Edge computing data security and privacy protection method based on Fabric
An edge computing and privacy protection technology, applied in the field of edge computing and blockchain technology, can solve problems such as database damage, data leakage, data loss, etc., and achieve the effect of improving accuracy, security, and protection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] Attached below Figure 1-3 The present invention is further described with example:
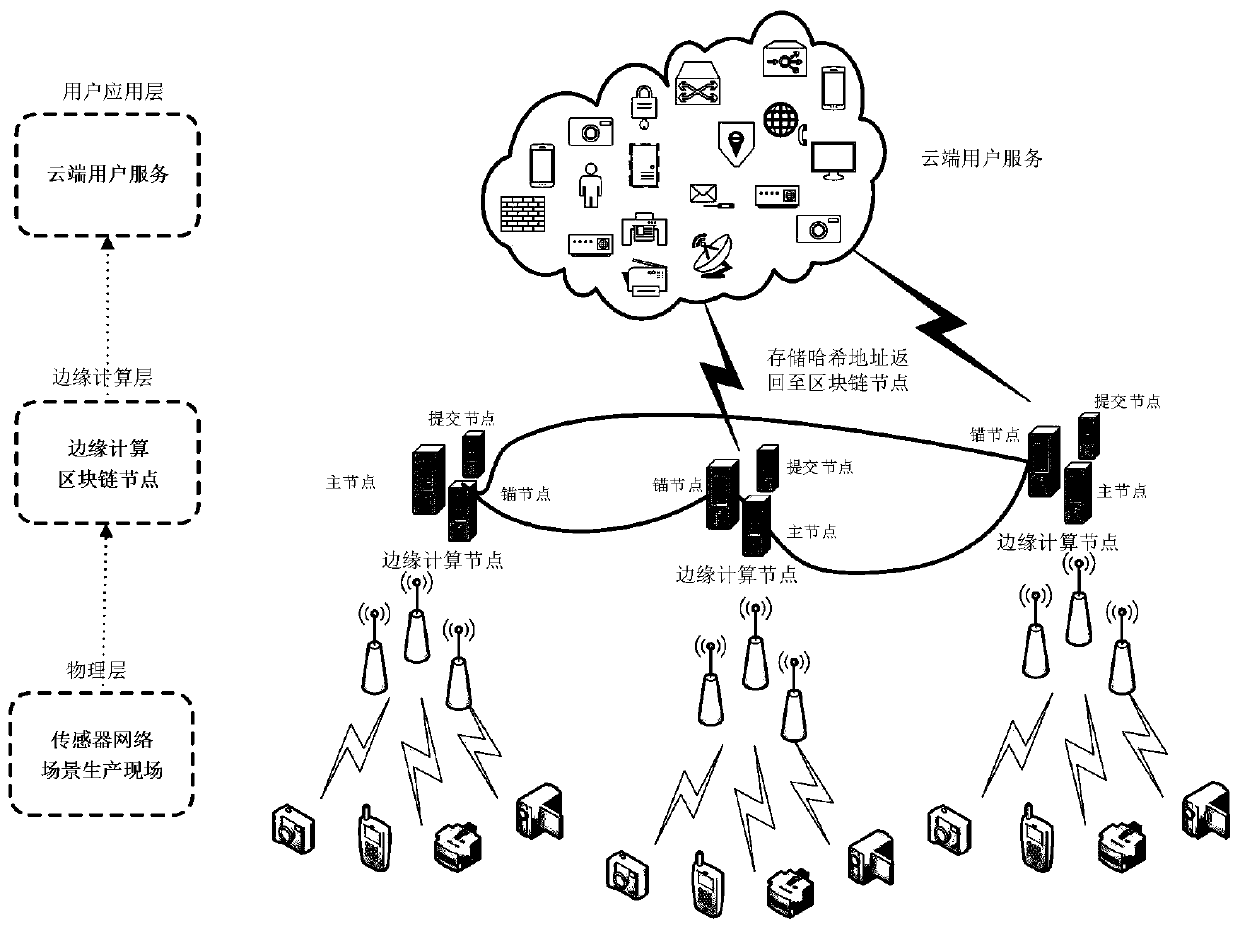
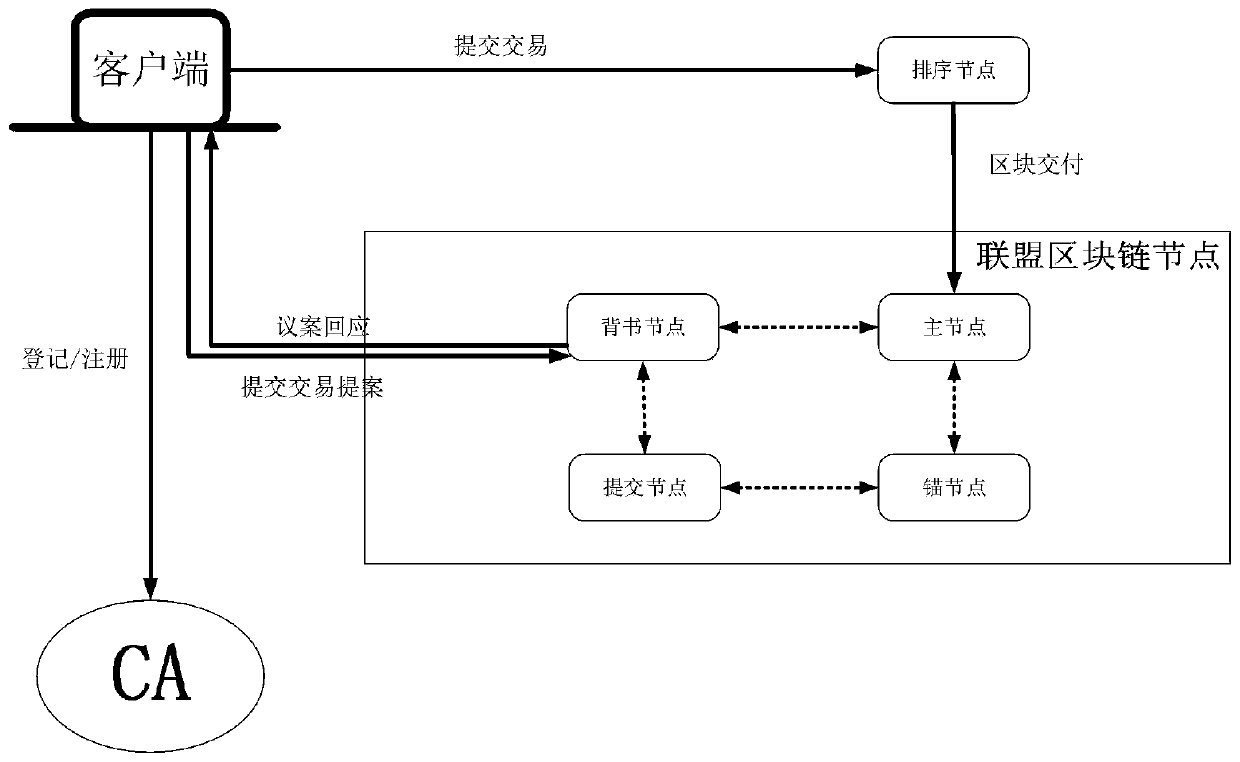
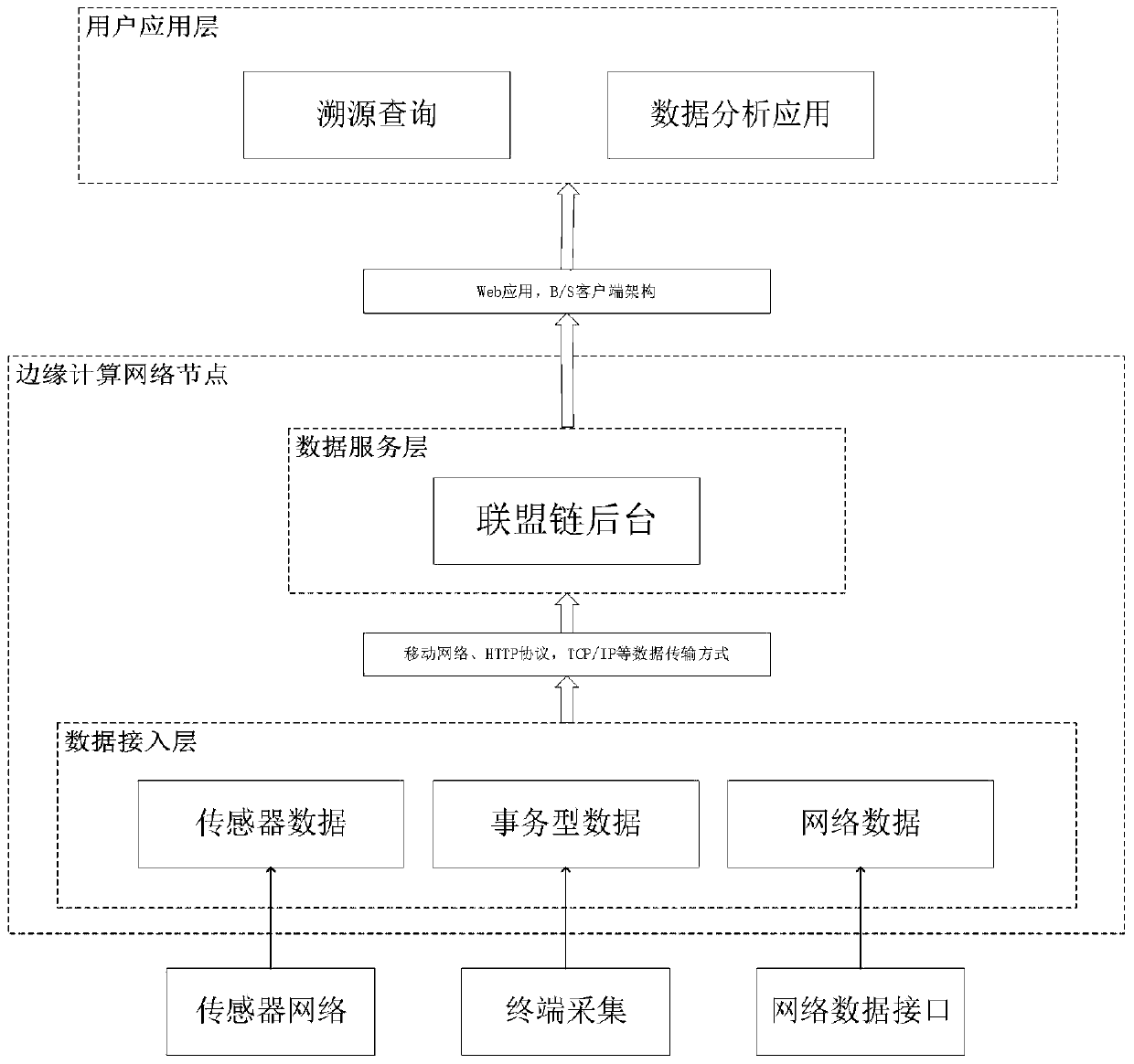
[0023] The present invention provides a Fabric-based edge computing data security and privacy protection method, the system logic architecture diagram is as follows image 3 As shown, the raw data of the Internet of Things is collected first, and the data access layer of the edge computing network node receives the collected Internet of Things data. Send the data to the Fabric background on the edge computing node through the mobile network, HTTP protocol, TCP / IP and other data transmission methods, organize the data into standardized data in json format, and upload the standardized data to Fabric. Users can perform operations such as traceability or data analysis on the data in Fabric through the web application or B / S client architecture.
[0024] Specifically include the following steps:
[0025] Step 1: IoT data collection;
[0026] Step 1.1 Through sensor collection, mobile ph...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com