Patents
Literature
58 results about "Malicious damage" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
M2M transmission control method, device and system
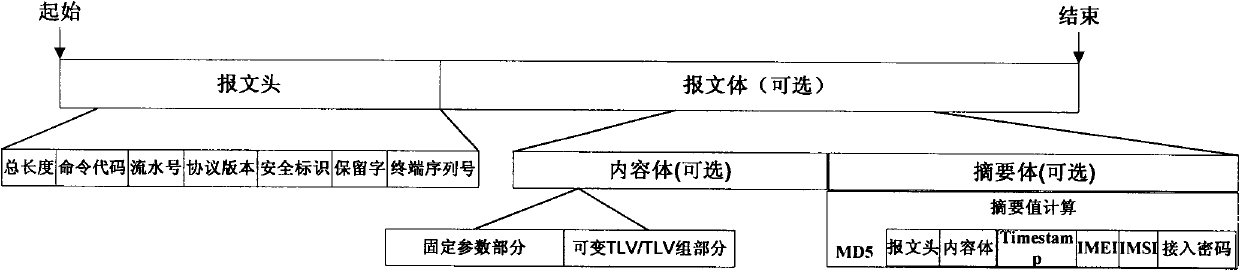
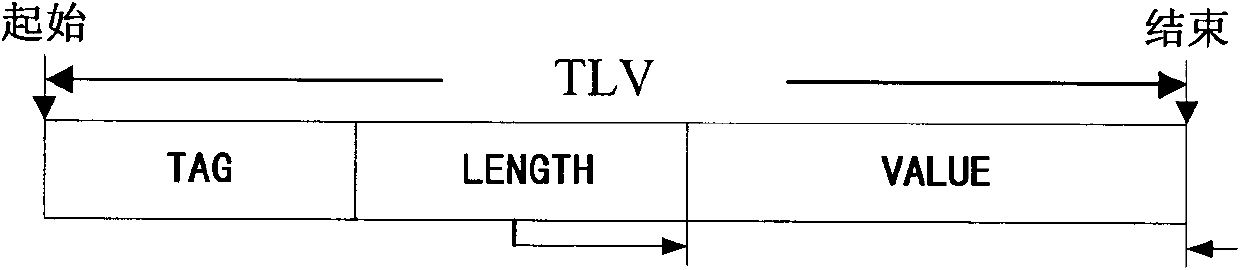
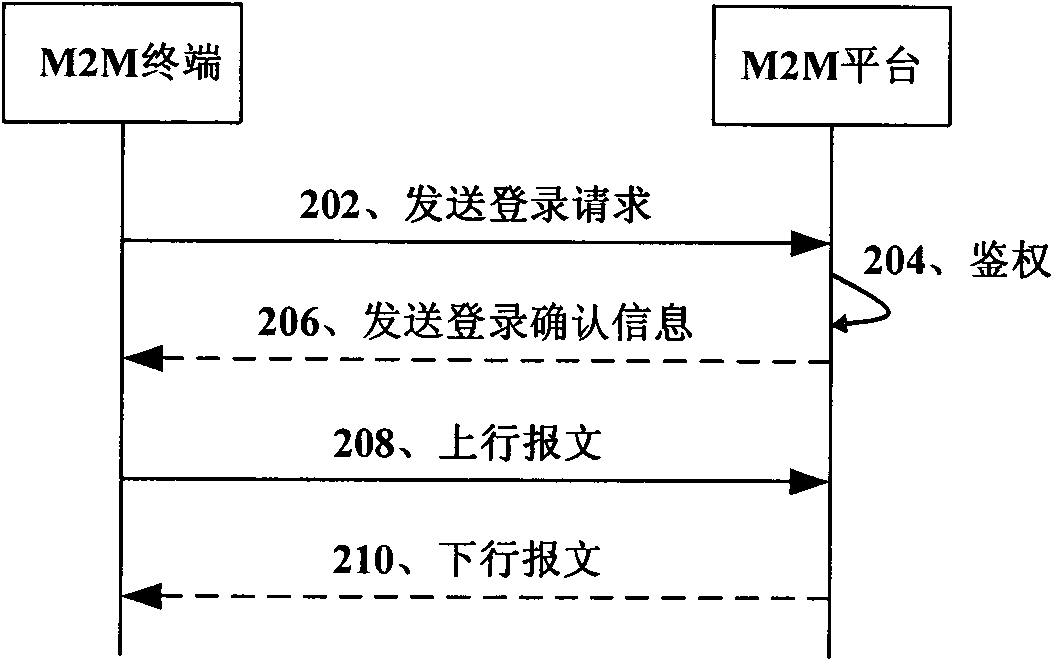
The invention discloses a model-to-model (M2M) transmission control method, an M2M transmission control device and an M2M transmission control system. The M2M transmission control method comprises that: B1, an M2M terminal transmits a login request carrying an access password, an international mobile equipment identity (IMEI) code, an international mobile subscriber identity (IMSI) code and a terminal serial number to an M2M platform; B2, the M2M platform receives the login request and authenticates the M2M terminal according to the correspondence among the IMEI code, the IMSI code and the terminal serial number; and B3, after the authentication is accomplished successfully, the M2M platform transmits login confirmation information to the M2M terminal. When the M2M transmission control method, the M2M transmission control device and the M2M transmission control system, which are disclosed by the invention, are used, through the authentication of the IMEI code, the IMSI code and the terminal serial number, namely the bonded authentication of a machine terminal, a communication module and or an SIM card, the access safety of the M2M terminal is improved, so that the illegal use of the machine terminal or SIM card after the M2M terminal is lost and malicious damage caused by other people to background systems for production, monitoring and the like can be avoided.
Owner:CHINA MOBILE COMM GRP CO LTD
Method for detecting artificial malicious damage to camera
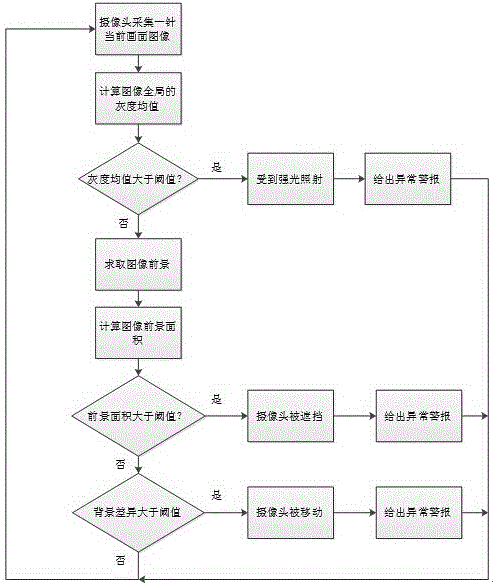
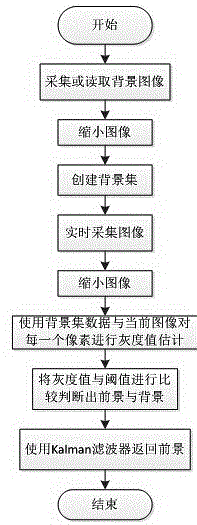
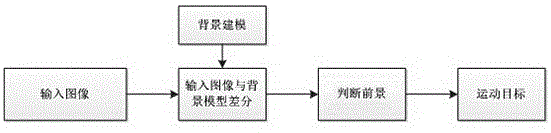
The invention discloses a method for detecting the artificial malicious damage to a camera. The method comprises the following steps that 1) a frame of current image is acquired; 2) the color image is converted into a gray scale image; 3) filtering processing is performed on the image; 4) the global gray scale mean of the image is calculated and compared with a preset threshold; 5) the foreground and the background of the image are estimated; 6) the size of foreground regional area of the image is compared with the preset threshold; 7) the background is compared with the background of the normal conditions; and 8) after abnormal behaviors appear, prompting information is marked, alarming is performed and the current abnormal image is saved. According to the method, the abnormal situation of the artificial malicious damage to the camera can be timely detected and alarmed, and the frame of the abnormal situation can be saved with no requirement for artificial protection for the camera. The method is low in cost and easy to operate so that manpower is greatly saved, the method is rapid and convenient, time deterioration can be effectively prevented, and thus the method has important meaning for safety and protection.
Owner:NANJING INST OF TECH
Method and device for storing traffic information based on coalition chain
ActiveCN108712431AFix serious damageSolve factors such as man-made malicious damageTransmissionDriver/operatorTraffic accident
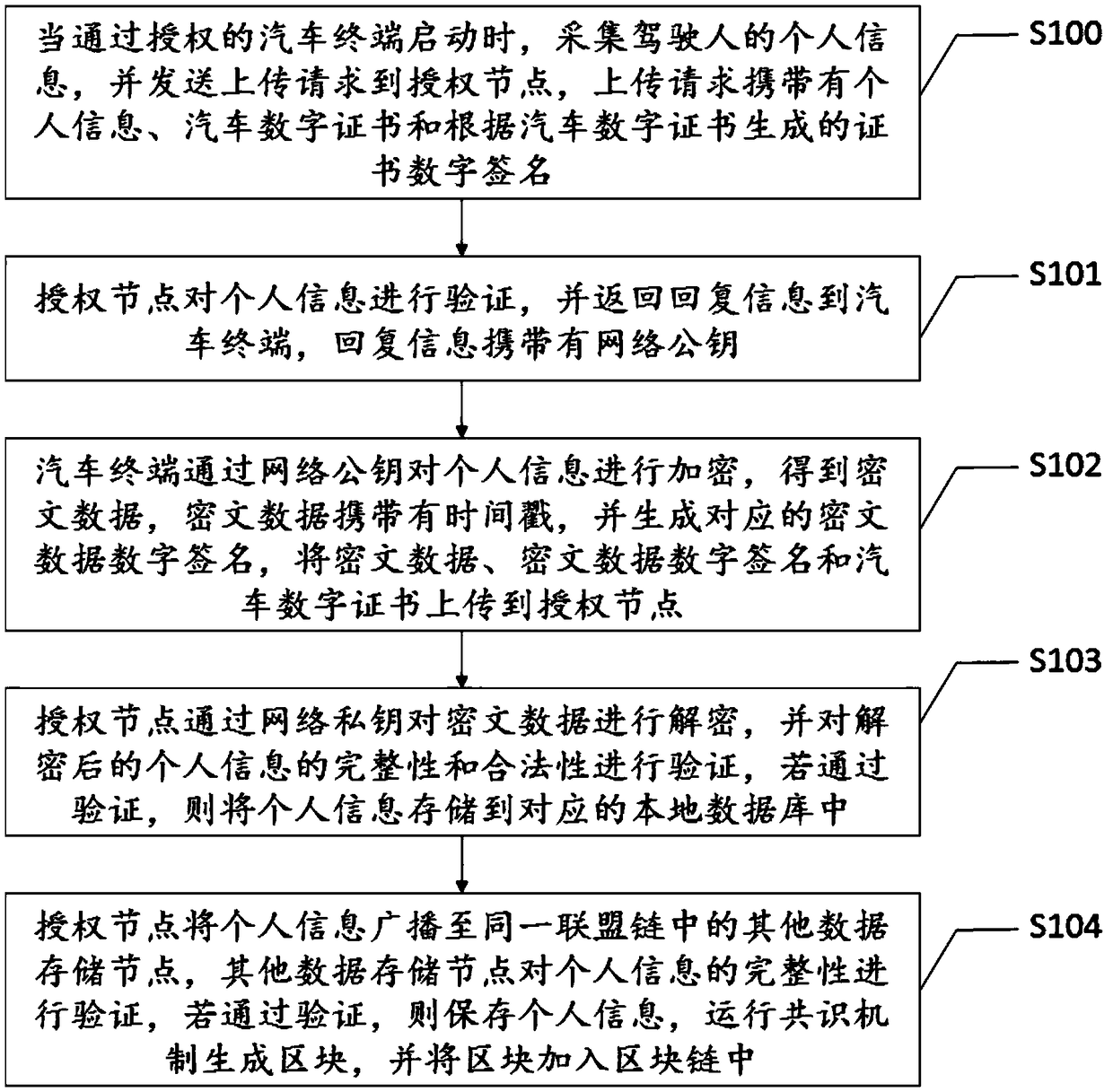
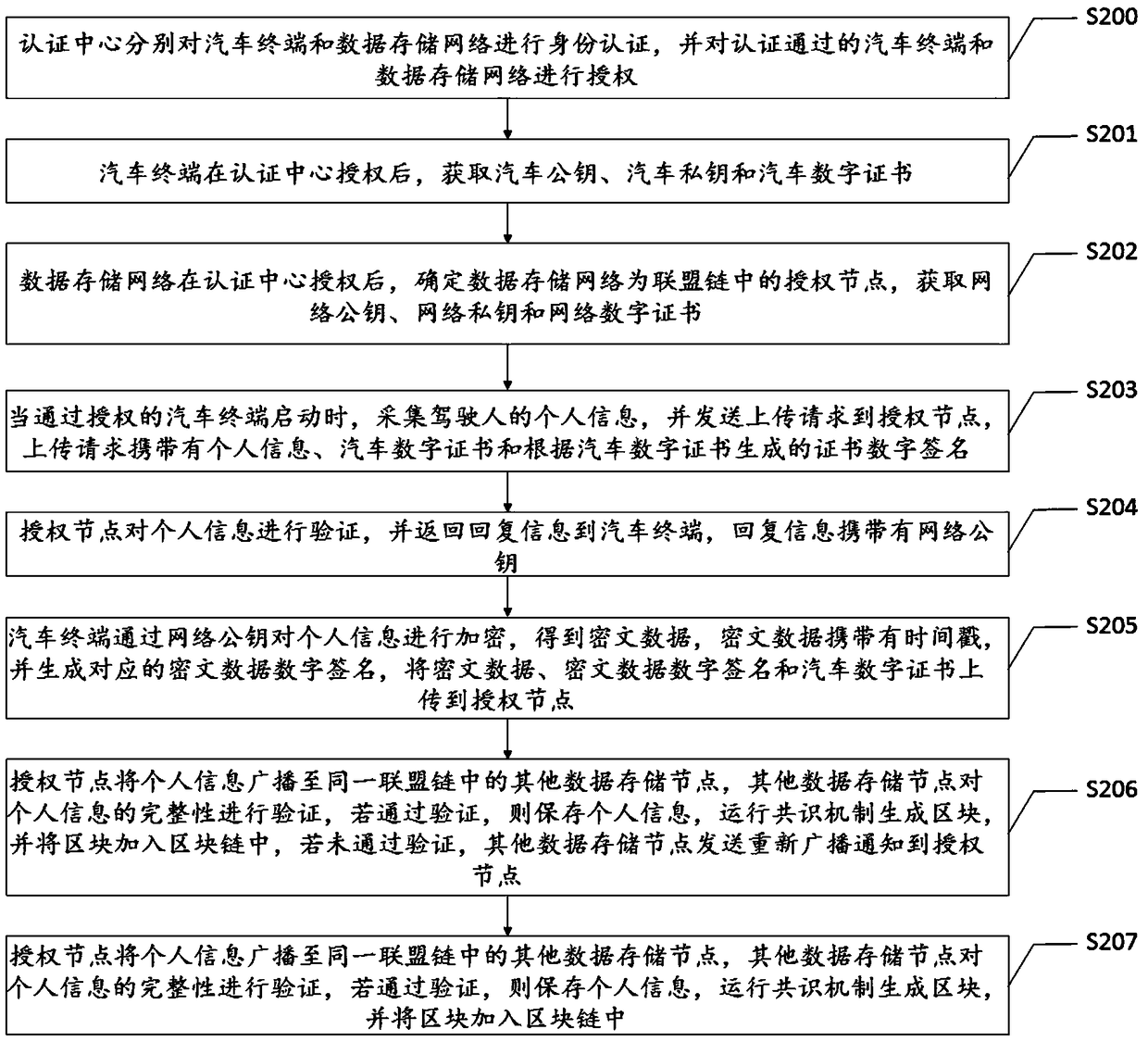
The invention discloses a method and a device for storing traffic information based on a coalition chain. The method comprises the following steps: the identity information of a driver is collected when an automobile terminal is started; authentication is carried out through the blockchain technology; the information is saved on the blockchain; the information on the blockchain has the characteristics of being non-tamperable and is stored in a decentralized database, thereby solving the technical problem that the current traffic information queries can only use the relevant sensors and other auxiliary means to determine the identity of a perpetrator after a traffic accident occurs; due to too many uncertain factors, the collection of evidence on the scene of the accident is affected, suchas the serious damage of the sensor in the accident, human malicious damage and other factors; and even after the relevant evidence has been collected and uploaded to a central server, the data may also be maliciously deleted, resulting in unreliable query results for the existing traffic information queries.
Owner:GUANGDONG UNIV OF TECH
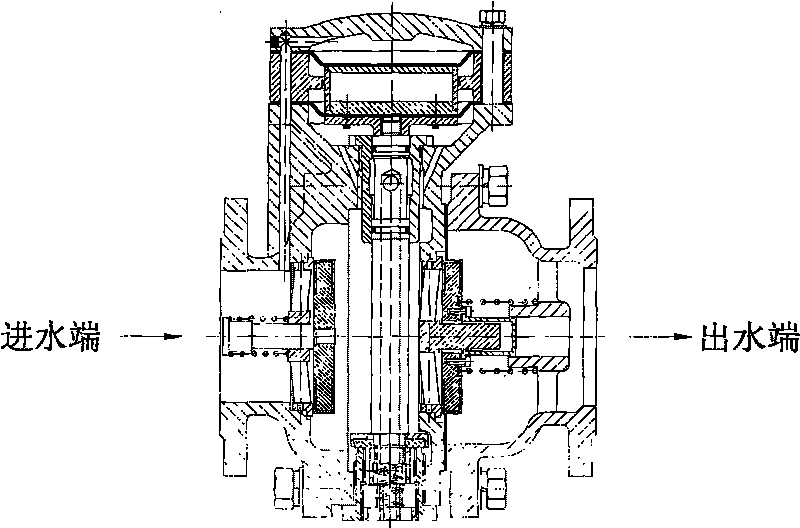
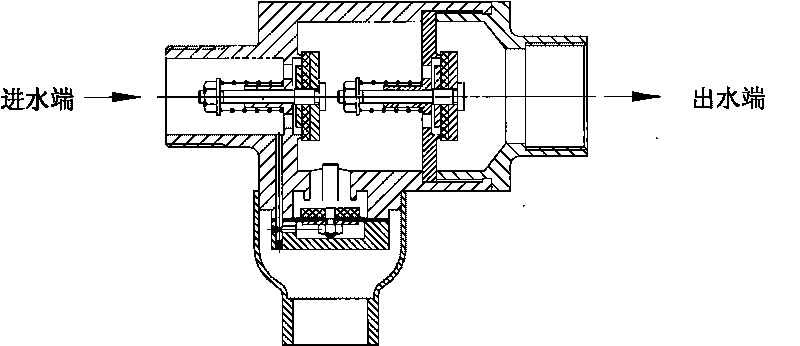
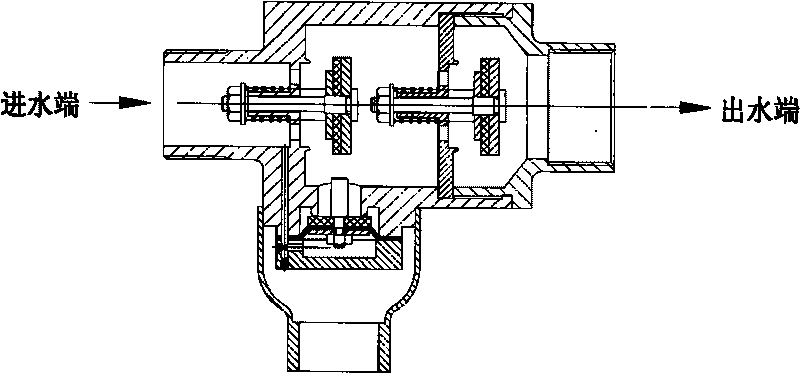
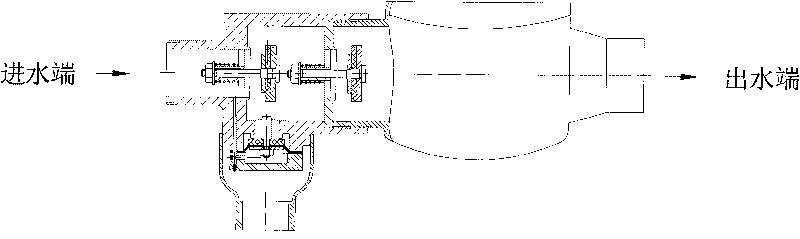
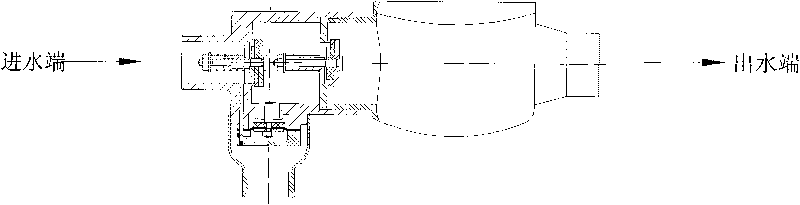
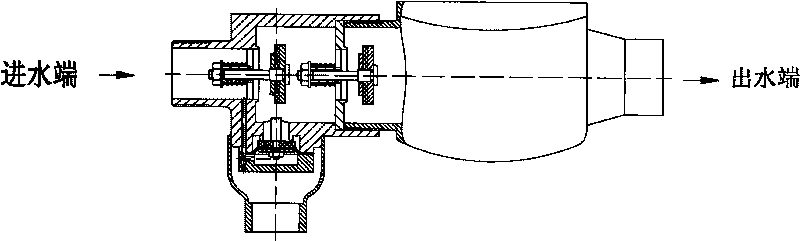
Dual-membrane micro-resistant ultrashort backflow preventer
The invention provides a dual-membrane micro-resistant ultrashort backflow preventer without a conduit. The backflow preventer comprises an inflow stop water-out valve and an effluent stop valve; valve bodies of the valve are fastened by a bolt and are communicated; a control chamber of the inflow stop water-out valve is provided with an interlayer sleeve; a guide pillar arranged in the control chamber is fixed in the middle of the control chamber by the interlayer sleeve; an upper membrane is arranged between a valve cover and the interlayer sleeve of the inflow stop water-out valve; an upper membrane is tiled on the top end surface of the guide pillar; a lower membrane is affixed on the bottom surface of the guide pillar and is fastened on the valve body of the inflow stop water-out valve with a bolt to form an upper cavity, double air isolating cavities and a lower cavity; a water-out valve rod of the inflow stop water-out valve is a hollow valve rod and communicated to outside air; an adjusting spring is arranged at the lower part of the water-out valve plate so as to adjust the minimum open pressure; and water from a water inlet of the inflow stop water-out valve enters through a through hole on the valve body and the interlayer sleeve into the upper cavity. The invention has the advantage that the backflow preventer with the structure is a combining device for flowing in single direction by strictly restricting pressure medium in a pipeline, has compact structure, saves installing space, can guide the backflow medium in the pipeline or medium in the critical backflow out of the pipe to form air isolation, does not need fittings, prevents malicious damage, ensures safe water supply, prevents pollution and is beneficial to observing and rapidly replacing membranes.
Owner:刘永 +1
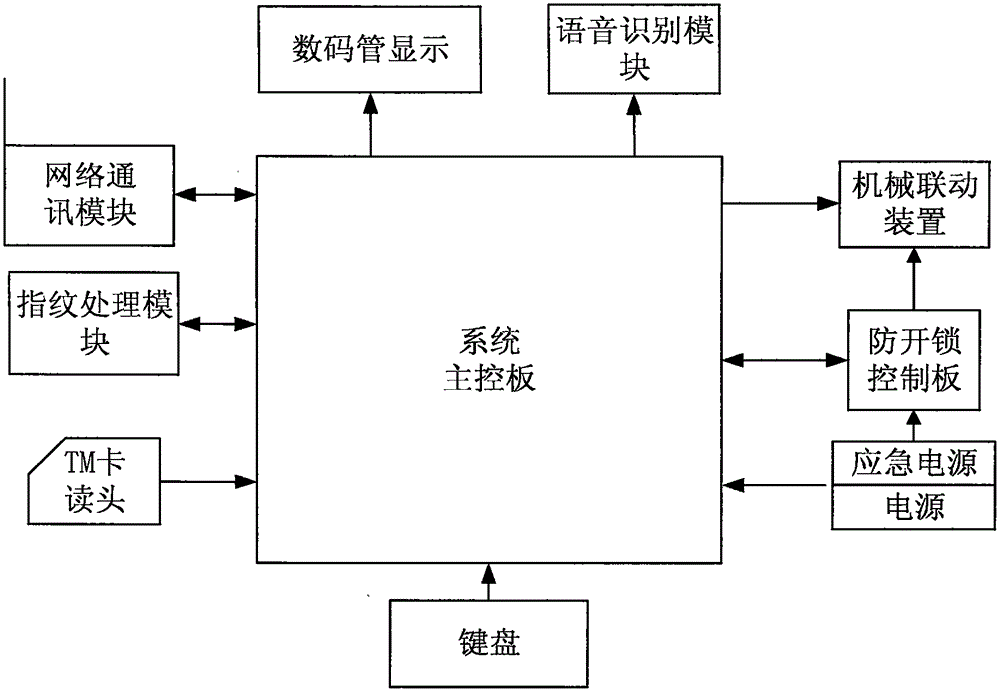
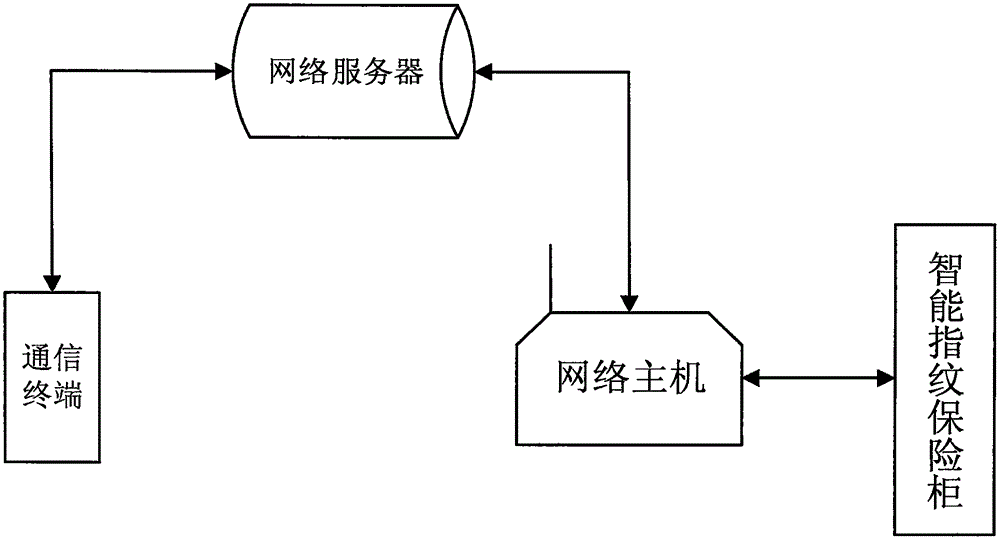
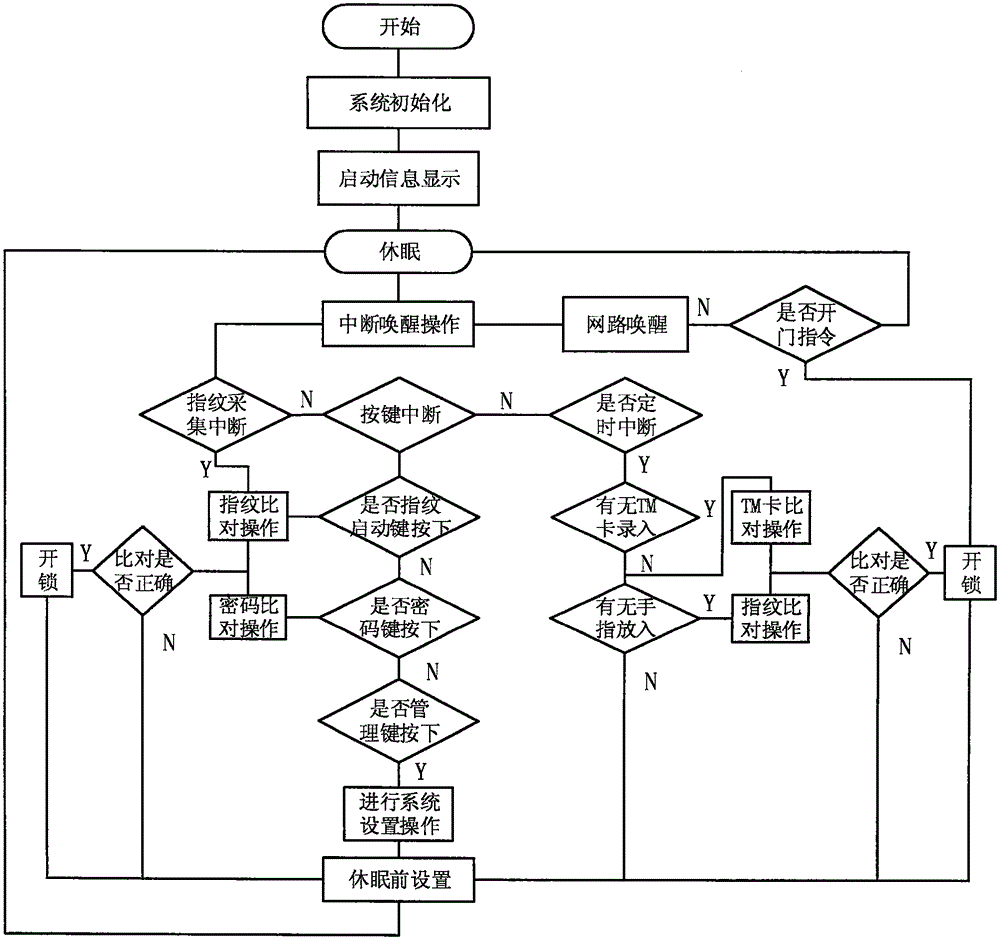
Network intelligent fingerprint safe case
InactiveCN105421934AEasy to useImprove securityIndividual entry/exit registersSafesNetwork intelligenceEmbedded system
The invention discloses a network intelligent fingerprint safe case, comprising a structure used for acquiring fingerprint, a network verification structure, and a safety structure of the safe case. The safe case performs fingerprint verification open in the following method: S1, initializing a fingerprint acquisition system, a network system, and a safe case body; S2, a screen of the safe case starting to display information; S3, the safe case body entering a dormant state; S4, waiting for a door opening instruction, and awakening through the door opening instruction; S5, after awakening, entering unlocking comparison; S6, the comparison being successful, a system master control panel sending an opening instruction to a mechanical linkage device, and the mechanical linkage device starting to operate to control the locking bolt of the safe case to contract, so as to open the case door. The safe case is high in system security, and a plurality of unlocking methods effectively prevent malicious damages. The safe case is flexible and has a function of tracking robbery.
Owner:青岛众音科技发展有限公司
Intelligent waste paper recycling system
InactiveCN105772176AEasy to recycleImprove recycling efficiencyPoint-of-sale network systemsGrain treatmentsPulp and paper industryPayment system
The invention provides an intelligent waste paper recycling system. The intelligent waste paper recycling system comprises a box body, a storage barrel, a weighing system, a paper shredder, a control center, a virtual currency payment system and a display screen, wherein the display screen is arranged on the outer side wall of the box body; a horizontal opening is formed in the outer side wall of the box body; the weighing system is arranged at the bottom of the box body; the storage barrel is arranged on the weighing system; the paper shredder is arranged in the opening; the control center is arranged on the box body; the control center is separately connected with the display screen, the weighing system and the paper shredder; and the virtual currency payment system is arranged in the control center. Users can conveniently recycle waste paper. The intelligent waste paper recycling system has the beneficial effects that firstly, users can conveniently recycle waste paper; secondly, malicious acts can be monitored in time, and malicious damage by certain people can be avoided; and thirdly the waste paper recycling efficiency is high, and when the storage barrel is about to be full during recycling, a signal is transmitted, so that related personnel can take the waste paper away.
Owner:温州智宇翱华商务服务有限公司
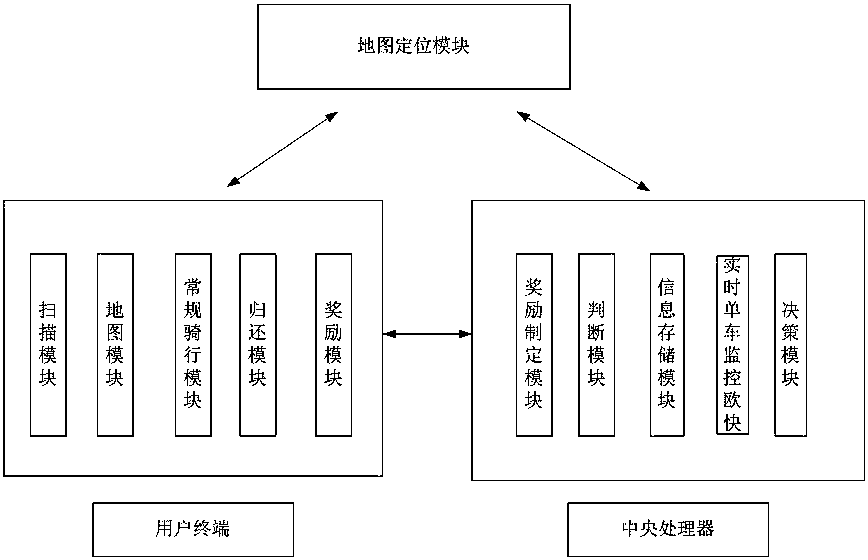
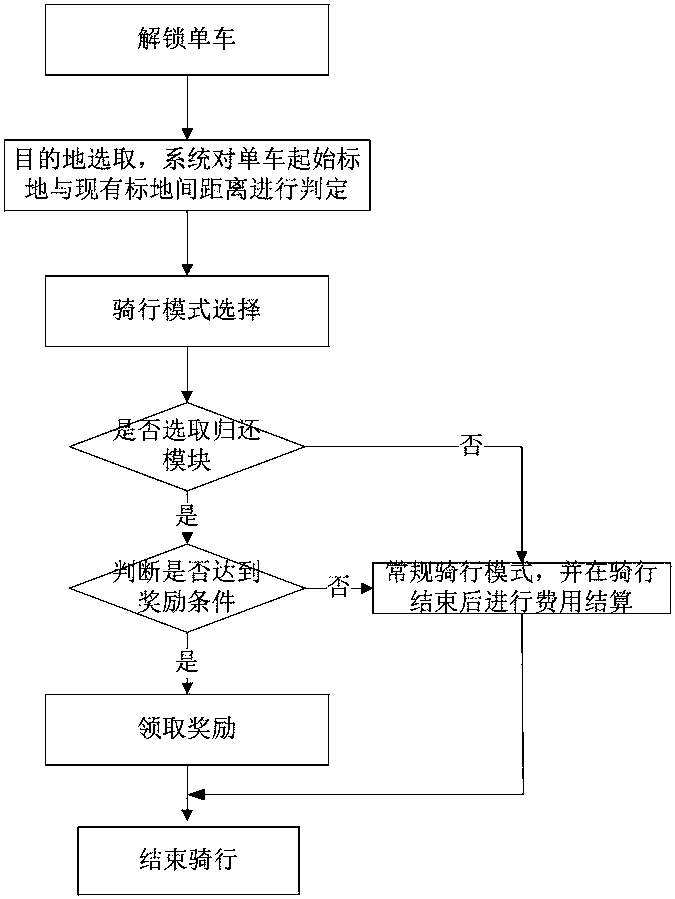
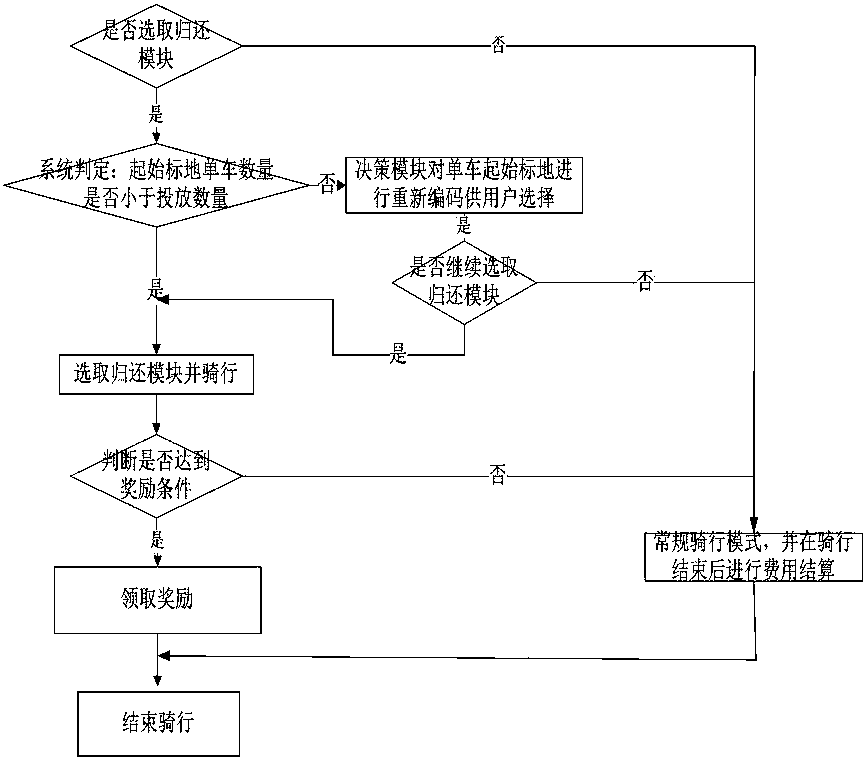
User terminal, system and method for avoiding bike aggregation and returning bikes
InactiveCN107610346ARegulate riding behaviorIncrease return rateRegistering/indicating working of vehiclesApparatus for meter-controlled dispensingComputer terminalOperation mode
The invention discloses a user terminal, system and method for avoiding bike aggregation and returning bikes. Compared with the conventional shared bike operation modes, the bike trip mode can help operators to normalize the number of bikes in each region, can maintain a basic stable input number of the bikes in each region, can be used in big cities and population-intensive areas, can improve thereturning rate of bike users, can adopt a manner of stimulating user bike sharing to normalize the bike use manner, and can improve the bike use pleasure of the users; the use rate of bikes in a sharing riding mode is higher, and the problem of malicious damage to the bikes can be greatly reduced in use of the bikes; the civilized travelling quality of urban residents can be improved, and the riding comfort level of the users can be improved; the use number and the promotion degree of the bikes can be improved by setting awards, and incomes of the operators can be increased; and the user terminal, the system and the method can be promoted.
Owner:孙成波
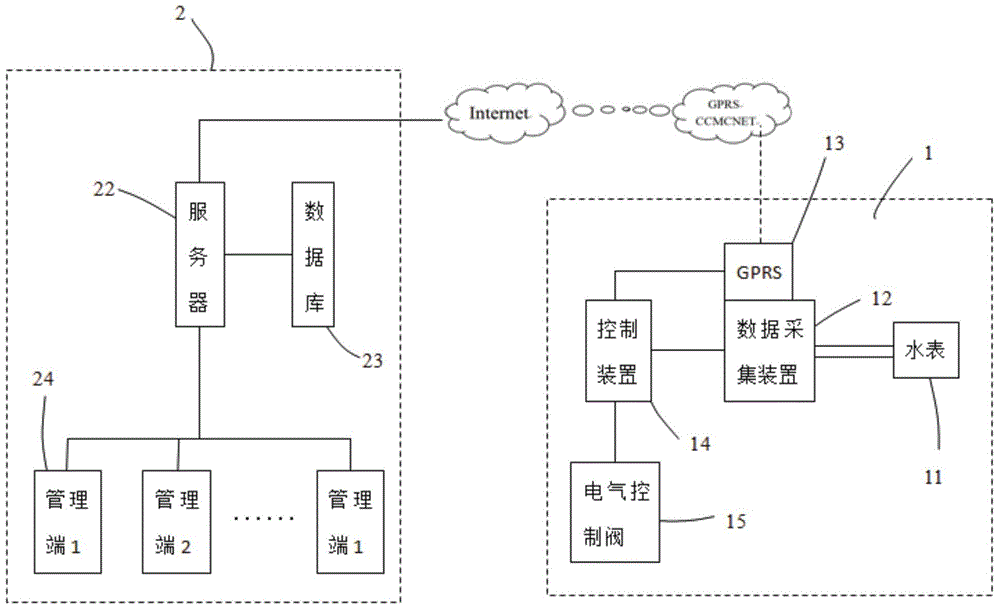
Remote water meter monitoring system and remote water meter monitoring method
InactiveCN104316124AAvoid lossPrevent vandalismVolume indication and recording devicesWater conservationMonitoring systemData acquisition
The invention relates to a remote water meter monitoring system and a remote water meter monitoring method. The remote water meter monitoring system comprises a water meter control end and a service end for realizing bidirectional communication, wherein the water meter control end comprises a water meter, a data acquisition device which is connected with the water meter and is used for acquiring the water consumption data of the water meter, a data transmission device which is connected with the data acquisition device and realizes bidirectional communication with a server, a control device which is connected with the data acquisition device and the data transmission device respectively and is used for controlling the data transmission device to transmit the water consumption data to the server, and an electric control valve which is connected with the control device and is controlled to be opened or closed by analyzing the water consumption data through the control device. The water consumption data of the water meter is acquired through the data acquisition device and is transmitted to a server side system, and the electric control valve is controlled to be opened or closed through the control device according to the data acquired by the data acquisition device, so that losing of water consumption information due to damage of the water meter is prevented, and malicious damage is prevented.
Owner:扬州恒信仪表有限公司
Network security processing method and wireless communications device
InactiveCN102045361AStrong preventive abilityImprove performanceTransmissionSecurity arrangementAnalysis dataNetwork packet
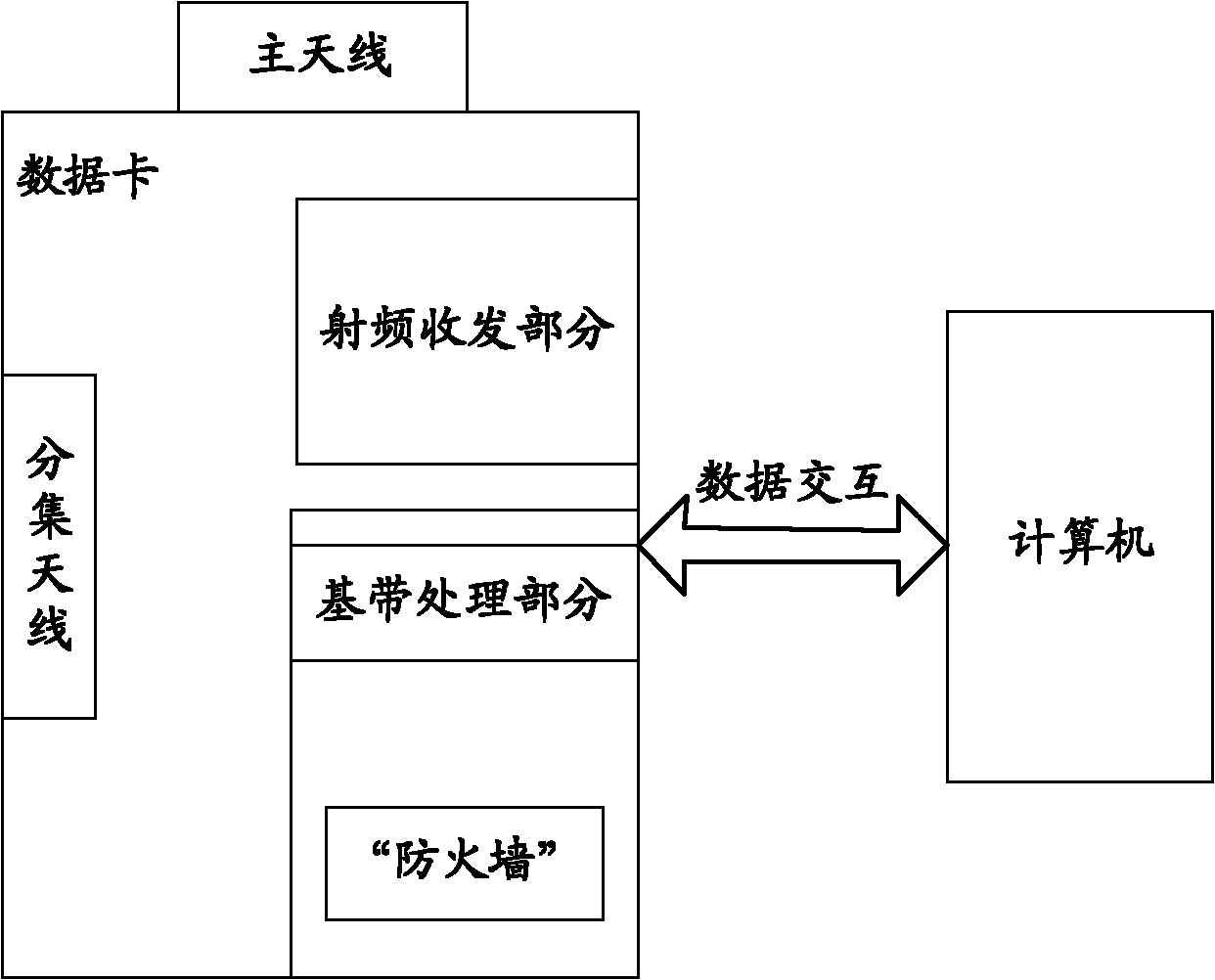
The invention puts forward a network security processing method and a wireless communication device. The network security processing method is used for carrying out network information interaction by a wireless communication device connected with a computer, and comprises the following steps: embedding a firewall module into the wireless communication device; then carrying out real-time monitoring on the network information directly by utilizing the wireless communications device; and intercepting the network accesses which do not conform to the requirements stipulated in rules. The wireless communication device provided by the invention can monitor external network attacks, and has a strong preventive effect on internal malicious damages, thereby improving the performance and security of the system; and through analyzing the addresses, protocols, ports and the like of data packets, the wireless communication device can filter and monitor the through dynamic of interactive data.
Owner:ZTE CORP
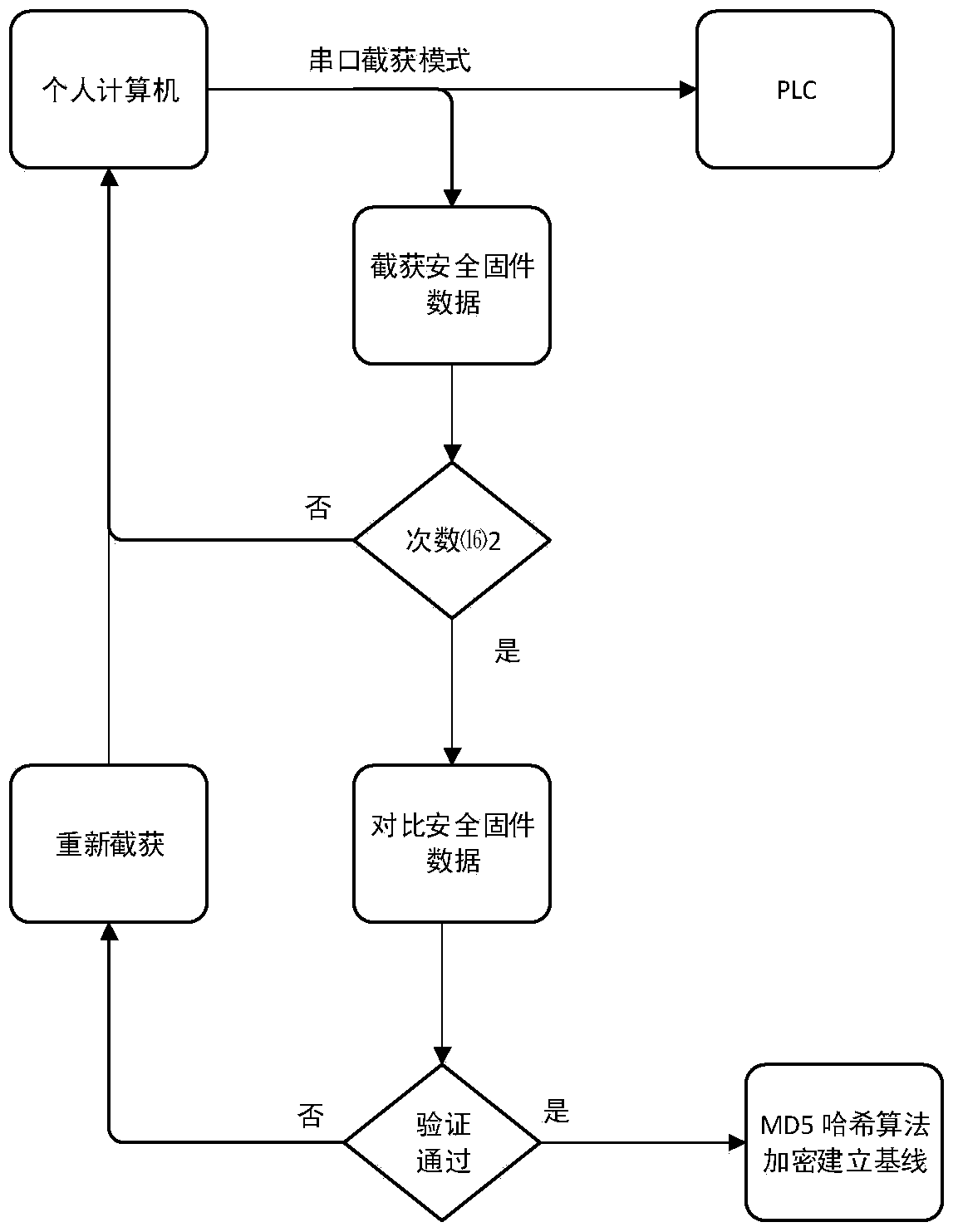
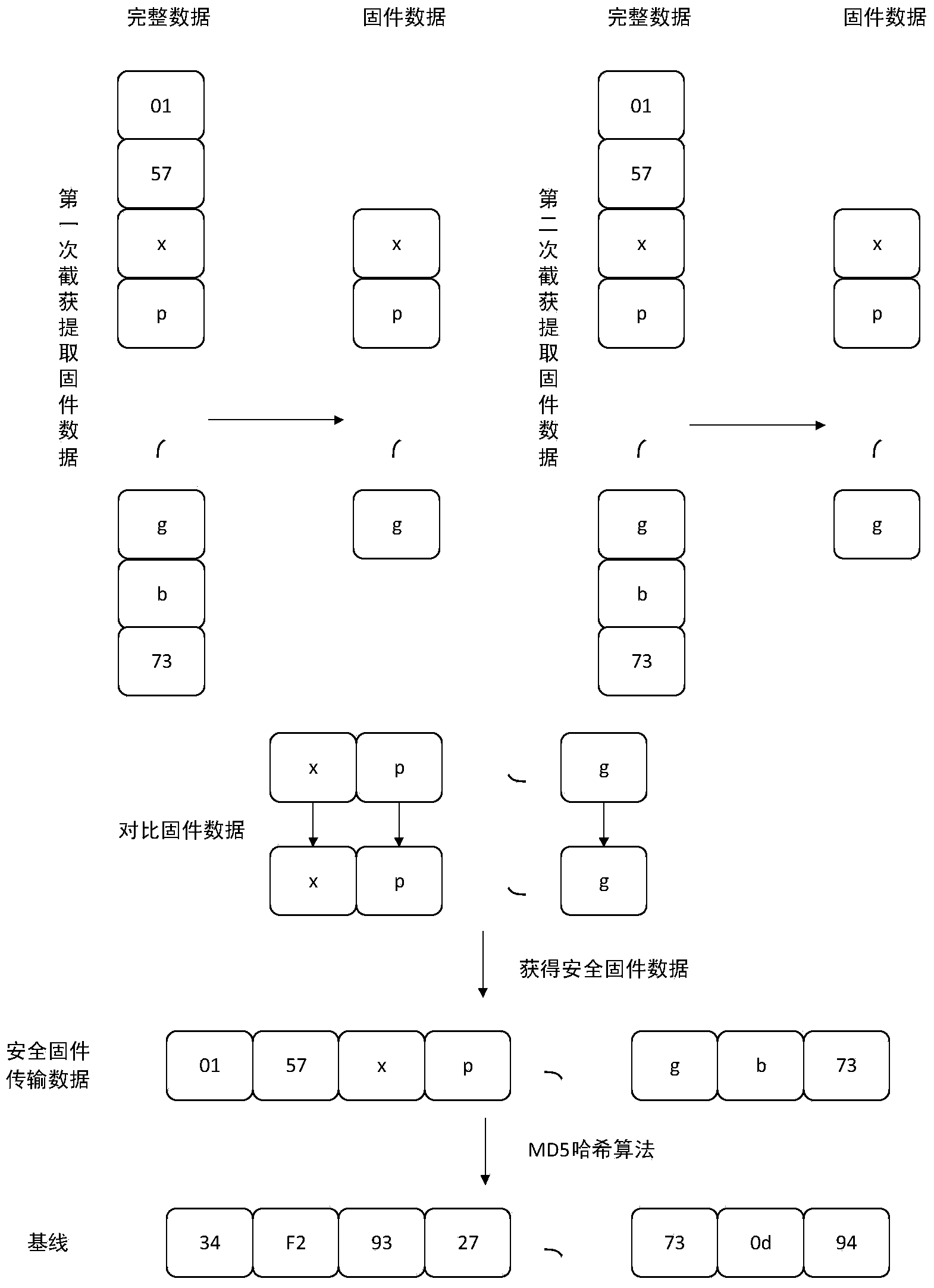
Device and method for verifying programmable logic controller (PLC) firmware integrity
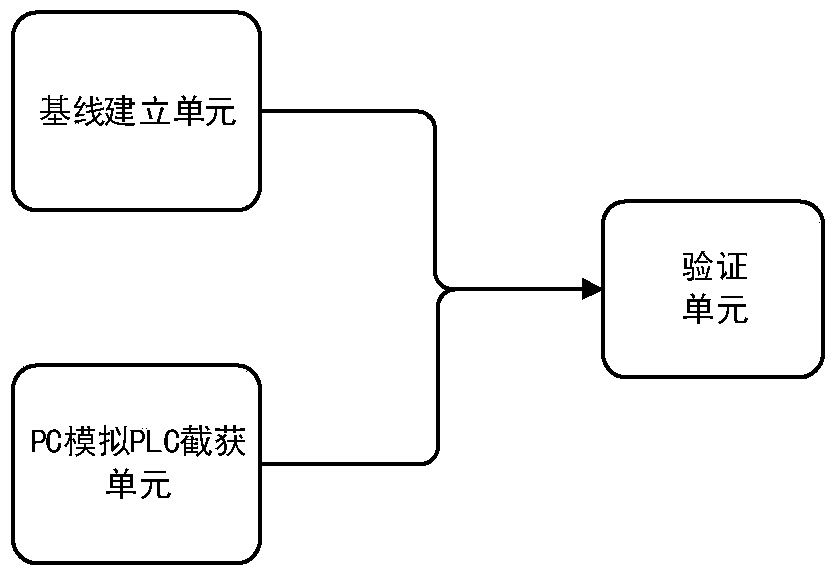
ActiveCN103645672AConvenient and effective verificationSolve extraction difficultiesProgramme control in sequence/logic controllersValidation methodsProgrammable logic controller
The invention discloses a device and method for verifying programmable logic controller (PLC) firmware integrity. The device comprises a base line establishment unit, a PC simulation PLC intercepting unit and a verification unit. The base line establishment unit is used for intercepting security firmware data and establishing 32-bit base lines on the basis of an MD5 Hash algorithm; the PC simulation PLC intercepting unit is used for transmitting unknown security firmware to a PC of a simulation PLC, intercepting the unknown security firmware and working out 32-bit firmware abstracts through the MD5 Hash algorithm; and the verification unit is used for performing comparing verification on the base lines and the firmware abstracts. Integrity verification is performed on the unknown security firmware before the unknown security firmware is loaded to the PLC, and the device and the method guarantee that the firmware led into the PLC is complete. Malicious damage to the firmware caused by lawbreakers or competitors of the same kind is avoided.
Owner:SOUTH CHINA UNIV OF TECH
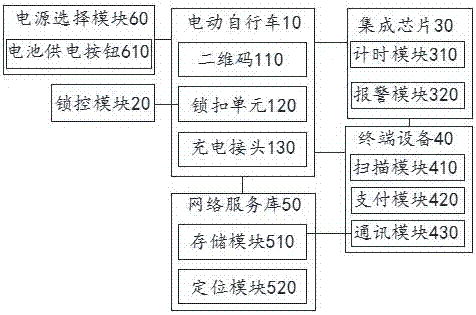
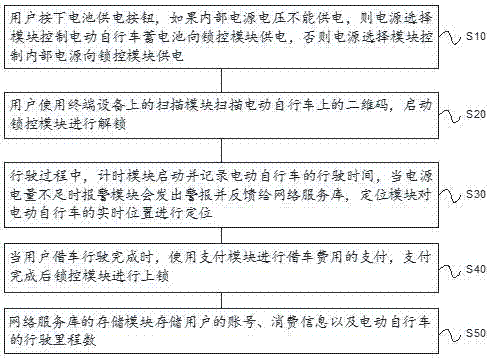
Public electric bicycle system and use method thereof
InactiveCN106960520AEasy to useImprove securityApparatus for meter-controlled dispensingPaymentComputer module
The invention discloses a public electric bicycle system and a use method thereof. The system comprises an electric bicycle, a lock control module, an integrated chip, a terminal device and a network service library, wherein a QR code, a lock catch unit and a charging connector are arranged on the electric bicycle; the lock control module is used for processing bicycle renting data and bicycle returning data to lock and unlock the electric vehicle; the integrated chip comprises a timing module and an alarming module; the terminal device comprises a scanning module, a payment module and a communication module; the network service library comprises a storage module and a positioning module. According to the bicycle system and the use method thereof, a user can conduct information interaction with the bicycle and the network service library timely, stealing and malicious damage conditions are avoided, the safety is higher, and the bicycle is more convenient and rapider to use by the aid of two power supply modes adopting a storage battery and an internal power supply.
Owner:合肥酷睿网络科技有限公司
Historical data processing method and device, computer equipment and storage medium
ActiveCN109902127ASave storage spaceAvoid malicious damageDatabase distribution/replicationDatabase design/maintainanceDatabase engineSecurity policy
The invention discloses a historical data processing method and device, computer equipment and a storage medium, and belongs to the technical field of databases. The method comprises the following steps: when any first device of a single-machine database system meets a data transfer condition, obtaining historical data to be copied from the single-machine database system; Based on the historical data, copying the copy data to a cluster database system; And when the copying is successful, allowing the standalone database system to delete the stored historical data and the meta-information in response to the deletion operation of the database engine. The invention provides a data security strategy for processing historical data. According to the method, when the copy data in the stand-alonedatabase system is successfully copied to the cluster database system, the historical data and the meta-information are allowed to be deleted, so that the storage space of the stand-alone database system is saved, malicious damage to the historical data is avoided, and the security of the historical data is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
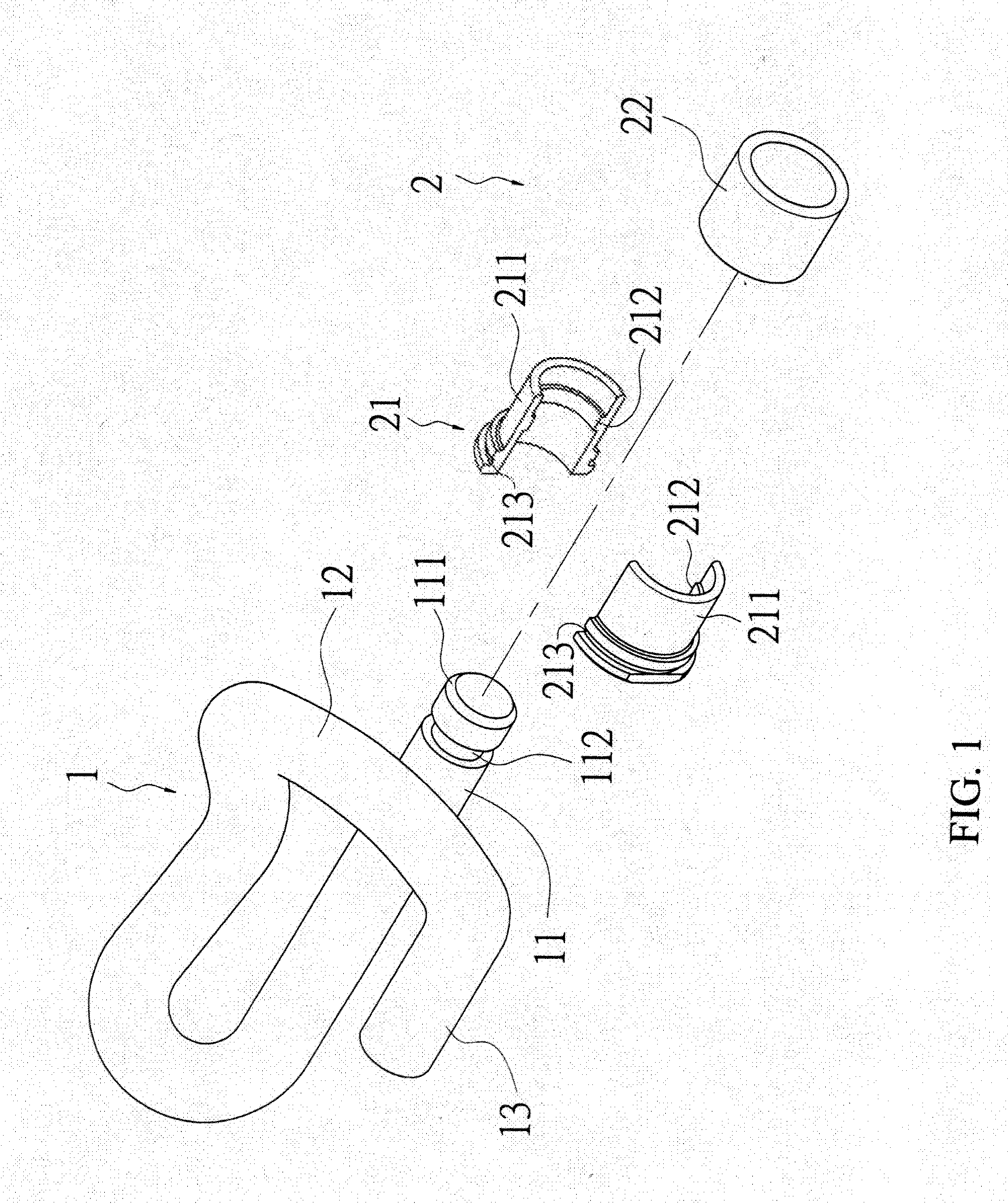
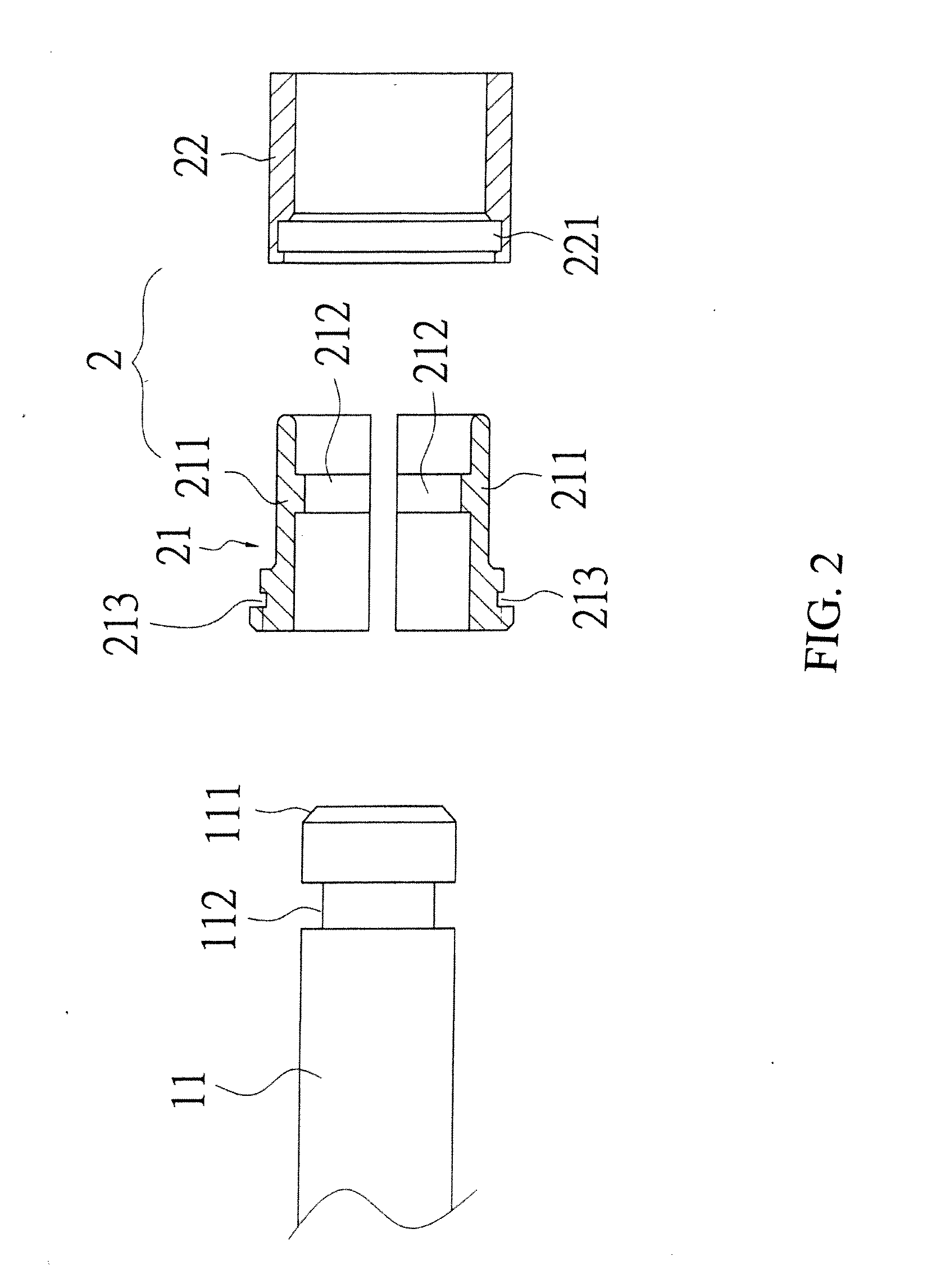
Steel rail clip assembly
InactiveUS20120187208A1Reduce riskAvoid easy removalRail fastenersTrack superstructureEngineeringMechanical engineering
A steel rail clip assembly having a clip and a locating member is revealed. A locating slot is arranged at an outer edge of an insertion rod of the clip while the locating member includes an inner bushing and an outer bushing mounted to each other. The inner bushing includes a locating block arranged at an inner surface and corresponding to the locating slot of the insertion rod. A locking projecting part and a corresponding locking concave part are respectively disposed on the inner bushing and the outer bushing. Thereby the clip is located by the locating member and unable to be removed easily without special tools. The falling of the clip of the steel rail caused by vibration of trains or malicious damage, knocking on railways is avoided. Thus the safety of train traffic services is ensured and the risk of related property losses and injuries is reduced.
Owner:WANG MING SHUN +1
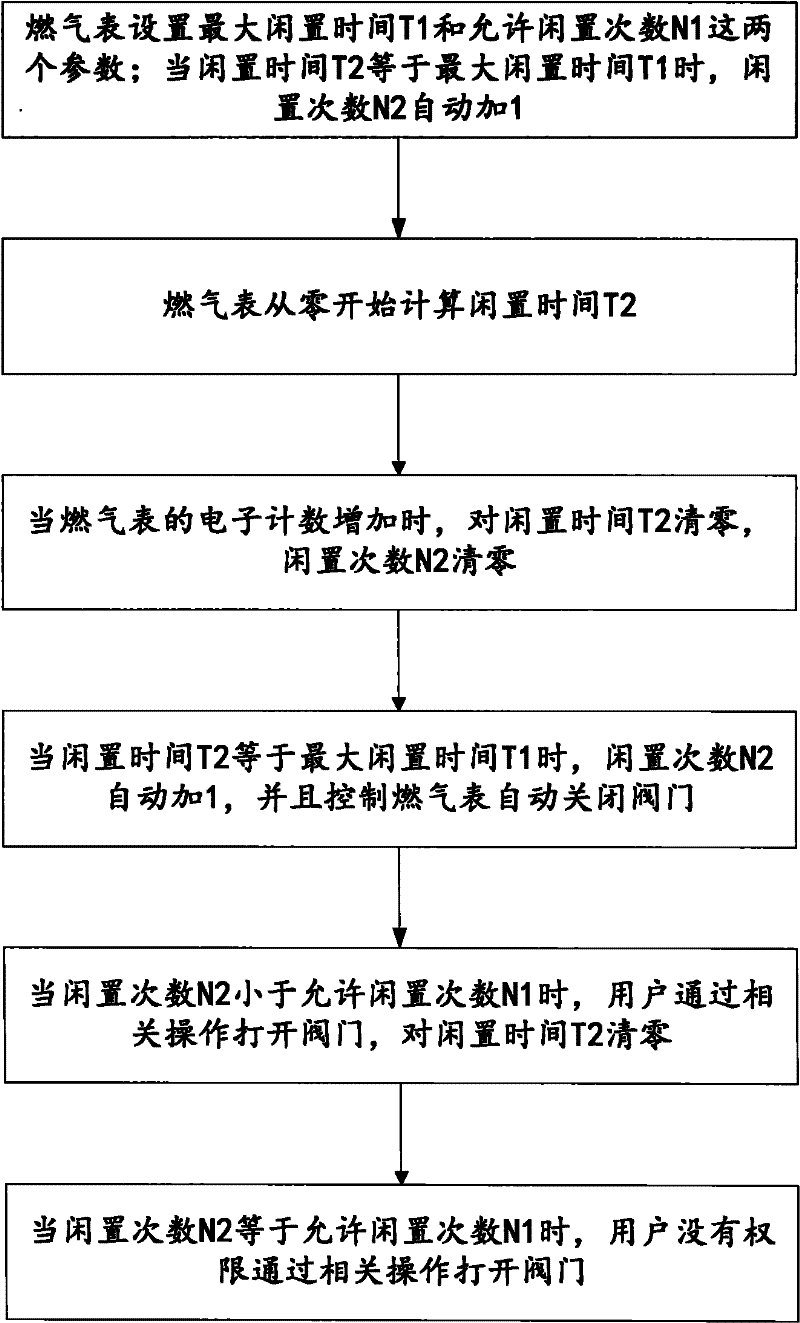
Idling control method for gas meter
InactiveCN102128660AAvoid malfunctioningReduce lossesVolume meteringApparatus for hiring articlesIdle timeTime control
The invention discloses an idling control method for a gas meter. The method comprises the following steps of: setting maximum idling time T1 and allowable idling times N1 of the gas meter; when idling time T2 is equal to the maximum idling time T1, adding 1 to the idling times N2; when the electronic counting of the gas meter increases, zeroing the idling time T2 and the idling times N2; when the idling time T2 is equal to the maximum idling time T1, adding 1 to the idling times N2 and controlling the gas meter to automatically close a valve; when the idling times N2 are smaller than the allowable idling times N1, making a user open the valve through relevant operation and zeroing the idling time T2; and when the idling times N2 are equal to the allowable idling times N1, forbidding the user from opening the valve through relevant operation. By adopting the method disclosed by the invention, the valve can be controlled to open and close according to the idling time of gas, the defects of unavailable normal work and failed electronic counting function of the gas meter caused by malicious damage to the gas meter by the user can be avoided and the loss of a gas company is reduced.
Owner:上海复展智能科技股份有限公司
Device for quickly installing and disassembling guardrail based on rotating shaft
ActiveCN105297652APrevent vandalismSmooth rotationRoadway safety arrangementsControl engineeringCalipers
The invention discloses a device for quickly installing and disassembling a guardrail based on a rotating shaft. The device comprises a quickly-disassembling joint, a guardrail cross rod, a clamping part and an upright post, wherein the quickly-disassembling joint comprises an upper fixed plate, a rotating shaft, a shaft spring, a lower fixed plate, a right caliper, a return spring, a left caliper and a fixed shaft. According to the device for quickly installing and disassembling the guardrail based on the rotating shaft, special tools are required when the quickly-disassembling joint and a cross rod component are installed on the upright post with a clamping opening or are disassembled, so that some malicious damages of non-staff can be avoided; and meanwhile, installation and disassembly only need simple rotary action, so that the labor intensity of workers in field installation is effectively reduced, the work hours and cost are saved, and the operation is convenient and fast.
Owner:邳州市景鹏创业投资有限公司
Screw-thread backflow prevention device being free from being equipped with external conduit
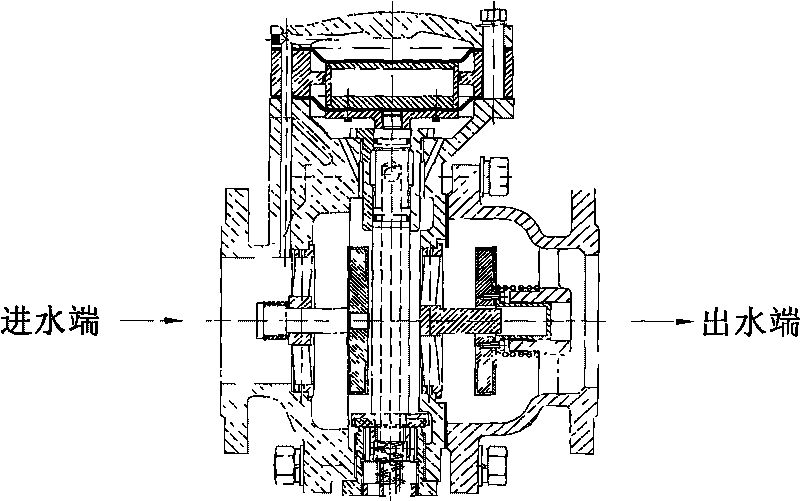
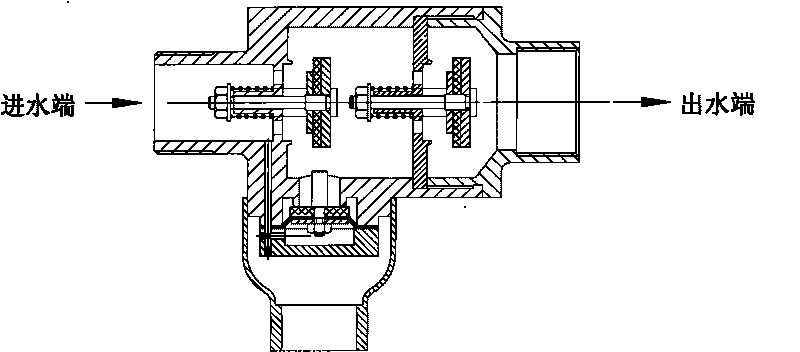
ActiveCN101749461AAvoid lostGuaranteed lossOperating means/releasing devices for valvesCheck valvesBackflow prevention deviceEngineering
The invention provides a screw-thread backflow prevention device being free from being equipped with an external conduit, which comprises an inlet water non-return water escape valve, an outlet water check valve and a connection port, wherein the inlet water non-return water escape valve, the outlet water check valve and the connection port are communicated with each other; a diaphragm is arranged inside a control chamber of the water escape valve, the diaphragm is flatly paved on the top end surface of a press plate to be covered by a lower cover and to be tightened onto a valve body of the water escape valve through bolt so as to form a control cavity, and water of a water inlet of the inlet water no-return valve flows through a through hole on the valve body and also flows through a through hole on the valve body of the water escape valve to enter the control cavity. The screw-thread backflow prevention device as the advantages that the backflow prevention device of the above structure is of a combination device which strictly limits that the pressure medium inside the pipeline flows in a single direction, the structure is compact, and the installation space can be saved; and the backflow medium inside the pipeline or the medium staying at the critical backflow state can be guided outside the pipe under any working conditions, and the air separation can be formed without any external accessory, so the device is free from the malicious damage, can ensure the safety of the water supply and can prevent the pollution.
Owner:TIANJIN GUOWEI FEEDING & DRAINAGE EQUIP MENT MFG
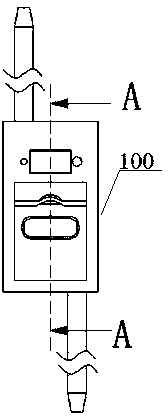
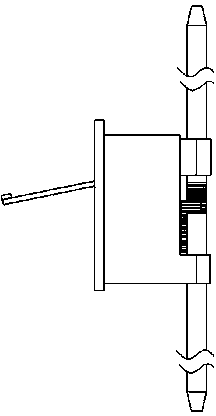
Intelligent lockset for outdoor ring main unit
ActiveCN104134258AImprove anti-theftImprove vandal resistanceWing handlesNon-mechanical controlsLocking mechanismEngineering
The invention discloses an intelligent lockset for an outdoor ring main unit. The lockset comprises a lock bracket (100) and a key (200). By identifying whether the key is authorized, opening and closing of a locking mechanism inside the lockset are realized. A solenoid is installed inside a cabinet door lock with the above function. In the locking state, the solenoid is inserted into a handle to block rotation of the handle, so as to block unlocking of the door lock. After the authorized key is inserted, the solenoid draws back to release locking of the handle. Then, the handle rotates to drive a gear to rotate, and a bolt also moves so as to open the door. However, when an unauthorized key is inserted, the solenoid is inserted inside the handle and the handle cannot rotate so as to block opening of the cabinet door. According to the invention, the severe potential safety hazard and malicious damage problems of a present outdoor ring main units' padlock mode are effectively solved.
Owner:STATE GRID CORP OF CHINA +3
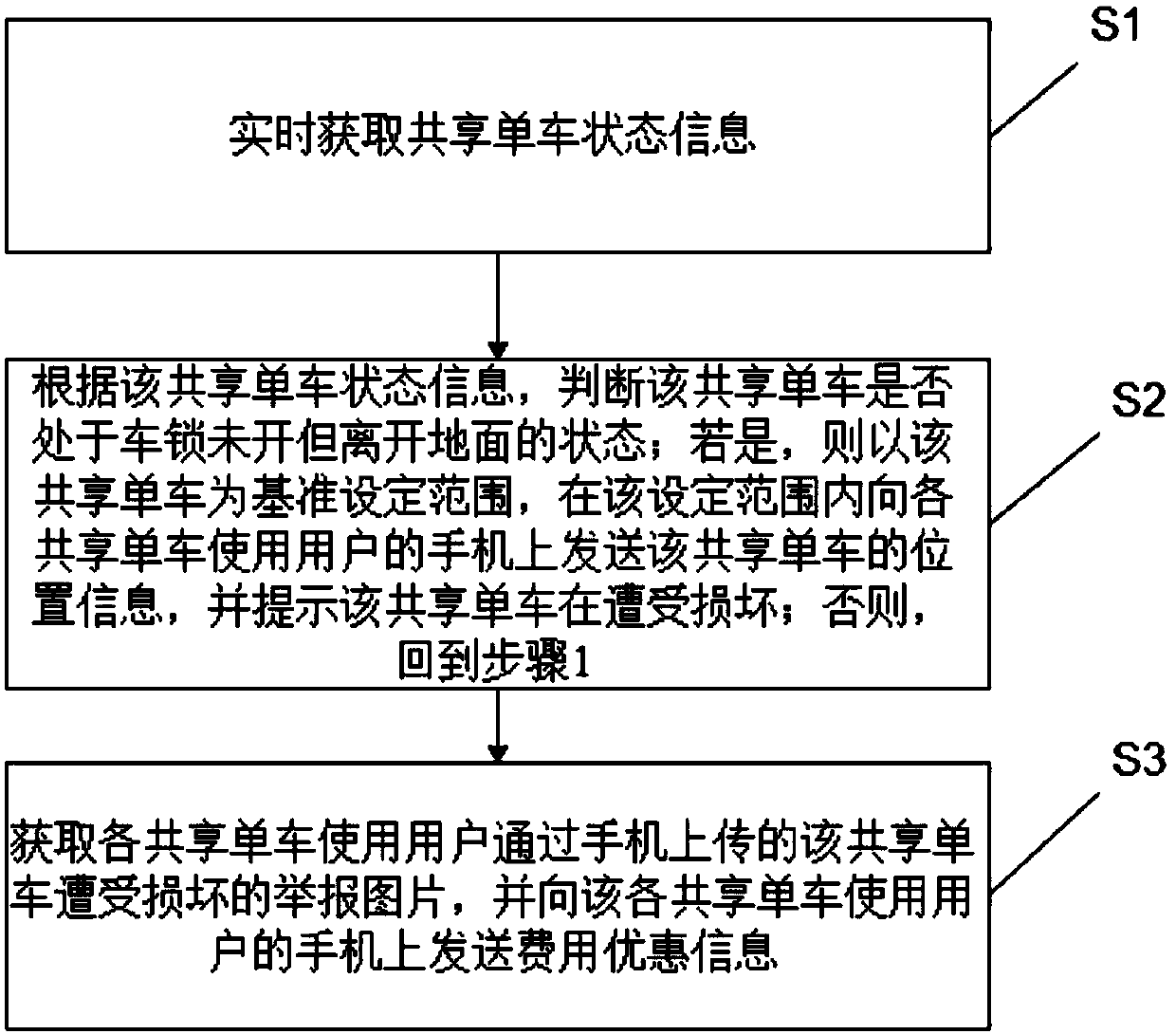
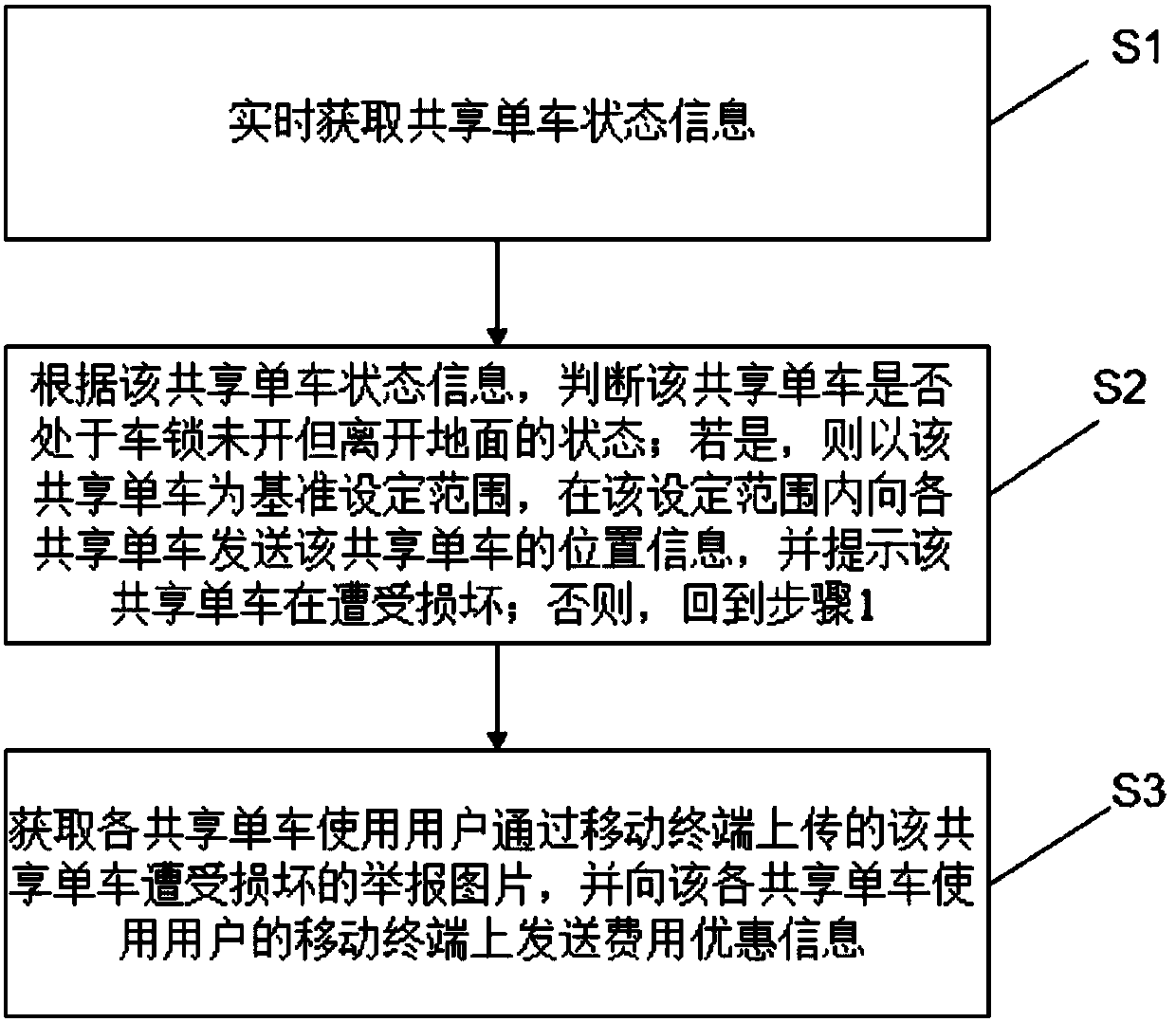
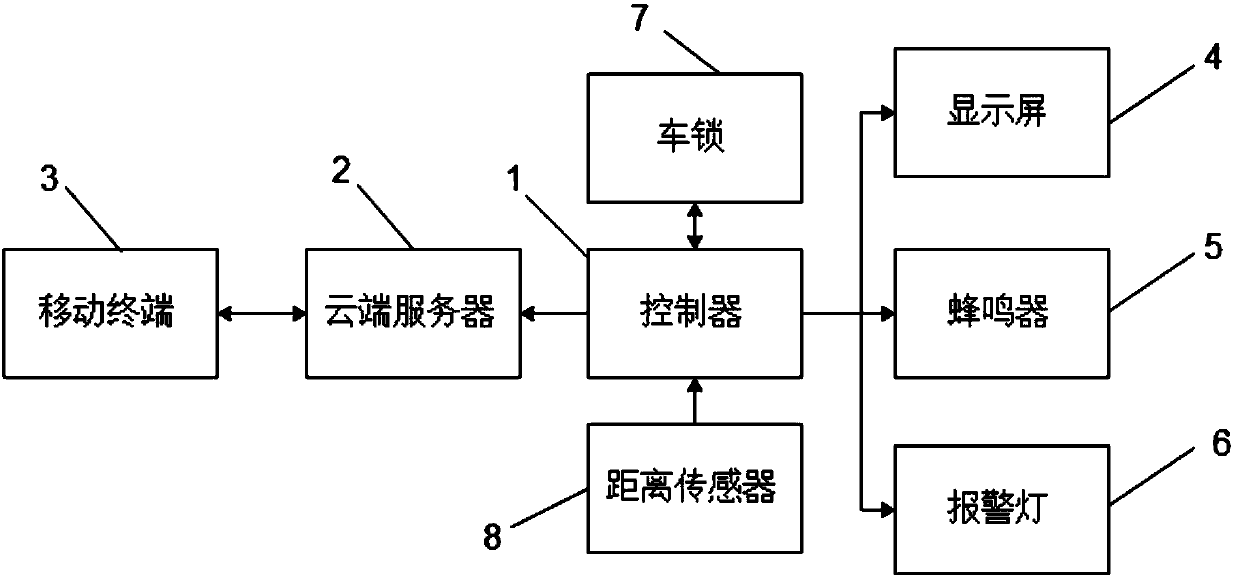
Shared bicycle damage monitoring system and method thereof
InactiveCN107703855APrevent malicious damage to shared bicyclesImprove monitoringProgramme controlComputer controlMonitoring systemSingle vehicle
The invention discloses a shared bicycle damage monitoring method. The method includes the following steps: real-timely acquiring the state information of a shared bicycle; based on the state information of the shared bicycle, determining whether the shared bicycle is in an unlocked state and is off the ground; if the shared bicycle is in an unlocked state and is off the ground, setting a range with the shared bicycle as the reference, transmitting the position information of the shared bicycle to the mobile phones of the users who use respective shared bicycles within the set range, and alerting the damages of the shared bicycle; acquiring the images of the damage of the shared bicycle that are reported and uploaded by the users who use respective shared bicycles through the mobile phones, and transmitting discount information to the mobile phones of the users who use respective shared bicycles. According to the invention, the method can automatically determine whether the shared bicycle is damaged, and without increasing production cost of the shared bicycle, the method herein increases monitoring capability, and prevents malicious damage to shared bicycles, such as preventing ashared bicycle from being left along in the street or being hung to a tree. The invention also provides a shared bicycle damage monitoring system.
Owner:余雪梅
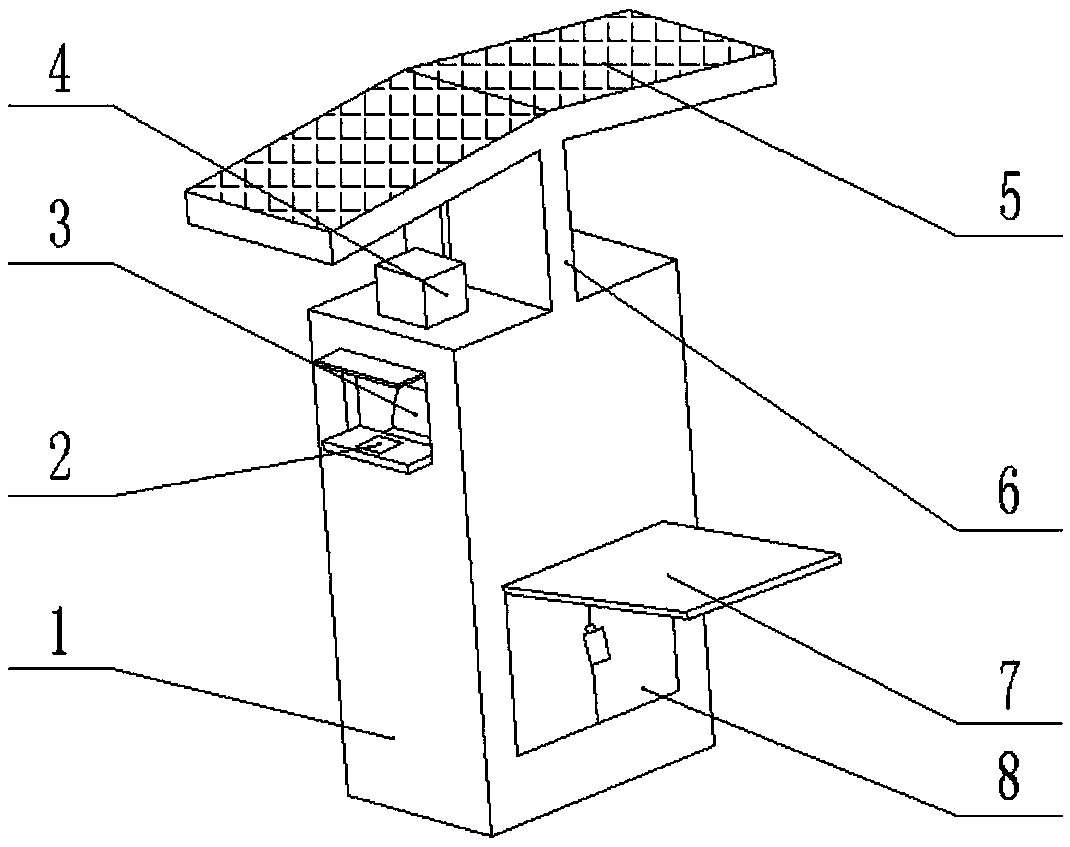
Intelligent object watching room of full-automatic safe deposit box
ActiveCN104314414AGuarantee the safety of useReduce Custody RiskBank protection deviceSafesObject storeEngineering
The invention relates to an intelligent object watching room of a full-automatic safe deposit box. The intelligent object watching room comprises safe deposit boxes and object watching rooms, wherein an outlet, which is used for picking and placing storage boxes, and an operating screen, which is used for displaying and operating, are arranged at one side of each safe deposit box, and each object watching room is a closed space which is used for enclosing the outlet and operating screen of the corresponding safe deposit box and is provided with a safe door; an examining device, which is used for examining whether each corresponding object watching room is in use or not, a card reader and a palm vein detector, which are used for verifying user identities, are arranged outside the object watching room, each safe door is provided with an electric lock, an automatic door closer and a key reviewing device, a lighting lamp and a human body detector are arranged in each object watching room, and an explosive detector, a hazardous liquid detector and a loss-preventing liquid detection device are arranged at the outlet of each safe deposit box. The intelligent object watching room has explosive and hazardous liquid prewarning functions, a storage box outlet malicious-damage alarming function, a user accidental-fainting detecting and alarming function and a key reviewing function, so that the risk of safekeeping of a bank can be reduced, the safety of use of users is guaranteed, and good object storing and safekeeping experience is provided.
Owner:GUANGZHOU UNICOMP TECH
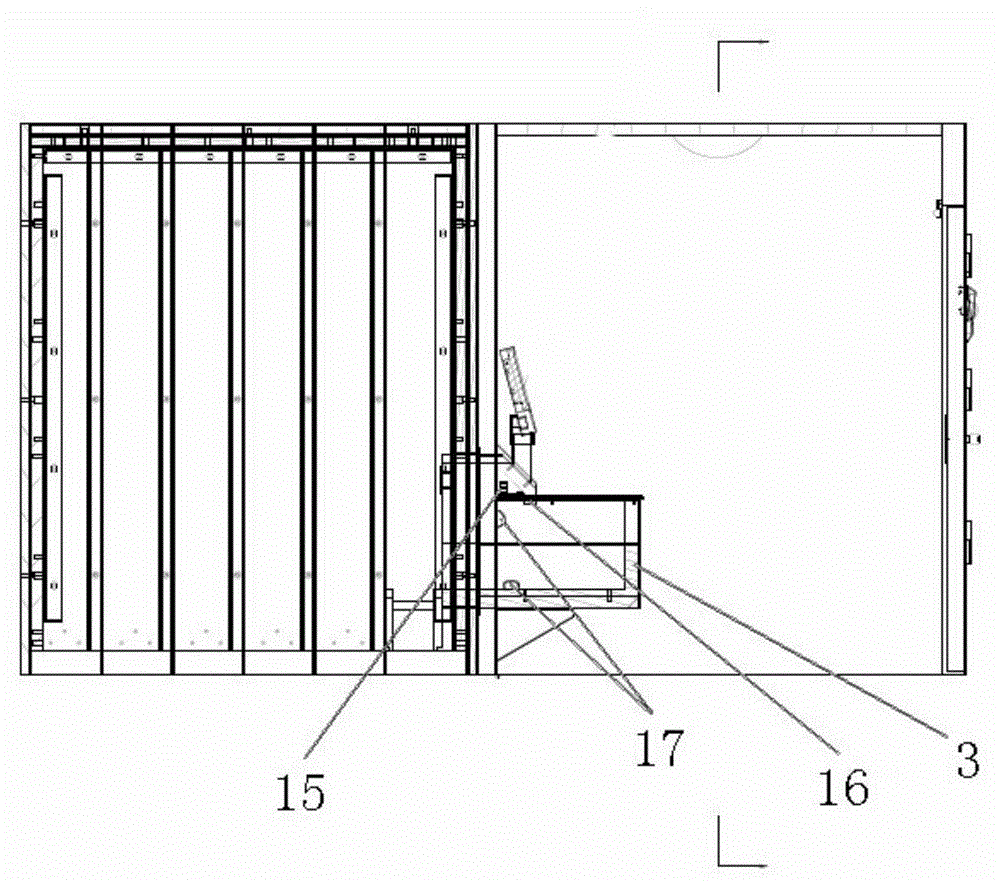
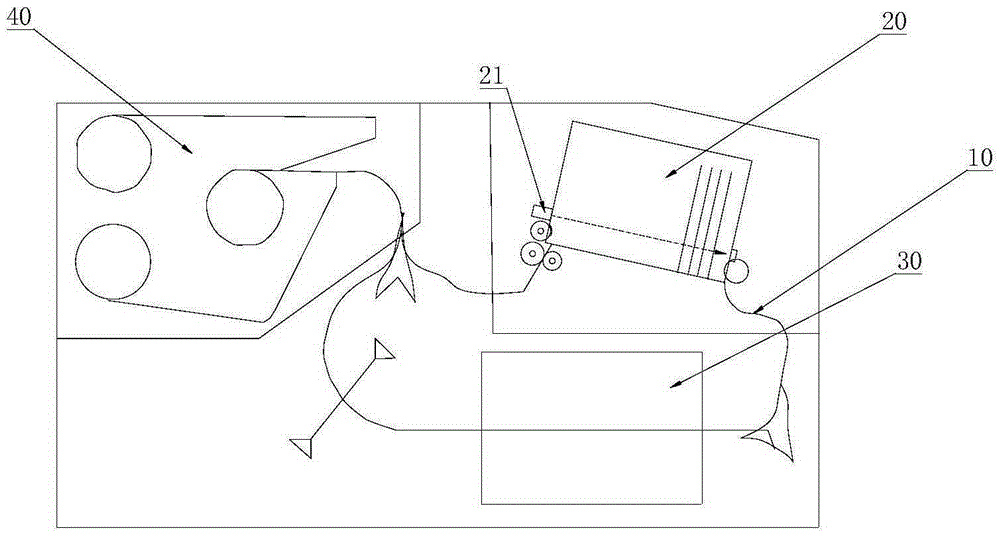
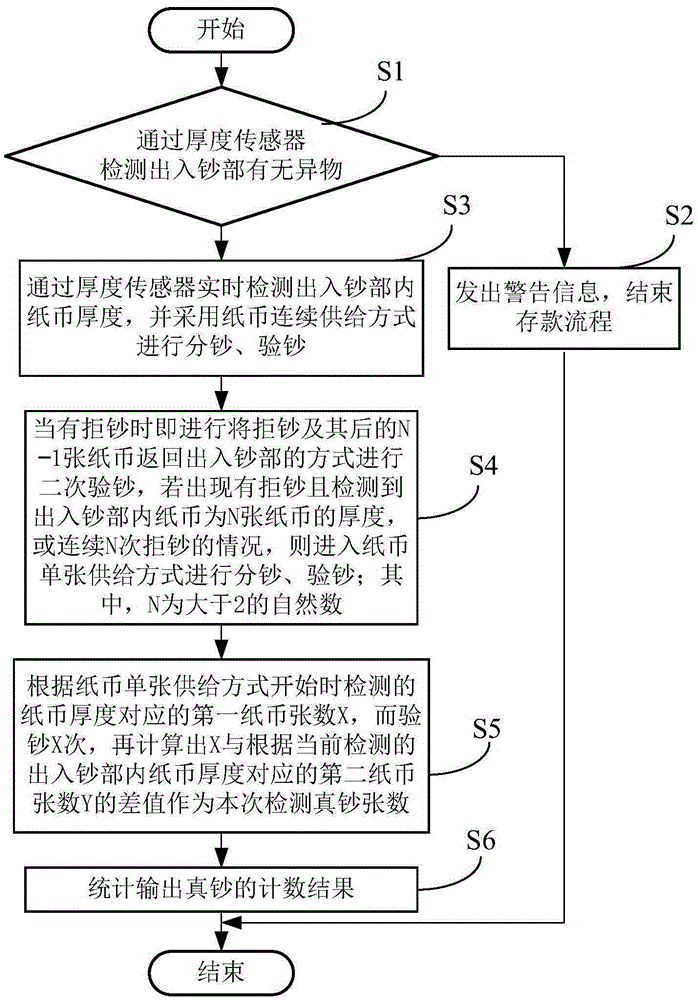
Deposit currency examination method and automatic currency recycling system
InactiveCN105427452AImprove experienceDiscovered in timePaper-money testing devicesCoin/currency accepting devicesForeign matterEngineering
The invention discloses a deposit currency examination method and an automatic currency recycling system. The automatic currency recycling system comprises a currency in and out portion, a currency examination portion and a temporary storage portion which realize communication through transmission channels, wherein the currency in and out portion is provided with a thickness sensor used for detecting whether the currency in and out portion has foreign matters internally and detects thickness of paper currency in the currency in and out portion, and a controller used for controlling switching currency division / examination modes is further comprised. According to the system, whether the currency in and out portion has foreign matters is firstly guaranteed, when currency rejection occurs, and thickness of paper currency in the currency in and out portion is detected to be equal to thickness of N papers, or N-times currency rejection occurs, a single paper currency supply mode is utilized to carry out currency division and currency examination, detection opportunity for possible-true currency is enhanced, a single paper currency supply mode is delayed, secondary paper currency examination times are effectively reduced, the whole deposit time is shortened, and client experience is improved, moreover, illegal objects can be timely discovered, the process is ended, and malicious damage to equipment can be avoided.
Owner:SHENZHEN YIHUA COMP +2
Shared bicycle damage monitoring system and shared bicycle damage monitoring method
InactiveCN107564274APrevent malicious damage to shared bicyclesImprove monitoringRoad vehicles traffic controlAlarmsMonitoring systemSingle vehicle
The invention discloses a shared bicycle damage monitoring method. The shared bicycle damage monitoring method includes acquiring shared bicycle state information in real time; judging whether a shared bicycle is in such states that a bicycle lock is locked but the shared bicycle gets away from the ground or not according to the shared bicycle state information; setting ranges on the basis of theshared bicycle if the shared bicycle is in the states, transmitting location information of the shared bicycle to various shared bicycles in the set ranges and prompting the fact that the shared bicycle is damaged; acquiring reported pictures uploaded by various shared bicycle users and transmitting expense concession information to the corresponding shared bicycle users. The fact that the sharedbicycle is damaged is indicated in the reported pictures. The shared bicycle damage monitoring method has the advantages that whether the shared bicycle is damaged or not can be automatically judged,concession is provided for the shared bicycle users who photograph the reported pictures indicating the fact that the shared bicycle is damaged, accordingly, the monitoring intensity can be improved,and the problem of malicious damage on existing shared bicycles due to the fact that existing shared bicycles are thrown aside or the existing shared bicycles are lifted to be hung on trees or the like can be solved. The invention further provides a shared bicycle damage monitoring system.
Owner:余雪梅
Direct buried optical cable communication access equipment
InactiveCN102595835BGuaranteed waterproof performanceAdd berth functionFibre mechanical structuresHermetically-sealed casingsHuman–machine interfaceWater leakage
The invention discloses a direct-embedded electronic equipment protection device and a direct-embedded optical-cable communication access equipment. The direct-embedded electronic equipment protection device comprises a protective housing of direct-embedded electronic equipment, and further comprises a shielding case arranged above the protective housing, wherein an air shielding space is formed between the upper part of the protective housing and the shielding case; the protective housing is provided with a sealing edge and / or a human-computer interface positioned in the air shielding space; and the shielding case is a sealed cover provided with an open cavity at the lower part. The protection device adopts a shielding case structure with the air shielding space and the multilayer sealing structure to take an IP68-grade sealing effect, and adopts a ventilated respirator to effectively ensure air circulation in the electronic equipment tank and prevent water in the tank from condensation. The problems of groundwater immersion, water leakage of the tank body and poor air circulation in the tank are effectively solved, and the functions of moisture protection, water resistance, mold prevention, salt haze prevention, dust prevention, burglary resistance, malicious damage avoidance and the like are served. The direct-embedded electronic equipment protection device can be widely used for waterproof protection of direct-embedded electronic equipment, such as direct-embedded communication equipment, direct-embedded monitoring equipment and the like.
Owner:CHINA MOBILE GRP GUANGDONG CO LTD
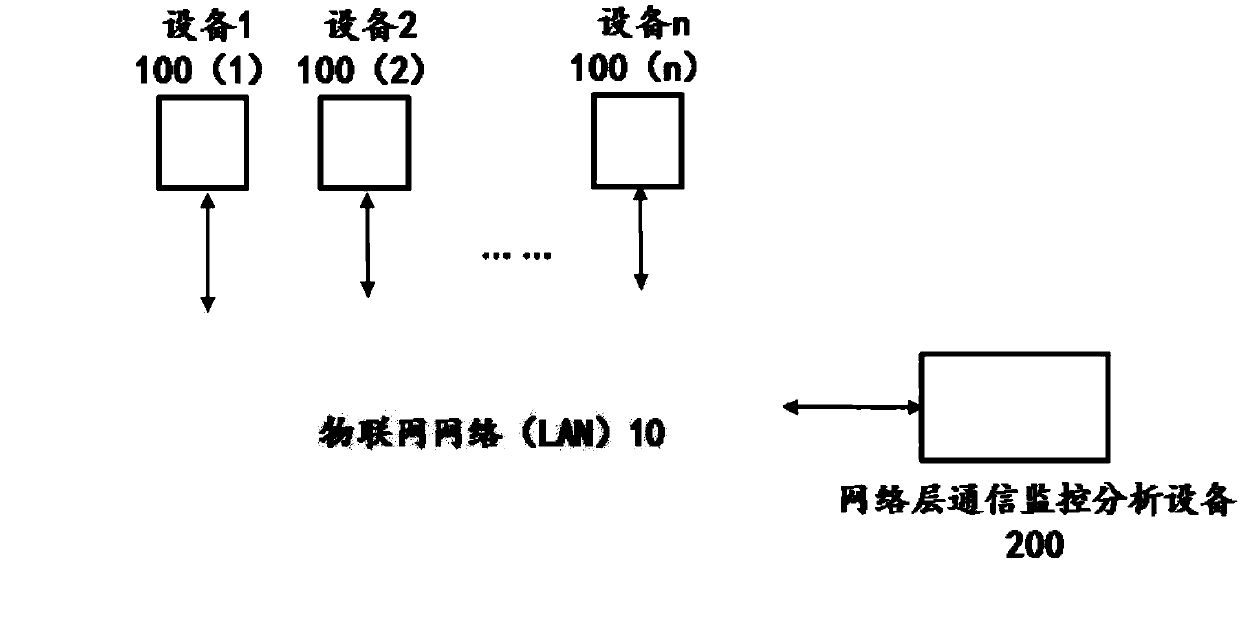
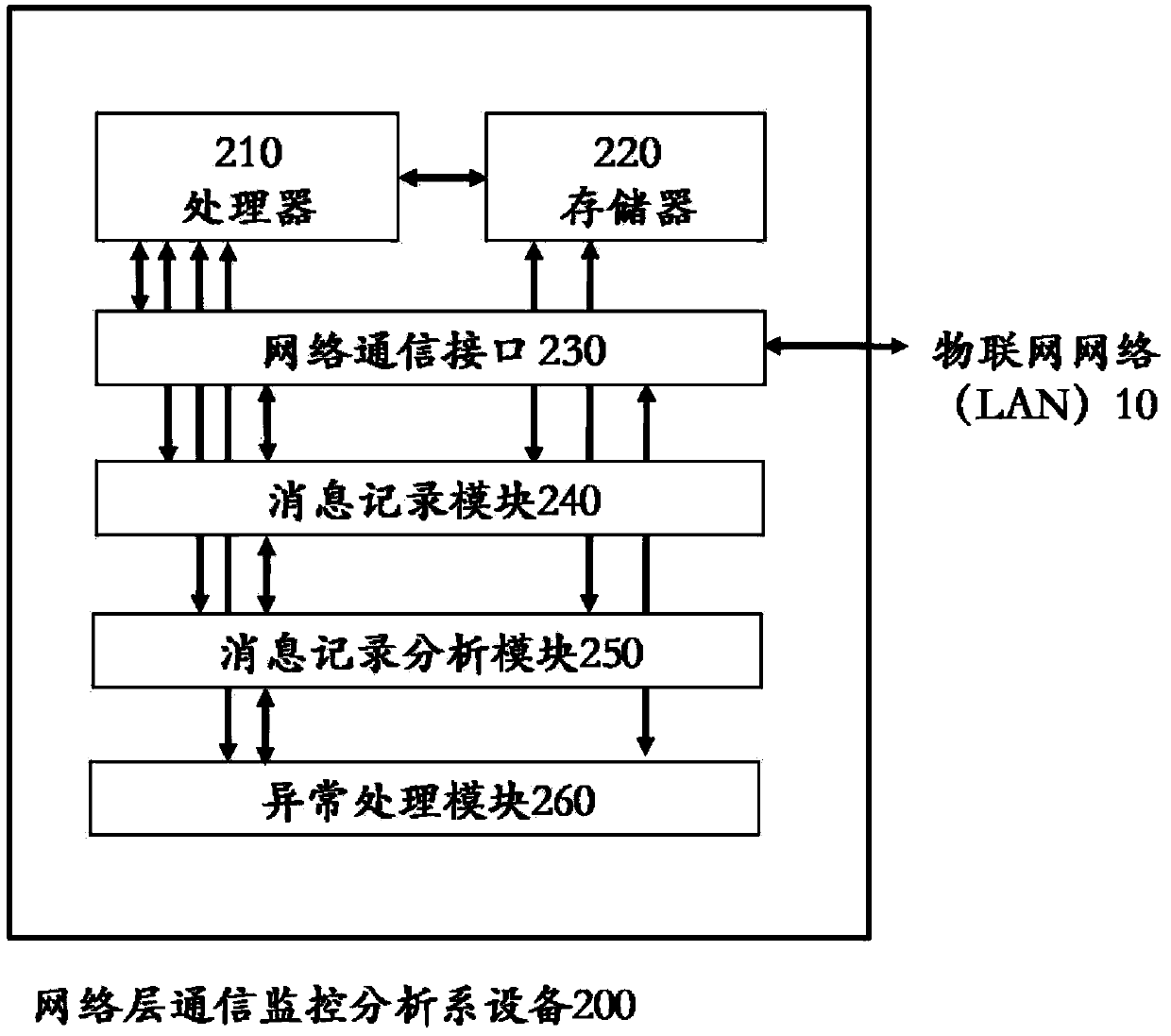
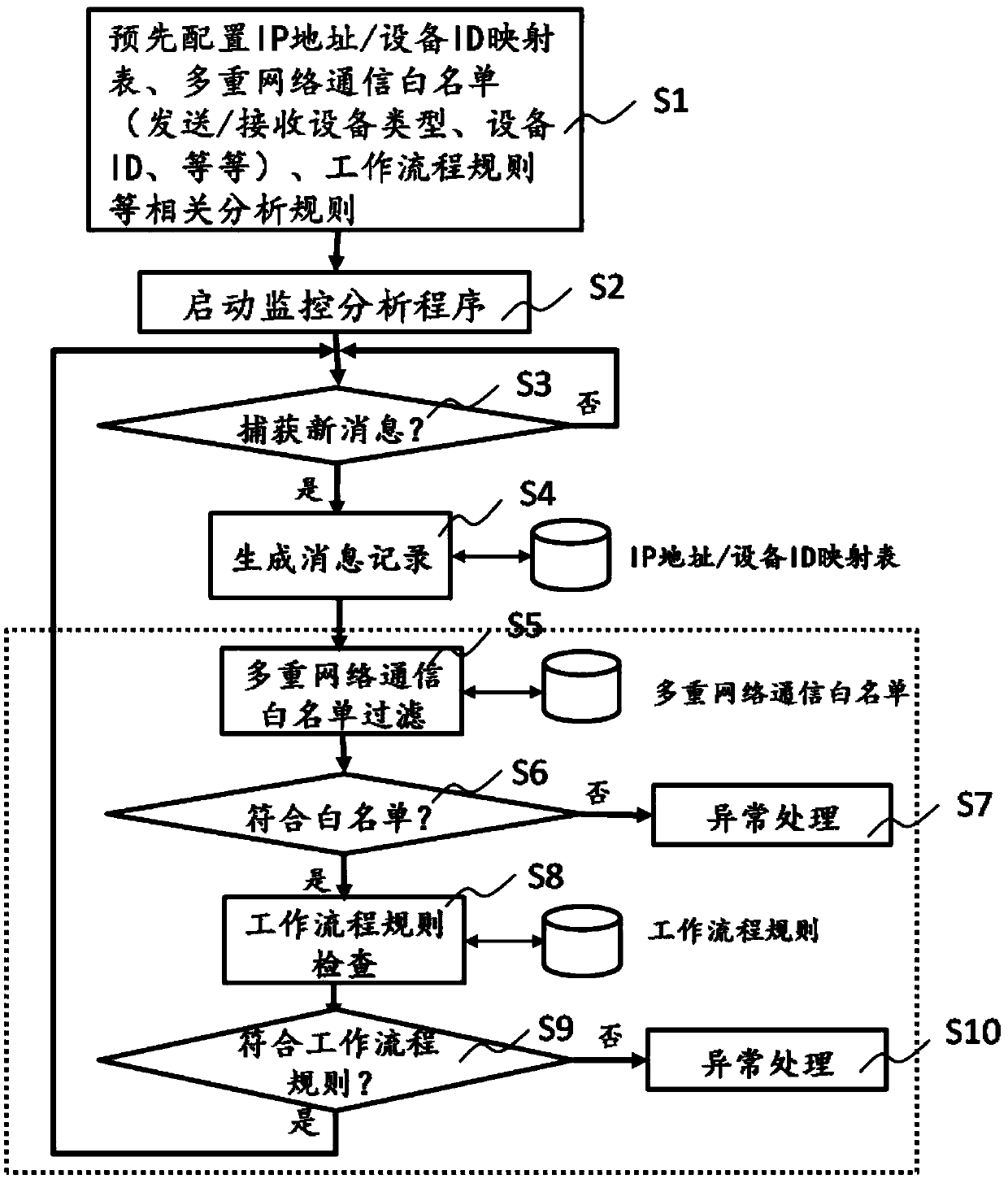
Monitoring analysis method of internet of things network layer communication
The invention relates to the field of the internet of things security, and especially relates to a monitoring analysis method of internet of things network layer communication. The monitoring analysismethod of the internet of things network layer communication comprises the following steps: capturing a network layer message on the internet of things through network layer communication monitoringanalysis equipment delayed in an internet of things network, generating a network message record; filtering the network message record by utilizing the preset multi-network communication white list, and performing workflow rule checking on the network message passing the multi-network communication white list filter; and performing abnormal processing the network message not passing the multi-network communication white list filter and the workflow rule checking. In the premise of not influencing the original work of the internet of things, the potential security threats from the internal andthe external are early troubleshooted, the behaviors of internal propagation of malicious software, malicious damage, data leakage and operating regulation violation are completely eradicated.
Owner:浙江汇安网络科技有限公司 +1
Electric sweeper anti-dismantle monitoring and control system based on Internet of Things
InactiveCN110045668AMonitor running statusReal-time monitoring of running statusProgramme controlComputer controlElectrical batteryTimer
The invention discloses an electric sweeper anti-dismantle monitoring and control system based on Internet of Things. The system comprises a DC contactor, an electric power input port, an electric power output port, a control board, a door control switch controller, a standby battery, an antenna, an infrared sensor, a contact type door control switch, a GPS position finder, a timer, a battery capacity detector, a wireless network module, a lower shell, an upper shell and a receiving terminal, one side of an inner wall of the bottom of the shell is provided with the DC contactor, and two corresponding sides of the lower shell are respectively provided with the electric power input port and the electric power output port. The system provided by the invention can monitor operation state of the sweeper, can acquire position information of the sweeper through GPS, can predict faults through a motion trail detection and journey statistic function, can be adaptive to a leasing mode of the sweeper well, has a dismantling alarming and power failure detection function, can monitor the box door control switch and can perform alarming when power supply is failed so as to prevent malicious damage to the sweeper monitoring control system.
Owner:常州昊云工控科技有限公司
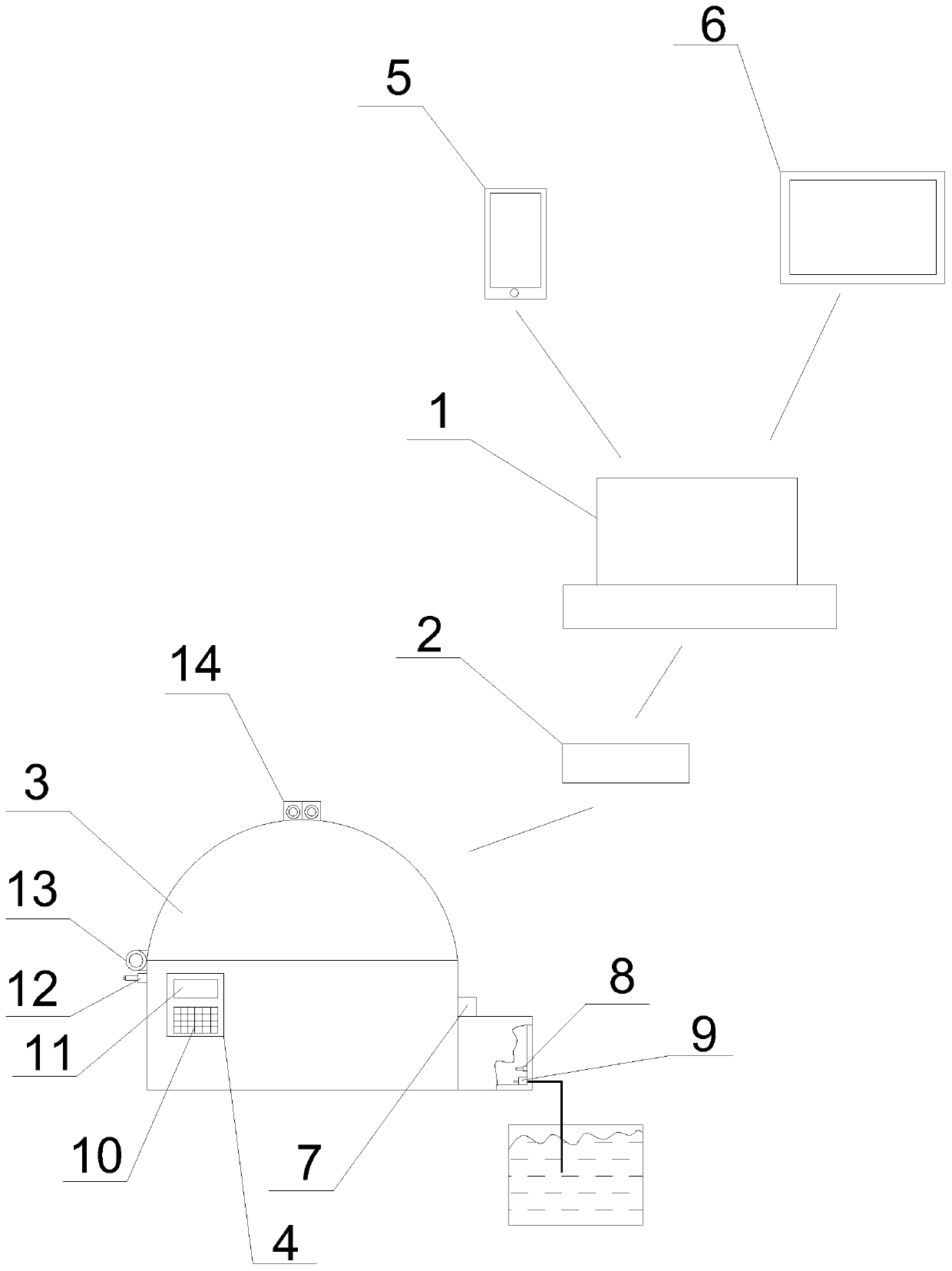
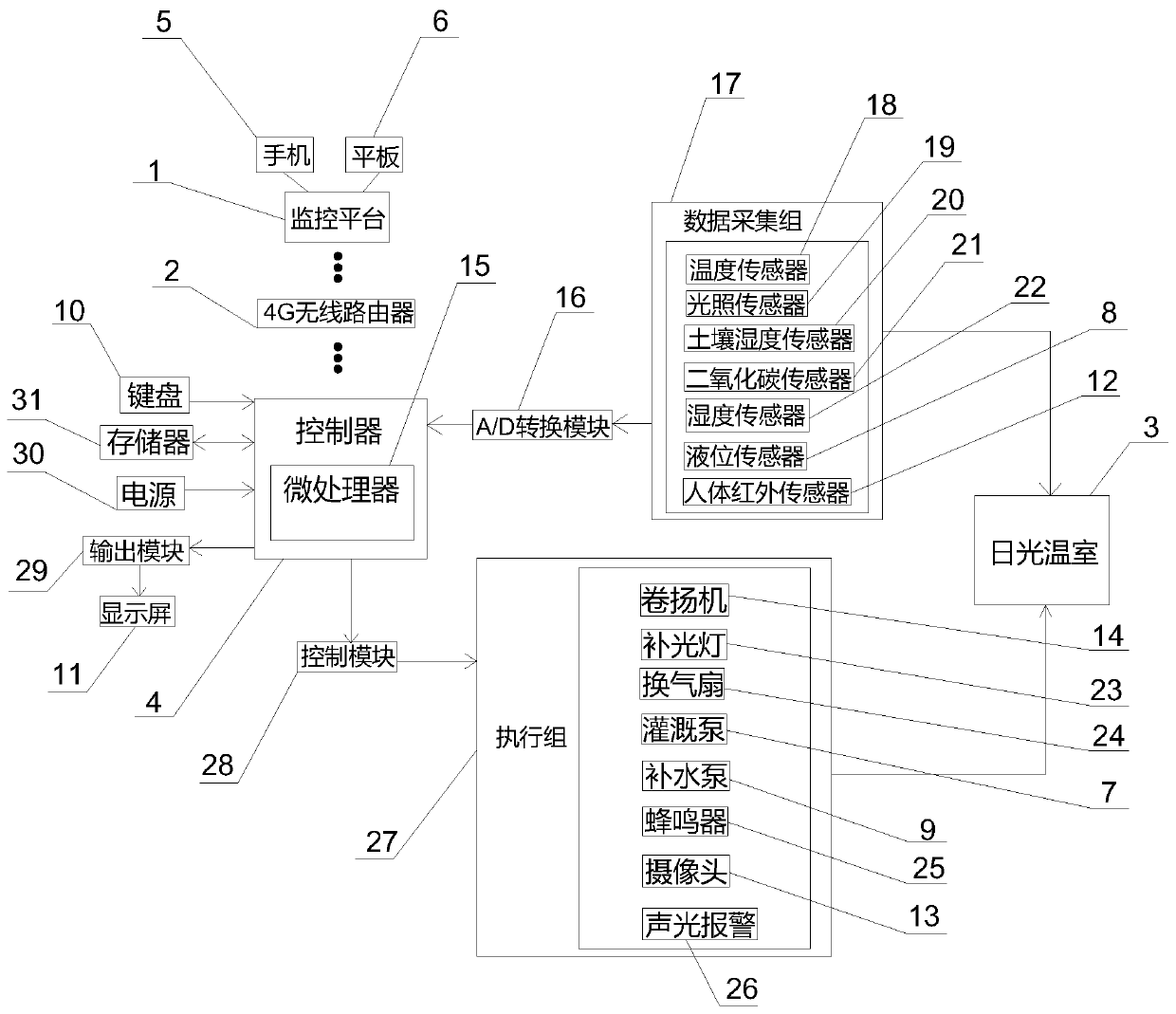
Intelligent control system for large-span solar greenhouse
InactiveCN110393110AImprove accuracyImprove timelinessProgramme controlComputer controlTablet computerData acquisition
The invention relates to the technical field of solar greenhouses, in particular to an intelligent control system for a large-span solar greenhouse. The system comprises a monitoring platform, a 4G wireless router, the solar greenhouse and a controller; one side of the solar greenhouse is provided with an irrigation water tank, the irrigation water tank is connected with a water pool, the solar greenhouse is cooperatively provided with the controller, the controller is internally provided with a microprocessor, the microprocessor is connected with the monitoring platform through the 4G wireless router, the monitoring platform is connected with a mobile phone and a tablet computer, and the microprocessor is connected with a data collection set through an A / D conversion module and connectedwith an execution set through a control module; the intelligent control over the solar greenhouse is achieved, the environment and irrigation water in the solar greenhouse are monitored and automatically supplemented, the outside of the greenhouse is monitored to avoid the artificial malicious damage to the greenhouse, the management efficiency of the solar greenhouse is improved, and the dependence on labor is reduced.
Owner:庆阳龙池菌业有限责任公司
Direct-embedded electronic equipment protection device and direct-embedded optical-cable communication access equipment
InactiveCN102595835AGuaranteed waterproof performanceAdd berth functionFibre mechanical structuresHermetically-sealed casingsHuman–machine interfaceWater leakage
The invention discloses a direct-embedded electronic equipment protection device and a direct-embedded optical-cable communication access equipment. The direct-embedded electronic equipment protection device comprises a protective housing of direct-embedded electronic equipment, and further comprises a shielding case arranged above the protective housing, wherein an air shielding space is formed between the upper part of the protective housing and the shielding case; the protective housing is provided with a sealing edge and / or a human-computer interface positioned in the air shielding space; and the shielding case is a sealed cover provided with an open cavity at the lower part. The protection device adopts a shielding case structure with the air shielding space and the multilayer sealing structure to take an IP68-grade sealing effect, and adopts a ventilated respirator to effectively ensure air circulation in the electronic equipment tank and prevent water in the tank from condensation. The problems of groundwater immersion, water leakage of the tank body and poor air circulation in the tank are effectively solved, and the functions of moisture protection, water resistance, mold prevention, salt haze prevention, dust prevention, burglary resistance, malicious damage avoidance and the like are served. The direct-embedded electronic equipment protection device can be widely used for waterproof protection of direct-embedded electronic equipment, such as direct-embedded communication equipment, direct-embedded monitoring equipment and the like.
Owner:CHINA MOBILE GRP GUANGDONG CO LTD
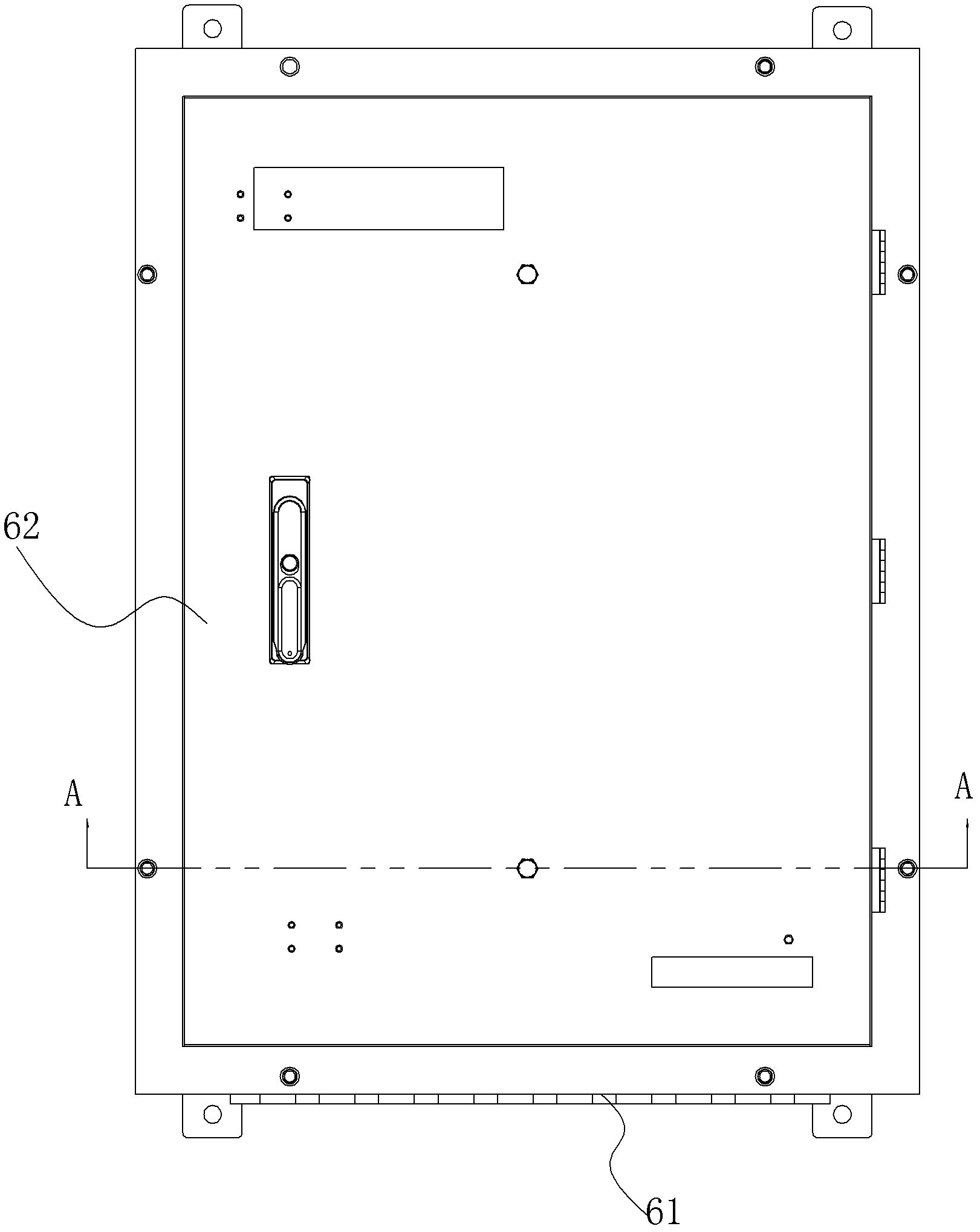
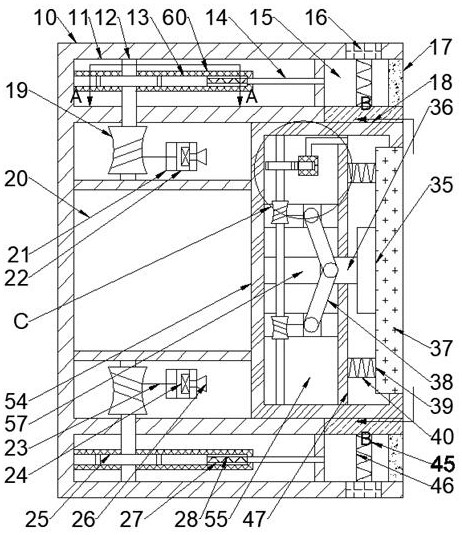
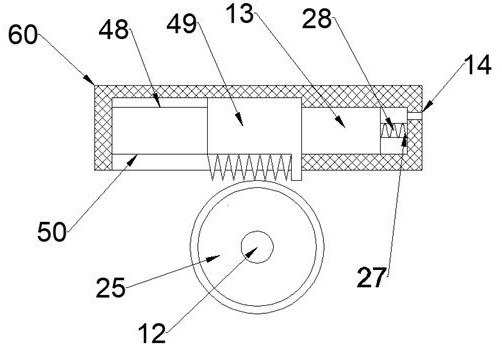
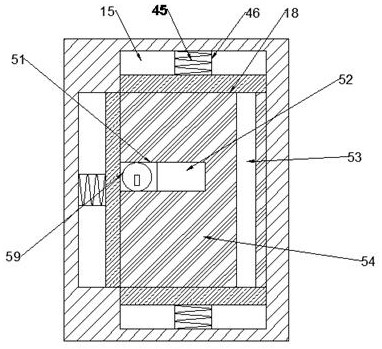
Power distribution cabinet capable of preventing malicious damage
InactiveCN112072496APrevent pryingAvoid destructionBuilding locksWing fastenersSuction forceWire wheel
The invention discloses a power distribution cabinet capable of preventing malicious damage, which comprises a power distribution cabinet and a sealing door in the power distribution cabinet, and is characterized in that an impact cavity is formed in a notch, first sliding grooves are symmetrically formed in the impact cavity up and down, fixing plates are slidably arranged on the first sliding grooves, and first springs are connected between the fixing plates and the left wall of the impact cavity; and an anti-collision cavity located on the left side of the impact cavity is formed in the sealing door, a wire wheel shaft is rotatably arranged between the upper wall and the lower wall of the anti-collision cavity, a first gear is fixedly arranged on the wire wheel shaft, and first wire wheels are fixedly arranged on the wire wheel shaft in an up-down symmetrical mode. According to the invention, the power distribution cabinet can be prevented from being maliciously opened by people. When a person wants to hit the power distribution cabinet open, an anti-shock force can be generated to prevent the power distribution cabinet from being opened, the anti-shock force can be changed according to the change of the impact force, meanwhile, the lock cylinder can be closed to prevent the lock cylinder from being damaged, and the power distribution cabinet can be prevented from being pried up and the suction force is adjusted according to the pried force to fix the closed door.
Owner:宁波变雪电子科技有限公司
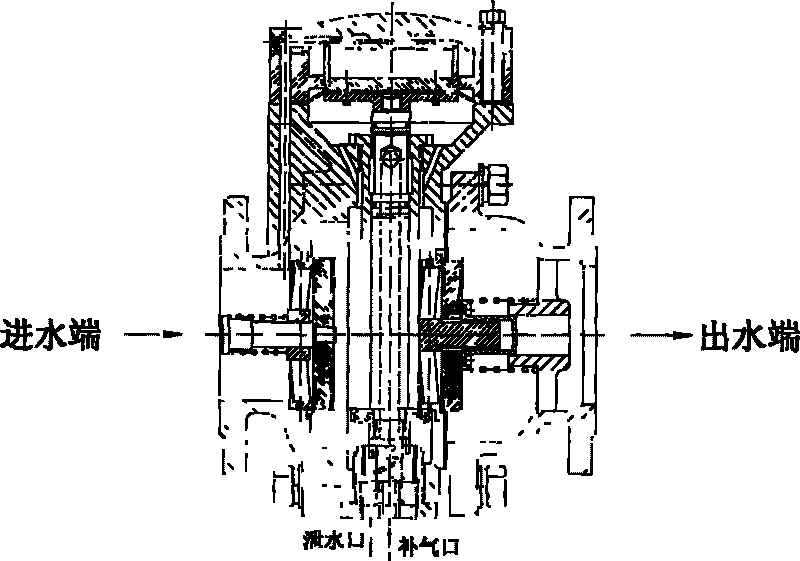
Water meter preventing back-flow of sewage
The invention provides a water meter combination preventing back-flow of sewage, the water meter combination preventing the back-flow of the sewage comprises a drain water non-return device, an outlet water non-return device and a water meter assembly, wherein a housing of the device is connected and communicated with the water meter assembly. An inlet of the water meter assembly comprises two non-return plates which are respectively matched with bases for realizing sealing and non-return effect, a control chamber is arranged at the lower part between the two non-return plates, a diaphragm is arranged in the control chamber, the diaphragm is flatly paved on the top end surface of a pressure plate, a lower cover is used for being covered and fastened on the housing of the drain water non-return device for forming a control cavity, and water of a water inlet of the drain water non-return device enters into the control cavity through a through hole on the housing without externally hanging a control accessory. The water meter combination has the benefits that the water meter combination preventing the back-flow of the sewage is a water meter device which strictly limits a pressure medium in a pipeline to flow in single direction, the structure is compact, and the mounting space is saved; the water meter combination can not only meet the metering requirement, but also meet the situation of guiding the back-flow medium or the medium in critical back-flow in the pipeline out of the pipe under any working condition and from air isolating, the mounting length is basically coincided with a home water meter, and the water meter combination has good interchangeability with the water meter which is currently used in families at the present stage, thereby being not afraid of malicious damage, ensuring the safety of water supply and preventing the pollution.
Owner:刘永 +1
Old clothes recycling bin
InactiveCN109051440AStop getting wetReduce frictionWaste collection and transferRefuse receptaclesElectricityEngineering
The invention discloses an old clothes recycling bin, and belongs to the field of municipal equipment. The old clothes recycling bin is composed of a box body, a human body pyroelectric sensor, a crawler, a control device, a solar panel, a bracket, a rain shielding plate, a pickup door, a box, a camera, a roller, a rotating shaft, a reduction gear, a speed sensor, a moisture-proof layer and a weight sensor. The old clothes recycling bin adopts a double-shaft crawler conveyor to effectively avoid the occurrence of malicious damage and theft; when the old clothes recycling bin encounters strongwind, the is driven by the wind force to rotate rapidly, and the disc type reduction gear is matched with the speed sensor to brake the rotating shaft rapidly; the human body pyroelectric sensor is matched with the camera to collect the information of a donor, and the presence of the camera provides the possibility to trace a destroyer; and the use of solar power does not impose additional burdenon a mains system.
Owner:张烨
Electronic payment system based on SET protocol
Electronic commerce is the generic terms of all activities that people use information technology to efficiently work on commodity exchange with low cost according to the appropriate commercial standard in the current society where economy and technique quickly develop. A series of safety hazards of malicious damage, counterfeit information, tampered information, information filch and the like happen generally in application and development of the electronic commerce. Thus, an information encryption technique becomes the important safety measure taken by the electronic commerce. Trading parties of the electronic commerce can use the information encryption technique in all stages of information exchange according self requirements.
Owner:天津云游四海科技发展有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com