Encryption method for communication between IoT terminal and cloud
An Internet of Things terminal and encryption method technology, applied in the field of lightweight Internet of Things security solutions, can solve the problems of paralyzed Internet of Things terminals or clouds, no two-way authentication between terminals and clouds, etc., to meet security requirements, reliable two-way authentication, The effect of reducing consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
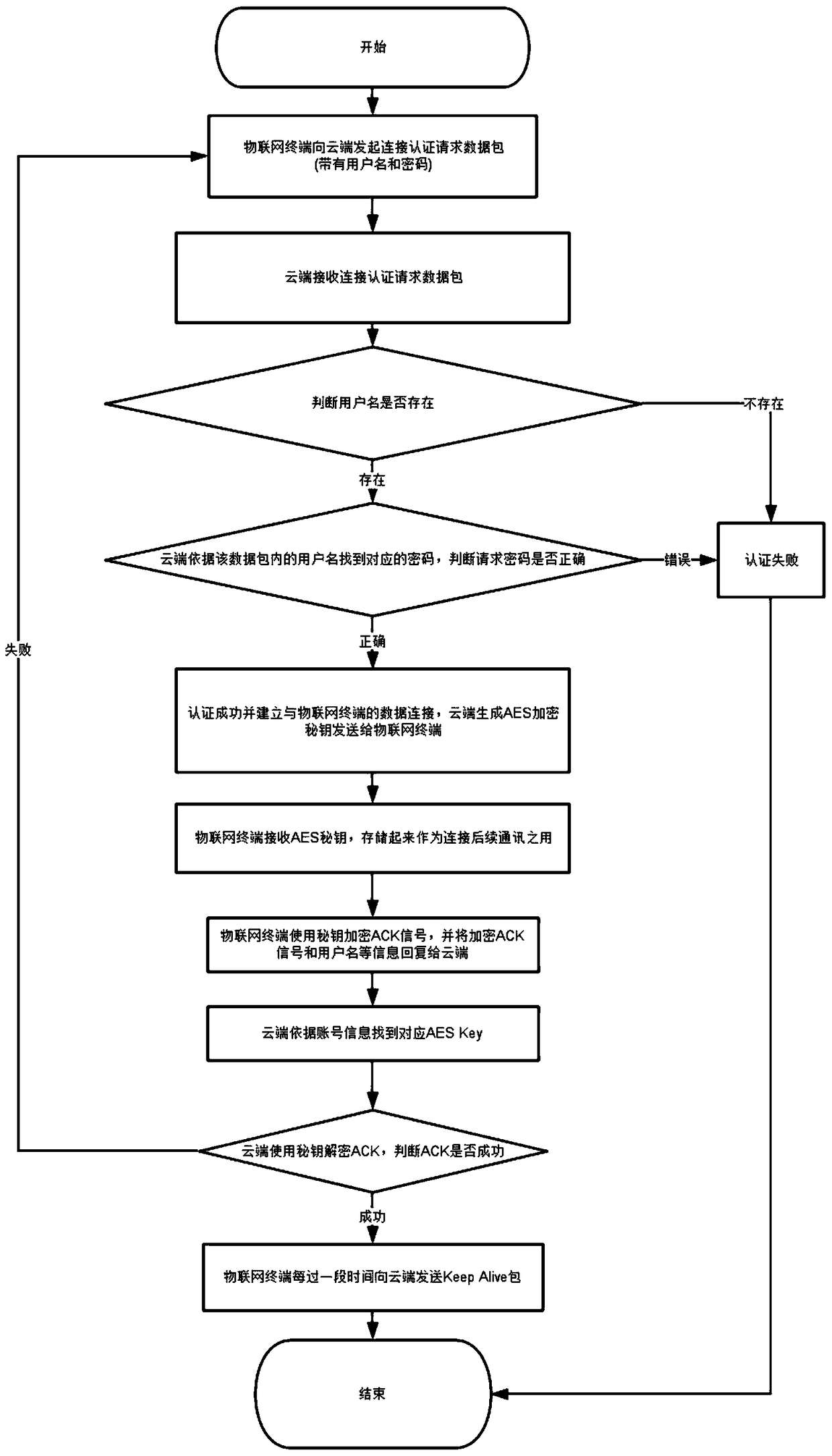
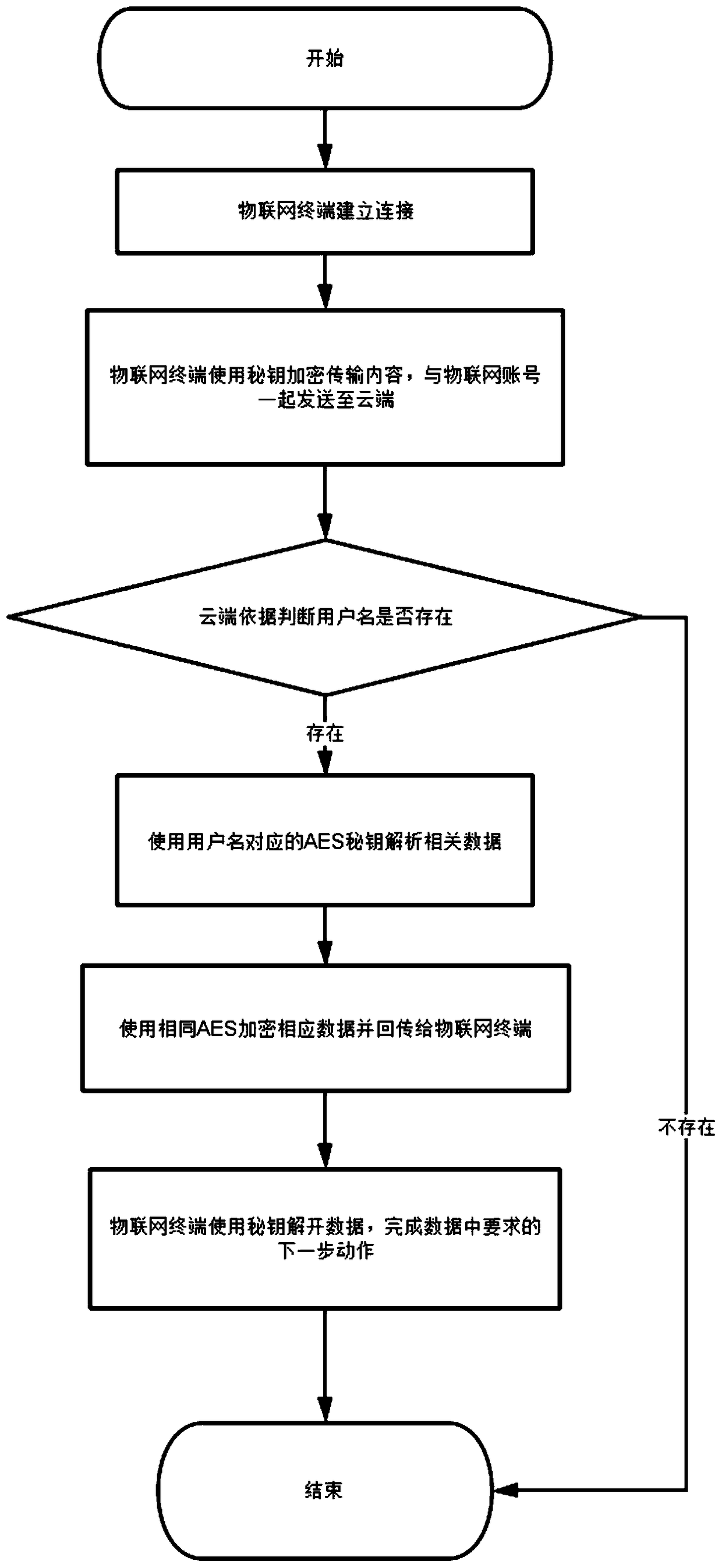
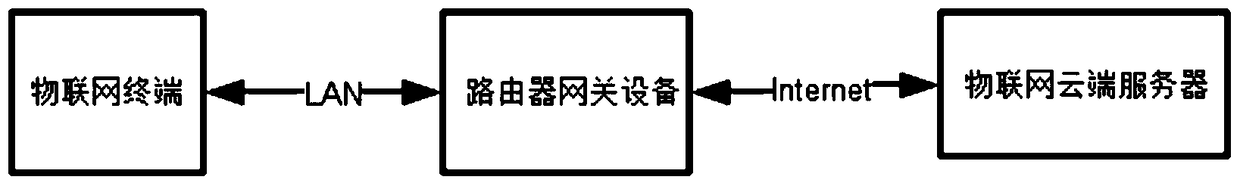
[0027] image 3 It is a schematic diagram of the system architecture of the present invention for IoT terminal and cloud communication; Figure 4 It is a schematic diagram of the encrypted communication process between the Internet of Things terminal and the cloud according to the present invention.
[0028] See image 3 and Figure 4 , the components of the communication system between IoT terminal and cloud provided by the present invention mainly include three parts, cloud, router gateway device and IoT terminal, wherein the router gateway device is generally a transparent device for transparent transmission in communication. The key to this solution lies in two parts, one part is the fixed byte key part stored in the IoT terminal and the cloud at the same time, the secret key consists of several bytes of IoT terminal ID, AES key and several bytes...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com