System and method for detecting and defending computer worm
A malicious program and computer technology, applied in the field of systems that can detect and defend unknown malicious programs, and can solve problems such as differences, large system resources, and inability to do so.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
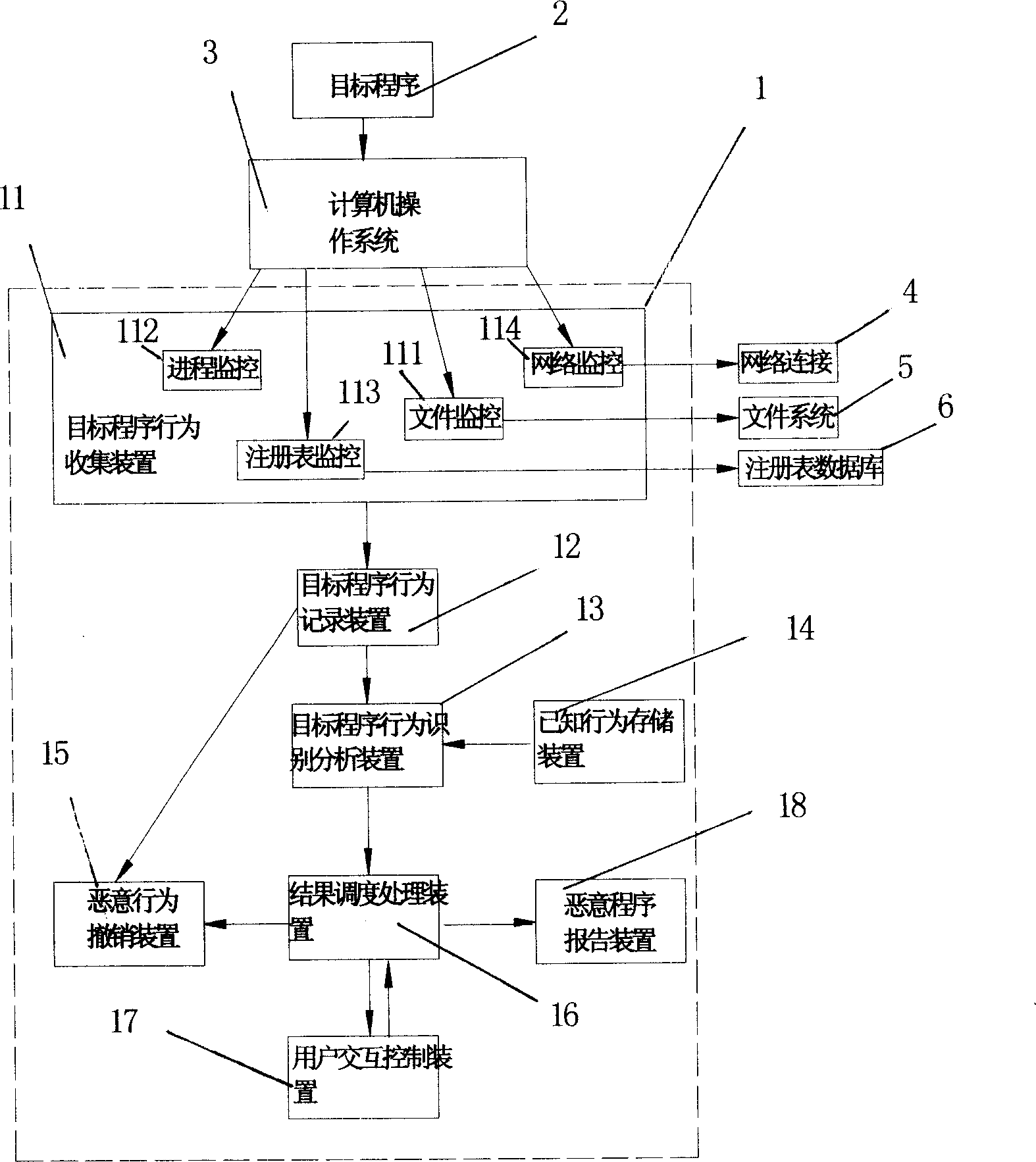
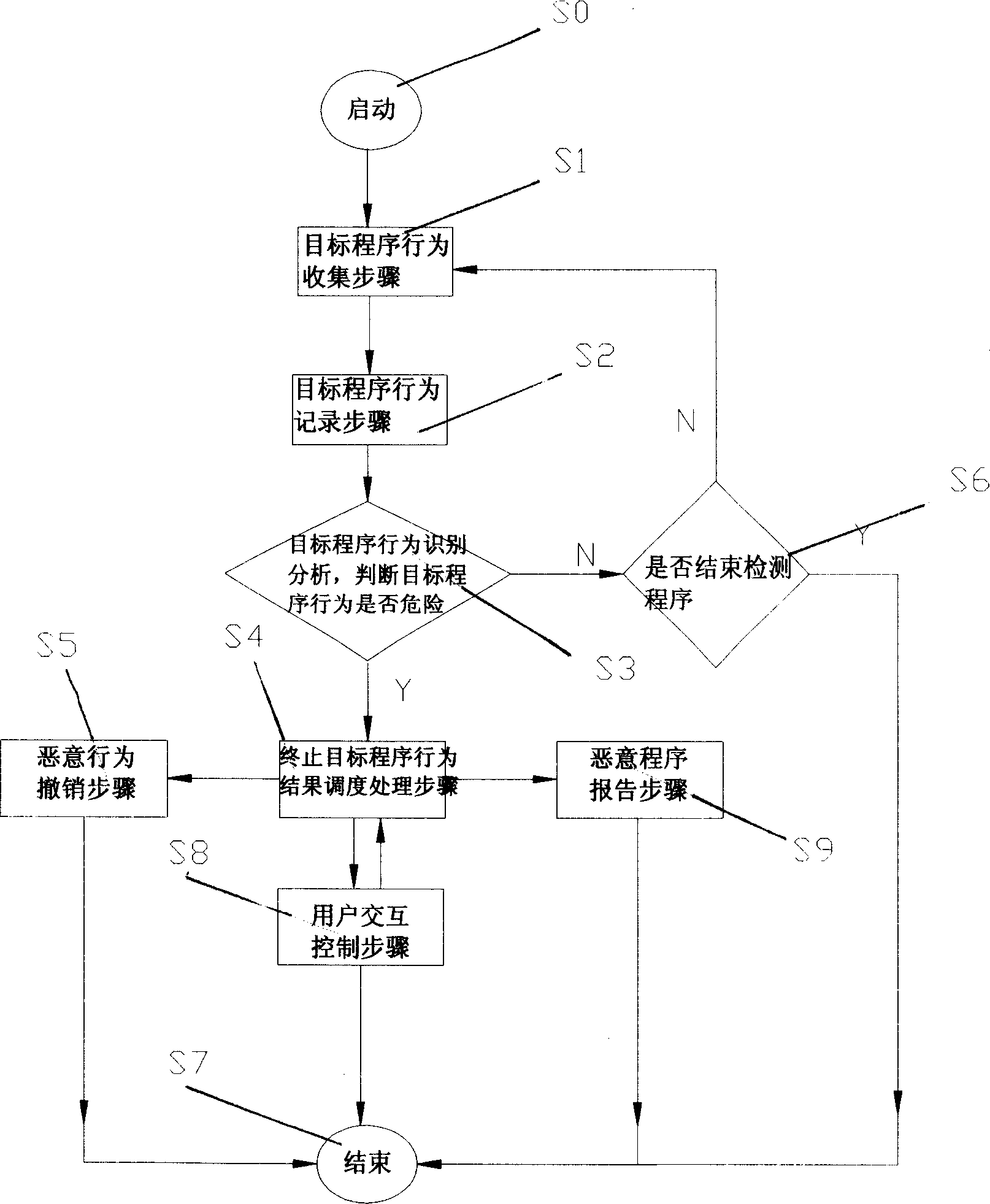
[0030] Such as figure 1 As shown, in an ordinary computer system, a system 1, a target program 2, a computer operating system 3, a network connection module 4, a file system 5, and a registry for detecting and defending computer malicious programs that can be executed by the computer are installed Database 6; also have common CPU, internal storage device and external storage device (not shown in the figure) in this computer. The target program 2 may exist in files in internal and external storage devices of the computer, as well as files or data packages downloaded and transmitted from the network. The target program 2 can run in the computer operating system 3, and can call related functions to operate the network connection module, file system, registry database and other software and hardware. The system 1 for detecting and defending against malicious computer programs can effectively monitor the process of calling related functions by the target program.
[0031] The sys...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com