Text data-oriented threat intelligence knowledge graph construction method
A technology of knowledge graph and text data, applied in the fields of unstructured text data retrieval, text database clustering/classification, special data processing applications, etc. Problems such as poor recognition effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] The following will clearly and completely describe the technical solutions in the embodiments of the present application with reference to the drawings in the embodiments of the present application.
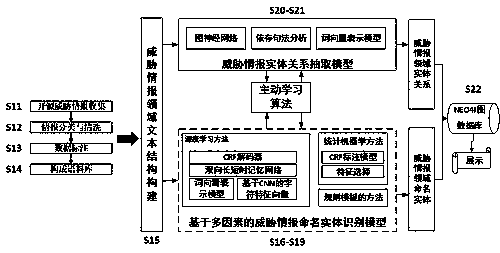
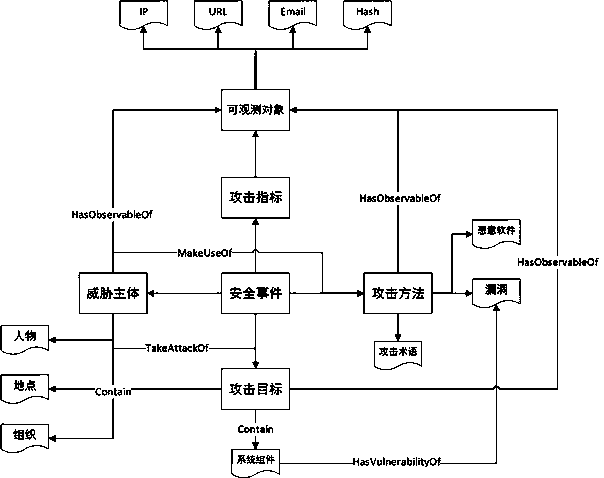
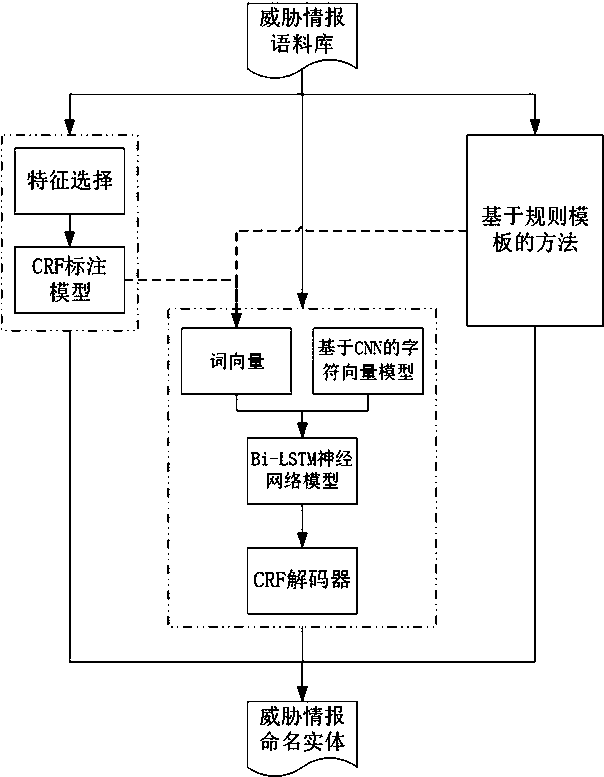
[0054] Threat intelligence technology is considered to be one of the effective means to combat advanced persistent attacks. Threat intelligence information based on text data is written by security researchers, which has higher accuracy and richer attack process information. Therefore, the present invention proposes a text data-oriented threat intelligence knowledge map construction method for how to extract structured and high-quality threat intelligence information from unstructured text information and display reasonably. The specific technical scheme is as follows.
[0055] Such as figure 1 The main architecture diagram of the system is shown, and the related design and deployment architecture of the threat awareness system are introduced in detail. Such as figure 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com