Data processing method and device based on block chain
A data processing and blockchain technology, applied in the blockchain field, can solve problems such as complex network environment, security risks, malicious attacks or tampering of user data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0056] See figure 2 , figure 2 It is a schematic flowchart of the blockchain-based data processing method provided by the embodiment of this application. The method provided in the embodiment of this application may include the following steps S201 to S203:
[0057] S201. Receive an information verification request sent by a first user.
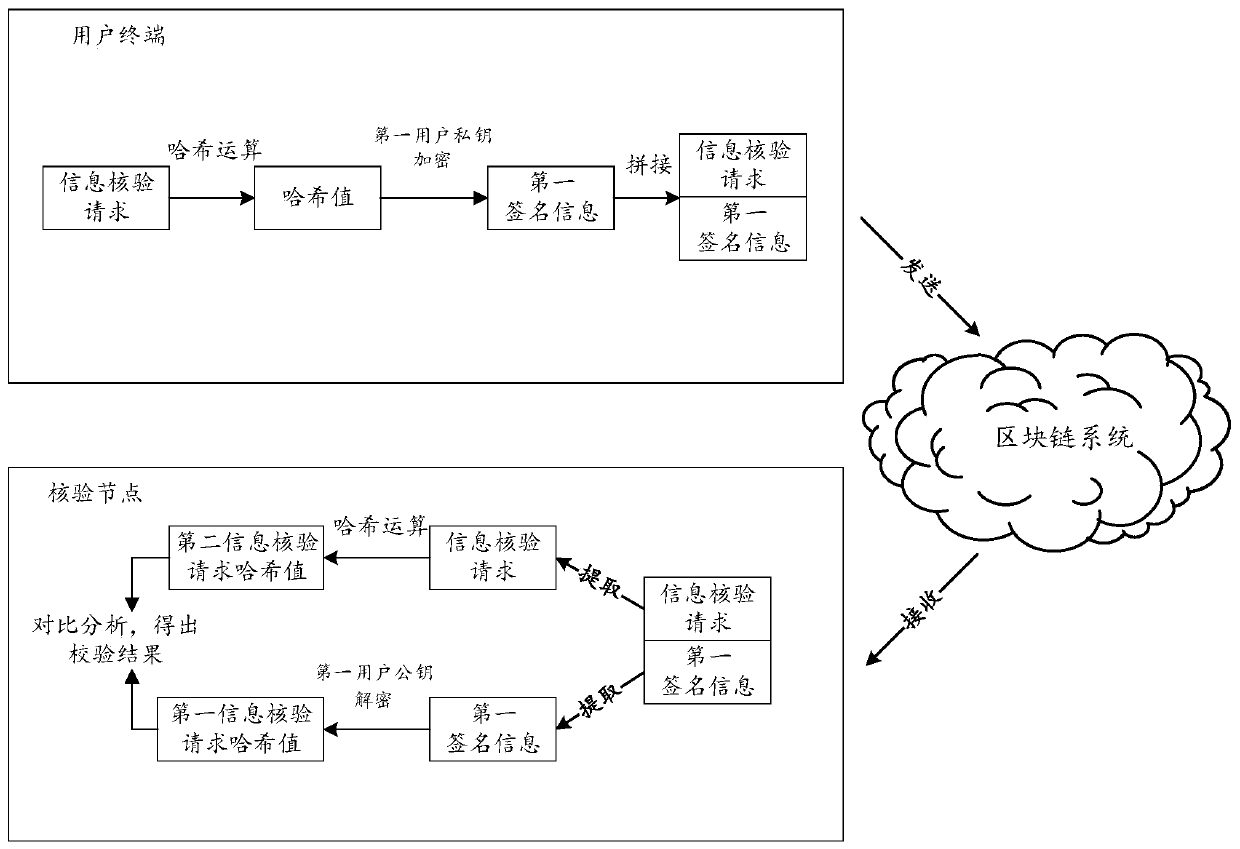
[0058] In some feasible implementations, the verification node can obtain the first signature information of the information verification request carried by the first user carried in the information verification request by receiving the information verification request sent / submitted by the first user through the user terminal, as well as the information verification request. The request includes the asset-related event, the event type of the asset-related event, the first user ID corresponding to the first user, and the first user's household registration ID. Wherein, the first user identification corresponding to the first user may be ...
Embodiment 2
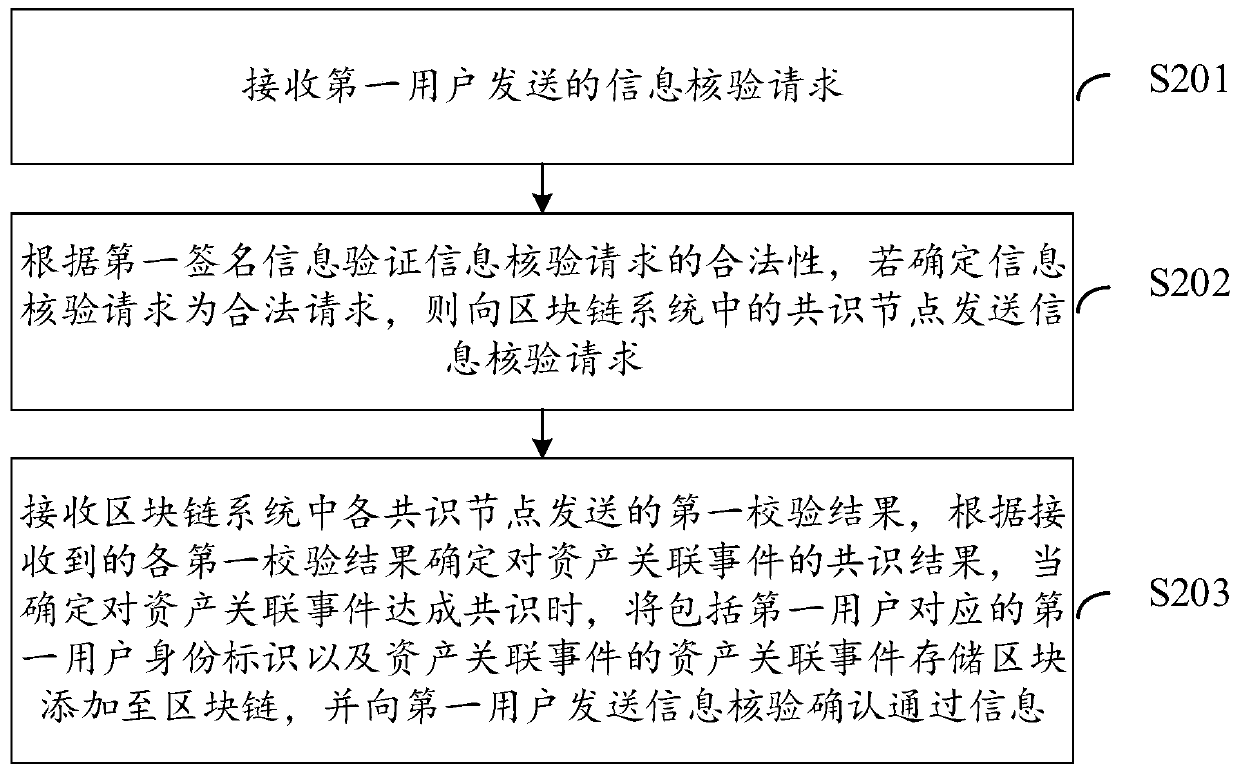
[0071] See image 3 , image 3 It is another schematic flowchart of the blockchain-based data processing method provided by the embodiment of this application. The method provided in the embodiment of the present application can be described by implementing the following steps S301 to S304:
[0072] S301. Receive an information verification request sent by a first user.
[0073] S302. Verify the legitimacy of the information verification request according to the first signature information, and send the information verification request to the consensus nodes in the blockchain system if it is determined that the information verification request is legal.
[0074] S303. Receive the first verification result sent by each consensus node in the blockchain system, and determine the consensus result on the asset-related event according to the received first verification results. When it is determined that a consensus is reached on the asset-related event, it will include The first...
Embodiment 3
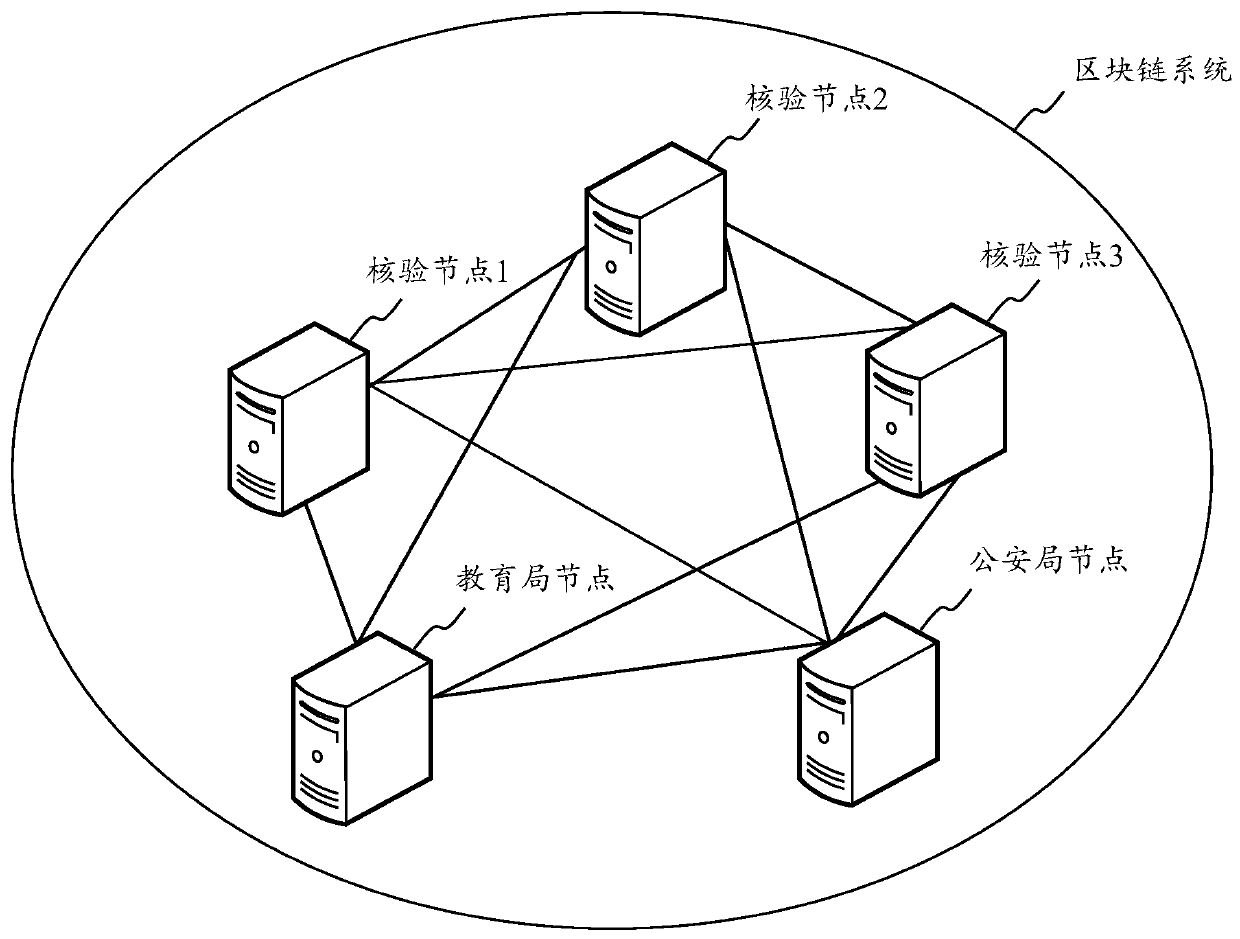
[0080] Further, for ease of understanding, the embodiment of the present application is described by taking the verification node as a tax bureau node, and the information verification request as an individual tax deduction declaration request of the first user as an example.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com