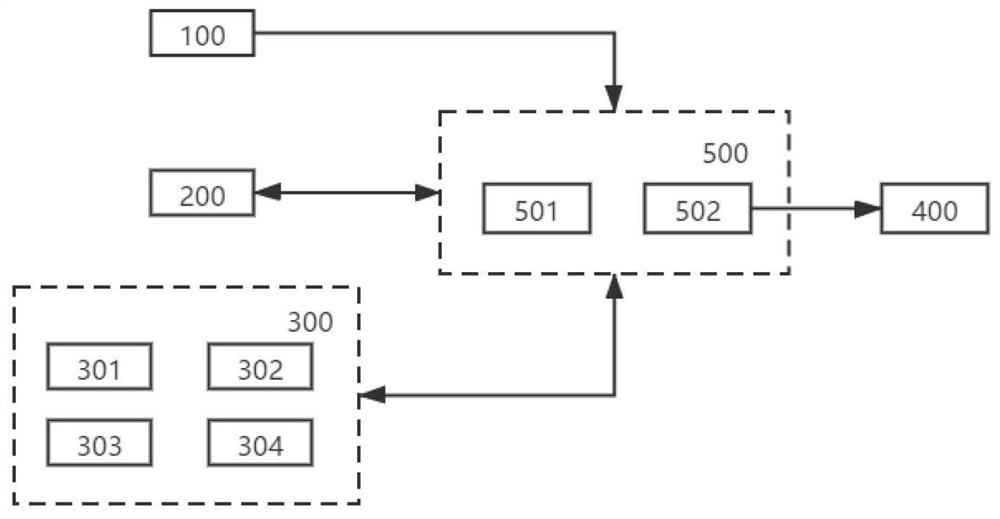
Patents
Literature
40results about How to "Achieve concurrency" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Block chain system-based digital asset transaction method and block chain system
InactiveCN107392608AAchieve concurrencyImprove securityPayment protocolsSecuring communicationFinancial transactionTree shaped
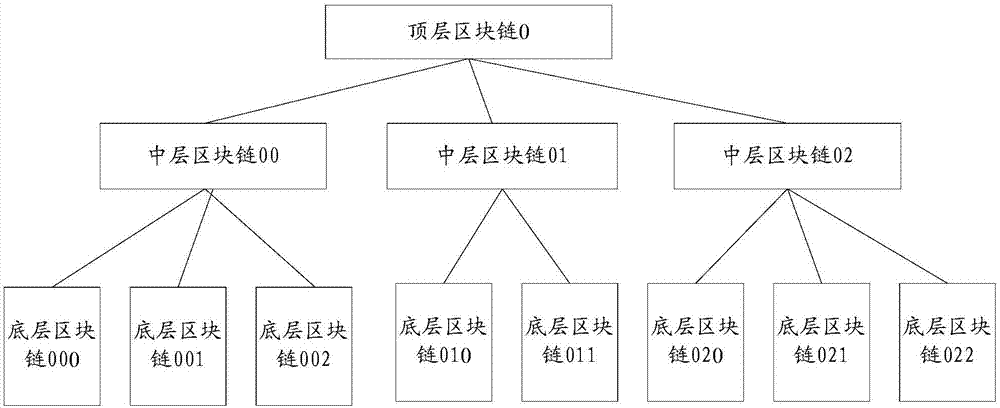
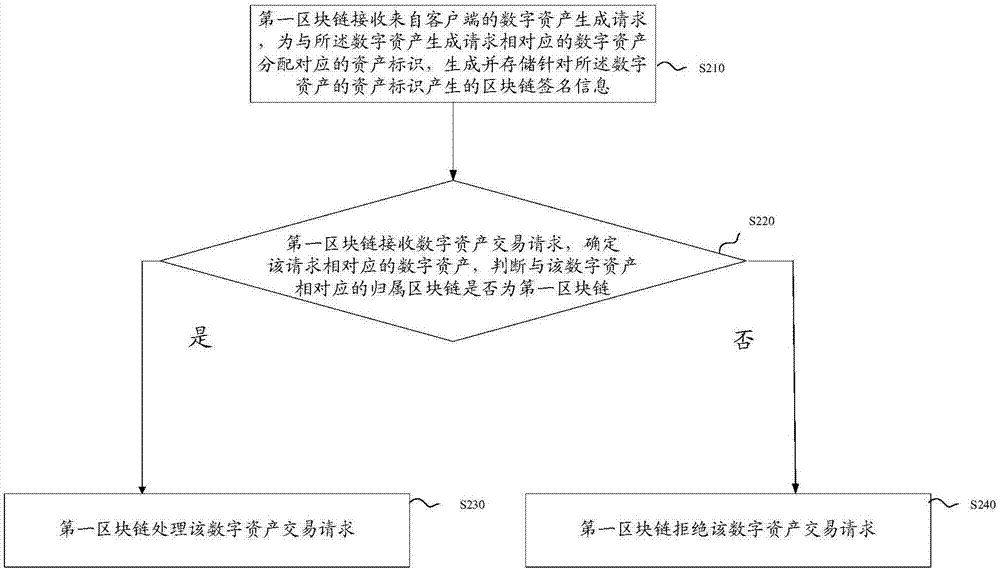
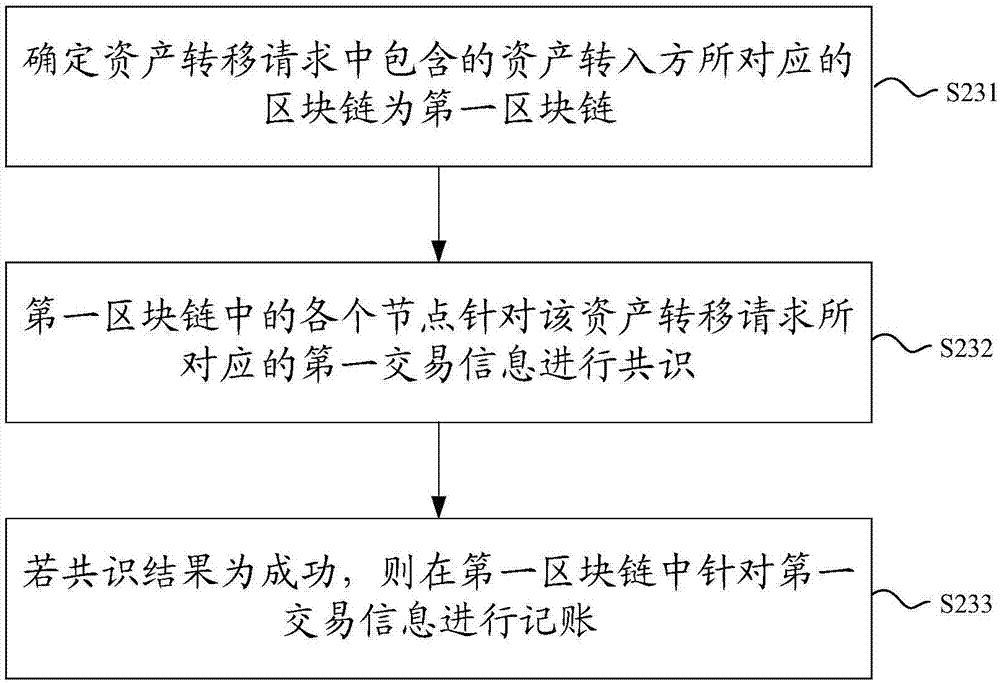
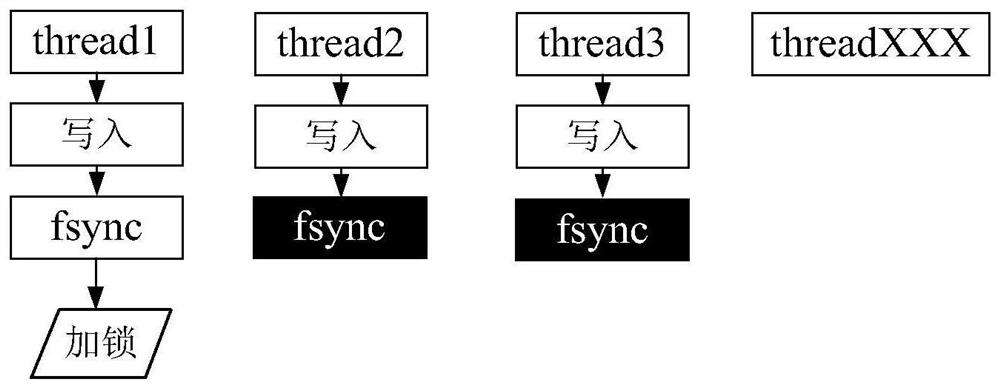
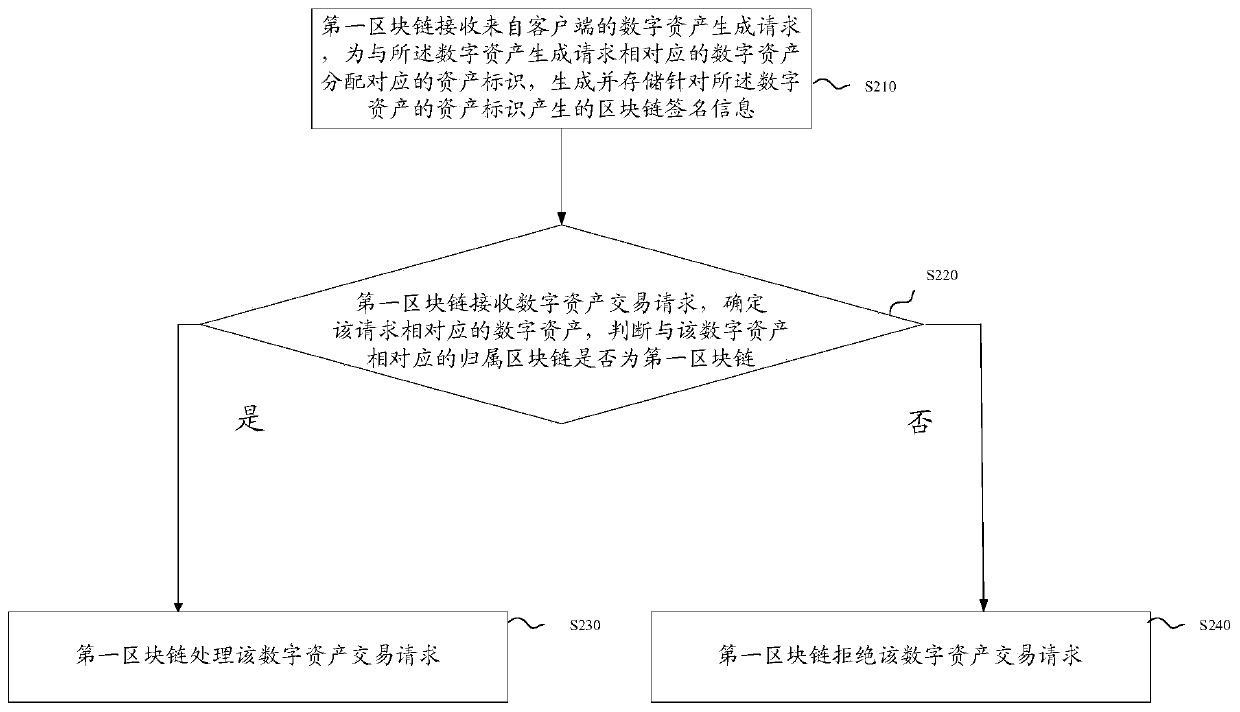
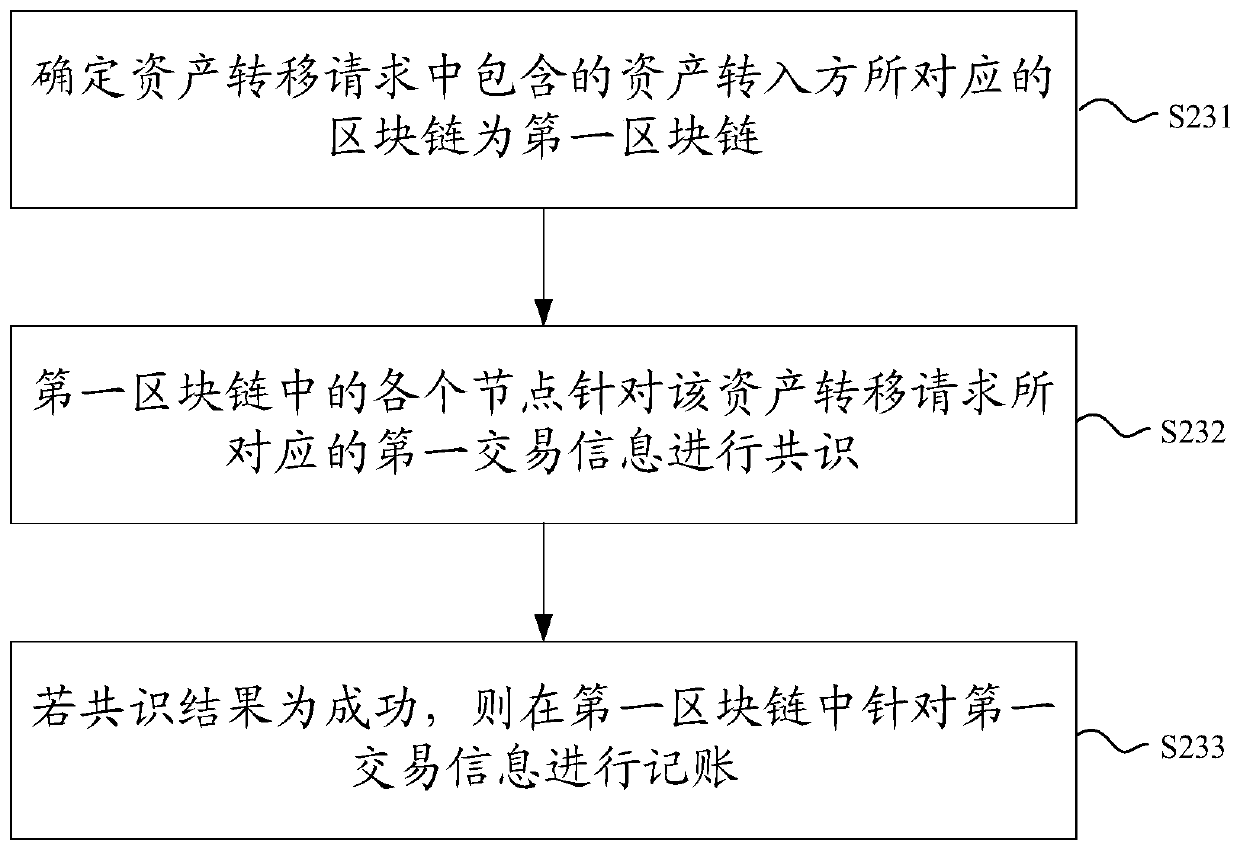
The invention discloses a block chain system-based digital asset transaction method and a block chain system. The block chain system is a tree-shaped distributed block chain system including a plurality of levels of block chains. The method comprises the following steps that: a first block chain receives a digital asset transaction request from a client, and determines digital assets corresponding to the digital asset transaction request; whether an attribution block chain corresponding to the digital assets is a first block chain is judged; if the attribution block chain corresponding to the digital assets is the first block chain, the first block chain processes the digital asset transaction request; and if the attribution block chain corresponding to the digital assets is not the first block chain, the first block chain rejects the digital asset transaction request, wherein the attribution block chain corresponding to the digital assets is a block chain that generates the digital assets. The method is especially suitable for the transactions of one-time one-use digital assets, wherein the digital assets can be only used once; and moreover, the method can also realize a cross-chain transactions between the digital assets, and the digital assets are corresponding to different attribution block chains before and after the cross-chain transactions are executed, and therefore, the security of the assets can be improved.
Owner:北京博晨技术有限公司
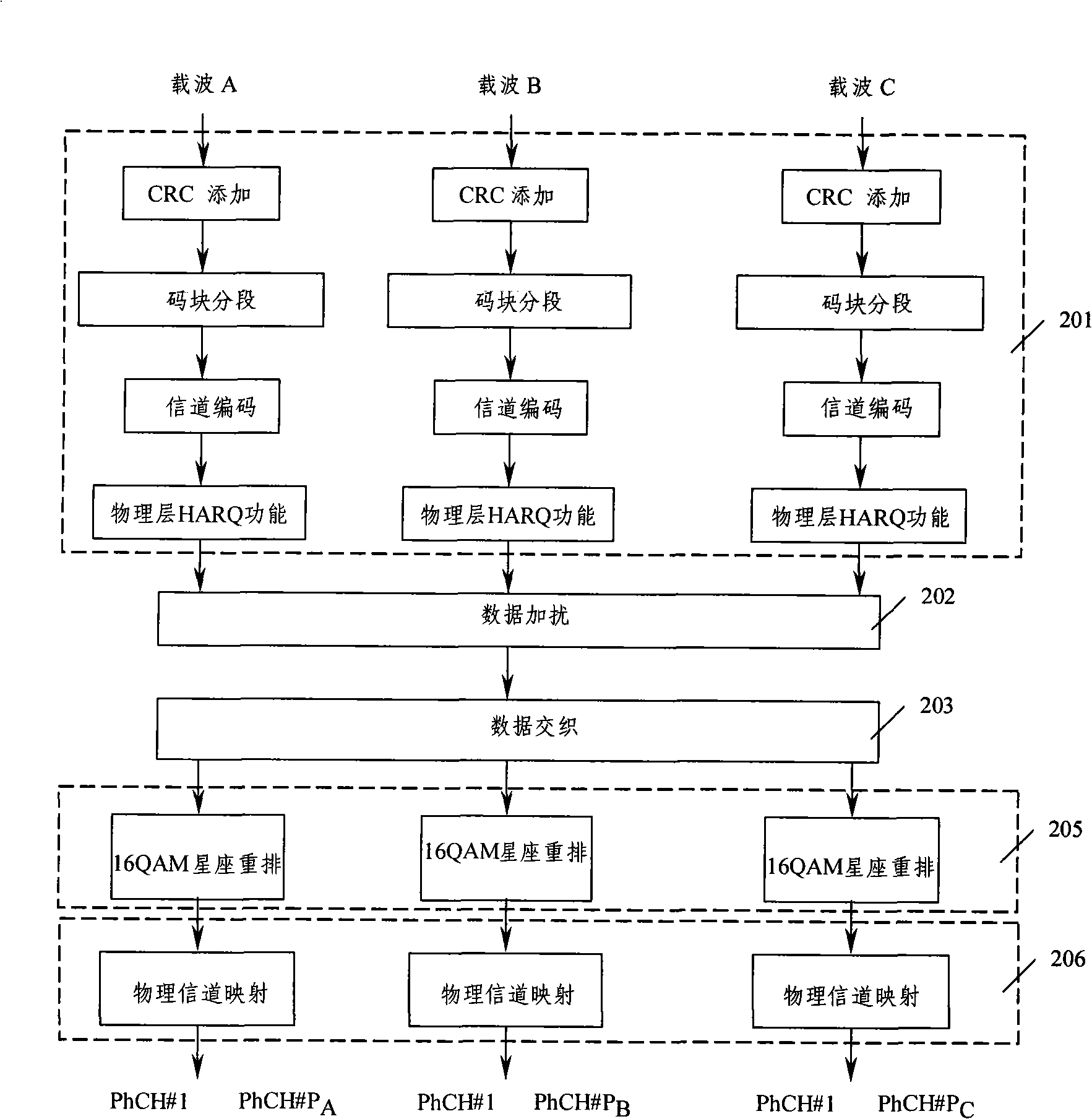
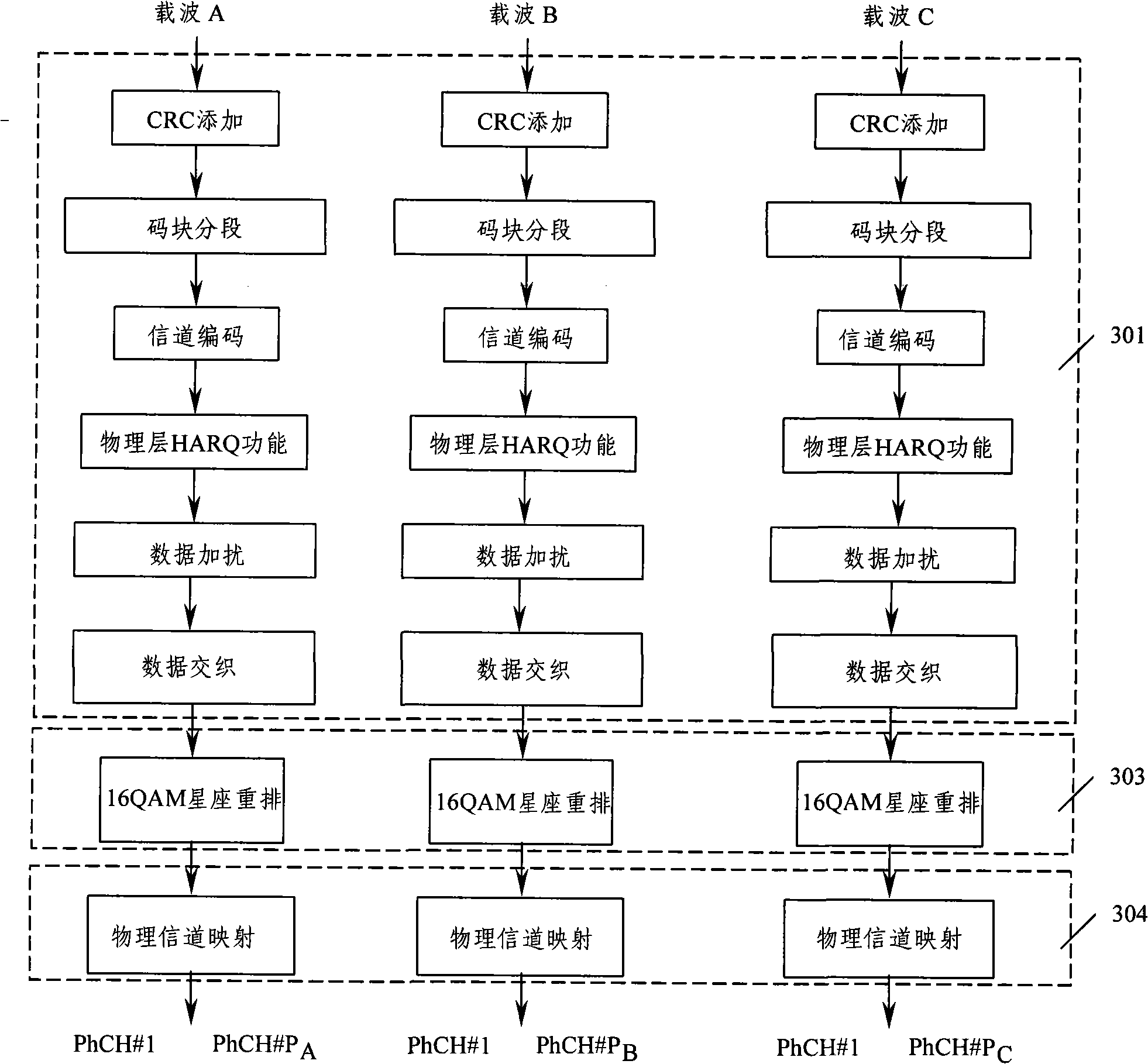
Encoding method and apparatus for multi-carrier time division duplex system service transmission channel
InactiveCN101359972AAchieve concurrencyEasy to achieve concurrencyError prevention/detection by using return channelDuplex systemConstellation
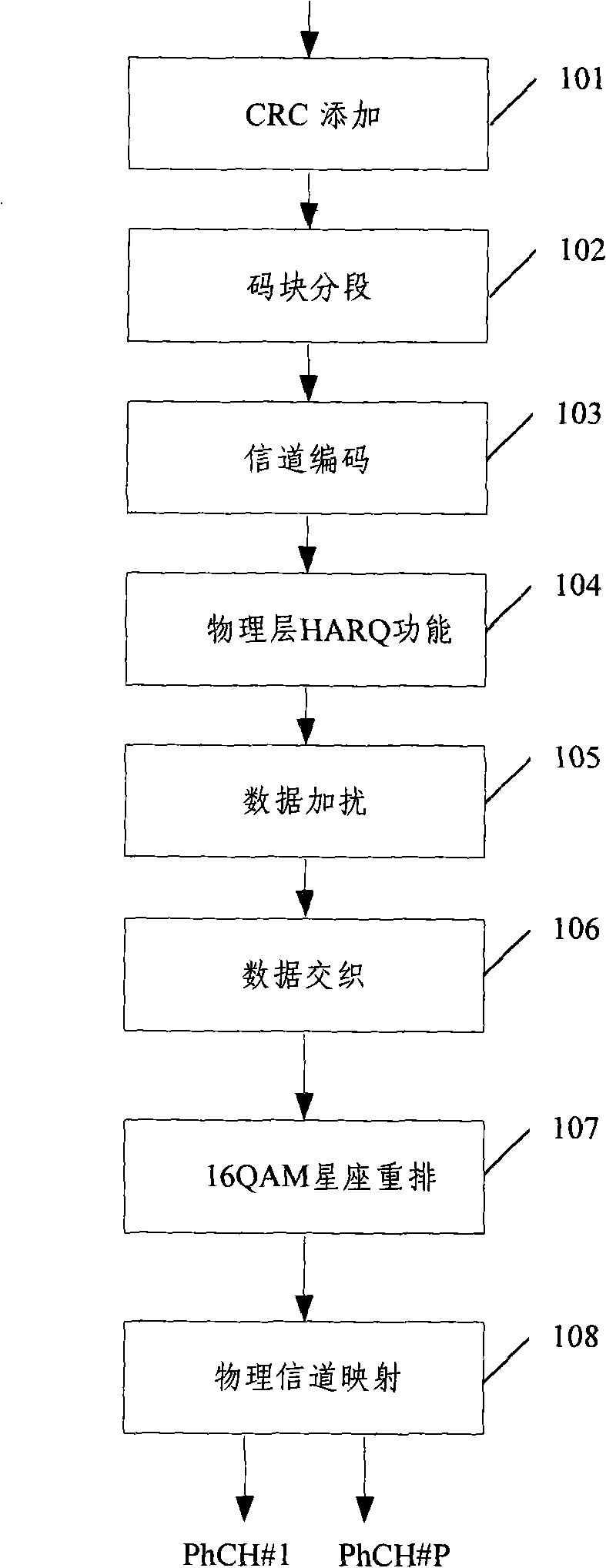
The invention discloses three realization proposals of an encoding method of a multicarrier TDD system business transmission channel, wherein, one of the realization proposals comprises the following steps: sending end equipment divides data to be sent into N routes and respectively carries out CRC addition, code block segmentation, channel encoding and physical layer HARQ functional module processing; the N routes of processed data are combined into one route of data in sequence, and data scrambling processing is carried out uniformly; processed data is carried out with data intertwined processing; when a high-order modulation mode is adopted, the N routes of the processed data are carried out with M Yuan constellation rearrangement; the N routes of the processed data are respectively carried out with physical channel mapping, and at last the N routes of the data are respectively modulated to N carriers to be sent to receiving end equipment. The invention also discloses three realization proposals of an encoding or / and decoding device of the multicarrier TDD system business transmission channel, when the method and the device are adopted, uplink data rate of the TDD system can be greatly promoted.
Owner:CHINA ACAD OF TELECOMM TECH
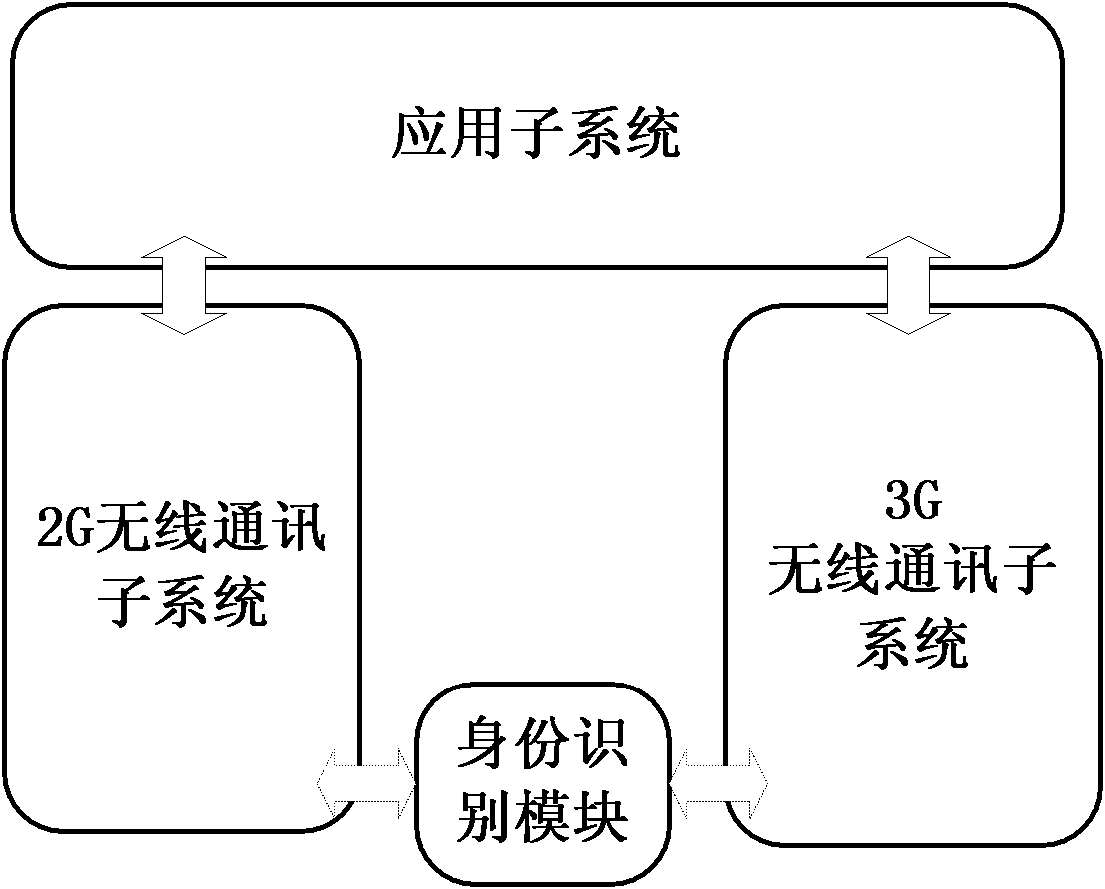
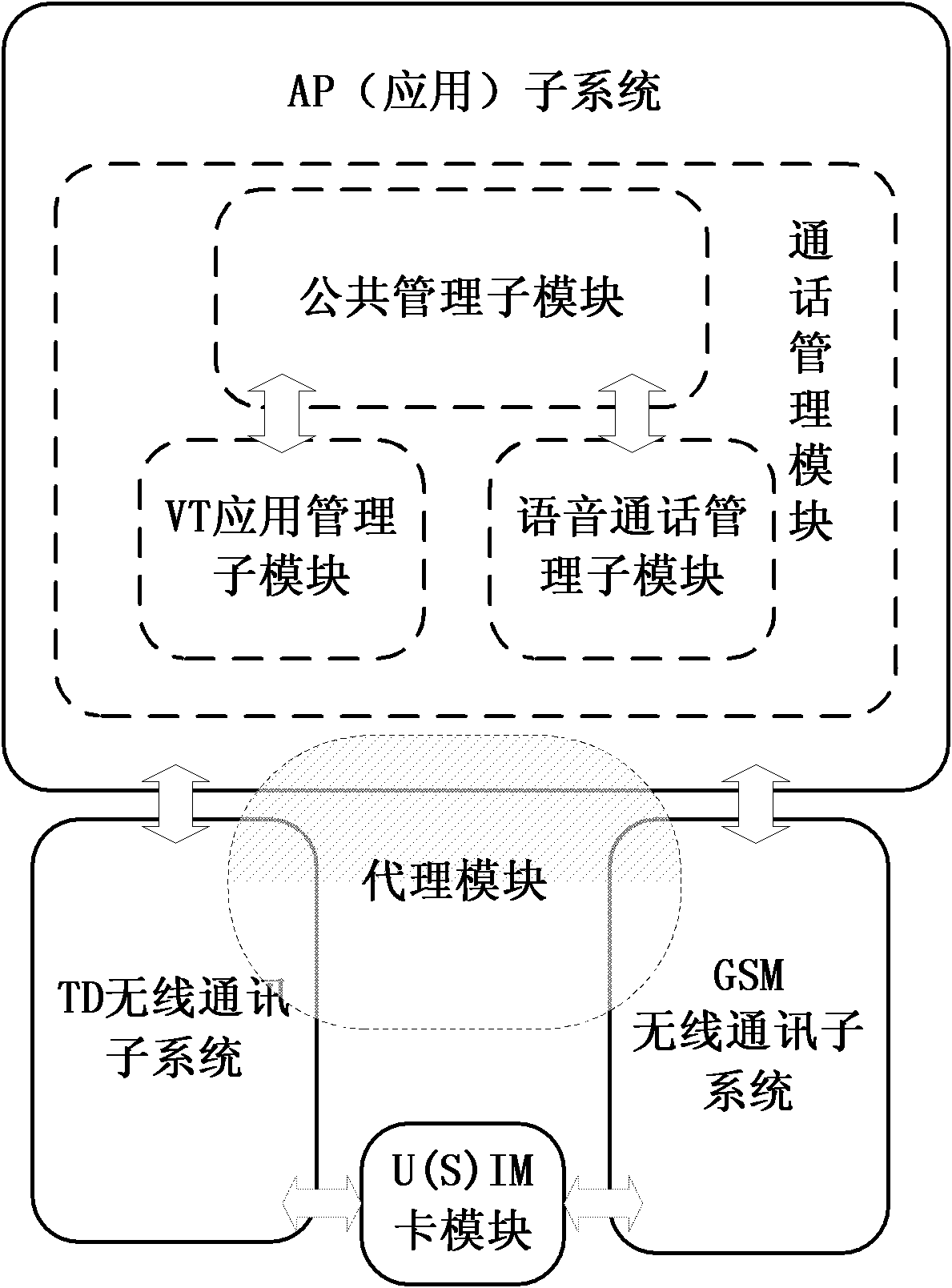
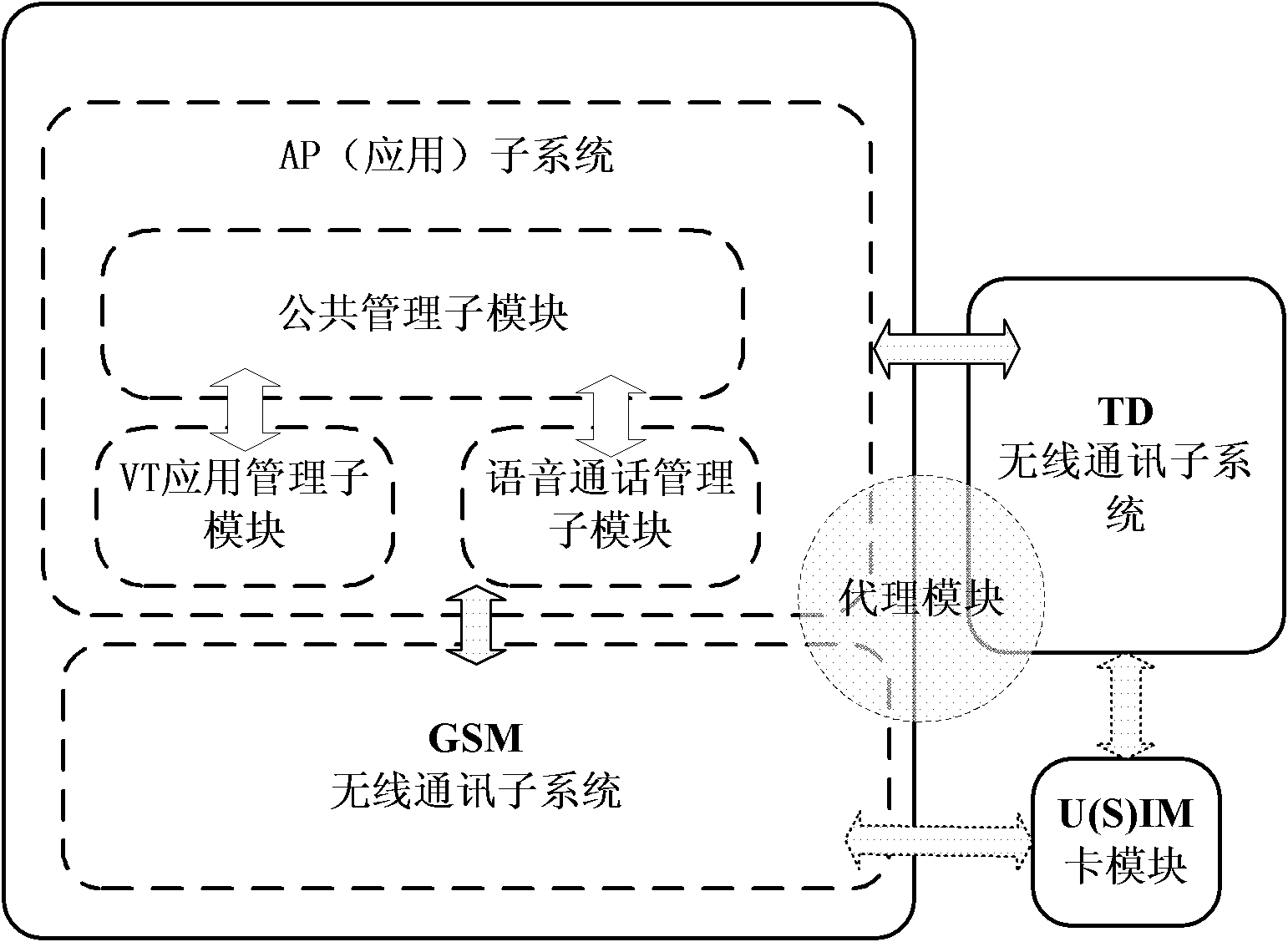
Telephone service executing method and device of double-network double-standby terminal
InactiveCN102083030AAchieve concurrencyEasy to useSpecial service for subscribersCommmunication supplementary servicesDouble networkDual network
The invention discloses a telephone service executing method and a telephone service executing device of a double-network double-standby terminal. The double-network double-standby terminal comprises an application subsystem, a 3rd generation (3G) wireless communication subsystem, a 2nd generation (2G) wireless communication subsystem and an identification module, wherein an identification card is inserted into the identification module; when a user of the double-network double-standby terminal uses a voice telephone service, the application subsystem selects the 2G wireless communication subsystem, the 2G wireless communication subsystem uses information in the identification card and the voice telephone service is executed through a 2G network; and when the user of the double-network double-standby terminal uses a video telephone service, the application subsystem selects the 3G wireless communication subsystem, the 3G wireless communication subsystem uses information in the identification card and the video telephone service is executed through the 3G network. Due to the adoption of the method and the device, concurrence of a voice telephone and a video telephone can be realized under a single-card single-number double-network double-standby condition.
Owner:ZTE CORP
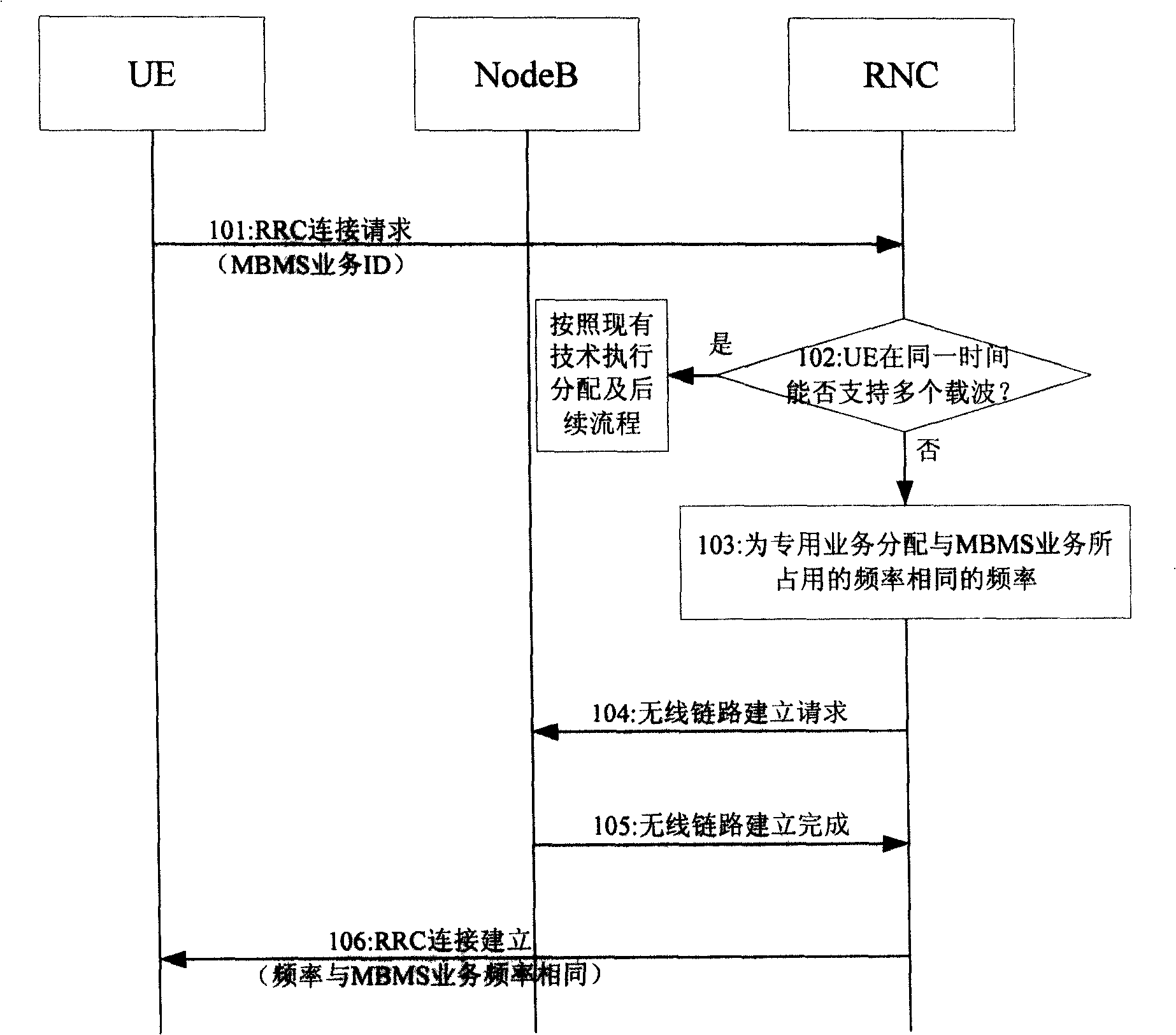
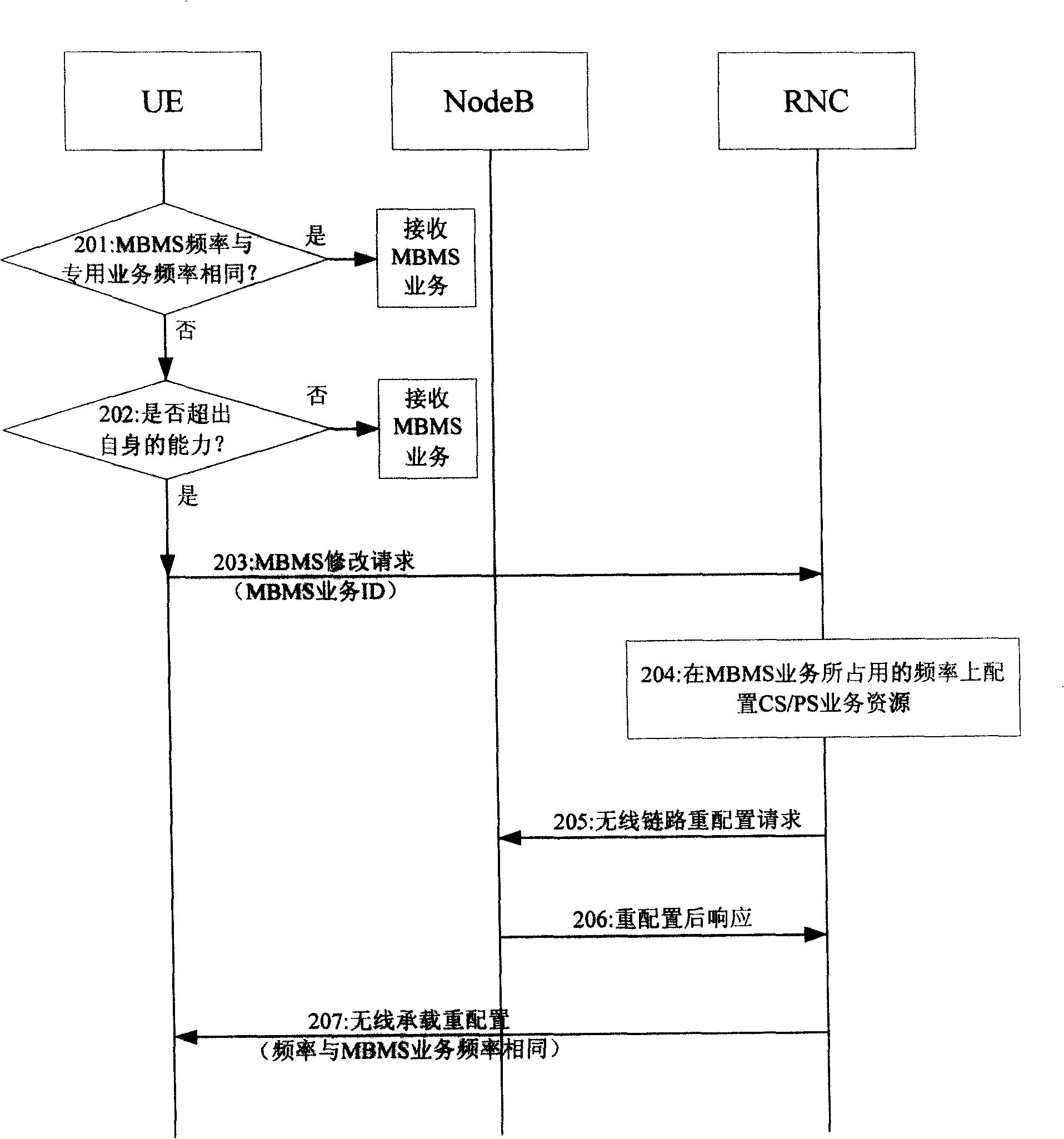
Method and system for realizing parallel transmission of broadcast/multicasting service and special service
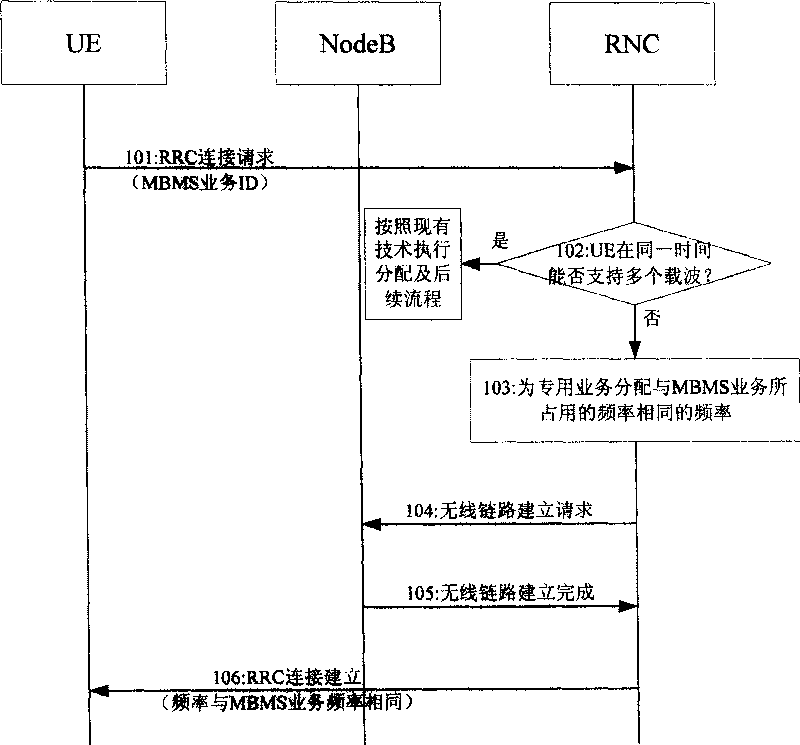
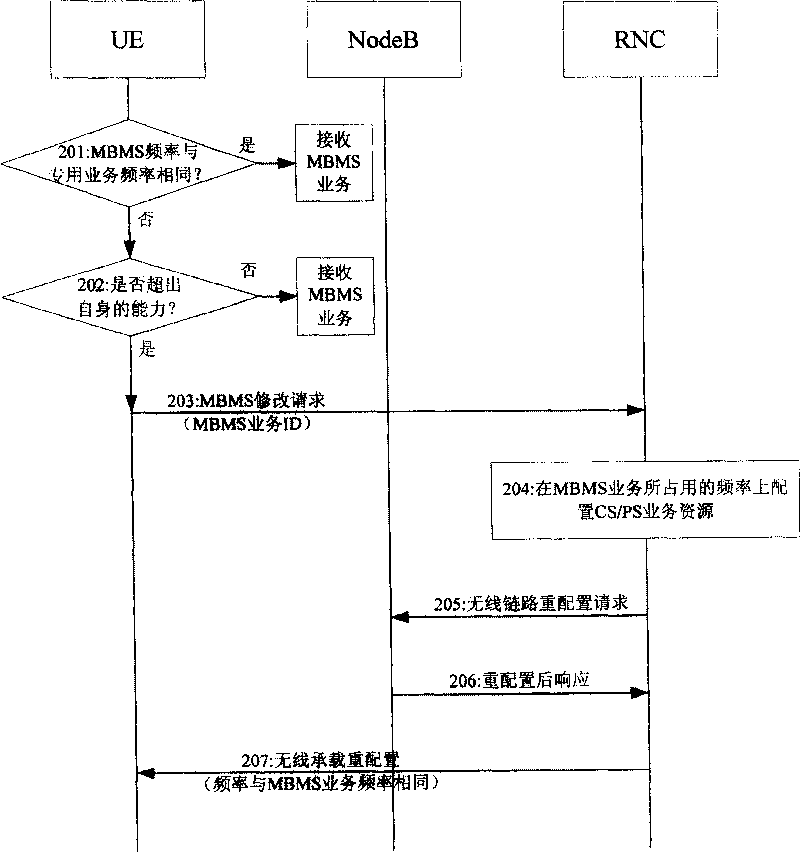
InactiveCN101257374AAchieve concurrencyRadio/inductive link selection arrangementsDuplex signal operationService developmentRadio Network Controller
The invention provides a method for realizing the concurrent of broadcast / multicast service. The method comprises: the user equipment (UE) transmits the frequency ID indicating the broadcast / multicast service to the radio network controller (RNC); RNC obtains the frequency of the broadcast / multicast service based on the ID and configures the specific service to the frequency resource of the broadcast / multicast. The invention also provides a system realizing the broadcast / multicast service and the specific service development, comprising UE and RNC. Because UE in the inventive embodiment transmits the ID indicating the operating frequency of the broadcast / multicast service to RNC at the network, RNC acquires the frequency of the broadcast / multicast service based on the ID and configures the specific service to the frequency resource of the broadcast / multicast service so as to lead UE to receive broadcast / multicast service and specific service at the same frequency and realize the development of the broadcast / multicast service and the specific service.
Owner:TD TECH COMM TECH LTD
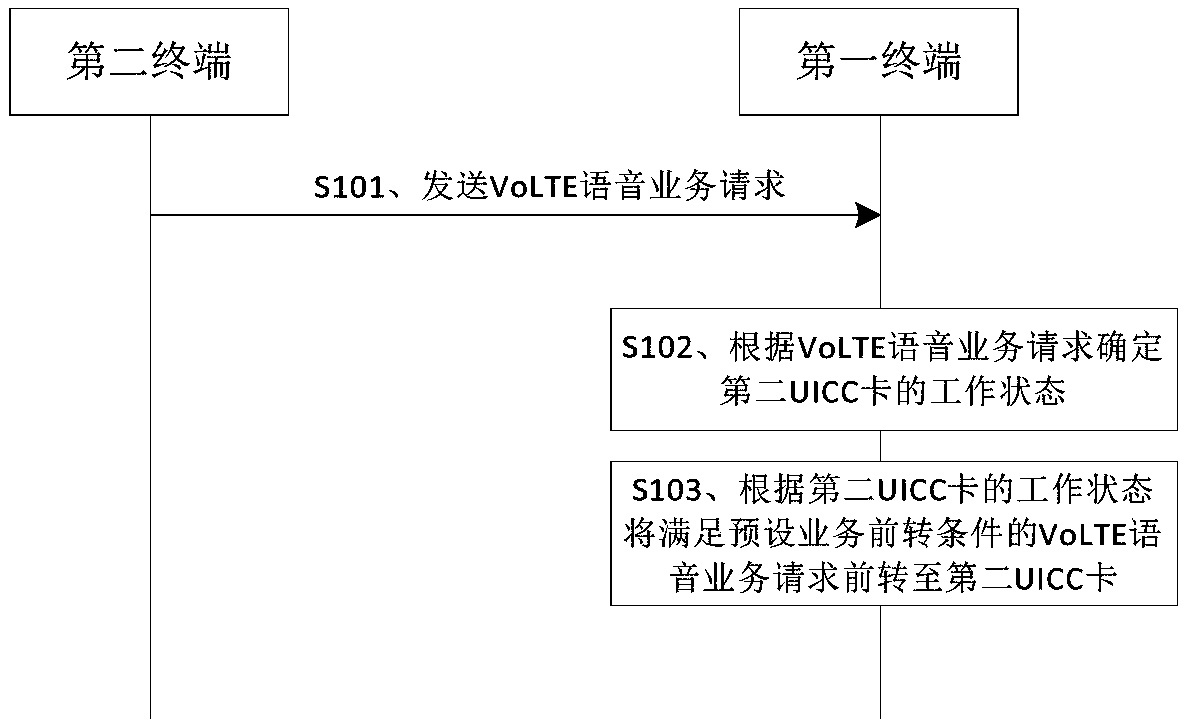
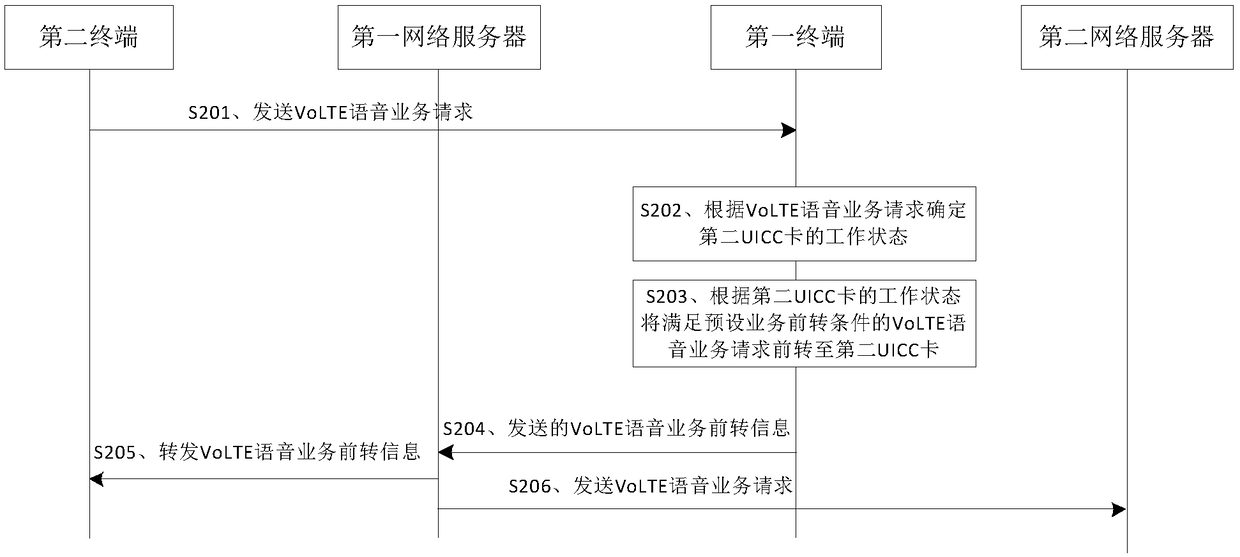
Service switching method, terminal, network server, and storage medium
InactiveCN109348470AAvoid interruptionAchieve concurrencyConnection managementNetwork data managementWork statusNetwork service
The invention provides a service switching method, a terminal, a network server, and a storage medium. A first terminal receives VoLTE voice service requests sent by a second terminal, wherein the VoLTE voice service requests include the identifier of a first UICC card of the first terminal; and the first terminal determines the working states of the first UICC card and a second UICC card according to the VoLTE voice service requests, and forwards a VoLTE voice service request that meets the preset service forwarding condition to the second UICC card according to the working states, thereby avoiding the interruption of the ongoing data service of the second UICC card due to the VoLTE voice service request of the first UICC card, and realizing the concurrence of the VoLTE voice and data onthe same UICC card.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
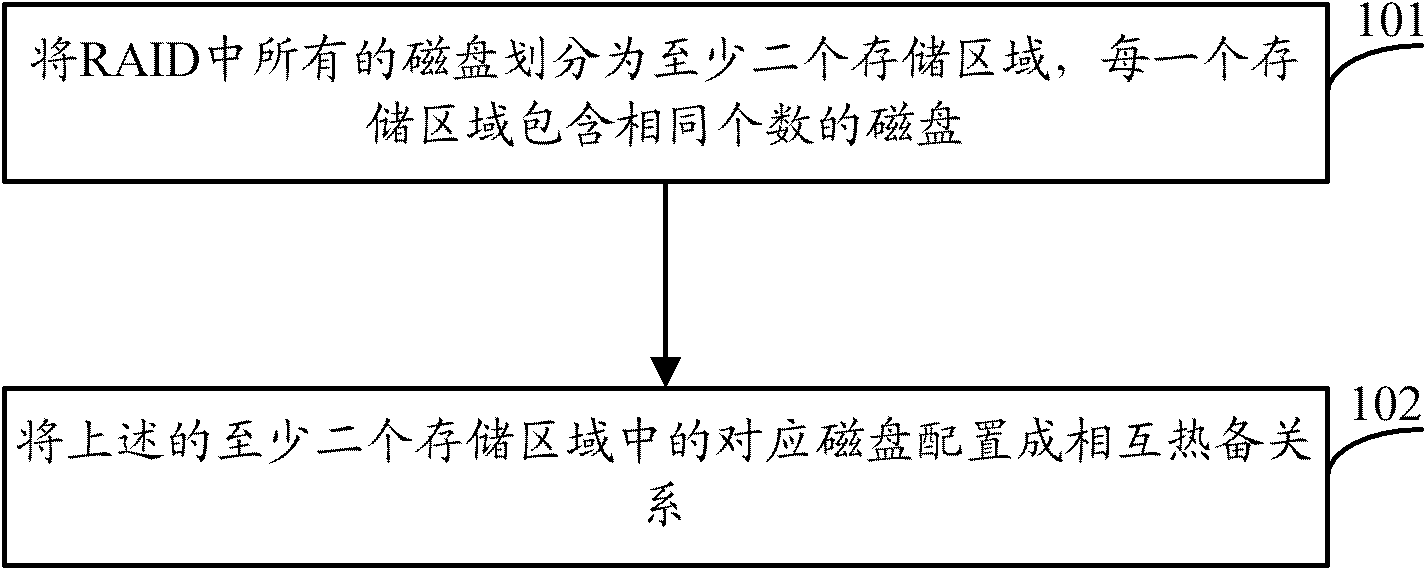
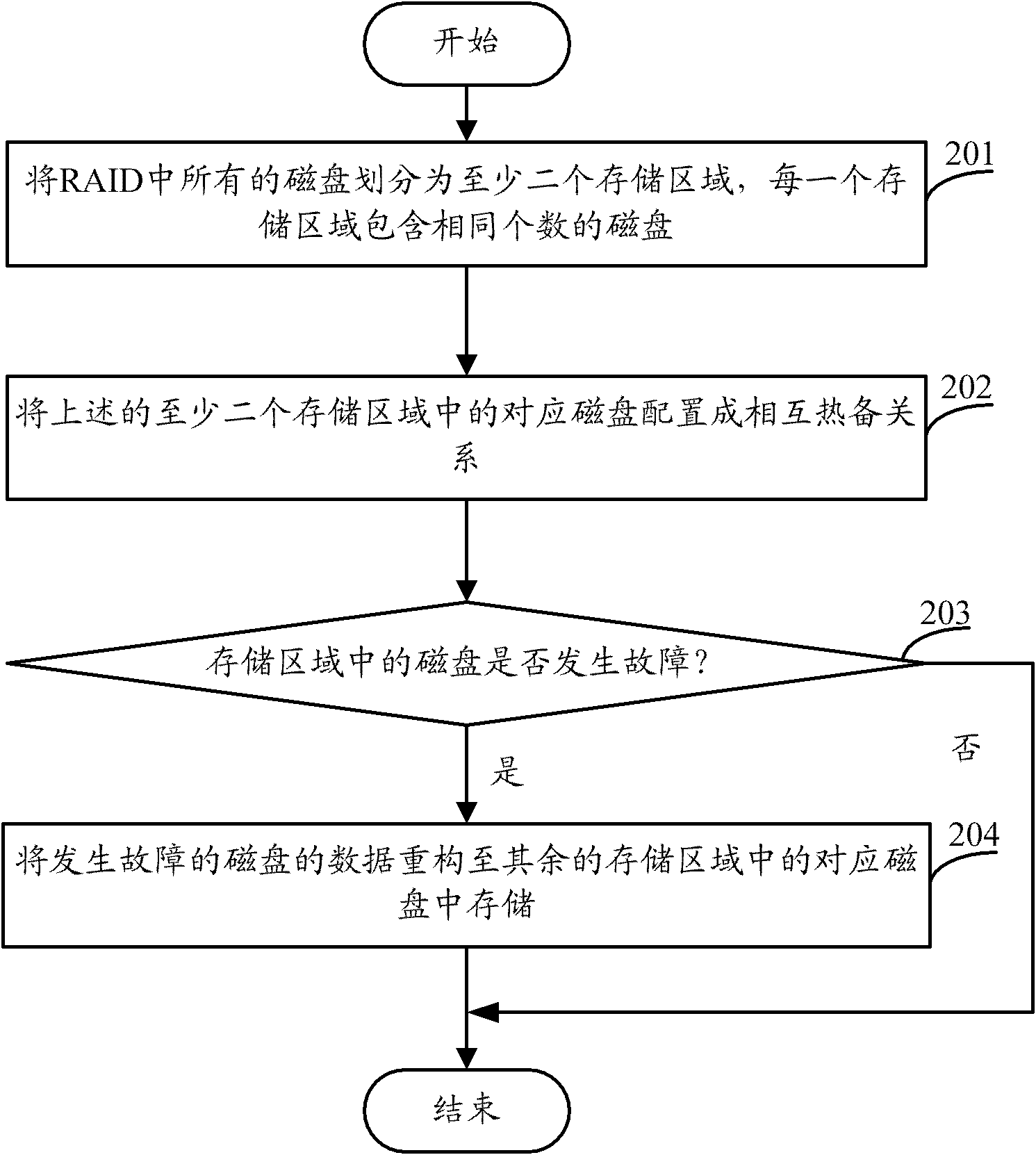
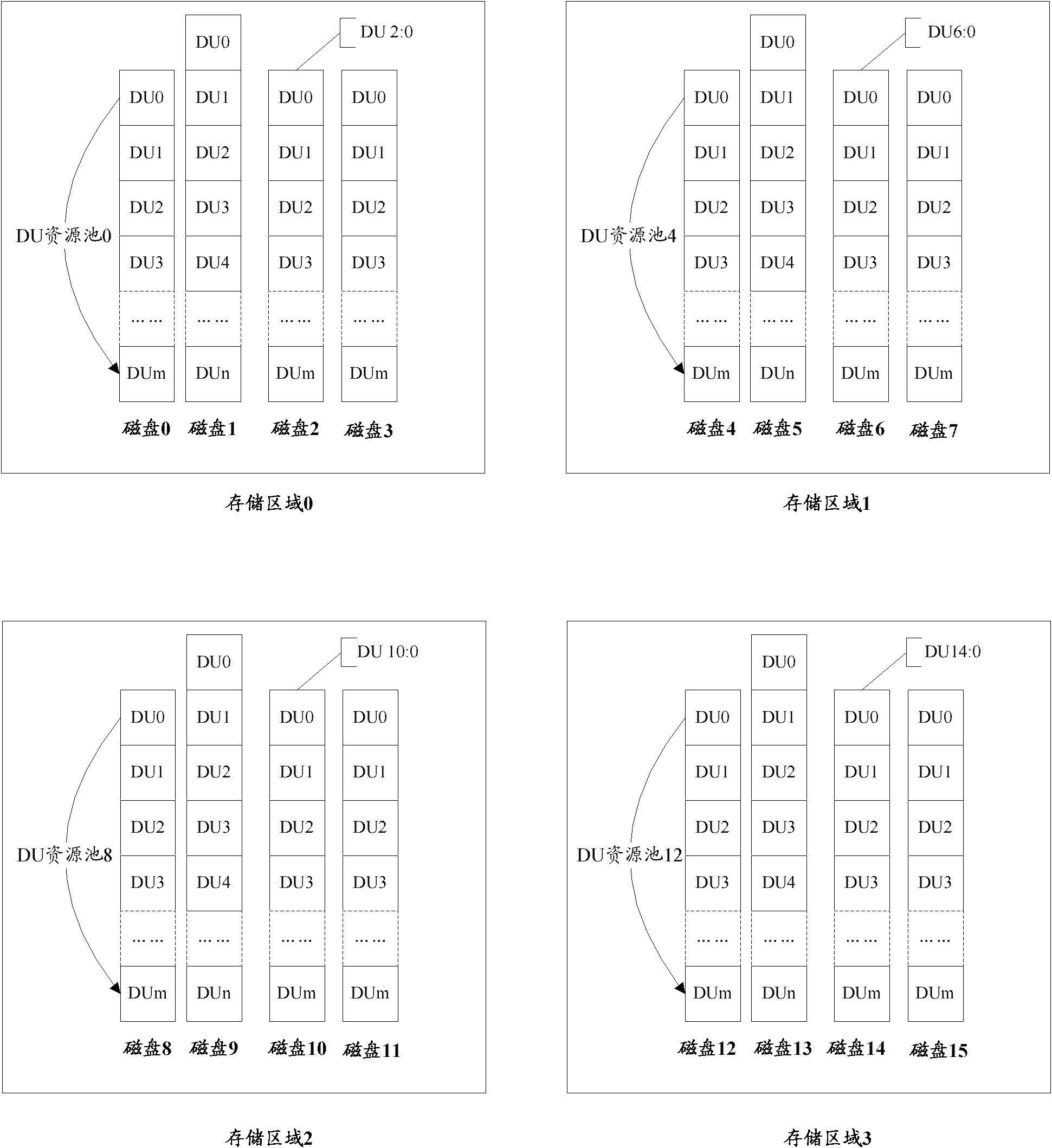
Disk hot standby method and device as well as storage system
InactiveCN102053801AImprove hot standby efficiencyAchieve concurrencyInput/output to record carriersDisk arrayEmbedded system
The embodiment of the invention relates to the technical field of hot standby and discloses a disk hot standby method and device as well as a storage system. The disk hot standby method comprises the following steps: dividing all disks in a cheap redundancy disk array into at least two storage areas, wherein each storage area contains same number of disks; and configuring the corresponding disks in the at least two storage areas into hot standby relation. According to embodiment of the invention, no reserved extra hot standby storage space is required, and the hot standby efficiency of the cheap redundancy disk array can be increased.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
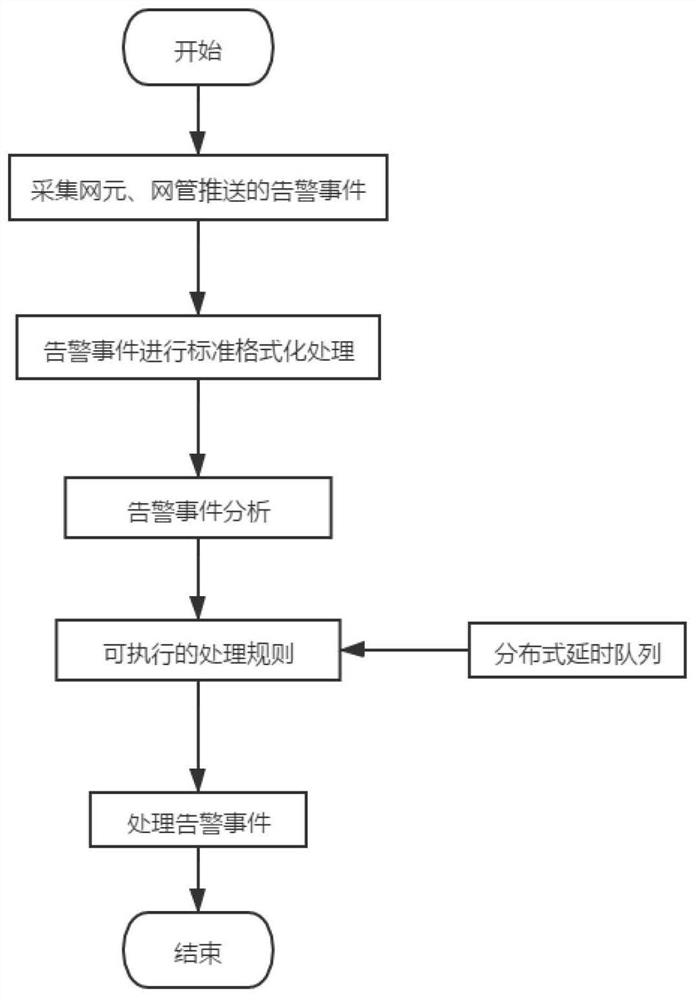
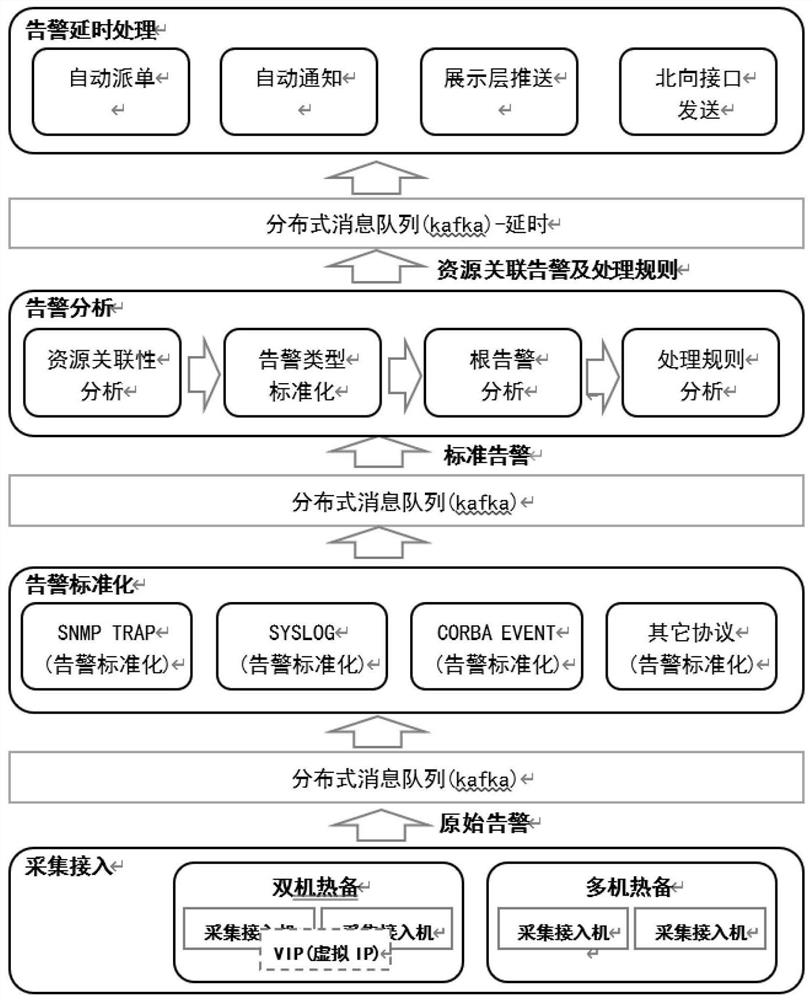
High-availability distributed real-time alarm processing method and high-availability distributed real-time alarm processing system
ActiveCN112671560ATo achieve fault toleranceAchieve concurrencyData switching networksManufacturing computing systemsMessage queueAlarm message
The invention discloses a high-availability distributed real-time alarm processing method and a high-availability distributed real-time alarm processing system. The method comprises the following steps of: acquiring alarm events pushed by a network element and a webmaster and sending the alarm events to a message queue; performing standard formatting processing on the alarm event, and converting the alarm event into the same data format; analyzing the standardized alarm event, and generating a most total executable processing rule; and unifying the sequence of all alarms by using a distributed delay queue to realize the processing of the alarm event. Real-time alarm processing is layered, the alarm receiving process and the alarm processing process are separated, the alarm receiving capacity is maximized, a large number of alarms appearing instantly can be better handled, and alarm messages are received and are not lost. A high-throughput distributed persistent message queue is adopted, so that the alarm can be reliably stored and buffered.
Owner:广东电力通信科技有限公司
Information processing method and system thereof
ActiveCN106385377AAddressing efficiency and control inefficienciesRealize access rate controlData switching networksData transmissionInformation processing
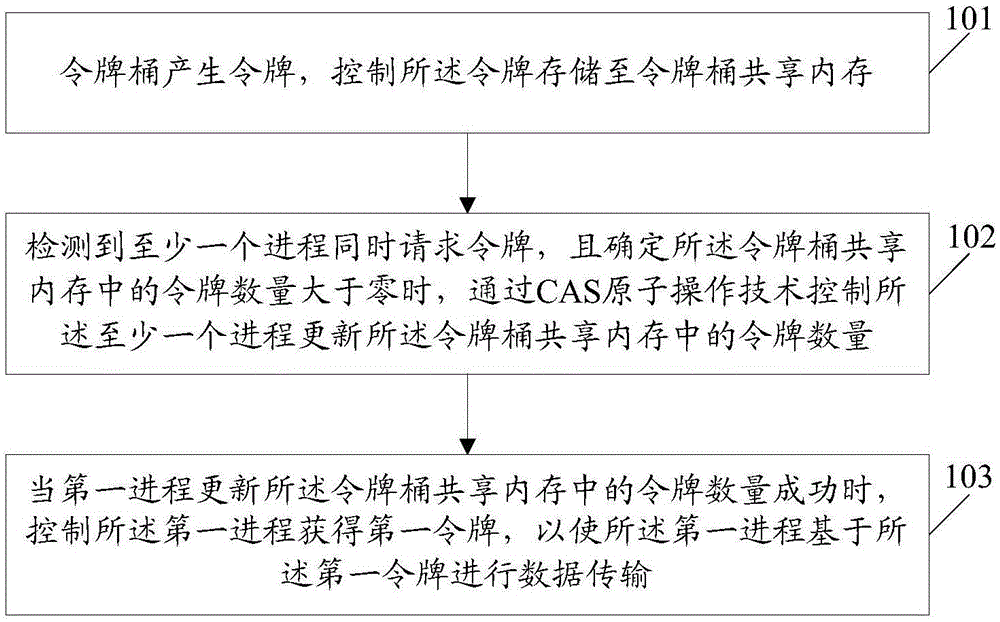
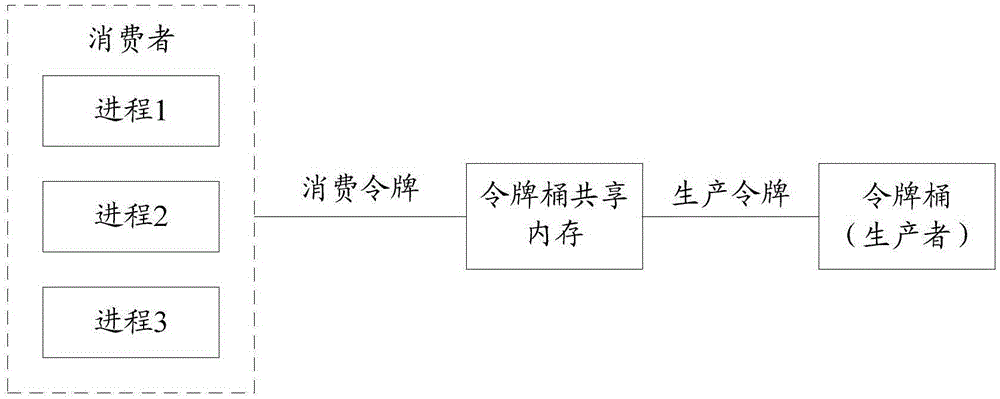
Embodiments of the invention disclose an information processing method and a system thereof. The method comprises the following steps of generating a token by a token bucket, and making the token be stored in a token-bucket shared memory; detecting that at least one process simultaneously requests for the token and determining that a token quantity in the token-bucket shared memory is greater than zero, and then through comparing and exchanging a (CAS) atom operation technology to make the at least one process update the token quantity in the token-bucket shared memory; and when a first process successfully updates the token quantity in the token-bucket shared memory, making the first process acquire a first token so that the first process carries out data transmission based on the first token, wherein the first process is any one process in the at least one process.
Owner:TENCENT TECH (SHENZHEN) CO LTD
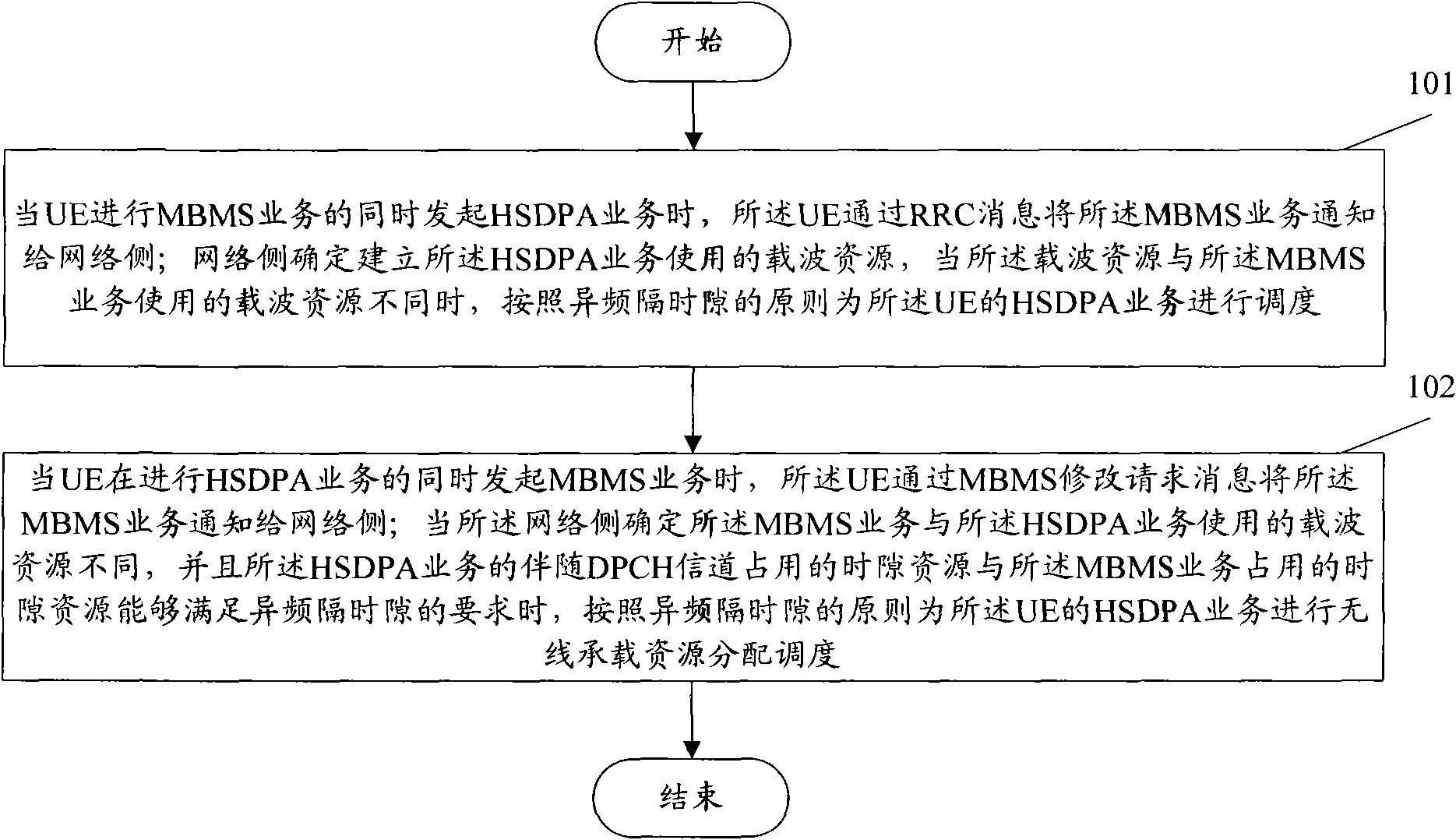
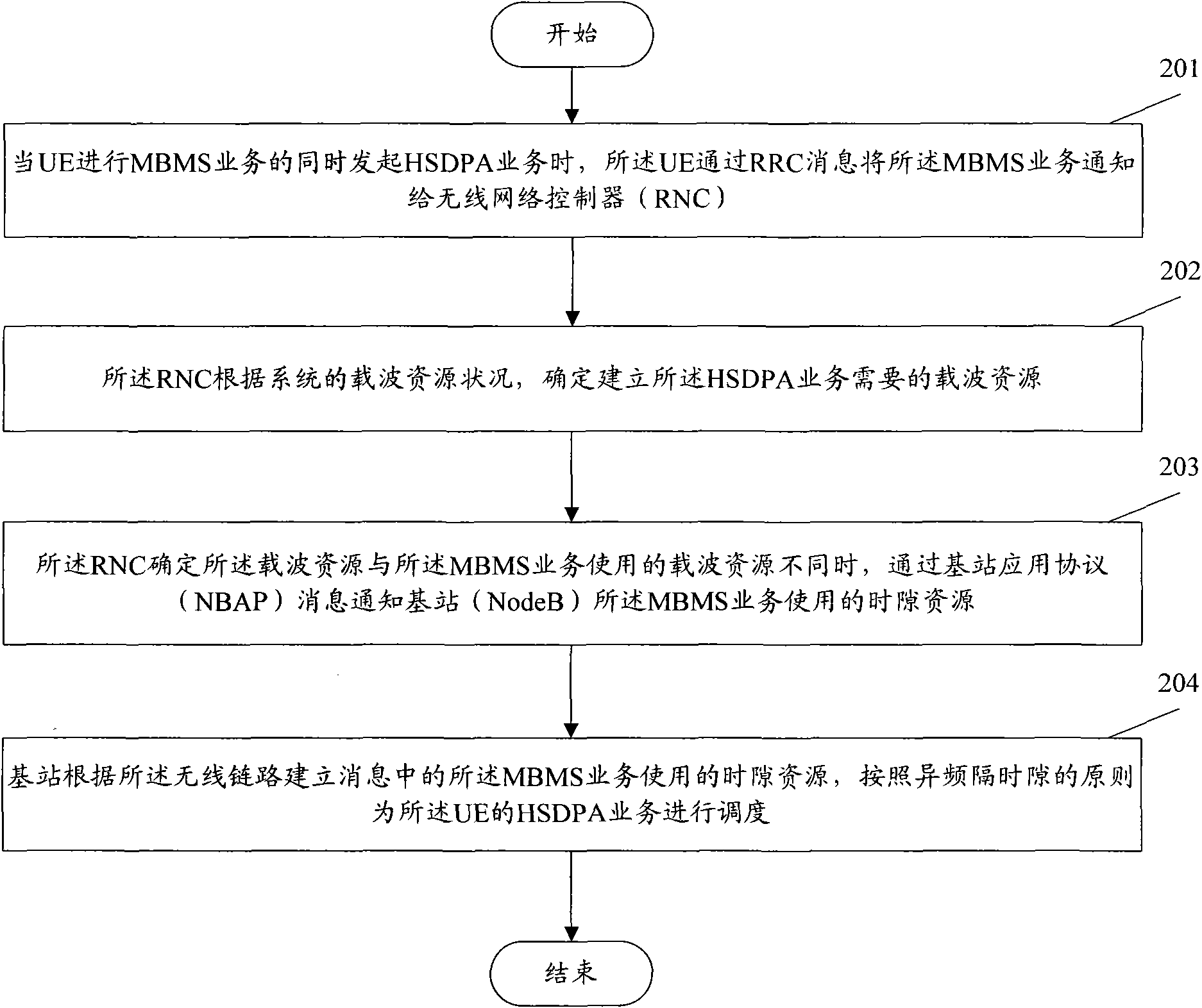
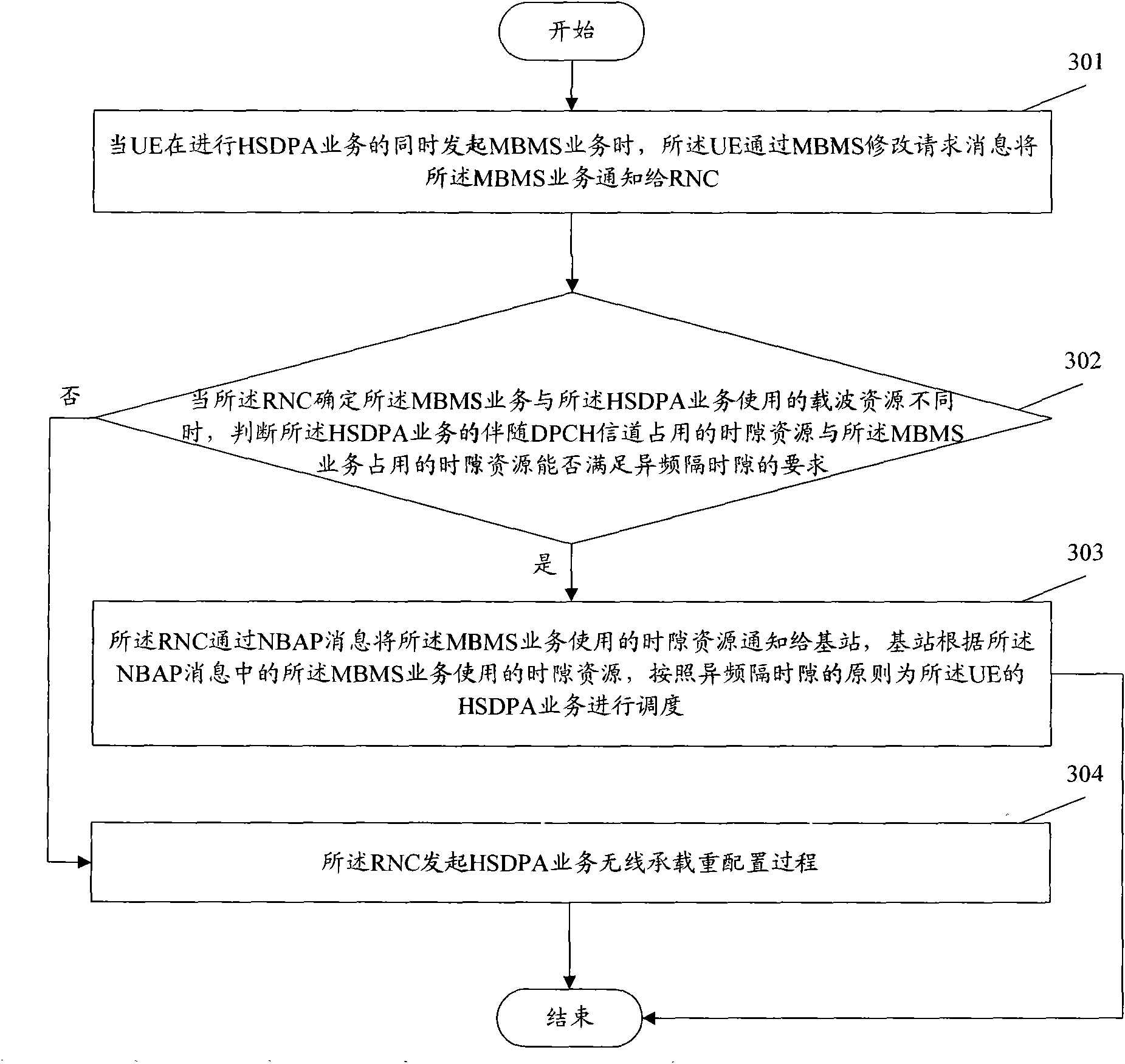
Method of jointly initiating high-speed downlink packet access (HSDPA) service and multimedia broadcast multicast service (MBMS)
InactiveCN101677461AAchieve concurrencyTransmissionWireless communicationMultimedia Broadcast Multicast ServiceTelecommunications
The invention discloses a method of jointly initiating high-speed downlink packet access (HSDPA) service and multimedia broadcast multicast service (MBMS), comprising the following steps: when initiating the MBMS, user equipment (UE) initiates the HSDPA service and informs the network side of the MBMS; when the network side determines that the carrier resources used for establishing the HSDPA service are different from the carrier resources used for establishing the MBMS, the HSDPA service is dispatched according to principle of different frequency across time slots; when initiating the HSDPAservice, the UE initiates the MBMS and informs the network side of the MBMS; when the network side determines that the carrier resources used for establishing the MBMS are different from the carrier resources used for establishing the HSDPA and determines that the following dedicated physical channel (DPCH) of the HSDPA service and the time slot resources occupied by the MBMS can meet the requirement of different frequency across time slots, the HSDPA service is dispatched according to principle of different frequency across time slots. The invention can jointly initiate the HSDPA service andthe MBMS on the UE side.
Owner:TD TECH COMM TECH LTD
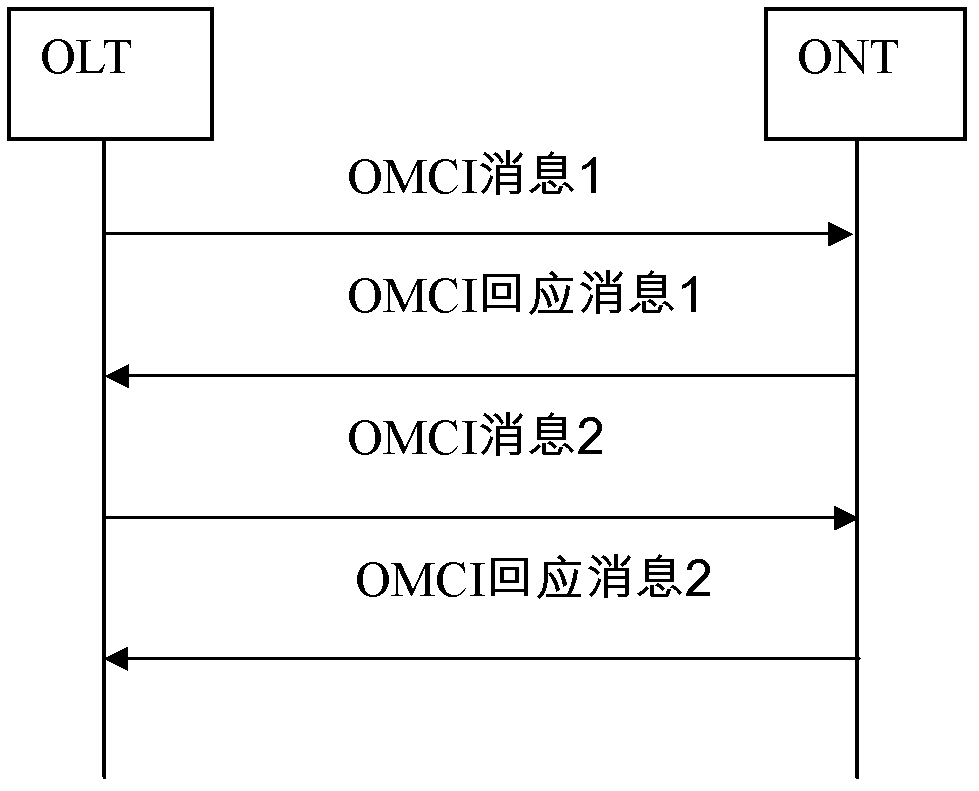
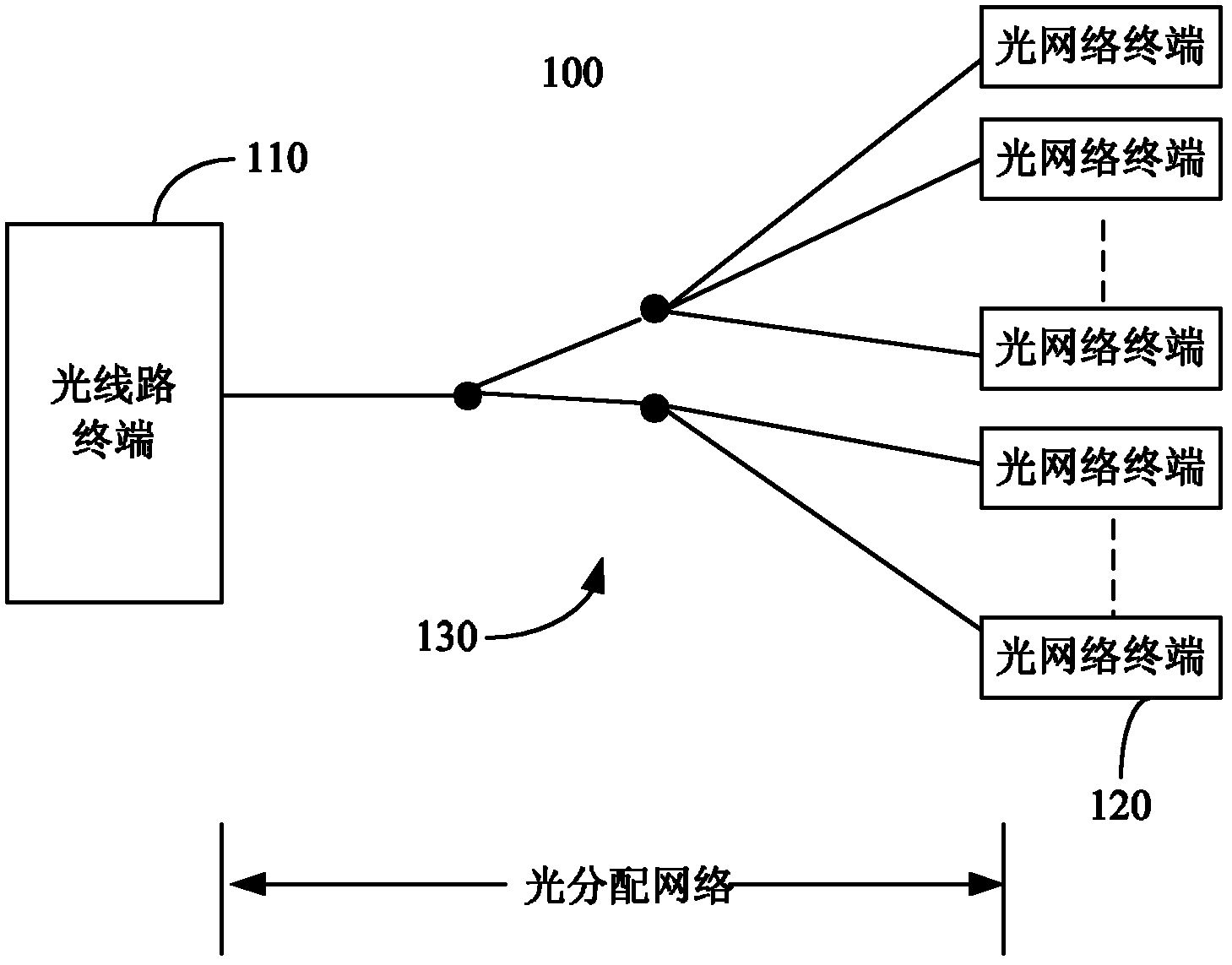
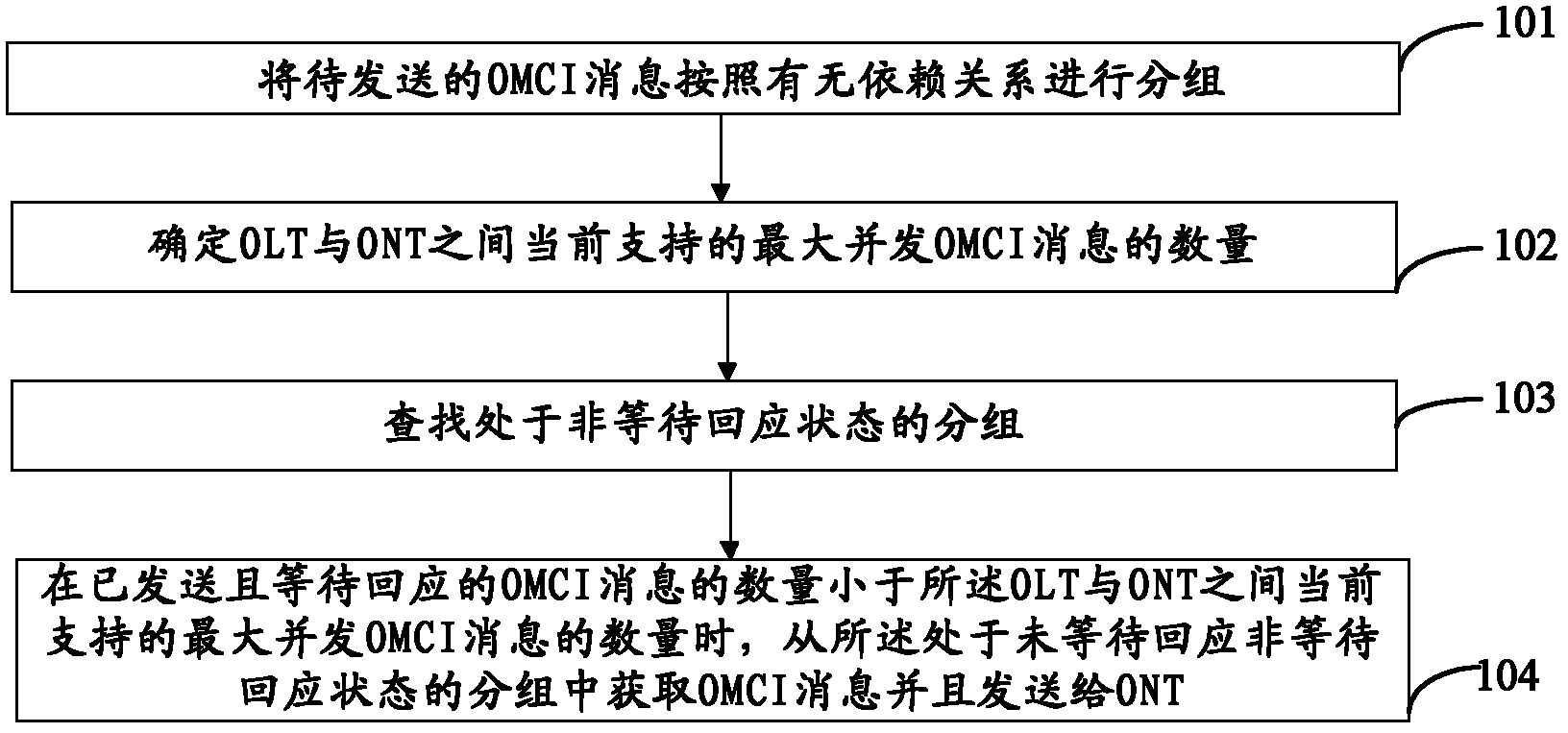
Omci message transmission method, device and passive optical network
InactiveCN102217328AImprove configuration efficiencyAchieve concurrencyMultiplex system selection arrangementsData switching networksDistributed computingPassive optical network
The invention provides an OMCI (Ont Management and Control Interface)message transmission method, a device and a passive optical network. The OMCI message transmission method includes dividing to-be-sent OMCI messages into groups, wherein OMCI messages in a same group have dependence and OMCI messages in different groups have no dependence; determining a maximum number of concurrent OMCI messagessupported between an OLT and ONT; according to the maximum number of concurrent OMCI messages supported between an OLT and ONT, acquiring OMCI messages from groups that not waiting for response and sending to the ONT.
Owner:李艳
Message processing method and system
ActiveCN112422404AImprove processing efficiencyImprove throughputData switching networksMessage queueMessage handling
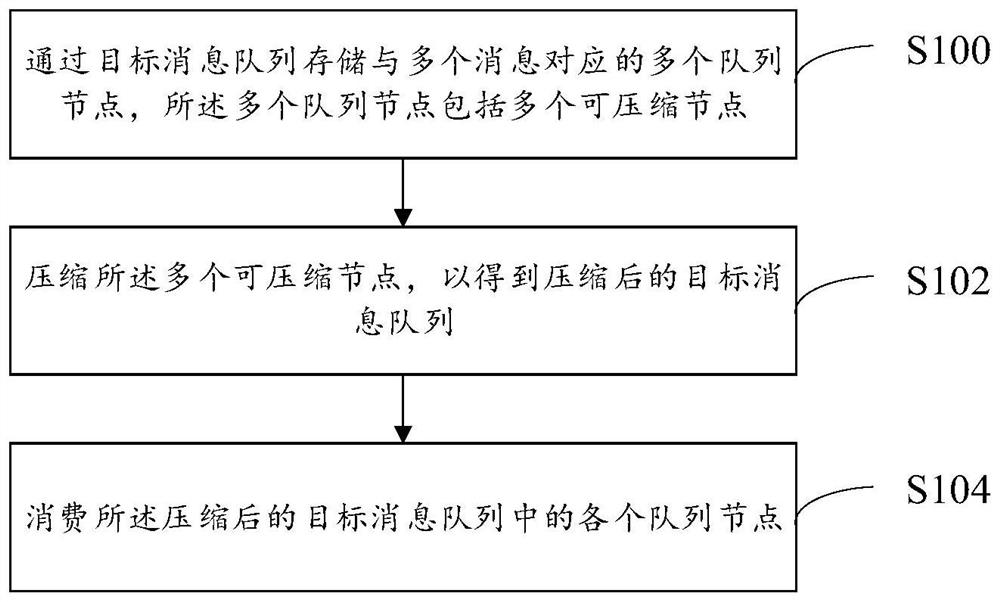
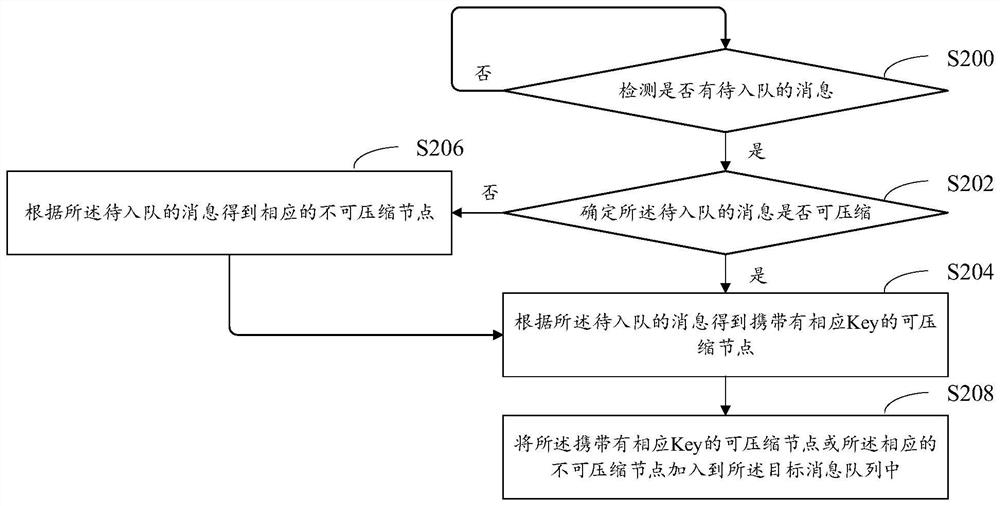
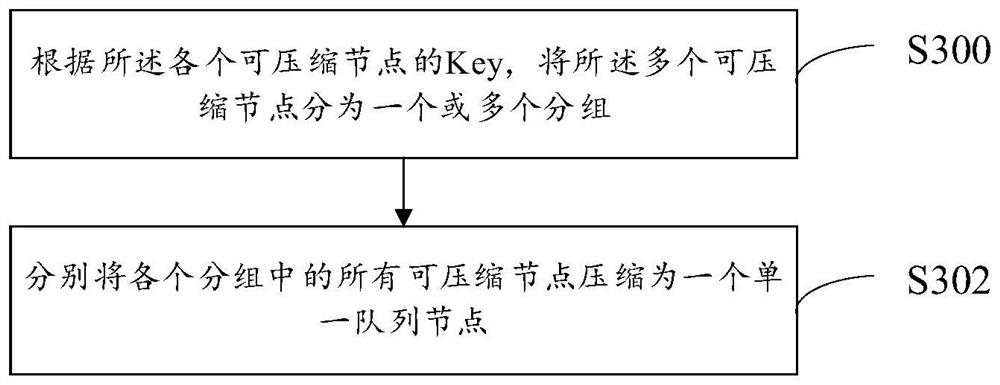
The embodiment of the invention discloses a message processing method, and the method comprises the steps: storing a plurality of queue nodes corresponding to a plurality of messages through a targetmessage queue, wherein the plurality of queue nodes comprises a plurality of compressible nodes; compressing the plurality of compressible nodes to obtain a compressed target message queue; and consuming each queue node in the compressed target message queue. According to the embodiment of the invention, the number of the messages (corresponding to the corresponding queue nodes) in the target message queue can be reduced, so that the throughput of processing the messages can be improved, the message processing efficiency is improved, and message extrusion and system congestion caused by excessive messages are avoided.
Owner:SHANGHAI BILIBILI TECH CO LTD
Data synchronization method and device, electronic equipment and storage medium
ActiveCN114661816AImprove synchronization efficiencyAchieve concurrencyDatabase updatingDatabase distribution/replicationData synchronizationTransaction log
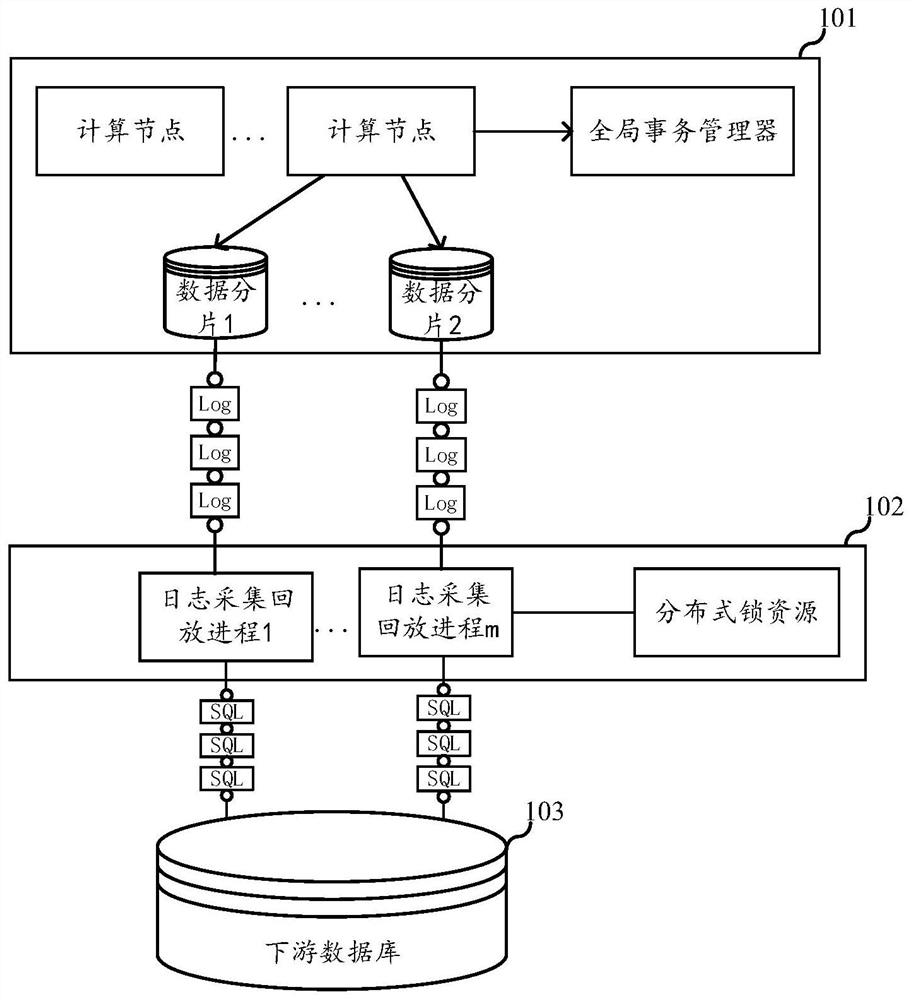
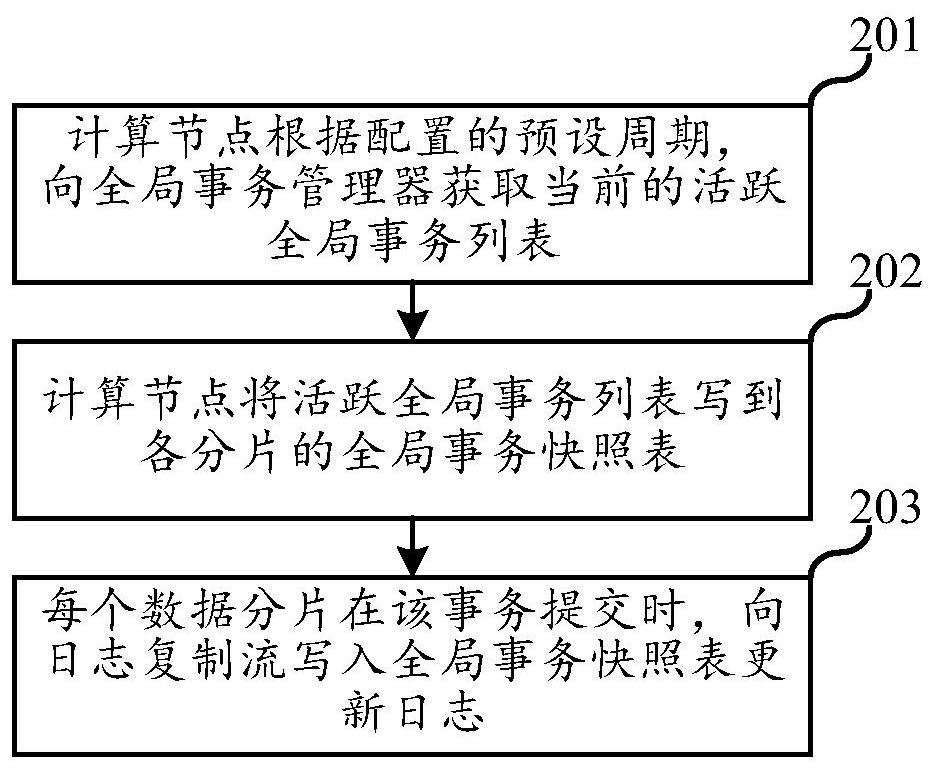
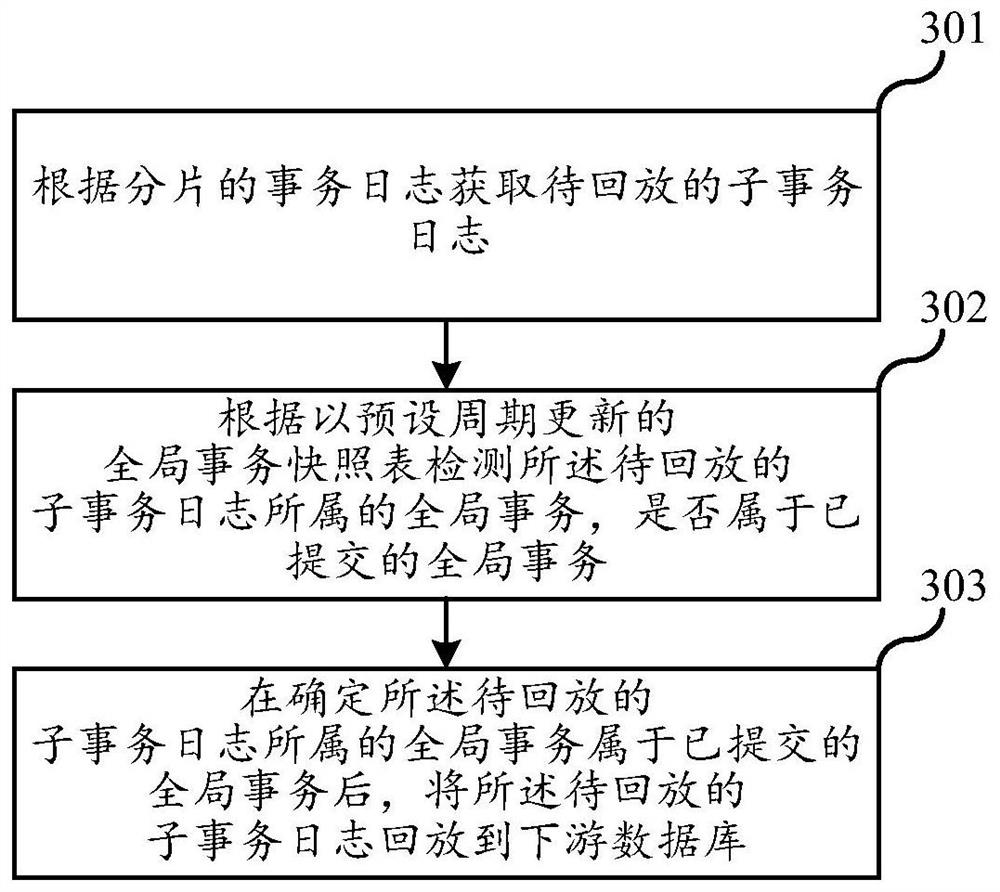
The embodiment of the invention relates to the field of databases, in particular to a data synchronization method and device, electronic equipment and a storage medium. The data synchronization method provided by the invention comprises the following steps: acquiring a to-be-played-back sub-transaction log according to a fragmented transaction log; detecting whether a global transaction to which the to-be-played-back sub-transaction log belongs belongs to a submitted global transaction or not according to a global transaction snapshot table updated in a preset period; wherein the global transaction snapshot table is used for recording the submission state of the global transaction; and after determining that the global transaction to which the to-be-played-back sub-transaction log belongs belongs to the submitted global transaction, the to-be-played-back sub-transaction log is played back to the downstream database, so that the problem that unsubmitted data is synchronized to the downstream database is avoided, and in addition, the embodiment takes fragments as granularity, so that the data synchronization efficiency is improved. And the fragments in the distributed database determine the sub-transaction logs capable of being played back according to the global transaction snapshot table, so that concurrence among the fragments is realized conveniently, and the data synchronization efficiency is improved.
Owner:金篆信科有限责任公司
Customized cleaning method and system based on container service
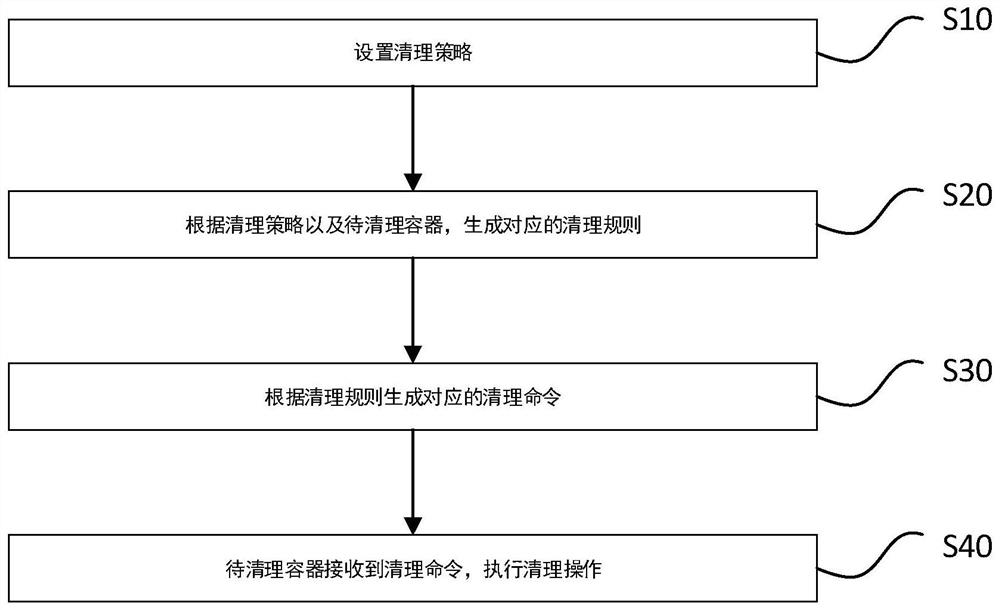
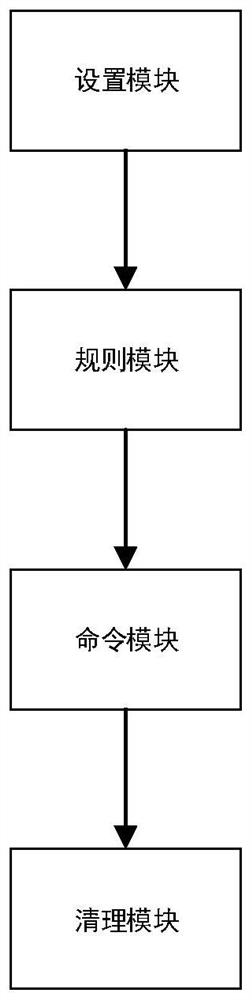
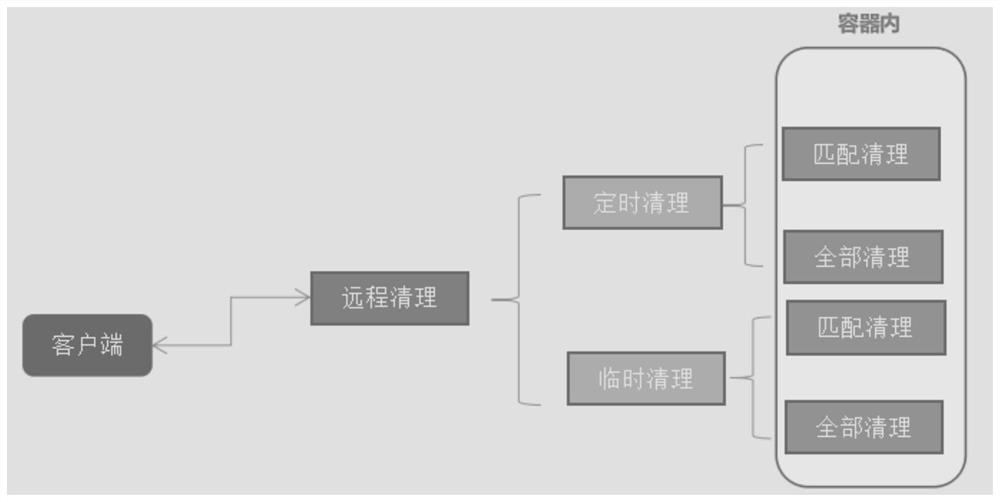
PendingCN111813575AIncrease flexibilityReduce couplingResource allocationInterprogram communicationProcess engineeringIndustrial engineering
The invention discloses a customized cleaning method and system based on container service, relates to the technical field of computers, and is used for realizing that scheduling, strategies and cleaning are divided into three parts for various cleaning requirements; the coupling degree is reduced to the minimum, and remote cleaning is carried out for different containers based on various cleaningstrategies. The invention has the beneficial effects that aiming at various cleaning requirements, scheduling, strategy and cleaning are divided into three parts, the coupling degree is reduced to the minimum, meanwhile, the maximum flexibility is reserved, the operation is simple and convenient, the expansion is easy, and effective support is provided for solving the problem of cleaning redundant files in a remote container.
Owner:ZHUHAI SEASUN MOBILE GAME TECH CO LTD
Data transmission method and device, and storage medium
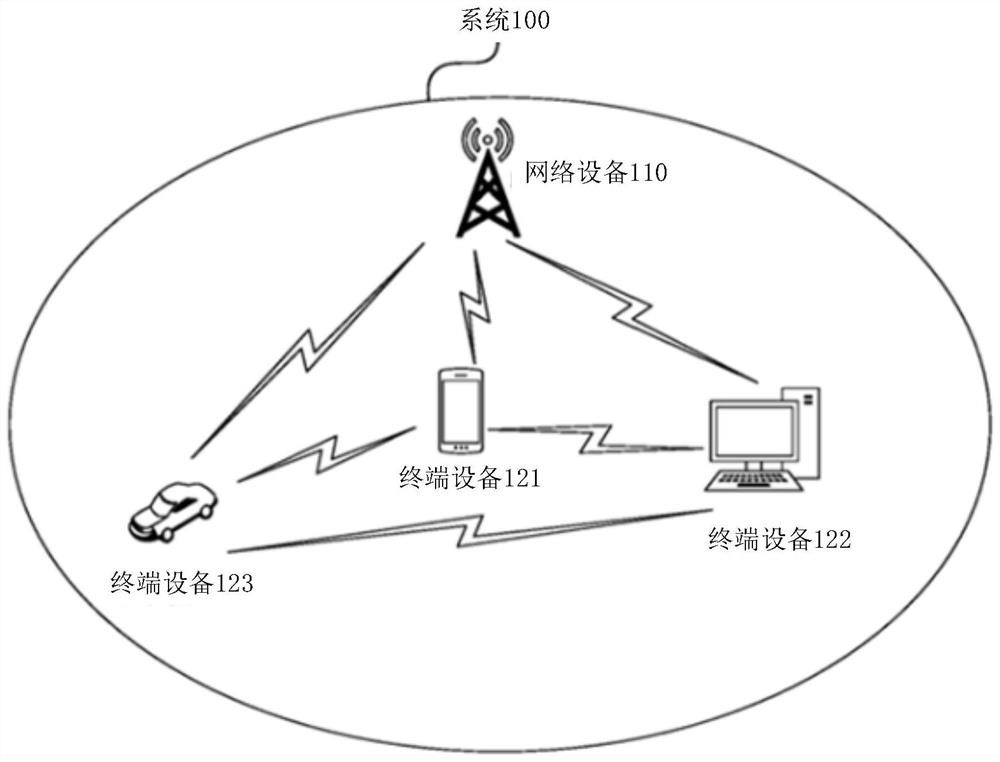
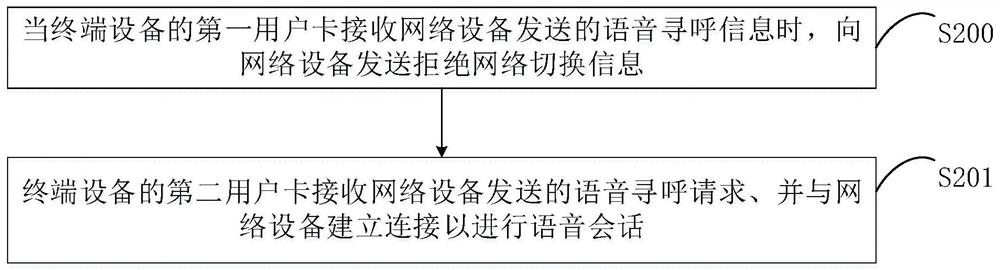
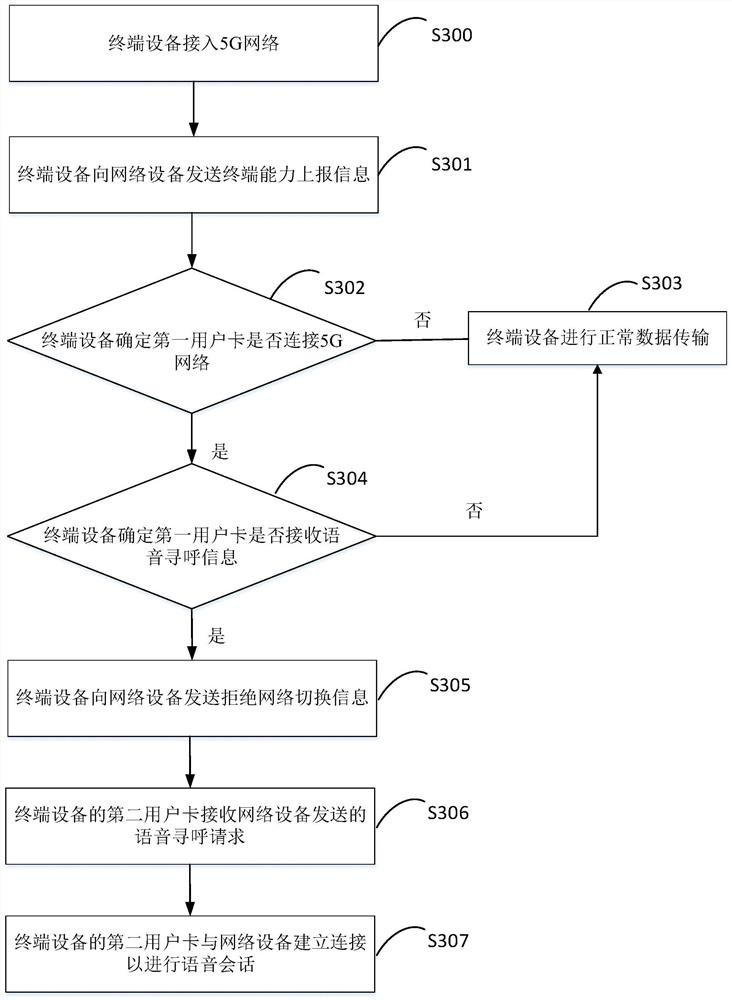
PendingCN114339922APrevent falling backAchieve concurrencyNetwork topologiesConnection managementTerminal equipmentUser perception
The invention provides a data transmission method and device, and a storage medium, and relates to the technical field of wireless communication. And when a first user card of the terminal equipment receives voice paging information sent by network equipment, the terminal equipment sends network switching rejection information to the network equipment to indicate the network equipment to reject switching from the 5G network to the 4G network, and in response to the network switching rejection information, the network equipment sends a voice paging request corresponding to the voice paging information to the second user card of the terminal equipment and establishes connection with the second user card of the terminal equipment to perform a voice session, so that the main card is prevented from falling back to 4G, the SA + LTE service concurrence of the main card is realized, the data performance is effectively guaranteed, and the user experience is improved. And meanwhile, the user perception of the bi-pass terminal equipment is greatly improved.
Owner:CHINA TELECOM CORP LTD
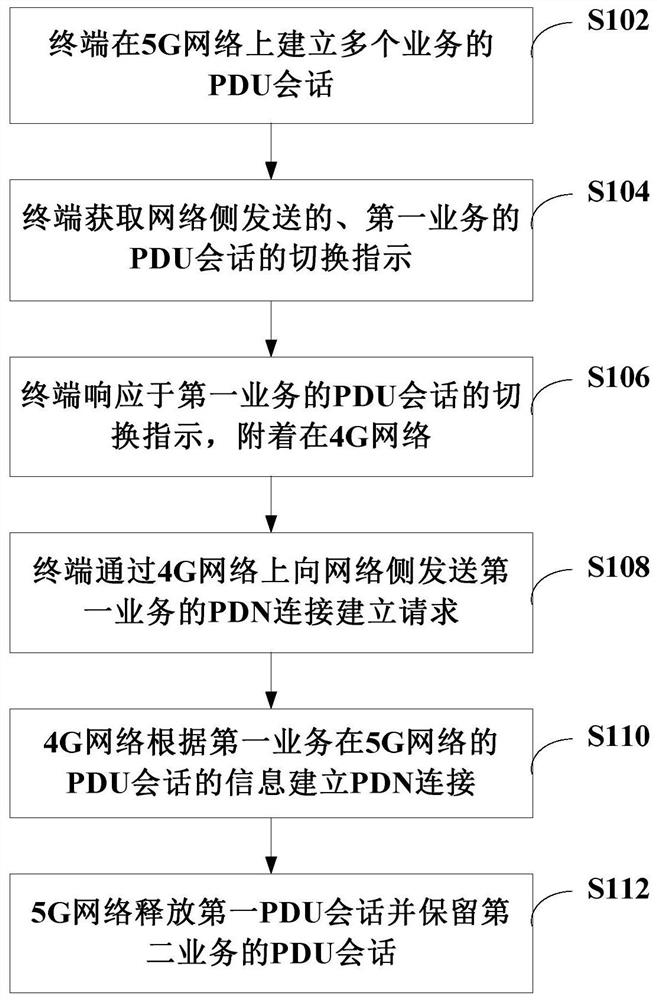
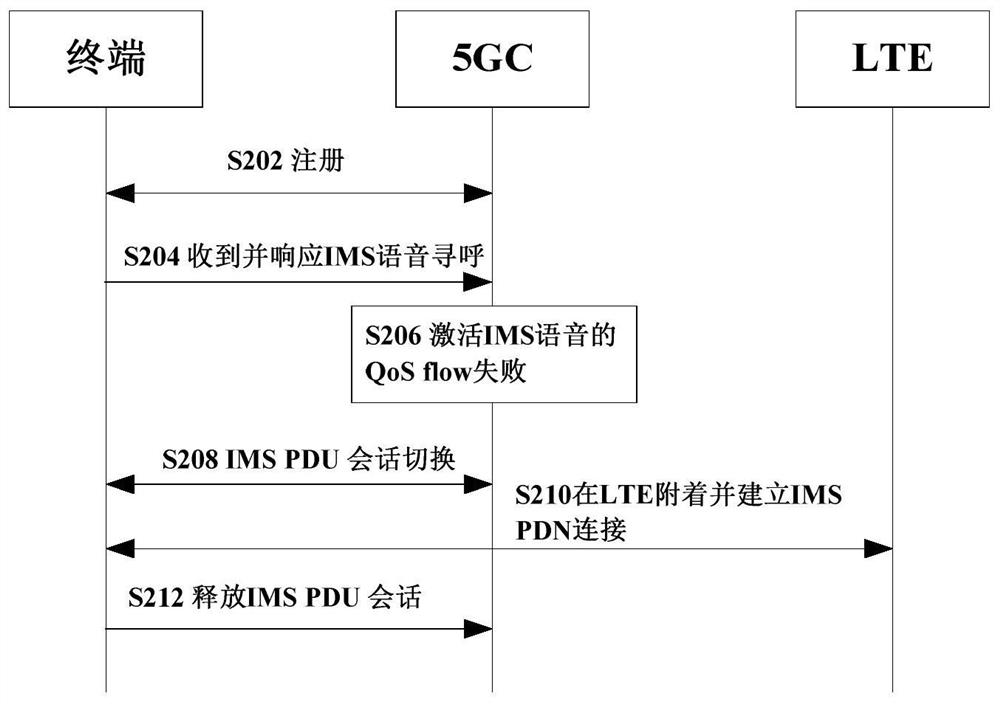
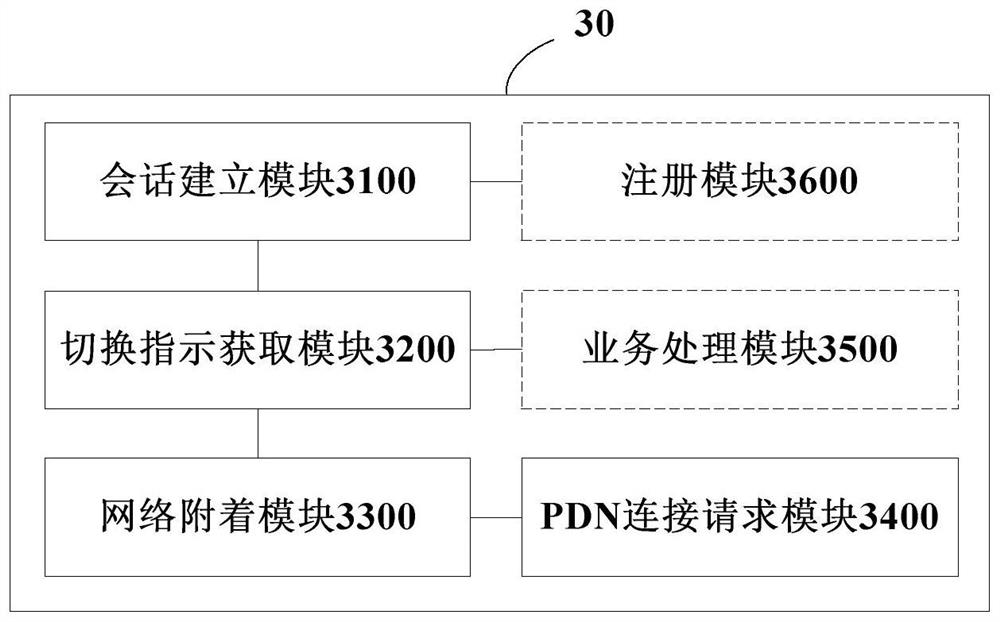
Service concurrence method, device and system and storage medium
The invention discloses a service concurrency method, device and system and a storage medium, and relates to the technical field of mobile communication. The service concurrency method comprises the following steps that a terminal establishes PDU sessions of a plurality of services on a 5G network, wherein the PDU sessions comprise a PDU session of a first service and a PDU session of a second service; the terminal obtains a switching instruction of the PDU session of the first service sent by the network side; the terminal is attached to the 4G network in response to the switching instruction of the PDU session of the first service; a terminal sends a PDN connection establishment request of a first service to a network side through a 4G network, the PDN connection establishment request comprises a PDU session switching instruction and information of a PDU session of the first service in a 5G network, so that the 4G network establishes a PDN connection according to the information of the PDU session of the first service in the 5G network, and the 5G network releases the first PDU session and reserves a PDU session of a second service. Therefore, the concurrence of services on different networks is realized.
Owner:CHINA TELECOM CORP LTD
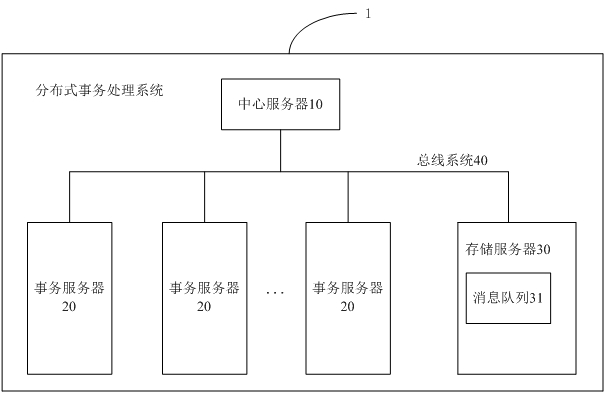
Distributed transaction processing method, device and system and electronic equipment
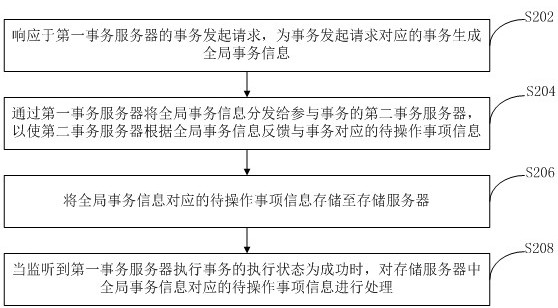
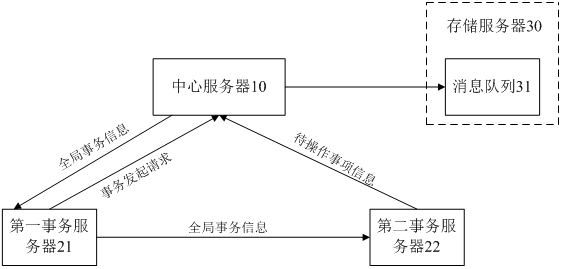
ActiveCN113254167AImprove processing efficiencyAchieve consistencyDatabase updatingDatabase distribution/replicationEngineeringDatabase
The invention provides a distributed transaction processing method, device and system and electronic equipment. The method comprises the following steps: a central server allocates global transaction information to a transaction corresponding to a transaction initiation request in response to the transaction initiation request of a first transaction server; the global transaction information is distributed to a second transaction server participating in the transaction through the first transaction server, so that the second transaction server feeds back to-be-operated item information corresponding to the transaction according to the global transaction information; item information to be operated corresponding to the global transaction information is stored to a storage server; and when it is monitored that the execution state of executing the transaction by the first transaction server is successful, the to-be-operated item information corresponding to the global transaction information in the storage server is processed, so that the consistency and concurrency of data in the distributed transaction processing process are realized, and the processing efficiency of the distributed transaction is improved.
Owner:中电金信软件有限公司
Data transmission method and device based on FUSE file system and NFS protocol
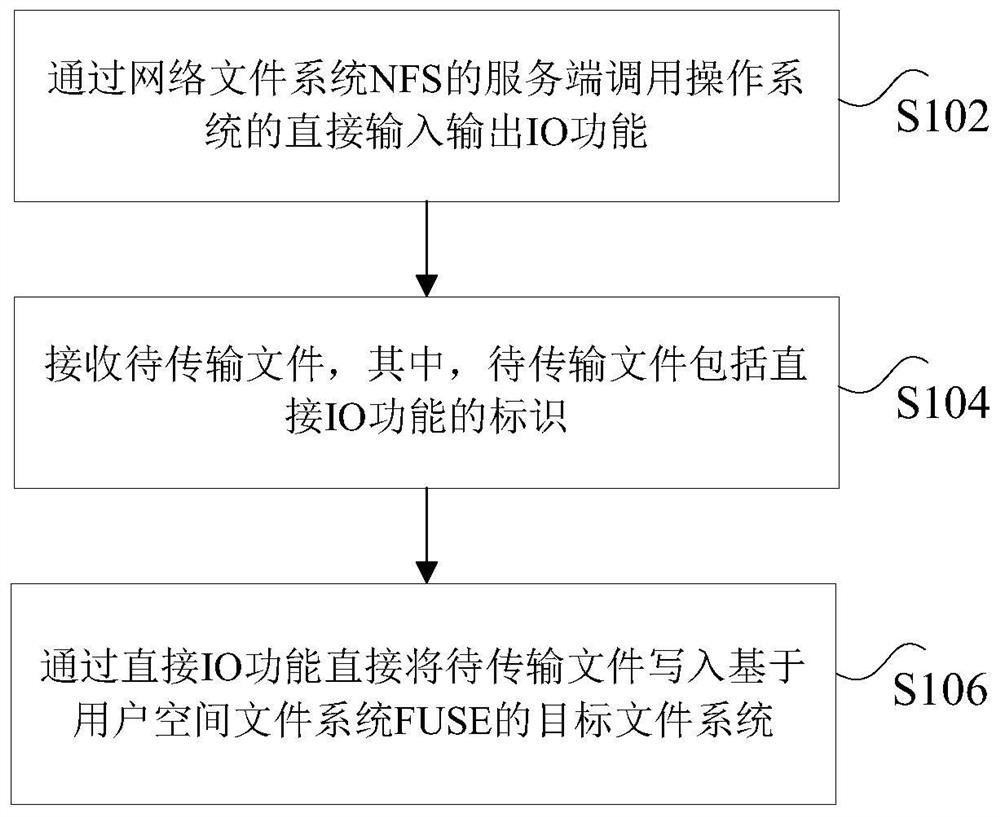
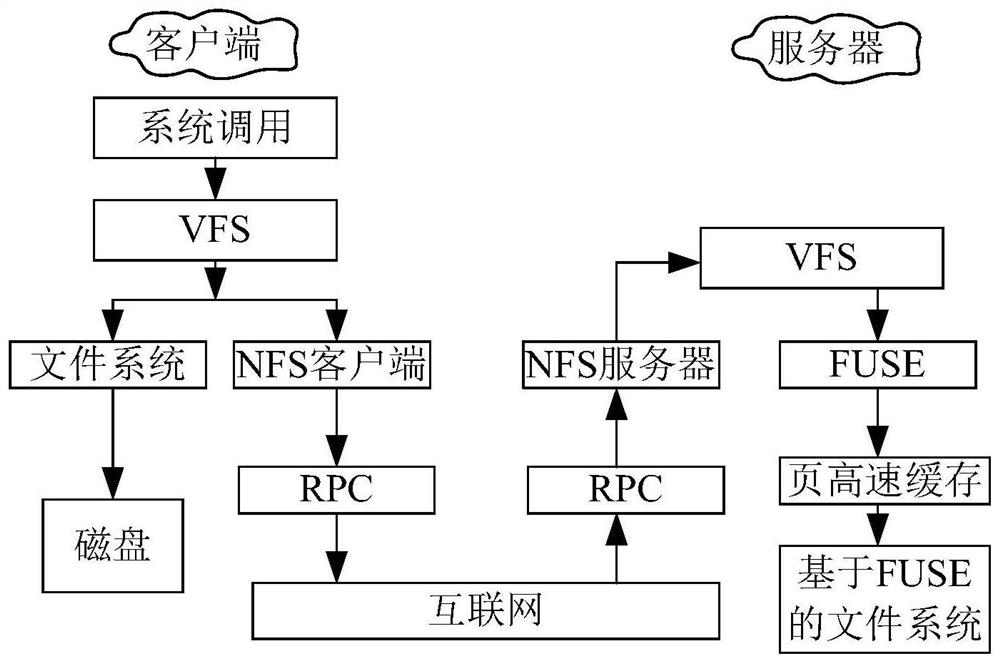
PendingCN111767257AAvoid one-linersAchieve concurrencyDigital data information retrievalTransmissionOperational systemFile system
The invention discloses a data transmission method and device based on a FUSE file system and an NFS protocol. The method comprises the following steps: calling a direct input / output (IO) function ofan operating system through a server of a network file system (NFS); receiving a to-be-transmitted file, wherein the to-be-transmitted file comprises an identifier of the direct IO function; and directly writing the to-be-transmitted file into a target file system based on a user space file system FUSE through a direct IO function. According to the method and the device, the technical problems that the concurrency of read-write data is influenced and the efficiency is relatively low due to the fact that a client needs to pass through a page cache at a server side when the client reads and writes the data to the server in related technologies are solved.
Owner:北京星辰天合科技股份有限公司
Digital asset transaction method and blockchain system based on blockchain system
InactiveCN107392608BAchieve concurrencyImprove securityPayment protocolsSecuring communicationSoftware engineeringFinancial transaction
The invention discloses a digital asset transaction method and a blockchain system based on a blockchain system. Wherein, the block chain system is a tree-shaped distributed block chain system including block chains of multiple levels, and the method includes: the first block chain receives the digital asset transaction request from the client, and determines that it corresponds to the digital asset transaction request digital assets; determine whether the attribution block chain corresponding to the digital asset is the first block chain; if so, the first block chain processes the digital asset transaction request; if not, the first block chain rejects the digital asset transaction request; wherein, the attribution blockchain corresponding to the digital asset is the blockchain that generated the digital asset. This method is especially suitable for one-time digital asset transactions, which can only be used once; moreover, this method can also realize cross-chain transactions between digital assets, and the digital assets before and after the execution of cross-chain transactions correspond to different Belonging to the blockchain, thus improving the security of assets.
Owner:北京博晨技术有限公司
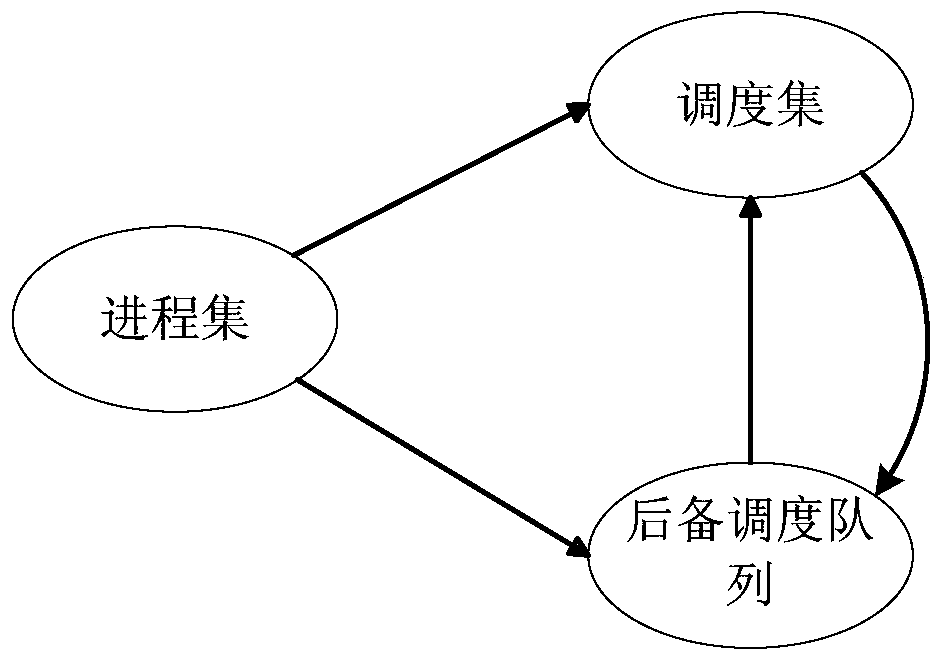
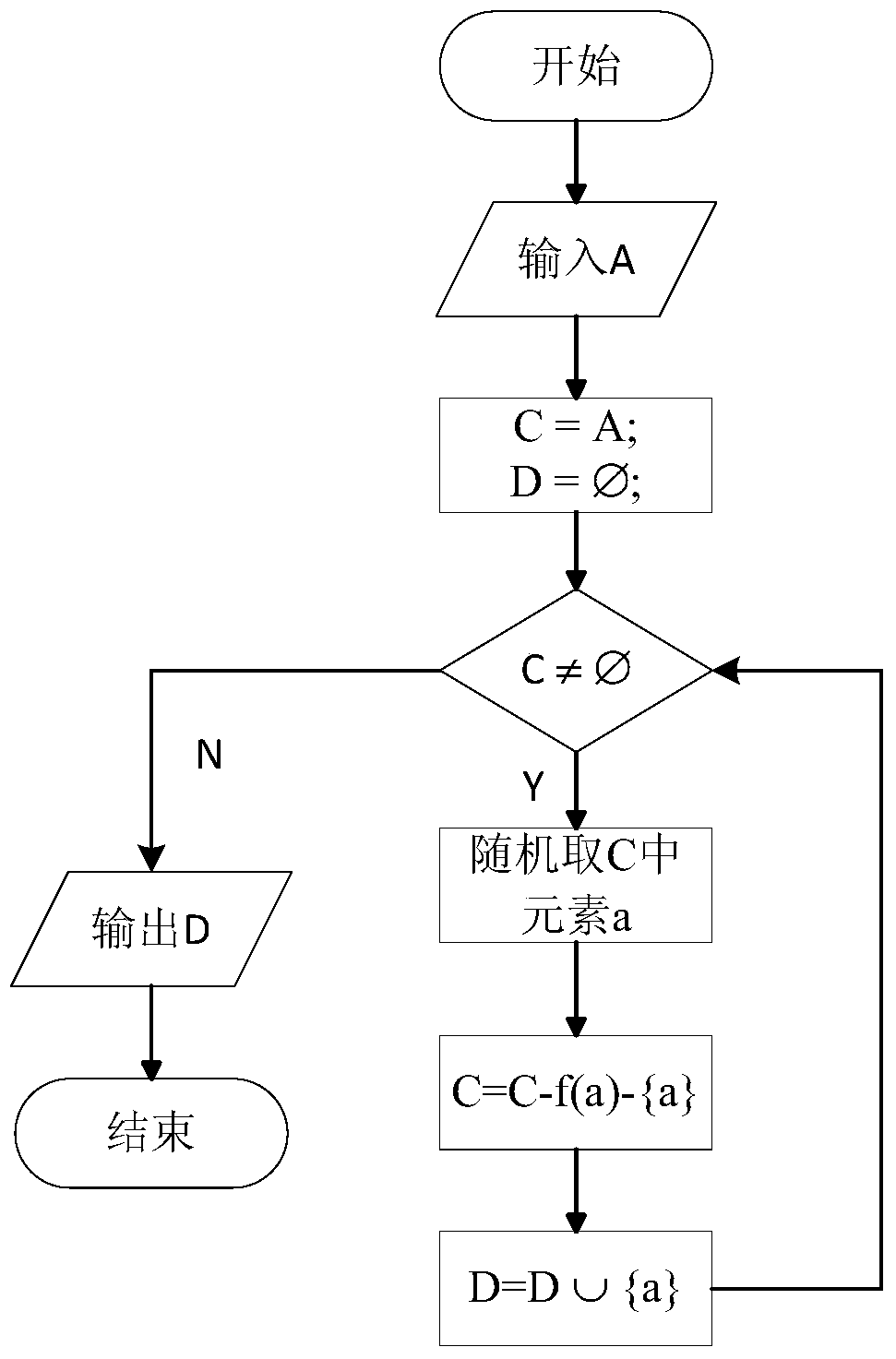
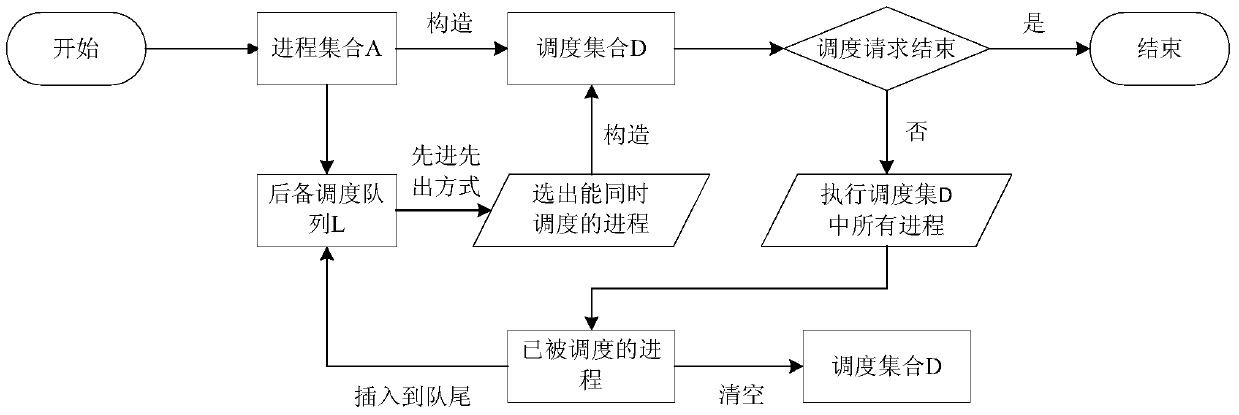
A method for computer multi-process fair scheduling
ActiveCN104636200BAchieve concurrencyAchieve fairnessResource allocationFair-share schedulingFair scheduling
The invention discloses a fair-share scheduling method for multiple processes of computer. The method comprises the following steps: 1, selecting processes from a process set to form a scheduling set, and a reserved scheduling queue is formed by the unselected processes; 2, determining whether the requirement of a process scheduling is over or not, if the requirement of the process scheduling is not over, the next step is conducted, or the scheduling is over; 3, scheduling the scheduling set; 4, conversionring the scheduled processes in the scheduling set to the tail of the reserved scheduling queue; 5, emptying the scheduling set; 6, selecting processes from the reserved scheduling queue to form a scheduling set and jumping to step 2. According to the fair-share scheduling method for multiple processes of computer, the scheduling set of the processes and the reserved scheduling queue are formed by the operation of set computation, so that the fair-share scheduling on computer multi process is achieved, the occurrence of deadlock during the concurrent scheduling of the processes is avoided, and the scheduling ability on concurrent processes of the computer processor is improved.
Owner:SHANGHAI DEV CENT OF COMP SOFTWARE TECH +2
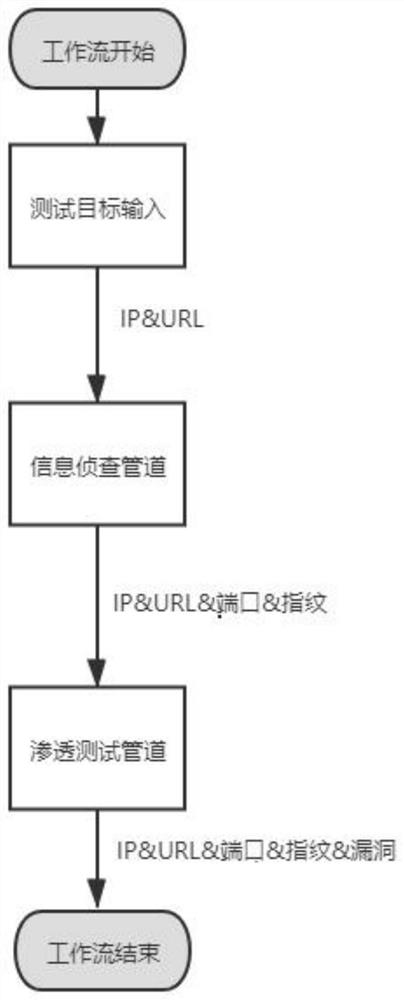
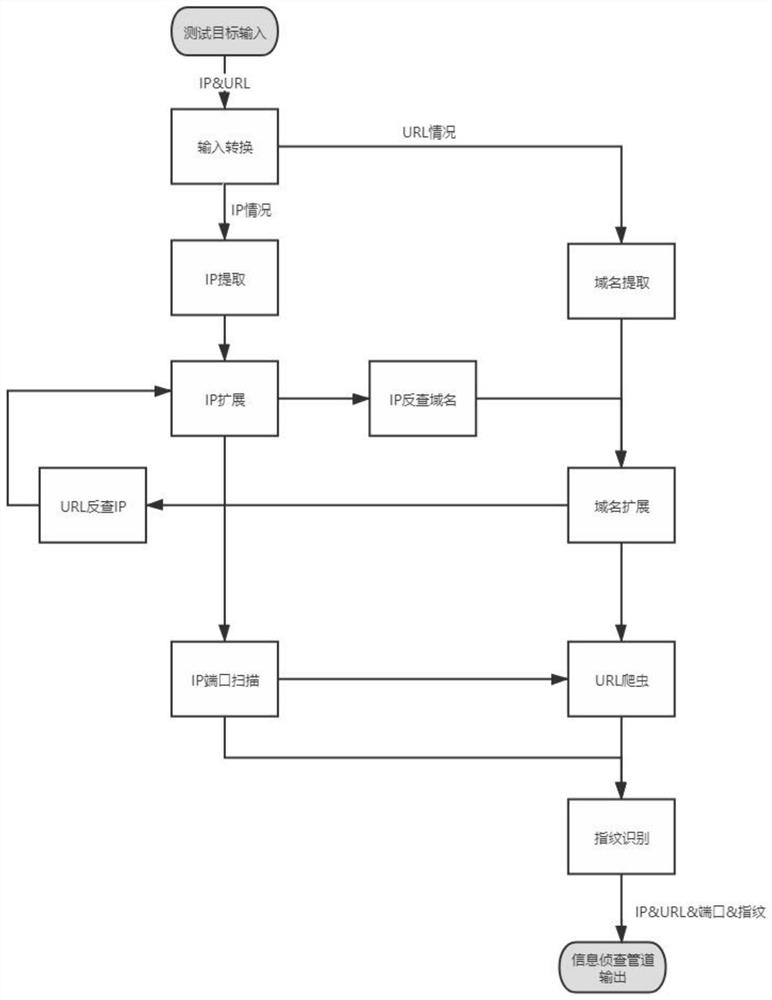
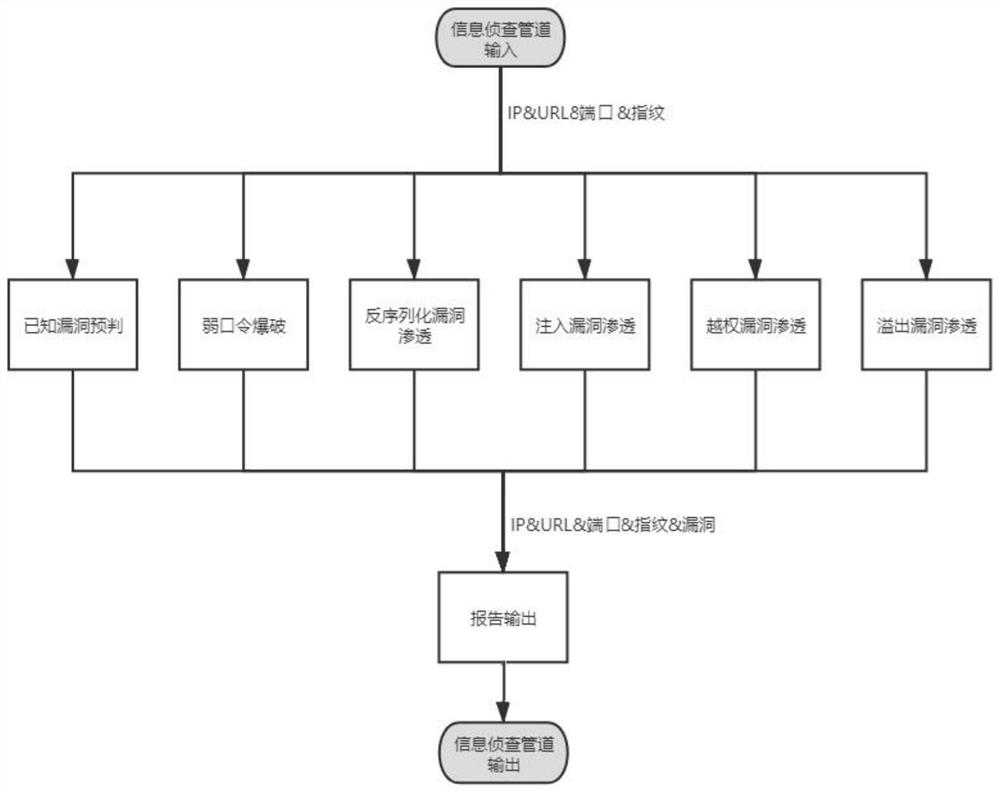
A Workflow-Based Information Detection and Penetration Testing Method
ActiveCN113254334BAchieve concurrencySoftware testing/debuggingPlatform integrity maintainanceDomain nameComputer software
The invention provides a method for information investigation and penetration testing based on workflow, and relates to the technical field of computer software information. Based on the workflow, the method realizes the detection, filtering and de-duplication of the domain name, IP, IP port, URL and fingerprint of the test target through the information detection pipeline and the penetration test pipeline, and conducts information detection and penetration testing for various vulnerabilities. The information detection pipeline is used to detect the information of the input target. Through the input IP and URL, the IP, URL, port and fingerprint information are obtained and stored based on multiple plug-ins, which are used for the penetration test pipeline call; the penetration test pipeline is connected with the information detection pipeline. , based on different multiple plug-ins, use the IP, URL, port and fingerprint obtained by the reconnaissance pipeline to perform penetration testing on various vulnerabilities, store the tested vulnerability information and output the test report at the same time. The method can detect and collect the information of the test target in a short time, and automatically carry out the vulnerability penetration, which improves the efficiency of the penetration test.
Owner:北方实验室(沈阳)股份有限公司
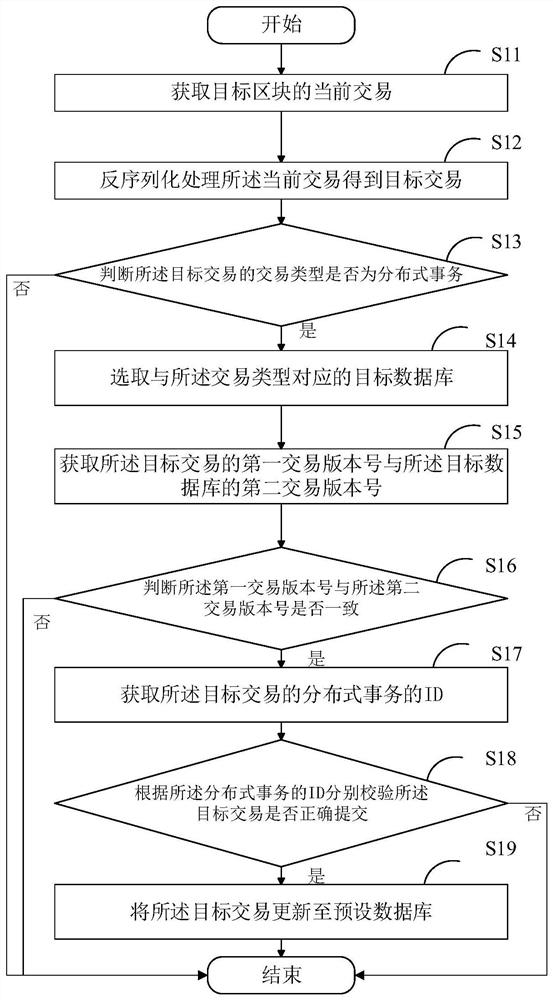
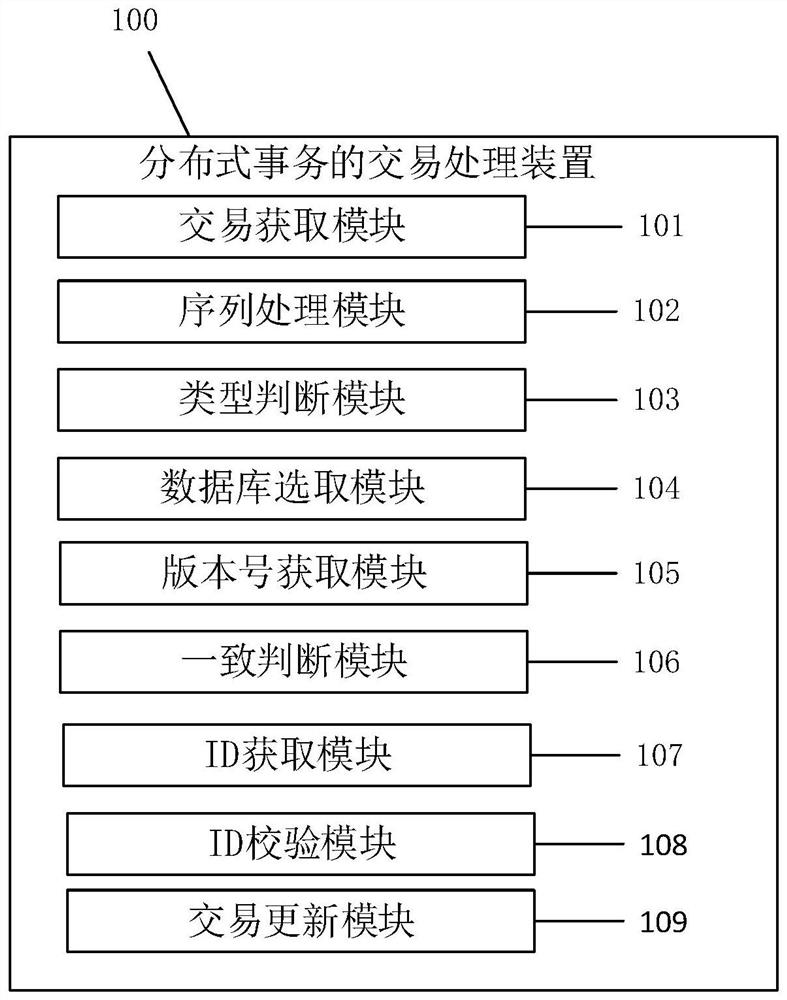
Transaction processing method for distributed transactions and related equipment
ActiveCN111694851AAchieve concurrencyAchieve correctnessDatabase updatingFinanceParallel computingEngineering
The invention relates to the technical field of block chains, and provides a transaction processing method and device for a distributed transaction and related equipment, and the method comprises thesteps: obtaining and carrying out the deserialization of a current transaction, and obtaining a target transaction; judging whether the transaction type of the target transaction is a distributed transaction or not; when the judgment result is yes, selecting a target database; obtaining a first transaction version number of the target transaction and a second transaction version number of the target database; judging whether the first transaction version number is consistent with the second transaction version number or not; when the judgment result is yes, obtaining the ID of the distributedtransaction; respectively verifying whether the target transaction is correctly submitted or not; and when the judgment result is that the target transaction is correctly submitted, updating the target transaction to a preset database. Through the improved mvcc mechanism, the correctness of the cross-chain distributed transaction operation is realized.
Owner:PING AN TECH (SHENZHEN) CO LTD
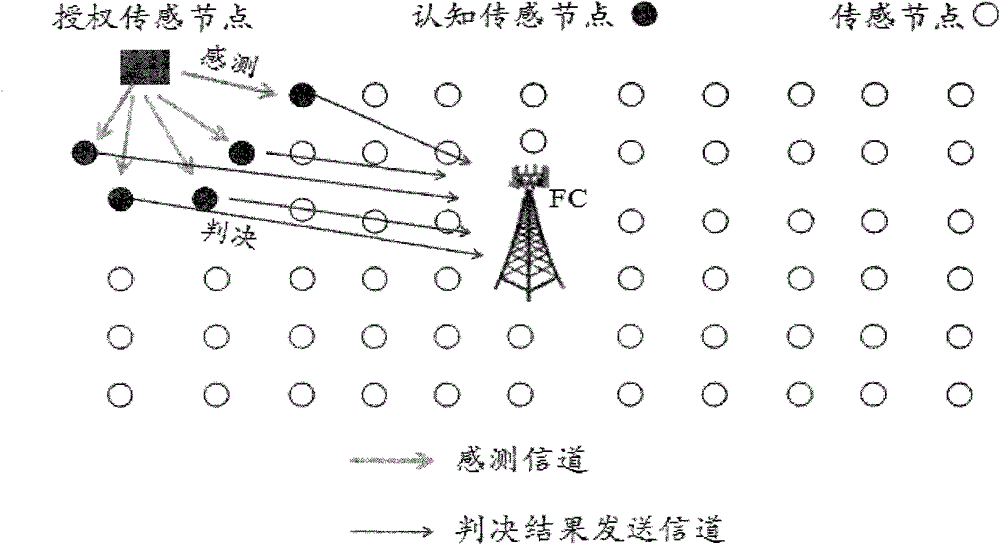
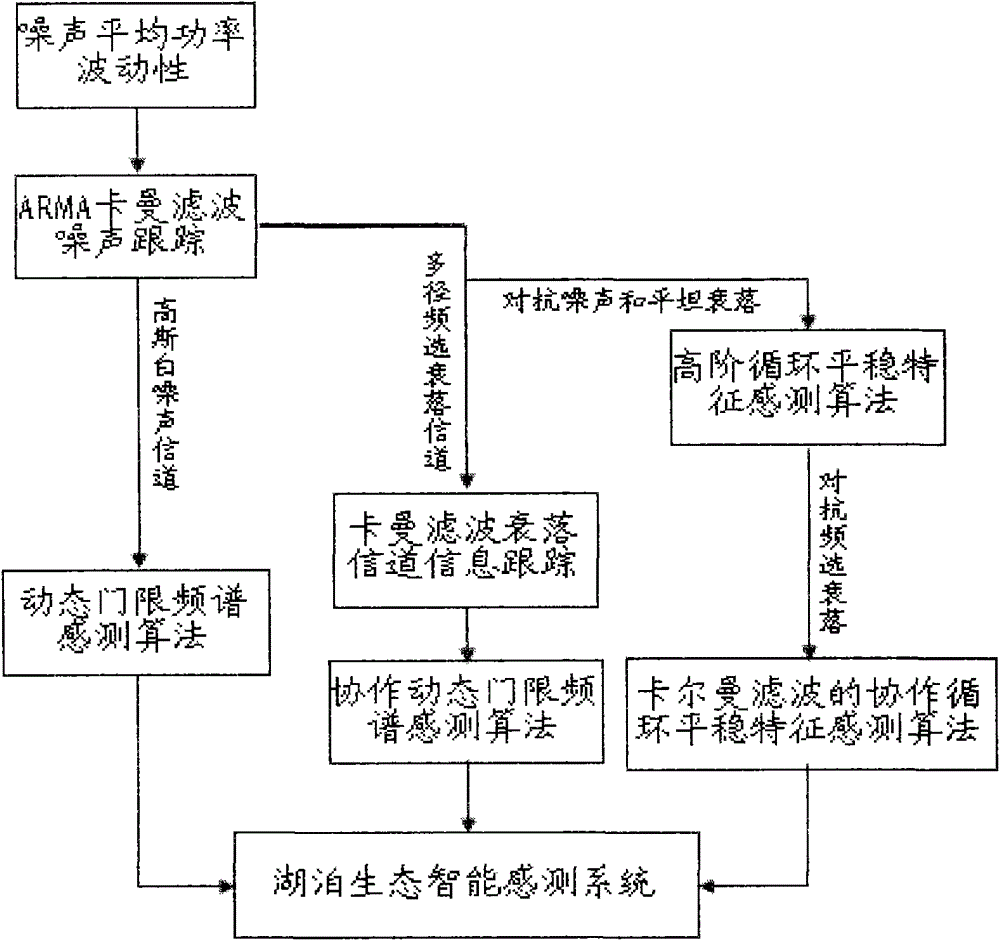
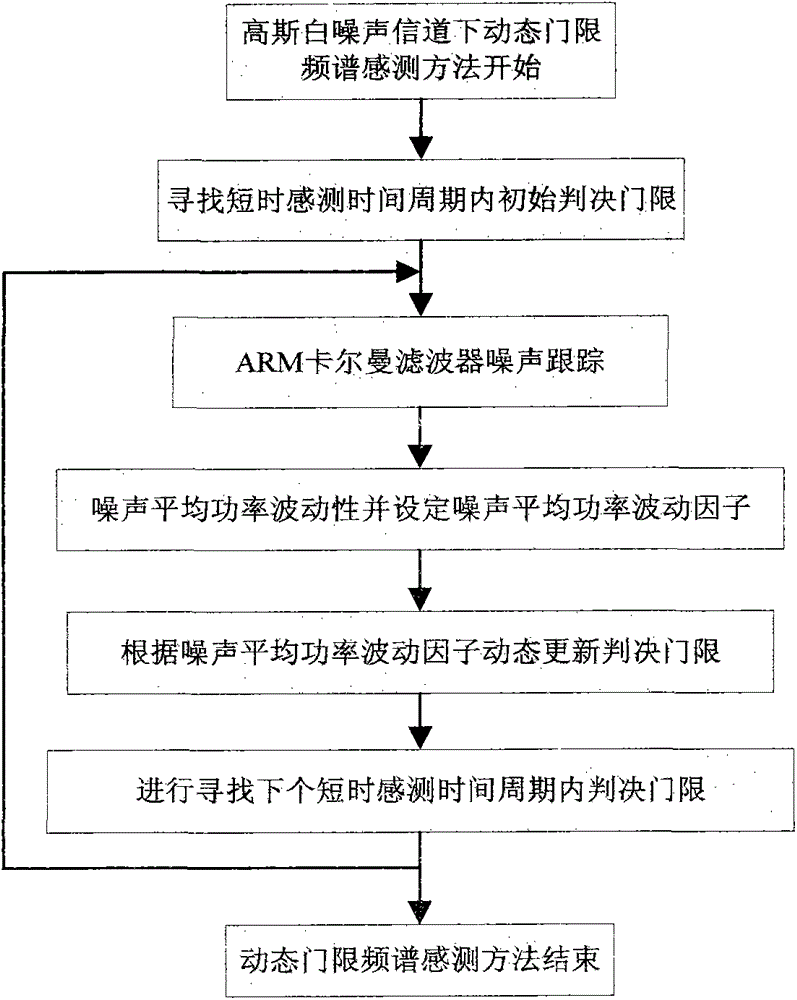
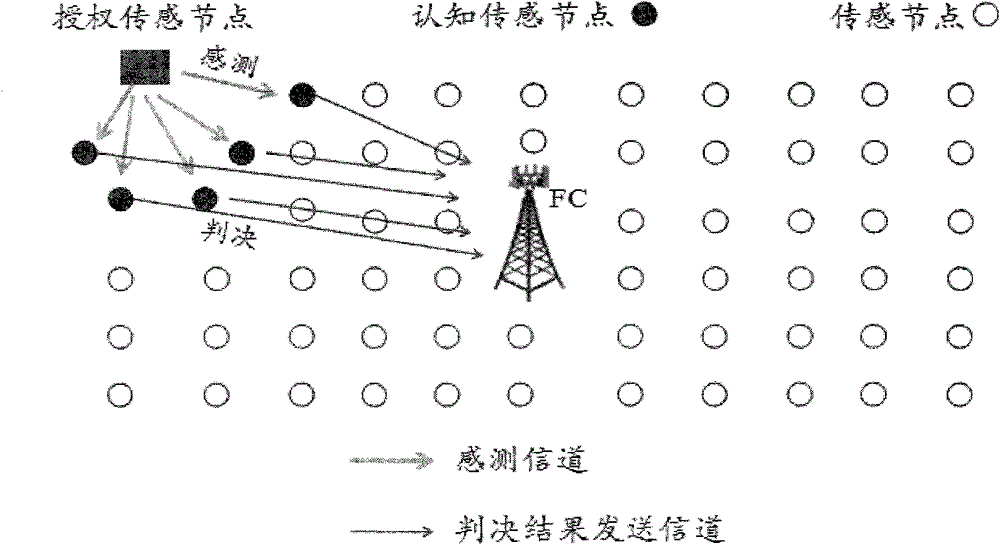
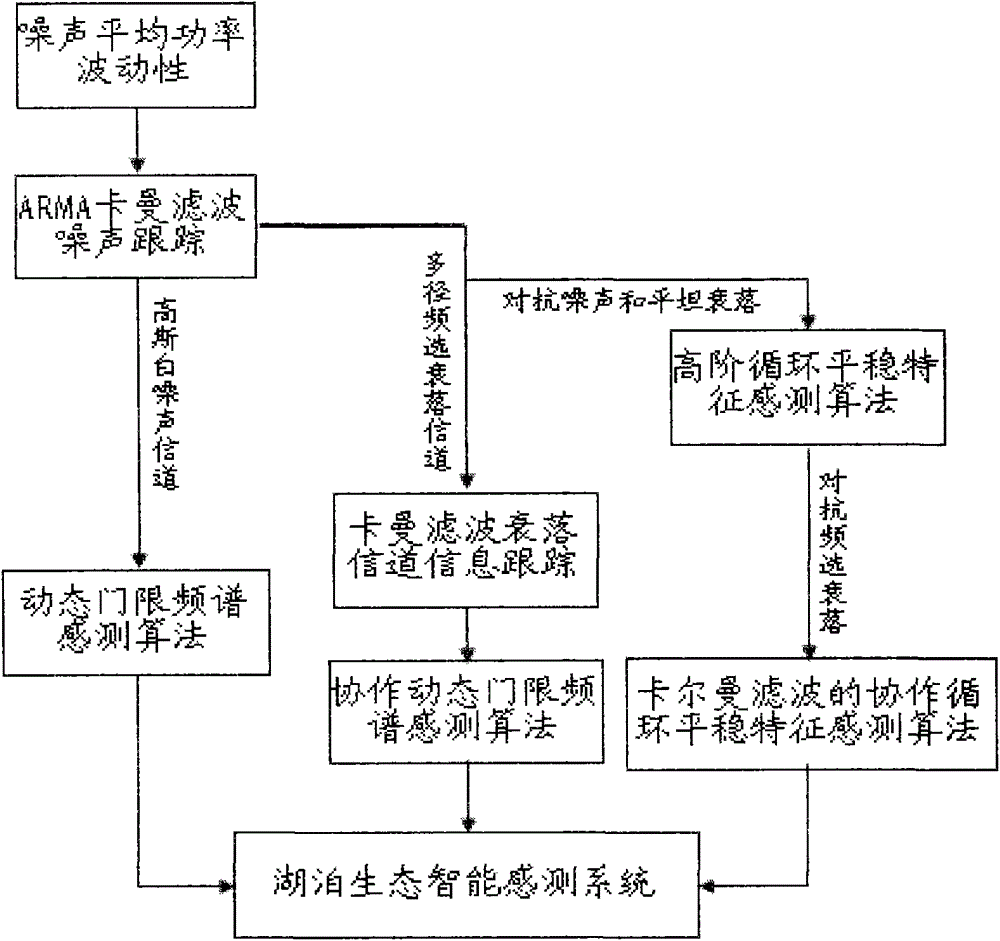
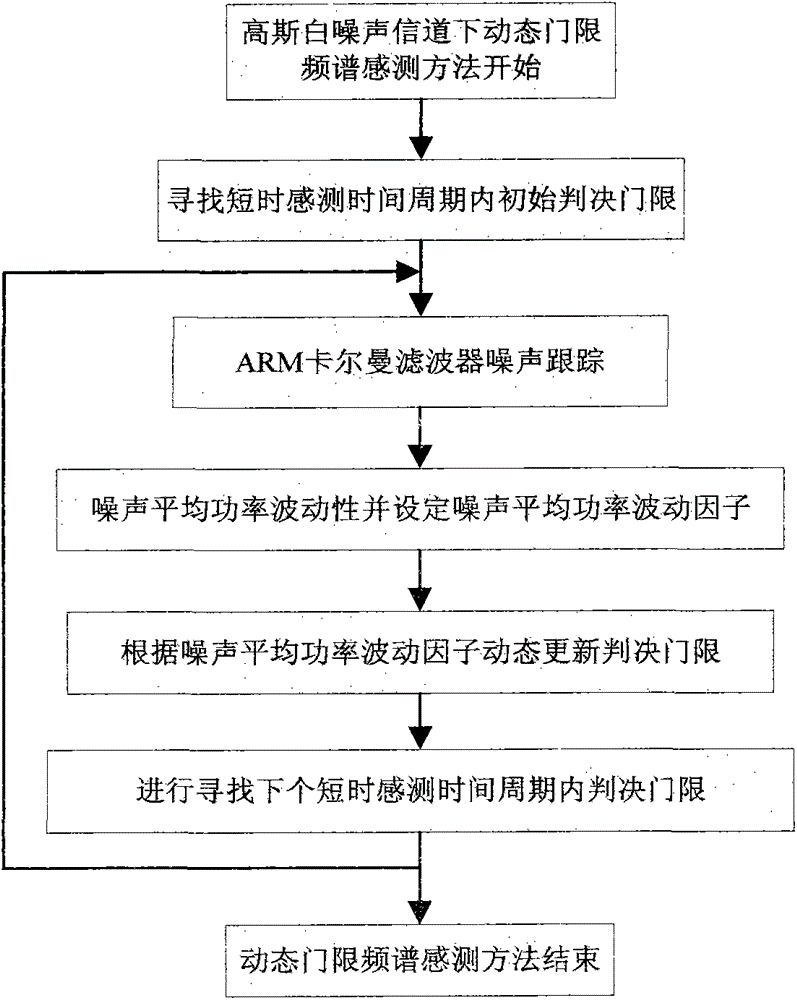
Lake Ecological Intelligent Sensing Method Based on Kalman Filter
InactiveCN103607250BAchieve concurrencyNetwork topologiesTransmission monitoringFrequency spectrumHigh density
The invention discloses a lake ecology intelligent sensing method based on Kalman filtering. The method comprises: giving noise mean power fluctuation; tracking noise by use of ARMA Kalman filtering; for a Gauss white noise channel, using a dynamic threshold frequency spectrum sensing method to perform intelligent sensing on the ecology; for a multipath frequency selection fading channel, using the Kalman filtering to perform correlation information tracking on a fading channel tracking method, and performing the intelligent sensing on the ecology through a cooperation dynamic threshold frequency spectrum sensing method; and for a Gauss white noise and flat fading channel, using a higher-order cycle stationary characteristic sensing method to perform sensing, and using the cooperation cycle stationary characteristic sensing method of the Kalman filtering to confront the frequency selection fading channel. The sensing method provided by the invention can effectively reduce the co-channel interference among high-density sensing nodes of a lake ecology monitoring perception system and enhance the concurrency of data transmission among sensing nodes.
Owner:NANCHANG UNIV
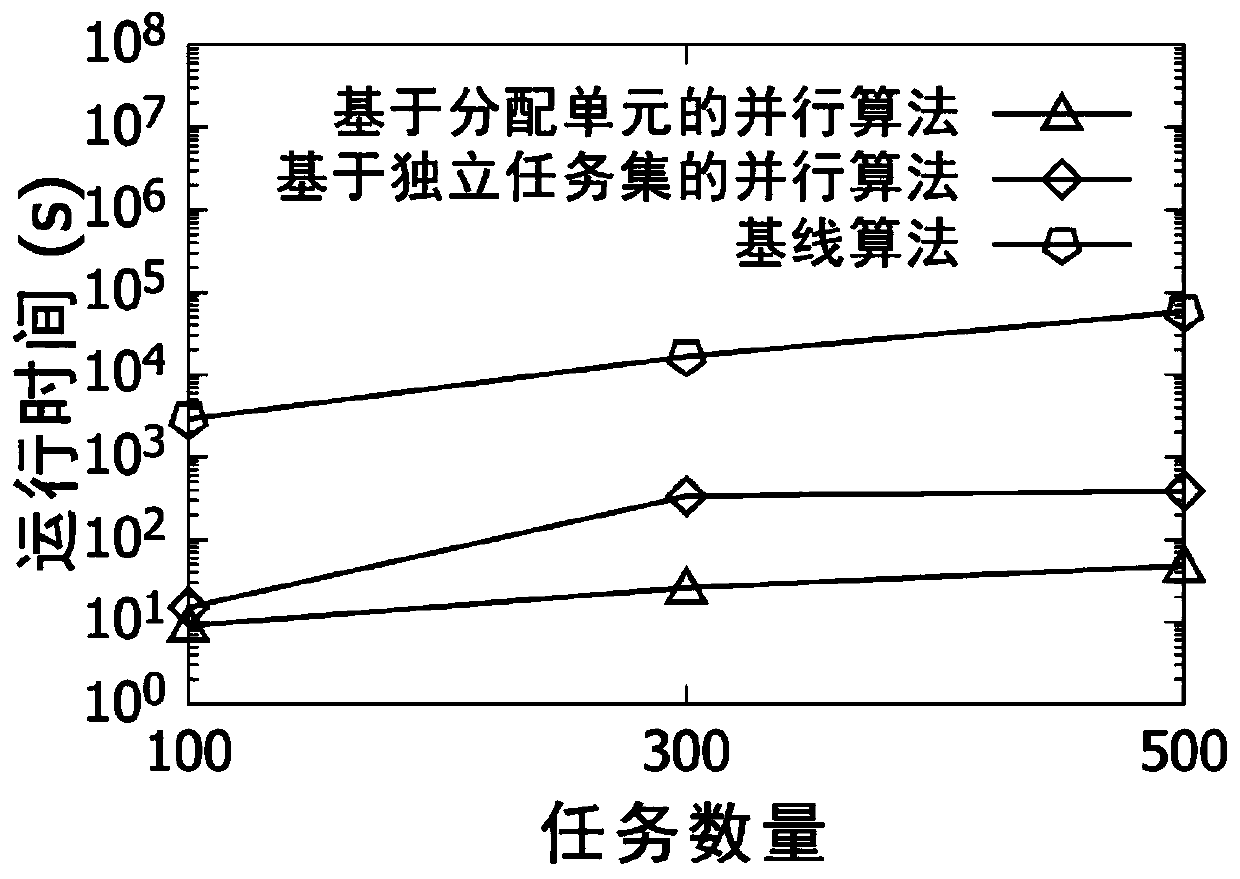
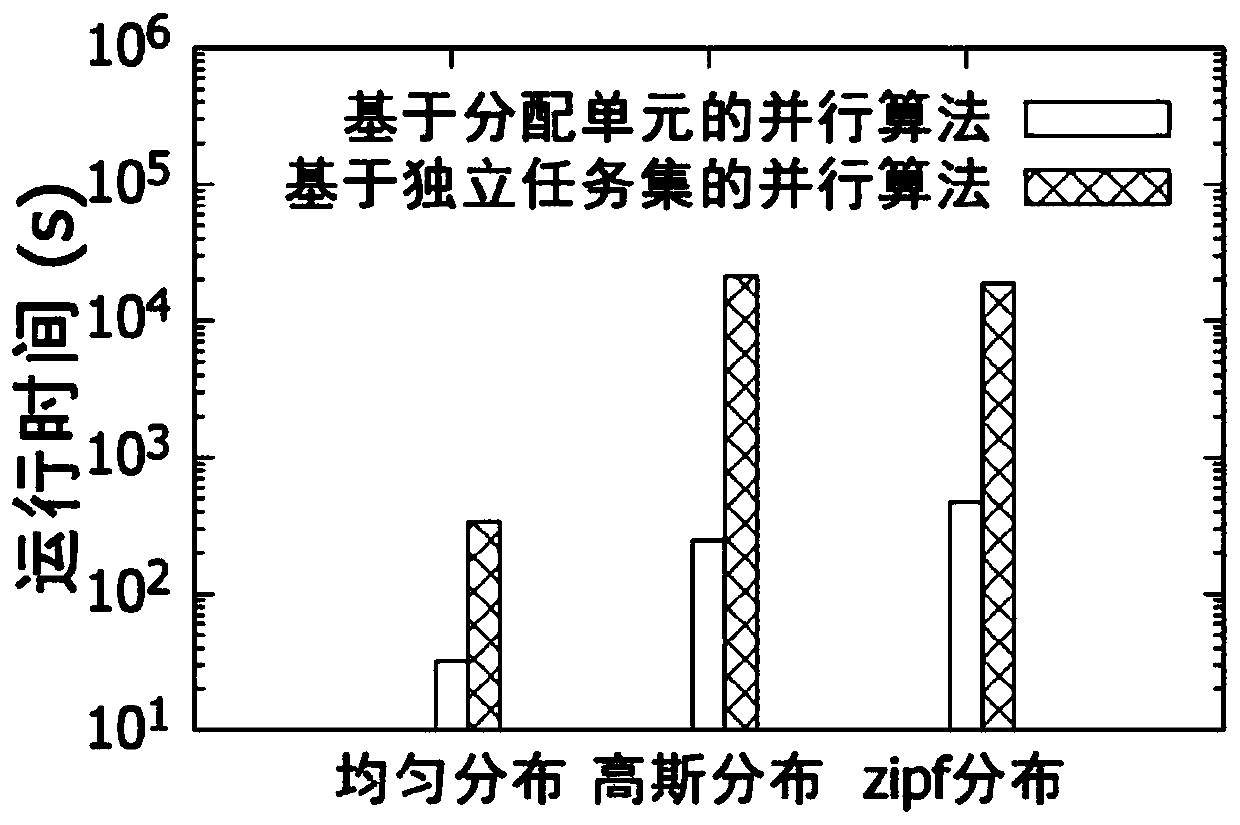
Time domain continuous space crowdsourcing efficient multi-task allocation method
InactiveCN110196763AAchieve concurrencyAchieve efficient distributionProgram initiation/switchingResource allocationTime domainParallel algorithm
The invention discloses a time domain continuous space crowdsourcing efficient multi-task allocation method. The method comprises the following specific steps of (1) a baseline algorithm, (2) a parallel algorithm based on an independent task set, and (3) a parallel algorithm based on an allocation unit. By the above time domain continuous space crowdsourcing efficient multi-task allocation method,after a plurality of crowdsourcing task requests are received at the same time, the total task quality needs to be maximized under the condition that the total task budget is limited, the distribution of a plurality of crowdsourcing tasks is completed, an efficient parallel framework is provided for processing the distribution conflicts, the concurrent and efficient distribution of the crowdsourcing tasks is achieved, and the method has the higher implementability and is more beneficial to practical application.
Owner:SUZHOU INST FOR ADVANCED STUDY USTC
A wireless communication network registration method and terminal
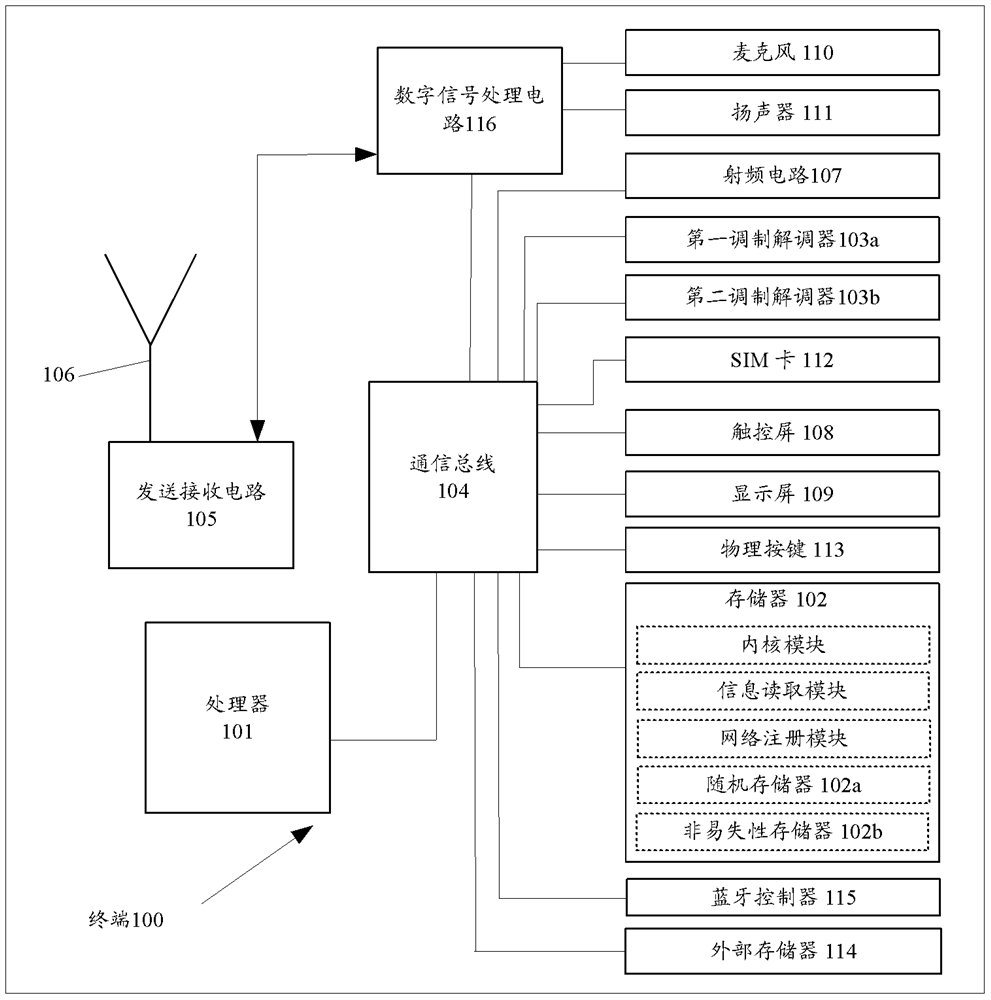
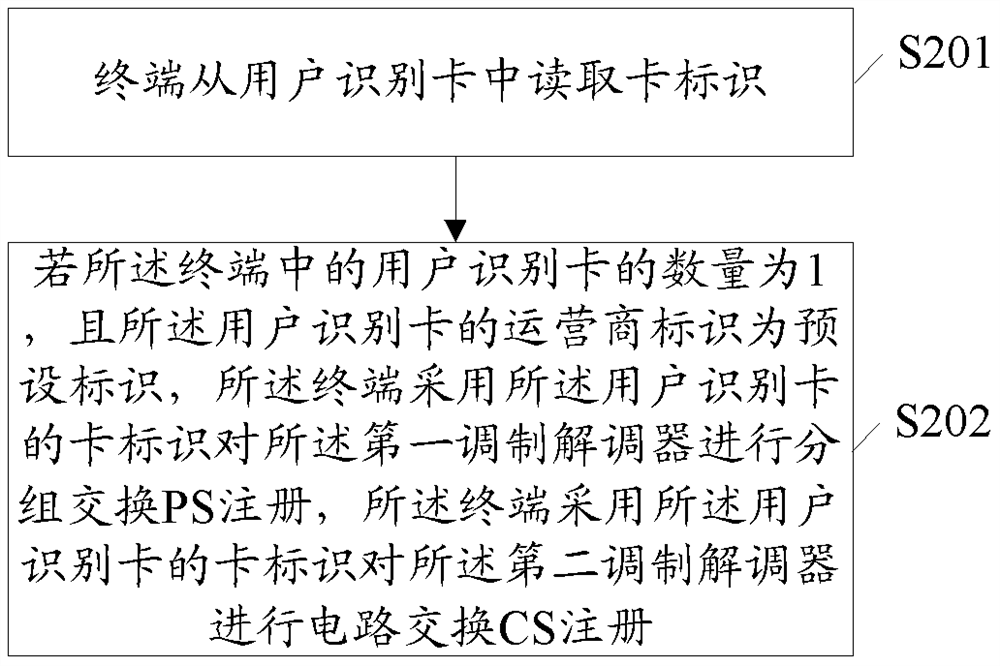
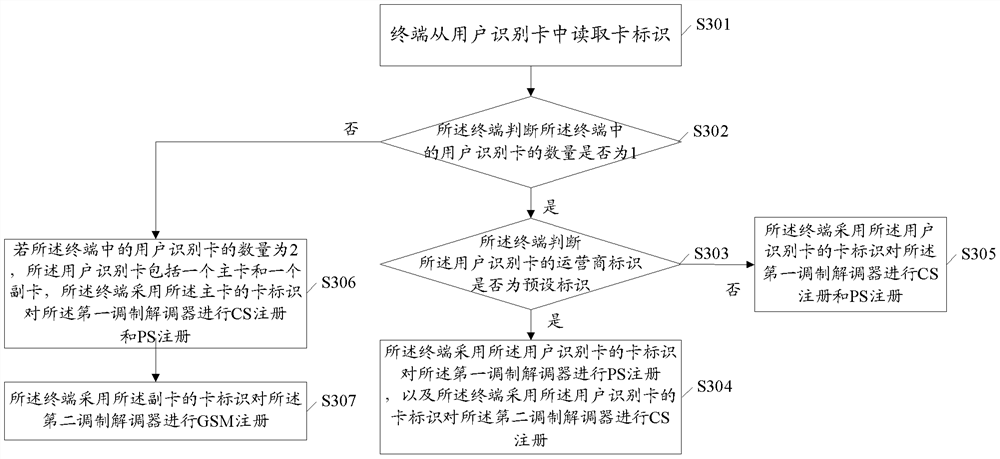
ActiveCN108432339BAchieve concurrencyImprove efficiencyAssess restrictionNetwork topologiesModem deviceEmbedded system
The invention discloses a wireless communication network registration method, which is applied to a dual-card dual-pass terminal. The terminal includes a first modem and a second modem, including: the terminal reads the card identification from the user identification card; if the The number of subscriber identification cards in the terminal is 1, and the operator identification of the subscriber identification card is a preset identification, and the terminal uses the card identification of the subscriber identification card to perform packet switching PS registration on the first modem The terminal uses the card identifier of the subscriber identification card to register the second modem with circuit switched CS. The embodiment of the present invention also provides a terminal. The embodiment of the present invention can solve the problem that the terminal in the prior art cannot implement concurrent data services and voice calls.
Owner:HONOR DEVICE CO LTD
Lake ecology intelligent sensing method based on Kalman filtering
InactiveCN103607250AReal-timeAchieve concurrencyNetwork topologiesTransmission monitoringPattern recognitionFrequency spectrum
The invention discloses a lake ecology intelligent sensing method based on Kalman filtering. The method comprises: giving noise mean power fluctuation; tracking noise by use of ARMA Kalman filtering; for a Gauss white noise channel, using a dynamic threshold frequency spectrum sensing method to perform intelligent sensing on the ecology; for a multipath frequency selection fading channel, using the Kalman filtering to perform correlation information tracking on a fading channel tracking method, and performing the intelligent sensing on the ecology through a cooperation dynamic threshold frequency spectrum sensing method; and for a Gauss white noise and flat fading channel, using a higher-order cycle stationary characteristic sensing method to perform sensing, and using the cooperation cycle stationary characteristic sensing method of the Kalman filtering to confront the frequency selection fading channel. The sensing method provided by the invention can effectively reduce the co-channel interference among high-density sensing nodes of a lake ecology monitoring perception system and enhance the concurrency of data transmission among sensing nodes.
Owner:NANCHANG UNIV
Method and system for realizing parallel transmission of broadcast/multicasting service and special service
InactiveCN101257374BAchieve concurrencyBroadcast service distributionTelecommunicationsService development
The invention provides a method for realizing the concurrent of broadcast / multicast service. The method comprises: the user equipment (UE) transmits the frequency ID indicating the broadcast / multicastservice to the radio network controller (RNC); RNC obtains the frequency of the broadcast / multicast service based on the ID and configures the specific service to the frequency resource of the broadcast / multicast. The invention also provides a system realizing the broadcast / multicast service and the specific service development, comprising UE and RNC. Because UE in the inventive embodiment transmits the ID indicating the operating frequency of the broadcast / multicast service to RNC at the network, RNC acquires the frequency of the broadcast / multicast service based on the ID and configures thespecific service to the frequency resource of the broadcast / multicast service so as to lead UE to receive broadcast / multicast service and specific service at the same frequency and realize the development of the broadcast / multicast service and the specific service.
Owner:TD TECH COMM TECH LTD
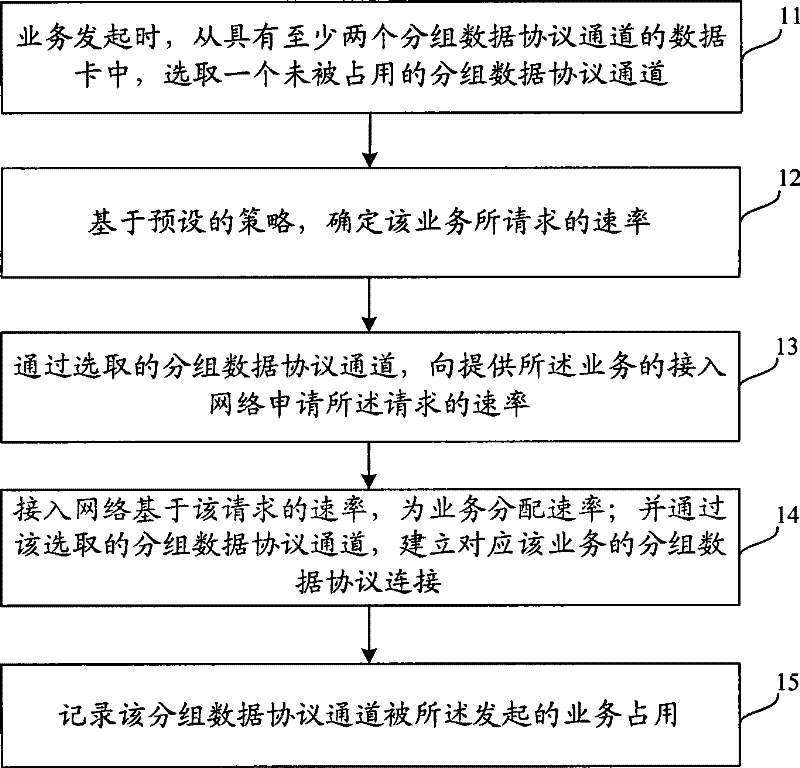
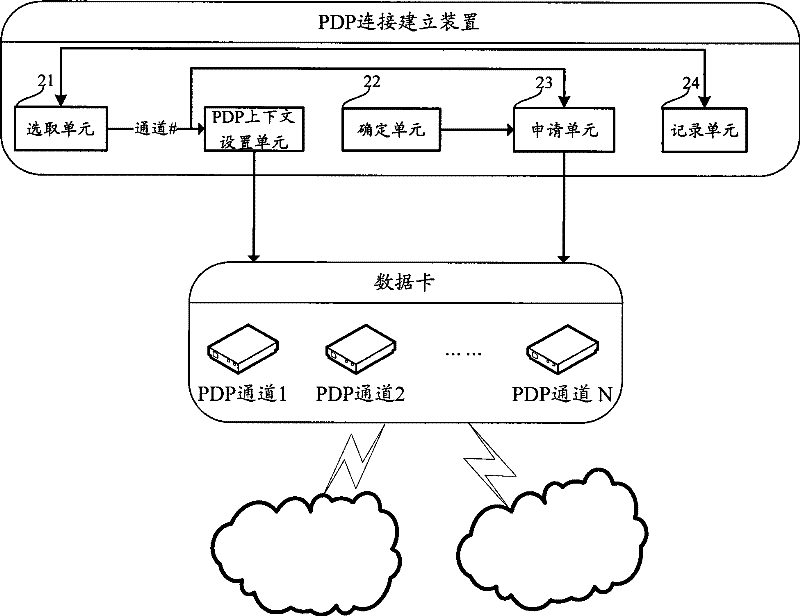
Method for establishing connection of grouped data protocol and device thereof
InactiveCN101662452BAchieve concurrencyImprove experienceData switching networksAccess networkEngineering
The invention discloses a method for establishing connection of grouped data protocol. The method comprises the following steps: selecting an unoccupied grouped data protocol channel from a data card having at least two grouped data protocol channels during initiating a current service; determining a rate required by the service on the basis of a preset strategy; applying to an access network of the service for the required rate through the selected grouped data protocol channel; allocating a rate for the service by the access network on the basis of the required rate; and establishing grouped data protocol connection corresponding to the service through the selected grouped data protocol channel. Accordingly, the invention also discloses a grouped data protocol connection device. The scheme of the invention can establish a plurality of grouped data protocol PDP connections at the same time, thereby realizing parallel development of multiple services, increasing efficiency and networkutilization rate and upgrading user experience.
Owner:CHINA MOBILE COMM GRP CO LTD
A method and device for real-time virtual reproduction of remote sound field
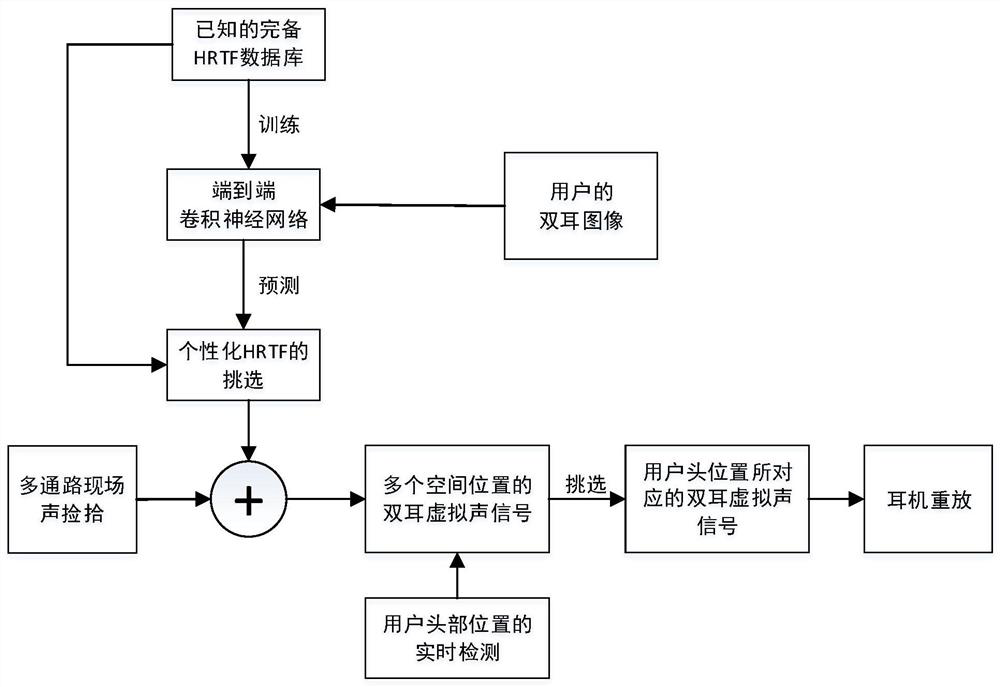
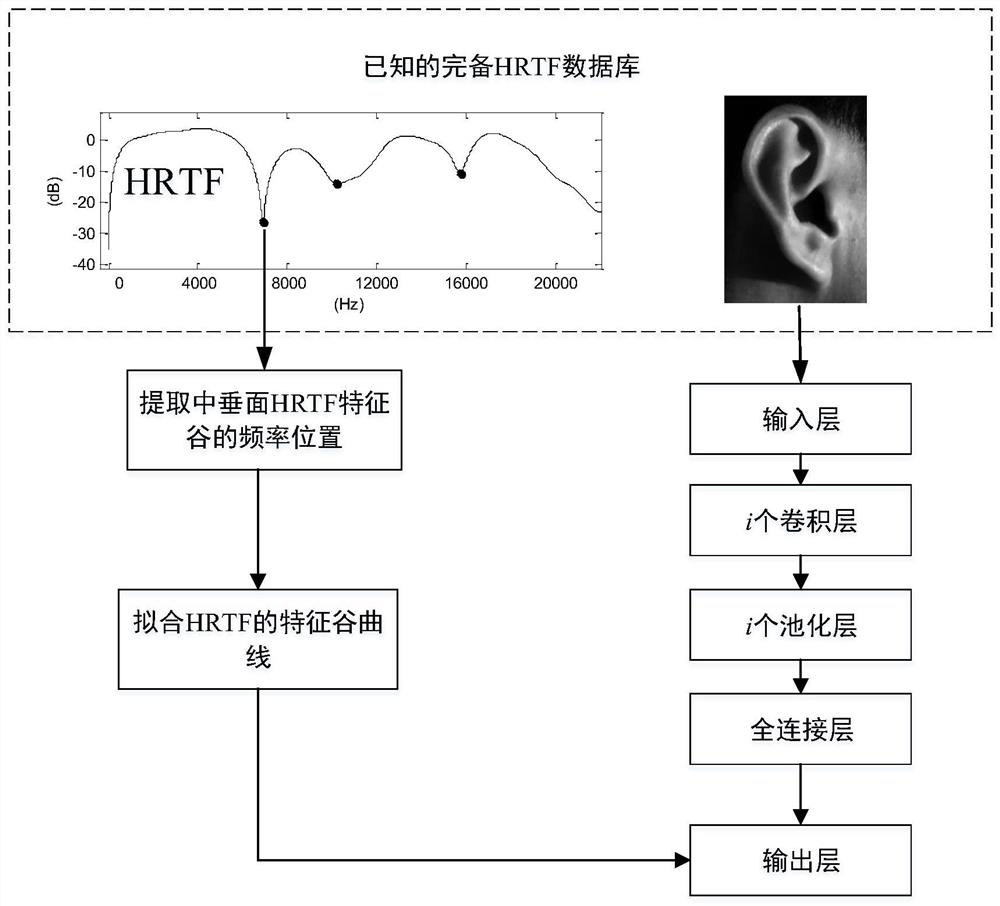
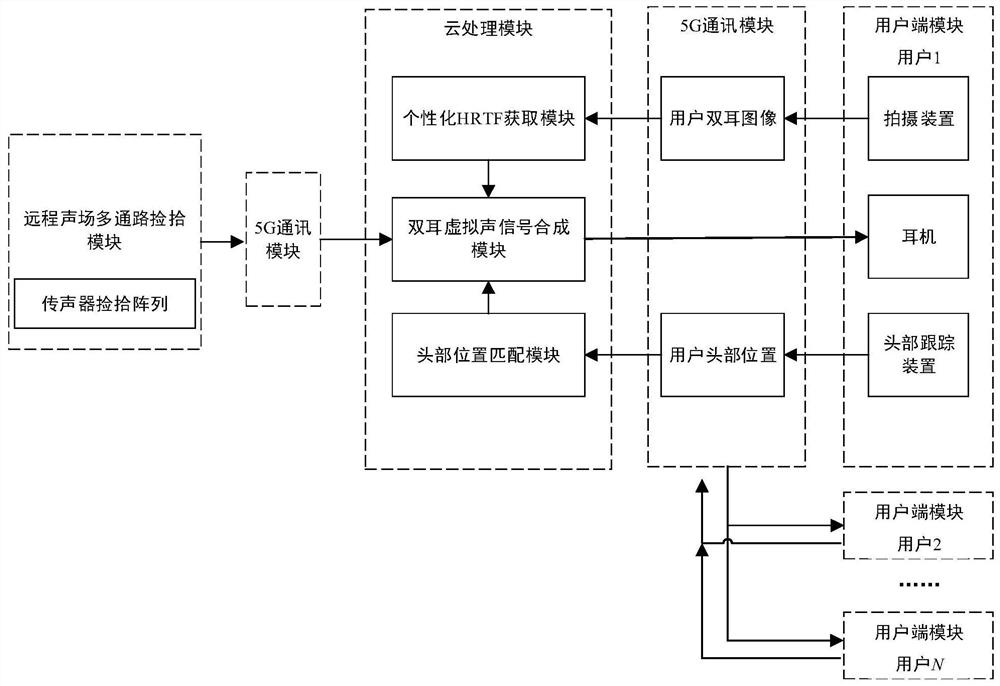
ActiveCN111246345BImprove perception accuracyEnhanced sense of presenceStereophonic circuit arrangementsPseudo-stereo systemsPersonalizationCloud processing
The invention discloses a method and device for real-time virtual reproduction of a remote sound field. The method includes: (1) Using an end-to-end convolutional neural network to infer the personalized elevation angle positioning factor from the user's ear image, and based on this, the general HRTF is customized, and the customized personalized HRTF is further applied Based on the synthesis of binaural virtual sound signals; (2) Based on the real-time detection of the user's head position, the playback of dynamic binaural virtual sound signals that track the head position is realized. The above-mentioned personalized customization and real-time dynamic virtual sound signal processing method can enhance the user's sense of presence and immersion. The device includes a remote sound field multi-channel pickup module, a cloud processing module, a client module and a 5G communication module. The implementation of the present invention is based on cloud computing technology and 5G network transmission, which can effectively reduce the computing load of the user end and meet the parallel requirements of multiple users. The present invention can be regarded as a sound module solution based on virtual reality of mobile portable equipment.
Owner:SOUTH CHINA UNIV OF TECH
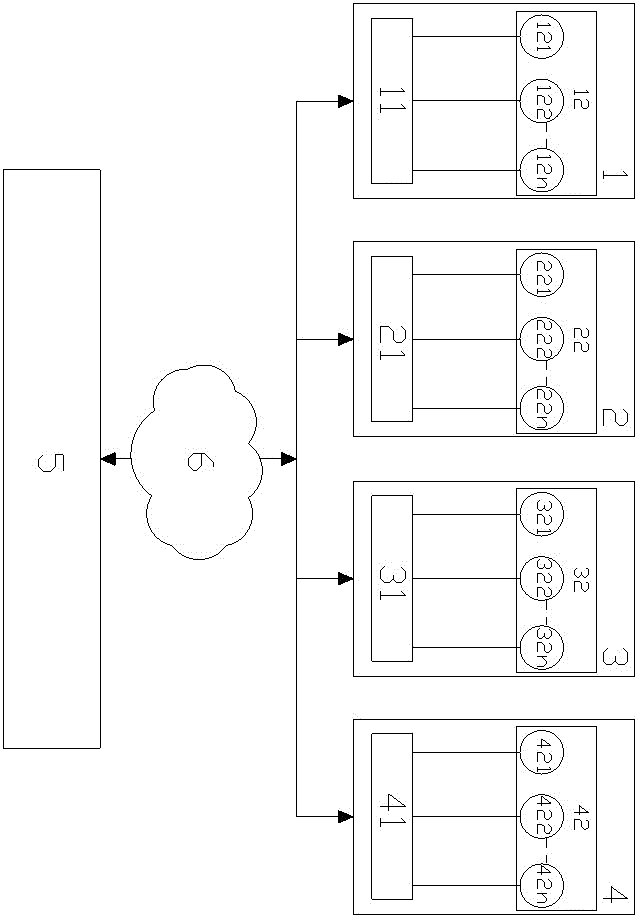
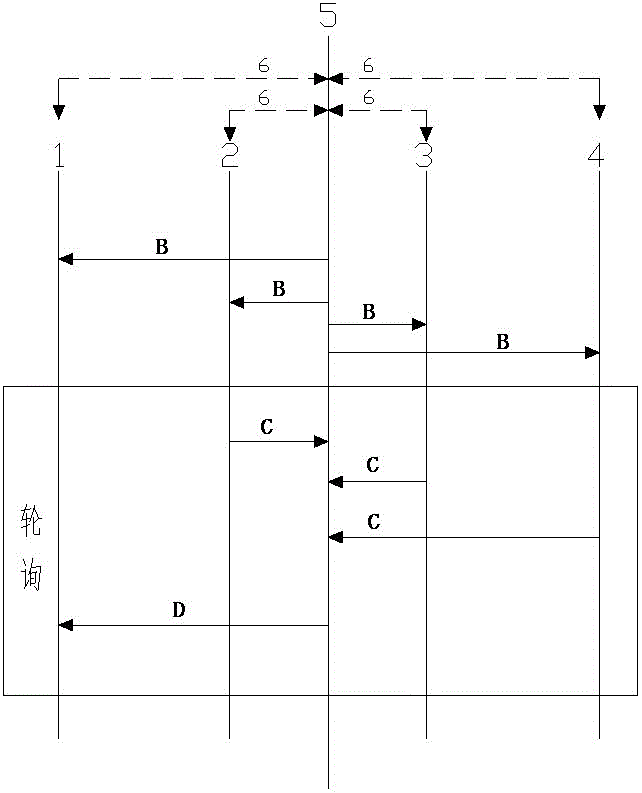
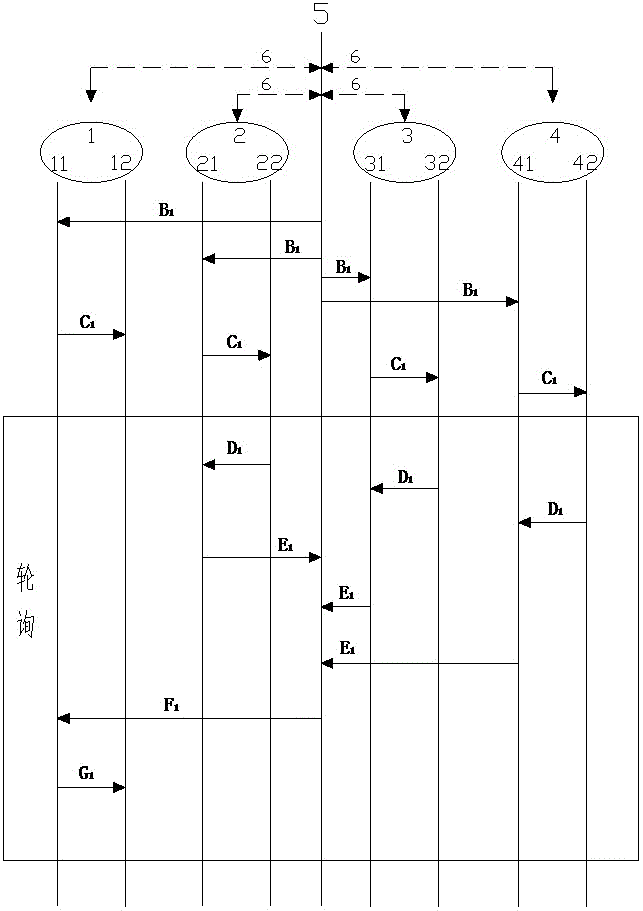
A Communication Method for Integrating Multiple Conference Systems with Low Bandwidth
ActiveCN103841361BReal-time meeting situationLower access costsTelevision conference systemsClosed circuit television systemsVideo monitoringCommunications system
The invention relates to a communication method for integrating various conference systems under low bandwidth, including a hardware video conference system, a software video conference system, a voice conference system, a video monitoring system, and a multipoint control center. The multipoint control center, as a super user, can Perform overall control over each conference system, establish a connection and retrieve audio and video data after arbitrarily specifying the participating users, and use its built-in protocol capability set to perform data interaction and unified processing, and then output data in the form of preset priorities to match Adapt to the minimum bandwidth of the transmission data format to ensure the data transmission under the minimum bandwidth. At the same time, after the conference connection is established, the multi-point control center polls the conference in real time, which not only ensures the real-time detection of the conference situation, but also provides support for low-bandwidth Integration provides the foundation. The communication method of the present invention solves the technical problems that communication systems in the construction industry are applied independently of each other, data cannot communicate with each other, high bandwidth requirements, large deployment costs, and poor compatibility.
Owner:SHANXI FIRST CONSTR GROUP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com