Trusted wireless storage equipment for wireless power supply and application method thereof
A storage device and wireless power supply technology, applied in the field of information security, to achieve the effect of ensuring security issues, reducing energy consumption, and improving operating efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0075] Device selection:
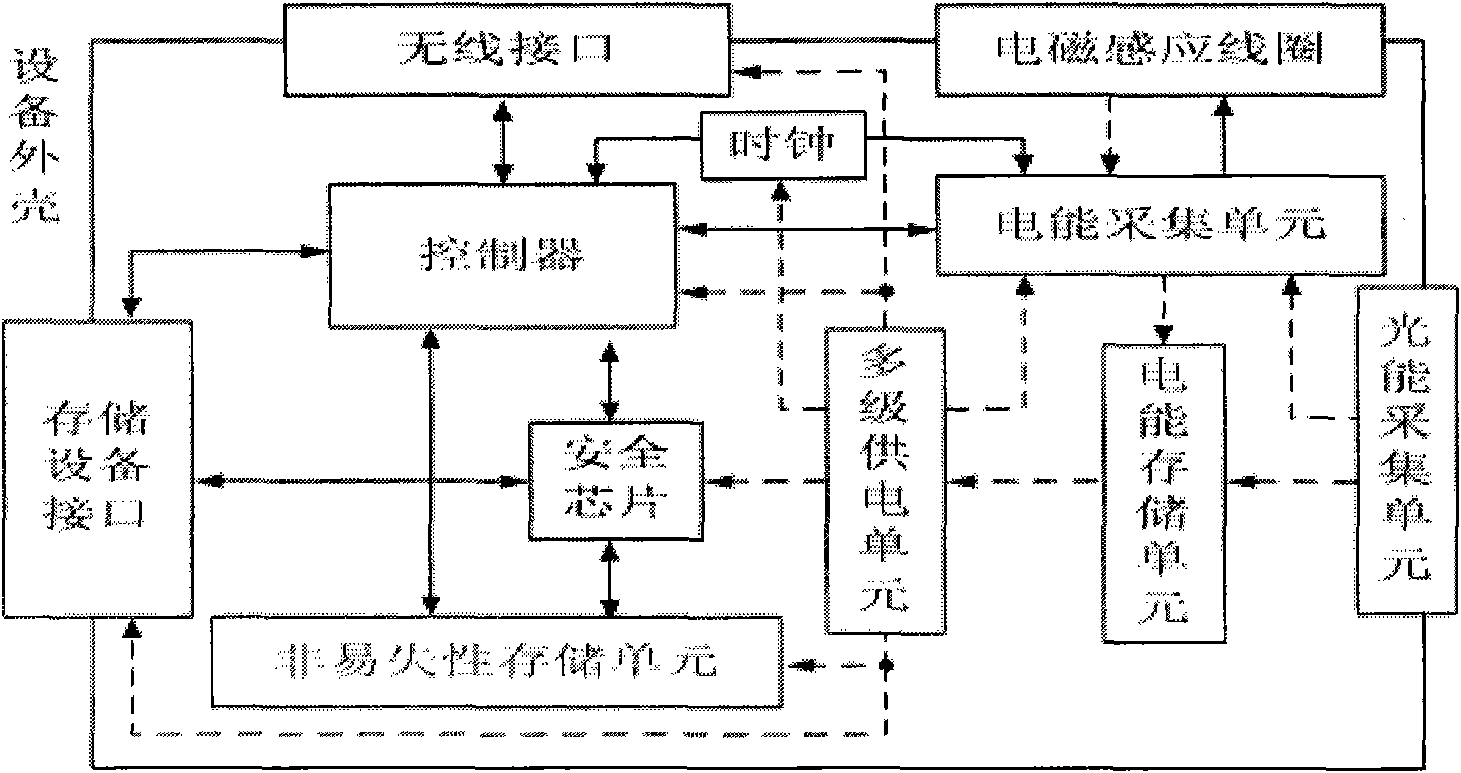
[0076] Controller: use CPU as OMAP3530 CORTEX-A processor
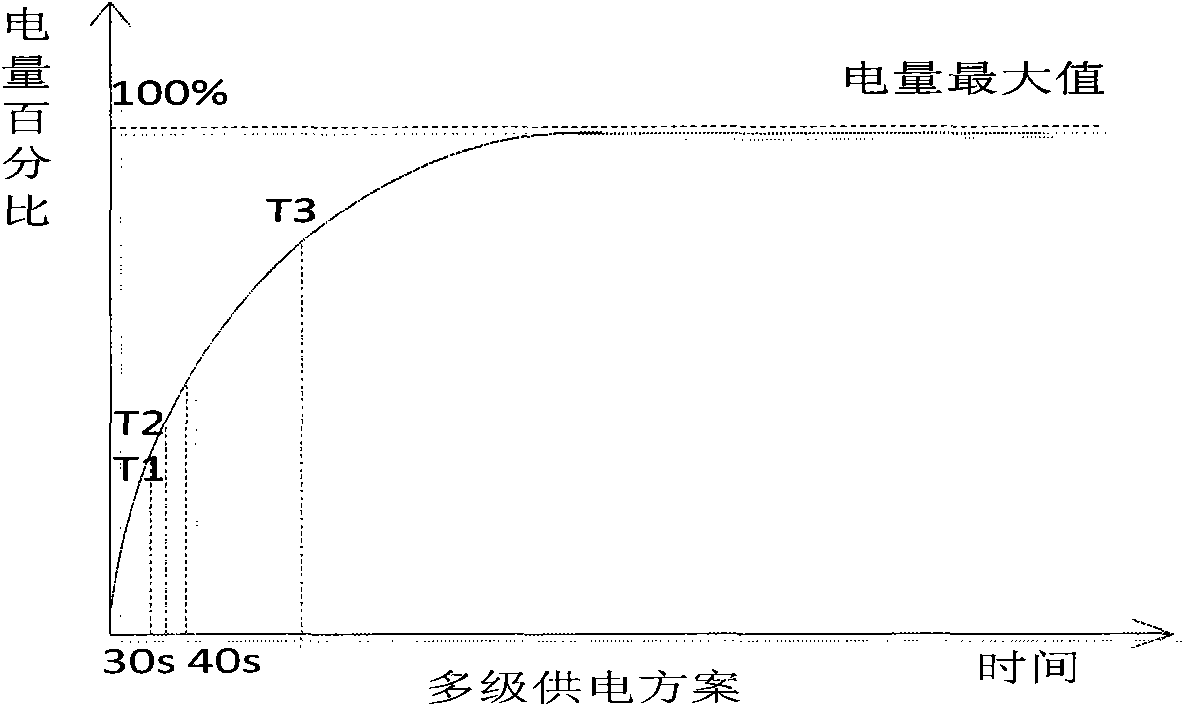
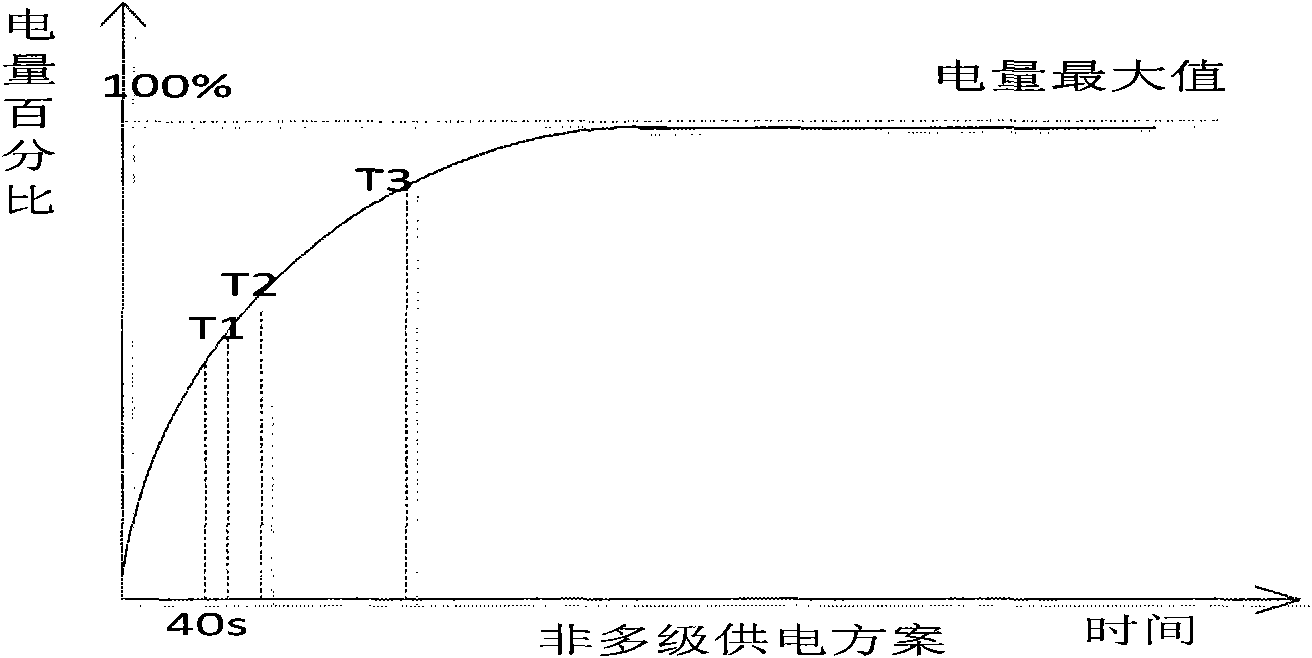
[0077] Electric energy acquisition unit: responsible for controlling the induction frequency of the electromagnetic induction coil, and responsible for controlling the energy storage operation of the electric energy storage unit.
[0078] Multi-stage power supply unit: refer to Linear LTC2978 chip
[0079] Security chip: ZTE SSX44 trusted cryptographic module security chip
[0080] Non-volatile storage unit: Jinxun Xingye EEPROM 24C16
[0081] Light energy collection unit: No. 23 solar panel 5V35MA of Guangzhou Fuji Solar Technology Co., Ltd.
[0082] Wireless interface:
[0083] Chip selection: Broadcom BCM43225 open source chipset, communication protocol selection 801.11n protocol, using MIMO (multiple input multiple output technology) theoretical speed up to 300M, actual transmission speed between 80-150M. No wireless encryption technology is used.
[0084] Storage device interface,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com