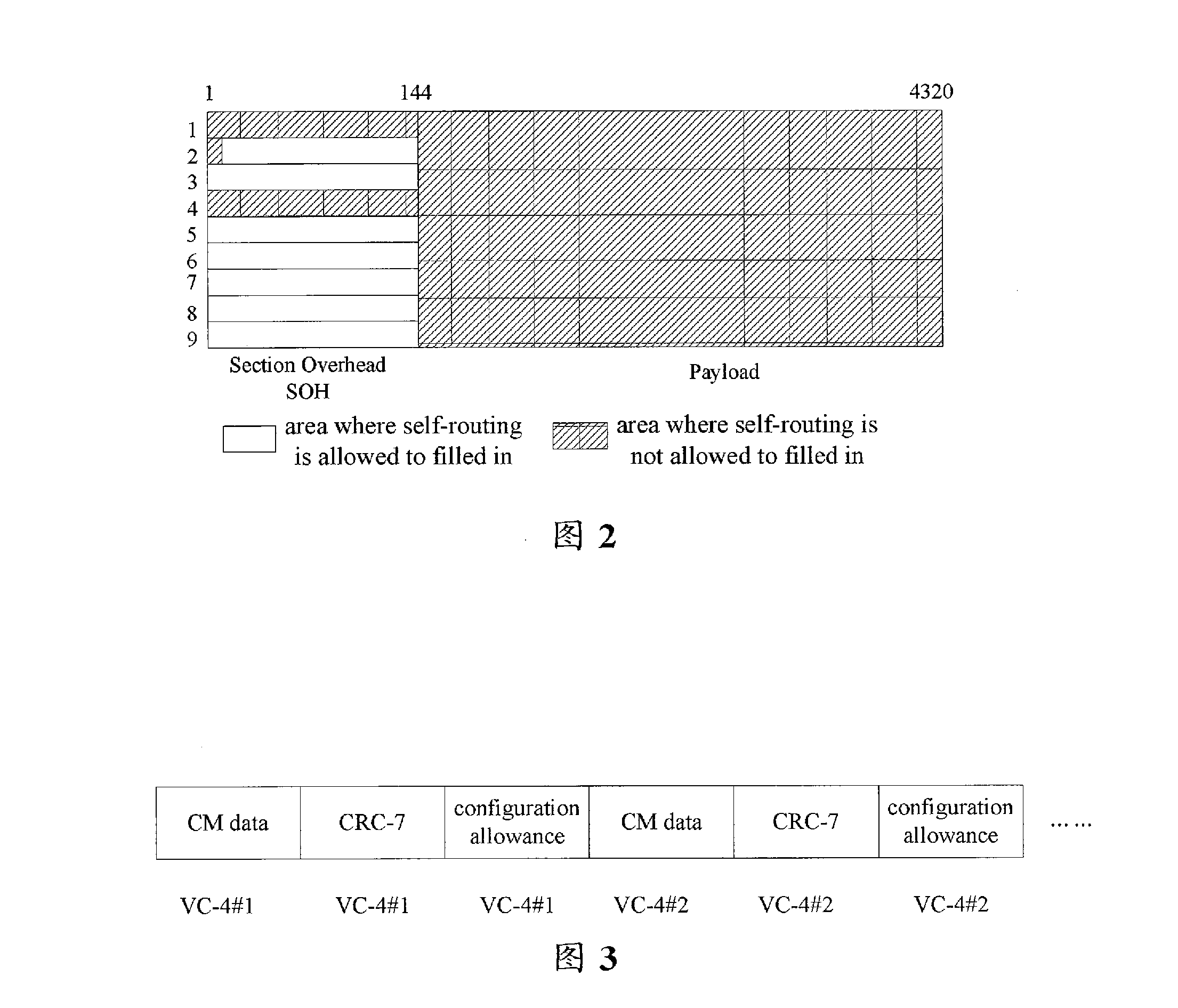
Synchronous digital cross connecting self-routing method and system
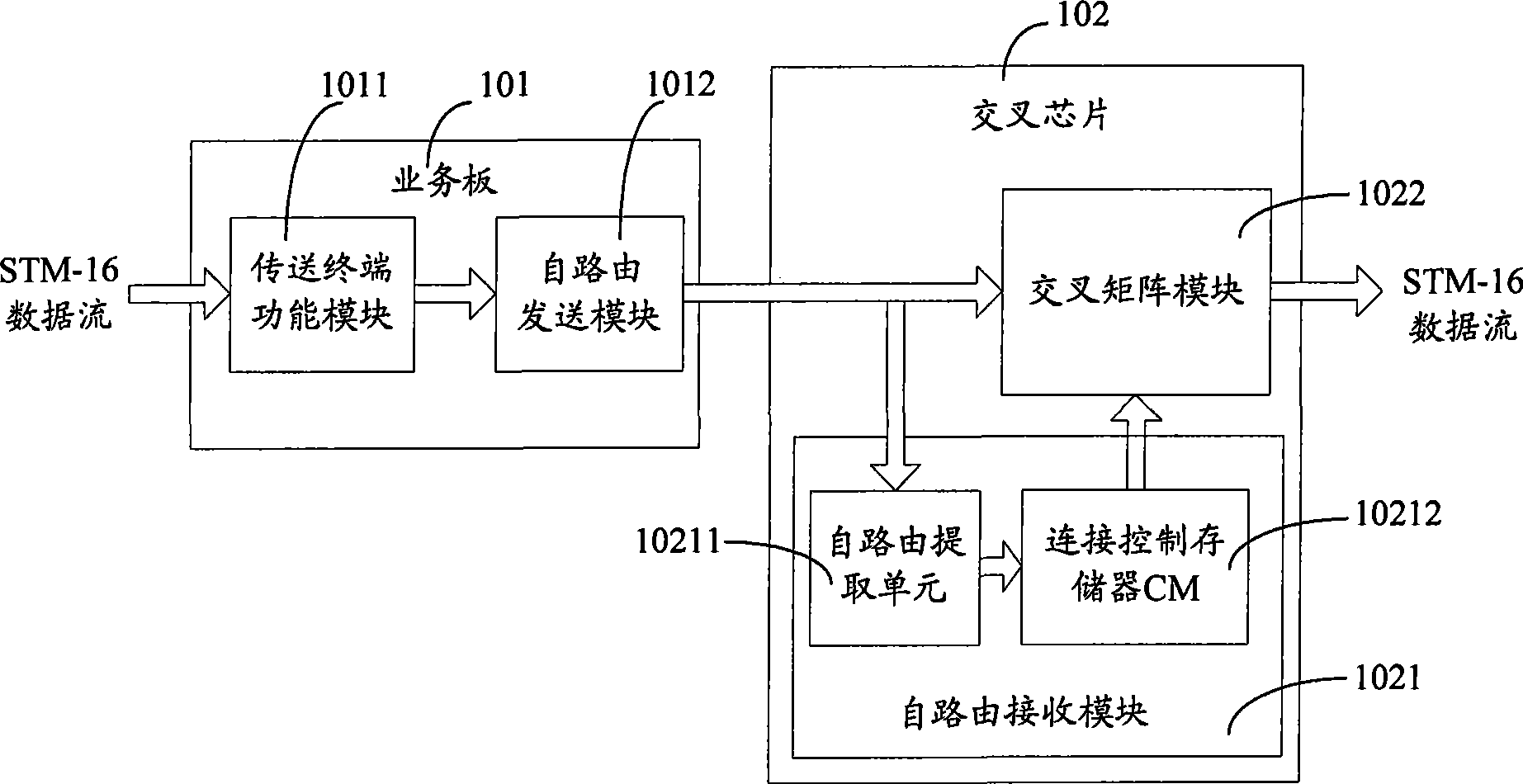
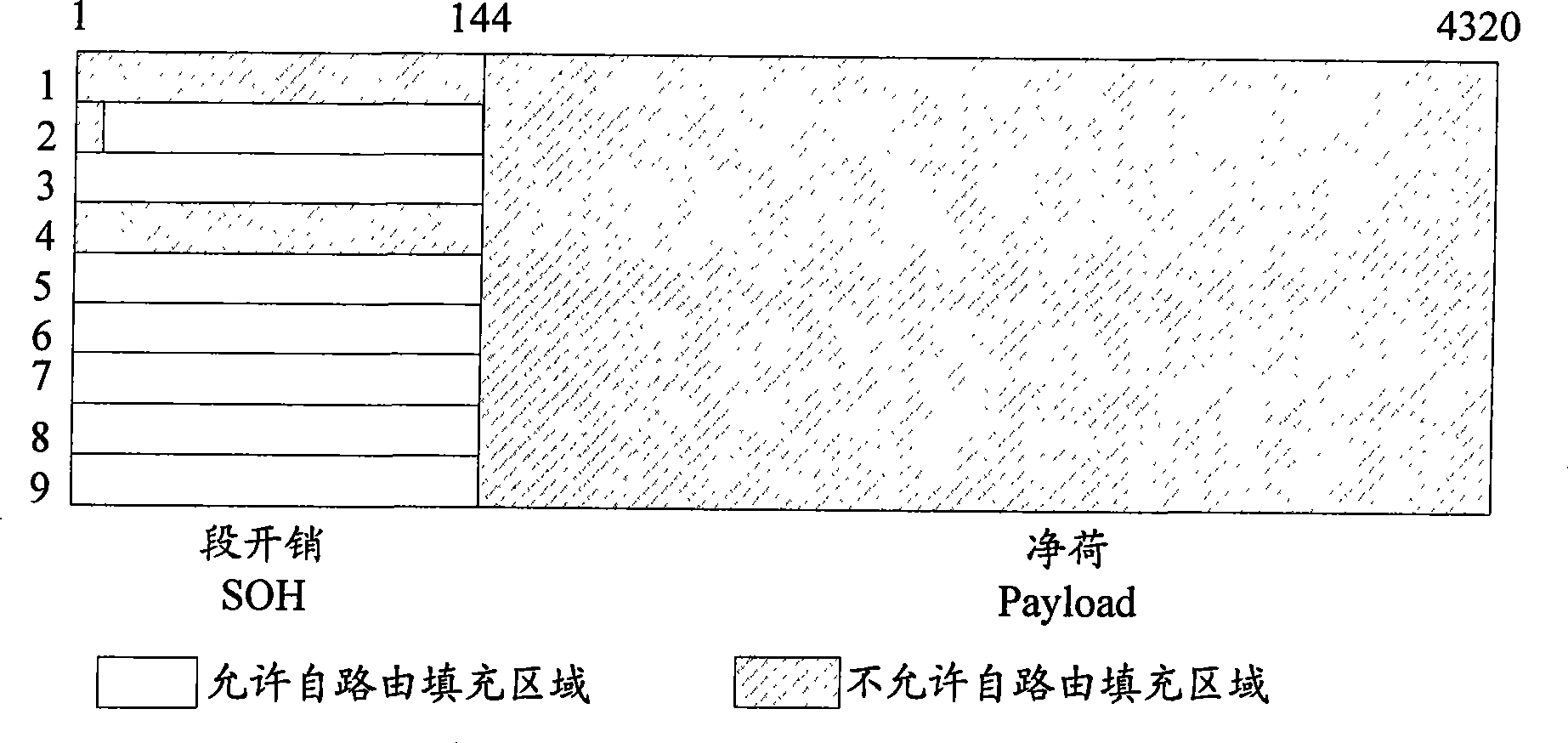
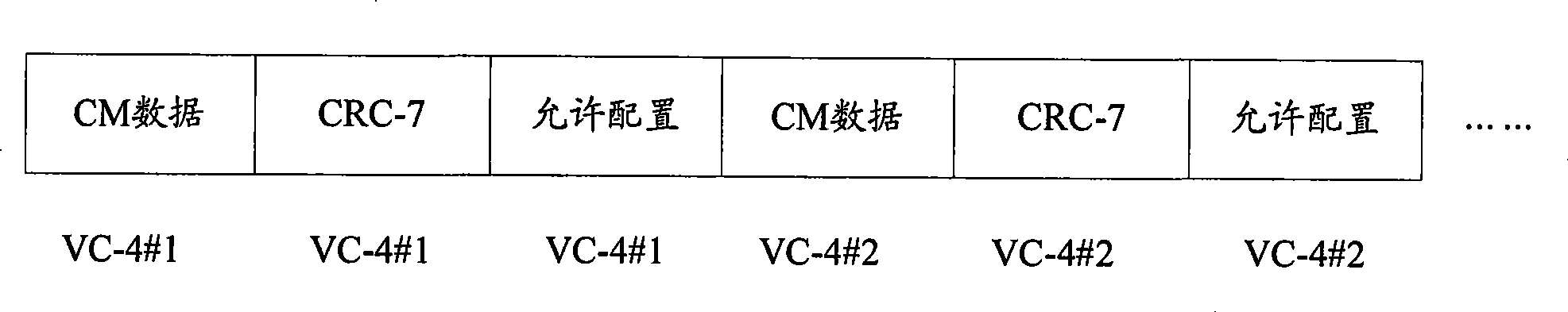
InactiveCN101394335AEasy to implementOccupies less system resourcesError preventionData switching networksData streamCross connection
The invention discloses a self-routing method for synchronous digital cross connect equipment, which comprises the following steps: a self-routing transmitting module inserts controller memory (CM) data into a STM-N data stream in accordance with a frame header marker and a self-routing start address signal; and a self-routing receiving module extracts the CM data from the STM-N data stream in accordance with the frame header marker and the self-routing start address signal, and writes the CM data into a cross connect control memory. The invention also discloses a self-routing system for synchronous digital cross connect equipment, which comprises a self-routing transmitting module and a self-routing receiving module; wherein the self-routing transmitting module comprises a self-routing transmitting control unit, a first cyclic redundancy check (CRC) unit, and an insert data generating unit; and the self-routing receiving module comprises a self-routing extraction control unit, a second CRC unit and a cross connect control memory. The invention provides a self-routing solution for users, has the advantages of easy implementation, low occupied system resources and high reliability, and is suitable for high-capacity synchronous digital cross connect equipment.
Owner:ZTE CORP
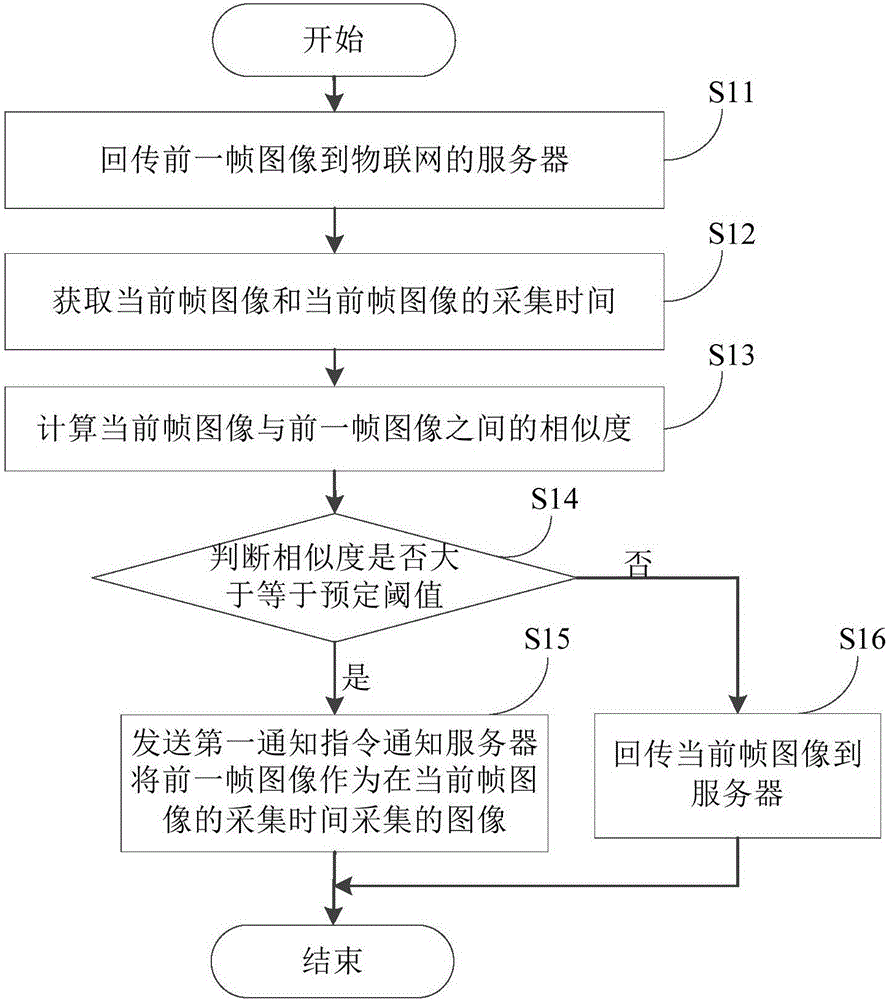
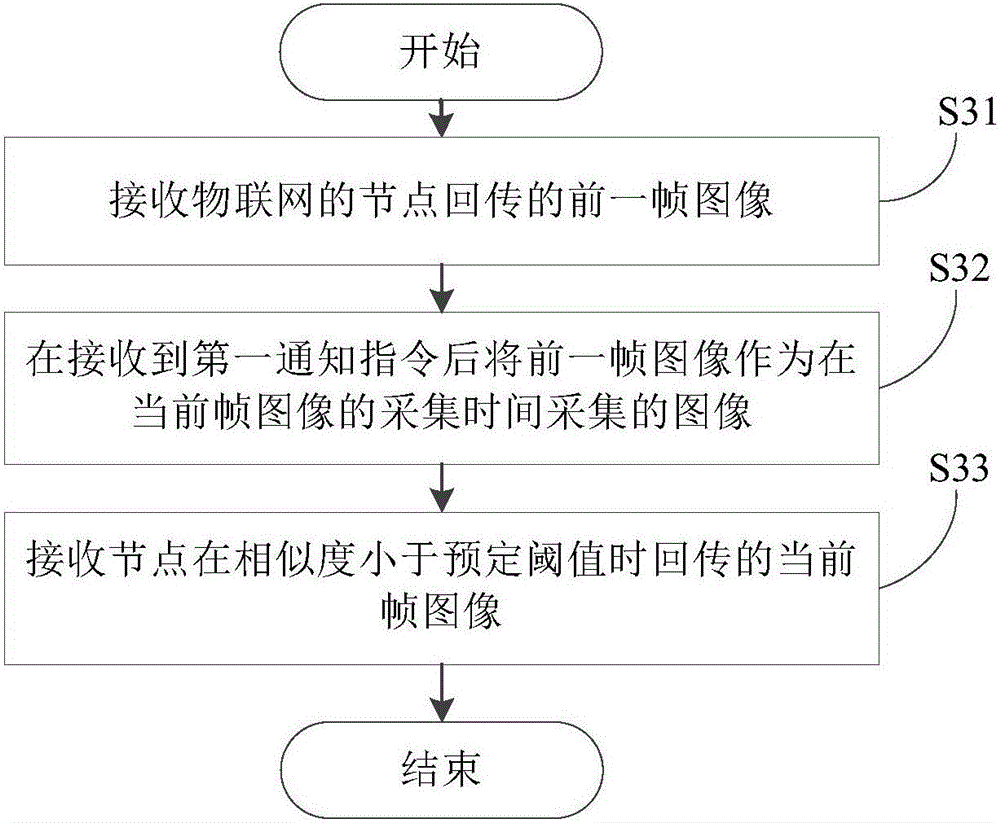
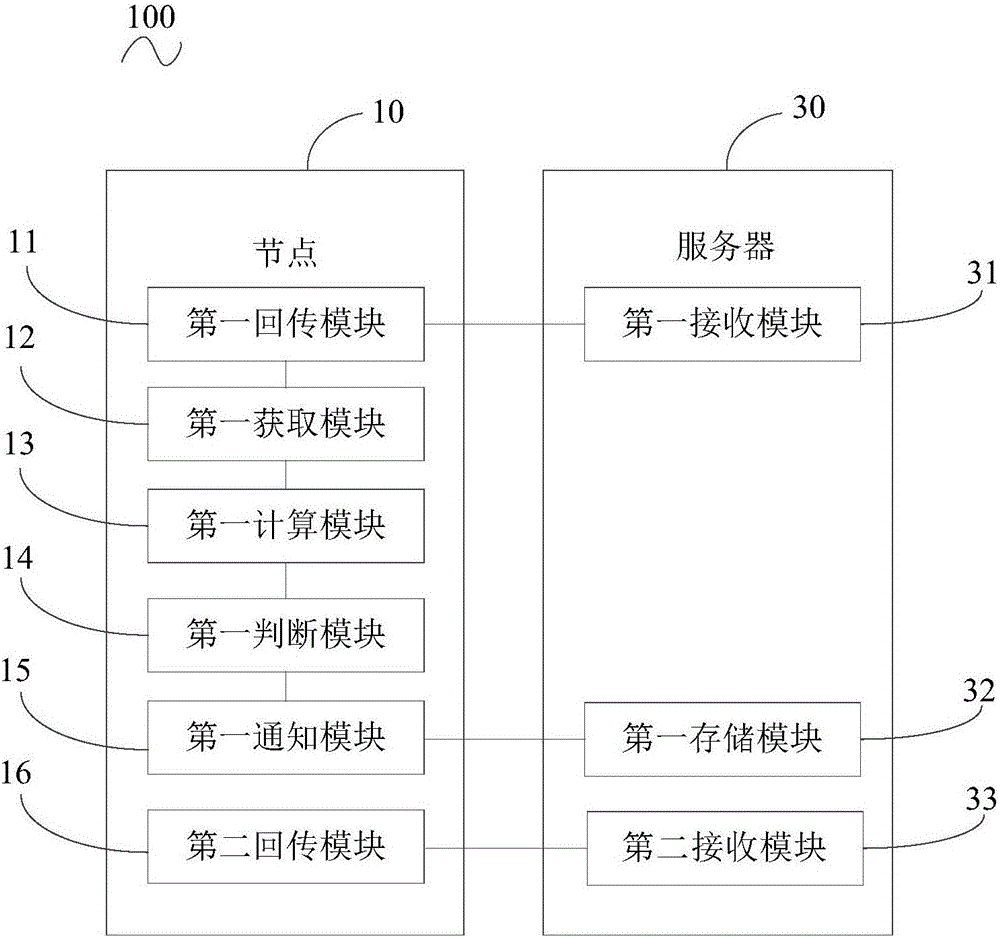
Image returning method, image storage method, internet of things node and server
ActiveCN106817410AReduce the amount of returned dataReduce the burden onCharacter and pattern recognitionTransmissionAcquisition timeThe Internet
The invention discloses an image returning method of internet of things nodes; the image returning method comprises the following steps: returning a previous frame image to an internet of things server; obtaining a present frame image and the acquisition time of the same; calculating the similarity between the present frame image and the previous frame image; determining whether the similarity is bigger than or equal to a preset threshold; if the similarity is >= the preset threshold, sending a first inform order to the server, thus allowing the server to use the previous frame image as the image collected at the acquisition time of the present frame image; if the similarity is < the preset threshold, returning the present frame image to the server. In addition, the invention also discloses an image storage method of the internet of things server, internet of things nodes, and the internet of things server. The image returning method, the image storage method, the internet of things node and server can greatly reduce the returning data amount, thus reducing system occupied resources, and reducing the system burden.
Owner:广州大气候农业科技有限公司
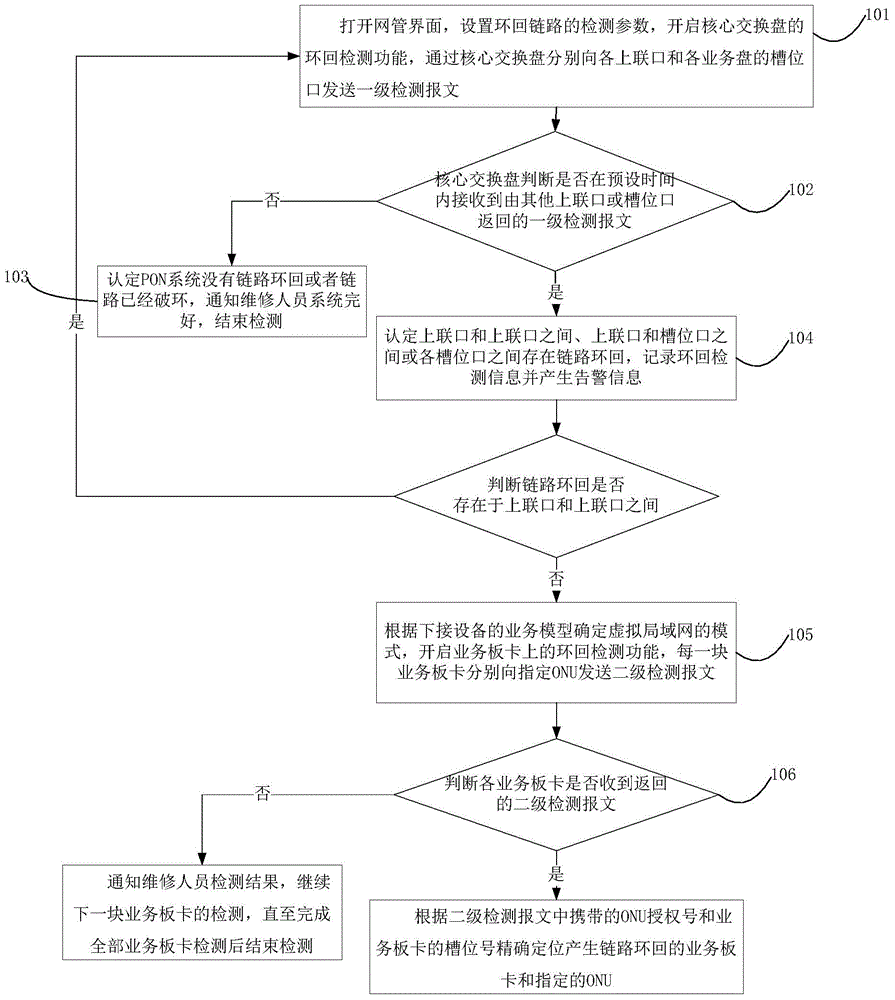
PON system link loopback detection method and device
ActiveCN104539348AOccupies less system resourcesEasy to implementMultiplex system selection arrangementsTransmission monitoring/testing/fault-measurement systemsTelecommunicationsAuthorization
The invention discloses a PON system link loopback detection method and device. A loopback detection function of a core switching disk is opened, and a primary detection message is sent to all upper connecting ports and slot position openings of all service disks respectively; detection is completed if the returned primary detection messages are not received; it is determined that loopback exists in a PON system if the returned primary detection messages are received; the detection is completed if loopback exists between the upper connecting ports; a loopback detection function of service board cards is opened if loopback exists between the upper connecting ports and the slot position openings or loopback exists between the slot position openings, each service board card respectively sends a secondary detection message to a specific ONU, and detection is completed if the service board cards do not receive the returned secondary detection messages; the service board cards and the specific ONU which produce the loopback are accurately positioned according to an ONU authorization number carried in the secondary detection messages and slot position numbers of the service board cards if the service board cards receive the returned secondary detection messages. By means of the PON system link loopback detection method and device, the implementation process is simple, detection results can be timely reported, and PON system link loopback detection efficiency is greatly improved.
Owner:FENGHUO COMM SCI & TECH CO LTD
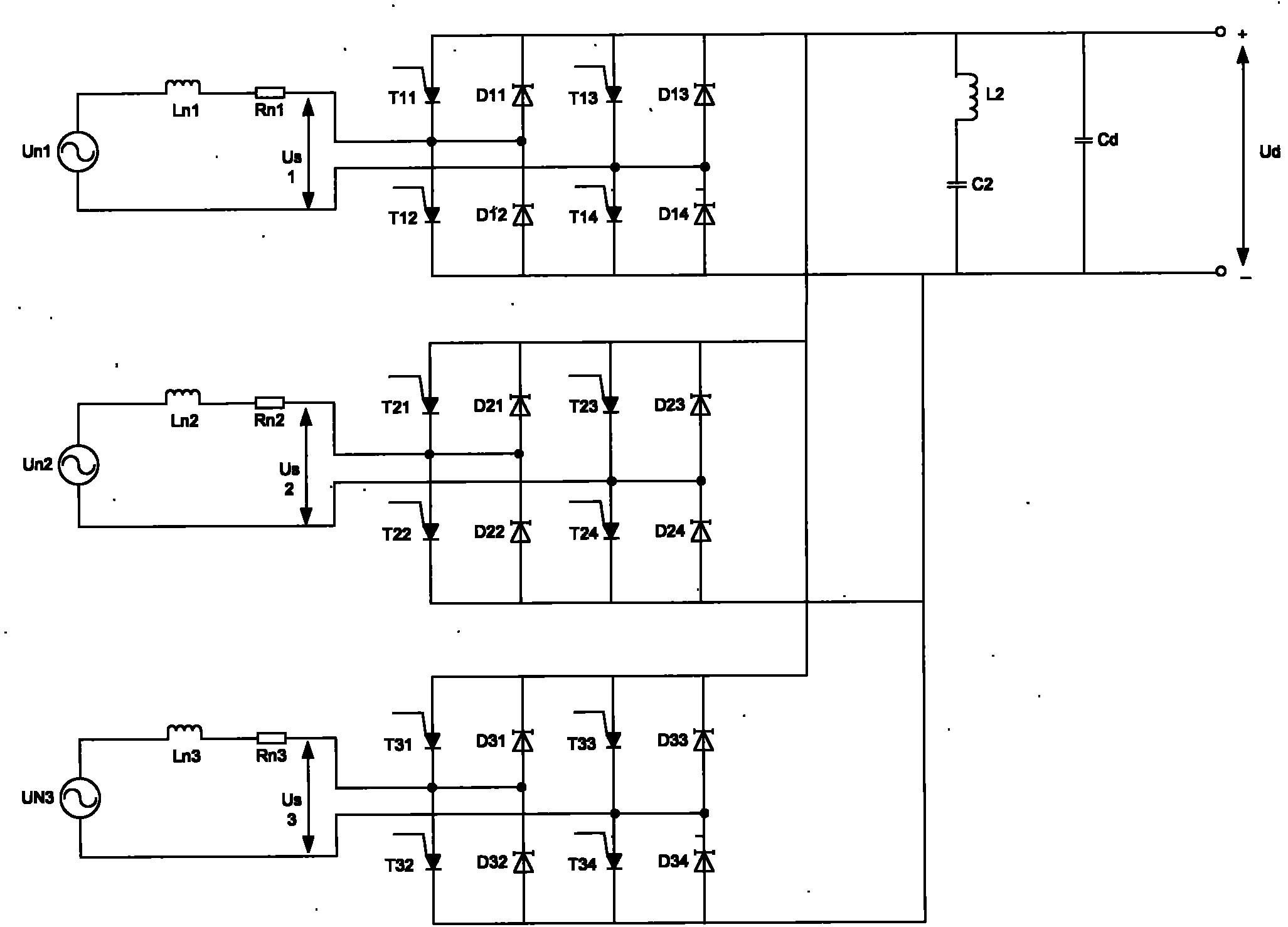
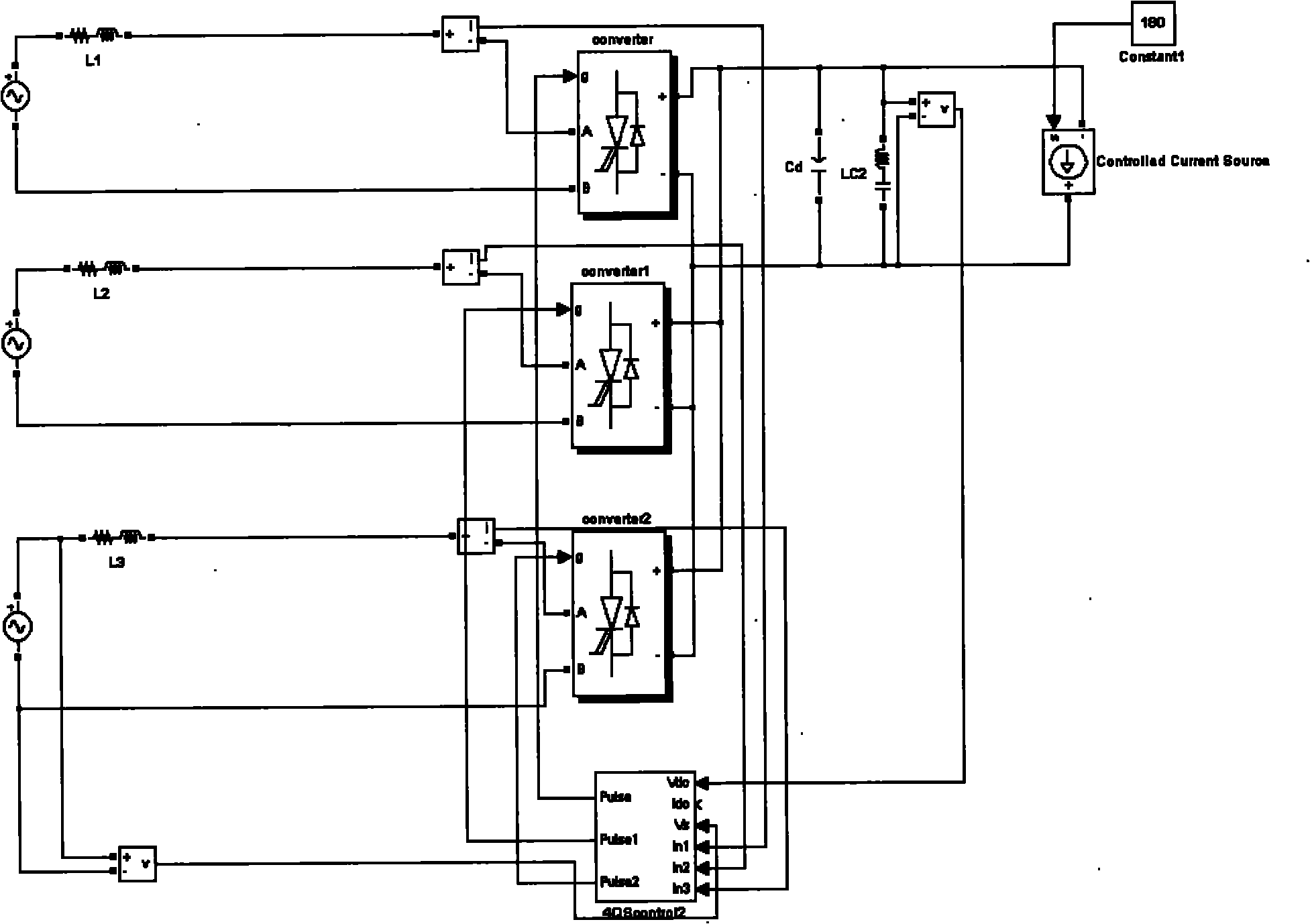
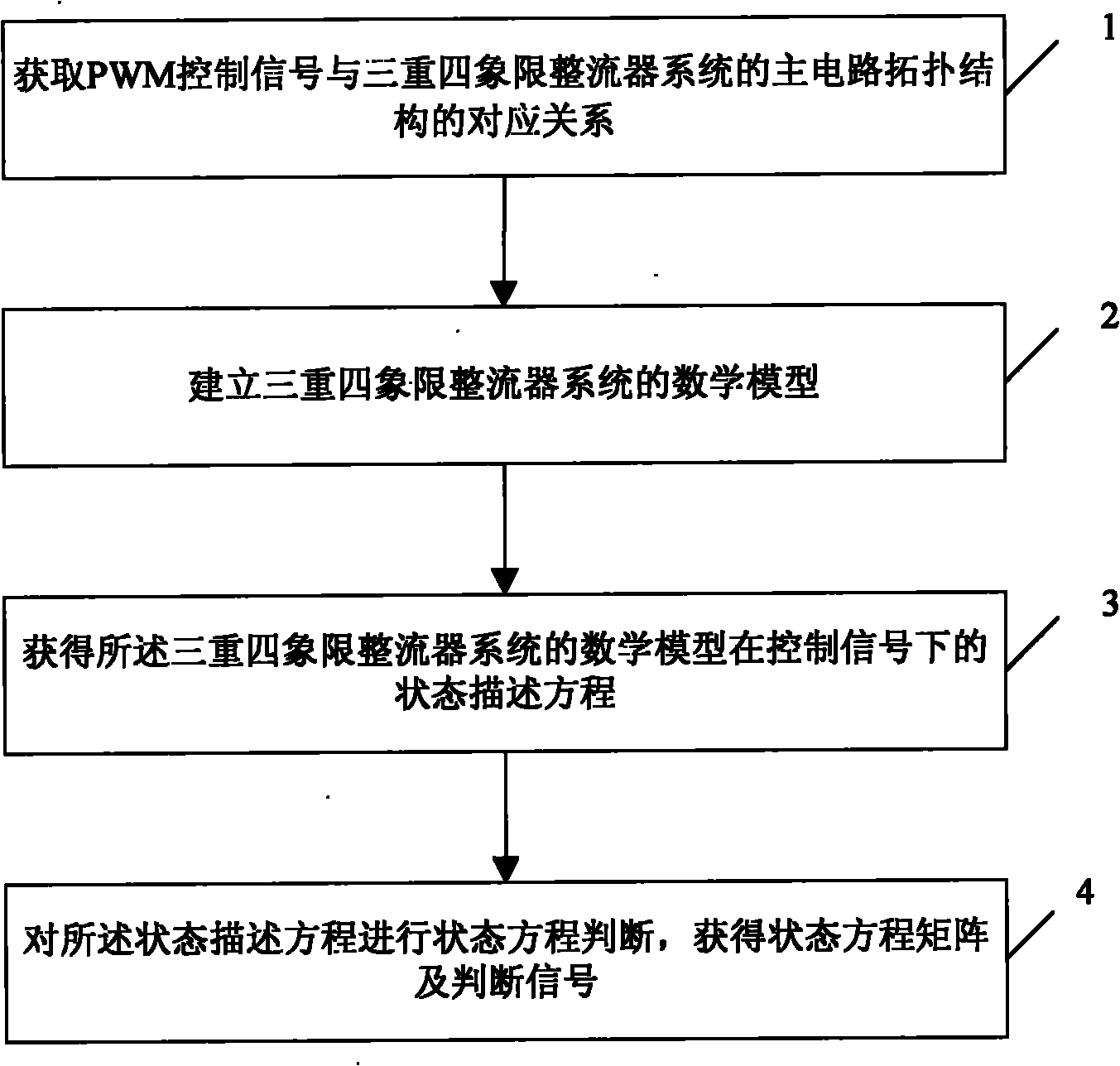
Triple four-quadrant rectifier simulation method
InactiveCN101895210AReduce complexityGuaranteed accuracyAc-dc conversion without reversalSoftware simulation/interpretation/emulationFour quadrantsReal-time simulation
The invention discloses a triple four-quadrant rectifier simulation method which comprises the following steps: acquiring the corresponding relation between each of PWM control signals and the main circuit topological structure of a triple four-quadrant rectifier system; establishing state mathematical description of the triple four-quadrant rectifier system; acquiring a state description equation of a mathematical model of the triple four-quadrant rectifier system under control signals; and carrying out state equation judgment on the state description equation to acquire a state equation matrix and the mathematical model of the triple four-quadrant rectifier. The real-time simulation method of the invention simplifies the problem of establishing a system state space model of the triple four-quadrant rectifier into the problem of selecting relevant parameters according to the conduction conditions of switching elements, thus the invention ensures the accuracy, reduces the complexity of mathematical modeling, simplifies the realization steps, occupies few system resources, has shorter sampling time in real-time simulation, and has very high real-time property.
Owner:ZHUZHOU CSR TIMES ELECTRIC CO LTD
Method and system for self-routing in synchronous digital cross-connection
InactiveUS20100195657A1Ease in realizingImprove reliabilityCode conversionData switching by path configurationCross connectionData stream
The present invention discloses a method for self-routing in synchronous digital cross-connection, comprising: self-routing transmitting means insert a CM data into a STM-N data stream according to a frame header indicator and a self-routing start address signal; self-routing receiving means extract the CM data from the STM-N data stream according to the frame header indicator and the self-routing start address signal, and write the CM data into a cross-connection control memory. The present invention also discloses a system for self-routing in synchronous digital cross-connection, comprising: self-routing transmitting means and self-routing receiving means, wherein, the self-routing transmitting means comprise a self-routing transmitting control unit, a first CRC checking unit and an inserting data generating unit, the self-routing receiving means comprise a self-routing extracting control unit, a second CRC checking unit and a cross-connection control memory. The present invention provides users with a self-routing scheme for synchronous digital cross-connection, which can be realized with ease, occupies less resource, has better reliability and is suitable for large capacity cross configuration.
Owner:ZTE CORP
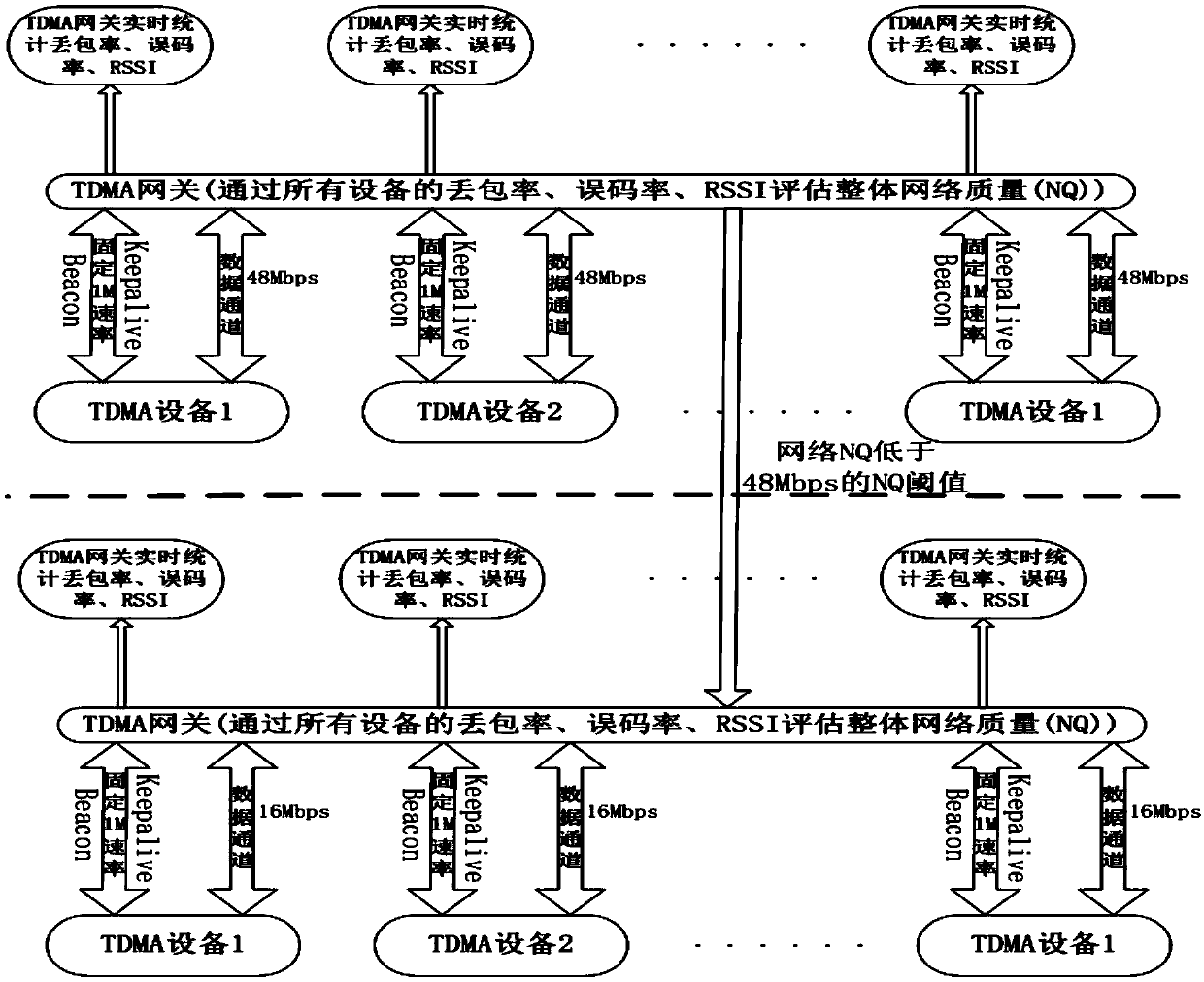
High-speed data transmission method for TDMA (Time Division Multiple Address) auto-negotiation rate
InactiveCN109639537AFlexible networkingEasy networkingData switching networksWireless communicationCommunication qualityNetworked Transport of RTCM via Internet Protocol
The invention provides a high-speed data transmission method for TDMA (Time Division Multiple Address) auto-negotiation rate. The method comprises the following steps: a TDMA gateway sends beacon messages to TDMA devices at a predetermined time interval; after receiving the beacon message, the TDMA devices immediately send keepalive messages to the TDMA gateway; the TDMA gateway checks the correctness of each frame of the keepalive messages in a unit time, and counts the bit error rate of the communication data between the TDMA gateway and the TDMA devices in real time; the TDMA gateway countsthe number of the keepalive messages sent by each TDMA device in the TDMA gateway per unit time, and calculates the packet loss rate of the network at this time; when receiving the keepalive messagesof the TDMA devices, the TDMA gateway reads the signal strength indicator RSSI of each keepalive message; the current communication quality of the network is evaluated; and the communication rate isadjusted. The method can not only improve the ability of the network to transmit big data, but also ensure the stability and reliability of the network.
Owner:SHENZHEN GALAXYWIND NETWORK SYST
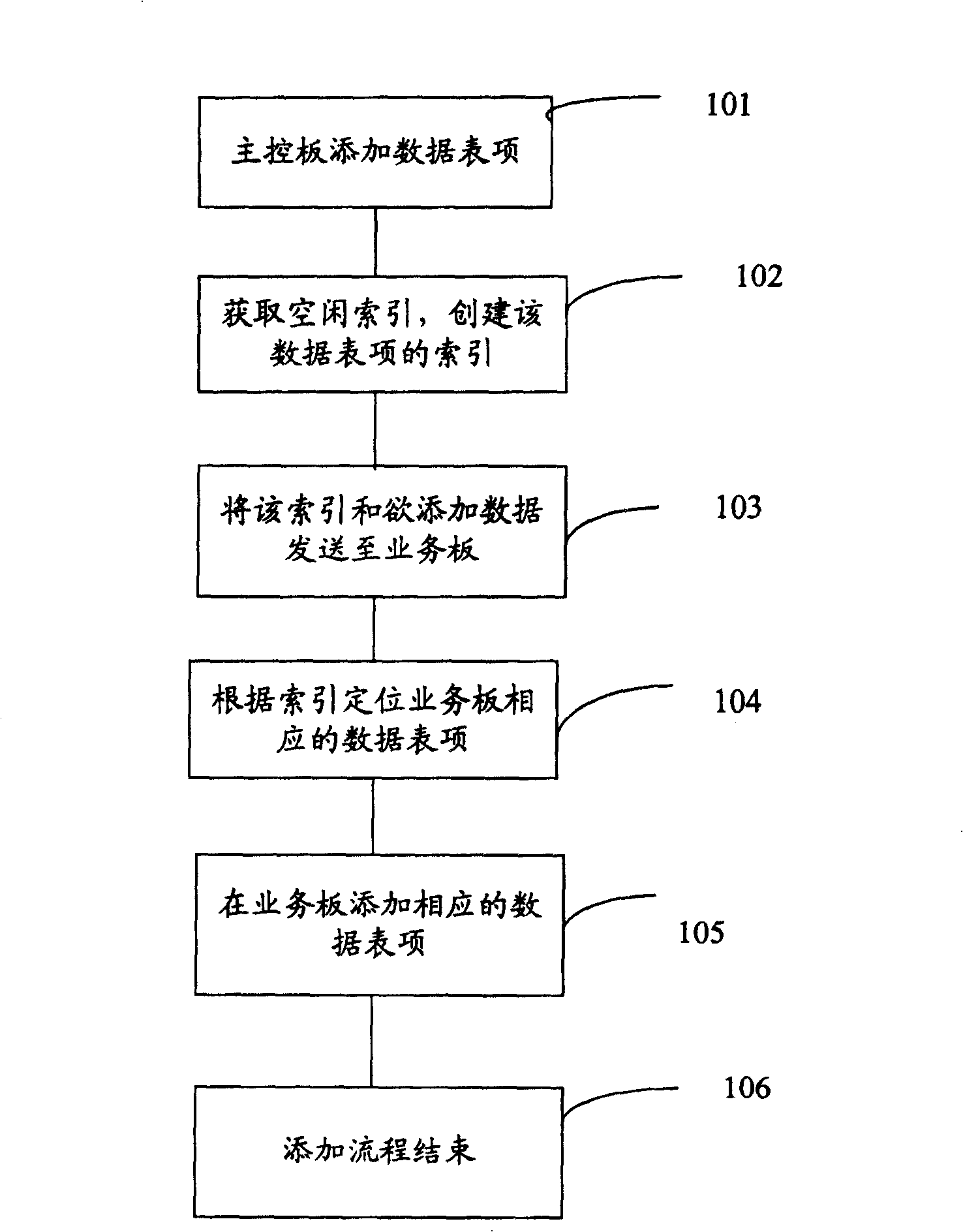
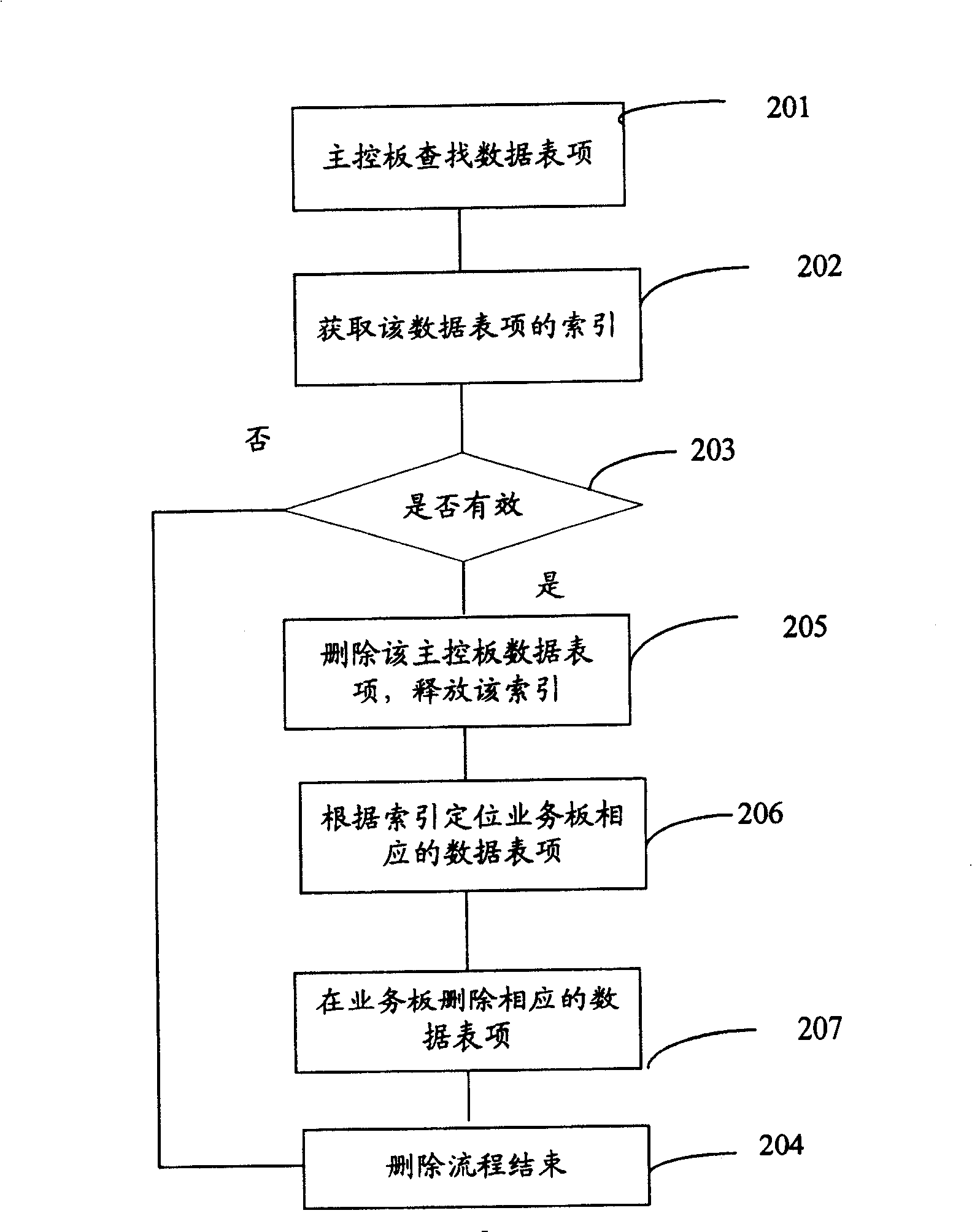
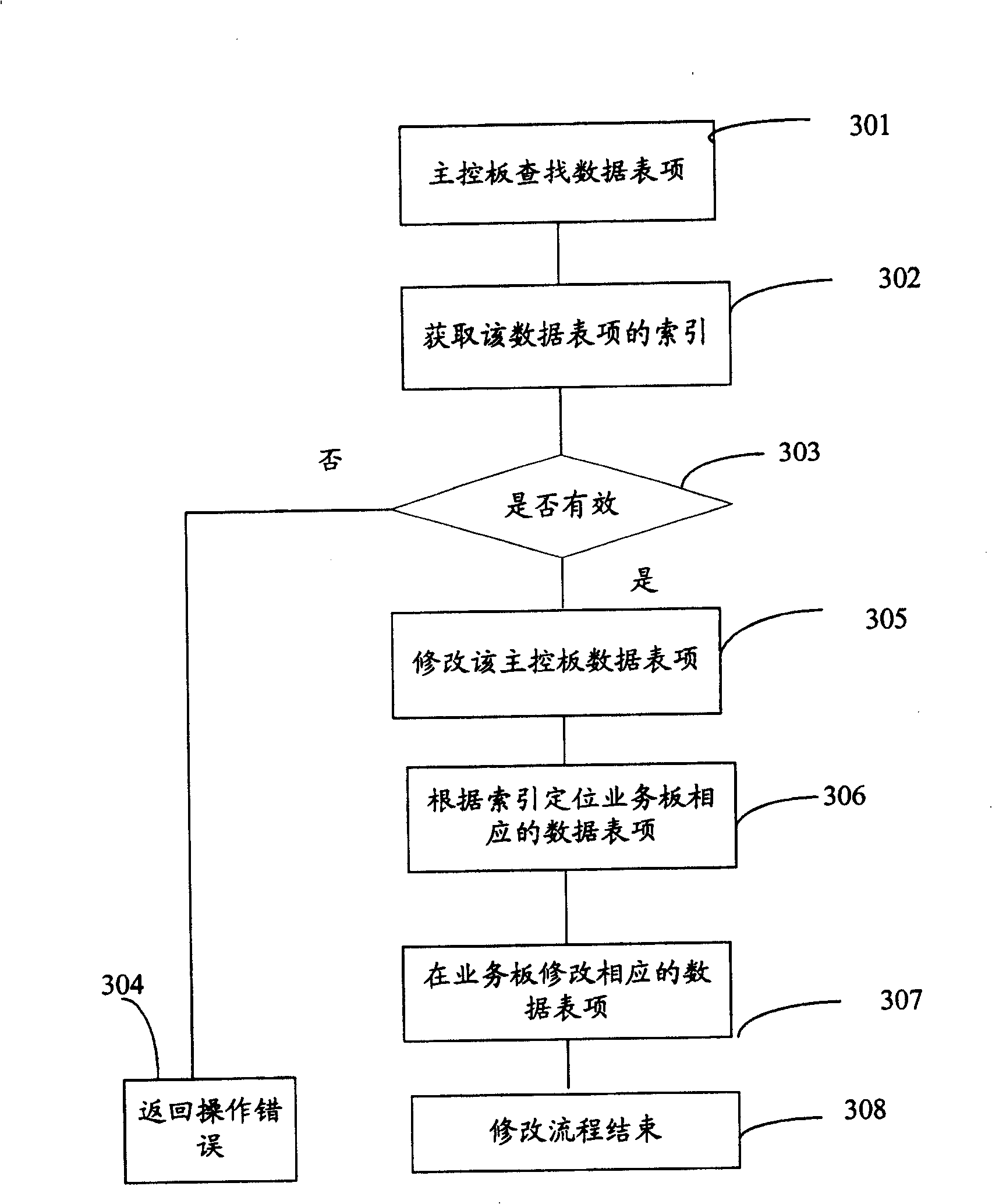
Method of data query and method of inter-board data synchronization in distributed system
InactiveCN100442282CEasy to implementOccupies less system resourcesTransmissionSpecial data processing applicationsData synchronizationBoard communication
The invention provides a method for data query in a distributed system. Firstly, the index of the data entry of the main control board and the corresponding data entry of each service board is established; the data entry of the main control board is searched, and the searched data on the main control board The index of the data table item is sent to the corresponding service board through the inter-board communication between the main control board and the service board, so that the service board that receives the index locates the corresponding data table item in the service board according to the index. In addition, the present invention also provides a method for synchronizing data between boards in a distributed system. First, an index is added to a certain data entry of the main control board, and the index is sent to each service board with a corresponding data entry; When the data entry of the main control board is updated, the main control board sends the index of the updated data entry to the corresponding service board, and the service board that receives the index searches the corresponding data entry in the service board according to the index, and sends the Update the corresponding data table item in . The invention is easy to implement and occupies less system resources.
Owner:NEW H3C TECH CO LTD
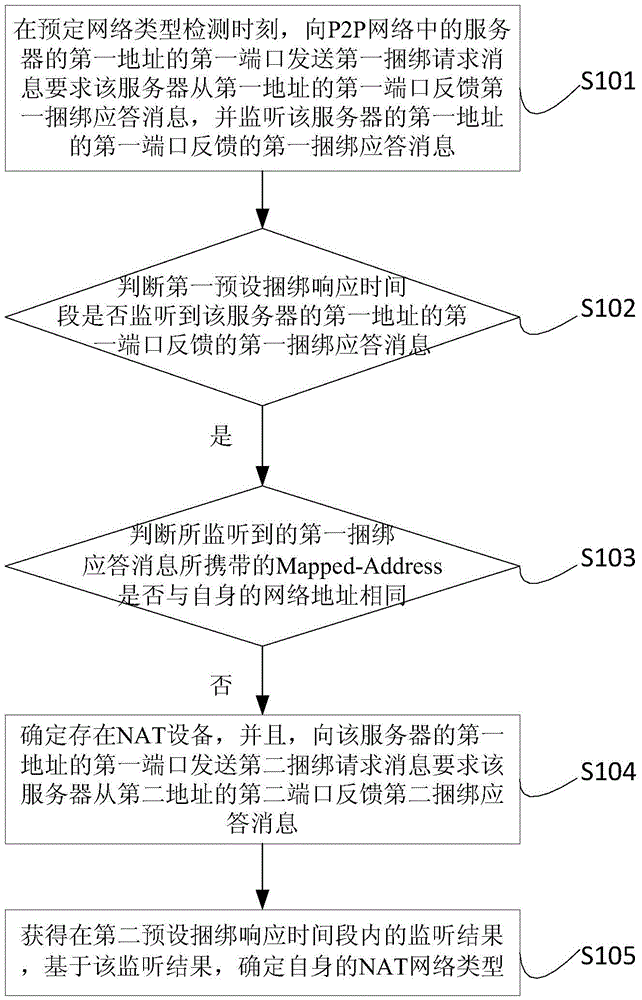
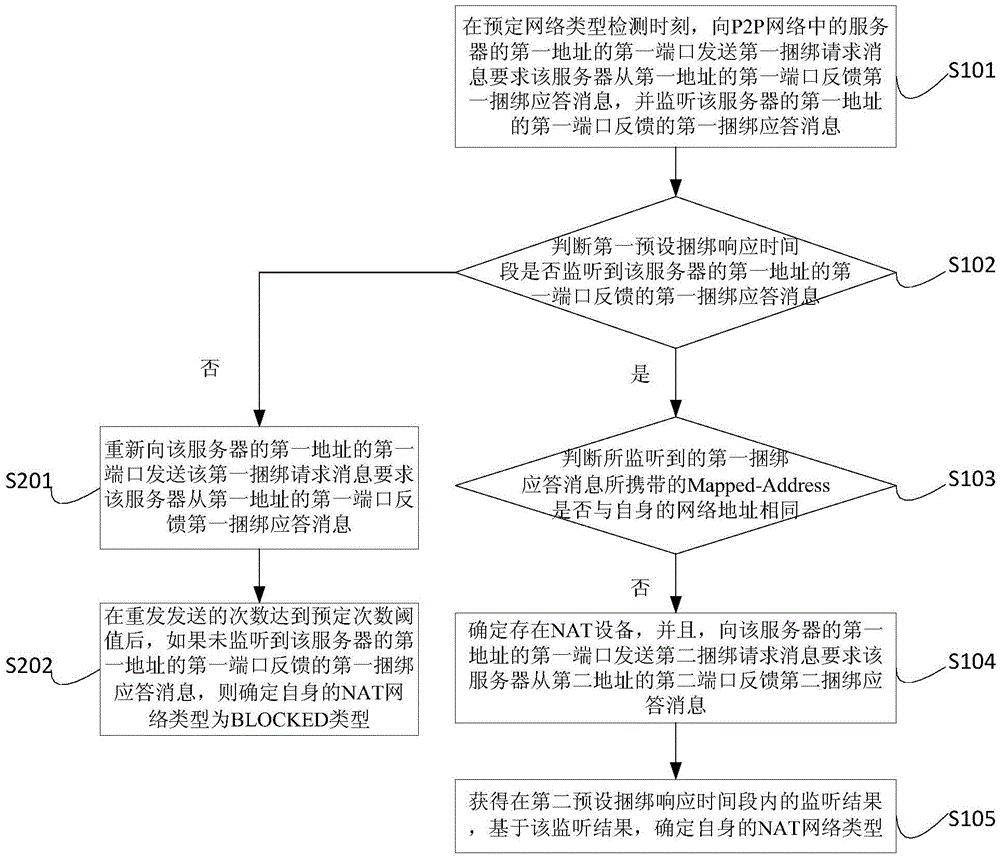
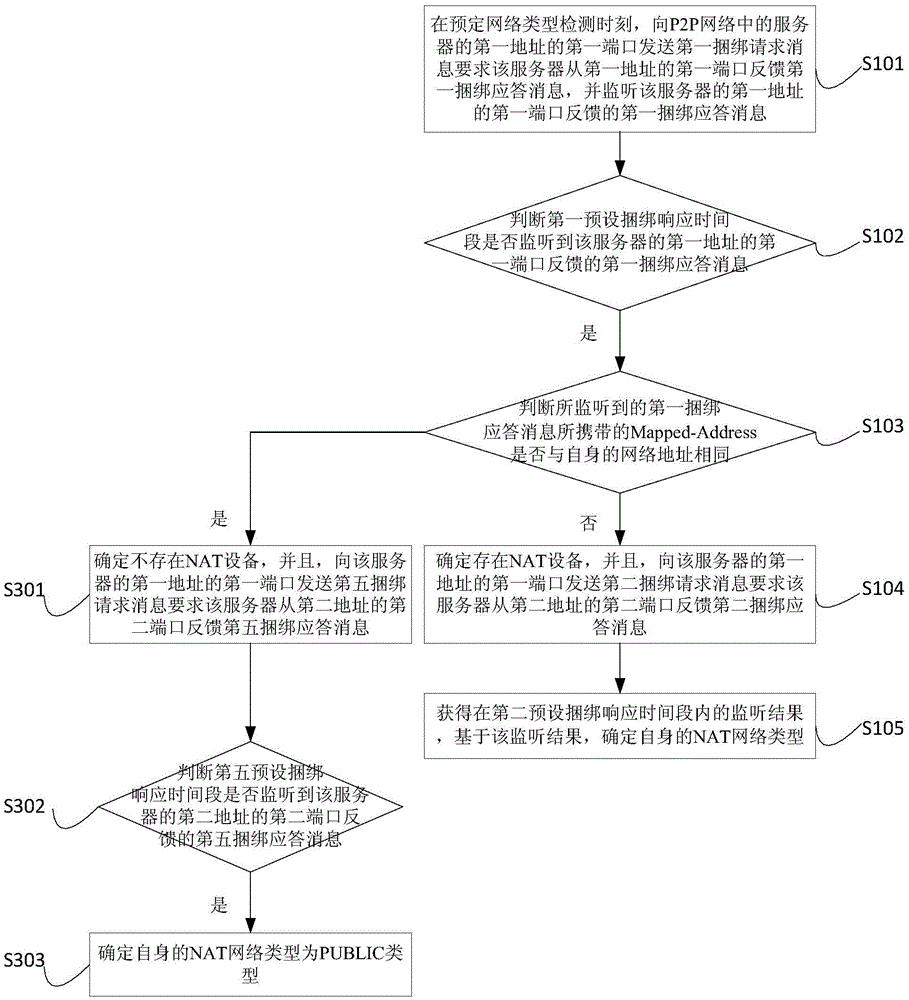
NAT network type detection method and device
The embodiment of the invention provides a NAT network type detection method and device. The first binding request information is sent to a server in a P2P network at the moment of preset network type detection, and the first binding response information fed back by the server is monitored; if the Mapped-Address carried by the monitored first binding response information is different from the network address itself, it is determined that there is provided a NAT device; the second binding request information is sent to the server to obtain monitoring results in a second preset binding response time period; and the NAT network type itself is determined based on the monitoring results. Compared with the prior art, the NAT network type detection method and device perform network type detection through a custom STUN protocol, the binding request information used by the protocol only includes information codes required by business, the used binding response information only includes a mapping address and a displacement address required by the business, and the STUN protocol is simplified through removing bytes being irrespective of the business to compress the information, so that the less system resource is occupied, and the network cost is saved.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
System and method for detecting and defending computer worm
ActiveCN100374972CEffective defenseOccupies less system resourcesDigital data processing detailsComputer wormOperational system
This invention relates to test and protective computer ill-purpose program system, which comprises the following parts: computer operation system monitor device to collect aim programs operation information; aim program operation record device to store aim programs operation records and to record repaired files, register form; known action characteristics memory device to store known, processed operation information and to store each operation relative danger degree weigh; aim program action identification analysis device to compare the aim program with known action; ill-purpose action removal device to remove the ill-purpose program.
Owner:ZHUHAI KINGSOFT SOFTWARE CO LTD
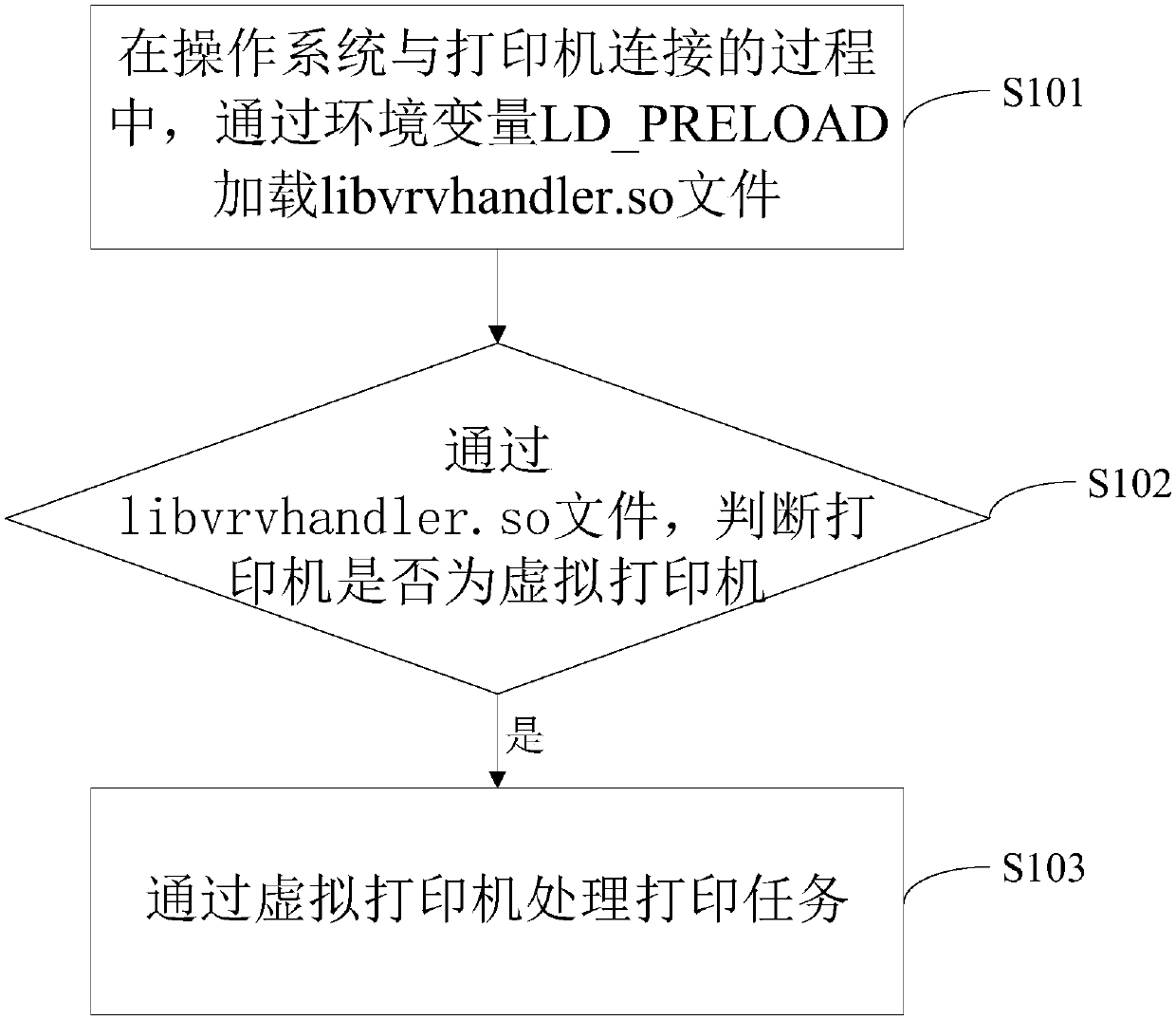
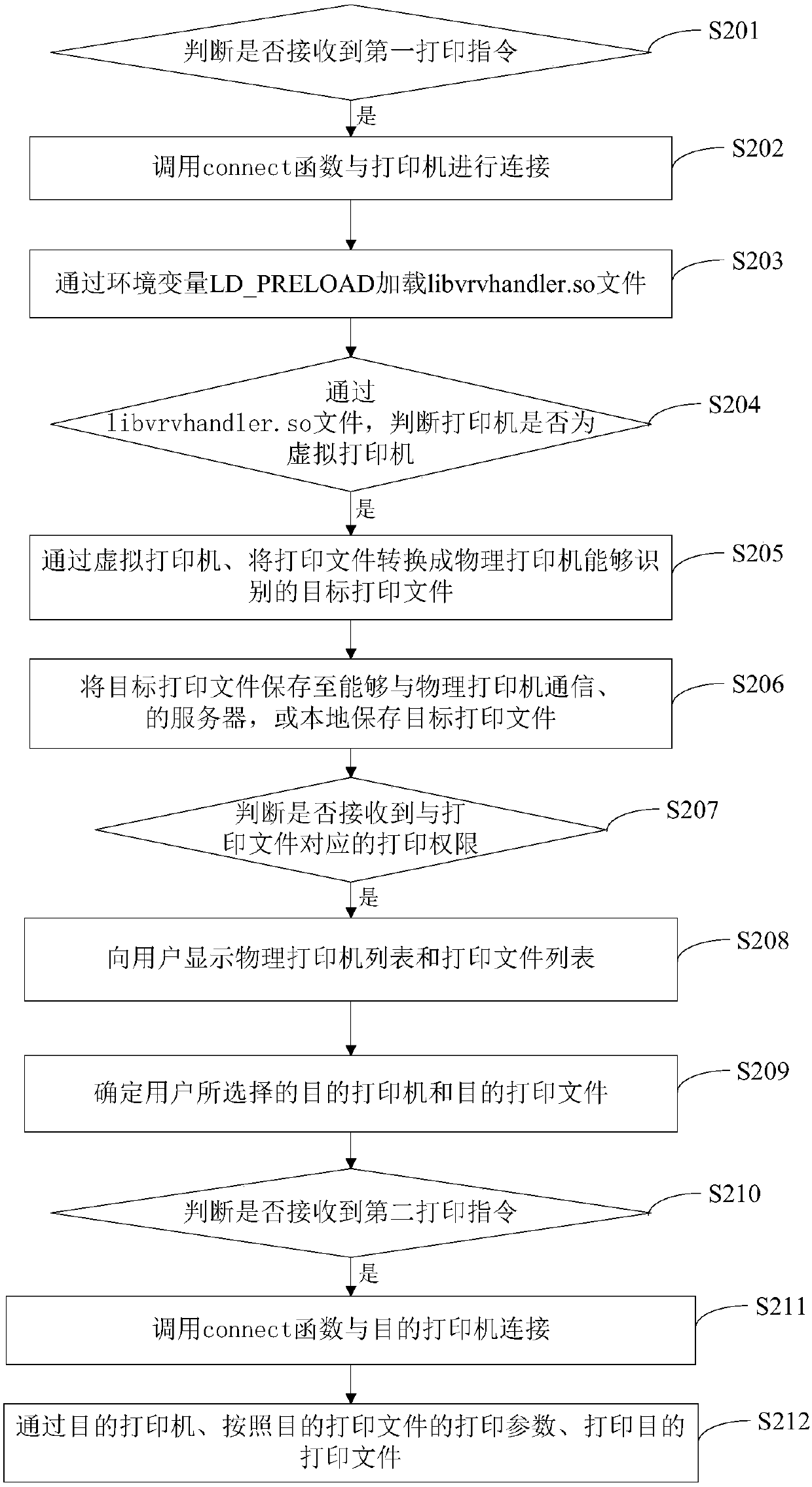
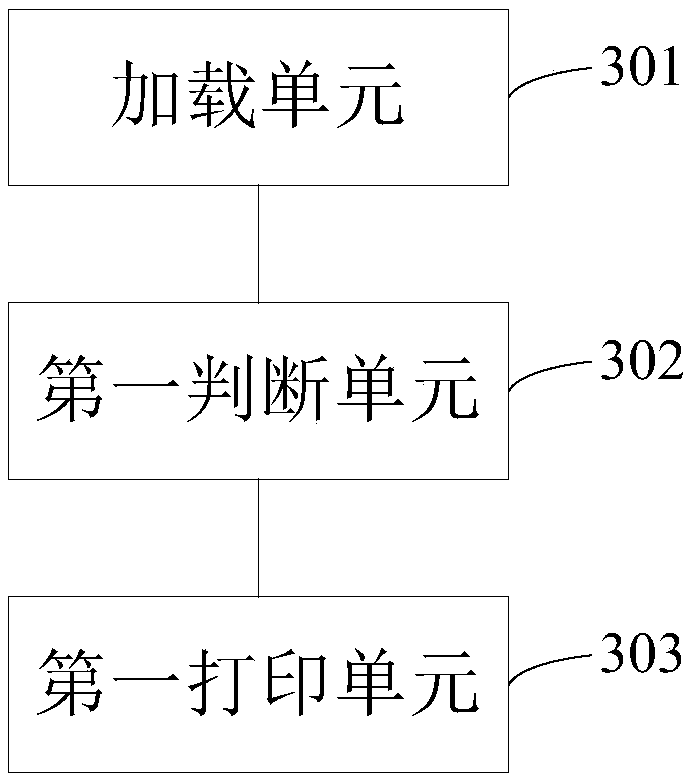
Printing method and device
ActiveCN107562391AOccupies less system resourcesIncrease profitDigital output to print unitsVirtual printerEnvironment variable
The invention discloses a printing method and device. The method comprises the following steps that: in a process that an operating system is connected with a printer, through an environment variableLD-PRELOAD, loading a libvrvhandler.so file, wherein the printer comprises a virtual printer and / or physical printer; through the libvrvhandler.so file, judging whether the printer is the virtual printer or not; and if the printer is the virtual printer, processing a printing task through the virtual printer. In the method, only in the process that the operating system is connected with the printer, the libvrvhandler.so file bound with the environment variable LD-PRELOAD in advance is loaded. Compared with the prior art that a process is under an operation state all the time, few system resources are occupied, and the use ratio of system resources is improved.
Owner:BEIJING VRV SOFTWARE CO LTD
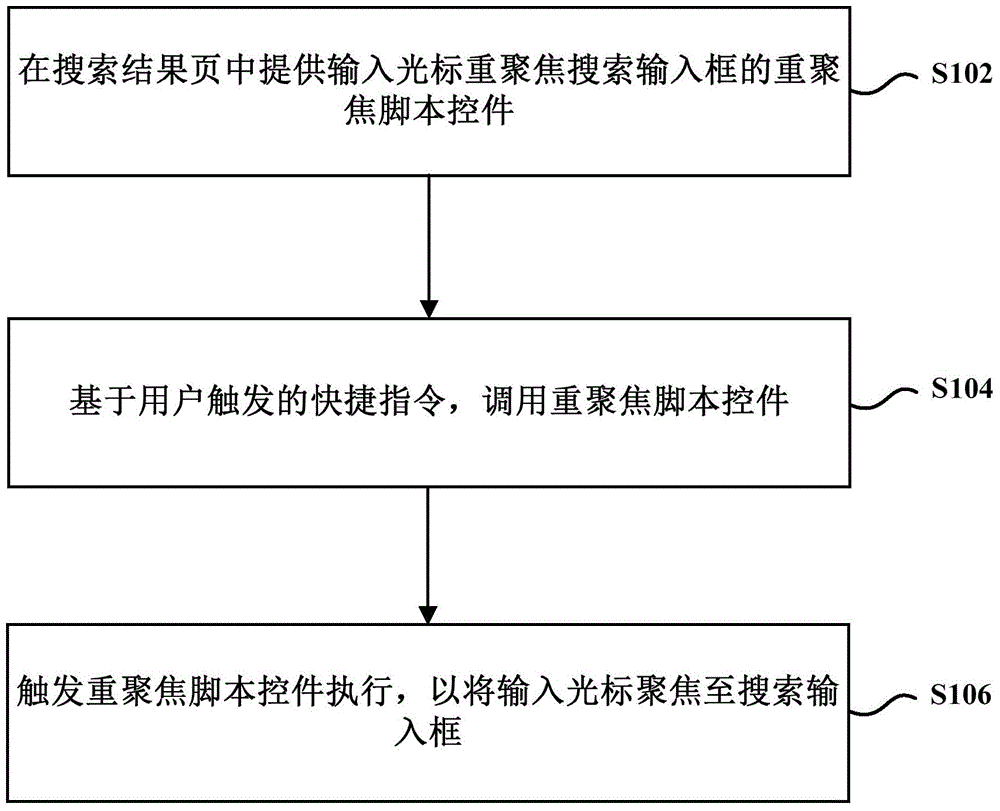
Search input box re-focusing method and device and search client terminal
ActiveCN104462498AEasy to operateSmall compatibilityWeb data indexingSpecial data processing applicationsClient-sideHuman–computer interaction
The invention provides a search input box re-focusing method and device and a search client terminal. The method includes the steps of providing a re-focusing script control for an input cursor to be re-focused on a search input box; based on a rapid command triggered by a user, calling the re-focusing script control; triggering the re-focusing script control to be executed so as to enable the input cursor to be re-focused on the search input box. By means of the technical scheme, the aim that a search engine rapidly and efficiently interacts with the user can be achieved, the operation of the user can be simplified, and the user experiences can be improved.
Owner:BEIJING QIHOO TECH CO LTD
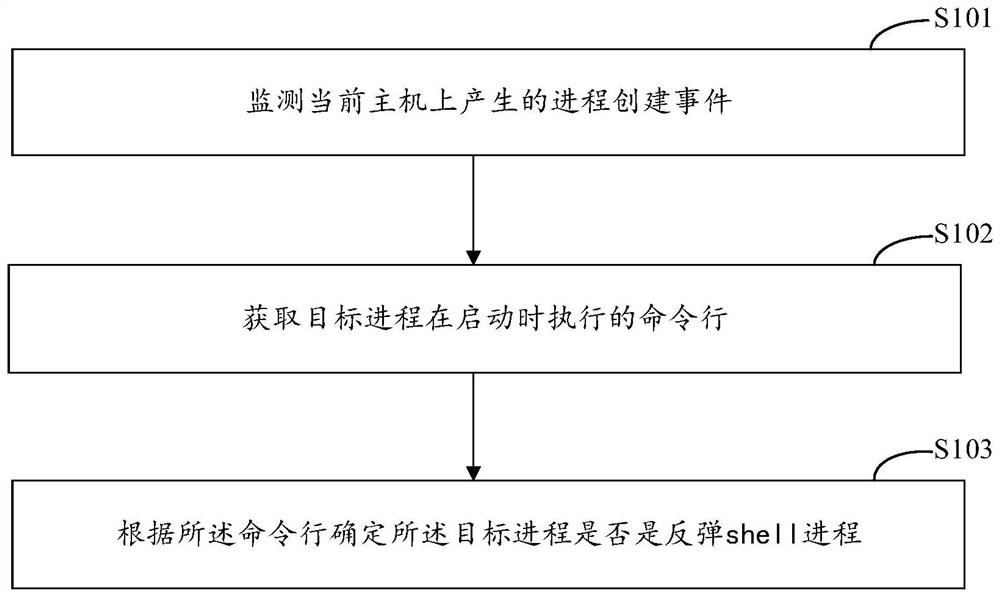
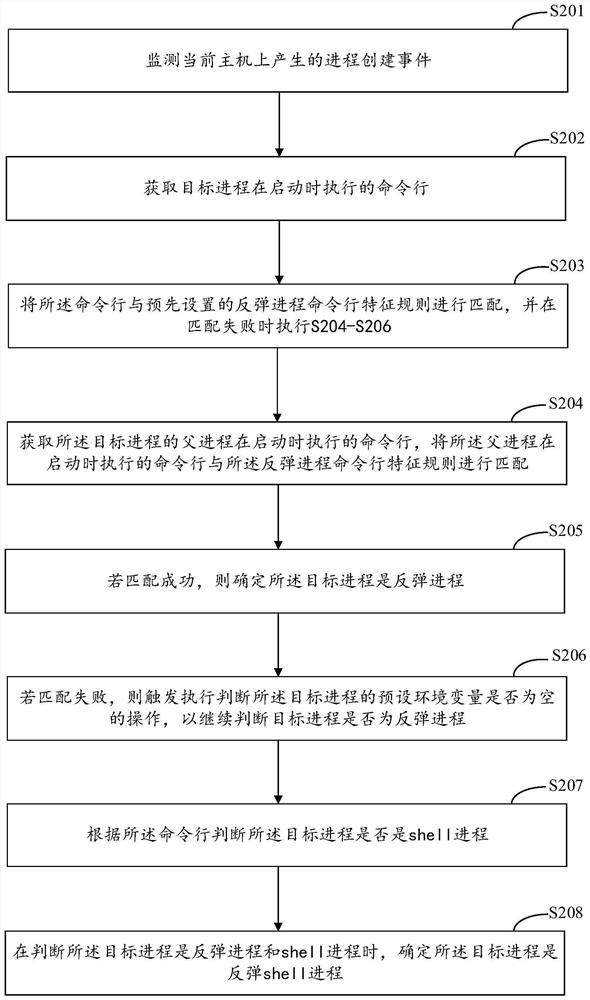
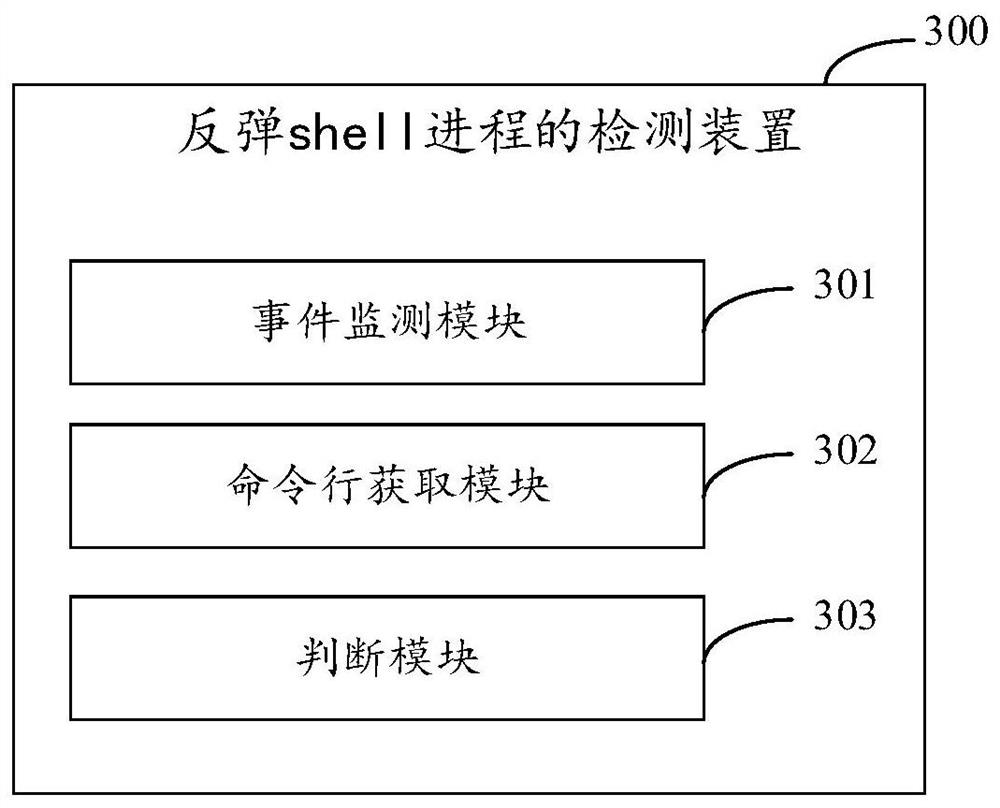
Detection method and device for rebound shell process, equipment and medium
PendingCN113449298AImprove accuracyImprove efficiencyPlatform integrity maintainanceTotal factory controlProcess engineeringSystems engineering
The invention discloses a detection method and device for a rebound shell process, equipment and a medium, and relates to the technical field of information security. According to the specific implementation scheme, the method includes monitoring a process creation event generated on a current host; acquiring a command line executed when the target process is started, wherein the target process is a process corresponding to a monitored process creation event; and determining whether the target process is a rebound shell process or not according to the command line. In the embodiment of the invention, as long as the process creation event is generated on the host, whether the process is the rebound shell process or not is determined according to the command line executed when the process is started, the detection of various rebound shell processes can be covered, and the command line can be captured no matter whether the command line is successfully executed or failed, so that the detection of the process with the rebound failure can be realized.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com