Log-based threat intelligence detection method and device
A detection method and intelligence technology, applied in the field of log-based threat intelligence detection, can solve the problems of reduced network operation speed, inability of detection method efficiency to meet requirements, and small data security detection coverage, so as to achieve the effect of improving detection efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The specific embodiments of the present invention will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
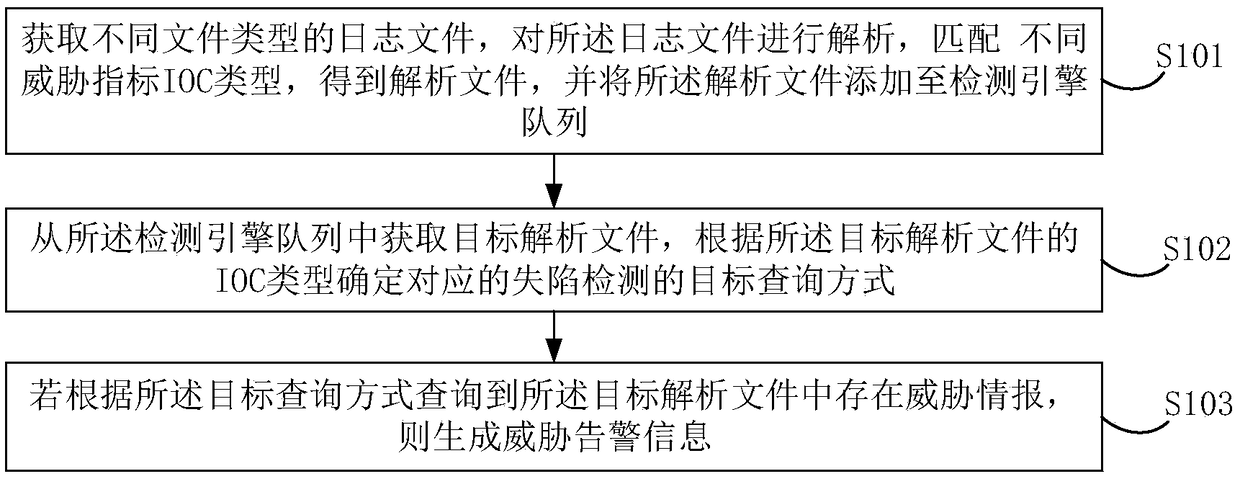
[0049] figure 1 A schematic flowchart of a log-based threat intelligence detection method provided in this embodiment is shown, including:
[0050] S101. Obtain log files of different file types, parse the log files, match different threat indicator IOC types, obtain parsed files, and add the parsed files to a detection engine queue.
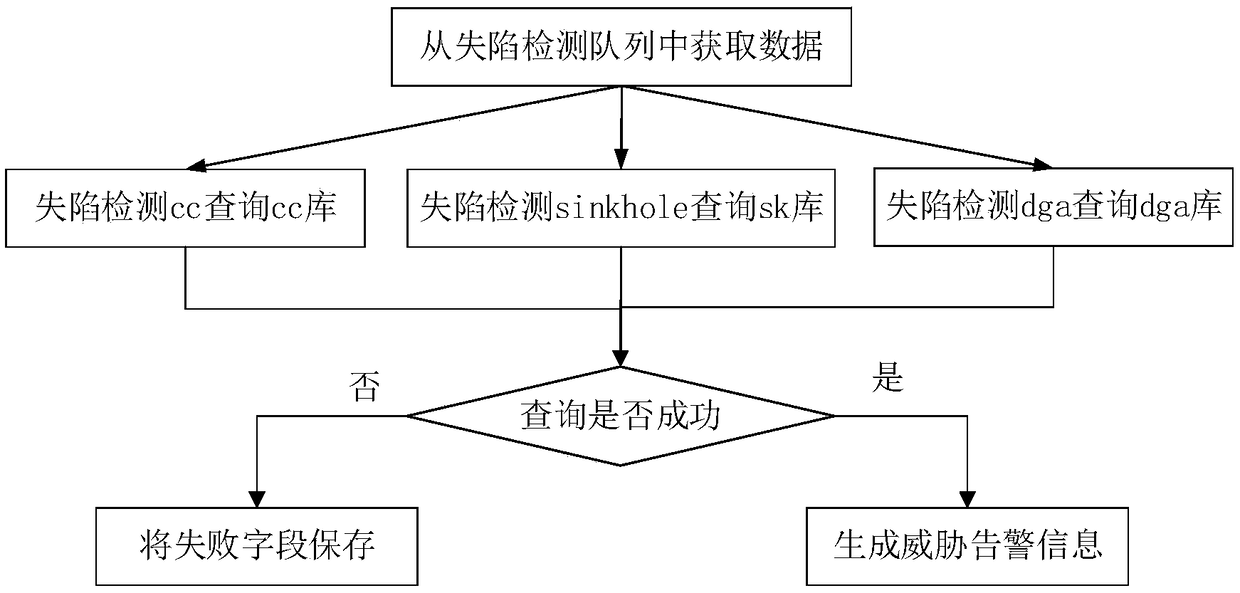
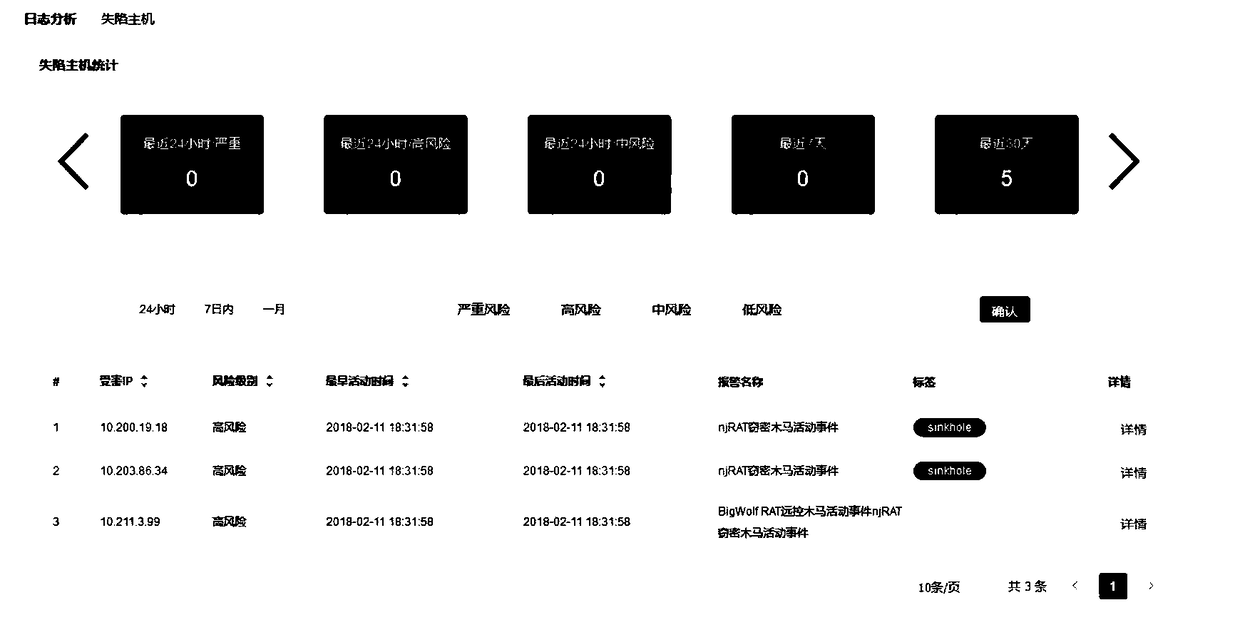
[0051] Among them, the file type of the log file can include various file methods, such as file method, logstash method or API method, and the specific file type can include JSON, Syslog, Netflow, DNS, HTTP and other log traffic and log records of the SEIM system. By obtaining log files of different file types, it is convenient to agg...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com