Encryption and decryption method based on RSA algorithm
An RSA algorithm, encryption and decryption technology, applied in the field of information security, which can solve the problems of inability to guarantee security, leakage of authorization information, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific example
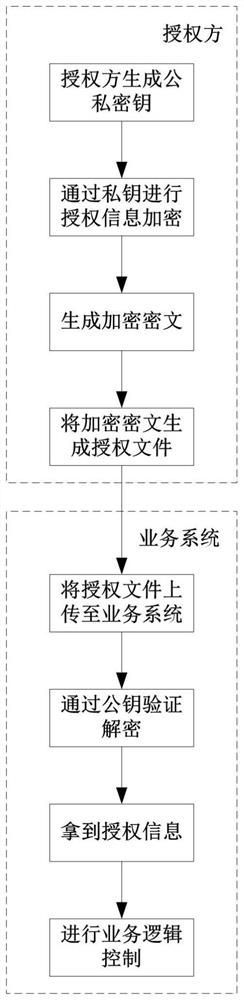
[0033] A specific example is as follows: A business system is deployed to a customer site and requires authorization from the manufacturer. The manufacturer first generates an RSA public-private key pair, puts the public key into the business system, and stores the private key in the manufacturer's own hands. After the business system is deployed, authorization is required for the business system to run normally. At this time, the manufacturer signs and encrypts the authorization information according to its own private key, writes the ciphertext to the authorization file, and sends the authorization file to the customer. After the customer gets the authorization file, upload the authorization file to the business system, and the business system gets the ciphertext in the authorization file, and performs verification and decryption according to the public key in the business system to obtain the authorization information. Afterwards, the business system finds that it is in co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com