Network attack event traceability processing method and device, equipment and storage medium
A network attack and event technology, applied in the field of network security, can solve the problems of single traceability analysis dimension, inability to trace the source of network attack events, etc., and achieve the effect of accurate traceability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
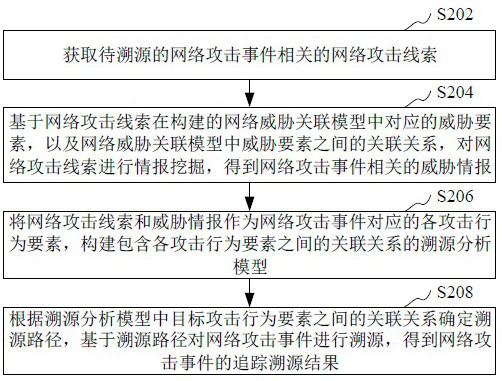
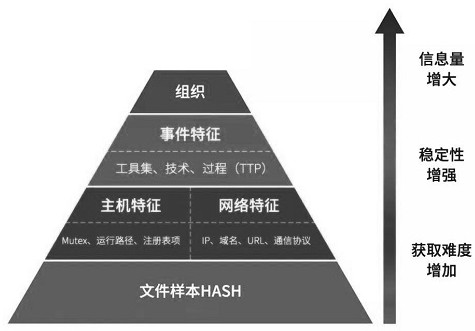
[0081] Example 1, for the network attack clues of log data belonging to the time dimension, it usually records the attacker’s attack behavior on the victim device. Network attacks are generally linear, and usually have contextual information and attack strategy models. This dimension is mainly from TTPS intelligence for analysis. Since the series of attack behaviors of the attackers belonging to the same attack group on the victim device and the order of each attack behavior are relatively similar, based on the log data and the network threat correlation model constructed based on the The attack behavior and attack time are related to the similar attack source, so as to dig out the attack organization associated with the similar attack source. For example, the record of a targeted network attack event records that the attack source first uses the white file to load the malicious PE file, then operates the cmd command, then checks netstat-ano to check the network status, and fi...
example 2
[0084]Example 2, for IOC intelligence network attack clues belonging to the space dimension, such as IP address, domain name, URL, in addition to basic information such as the operator of the IP address, IP open port, ASN, registration information of the domain name, etc., it also includes the domain name The registration information, similarity of domain names, etc., whether the URL is a malicious URL, detailed information of the URL, and similarity of the URL also include the association relationship between the IP address, domain name, URL, and MD5. Malicious network attackers are also in line with the inertia of human thinking. They have certain preferences when creating or selecting domain names. There are certain similarities in the domain names or URLs of the same group or organization. These infrastructures also have certain short-term invariance, so when malicious groups attack, the infrastructures used by similar incidents have one or more IOCs that are the same or si...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com