APT organization identification method and apparatus
An identification method and organizational technology, applied in the field of data processing, can solve problems such as sabotage and effective defense schemes for APT organization attacks that have not yet been proposed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
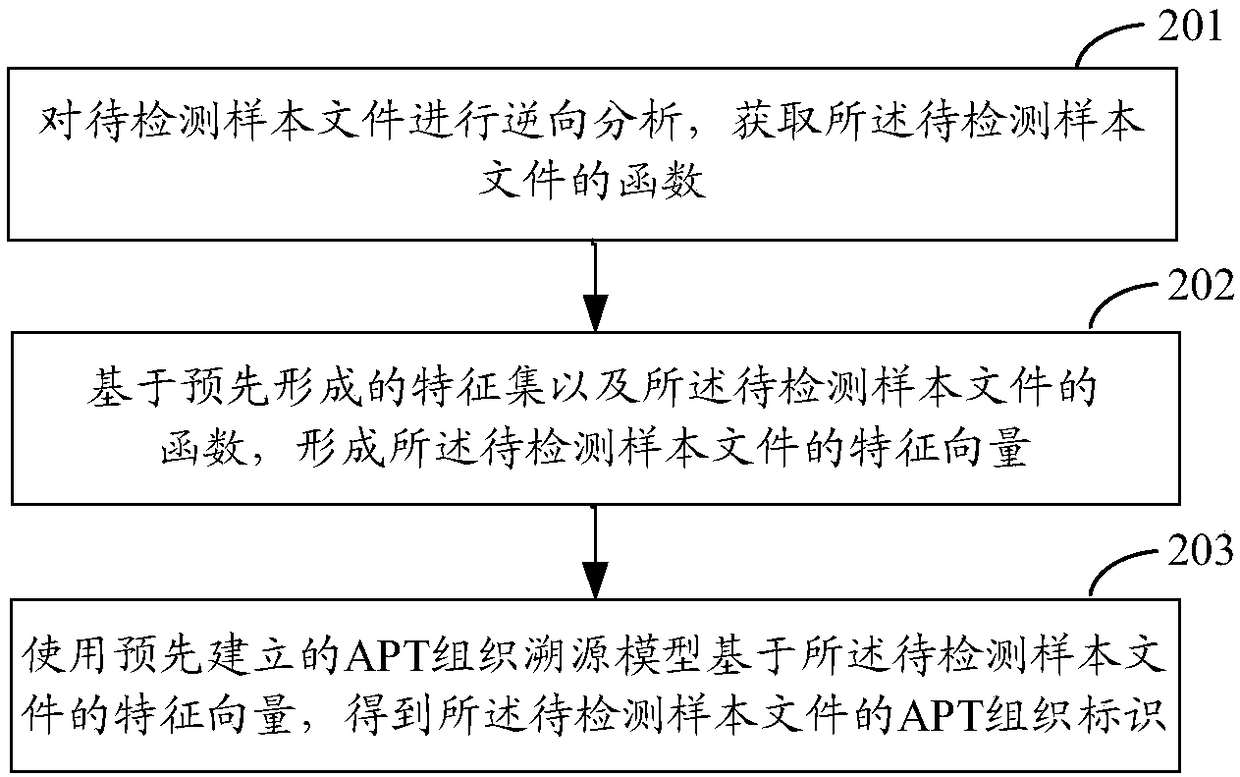
[0043] A method for identifying an APT organization, such as figure 2 shown, may include:
[0044] Step 201, perform reverse analysis on the sample file to be detected, and obtain the function of the sample file to be detected;
[0045] Step 202: Based on the pre-formed feature set and the function of the sample file to be detected, a feature vector of the sample file to be detected is formed, and the feature vector represents the relationship between the function in the sample file to be detected and the feature set , one feature set is a set of similar function sets, and the functions in the similar function set correspond to the same APT organization;
[0046]Step 203, using a pre-established APT tissue traceability model based on the feature vector of the sample file to be detected to obtain the APT tissue identifier of the sample file to be detected, the APT tissue traceability model is a calculation model based on a machine learning algorithm.
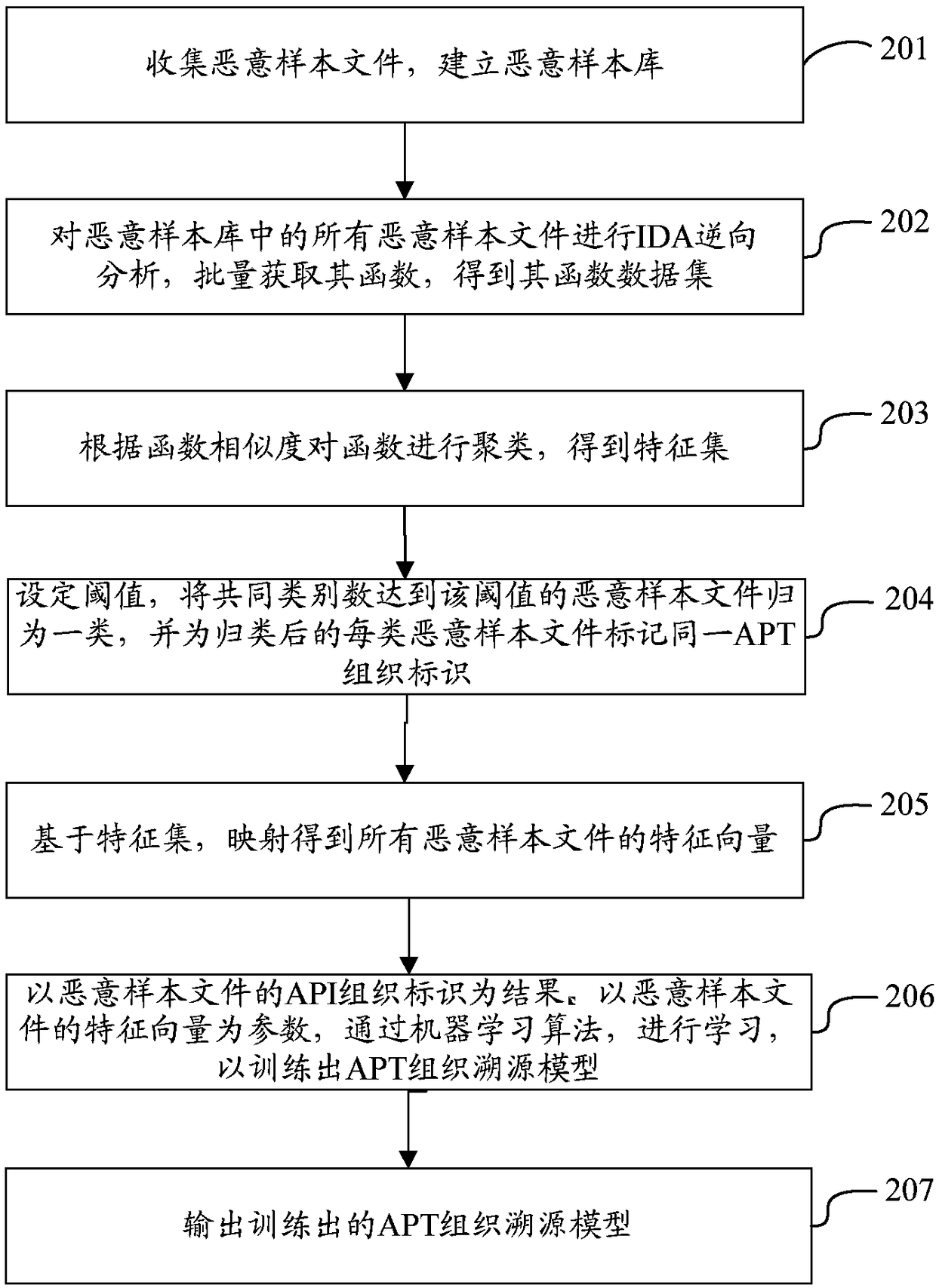
[0047] The method of t...
Embodiment 2
[0100] An identification device for an APT organization, such as Figure 7 As shown, it includes: a memory 71 and a processor 72; the memory 101 stores a computer program, and the processor 72 is configured to read the computer program to execute the operation of the method for identifying an APT organization in Embodiment 1.
[0101] Specifically, the processor 72 may at least be configured to read the computer program to execute steps 201 to 203 in the first example. In addition, the processor 72 may also be configured to read the computer program to execute other operations of the method for identifying an APT organization in Embodiment 1. The technical details of these operations can refer to Embodiment 1.
[0102] It should be noted, Figure 7 The shown structure only shows the basic structure of the identification device of the APT organization in this embodiment. In practical applications, the identification device of the APT organization may include not only the bas...
Embodiment 3
[0104] A computer-readable storage medium. A computer program is stored on the computer-readable storage medium. When the computer program is executed by a processor, the steps of the method for identifying an APT organization in Embodiment 1 are implemented.
[0105] Specifically, when the computer program is executed by the processor, at least the operations of steps 201 to 203 are implemented. In addition, when the computer program is executed by the processor, other steps of the method for identifying an APT organization in Embodiment 1 can be implemented. The technical details of these steps can refer to Embodiment 1.
[0106] In practical applications, the computer-readable medium includes permanent and non-permanent, removable and non-removable storage media, and information storage can be realized by any method or technology. Information may be computer readable instructions, data structures, modules of a program, or other data. Examples of computer storage media inc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com