Method for determining inquiry answer type bidirectional identification and business, and encipher device applying the method
An encryption device and identity confirmation technology, applied in the direction of secure communication device, data processing application, transmission system, etc., can solve the problem of not being tampered and deceived.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
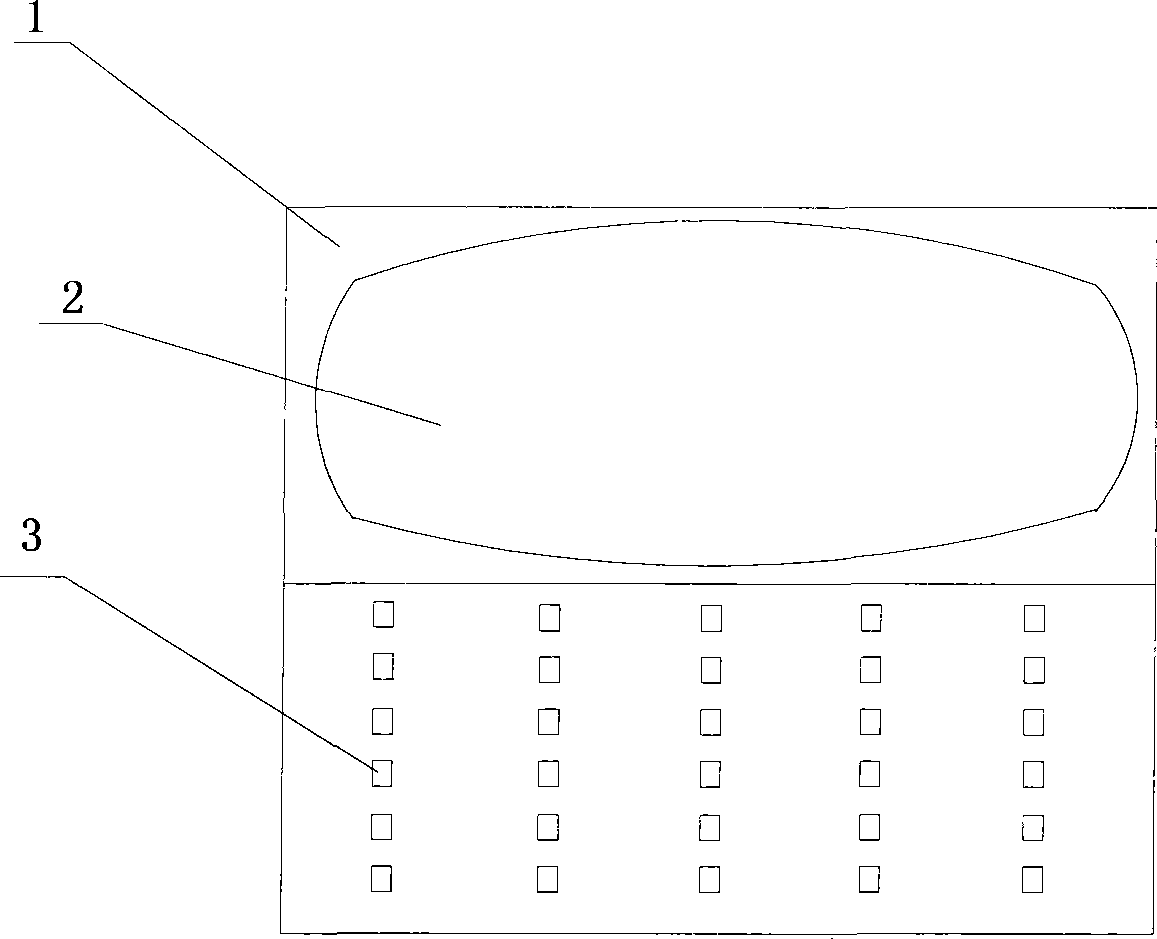
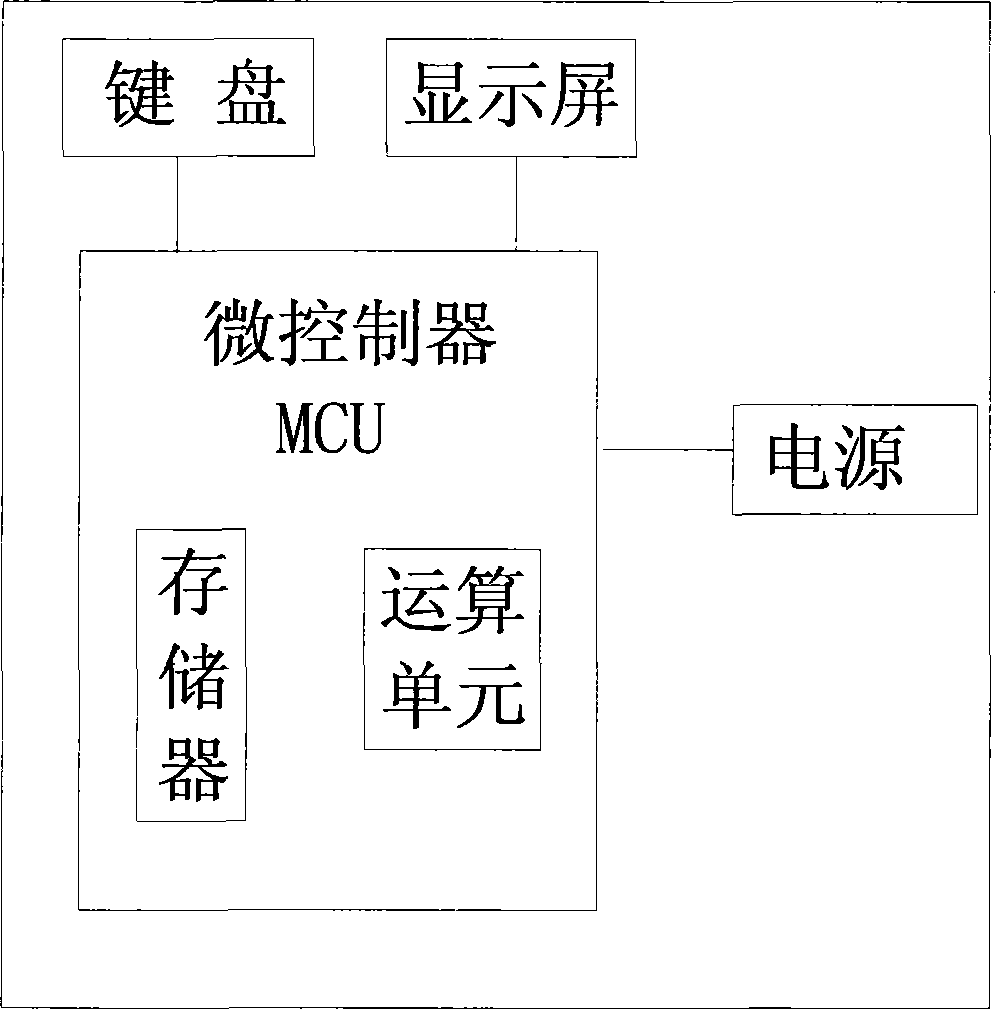
[0083] Using the two-way authentication method of the two parties of the transaction using the encryption device 1, the authentication method includes identity confirmation, and the identity confirmation includes the following steps:
[0084] (a) The customer service provider distributes independent encryption devices to dedicated customers;
[0085] (b) The user connects to the server through the network or telephone and enters the customer account number K;
[0086] (c) The server retrieves the server password Mo and the encryption algorithm Fo indicating the identity of the server according to the client account K;
[0087] (d) The server generates a random number N, calculates the encrypted result Q, Q=Fo(K, Mo, N), and displays N and Q to the user;
[0088] (e) The user inputs his account number K, random number N and encryption result Q on the encryption device;
[0089] (f) The encryption device calls the encryption algorithm fo of the verification server that comes w...
Embodiment 2
[0096] Using the two-way authentication method of the two parties of the transaction using the encryption device 1, the authentication method includes identity confirmation and transaction content confirmation, the identity confirmation is the same as the steps in embodiment 1, and the transaction content confirmation includes the following steps:
[0097] (A) The user enters the account T of the other party online;
[0098] (B) The server generates a random number Y, and calculates Q'=Fo(T, Mo, Y), and displays Y and Q' to the user;
[0099] (C) The user inputs T, Y and Q' on the encryption device;
[0100] (D) The encryption device invokes the encryption algorithm fo, and uses the mo stored on the encryption device to calculate the encryption result q', q'=fo(T, mo, Y);
[0101] (E) The encryption device compares q' and Q', if they are equal, it means that mo=Mo, fo=Fo, and the T value has not been tampered with, the server is not a trap, continue; if they are not equal, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com