Collapsed host computer detection method
A detection method and host technology, applied in the field of network security, can solve problems such as inability to prevent in advance, large losses, etc., and achieve the effect of ensuring long-term visibility and network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
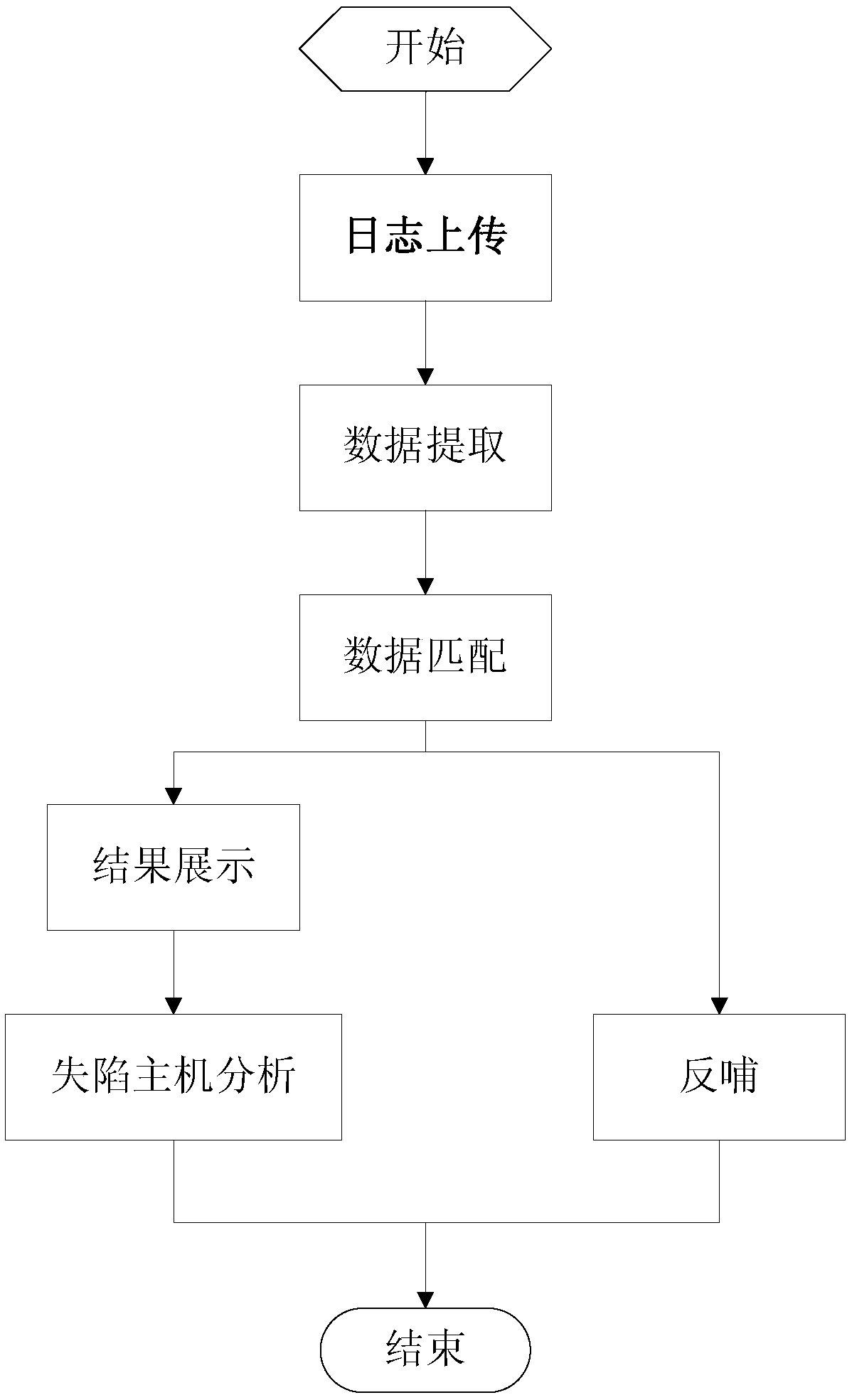
[0025] see figure 1 In order to better understand the technical solution of the present invention, the inventors of the present invention will describe in detail below through specific embodiments in conjunction with the accompanying drawings:
[0026] A kind of lost host detection method of the present invention comprises the following steps:
[0027] Log upload steps: Each border security probe device uploads the log data generated by the traffic between security domains, including application access logs, URL access logs, file transfer logs, and threat logs to the security cloud early warning platform. The role of border security probes is to continuously upload and summarize valuable log data to the security cloud early warning platform based on its own perception of user behavior and threat information in the network.
[0028] Data extraction steps: the security cloud early warning platform aggregates the log data reported by each border security probe device to the clou...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com