Document data security verification method based on block chain
A verification method and data security technology, which is applied to secure communication devices, user identity/authority verification, and key distribution, can solve problems affecting the accuracy of verification results, and achieve the effects of enhancing non-tampering, ensuring accuracy, and convenient operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
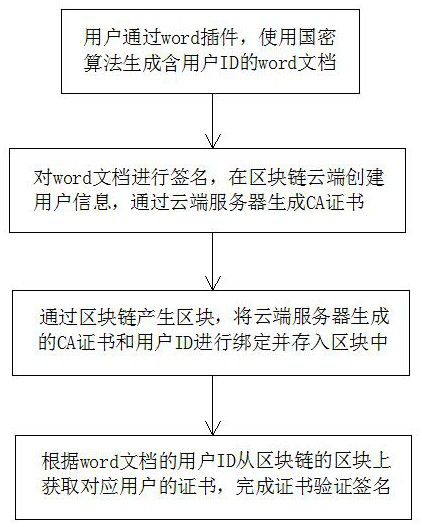
[0040] see figure 1 , a blockchain-based document data security verification method, comprising the following steps:
[0041] a. The user uses the word plug-in to generate a word document containing the user ID using the national secret algorithm. The national secret algorithm includes the SM2 algorithm and the SM3 algorithm;
[0042] b. Sign the word document, create user information in the blockchain cloud, and generate a CA certificate through the cloud server;
[0043] c. Generate blocks through the blockchain, bind the CA certificate and user ID generated by the cloud server and store them in the block;
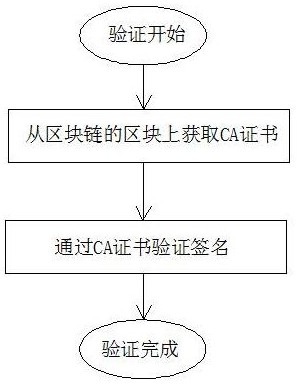
[0044] d. Obtain the certificate of the corresponding user from the block of the blockchain according to the user ID of the word document, and complete the certificate verification and signature.
[0045] This embodiment is the most basic implementation, with distributed features, each user can independently sign and verify the electronic document, ensure the accuracy ...
Embodiment 2
[0047] see figure 1 , a blockchain-based document data security verification method, comprising the following steps:
[0048] a. The user uses the word plug-in to generate a word document containing the user ID using the national secret algorithm. The national secret algorithm includes the SM2 algorithm and the SM3 algorithm;
[0049]b. Sign the word document, create user information in the blockchain cloud, and generate a CA certificate through the cloud server;
[0050] c. Generate blocks through the blockchain, bind the CA certificate and user ID generated by the cloud server and store them in the block;
[0051] d. Obtain the certificate of the corresponding user from the block of the blockchain according to the user ID of the word document, and complete the certificate verification and signature.
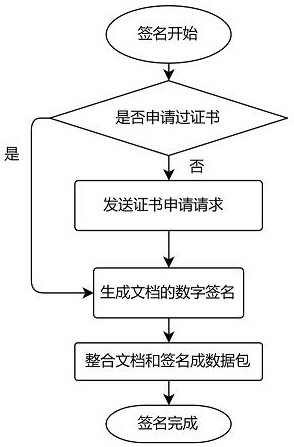
[0052] In the step a, the word plug-in is used to integrate signature, signature verification and user application for a certificate.
[0053] The user's application for a c...
Embodiment 3
[0058] see figure 1 , a blockchain-based document data security verification method, comprising the following steps:
[0059] a. Through the word plug-in, the user uses the national secret algorithm to generate a word document containing the user ID. The national secret algorithm includes the SM2 algorithm and the SM3 algorithm;
[0060] b. Sign the word document, create user information in the blockchain cloud, and generate a CA certificate through the cloud server;
[0061] c. Generate blocks through the blockchain, bind the CA certificate and user ID generated by the cloud server and store them in the block;
[0062] d. Obtain the certificate of the corresponding user from the block of the blockchain according to the user ID of the word document, and complete the certificate verification and signature.
[0063] In the step a, the word plug-in is used to integrate signature, signature verification and user application for a certificate.
[0064] The user's application for...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com