Method for controlling data in active defense system of Honeynet
A technology of active defense and data control, applied in the field of information security, which can solve the problems of helplessness in intelligent identification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The present invention will be further described below in conjunction with drawings and embodiments.
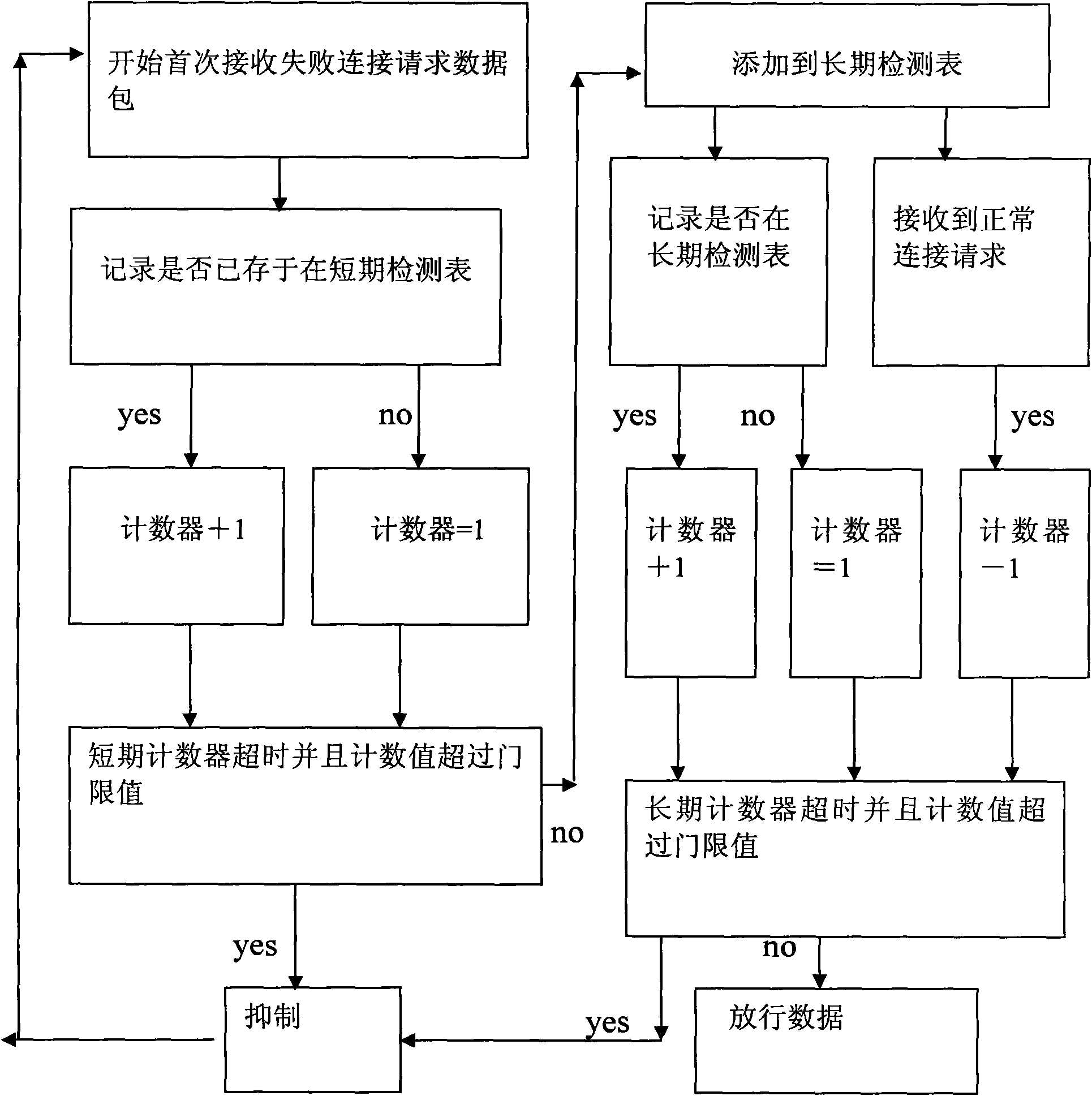
[0018] The present invention aims to provide a data control method in an advanced honeynet defense system, using a multi-round detection mechanism in the honeynet system framework to improve the data control and attack behavior feature classification technology; to solve the problems that plague the honeynet work efficiency Key issues of data control.
[0019] The present invention controls in a targeted manner by analyzing the differences among various attack behavior modes, so that the high-efficiency honeynet defense system can classify and identify the slow attack data flow. The traditional honeynet is not intelligent enough to deliberately slow down the attack rate in order to bypass the unknown attack behavior controlled by the firewall, and it is also helpless to intelligently distinguish the hidden attack behavior. The invention introduces a multi-round detecti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com