Method and system for online security trading
A safe transaction and legal technology, applied in the field of information security, to achieve the effect of restricting replay attacks, increasing security, and ensuring smooth progress
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
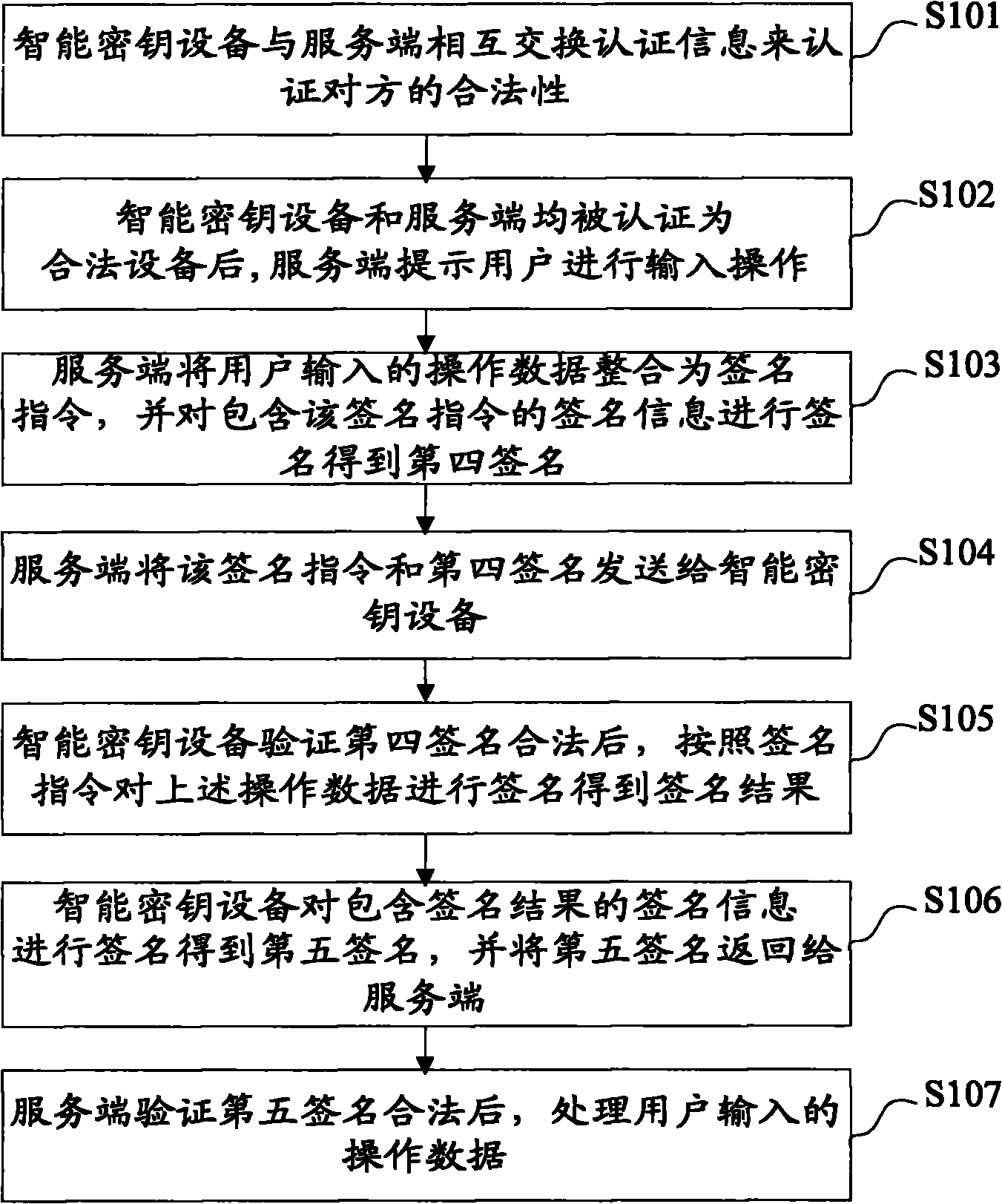
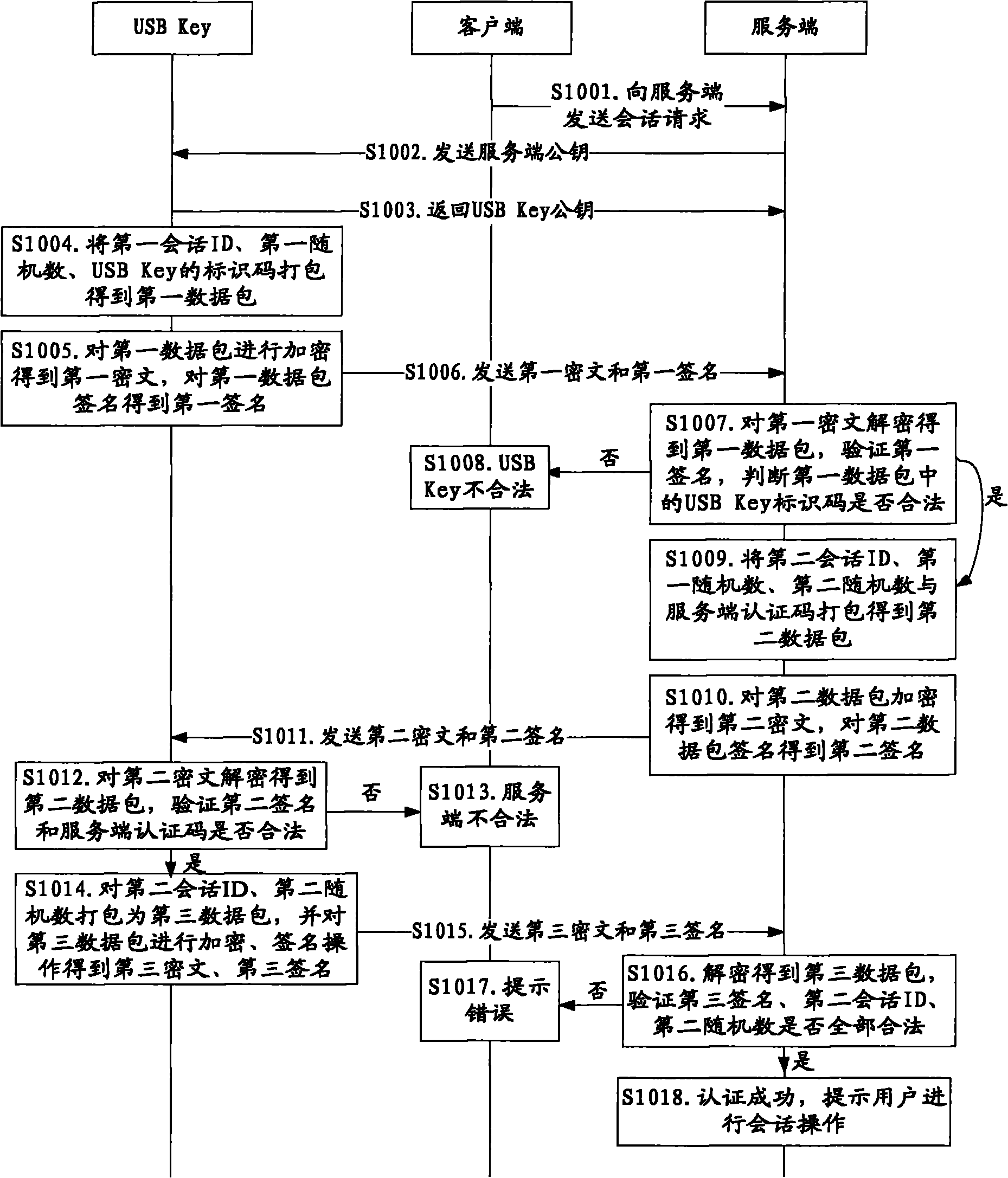
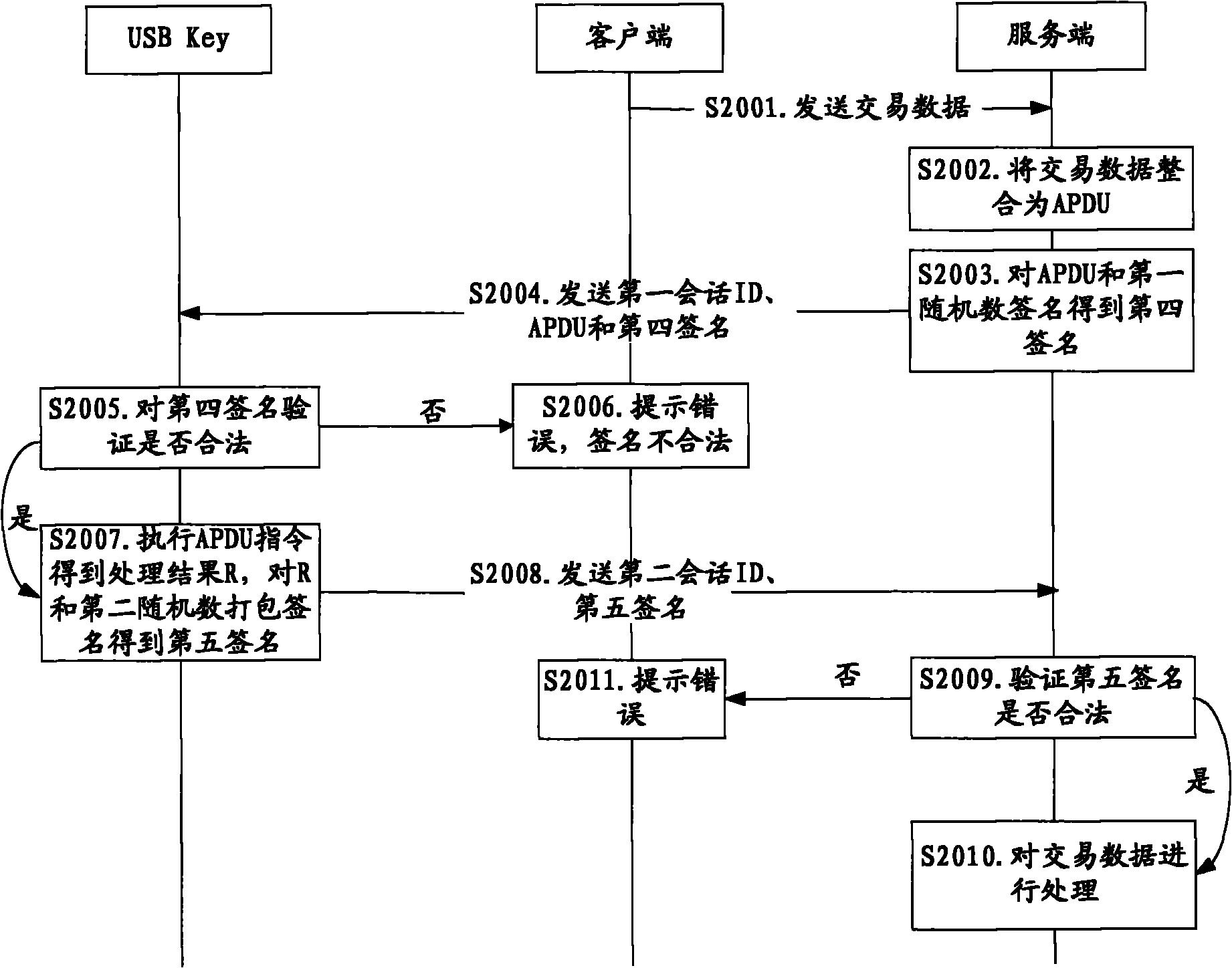
[0084] figure 2 and image 3 It is a flow chart of the online secure transaction method in Embodiment 1 of the present invention. Such as figure 2 and image 3 As shown, an online secure transaction method is provided. In this embodiment, a USB Key is used as a smart key device, and an example is illustrated by taking a user to conduct online banking transactions through a USB Key. A unique identification code is written inside the USB Key. It is used to authenticate the legality of the USB Key, and there is a server authentication code stored in the USB Key, which can be used to judge the legitimacy of the server, and at the same time, the legal server stores the unique identification code of the USB Key , this embodiment uses the RSA algorithm as an example for illustration. The online banking transaction method includes peer-to-peer entity authentication and a session process. Peer-to-peer entity authentication is a process in which the USB Key and the online banking ...
Embodiment 2
[0295] Figure 4 and Figure 5 It is a flow chart of the online secure transaction method in Embodiment 2 of the present invention. Such as Figure 4 and Figure 5 As shown, an online secure transaction method is provided. The difference from Embodiment 1 is that in this embodiment, a process of negotiating a session key is added to the process of peer entity authentication, and the negotiated key is used during the session. The session key encrypts and decrypts the signature instruction, making the entire online transaction process more secure
[0296] Such as Figure 4 As shown, the specific steps of the peer entity authentication process are as follows:
[0297] Step S3001 to step S3015 are the same as step S1001 to step S1015 in Embodiment 1, and will not be repeated here.
[0298] Step S3016, the server decrypts the third ciphertext to obtain the second session ID and the second random number, the server authenticates the third ciphertext M3, the second session ID, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com